8937337c378261c3128bb2f3086efc6c.ppt
- Количество слайдов: 57

All slides © 2006 RSA Laboratories

RFID (Radio-Frequency IDentication) takes many forms…
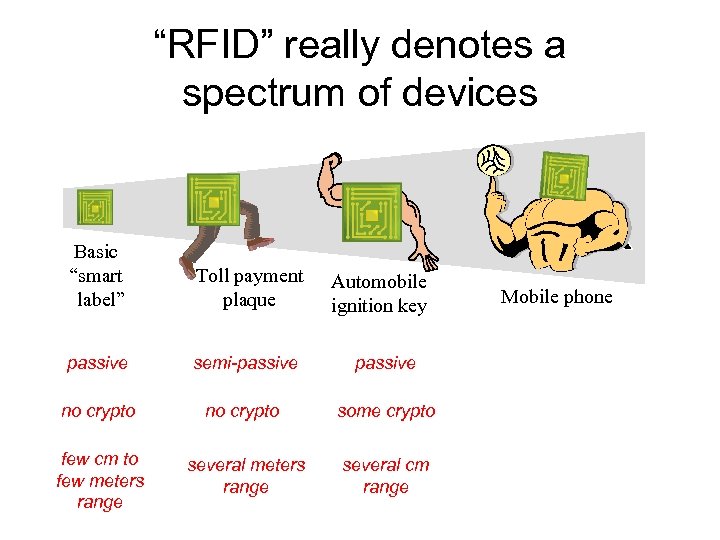
“RFID” really denotes a spectrum of devices Basic “smart label” Toll payment plaque passive semi-passive no crypto some crypto few cm to few meters range several cm range Automobile ignition key Mobile phone
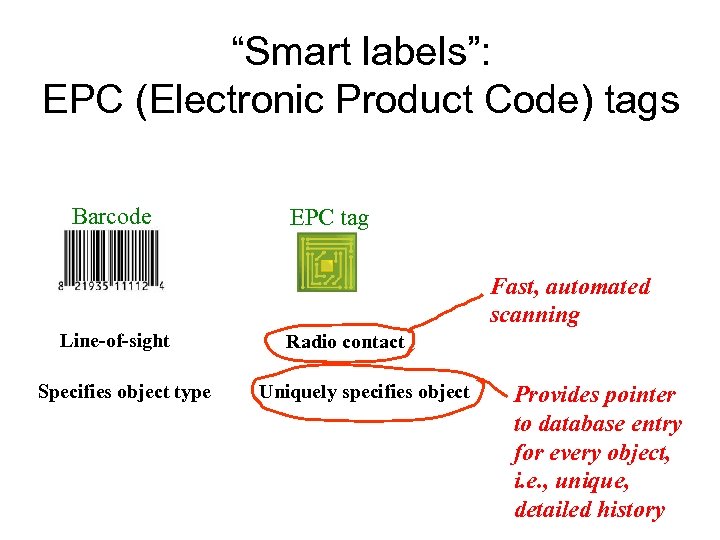
“Smart labels”: EPC (Electronic Product Code) tags Barcode EPC tag Fast, automated scanning Line-of-sight Specifies object type Radio contact Uniquely specifies object Provides pointer to database entry for every object, i. e. , unique, detailed history
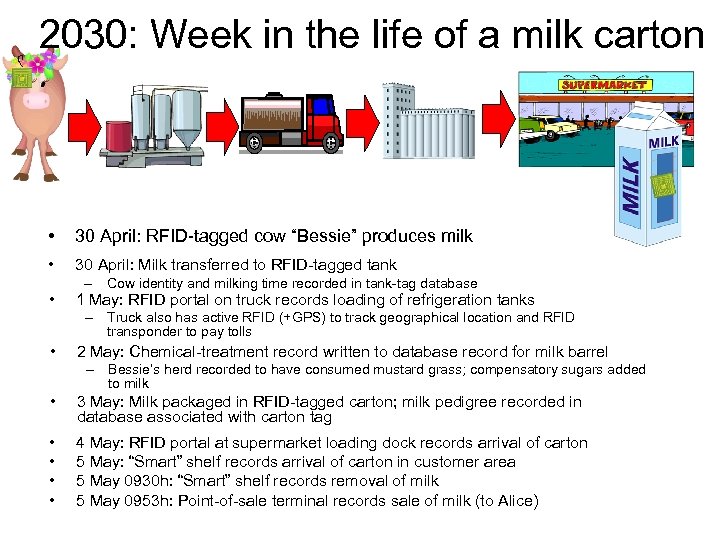
2030: Week in the life of a milk carton • 30 April: RFID-tagged cow “Bessie” produces milk • 30 April: Milk transferred to RFID-tagged tank • – Cow identity and milking time recorded in tank-tag database 1 May: RFID portal on truck records loading of refrigeration tanks – Truck also has active RFID (+GPS) to track geographical location and RFID transponder to pay tolls • 2 May: Chemical-treatment record written to database record for milk barrel – Bessie’s herd recorded to have consumed mustard grass; compensatory sugars added to milk • 3 May: Milk packaged in RFID-tagged carton; milk pedigree recorded in database associated with carton tag • • 4 May: RFID portal at supermarket loading dock records arrival of carton 5 May: “Smart” shelf records arrival of carton in customer area 5 May 0930 h: “Smart” shelf records removal of milk 5 May 0953 h: Point-of-sale terminal records sale of milk (to Alice)

2030: Week in the life of a milk carton • 6 May 0953 h: Supermarket transfers carton tag ownership to Alice’s smart home • • 6 May 1103 h: Alice’s refrigerator records arrival of milk 6 May 1405 h: Alice’s refrigerator records removal of milk; refrigerator looks up database-recorded pedigree and displays: “Woodstock, Vermont, Grade A, light pasturization, artisanal, USDA organic, breed: Jersey, genetic design #81726” • 6 May 1807 h: Alice’s “smart” home warns domestic robot that milk has been left out of refrigerator for more than four hours 6 May 1809 h: Alice’s refrigerator records replacement of milk • • 7 May 0530 h: Domestic robot uses RFID tag to locate milk in refrigerator; refills baby bottle

2030: Week in the life of a milk carton • 6 May 0953 h: Supermarket transfers carton tag ownership to Alice’s smart home • • 6 May 1103 h: Alice’s refrigerator records arrival of milk 6 May 1405 h: Alice’s refrigerator records removal of milk; refrigerator looks up database-recorded pedigree and displays: “Woodstock, Vermont, Grade A, light pasturization, artisanal, USDA organic, breed: Jersey, genetic design #81726” • 6 May 1807 h: Alice’s “smart” home warns domestic robot that milk has been left out of refrigerator for more than four hours 6 May 1809 h: Alice’s refrigerator records replacement of milk • • 7 May 0530 h: Domestic robot uses RFID tag to locate milk in refrigerator; refills baby bottle 7 May 0531 h: Robot discards carton; “Smart” refrigerator notes absence of milk; transfers order to Alice’s PDA/phone/portable server grocery list 7 May 2357 h: Recycling center scans RFID tag on carton; directs carton to paper-brick recycling substation
r. Fid today: in your pocket Note: Often just emit static identifiers, i. e. , they are just smart labels! Proximity cards
in your pocket RFID helps secure hundreds of millions of automobiles • Cryptographic challenge-response • Philips claims more than 90% reduction in car theft thanks to RFID! • Note: some devices, e. g. , Texas Instruments DST, are weak… f Automobile ignition keys

in your pocket • Exxon. Mobil Speedpass. TM • RFID now offered in all major credit cards in U. S. … Payment devices
in animals • Cattle • Housepets 50 million+ “Not Really Mad” The cat came back, the very next day…

on people • • Schools Amusement parks Hospitals In the same vein: mobile phones with GPS…

in passports • Dozens of countries issuing or soon to issue RFID-enabled passports • Other identity documents, e. g. , drivers’ licenses, to follow

in mobile phones NFC (Near-Field Consortium) Showtimes: 16. 00, 19. 00 • Also, ticket purchases, payments, comparison shopping Phone can act as reader or tag • NFC is a general-purpose protocol • Already available in some models

in currency? • Talk in 2003 -4 of planting RFID tags in 10, 000 Yen banknotes and Euro banknotes • Talk has dissipated • Main interest: anti-counterfeiting
in pharmaceuticals • Anti-counterfeiting: Better supply-chain visibility means less fraud – U. S. govt. urging RFID to combat counterfeiting of drugs • Medical compliance: Greater independence (and privacy!), particularly for elderly
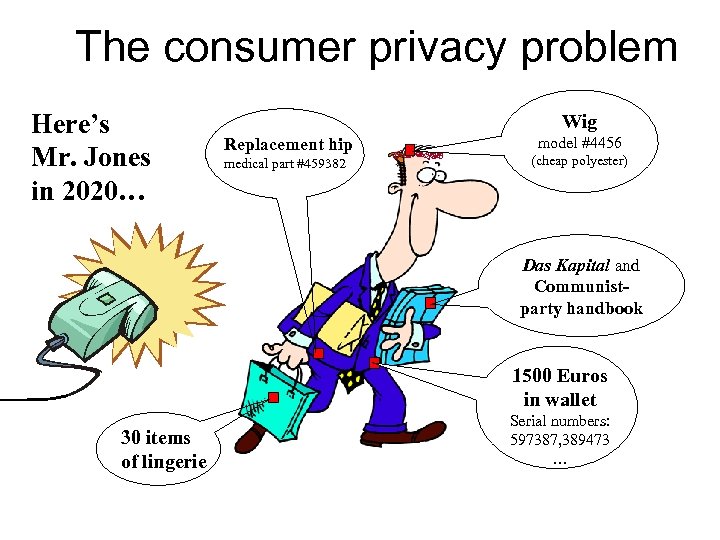
The consumer privacy problem Here’s Mr. Jones in 2020… Wig Replacement hip medical part #459382 model #4456 (cheap polyester) Das Kapital and Communistparty handbook 1500 Euros in wallet 30 items of lingerie Serial numbers: 597387, 389473 …

…and the tracking problem Wig serial #A 817 TS 8 • Mr. Jones pays with a credit card; his RFID tags now linked to his identity; determines level of customer service – Think of car dealerships using drivers’ licenses to run credit checks… • Mr. Jones attends a political rally; law enforcement scans his RFID tags • Mr. Jones wins Turing Award; physically tracked by paparazzi via RFID

Suica Image courtesy of Kevin Fu

Suica Images courtesy of Kevin Fu
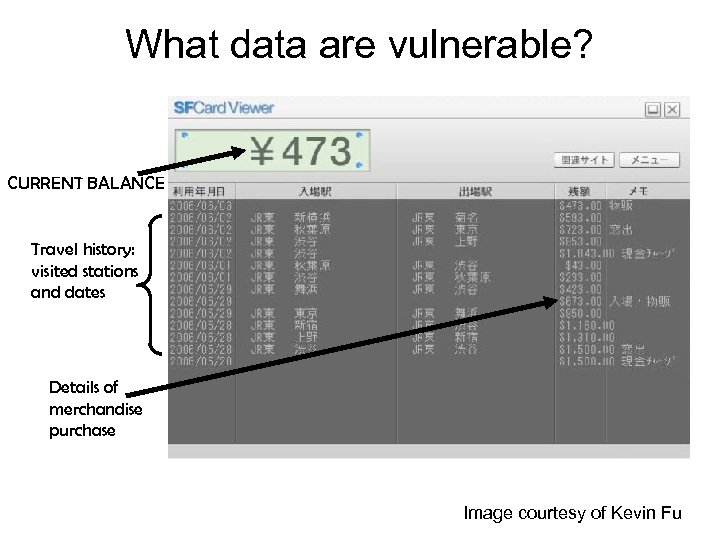
What data are vulnerable? CURRENT BALANCE Travel history: visited stations and dates Details of merchandise purchase Image courtesy of Kevin Fu
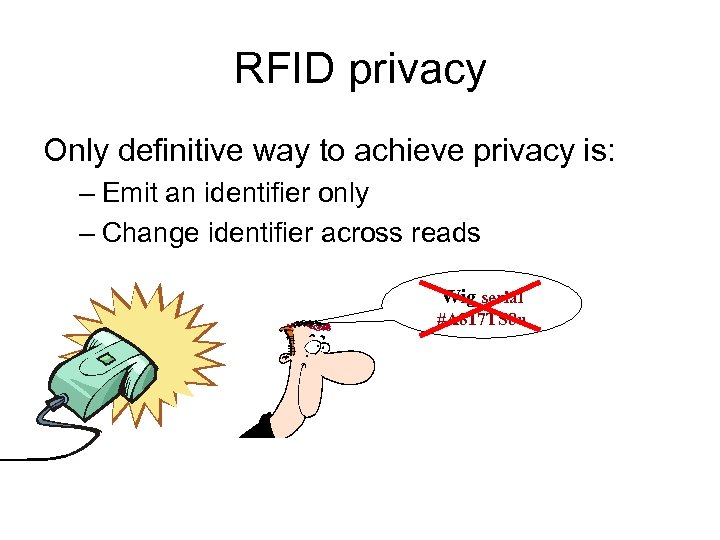
RFID privacy Only definitive way to achieve privacy is: – Emit an identifier only – Change identifier across reads Wig serial #A 817 TS 8 u
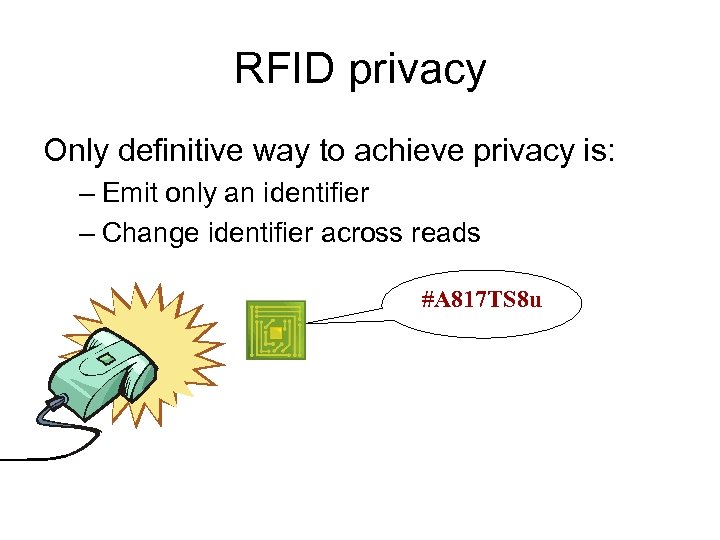
RFID privacy Only definitive way to achieve privacy is: – Emit only an identifier – Change identifier across reads #A 817 TS 8 u
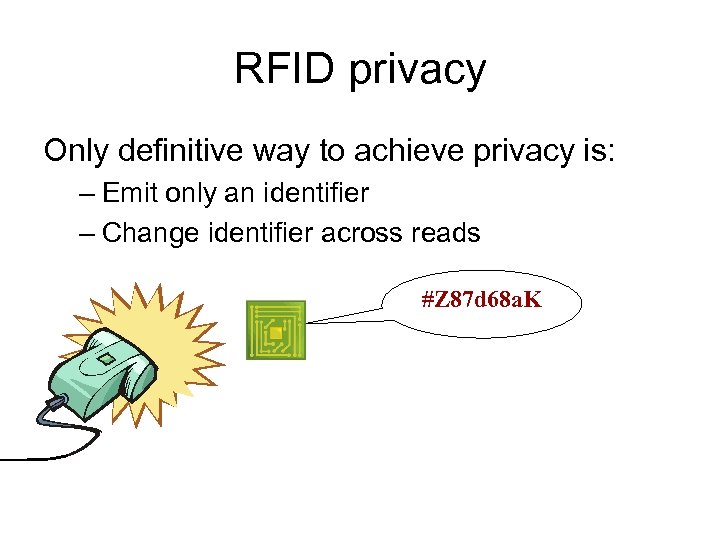
RFID privacy Only definitive way to achieve privacy is: – Emit only an identifier – Change identifier across reads #Z 87 d 68 a. K
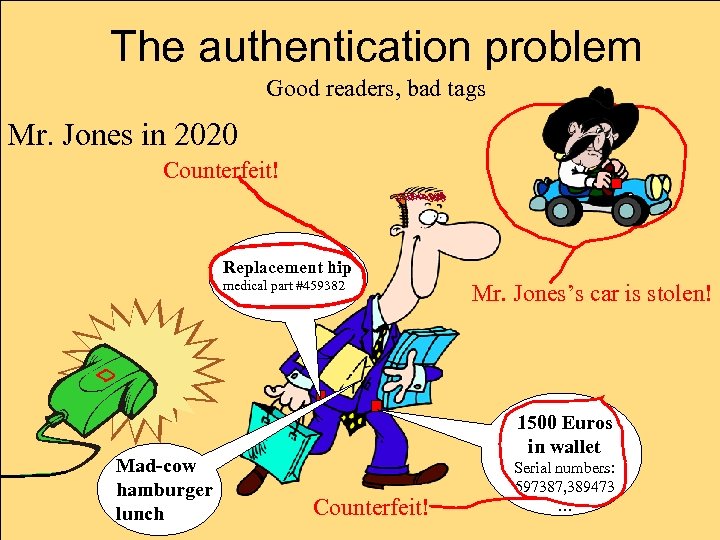
The authentication problem Good readers, bad tags Mr. Jones in 2020 Counterfeit! Replacement hip medical part #459382 Mad-cow hamburger lunch Mr. Jones’s car is stolen! 1500 Euros in wallet Counterfeit! Serial numbers: 597387, 389473 …

Won’t crypto solve our problems? Side-channel countermeasures AES We can do: • Challenge-response for authentication • Mutual authentication and/or encryption for privacy But: 1. Moore’s Law vs. pricing pressure 2. Beyond simple “terrestrial” problems, basic cryptography may not be enough… This is theme of our talk!
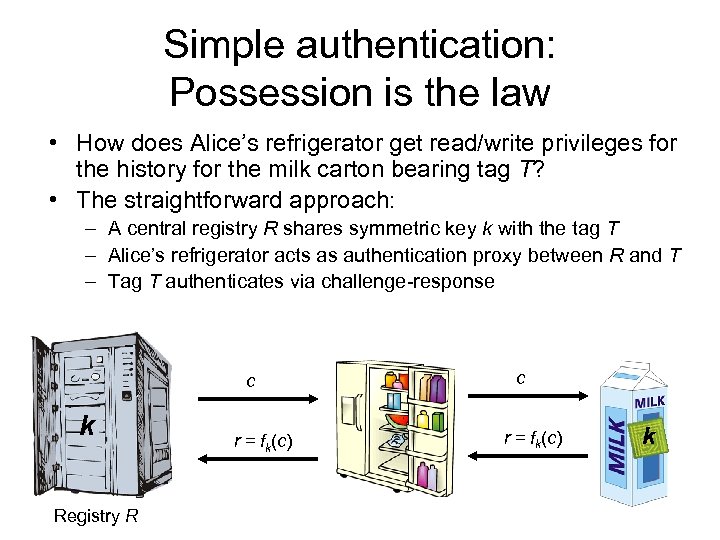
Simple authentication: Possession is the law • How does Alice’s refrigerator get read/write privileges for the history for the milk carton bearing tag T? • The straightforward approach: – A central registry R shares symmetric key k with the tag T – Alice’s refrigerator acts as authentication proxy between R and T – Tag T authenticates via challenge-response c k Registry R r = fk(c) c r = fk(c) k

Simple authentication: Possession is the law • But what if the tag is on Alice’s wristwatch? – Should any nearby reader be able to read tag history? – Should any nearby reader be able to modify tag history? • What if registry R is unavailable? – Will the tag carry information on board? – If so, who can access it? – Does Alice’s baby get its milk?
The Veri. Chip. TM + = ? ? ? Human-implantable RFID
The Veri. Chip. TM • Proposed for medical-patient identification • Also proposed and used as an authenticator for physical access control, a “prosthetic biometric” – E. g. , Mexican attorney general purportedly used for access to secure facility + = • What kind of cryptography does it have? – None: It can be easily cloned • So shouldn’t we add a challenge-response protocol? Human-implantable RFID • Cloning may actually be a good thing
The Veri. Chip. TM • Physical coercion and attack – In 2005, a man in Malaysia had his fingertip cut off by thieves stealing his biometric-enabled Mercedes – What would happen if the Veri. Chip were used to access ATM machines and secure facilities? • Perhaps it is better then if tags can be cloned and are not used for authentication—only for identification • But if a tag is cloneable, and used for identification, does that mean that privacy is impossible? – I. e. , does cloneability imply an ability to track?
Private identification • A very simple scheme allows for simultaneous cloneability and privacy • El Gamal public-key cryptosystem: – Randomized scheme: C = EPK, r [m] – Semantic security: Cannot distinguish between ciphertexts C and C’ on known plaintexts without knowledge of SK • Adversary cannot distinguish between C = EPK, r [Alice] and C’ = EPK, r’ [Bob]
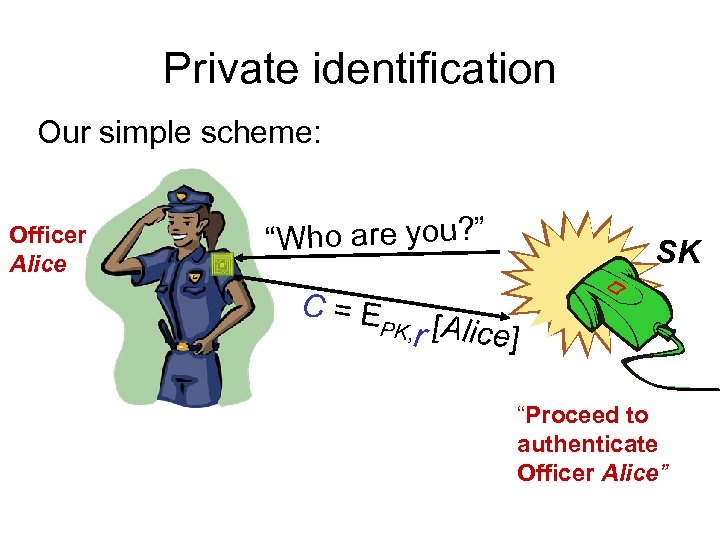
Private identification Our simple scheme: Officer Alice “Who are you? ” C=E SK r [Alice] PK, “Proceed to authenticate Officer Alice”

Private identification Take two: Officer Alice “Who are you? ” C’ = E SK r’ [Alice] PK , “Proceed to authenticate Officer Alice”

Private identification • Semantic security → An attacker who intercepts C and C’ cannot tell if they come from the same chip – Attacker cannot identify or track Alice • But attacker can still clone Alice’s chip! • El Gamal re-encryption (homomorphism): – Let U = EPK, r [1] have uniformly random r – Then given C = EPK, r’ [m], the distribution Cx. U is uniform over ciphertexts on m • Clone chip selects U and outputs Cx. U • Clone chip is indistinguishable from Alice’s!
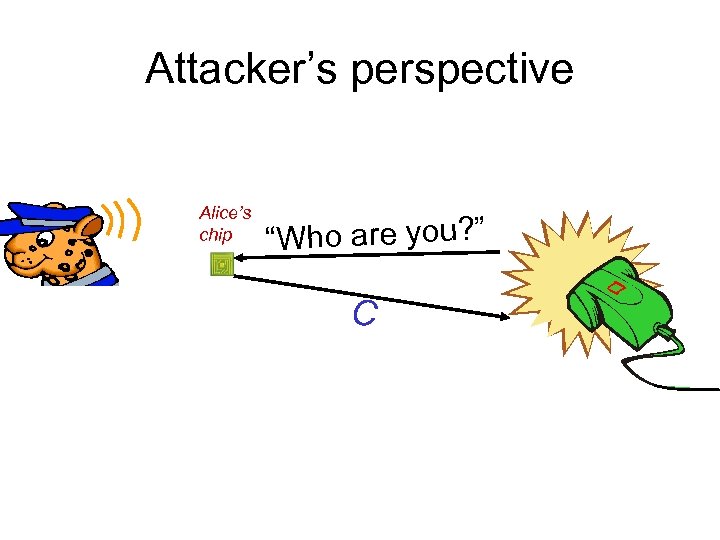
Attacker’s perspective Alice’s chip “Who are you? ” C
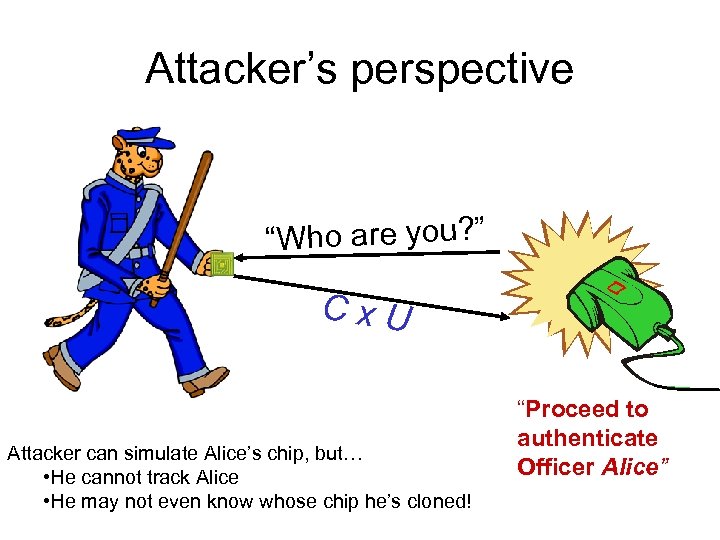
Attacker’s perspective “Who are you? ” Cx. U Attacker can simulate Alice’s chip, but… • He cannot track Alice • He may not even know whose chip he’s cloned! “Proceed to authenticate Officer Alice”

The covert-channel problem Suppose there is a secret sensor… Officer Alice “Who are you? ” SK C “Officer Alice has low blood pressure and high blood-alcohol”

The covert-channel problem Suppose there is a secret sensor… Officer Alice “Who are you? ” SK C “Officer Alice recently passed near the RFID reader of a casino”

The covert-channel problem Suppose there is a secret sensor… Officer Alice “Who are you? ” SK C “Mercury switch indicates that Officer Alice took a nap this afternoon. ”

How can we ensure no covert channels? • Must make outputs deterministic • Can also, e. g. , give PRNG keys to Alice • But can we: – Allow Alice to verify covert-freeness without exposing secret keys to her? – Enable a third party to verify covert-freeness? • It turns out that privacy and such verifiable covert-freeness are contradictory!
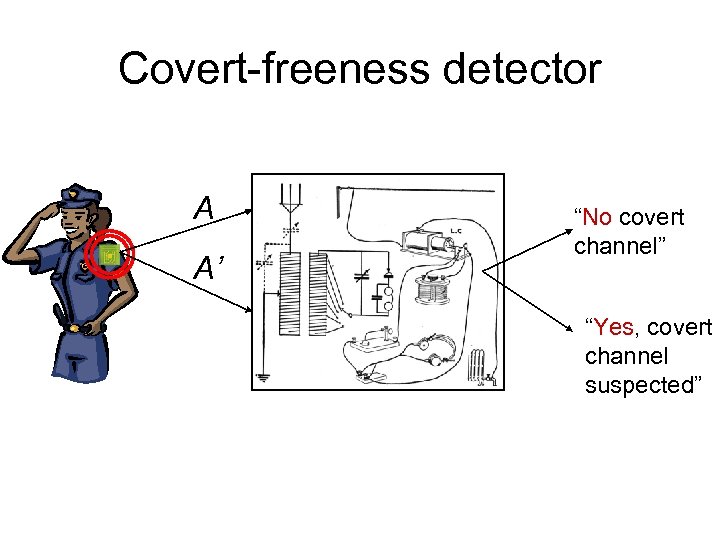
Covert-freeness detector A A’ “No covert channel” “Yes, covert channel suspected”
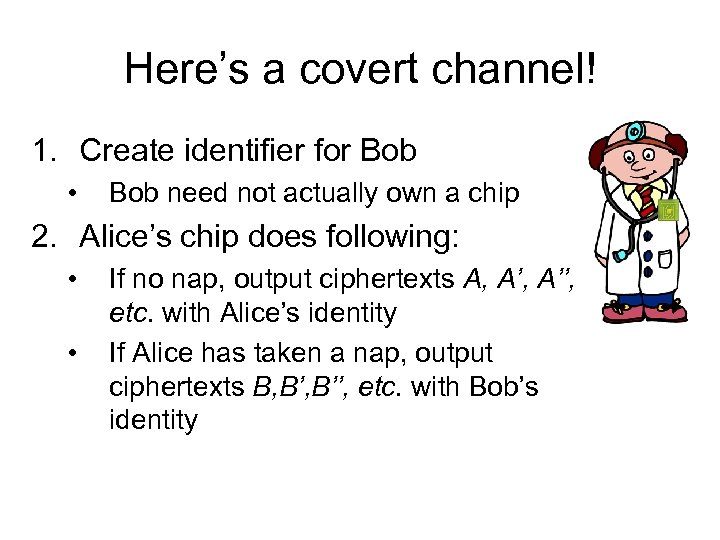
Here’s a covert channel! 1. Create identifier for Bob • Bob need not actually own a chip 2. Alice’s chip does following: • • If no nap, output ciphertexts A, A’’, etc. with Alice’s identity If Alice has taken a nap, output ciphertexts B, B’’, etc. with Bob’s identity
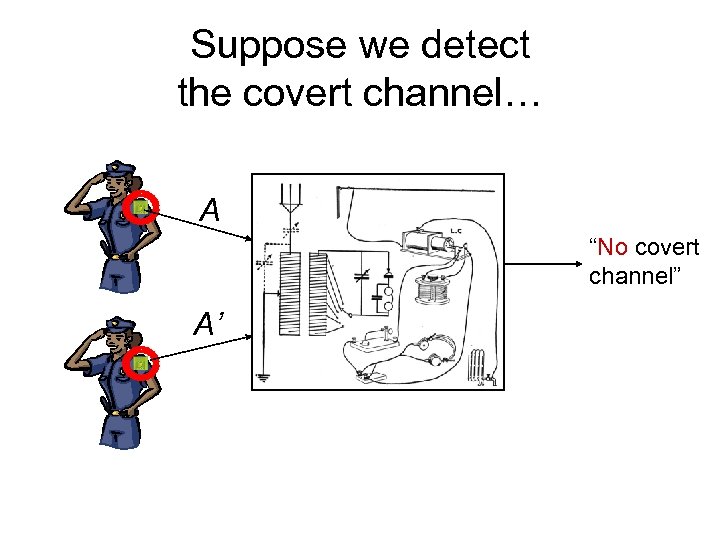
Suppose we detect the covert channel… A “No covert channel” A’
Suppose we detect the covert channel… A “Yes, covert channel B suspected”
Then we can distinguish between Alice and Bob: Privacy is broken! A “Yes, covert channel B suspected”
Then we can distinguish between Alice and Bob: Privacy is broken! A “A and B B represent different people”
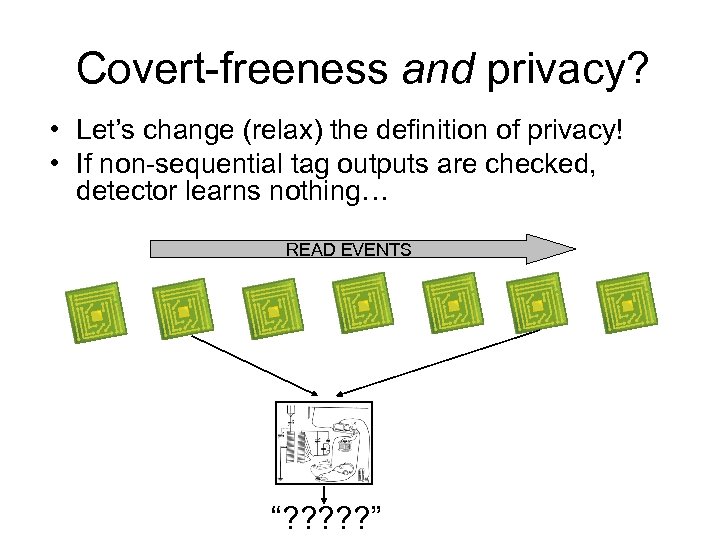
Covert-freeness and privacy? • Let’s change (relax) the definition of privacy! • If non-sequential tag outputs are checked, detector learns nothing… READ EVENTS “? ? ? ”
Covert-freeness and privacy? • Detector can do pairwise check only… • Achievable “efficiently” with pairings-based cryptography (ECC) READ EVENTS “Covert-free pair”
Covert-freeness and privacy? • Privacy is largely preserved because of locality • Covert-freeness checkable probabilistically, i. e. , with spot checks READ EVENTS “Covert-free pair”

Returning to basic issue of privacy: Kill codes • EPC tags have a “kill” function • • • Developed for EPC to protect consumers after point of sale • • • On receiving password, tag self-destructs Tag is permanently inoperative “Dead tags tell no tales” Privacy is preserved Simple and categorical, but not a wholly satisfying solution…

Problem 1: Post-consumer uses of tags k Dead tags perhaps not harmful, but certainly not beneficial…
Problem 2: RF signatures • Y. Oren and A. Shamir attacked EPC kill passwords via over-theair power analysis Found that dead tags are detectable! • – • Backscatter from antennas Hypothesize manufacturer type may be learnable • 3 type A tags (merchandise) • 2 type B tags (medication) • 10 type C tags (500 -Euro banknotes) • • Probably of limited significance, but still bears on privacy Do tags possess uniquely detectable RF fingerprints? – • Device signatures a staple of electronic warfare Cryptography would not help here!

So what might solve our problems? • The fact that privacy is not RFID specific • Laws and policy • RFID security as a database problem – Reduces problem to access control, but: – Accept tracking of identifiers – Create further dependence on network connectivity
So what might solve our problems? • Higher-powered intermediaries like mobile phones – RFID “Guardian” and RFID REP Please show reader certificate and privileges

So what might solve our problems? • Cryptography! – Urgent need for cheaper hardware for primitives and better sidechannel defenses • Some of talk really in outer limits, but basic caveats are important: – Pressure to build a smaller, cheaper tags without cryptography – RFID tags are close and personal, giving privacy a special dimension – RFID tags change ownership frequently – Key management will be a major problem • Think for a moment after this talk about distribution of kill passwords… • Are there good hardware approaches to key distribution, e. g. , proximity as measure of trust

To learn more • Largely collaborative work within RFID CUSP – www. rfid-cusp. org – Papers available on publications page • Papers: – “RFID security and privacy: a research survey” – “The security implications of Veri. Chip. TM cloning, ” • Joint work with J. Halamka, A. Stubblefield, and J. Westhues – “Covert channels in privacy-preserving identification systems” • Forthcoming joint work with Dan Bailey – “Power analysis of RFID tags” (on Internet; not RFID-CUSP) • Y. Oren and A. Shamir
8937337c378261c3128bb2f3086efc6c.ppt