6f38643bc5bc6ee8a0a3375a16cd12fa.ppt
- Количество слайдов: 74

Alcatel Omni. Switch Boot Camp Labs Edoardo Berera April 2005 1
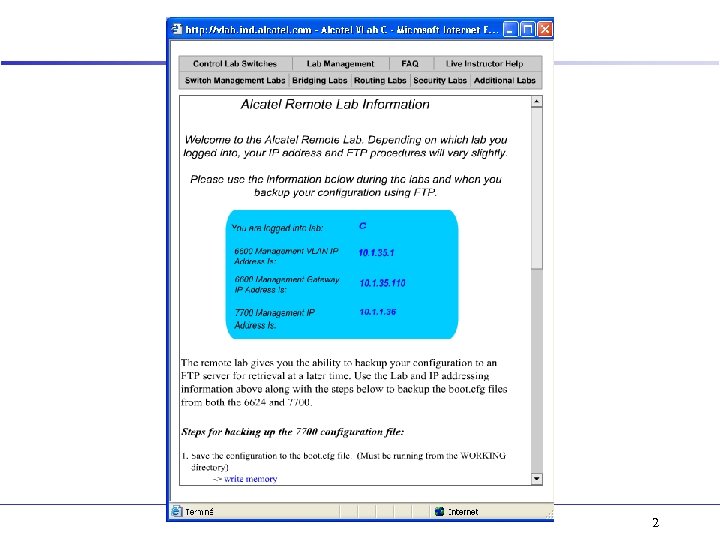
2
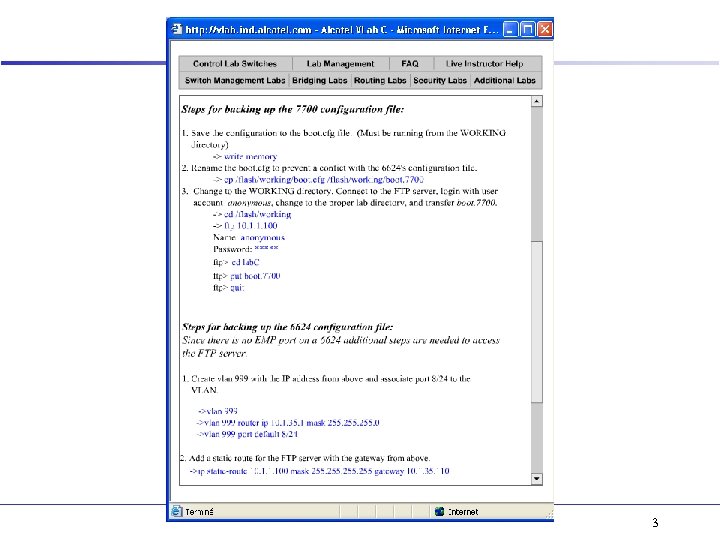
3
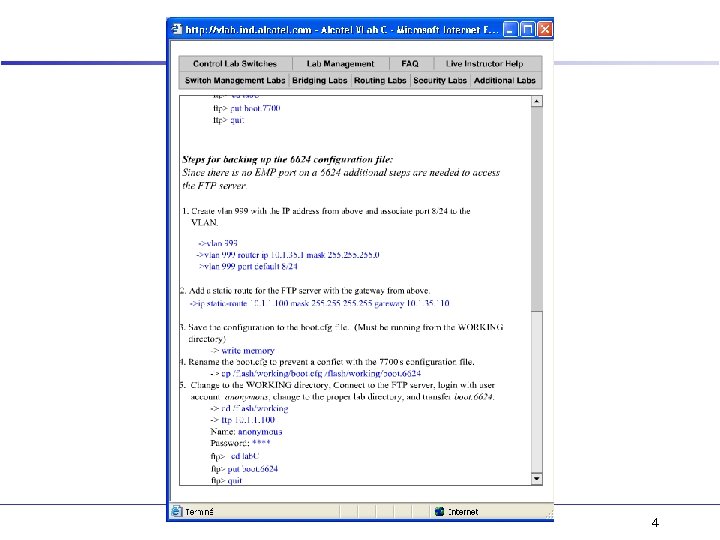
4
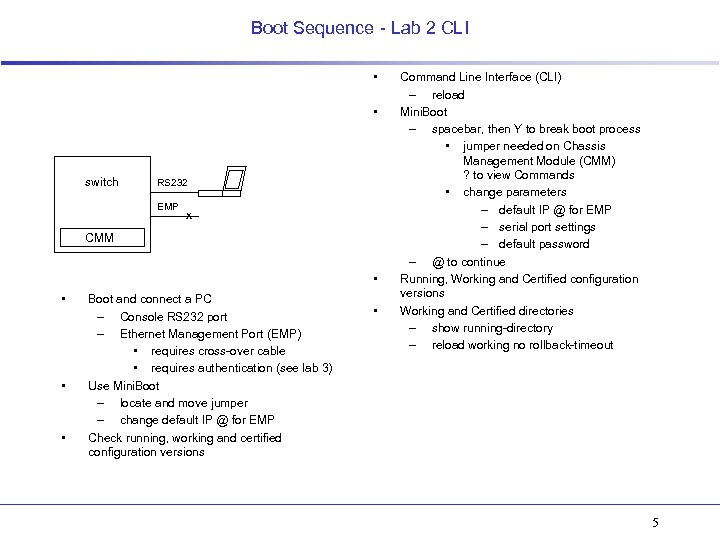
Boot Sequence - Lab 2 CLI • • switch RS 232 EMP x CMM • • Boot and connect a PC – Console RS 232 port – Ethernet Management Port (EMP) • requires cross-over cable • requires authentication (see lab 3) Use Mini. Boot – locate and move jumper – change default IP @ for EMP Check running, working and certified configuration versions • Command Line Interface (CLI) – reload Mini. Boot – spacebar, then Y to break boot process • jumper needed on Chassis Management Module (CMM) ? to view Commands • change parameters – default IP @ for EMP – serial port settings – default password – @ to continue Running, Working and Certified configuration versions Working and Certified directories – show running-directory – reload working no rollback-timeout 5
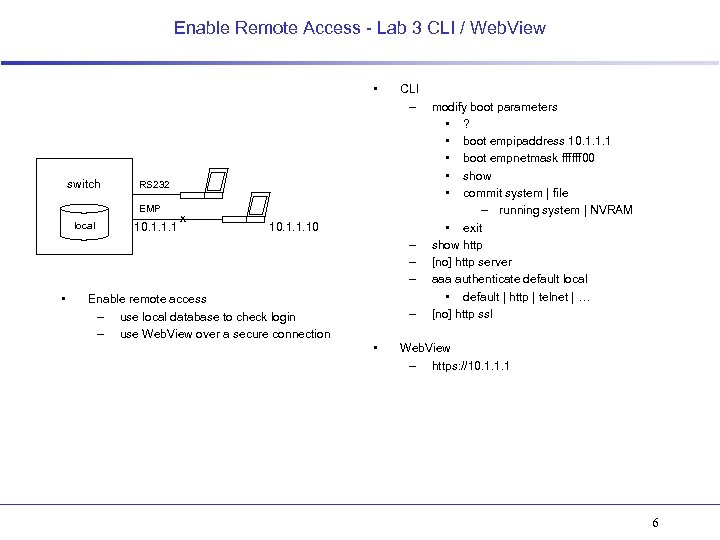
Enable Remote Access - Lab 3 CLI / Web. View • switch RS 232 EMP local CLI – 10. 1. 1. 1 x 10. 1. 1. 10 – – – • Enable remote access – use local database to check login – use Web. View over a secure connection – • modify boot parameters • ? • boot empipaddress 10. 1. 1. 1 • boot empnetmask ffffff 00 • show • commit system | file – running system | NVRAM • exit show http [no] http server aaa authenticate default local • default | http | telnet | … [no] http ssl Web. View – https: //10. 1. 1. 1 6
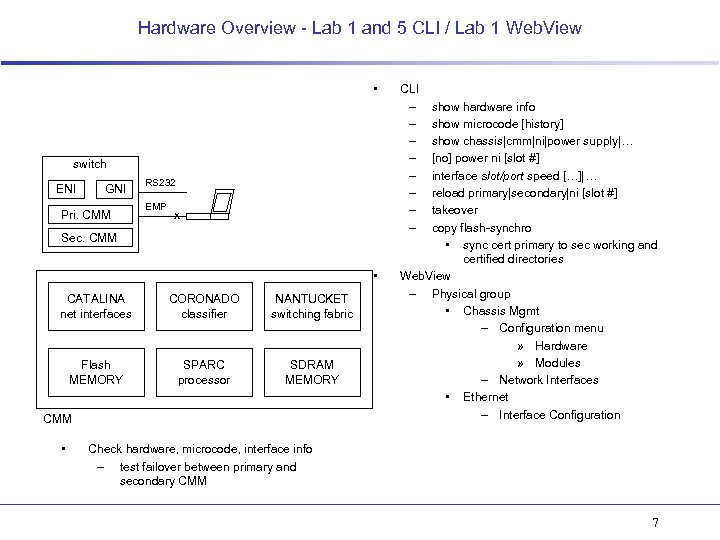
Hardware Overview - Lab 1 and 5 CLI / Lab 1 Web. View • switch ENI GNI Pri. CMM RS 232 EMP x Sec. CMM • CATALINA net interfaces CORONADO classifier NANTUCKET switching fabric Flash MEMORY SPARC processor SDRAM MEMORY CMM • CLI – – – – show hardware info show microcode [history] show chassis|cmm|ni|power supply|… [no] power ni [slot #] interface slot/port speed […]|… reload primary|secondary|ni [slot #] takeover copy flash-synchro • sync cert primary to sec working and certified directories Web. View – Physical group • Chassis Mgmt – Configuration menu » Hardware » Modules – Network Interfaces • Ethernet – Interface Configuration Check hardware, microcode, interface info – test failover between primary and secondary CMM 7
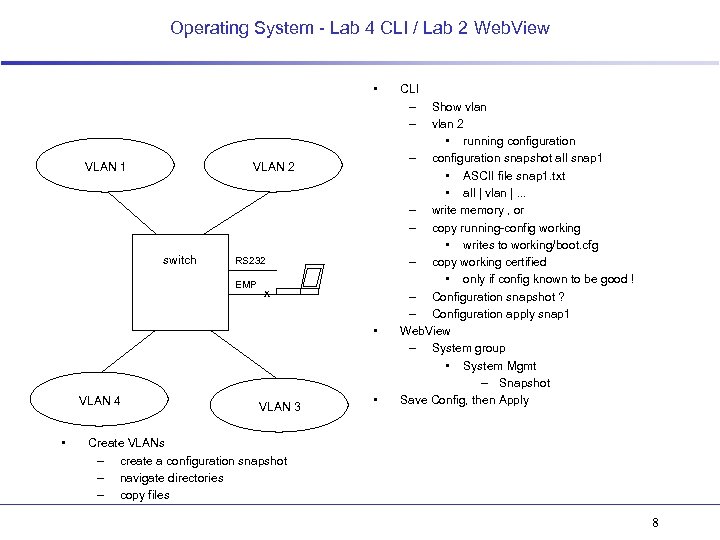
Operating System - Lab 4 CLI / Lab 2 Web. View • VLAN 1 VLAN 2 switch RS 232 EMP x • VLAN 4 • VLAN 3 • CLI – – Show vlan 2 • running configuration – configuration snapshot all snap 1 • ASCII file snap 1. txt • all | vlan |. . . – write memory , or – copy running-config working • writes to working/boot. cfg – copy working certified • only if config known to be good ! – Configuration snapshot ? – Configuration apply snap 1 Web. View – System group • System Mgmt – Snapshot Save Config, then Apply Create VLANs – create a configuration snapshot – navigate directories – copy files 8
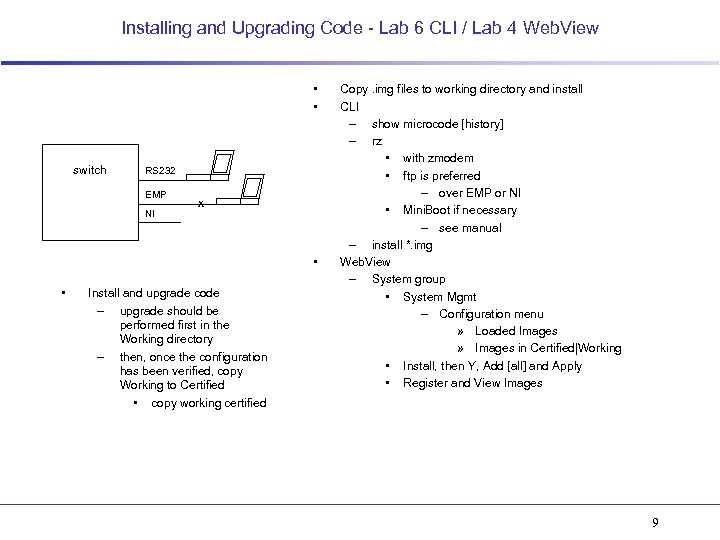
Installing and Upgrading Code - Lab 6 CLI / Lab 4 Web. View • • switch RS 232 EMP NI x • • Install and upgrade code – upgrade should be performed first in the Working directory – then, once the configuration has been verified, copy Working to Certified • copy working certified Copy. img files to working directory and install CLI – show microcode [history] – rz • with zmodem • ftp is preferred – over EMP or NI • Mini. Boot if necessary – see manual – install *. img Web. View – System group • System Mgmt – Configuration menu » Loaded Images » Images in Certified|Working • Install, then Y, Add [all] and Apply • Register and View Images 9
Switch Security - Lab 7 CLI / Lab 4 Web. View • switch RS 232 EMP x • • Test ASA (Authenticated Switch Access) – Users: admin, default, new users – Privileges: read-only, read-write – Partition Management: domains – End User Profiles – Password Expiration – default account cannot be used to login • its privileges are applied to new users CLI – – – – show user 1 password pass 1 user 1 read-only all | domain-layer 2 | … end-user profile 1 read-write all user 1 end-user-profile 1 user 1 expiration 5 [no] aaa authentication telnet Web. View – Security group • ASA – Local User DB » View & Modify Family Privileges 10
VLANs - Lab 8 CLI / Lab 5 Web. View • VLAN 1 192. 168. 10. 0 / 24 192. 168. 101 switch 192. 168. 10. 1 router RS 232 EMP 192. 168. 11. 1 192. 168. 11. 0 / 24 VLAN 2 • • 192. 168. 11. 102 Port type: default (static), mobile Group Mobility Rules CLI – – – show vlan [#] port [slot/port] vlan 1 router ip @ vlan 2 show vlan router ip vlan 2 port default slot/port • static association – vlan port mobile slot/port • needs a traffic matching rule – Show vlan rules – vlan 2 ip 192. 168. 11. 0 255. 0 – show mac-address-table [slot #] • will show the mac @ the switch has learned Web. View – Layer 2 group • VLAN Mgmt – Configuration menu » Vlan Config 11
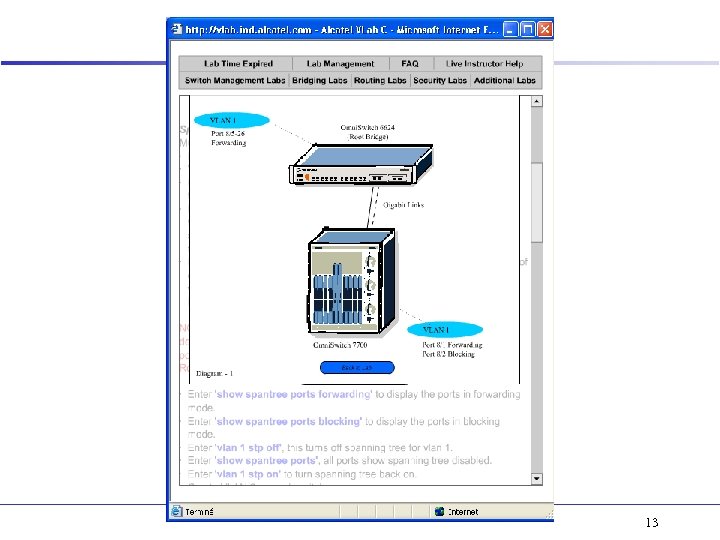
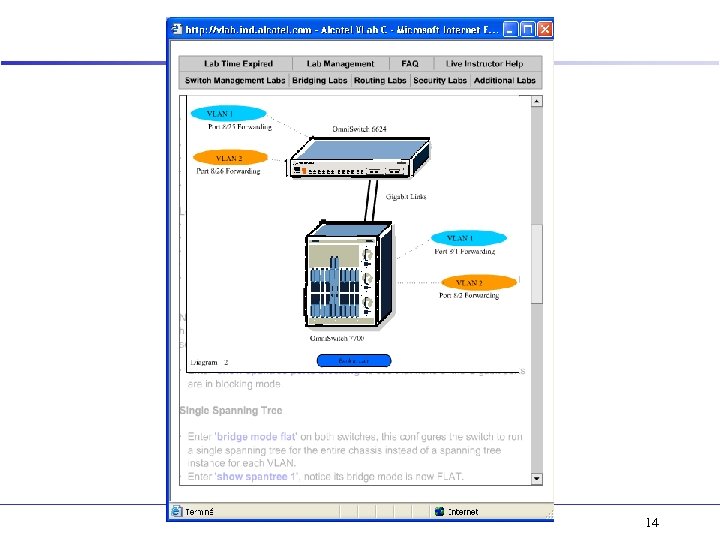
Spanning Tree - Lab 9 CLI / Lab 6 Web. View • VLAN 1 switch EMP VLAN 2 • VID 1 VID 2 RS 232 • VLAN 1 VID 2 switch RS 232 EMP VLAN 2 Spanning Tree Protocol, 802. 1 d – Multiple Spanning Tree, mode 1 X 1 – Single Spanning Tree, mode flat Fast Spanning Tree, 802. 1 w • CLI – – – show spantree 1 show spantree ports [forward|blocking] vlan 1 stp on|off show spantree 2 [ports] bridge mode flat | 1 X 1 • single | multiple spanning tree – bridge 1 protocol 1 w • Next Best Root Cost and Port • Root Port Web. View – Layer 2 group • Spanning Tree – Configuration menu » Bridge Parameters » Statistics » -- Port Statistics 12
13
14
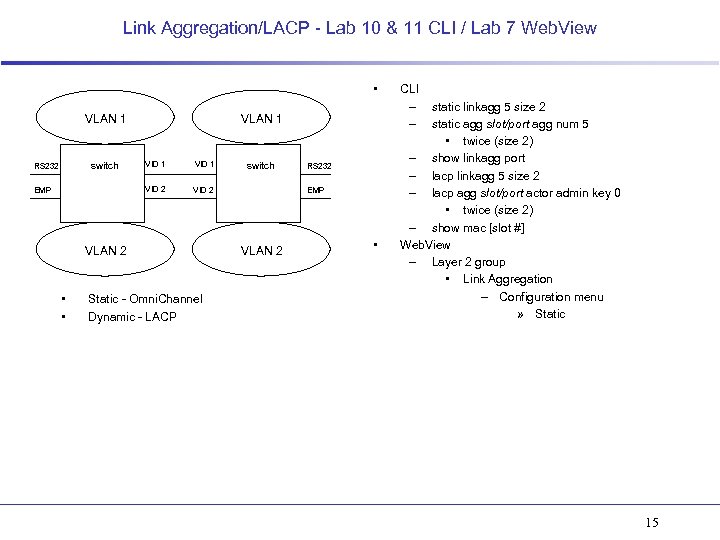
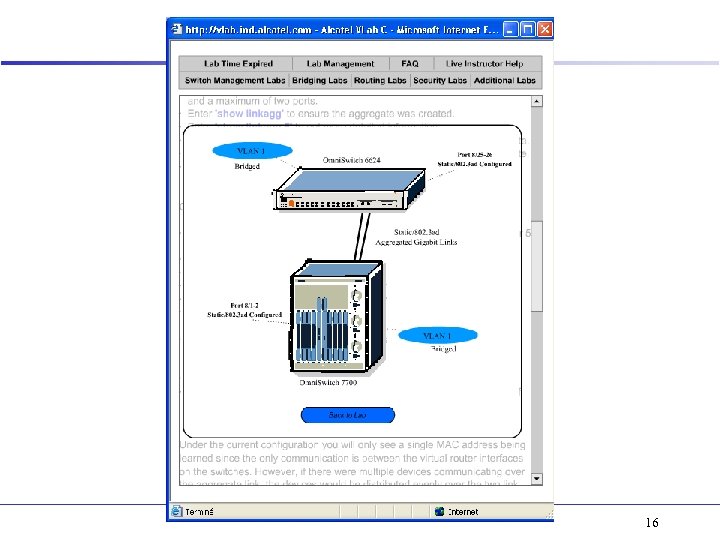
Link Aggregation/LACP - Lab 10 & 11 CLI / Lab 7 Web. View • VLAN 1 EMP VID 1 VID 2 switch RS 232 VID 2 VLAN 2 • • Static - Omni. Channel Dynamic - LACP switch RS 232 EMP VLAN 2 • CLI – – static linkagg 5 size 2 static agg slot/port agg num 5 • twice (size 2) – show linkagg port – lacp linkagg 5 size 2 – lacp agg slot/port actor admin key 0 • twice (size 2) – show mac [slot #] Web. View – Layer 2 group • Link Aggregation – Configuration menu » Static 15
16
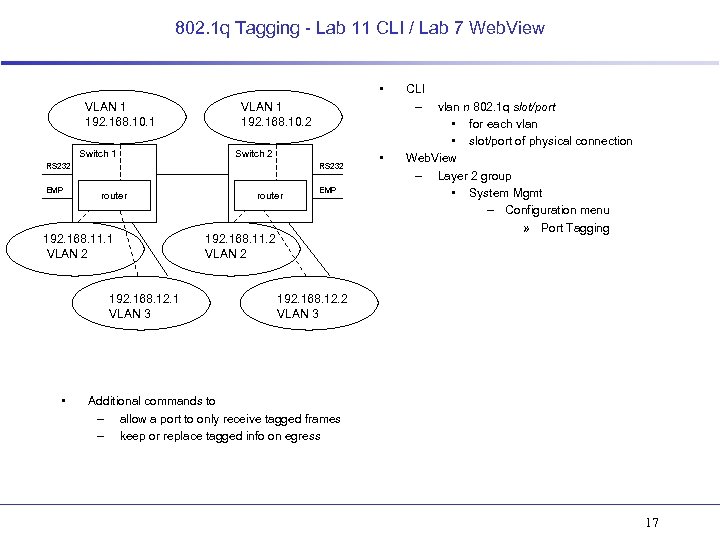
802. 1 q Tagging - Lab 11 CLI / Lab 7 Web. View • VLAN 1 192. 168. 10. 1 Switch 1 VLAN 1 192. 168. 10. 2 Switch 2 RS 232 EMP RS 232 router 192. 168. 11. 1 VLAN 2 192. 168. 12. 1 VLAN 3 • router EMP 192. 168. 11. 2 VLAN 2 • CLI – vlan n 802. 1 q slot/port • for each vlan • slot/port of physical connection Web. View – Layer 2 group • System Mgmt – Configuration menu » Port Tagging 192. 168. 12. 2 VLAN 3 Additional commands to – allow a port to only receive tagged frames – keep or replace tagged info on egress 17
18
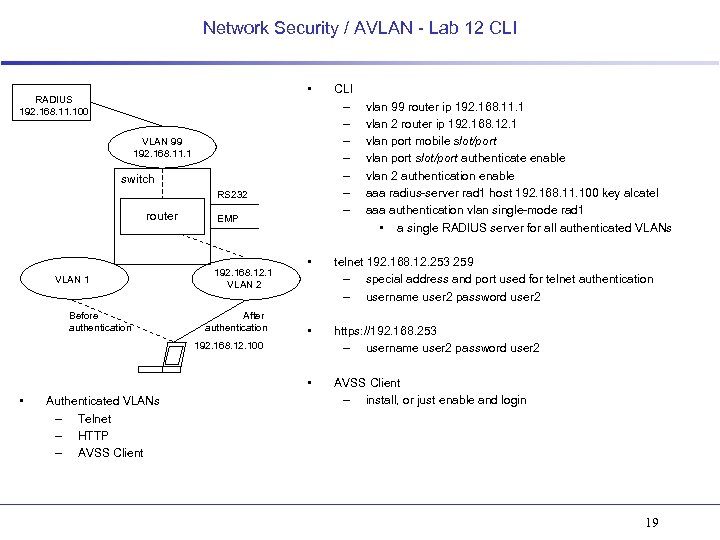
Network Security / AVLAN - Lab 12 CLI • RADIUS 192. 168. 11. 100 VLAN 99 192. 168. 11. 1 switch RS 232 router EMP CLI – – – – vlan 99 router ip 192. 168. 11. 1 vlan 2 router ip 192. 168. 12. 1 vlan port mobile slot/port vlan port slot/port authenticate enable vlan 2 authentication enable aaa radius-server rad 1 host 192. 168. 11. 100 key alcatel aaa authentication vlan single-mode rad 1 • a single RADIUS server for all authenticated VLANs Before authentication After authentication • telnet 192. 168. 12. 253 259 – special address and port used for telnet authentication – username user 2 password user 2 • https: //192. 168. 253 – username user 2 password user 2 • VLAN 1 192. 168. 12. 1 VLAN 2 AVSS Client – install, or just enable and login 192. 168. 12. 100 • Authenticated VLANs – Telnet – HTTP – AVSS Client 19
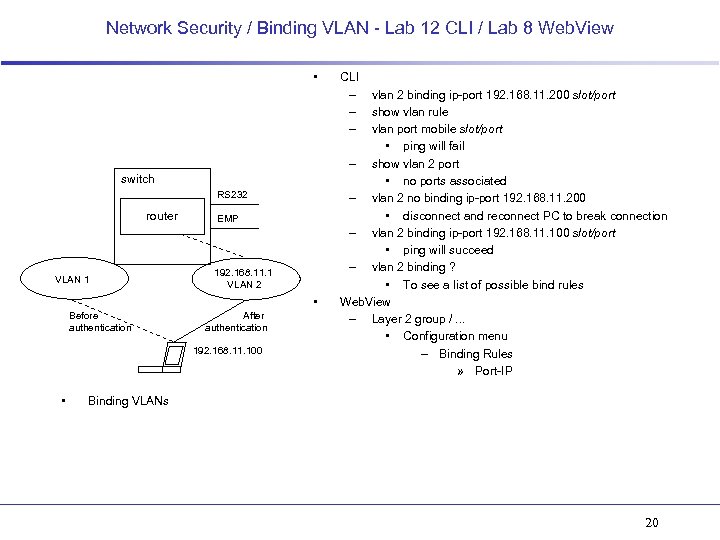
Network Security / Binding VLAN - Lab 12 CLI / Lab 8 Web. View • switch RS 232 router VLAN 1 EMP 192. 168. 11. 1 VLAN 2 • Before authentication After authentication 192. 168. 11. 100 • CLI – – – vlan 2 binding ip-port 192. 168. 11. 200 slot/port show vlan rule vlan port mobile slot/port • ping will fail – show vlan 2 port • no ports associated – vlan 2 no binding ip-port 192. 168. 11. 200 • disconnect and reconnect PC to break connection – vlan 2 binding ip-port 192. 168. 11. 100 slot/port • ping will succeed – vlan 2 binding ? • To see a list of possible bind rules Web. View – Layer 2 group /. . . • Configuration menu – Binding Rules » Port-IP Binding VLANs 20
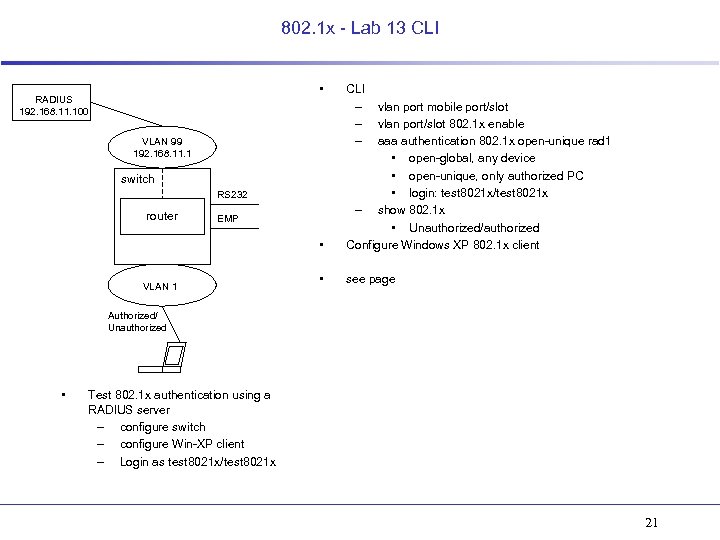
802. 1 x - Lab 13 CLI • RADIUS 192. 168. 11. 100 CLI – – – • vlan port mobile port/slot vlan port/slot 802. 1 x enable aaa authentication 802. 1 x open-unique rad 1 • open-global, any device • open-unique, only authorized PC • login: test 8021 x/test 8021 x – show 802. 1 x • Unauthorized/authorized Configure Windows XP 802. 1 x client • see page VLAN 99 192. 168. 11. 1 switch RS 232 router EMP VLAN 1 Authorized/ Unauthorized • Test 802. 1 x authentication using a RADIUS server – configure switch – configure Win-XP client – Login as test 8021 x/test 8021 x 21
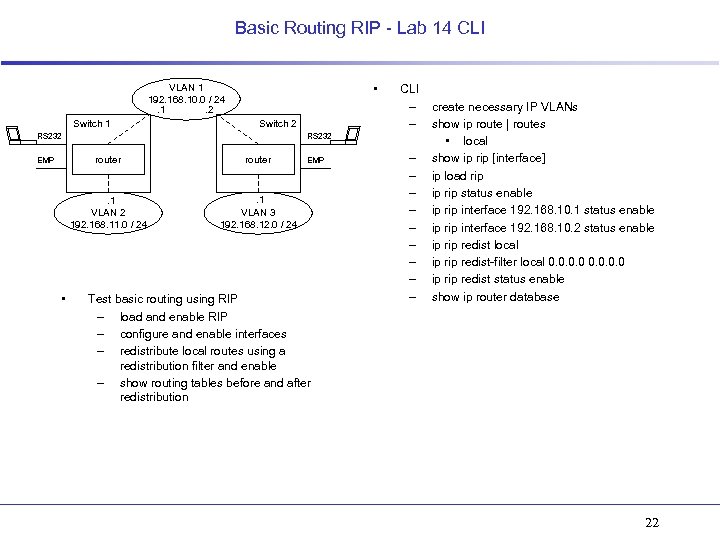
Basic Routing RIP - Lab 14 CLI • VLAN 1 192. 168. 10. 0 / 24. 1. 2 Switch 1 Switch 2 RS 232 router • router . 1 VLAN 2 192. 168. 11. 0 / 24 EMP CLI – – . 1 VLAN 3 192. 168. 12. 0 / 24 EMP Test basic routing using RIP – load and enable RIP – configure and enable interfaces – redistribute local routes using a redistribution filter and enable – show routing tables before and after redistribution – – – – – create necessary IP VLANs show ip route | routes • local show ip rip [interface] ip load rip ip rip status enable ip rip interface 192. 168. 10. 1 status enable ip rip interface 192. 168. 10. 2 status enable ip redist local ip redist-filter local 0. 0 ip redist status enable show ip router database 22
23
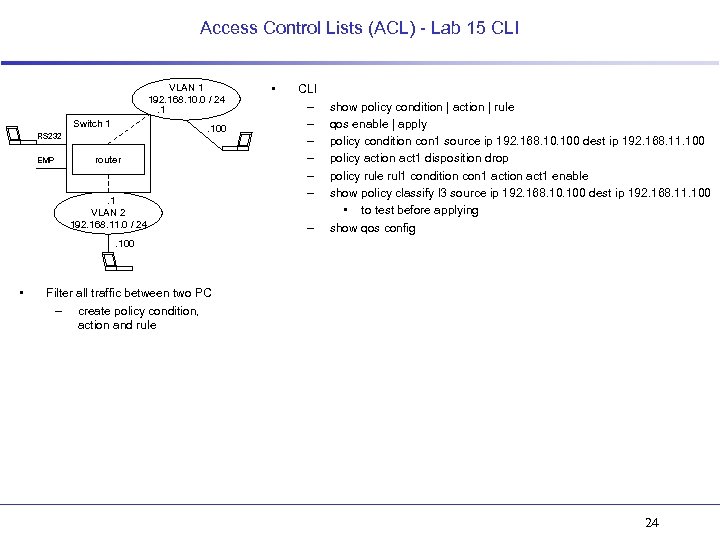
Access Control Lists (ACL) - Lab 15 CLI VLAN 1 192. 168. 10. 0 / 24. 1 Switch 1 . 100 RS 232 EMP router . 1 VLAN 2 192. 168. 11. 0 / 24 • CLI – – – – show policy condition | action | rule qos enable | apply policy condition con 1 source ip 192. 168. 100 dest ip 192. 168. 11. 100 policy action act 1 disposition drop policy rule rul 1 condition con 1 action act 1 enable show policy classify l 3 source ip 192. 168. 100 dest ip 192. 168. 11. 100 • to test before applying show qos config . 100 • Filter all traffic between two PC – create policy condition, action and rule 24
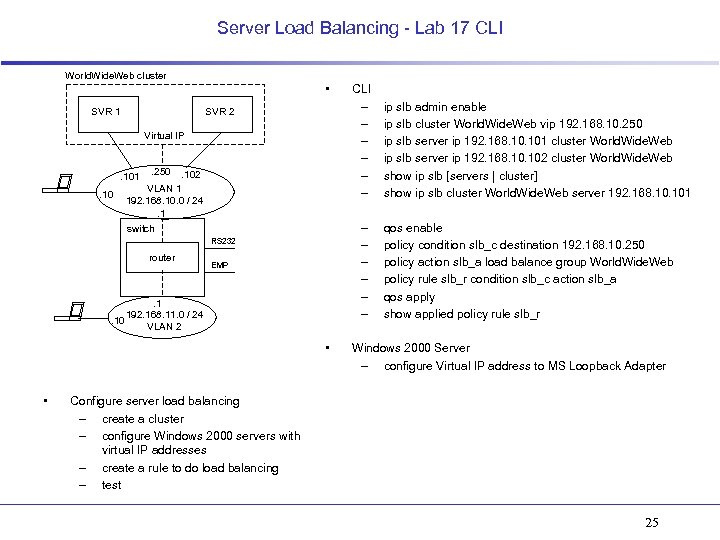
Server Load Balancing - Lab 17 CLI World. Wide. Web cluster • SVR 1 SVR 2 Virtual IP . 10 . 250 . 102 VLAN 1 192. 168. 10. 0 / 24. 1 switch . 101 – – – RS 232 router EMP . 1 192. 168. 11. 0 / 24. 10 VLAN 2 • • CLI – – – ip slb admin enable ip slb cluster World. Wide. Web vip 192. 168. 10. 250 ip slb server ip 192. 168. 101 cluster World. Wide. Web ip slb server ip 192. 168. 102 cluster World. Wide. Web show ip slb [servers | cluster] show ip slb cluster World. Wide. Web server 192. 168. 101 qos enable policy condition slb_c destination 192. 168. 10. 250 policy action slb_a load balance group World. Wide. Web policy rule slb_r condition slb_c action slb_a qos apply show applied policy rule slb_r Windows 2000 Server – configure Virtual IP address to MS Loopback Adapter Configure server load balancing – create a cluster – configure Windows 2000 servers with virtual IP addresses – create a rule to do load balancing – test 25
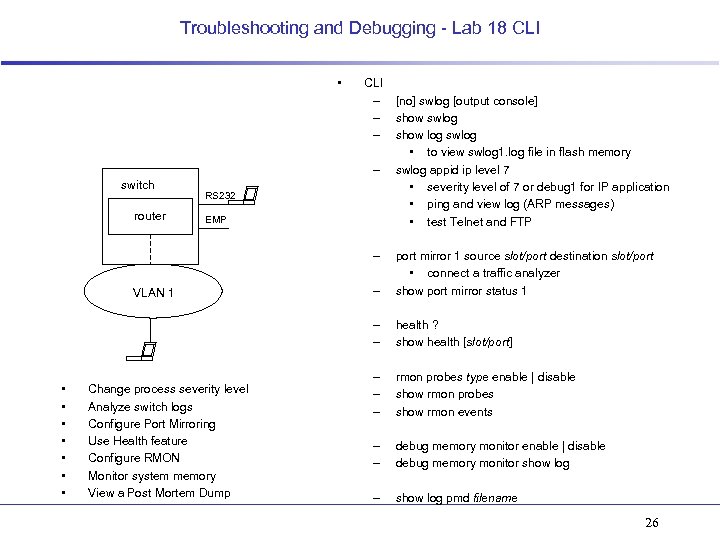
Troubleshooting and Debugging - Lab 18 CLI • CLI – – switch router RS 232 EMP – [no] swlog [output console] show swlog show log swlog • to view swlog 1. log file in flash memory swlog appid ip level 7 • severity level of 7 or debug 1 for IP application • ping and view log (ARP messages) • test Telnet and FTP • • Change process severity level Analyze switch logs Configure Port Mirroring Use Health feature Configure RMON Monitor system memory View a Post Mortem Dump – – – VLAN 1 port mirror 1 source slot/port destination slot/port • connect a traffic analyzer show port mirror status 1 health ? show health [slot/port] – – – rmon probes type enable | disable show rmon probes show rmon events – – debug memory monitor enable | disable debug memory monitor show log – show log pmd filename 26
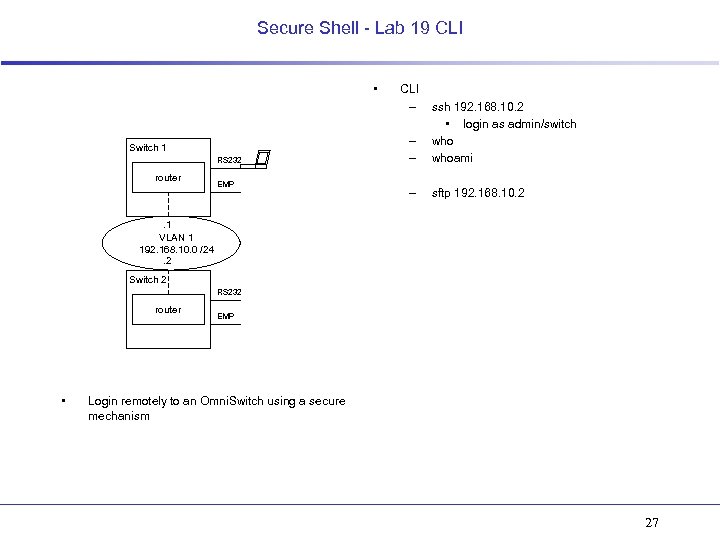
Secure Shell - Lab 19 CLI • Switch 1 RS 232 router EMP CLI – – – ssh 192. 168. 10. 2 • login as admin/switch whoami – sftp 192. 168. 10. 2 . 1 VLAN 1 192. 168. 10. 0 /24. 2 Switch 2 RS 232 router • EMP Login remotely to an Omni. Switch using a secure mechanism 27
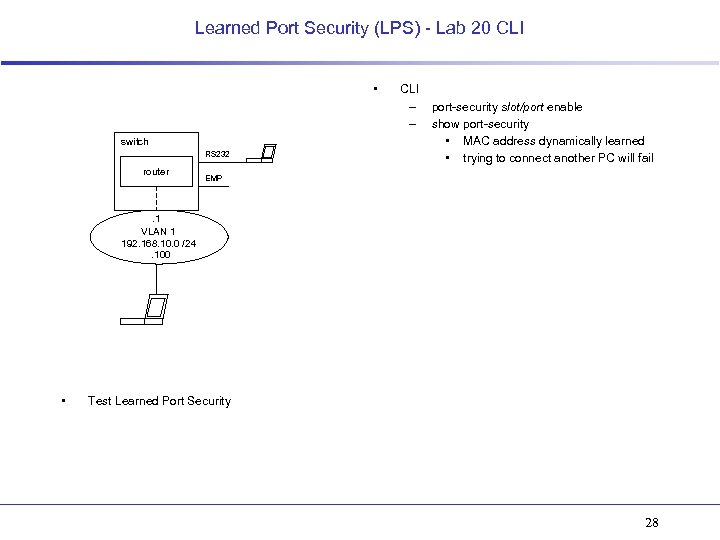
Learned Port Security (LPS) - Lab 20 CLI • switch RS 232 router CLI – – port-security slot/port enable show port-security • MAC address dynamically learned • trying to connect another PC will fail EMP . 1 VLAN 1 192. 168. 10. 0 /24. 100 • Test Learned Port Security 28
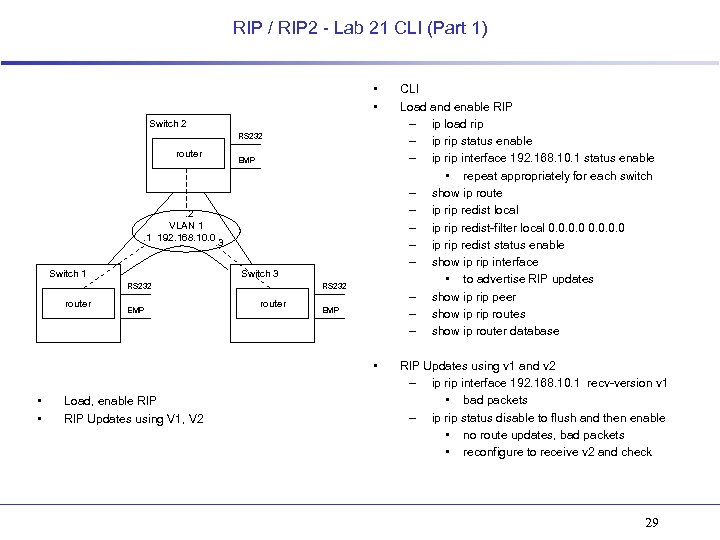
RIP / RIP 2 - Lab 21 CLI (Part 1) • • CLI Load and enable RIP – ip load rip – ip rip status enable – ip rip interface 192. 168. 10. 1 status enable • repeat appropriately for each switch – show ip route – ip redist local – ip redist-filter local 0. 0 – ip redist status enable – show ip rip interface • to advertise RIP updates – show ip rip peer – show ip routes – show ip router database • RIP Updates using v 1 and v 2 – ip rip interface 192. 168. 10. 1 recv-version v 1 • bad packets – ip rip status disable to flush and then enable • no route updates, bad packets • reconfigure to receive v 2 and check Switch 2 RS 232 router EMP . 2 VLAN 1. 1 192. 168. 10. 0. 3 Switch 1 Switch 3 RS 232 router • • EMP Load, enable RIP Updates using V 1, V 2 RS 232 router EMP 29
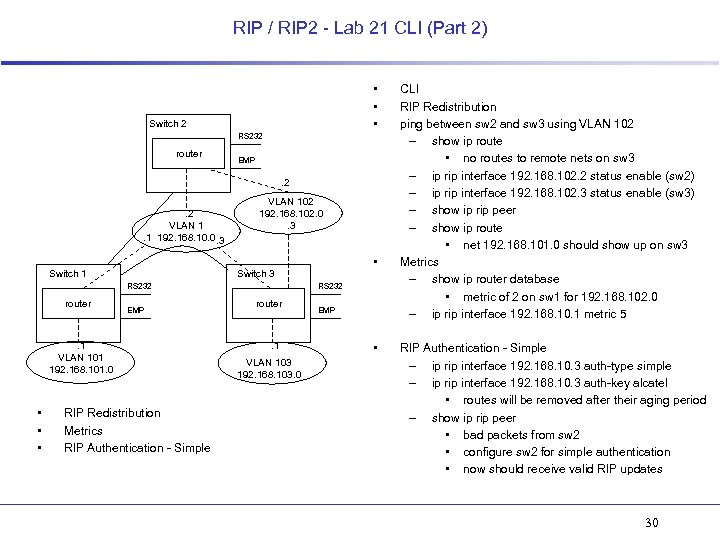
RIP / RIP 2 - Lab 21 CLI (Part 2) • • • Switch 2 RS 232 router EMP . 2. 2 VLAN 1. 1 192. 168. 10. 0. 3 Switch 1 VLAN 102 192. 168. 102. 0. 3 RS 232 router EMP . 1 VLAN 101 192. 168. 101. 0 • • Switch 3 RIP Redistribution Metrics RIP Authentication - Simple RS 232 router . 1 VLAN 103 192. 168. 103. 0 EMP • CLI RIP Redistribution ping between sw 2 and sw 3 using VLAN 102 – show ip route • no routes to remote nets on sw 3 – ip rip interface 192. 168. 102. 2 status enable (sw 2) – ip rip interface 192. 168. 102. 3 status enable (sw 3) – show ip rip peer – show ip route • net 192. 168. 101. 0 should show up on sw 3 Metrics – show ip router database • metric of 2 on sw 1 for 192. 168. 102. 0 – ip rip interface 192. 168. 10. 1 metric 5 RIP Authentication - Simple – ip rip interface 192. 168. 10. 3 auth-type simple – ip rip interface 192. 168. 10. 3 auth-key alcatel • routes will be removed after their aging period – show ip rip peer • bad packets from sw 2 • configure sw 2 for simple authentication • now should receive valid RIP updates 30
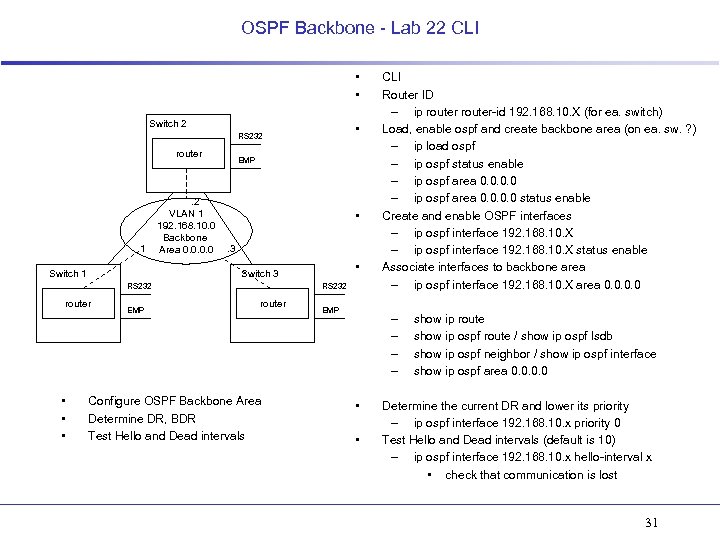
OSPF Backbone - Lab 22 CLI • • Switch 2 • RS 232 router . 1 Switch 1 . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 EMP • . 3 RS 232 router • • Switch 3 EMP RS 232 router Configure OSPF Backbone Area Determine DR, BDR Test Hello and Dead intervals EMP CLI Router ID – ip router-id 192. 168. 10. X (for ea. switch) Load, enable ospf and create backbone area (on ea. sw. ? ) – ip load ospf – ip ospf status enable – ip ospf area 0. 0 status enable Create and enable OSPF interfaces – ip ospf interface 192. 168. 10. X status enable Associate interfaces to backbone area – ip ospf interface 192. 168. 10. X area 0. 0 – – • • show ip route show ip ospf route / show ip ospf lsdb show ip ospf neighbor / show ip ospf interface show ip ospf area 0. 0 Determine the current DR and lower its priority – ip ospf interface 192. 168. 10. x priority 0 Test Hello and Dead intervals (default is 10) – ip ospf interface 192. 168. 10. x hello-interval x • check that communication is lost 31
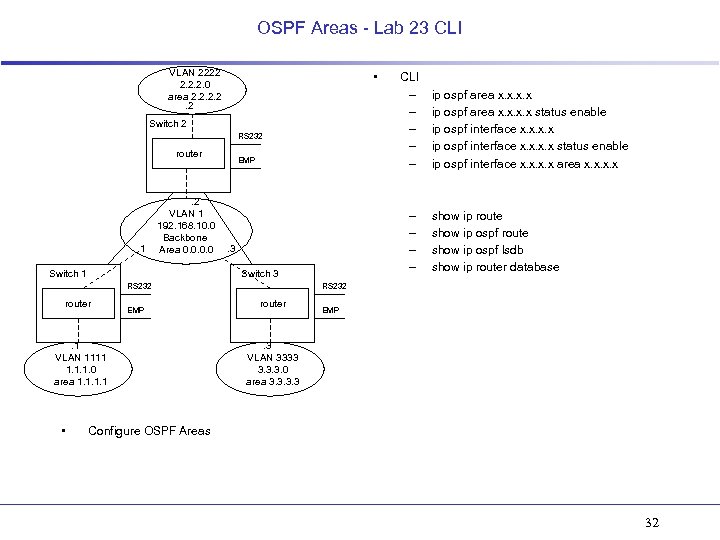
OSPF Areas - Lab 23 CLI VLAN 2222 2. 2. 2. 0 area 2. 2. 2 • Switch 2 RS 232 router . 1 . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 Switch 1 EMP Switch 3 router EMP . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • – – . 3 RS 232 CLI – – – ip ospf area x. x status enable ip ospf interface x. x area x. x show ip route show ip ospf lsdb show ip router database RS 232 router EMP . 3 VLAN 3333 3. 3. 3. 0 area 3. 3 Configure OSPF Areas 32
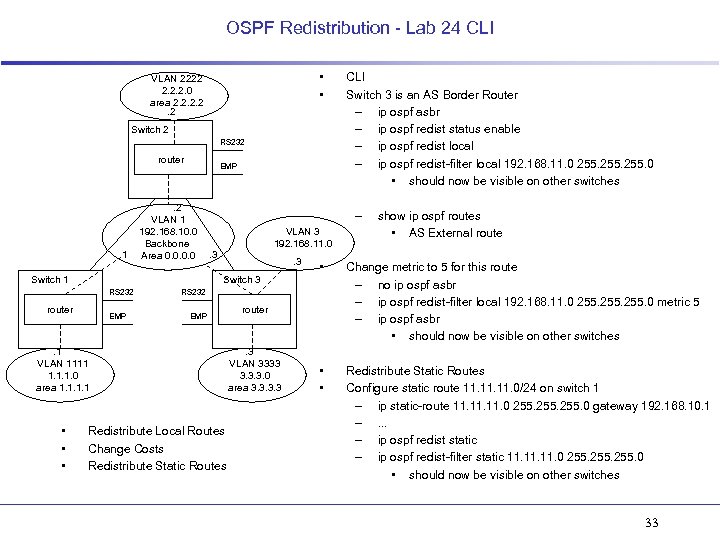
OSPF Redistribution - Lab 24 CLI • • VLAN 2222 2. 2. 2. 0 area 2. 2. 2 Switch 2 RS 232 router . 1 EMP . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 Switch 1 – VLAN 3 192. 168. 11. 0 . 3 router EMP . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • • • Change metric to 5 for this route – no ip ospf asbr – ip ospf redist-filter local 192. 168. 11. 0 255. 0 metric 5 – ip ospf asbr • should now be visible on other switches • • Redistribute Static Routes Configure static route 11. 11. 0/24 on switch 1 – ip static-route 11. 11. 0 255. 0 gateway 192. 168. 10. 1 –. . . – ip ospf redist static – ip ospf redist-filter static 11. 11. 0 255. 0 • should now be visible on other switches RS 232 EMP Redistribute Local Routes Change Costs Redistribute Static Routes router . 3 VLAN 3333 3. 3. 3. 0 area 3. 3 show ip ospf routes • AS External route • Switch 3 RS 232 CLI Switch 3 is an AS Border Router – ip ospf asbr – ip ospf redist status enable – ip ospf redist local – ip ospf redist-filter local 192. 168. 11. 0 255. 0 • should now be visible on other switches 33
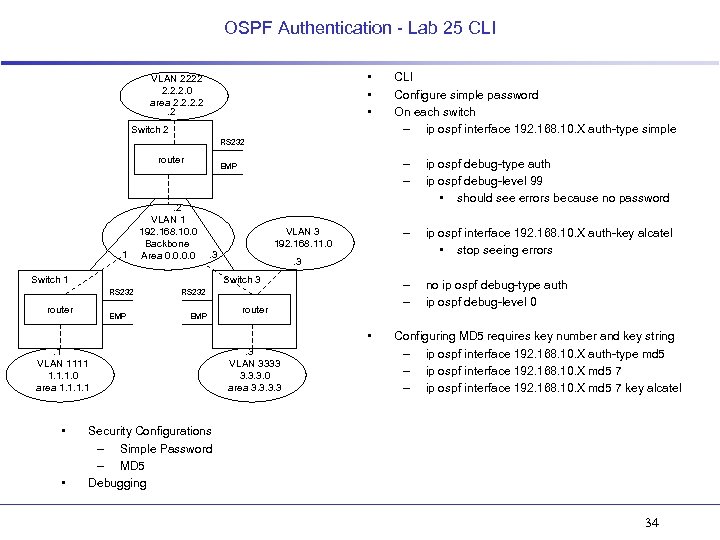
OSPF Authentication - Lab 25 CLI • • • VLAN 2222 2. 2. 2. 0 area 2. 2. 2 Switch 2 CLI Configure simple password On each switch – ip ospf interface 192. 168. 10. X auth-type simple RS 232 router . 1 – – . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 . 3 Switch 1 router EMP RS 232 EMP router • . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • • no ip ospf debug-type auth ip ospf debug-level 0 . 3 Switch 3 RS 232 ip ospf interface 192. 168. 10. X auth-key alcatel • stop seeing errors – – VLAN 3 192. 168. 11. 0 ip ospf debug-type auth ip ospf debug-level 99 • should see errors because no password – EMP . 3 VLAN 3333 3. 3. 3. 0 area 3. 3 Configuring MD 5 requires key number and key string – ip ospf interface 192. 168. 10. X auth-type md 5 – ip ospf interface 192. 168. 10. X md 5 7 key alcatel Security Configurations – Simple Password – MD 5 Debugging 34
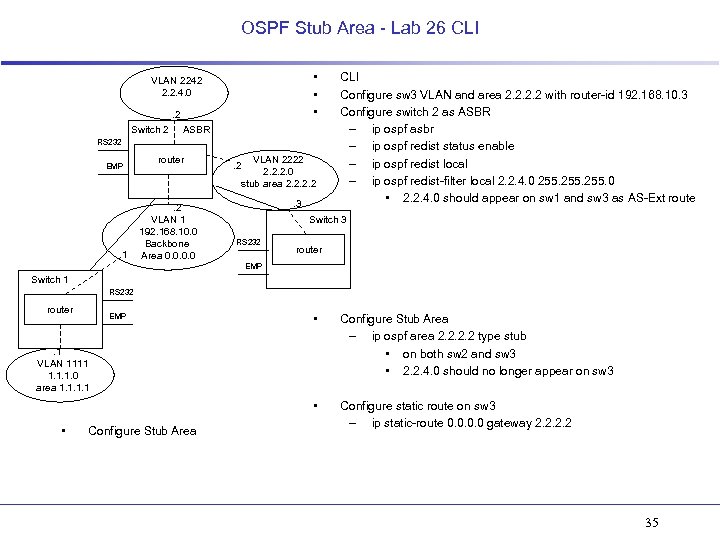
OSPF Stub Area - Lab 26 CLI • • • VLAN 2242 2. 2. 4. 0. 2 Switch 2 ASBR RS 232 EMP . 1 router . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 VLAN 2222 2. 2. 2. 0 stub area 2. 2 . 3 CLI Configure sw 3 VLAN and area 2. 2 with router-id 192. 168. 10. 3 Configure switch 2 as ASBR – ip ospf asbr – ip ospf redist status enable – ip ospf redist local – ip ospf redist-filter local 2. 2. 4. 0 255. 0 • 2. 2. 4. 0 should appear on sw 1 and sw 3 as AS-Ext route Switch 3 RS 232 router EMP Switch 1 RS 232 router • Configure Stub Area – ip ospf area 2. 2 type stub • on both sw 2 and sw 3 • 2. 2. 4. 0 should no longer appear on sw 3 • EMP Configure static route on sw 3 – ip static-route 0. 0 gateway 2. 2 . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • Configure Stub Area 35
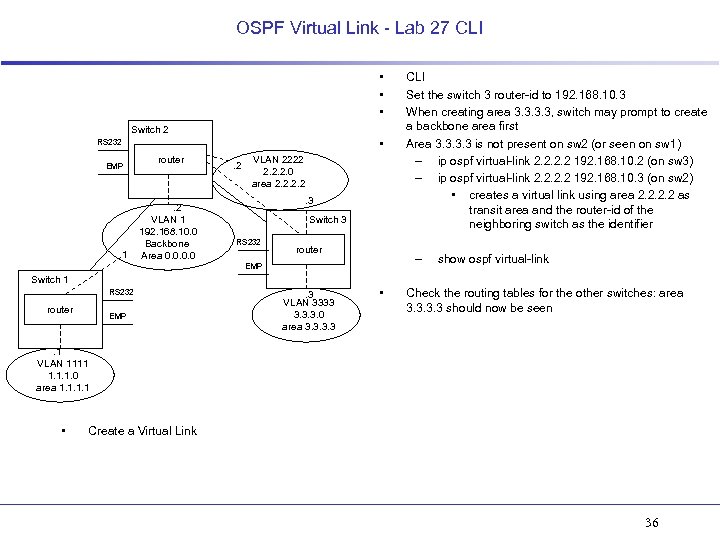
OSPF Virtual Link - Lab 27 CLI • • • Switch 2 • RS 232 EMP . 1 router . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 . 2 VLAN 2222 2. 2. 2. 0 area 2. 2. 3 Switch 3 RS 232 router CLI Set the switch 3 router-id to 192. 168. 10. 3 When creating area 3. 3, switch may prompt to create a backbone area first Area 3. 3 is not present on sw 2 (or seen on sw 1) – ip ospf virtual-link 2. 2 192. 168. 10. 2 (on sw 3) – ip ospf virtual-link 2. 2 192. 168. 10. 3 (on sw 2) • creates a virtual link using area 2. 2 as transit area and the router-id of the neighboring switch as the identifier – EMP show ospf virtual-link Switch 1 RS 232 router EMP . 3 VLAN 3333 3. 3. 3. 0 area 3. 3 • Check the routing tables for the other switches: area 3. 3 should now be seen . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • Create a Virtual Link 36
37
local switch RS 232 EMP router switch VLAN N EMP router switch RS 232 WLAN switch EMP router AP VLAN N x x 38

Wireless LANs 39
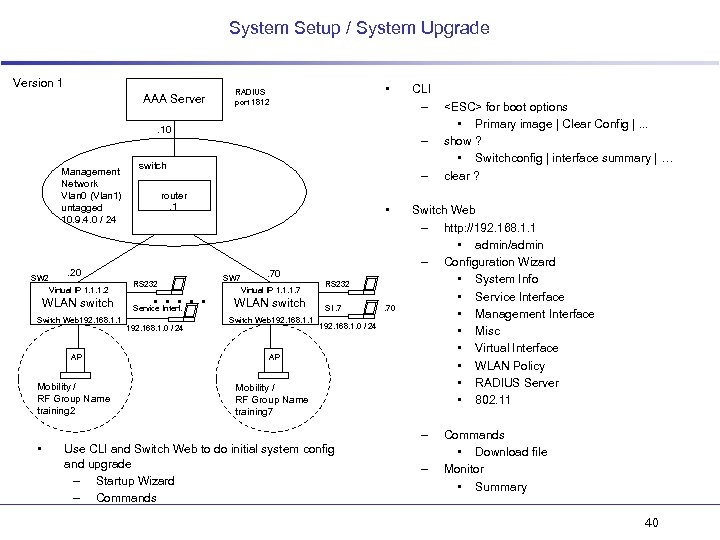
System Setup / System Upgrade Version 1 AAA Server • RADIUS port 1812 . 10 Management Network Vlan 0 (Vlan 1) untagged 10. 9. 4. 0 / 24 SW 2 Virtual IP 1. 1. 1. 2 WLAN switch Switch Web 192. 168. 1. 1 AP Mobility / RF Group Name training 2 – switch – router. 1 . 20 RS 232 . . . Service Interf. 192. 168. 1. 0 / 24 CLI – • SW 7 . 70 Virtual IP 1. 1. 1. 7 WLAN switch Switch Web 192. 168. 1. 1 RS 232 SI. 7 192. 168. 1. 0 / 24 AP Mobility / RF Group Name training 7 . 70 Switch Web – http: //192. 168. 1. 1 • admin/admin – Configuration Wizard • System Info • Service Interface • Management Interface • Misc • Virtual Interface • WLAN Policy • RADIUS Server • 802. 11 – • Use CLI and Switch Web to do initial system config and upgrade – Startup Wizard – Commands <ESC> for boot options • Primary image | Clear Config |. . . show ? • Switchconfig | interface summary | … clear ? – Commands • Download file Monitor • Summary 40
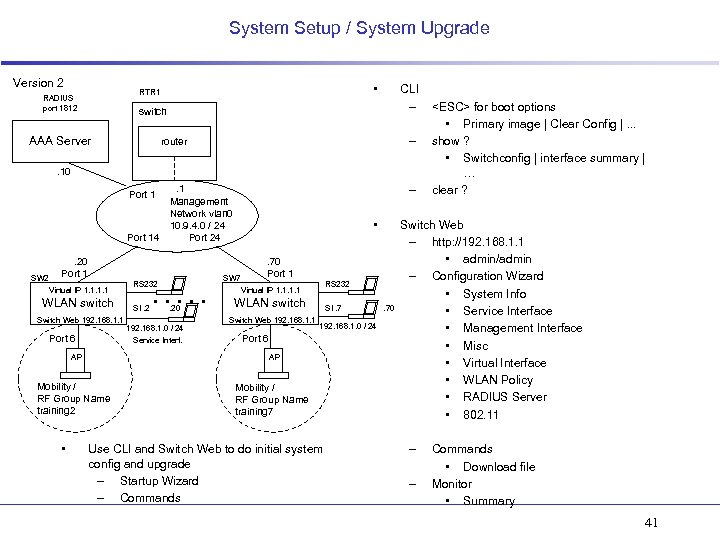
System Setup / System Upgrade Version 2 • RTR 1 RADIUS port 1812 CLI – switch AAA Server – router . 10 Port 14 SW 2 . 20 Port 1 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 Port 6 AP . . . 20 192. 168. 1. 0 / 24 Service Interf. • SW 7 . 70 Port 1 RS 232 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 SI. 7 192. 168. 1. 0 / 24 Port 6 AP Mobility / RF Group Name training 2 • RS 232 SI. 2 – . 1 Management Network vlan 0 10. 9. 4. 0 / 24 Port 24 Mobility / RF Group Name training 7 Use CLI and Switch Web to do initial system config and upgrade – Startup Wizard – Commands . 70 <ESC> for boot options • Primary image | Clear Config |. . . show ? • Switchconfig | interface summary | … clear ? Switch Web – http: //192. 168. 1. 1 • admin/admin – Configuration Wizard • System Info • Service Interface • Management Interface • Misc • Virtual Interface • WLAN Policy • RADIUS Server • 802. 11 – – Commands • Download file Monitor • Summary 41
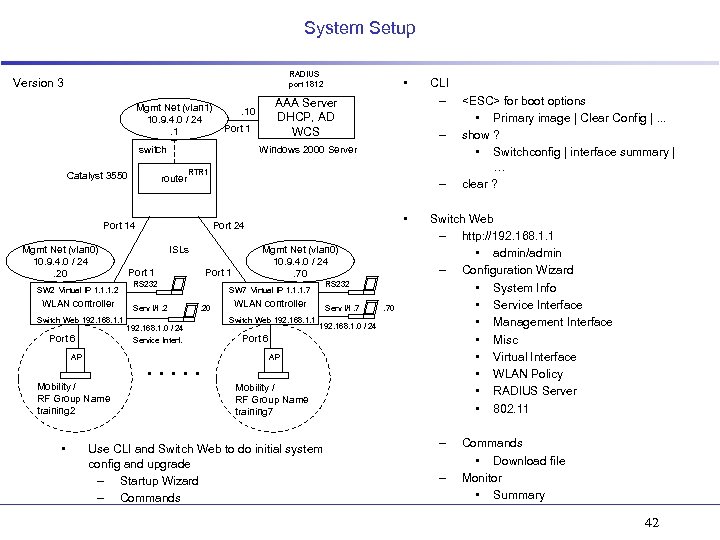
System Setup RADIUS port 1812 Version 3 Mgmt Net (vlan 1) 10. 9. 4. 0 / 24. 1 Catalyst 3550 Port 1 SW 2 Virtual IP 1. 1. 1. 2 WLAN controller Switch Web 192. 168. 1. 1 Port 6 AP router • – RTR 1 – • Port 24 ISLs Port 1 RS 232 Serv I/f. 2 Mgmt Net (vlan 0) 10. 9. 4. 0 / 24. 70 RS 232 SW 7 Virtual IP 1. 1. 1. 7. 20 192. 168. 1. 0 / 24 Service Interf. . . Mobility / RF Group Name training 2 CLI – Windows 2000 Server Port 14 Mgmt Net (vlan 0) 10. 9. 4. 0 / 24. 20 AAA Server DHCP, AD WCS . 10 switch • WLAN controller Switch Web 192. 168. 1. 1 Serv I/f. 7 192. 168. 1. 0 / 24 Port 6 AP Mobility / RF Group Name training 7 Use CLI and Switch Web to do initial system config and upgrade – Startup Wizard – Commands . 70 <ESC> for boot options • Primary image | Clear Config |. . . show ? • Switchconfig | interface summary | … clear ? Switch Web – http: //192. 168. 1. 1 • admin/admin – Configuration Wizard • System Info • Service Interface • Management Interface • Misc • Virtual Interface • WLAN Policy • RADIUS Server • 802. 11 – – Commands • Download file Monitor • Summary 42
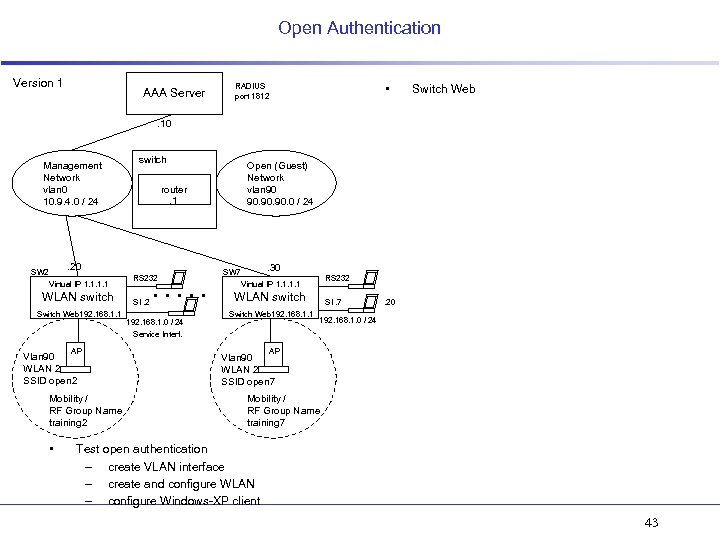
Open Authentication Version 1 AAA Server • RADIUS port 1812 Switch Web . 10 Management Network vlan 0 10. 9. 4. 0 / 24 switch router. 1 . 20 SW 2 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 AP Vlan 90 WLAN 2 SSID open 2 Mobility / RF Group Name training 2 • Open (Guest) Network vlan 90 90. 90. 0 / 24 RS 232 SI. 2 . . . 192. 168. 1. 0 / 24 Service Interf. . 30 SW 7 RS 232 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 SI. 7 . 20 192. 168. 1. 0 / 24 AP Vlan 90 WLAN 2 SSID open 7 Mobility / RF Group Name training 7 Test open authentication – create VLAN interface – create and configure WLAN – configure Windows-XP client 43
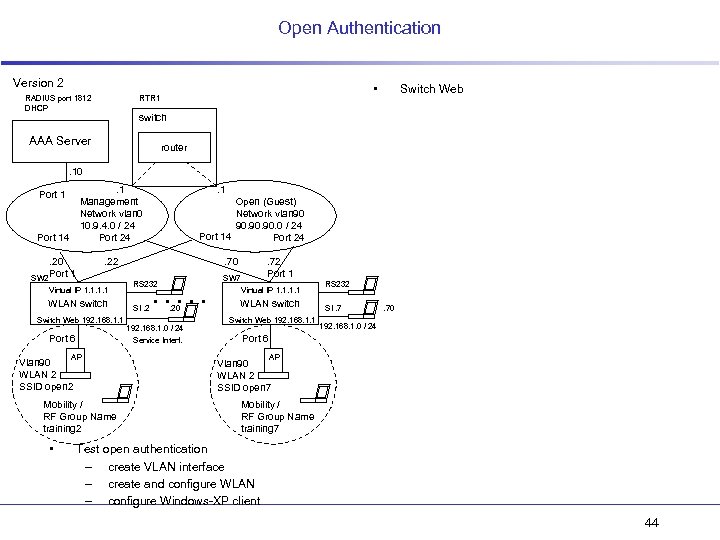
Open Authentication Version 2 RADIUS port 1812 DHCP • RTR 1 Switch Web switch AAA Server router . 10. 1 Management Network vlan 0 10. 9. 4. 0 / 24 Port 14. 20 Port 1 SW 2 Open (Guest) Network vlan 90 90. 90. 0 / 24 Port 14 Port 24 . 22 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 Port 6 AP Vlan 90 WLAN 2 SSID open 2 Mobility / RF Group Name training 2 • . 1 . 70 RS 232 SI. 2 . . . 20 192. 168. 1. 0 / 24 Service Interf. . 72 Port 1 SW 7 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 RS 232 SI. 7 . 70 192. 168. 1. 0 / 24 Port 6 AP Vlan 90 WLAN 2 SSID open 7 Mobility / RF Group Name training 7 Test open authentication – create VLAN interface – create and configure WLAN – configure Windows-XP client 44
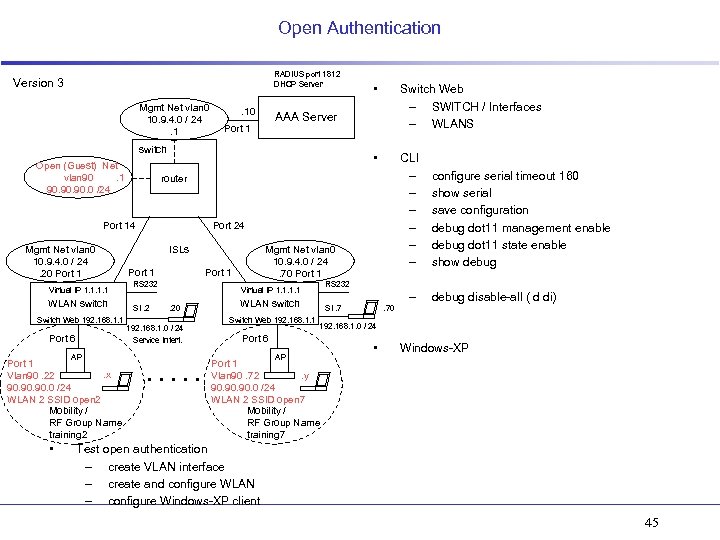
Open Authentication RADIUS port 1812 DHCP Server Version 3. 10 router Port 14 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 20 Port 1 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 Port 6 AP Port 1. x Vlan 90. 22 90. 90. 0 /24 WLAN 2 SSID open 2 Mobility / RF Group Name training 2 • CLI – – – AAA Server Port 1 switch Open (Guest) Net vlan 90. 1 90. 90. 0 /24 Switch Web – SWITCH / Interfaces – WLANS • Mgmt Net vlan 0 10. 9. 4. 0 / 24. 1 • Port 24 ISLs Port 1 RS 232 SI. 2 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 70 Port 1 RS 232 Virtual IP 1. 1. 20 192. 168. 1. 0 / 24 Service Interf. . . – WLAN switch Switch Web 192. 168. 1. 1 SI. 7 debug disable-all ( d di) . 70 192. 168. 1. 0 / 24 Port 6 AP configure serial timeout 160 show serial save configuration debug dot 11 management enable debug dot 11 state enable show debug • Windows-XP Port 1 Vlan 90. 72. y 90. 90. 0 /24 WLAN 2 SSID open 7 Mobility / RF Group Name training 7 Test open authentication – create VLAN interface – create and configure WLAN – configure Windows-XP client 45
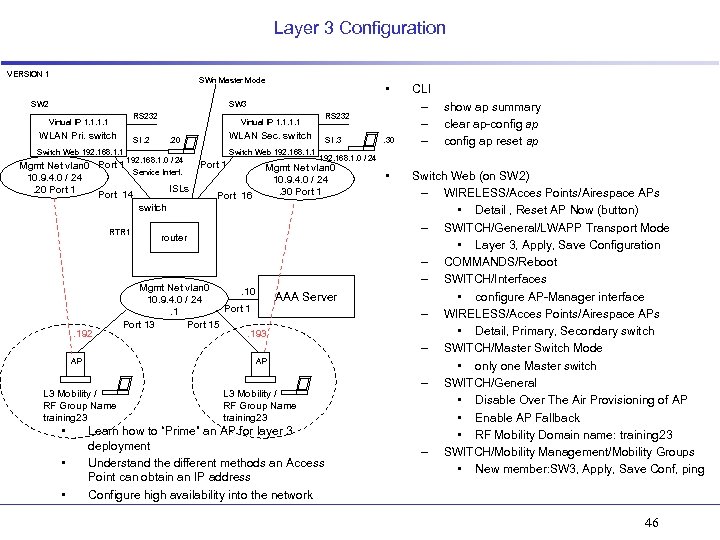
Layer 3 Configuration VERSION 1 SWn Master Mode SW 2 • SW 3 RS 232 Virtual IP 1. 1 WLAN Pri. switch SI. 2 Switch Web 192. 168. 1. 1 Virtual IP 1. 1 . 192 AP 192. 168. 1. 0 / 24 • • Switch Web 192. 168. 1. 1 Port 16 SI. 3 router Mgmt Net vlan 0. 10 10. 9. 4. 0 / 24 Port 1. 1 Port 13 Port 15. 193 . 30 show ap summary clear ap-config ap reset ap 192. 168. 1. 0 / 24 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 30 Port 1 AAA Server AP L 3 Mobility / RF Group Name training 23 • WLAN Sec. switch . 20 Mgmt Net vlan 0 Port 1 Service Interf. 10. 9. 4. 0 / 24 ISLs. 20 Port 14 switch RTR 1 RS 232 CLI – – – L 3 Mobility / RF Group Name training 23 Learn how to “Prime” an AP for layer 3 deployment Understand the different methods an Access Point can obtain an IP address Configure high availability into the network • Switch Web (on SW 2) – WIRELESS/Acces Points/Airespace APs • Detail , Reset AP Now (button) – SWITCH/General/LWAPP Transport Mode • Layer 3, Apply, Save Configuration – COMMANDS/Reboot – SWITCH/Interfaces • configure AP-Manager interface – WIRELESS/Acces Points/Airespace APs • Detail, Primary, Secondary switch – SWITCH/Master Switch Mode • only one Master switch – SWITCH/General • Disable Over The Air Provisioning of AP • Enable AP Fallback • RF Mobility Domain name: training 23 – SWITCH/Mobility Management/Mobility Groups • New member: SW 3, Apply, Save Conf, ping 46
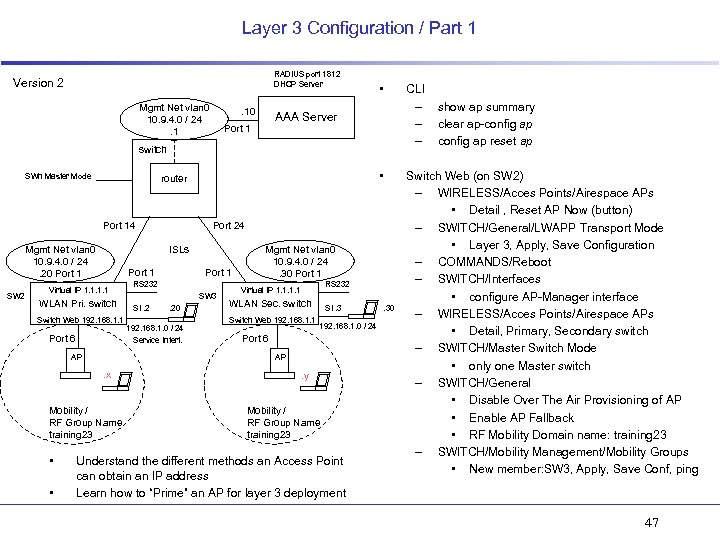
Layer 3 Configuration / Part 1 RADIUS port 1812 DHCP Server Version 2 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 1 . 10 • AAA Server Port 1 switch SWn Master Mode Port 14 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 20 Port 1 SW 2 Port 1 WLAN Pri. switch Switch Web 192. 168. 1. 1 Port 6 AP Port 1 RS 232 SW 3 SI. 2 . 20 192. 168. 1. 0 / 24 Service Interf. Mgmt Net vlan 0 10. 9. 4. 0 / 24. 30 Port 1 RS 232 Virtual IP 1. 1 WLAN Sec. switch Switch Web 192. 168. 1. 1 SI. 3 192. 168. 1. 0 / 24 Port 6 AP . x Mobility / RF Group Name training 23 • Port 24 ISLs Virtual IP 1. 1 • • router . y Mobility / RF Group Name training 23 Understand the different methods an Access Point can obtain an IP address Learn how to “Prime” an AP for layer 3 deployment . 30 CLI – – – show ap summary clear ap-config ap reset ap Switch Web (on SW 2) – WIRELESS/Acces Points/Airespace APs • Detail , Reset AP Now (button) – SWITCH/General/LWAPP Transport Mode • Layer 3, Apply, Save Configuration – COMMANDS/Reboot – SWITCH/Interfaces • configure AP-Manager interface – WIRELESS/Acces Points/Airespace APs • Detail, Primary, Secondary switch – SWITCH/Master Switch Mode • only one Master switch – SWITCH/General • Disable Over The Air Provisioning of AP • Enable AP Fallback • RF Mobility Domain name: training 23 – SWITCH/Mobility Management/Mobility Groups • New member: SW 3, Apply, Save Conf, ping 47
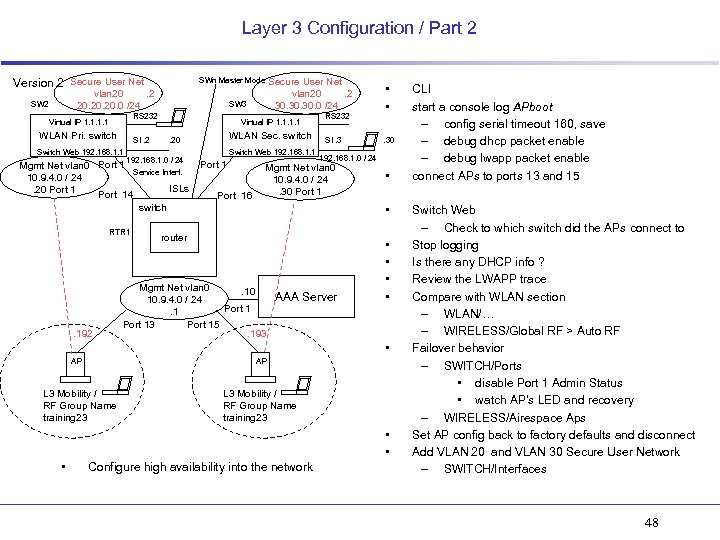
Layer 3 Configuration / Part 2 SWn Master Mode Version 2 Secure User Net vlan 20. 20. 20. 0 /24 SW 2 SW 3 RS 232 Virtual IP 1. 1 WLAN Pri. switch SI. 2 Switch Web 192. 168. 1. 1 Virtual IP 1. 1 . 192 WLAN Sec. switch . 20 192. 168. 1. 0 / 24 Mgmt Net vlan 0 Port 1 Service Interf. 10. 9. 4. 0 / 24 ISLs. 20 Port 14 switch RTR 1 Secure User Net vlan 20. 2 30. 30. 0 /24 Switch Web 192. 168. 1. 1 Port 16 RS 232 SI. 3 • • . 30 192. 168. 1. 0 / 24 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 30 Port 1 • • router Mgmt Net vlan 0. 10 10. 9. 4. 0 / 24 Port 1. 1 Port 13 Port 15. 193 AAA Server • • • AP AP L 3 Mobility / RF Group Name training 23 • • • Configure high availability into the network CLI start a console log APboot – config serial timeout 160, save – debug dhcp packet enable – debug lwapp packet enable connect APs to ports 13 and 15 Switch Web – Check to which switch did the APs connect to Stop logging Is there any DHCP info ? Review the LWAPP trace Compare with WLAN section – WLAN/… – WIRELESS/Global RF > Auto RF Failover behavior – SWITCH/Ports • disable Port 1 Admin Status • watch AP’s LED and recovery – WIRELESS/Airespace Aps Set AP config back to factory defaults and disconnect Add VLAN 20 and VLAN 30 Secure User Network – SWITCH/Interfaces 48
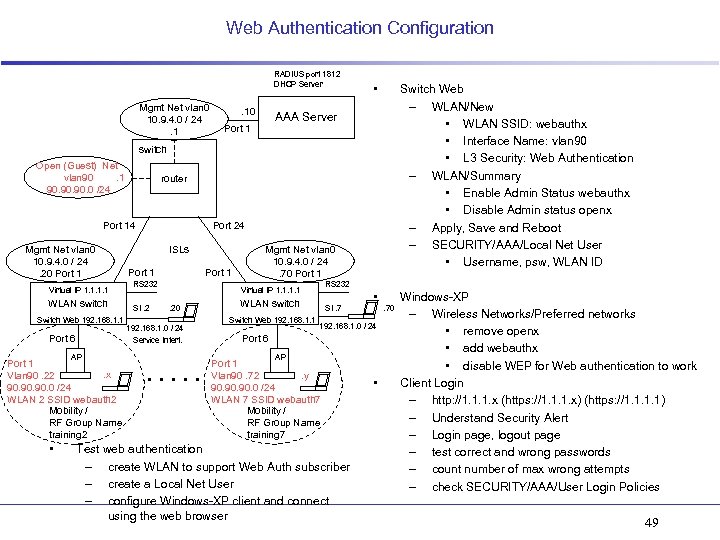
Web Authentication Configuration RADIUS port 1812 DHCP Server Mgmt Net vlan 0 10. 9. 4. 0 / 24. 1 . 10 • Switch Web – WLAN/New • WLAN SSID: webauthx • Interface Name: vlan 90 • L 3 Security: Web Authentication – WLAN/Summary • Enable Admin Status webauthx • Disable Admin status openx – Apply, Save and Reboot – SECURITY/AAA/Local Net User • Username, psw, WLAN ID AAA Server Port 1 switch Open (Guest) Net vlan 90. 1 90. 90. 0 /24 router Port 14 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 20 Port 1 Virtual IP 1. 1 WLAN switch Switch Web 192. 168. 1. 1 Port 6 AP Port 1. x Vlan 90. 22 90. 90. 0 /24 WLAN 2 SSID webauth 2 Mobility / RF Group Name training 2 • Port 24 ISLs Port 1 RS 232 SI. 2 Mgmt Net vlan 0 10. 9. 4. 0 / 24. 70 Port 1 RS 232 Virtual IP 1. 1. 20 192. 168. 1. 0 / 24 Service Interf. . . • WLAN switch Switch Web 192. 168. 1. 1 SI. 7 . 70 192. 168. 1. 0 / 24 Port 6 AP Port 1 Vlan 90. 72. y 90. 90. 0 /24 WLAN 7 SSID webauth 7 Mobility / RF Group Name training 7 Test web authentication – create WLAN to support Web Auth subscriber – create a Local Net User – configure Windows-XP client and connect using the web browser • Windows-XP – Wireless Networks/Preferred networks • remove openx • add webauthx • disable WEP for Web authentication to work Client Login – http: //1. 1. 1. x (https: //1. 1. 1. x) (https: //1. 1) – Understand Security Alert – Login page, logout page – test correct and wrong passwords – count number of max wrong attempts – check SECURITY/AAA/User Login Policies 49

Web Authentication Configuration 50

WEP Authentication Configuration 51
802. 1 x EAP-PEAP-MSCHAPv 2 Configuration 52

WPA EAP-PEAP-MSCHAPv 2 Configration 53

IPSec Configuration 54
IPSec Over L 2 TP Configuration Using Win-XP Client 55
Airespace Control System 56

AS Site Survey 57

Troubleshooting 58
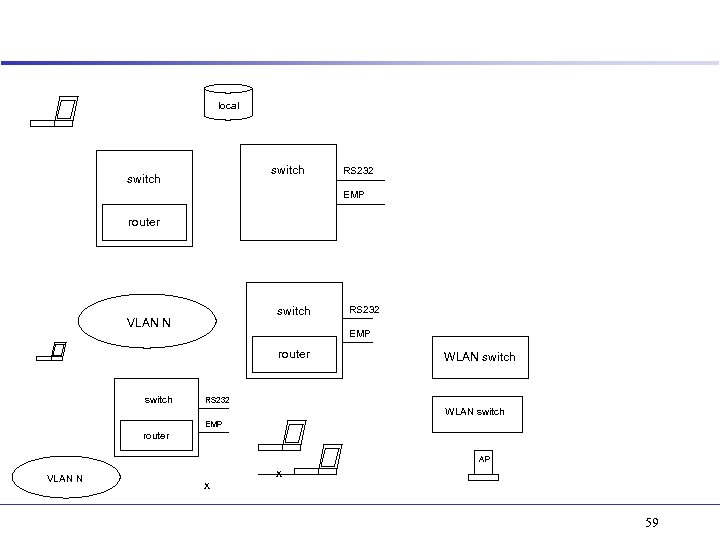
local switch RS 232 EMP router switch VLAN N EMP router switch RS 232 WLAN switch EMP router AP VLAN N x x 59
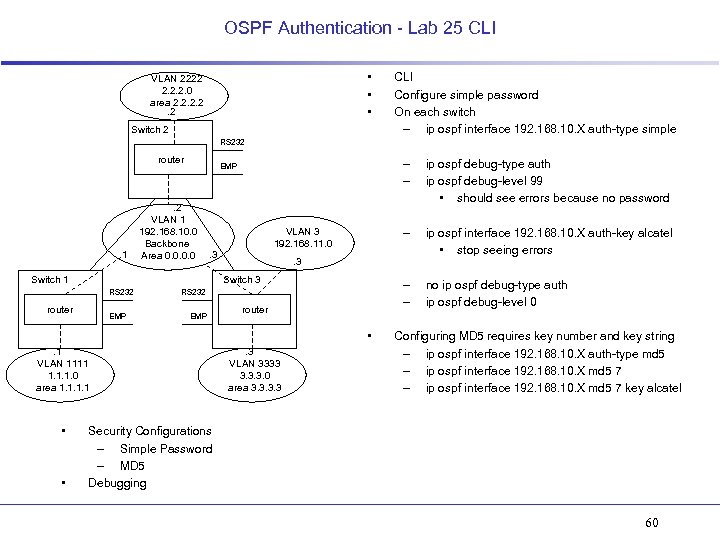
OSPF Authentication - Lab 25 CLI • • • VLAN 2222 2. 2. 2. 0 area 2. 2. 2 Switch 2 CLI Configure simple password On each switch – ip ospf interface 192. 168. 10. X auth-type simple RS 232 router . 1 – – . 2 VLAN 1 192. 168. 10. 0 Backbone Area 0. 0 . 3 Switch 1 router EMP RS 232 EMP router • . 1 VLAN 1111 1. 1. 1. 0 area 1. 1 • • no ip ospf debug-type auth ip ospf debug-level 0 . 3 Switch 3 RS 232 ip ospf interface 192. 168. 10. X auth-key alcatel • stop seeing errors – – VLAN 3 192. 168. 11. 0 ip ospf debug-type auth ip ospf debug-level 99 • should see errors because no password – EMP . 3 VLAN 3333 3. 3. 3. 0 area 3. 3 Configuring MD 5 requires key number and key string – ip ospf interface 192. 168. 10. X auth-type md 5 – ip ospf interface 192. 168. 10. X md 5 7 key alcatel Security Configurations – Simple Password – MD 5 Debugging 60

Configurations labs IPv 6 61

Sous-réseau avec adresses lien-local • Commandes 1) Vérifier les interfaces disponibles Panneau de configuration/Connexions réseau Activer les connexions réseau local et réseau sans fil Programmes/Accessoires/Invite de commande ipconfig /all Lister les interfaces (en IPv 4) ____________________ 2) Installer la pile IPv 6 ipv 6 install • Objectifs Installation (et désinstallation) de IPv 6 Configuration automatique des adresses Test du lien Lister les interfaces (en IPv 6) ipv 6 if ____________________ ____________________ 3) Tester le lien ping 6 adresse%index-interface 4) Désinstaller IPv 6 ipv 6 uninstall 62
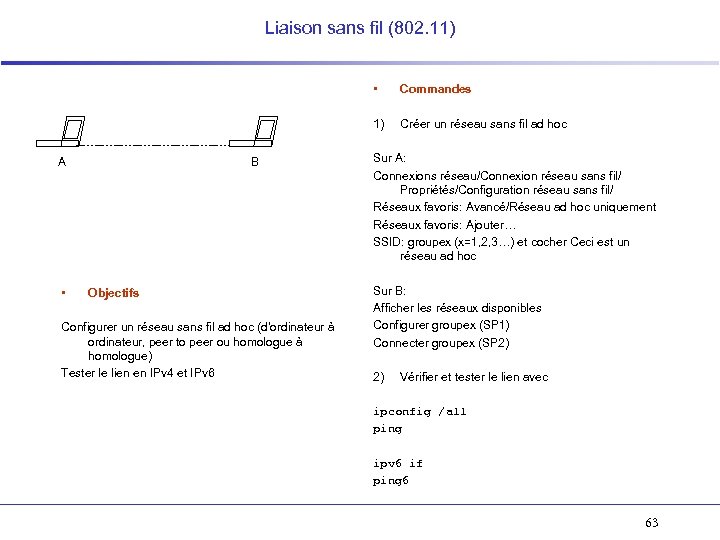
Liaison sans fil (802. 11) • 1) A • B Objectifs Configurer un réseau sans fil ad hoc (d’ordinateur à ordinateur, peer to peer ou homologue à homologue) Tester le lien en IPv 4 et IPv 6 Commandes Créer un réseau sans fil ad hoc Sur A: Connexions réseau/Connexion réseau sans fil/ Propriétés/Configuration réseau sans fil/ Réseaux favoris: Avancé/Réseau ad hoc uniquement Réseaux favoris: Ajouter… SSID: groupex (x=1, 2, 3…) et cocher Ceci est un réseau ad hoc Sur B: Afficher les réseaux disponibles Configurer groupex (SP 1) Connecter groupex (SP 2) 2) Vérifier et tester le lien avec ipconfig /all ping ipv 6 if ping 6 63
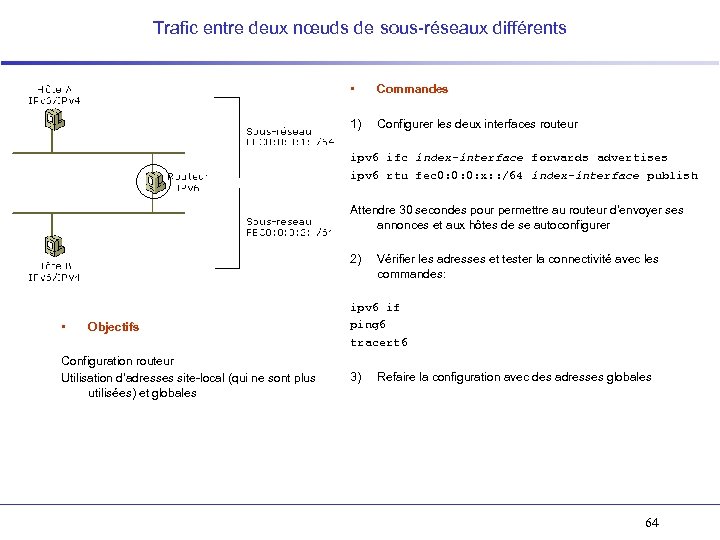
Trafic entre deux nœuds de sous-réseaux différents • Commandes 1) Configurer les deux interfaces routeur ipv 6 ifc index-interface forwards advertises ipv 6 rtu fec 0: 0: 0: x: : /64 index-interface publish Attendre 30 secondes pour permettre au routeur d’envoyer ses annonces et aux hôtes de se autoconfigurer 2) • Objectifs Configuration routeur Utilisation d’adresses site-local (qui ne sont plus utilisées) et globales Vérifier les adresses et tester la connectivité avec les commandes: ipv 6 if ping 6 tracert 6 3) Refaire la configuration avec des adresses globales 64
Routage statique et dynamique • • Commandes Objectifs 65
IPsec • • Commandes Objectifs 66
Mobilité • • Commandes Objectifs 67

Transition IPv 4 à IPv 6 68
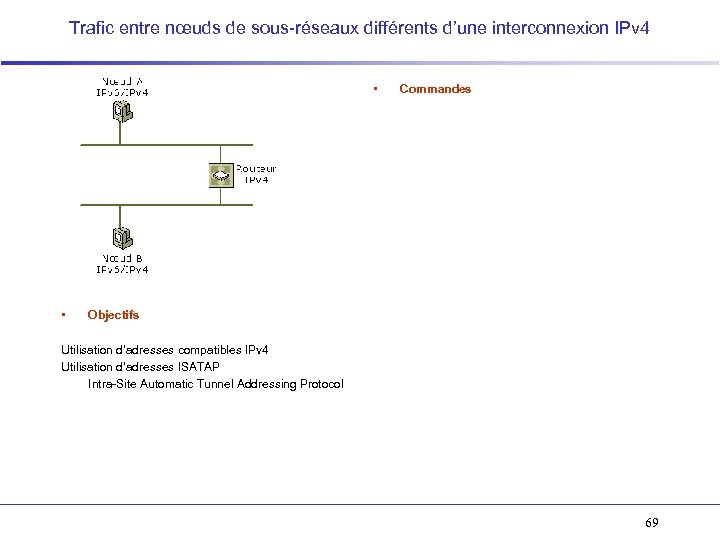
Trafic entre nœuds de sous-réseaux différents d’une interconnexion IPv 4 • • Commandes Objectifs Utilisation d’adresses compatibles IPv 4 Utilisation d’adresses ISATAP Intra-Site Automatic Tunnel Addressing Protocol 69
Trafic entre site différents via Internet (6 to 4) • • Commandes Objectifs 70
Connexion à 6 bone • • Commandes Objectifs 71

Utilisation de DNS (et DHCPv 6) 72
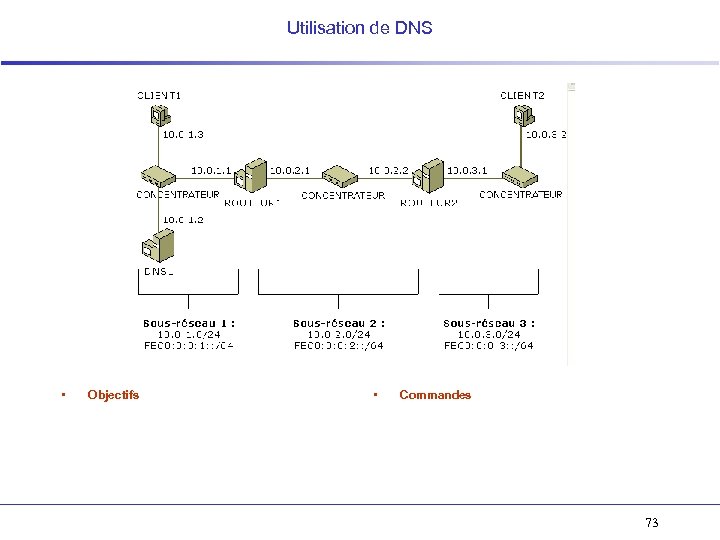
Utilisation de DNS • Objectifs • Commandes 73

• • Commandes Objectifs 74
6f38643bc5bc6ee8a0a3375a16cd12fa.ppt