8e4bf93089a727165431789c7db8a8e4.ppt
- Количество слайдов: 15

Akenti - Certificate-based Access Control for Widely Distributed Resources Abdelilah Essiari Gary Hoo Keith Jackson William Johnston Srilekha Mudumbai Mary Thompson

Motivation l Distributed computing environments, collaborative research environments l Resources, stakeholders and users are all distributed l Spanning organizational as well as geographical boundaries, e. g. , DOE Collaboratories l Requires a flexible but secure way to identify users l Requires a flexible and secure way for stakeholders to remotely specify access control for their resources

Goals l Access based on policy statements made by stakeholders l Handle multiple independent stakeholders for a single resource l Use Public Key Infrastructure standards to identify users and create digitally signed certificates l Emphasize usability
Approach l Public Key Infrastructure (PKI) l Architecture l Usability features

Public Key Infrastructure l Provides a uniform way for organizations to identify people or other entities through X. 509 identity certificates containing public keys. l These certificates and keys can be used though secured connections (SSL) and possession of a private key to establish the identity of the entities on the connection. l The keys can be used to provide digital signatures on documents. The authors and contents of signed documents can be verified at the time of use. l Public Key Infrastructure is beginning to be widely deployed in terms of organizations running Certificate Authorities.

Akenti Access Control l Minimal local Policy Files (authorization files). Who to trust, where to look for certificates. l Based on the following digitally signed certificates: n n Use. Condition certificates containing stakeholder policy n l X. 509 certificates for user authentication Attribute certificates in which a trusted party attests that a user possesses some attribute, e. g. training, group membership Can be called from any application that has an authenticated user’s identity certificate and a unique resource name, to return that users privileges with respect to the resource.
Required Infrastructure l Certificate Authority to issue identity certificates (required) n n Netscape CA - moderate cost and effort n l SSLeay provides simple CA for testing Enterprise solutions - Entrust, Verisign, … Method to check for revocation of identity certificates (required) n n l LDAP server - free from Univ. of Mich. . Or comes with Netscape CA Certificate Revocation lists - supported by most CA’s Network accessible ways for stakeholders to store their certificates (optional) n Web servers n MSQL web accessible data bases
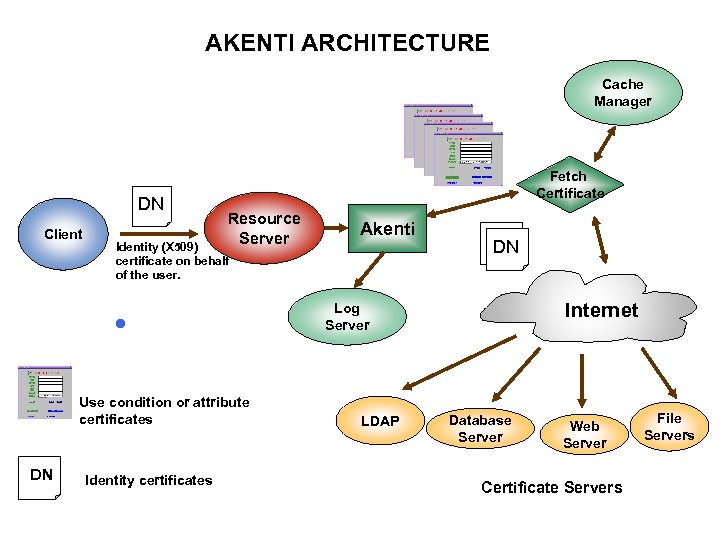
AKENTI ARCHITECTURE Cache Manager DN Client Fetch Certificate Resource Server Identity (X 509) certificate on behalf of the user. l Use condition or attribute certificates DN Akenti Identity certificates DN DN Internet Log Server LDAP Database Server Web Server Certificate Servers File Servers
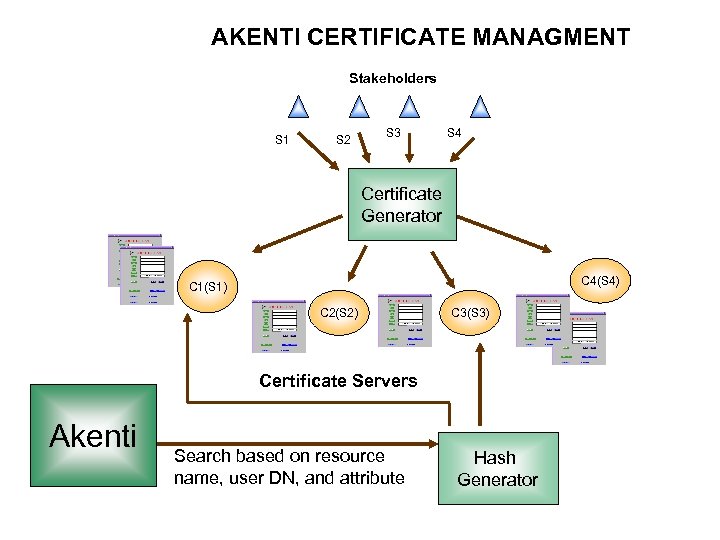
AKENTI CERTIFICATE MANAGMENT Stakeholders S 1 S 2 S 3 S 4 Certificate Generator C 4(S 4) C 1(S 1) C 2(S 2) C 3(S 3) Certificate Servers Akenti Search based on resource name, user DN, and attribute Hash Generator

Emphasis on usability l Akenti certificate generators provide a user friendly interface for stakeholders to specify the use constraints for their resources. l User or stakeholder can see a static view of the policy that controls the use of a resource. l Akenti Monitor applet provides a Web interface for a user to check his access to a resource to see why it succeeded or failed.

Vulnerabilities l Distributed certificates might not be available when needed. l Independent stakeholders may create a policy that is inconsistent with what they intend. Easy to deny all access.
Related Work l Ellison, et. al. SPKI - authorization certificates l Nekander & Partanen (HUT) SPKI style certificates for access permissions on Java code. To replace per/machine Java policy files. l Blaze, Feigenbaum Policy Maker and Key. Note based on authorization certificates written in a specified executable language. l Foster, Kesselman Globus Use of X. 509 identity certificates to authenticate users. l Ryutov, Neuman Generic Authorization and Accesscontrol API - and IETF draft standard t define an interface for authorization.
Status l Akenti enabled Apache Web servers deployed at LBNL and Sandia. n Controlling Akenti code distribution, secure data/image repository, ORNL electronic notebooks l We have given code to CONDOR, Univ. of Wisc. , Web. Flow at Syracuse Univ. , NIST, and ISI/USC l Servers run on Solaris, but client code runs on Linux as well l Java interface to Akenti policy engine exists and is used by the Anchor agent code.
Future Directions l Implement Akenti as a standalone server l Expand Use Conditions to include dynamic variables such as time-of-day, originating IP address, state variables. l Change syntax of certificates, probably to XML. We already have a Matchmaker want-ad style in addition to our original key-word/value syntax. l Add delegation - probably in the form of authorization certificates l Integrate with additional applications n Network bandwidth Quality of service, n Secure Mobile agents, n Group key agreement protocol.
Conclusions l As enterprises deploy PKI, identifying users by their identity certificates will become natural and transparent. n Currently there are several competing standards m browsers, Netscape and Explorer m Entrust - own client interface l Akenti/SSL overhead acceptable for medium grained access checking. E. g , starting an operation, making a authenticated connection. l Ease of use for stakeholders must be emphasized.
8e4bf93089a727165431789c7db8a8e4.ppt