b04985d883dfab3066cd4fcfa2efca27.ppt
- Количество слайдов: 61
 Agenda n Trust negotiation frameworks n Introduction n Trust. Builder n Trust-X n Laboratory assignment #2 n IPSec review n IPSec connections and configuration requirements n Assignment description
Agenda n Trust negotiation frameworks n Introduction n Trust. Builder n Trust-X n Laboratory assignment #2 n IPSec review n IPSec connections and configuration requirements n Assignment description
 Trust Negotiation Frameworks Introduction
Trust Negotiation Frameworks Introduction
 Trust Establishment n Trust establishment between strangers in open system. The client and server are not in the same security domain. n Access control decision is attribute based instead of identity based. n n n Examples: citizenship, clearance, job classification, group memberships, licenses, etc. The client’s role within his home organization. n Trust Management – coined by Matt Blaze
Trust Establishment n Trust establishment between strangers in open system. The client and server are not in the same security domain. n Access control decision is attribute based instead of identity based. n n n Examples: citizenship, clearance, job classification, group memberships, licenses, etc. The client’s role within his home organization. n Trust Management – coined by Matt Blaze
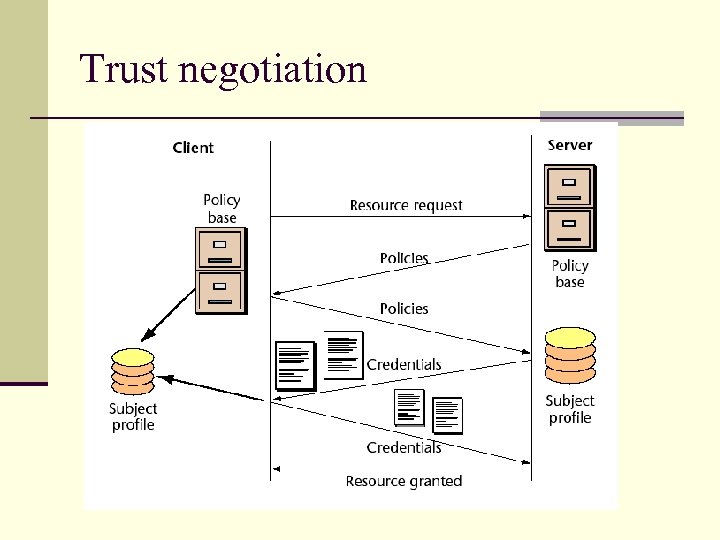 Trust negotiation
Trust negotiation
 Trust Negotiation n TN=“Approach to access control and authentication that enables resource requesters and providers in open systems to establish trust based on attributes other than identity. ”* n Goals n n Establish trust Maintain privacy of attributes n Process n Iteratively exchange digital credentials between two negotiating participants. n Begin by exchanging less sensitive credentials n Build trust gradually in order to exchange more sensitive credentials * Adaptive Trust Negotiation and Access Control, Tatyana Ryutov, et. al.
Trust Negotiation n TN=“Approach to access control and authentication that enables resource requesters and providers in open systems to establish trust based on attributes other than identity. ”* n Goals n n Establish trust Maintain privacy of attributes n Process n Iteratively exchange digital credentials between two negotiating participants. n Begin by exchanging less sensitive credentials n Build trust gradually in order to exchange more sensitive credentials * Adaptive Trust Negotiation and Access Control, Tatyana Ryutov, et. al.
 Example/Scenario Electronic business transactions n Parties in transaction don’t know each other n Attacks can be launched to the transaction (negotiation) infrastructure n Trust is required for transaction n n For buyers: n Trust that sellers will provide services n No disclosure of private buyer info For Sellers: n Trust that buyers will pay for services n Meet conditions for buying certain goods (age)
Example/Scenario Electronic business transactions n Parties in transaction don’t know each other n Attacks can be launched to the transaction (negotiation) infrastructure n Trust is required for transaction n n For buyers: n Trust that sellers will provide services n No disclosure of private buyer info For Sellers: n Trust that buyers will pay for services n Meet conditions for buying certain goods (age)
 Example/Scenario n In an electronic business transaction, participants interact beyond their local security domain. n Traditionally, pre-registration required n Without a pre-existing relationship trust must be established n Access control policies to control: Granting of resources n Revealing sensitive user information n
Example/Scenario n In an electronic business transaction, participants interact beyond their local security domain. n Traditionally, pre-registration required n Without a pre-existing relationship trust must be established n Access control policies to control: Granting of resources n Revealing sensitive user information n
 Digital Credentials n Are the vehicle for carrying attribute information reliably n Contain attributes of the credential owner asserted by the issuer n Issuer is a certification authority n n n Must be unforgeable Must be verifiable Digitally signed using PKI n X. 509 V 3 standard for public-key certificate
Digital Credentials n Are the vehicle for carrying attribute information reliably n Contain attributes of the credential owner asserted by the issuer n Issuer is a certification authority n n n Must be unforgeable Must be verifiable Digitally signed using PKI n X. 509 V 3 standard for public-key certificate
 Credential disclosure n Credential disclosure policy (CDP) n Conditions under which a party releases resources n Credentials it contains may be sensitive information and should be treated as protected resources n The CDP itself could be a protected object
Credential disclosure n Credential disclosure policy (CDP) n Conditions under which a party releases resources n Credentials it contains may be sensitive information and should be treated as protected resources n The CDP itself could be a protected object
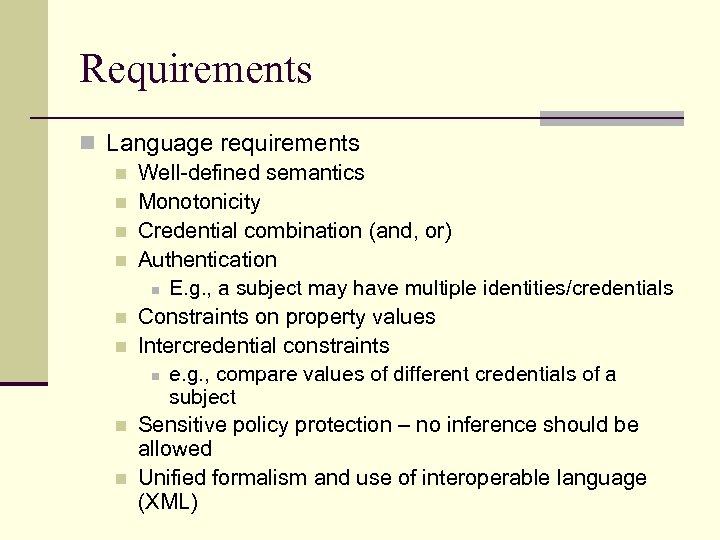 Requirements n Language requirements n Well-defined semantics n Monotonicity n Credential combination (and, or) n Authentication n E. g. , a subject may have multiple identities/credentials n Constraints on property values n Intercredential constraints n e. g. , compare values of different credentials of a subject n Sensitive policy protection – no inference should be allowed n Unified formalism and use of interoperable language (XML)
Requirements n Language requirements n Well-defined semantics n Monotonicity n Credential combination (and, or) n Authentication n E. g. , a subject may have multiple identities/credentials n Constraints on property values n Intercredential constraints n e. g. , compare values of different credentials of a subject n Sensitive policy protection – no inference should be allowed n Unified formalism and use of interoperable language (XML)
 Requirements n System requirement n Credential ownership (challenge response) n Credential validity n Credential chain discovery n Privacy protection mechanisms n Support for alternative negotiation strategies n n E. g. , maximizing protection or considering first the computation efforts Fast negotiation strategies
Requirements n System requirement n Credential ownership (challenge response) n Credential validity n Credential chain discovery n Privacy protection mechanisms n Support for alternative negotiation strategies n n E. g. , maximizing protection or considering first the computation efforts Fast negotiation strategies
 Some existing systems n Keynote trust management system n Trust Establishment at Haifa Research lab n Trust Policy Language n Trust. Builder n Unipro n Role-based trust management framework n Trust-X
Some existing systems n Keynote trust management system n Trust Establishment at Haifa Research lab n Trust Policy Language n Trust. Builder n Unipro n Role-based trust management framework n Trust-X
 Adaptive Trust Negotiation and Access Control Tatyana Ryutov, et. al.
Adaptive Trust Negotiation and Access Control Tatyana Ryutov, et. al.
 Introduction n Proposed framework: Adaptive Trust Negotiation and Access Control (ATNAC) n Combination of two systems into an access control architecture for electronic business services n Trust. Builder: Determines how sensitive information is disclosed n GAA-API: For adaptive access control
Introduction n Proposed framework: Adaptive Trust Negotiation and Access Control (ATNAC) n Combination of two systems into an access control architecture for electronic business services n Trust. Builder: Determines how sensitive information is disclosed n GAA-API: For adaptive access control
 GAA-API : Generic Authorization and Access-control API n Middleware API n Fine-grained access control n Application level intrusion detection and response n Can interact with Intrusion Detection Systems (IDS) to adapt network threat conditions n It does not support trust negotiation
GAA-API : Generic Authorization and Access-control API n Middleware API n Fine-grained access control n Application level intrusion detection and response n Can interact with Intrusion Detection Systems (IDS) to adapt network threat conditions n It does not support trust negotiation
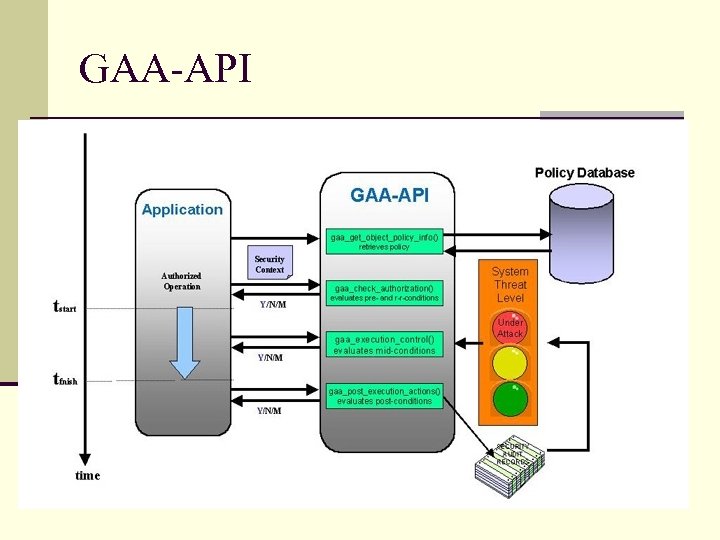 GAA-API
GAA-API
 Trust. Builder n Trust negotiation system developed by BYU and UIUC n Vulnerable to Do. S attacks. Large number of TN sessions sent to server n Having the server evaluate a very complex policy n Having the server evaluate invalid or irrelevant credentials n n Attacks aimed at collecting sensitive information
Trust. Builder n Trust negotiation system developed by BYU and UIUC n Vulnerable to Do. S attacks. Large number of TN sessions sent to server n Having the server evaluate a very complex policy n Having the server evaluate invalid or irrelevant credentials n n Attacks aimed at collecting sensitive information
 ATNAC n Combines an access control and a TN system to avoid the problems that each has on its own. n Supports fine-grained adaptive policies Protection based on perceived suspicion level n Uses feedback from IDS systems n n Reduces computational overhead n Associates less restrictive policies with lower suspicion levels.
ATNAC n Combines an access control and a TN system to avoid the problems that each has on its own. n Supports fine-grained adaptive policies Protection based on perceived suspicion level n Uses feedback from IDS systems n n Reduces computational overhead n Associates less restrictive policies with lower suspicion levels.
 ATNAC (2) n GAA-API n Access control policies for resources, services and operations n Policies are expressed in EACL format n Trust. Builder n Enforces sensitive security policies n Uses X. 509 v 3 digital certificates n Uses TPL policies EACL: Enhanced Access Control List TPL: Trust Policy Language
ATNAC (2) n GAA-API n Access control policies for resources, services and operations n Policies are expressed in EACL format n Trust. Builder n Enforces sensitive security policies n Uses X. 509 v 3 digital certificates n Uses TPL policies EACL: Enhanced Access Control List TPL: Trust Policy Language
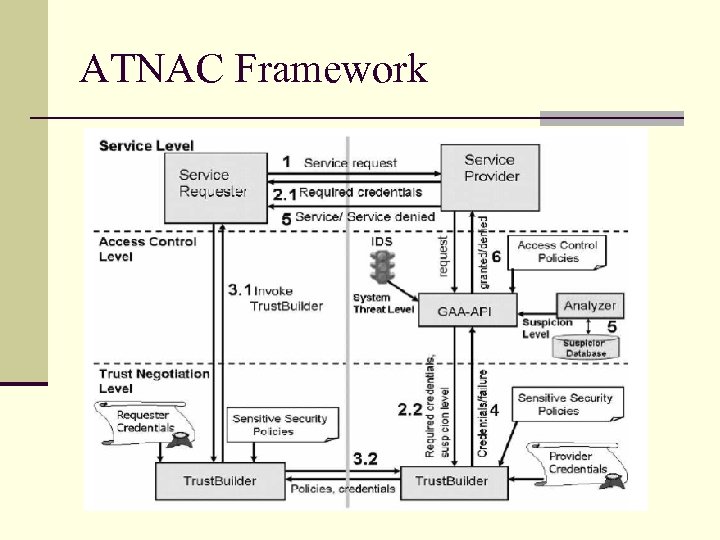 ATNAC Framework
ATNAC Framework
 Suspicion Level n Indicates how likely it is that the requester is acting improperly. n A separate SL is maintained for each requester of a service. n Has three components: n n n SDOS : Indicates probability of a Do. S attack from the requester SIL : For sensitive information leakage attempts So : Indicates other suspicious behavior n SL is increased as suspicious events occur and decreased as “positive” events occur.
Suspicion Level n Indicates how likely it is that the requester is acting improperly. n A separate SL is maintained for each requester of a service. n Has three components: n n n SDOS : Indicates probability of a Do. S attack from the requester SIL : For sensitive information leakage attempts So : Indicates other suspicious behavior n SL is increased as suspicious events occur and decreased as “positive” events occur.
 ATNAC operation n The Analyzer identifies requesters that generate n n unusually high numbers of similar requests and increment SDo. S In a trust negotiation process, credentials sent by client must match credentials requested by the system otherwise SDo. S set to 1. If either SDo. S, SIL or So > 0. 9, the system will block the requester at the firewall If SIL > threshold. Trust Builder will impose stricter sensitive credential release policies. As SIL increases, GAA-API uses tighter access control policies
ATNAC operation n The Analyzer identifies requesters that generate n n unusually high numbers of similar requests and increment SDo. S In a trust negotiation process, credentials sent by client must match credentials requested by the system otherwise SDo. S set to 1. If either SDo. S, SIL or So > 0. 9, the system will block the requester at the firewall If SIL > threshold. Trust Builder will impose stricter sensitive credential release policies. As SIL increases, GAA-API uses tighter access control policies
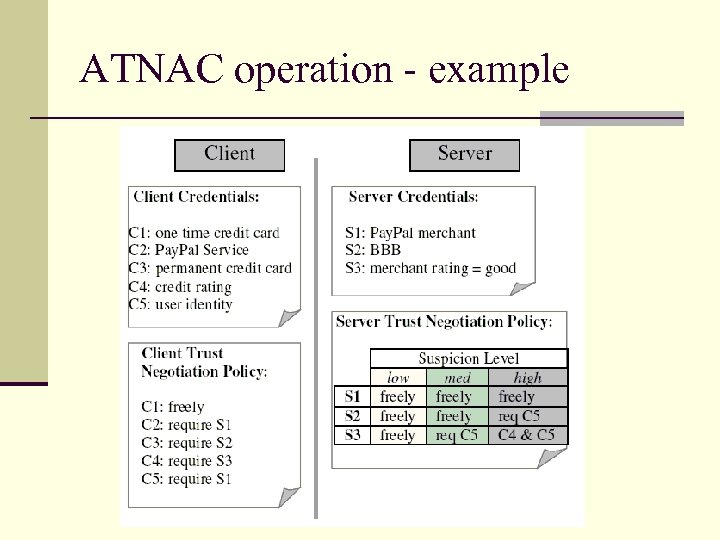 ATNAC operation - example
ATNAC operation - example
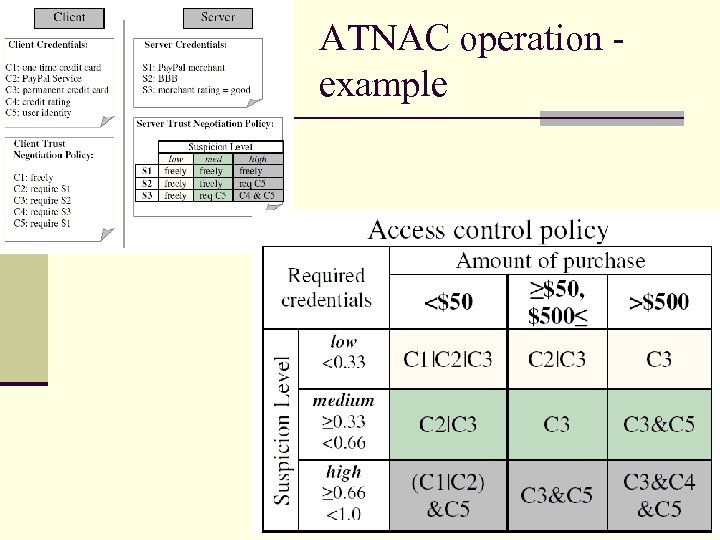 ATNAC operation example
ATNAC operation example
 Summary n ATNAC = framework for protecting sensitive resources in e-commerce n Trust negotiation useful for access control and authentication. n ATNAC dynamically adjusts security policies based on suspicion level n System protects against Do. S attacks on the service provider n Guards against sensitive information leaks.
Summary n ATNAC = framework for protecting sensitive resources in e-commerce n Trust negotiation useful for access control and authentication. n ATNAC dynamically adjusts security policies based on suspicion level n System protects against Do. S attacks on the service provider n Guards against sensitive information leaks.
 Trust-X: A Peer-to-Peer Framework for Trust Establishment Elisa Bertino, et. al.
Trust-X: A Peer-to-Peer Framework for Trust Establishment Elisa Bertino, et. al.
 Introduction n Trust establishment via trust negotiation n Exchange of digital credentials n Credential exchange has to be protected n Policies for credential disclosure n Claim: Current approaches to trust negotiation don’t provide a comprehensive solution that takes into account all phases of the negotiation process
Introduction n Trust establishment via trust negotiation n Exchange of digital credentials n Credential exchange has to be protected n Policies for credential disclosure n Claim: Current approaches to trust negotiation don’t provide a comprehensive solution that takes into account all phases of the negotiation process
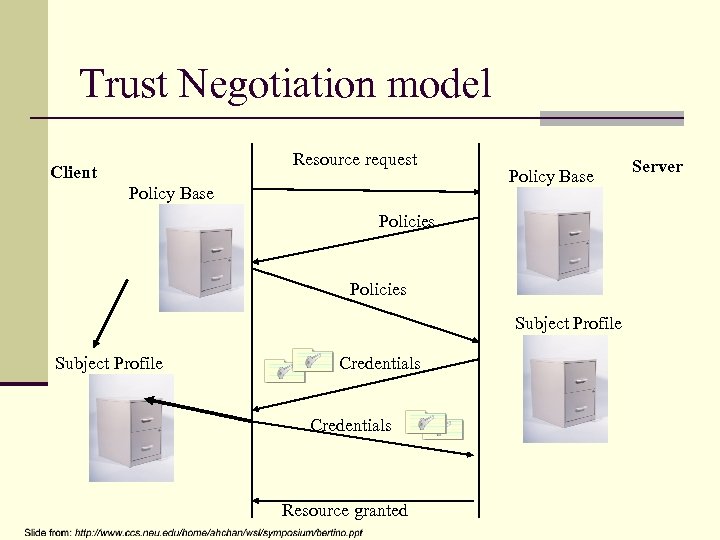 Trust Negotiation model Resource request Client Policy Base Policies Subject Profile Credentials Resource granted Server
Trust Negotiation model Resource request Client Policy Base Policies Subject Profile Credentials Resource granted Server
 Trust-X n XML-based system n Designed for a peer-to-peer environment n Both parties are equally responsible for negotiation management. n Either party can act as a requester or a controller of a resource n X-TNL: XML based language for specifying certificates and policies
Trust-X n XML-based system n Designed for a peer-to-peer environment n Both parties are equally responsible for negotiation management. n Either party can act as a requester or a controller of a resource n X-TNL: XML based language for specifying certificates and policies
 Trust-X (2) n Certificates: They are of two types n Credentials: States personal characteristics of its owner and is certified by a CA n Declarations: collect personal information about its owner that does not need to be certified n Trust tickets (X-TNL) n Used to speed up negotiations for a resource when access was granted in a previous negotiation n Support for policy pre-conditions n Negotiation conducted in phases
Trust-X (2) n Certificates: They are of two types n Credentials: States personal characteristics of its owner and is certified by a CA n Declarations: collect personal information about its owner that does not need to be certified n Trust tickets (X-TNL) n Used to speed up negotiations for a resource when access was granted in a previous negotiation n Support for policy pre-conditions n Negotiation conducted in phases
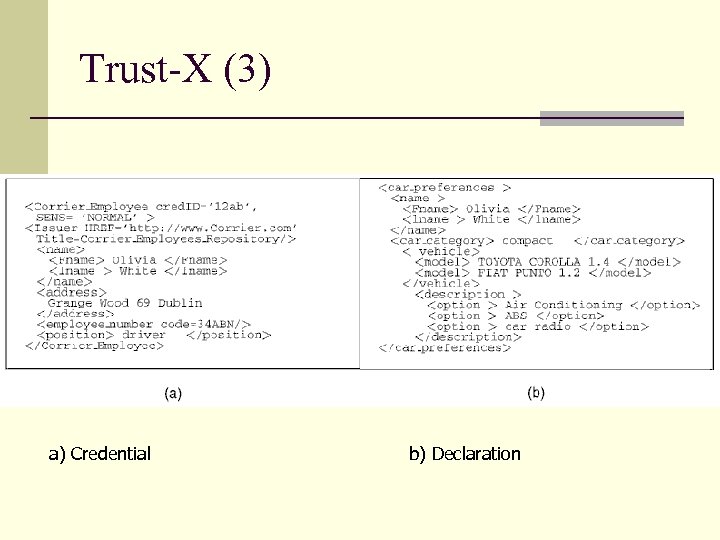 Trust-X (3) a) Credential b) Declaration
Trust-X (3) a) Credential b) Declaration
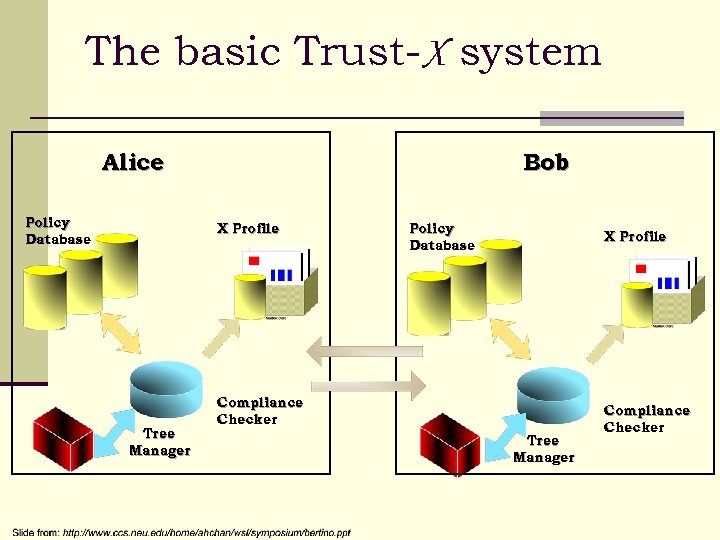 The basic Trust-X system Alice Policy Database Bob X Profile Tree Manager Policy Database X Profile Compliance Checker Tree Manager Compliance Checker
The basic Trust-X system Alice Policy Database Bob X Profile Tree Manager Policy Database X Profile Compliance Checker Tree Manager Compliance Checker
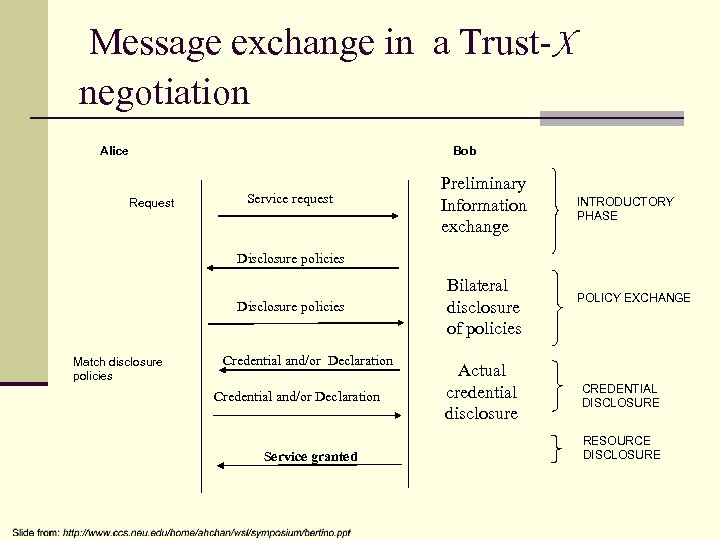 Message exchange in a Trust-X negotiation Alice Bob Request Service request Preliminary Information exchange INTRODUCTORY PHASE Disclosure policies Match disclosure policies Credential and/or Declaration Service granted Bilateral disclosure of policies Actual credential disclosure POLICY EXCHANGE CREDENTIAL DISCLOSURE RESOURCE DISCLOSURE
Message exchange in a Trust-X negotiation Alice Bob Request Service request Preliminary Information exchange INTRODUCTORY PHASE Disclosure policies Match disclosure policies Credential and/or Declaration Service granted Bilateral disclosure of policies Actual credential disclosure POLICY EXCHANGE CREDENTIAL DISCLOSURE RESOURCE DISCLOSURE
 Disclosure Policies n “They state the conditions under which a resource can be released during a negotiation” n Prerequisites – associated to a policy, it’s a set of alternative disclosure policies that must be satisfied before the disclosure of the policy they refer to.
Disclosure Policies n “They state the conditions under which a resource can be released during a negotiation” n Prerequisites – associated to a policy, it’s a set of alternative disclosure policies that must be satisfied before the disclosure of the policy they refer to.
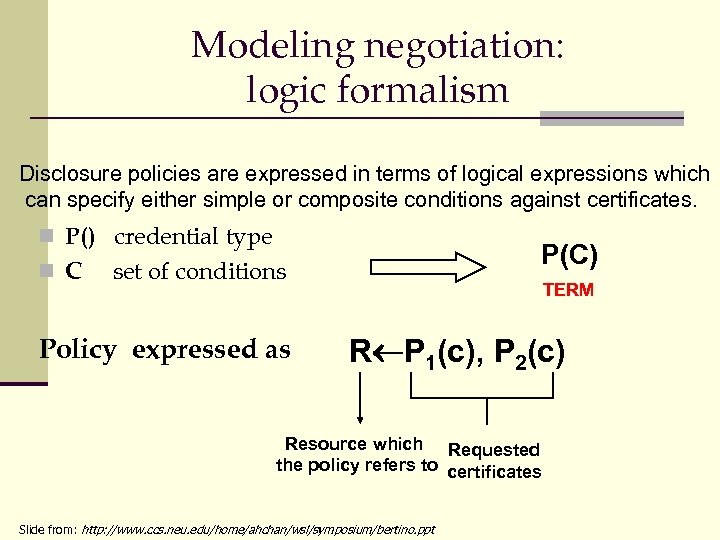 Modeling negotiation: logic formalism Disclosure policies are expressed in terms of logical expressions which can specify either simple or composite conditions against certificates. n P() credential type n C P(C) set of conditions Policy expressed as TERM R P 1(c), P 2(c) Resource which Requested the policy refers to certificates Slide from: http: //www. ccs. neu. edu/home/ahchan/wsl/symposium/bertino. ppt
Modeling negotiation: logic formalism Disclosure policies are expressed in terms of logical expressions which can specify either simple or composite conditions against certificates. n P() credential type n C P(C) set of conditions Policy expressed as TERM R P 1(c), P 2(c) Resource which Requested the policy refers to certificates Slide from: http: //www. ccs. neu. edu/home/ahchan/wsl/symposium/bertino. ppt
 Example Consider a Rental Car service. n The service is free for the employees of Corrier company. n Moreover, the Company already knows Corrier employees and has a digital copy of their driving licenses. Thus, it only asks the employees for the company badge and a valid copy of the ID card, to double check the ownership of the badge. n By contrast, rental service is available on payment for unknown requesters, who have to submit first a digital copy of their driving license and then a valid credit card. n These requirements can be formalized as follows:
Example Consider a Rental Car service. n The service is free for the employees of Corrier company. n Moreover, the Company already knows Corrier employees and has a digital copy of their driving licenses. Thus, it only asks the employees for the company badge and a valid copy of the ID card, to double check the ownership of the badge. n By contrast, rental service is available on payment for unknown requesters, who have to submit first a digital copy of their driving license and then a valid credit card. n These requirements can be formalized as follows:
 Example (2)
Example (2)
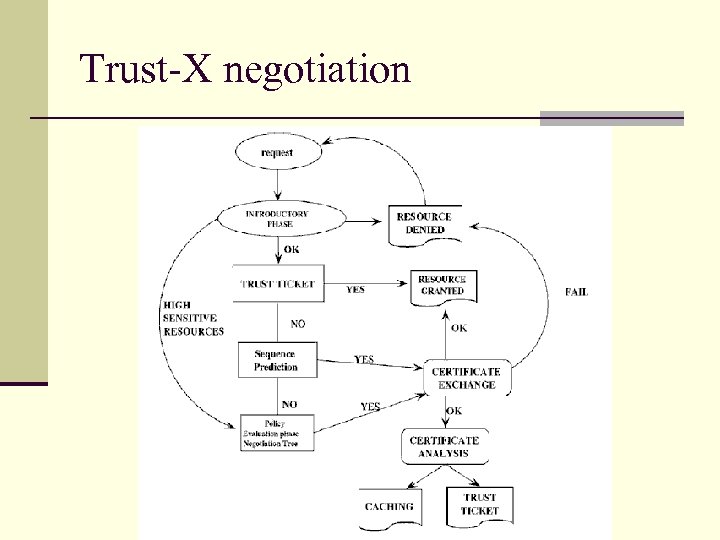 Trust-X negotiation
Trust-X negotiation
 Security Lab – Assignment #2 Carlos Caicedo Department of Information Science and Telecommunications University of Pittsburgh
Security Lab – Assignment #2 Carlos Caicedo Department of Information Science and Telecommunications University of Pittsburgh
 IPSec n Set of protocols/mechanisms n Encrypts and authenticates all traffic at the IP level n n n Protects all messages sent along a path Intermediate host with IPSec mechanism (firewall, gateway) is called a security gateway Use on LANs, WANs, public, and private networks n Application independent (Transparent to user) n Web browsing, telnet, ftp… n Provides at the IP level n n n Access control Connectionless integrity Data origin authentication Rejection of replayed packets Data confidentiality Limited traffic analysis confidentiality
IPSec n Set of protocols/mechanisms n Encrypts and authenticates all traffic at the IP level n n n Protects all messages sent along a path Intermediate host with IPSec mechanism (firewall, gateway) is called a security gateway Use on LANs, WANs, public, and private networks n Application independent (Transparent to user) n Web browsing, telnet, ftp… n Provides at the IP level n n n Access control Connectionless integrity Data origin authentication Rejection of replayed packets Data confidentiality Limited traffic analysis confidentiality
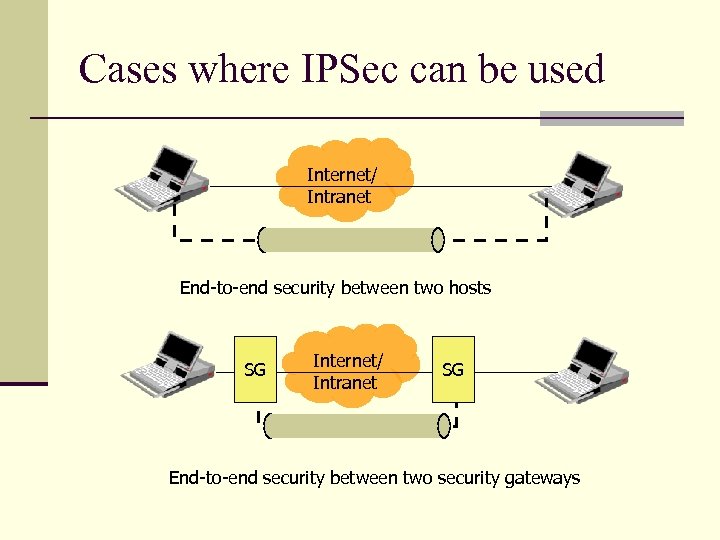 Cases where IPSec can be used Internet/ Intranet End-to-end security between two hosts SG Internet/ Intranet SG End-to-end security between two security gateways
Cases where IPSec can be used Internet/ Intranet End-to-end security between two hosts SG Internet/ Intranet SG End-to-end security between two security gateways
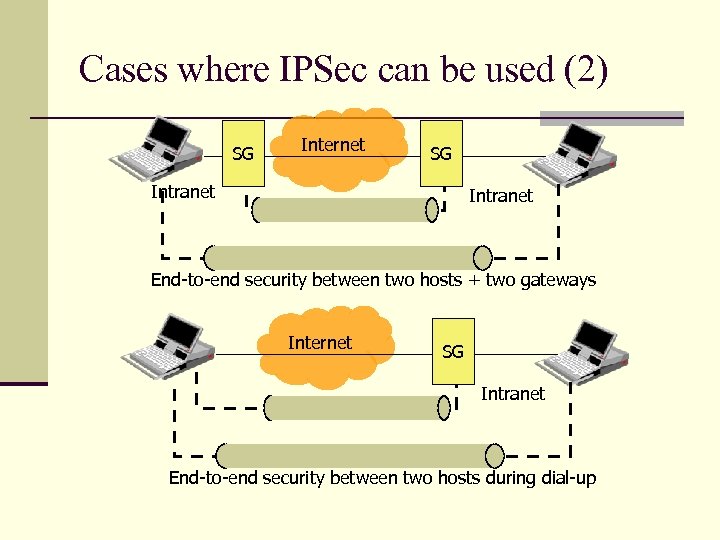 Cases where IPSec can be used (2) SG Internet SG Intranet End-to-end security between two hosts + two gateways Internet SG Intranet End-to-end security between two hosts during dial-up
Cases where IPSec can be used (2) SG Internet SG Intranet End-to-end security between two hosts + two gateways Internet SG Intranet End-to-end security between two hosts during dial-up
 IPSec Protocols n Authentication header (AH) protocol n Message integrity n Origin authentication n Anti-replay services n Encapsulating security payload (ESP) protocol n Confidentiality n Message integrity n Origin authentication n Anti-replay services n Internet Key Exchange (ISAKMP/IKE) n Exchanging keys between entities that need to communicate over the Internet n What authentication methods to use, how long to use the keys, etc.
IPSec Protocols n Authentication header (AH) protocol n Message integrity n Origin authentication n Anti-replay services n Encapsulating security payload (ESP) protocol n Confidentiality n Message integrity n Origin authentication n Anti-replay services n Internet Key Exchange (ISAKMP/IKE) n Exchanging keys between entities that need to communicate over the Internet n What authentication methods to use, how long to use the keys, etc.
 Security Association (SA) n Unidirectional relationship between peers (a sender and a receiver) n Specifies the security services provided to the traffic carried on the SA n Security enhancements to a channel along a path n Identified by three parameters: n IP Destination Address n Security Protocol Identifier Specifies whether AH or ESP is being used Security Parameters Index (SPI) n Specifies the security parameters associated with the SA n n
Security Association (SA) n Unidirectional relationship between peers (a sender and a receiver) n Specifies the security services provided to the traffic carried on the SA n Security enhancements to a channel along a path n Identified by three parameters: n IP Destination Address n Security Protocol Identifier Specifies whether AH or ESP is being used Security Parameters Index (SPI) n Specifies the security parameters associated with the SA n n
 Security Association Databases n IPSec needs to know the SAs that exist in order to provide security services n Security Policy Database (SPD) n n IPSec uses SPD to handle messages For each IP packet, it decides whether an IPSec service is provided, bypassed, or if the packet is to be discarded n Security Association Database (SAD) n Keeps track of the sequence number n AH information (keys, algorithms, lifetimes) n ESP information (keys, algorithms, lifetimes, etc. ) n Lifetime of the SA n Protocol mode n MTU
Security Association Databases n IPSec needs to know the SAs that exist in order to provide security services n Security Policy Database (SPD) n n IPSec uses SPD to handle messages For each IP packet, it decides whether an IPSec service is provided, bypassed, or if the packet is to be discarded n Security Association Database (SAD) n Keeps track of the sequence number n AH information (keys, algorithms, lifetimes) n ESP information (keys, algorithms, lifetimes, etc. ) n Lifetime of the SA n Protocol mode n MTU
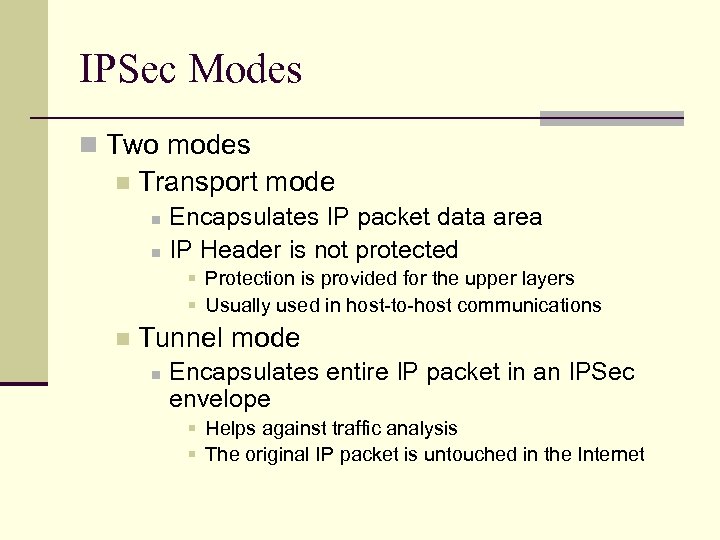 IPSec Modes n Two modes n Transport mode Encapsulates IP packet data area n IP Header is not protected n § Protection is provided for the upper layers § Usually used in host-to-host communications n Tunnel mode n Encapsulates entire IP packet in an IPSec envelope § Helps against traffic analysis § The original IP packet is untouched in the Internet
IPSec Modes n Two modes n Transport mode Encapsulates IP packet data area n IP Header is not protected n § Protection is provided for the upper layers § Usually used in host-to-host communications n Tunnel mode n Encapsulates entire IP packet in an IPSec envelope § Helps against traffic analysis § The original IP packet is untouched in the Internet
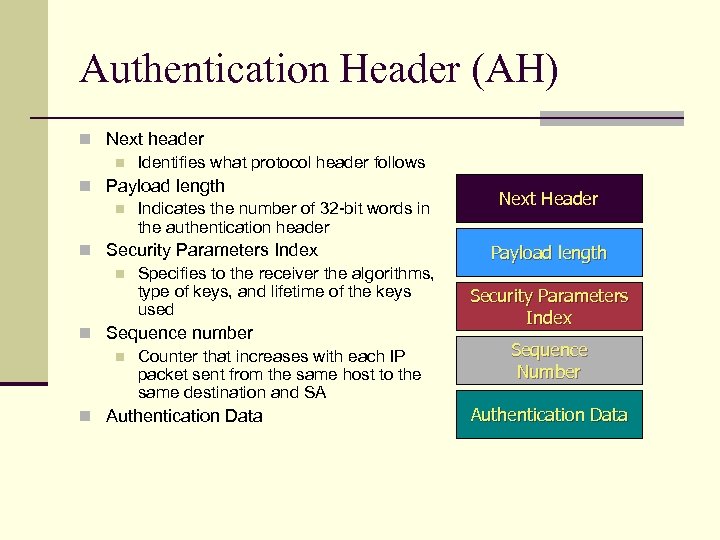 Authentication Header (AH) n Next header n Identifies what protocol header follows n Payload length n Indicates the number of 32 -bit words in the authentication header n Security Parameters Index n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used n Sequence number n Counter that increases with each IP packet sent from the same host to the same destination and SA n Authentication Data Next Header Payload length Security Parameters Index Sequence Number Authentication Data
Authentication Header (AH) n Next header n Identifies what protocol header follows n Payload length n Indicates the number of 32 -bit words in the authentication header n Security Parameters Index n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used n Sequence number n Counter that increases with each IP packet sent from the same host to the same destination and SA n Authentication Data Next Header Payload length Security Parameters Index Sequence Number Authentication Data
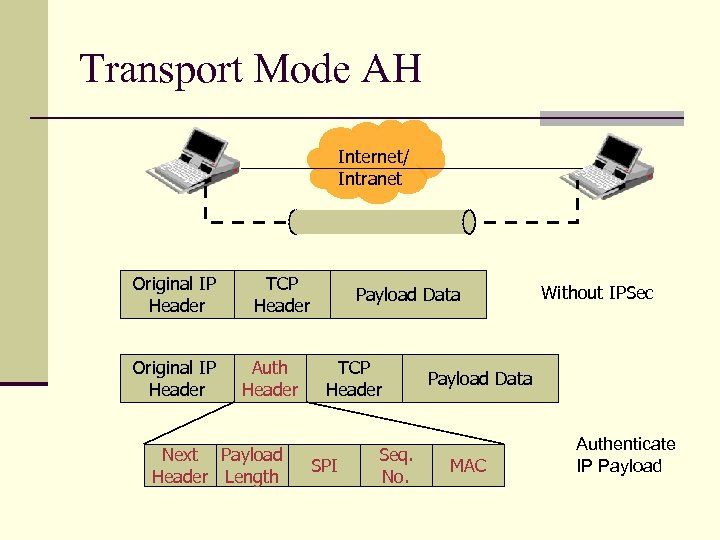 Transport Mode AH Internet/ Intranet Original IP Header TCP Header Auth Header Next Payload Header Length Payload Data TCP Header SPI Seq. No. Without IPSec Payload Data MAC Authenticate IP Payload
Transport Mode AH Internet/ Intranet Original IP Header TCP Header Auth Header Next Payload Header Length Payload Data TCP Header SPI Seq. No. Without IPSec Payload Data MAC Authenticate IP Payload
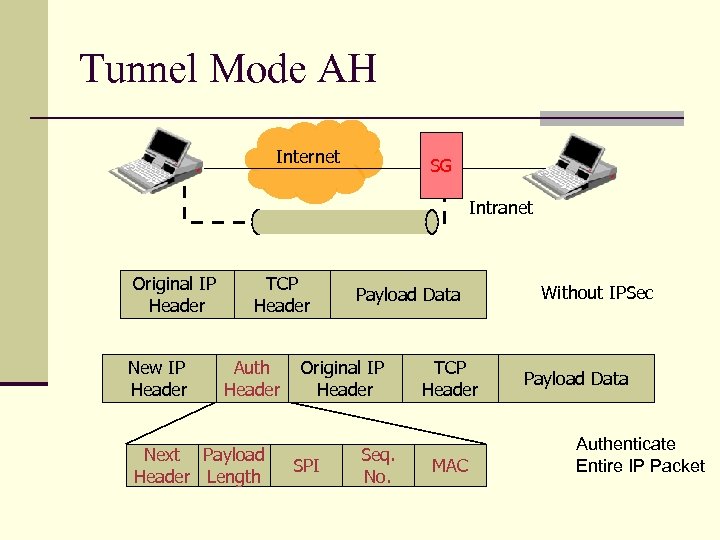 Tunnel Mode AH Internet SG Intranet Original IP Header New IP Header TCP Header Auth Header Next Payload Header Length Payload Data Original IP Header SPI Seq. No. TCP Header MAC Without IPSec Payload Data Authenticate Entire IP Packet
Tunnel Mode AH Internet SG Intranet Original IP Header New IP Header TCP Header Auth Header Next Payload Header Length Payload Data Original IP Header SPI Seq. No. TCP Header MAC Without IPSec Payload Data Authenticate Entire IP Packet
 ESP – Encapsulating Security Payload n Creates a new header n n in addition to the IP header Creates a new trailer Encrypts the payload data Authenticates the security association Prevents replay Security Parameters Index (SPI) – 32 bits Sequence Number 32 bits Payload Data Padding/ Next Header Authentication Data
ESP – Encapsulating Security Payload n Creates a new header n n in addition to the IP header Creates a new trailer Encrypts the payload data Authenticates the security association Prevents replay Security Parameters Index (SPI) – 32 bits Sequence Number 32 bits Payload Data Padding/ Next Header Authentication Data
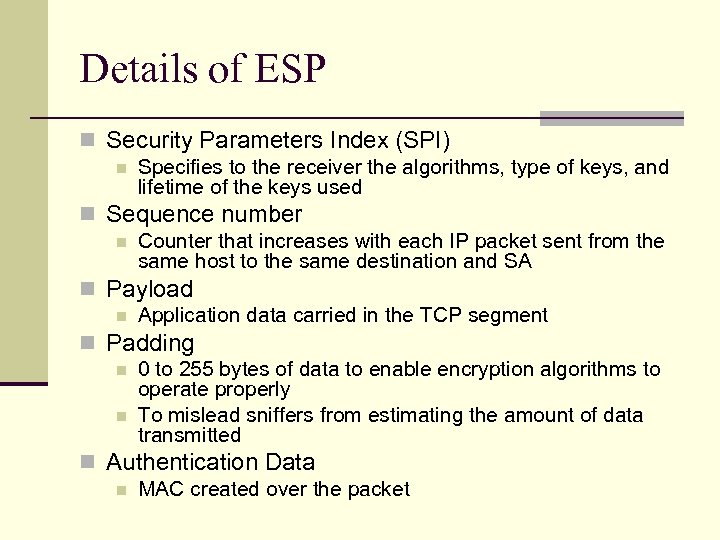 Details of ESP n Security Parameters Index (SPI) n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used n Sequence number n Counter that increases with each IP packet sent from the same host to the same destination and SA n Payload n Application data carried in the TCP segment n Padding n 0 to 255 bytes of data to enable encryption algorithms to operate properly n To mislead sniffers from estimating the amount of data transmitted n Authentication Data n MAC created over the packet
Details of ESP n Security Parameters Index (SPI) n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used n Sequence number n Counter that increases with each IP packet sent from the same host to the same destination and SA n Payload n Application data carried in the TCP segment n Padding n 0 to 255 bytes of data to enable encryption algorithms to operate properly n To mislead sniffers from estimating the amount of data transmitted n Authentication Data n MAC created over the packet
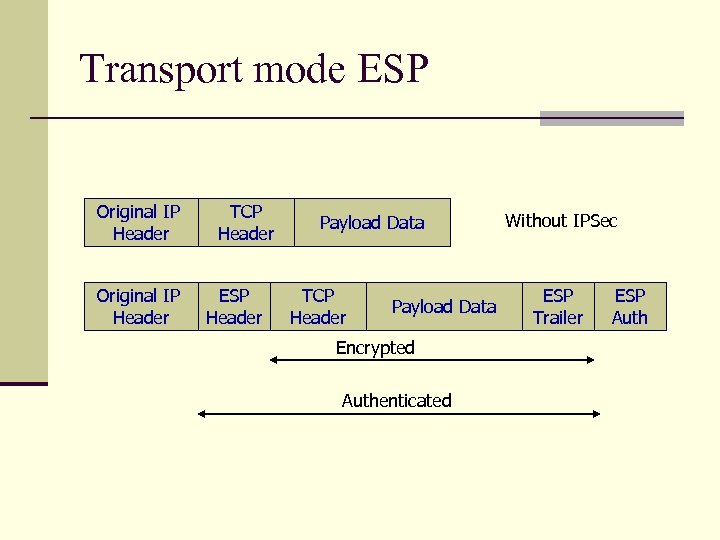 Transport mode ESP Original IP Header TCP Header ESP Header Payload Data TCP Header Payload Data Encrypted Authenticated Without IPSec ESP Trailer ESP Auth
Transport mode ESP Original IP Header TCP Header ESP Header Payload Data TCP Header Payload Data Encrypted Authenticated Without IPSec ESP Trailer ESP Auth
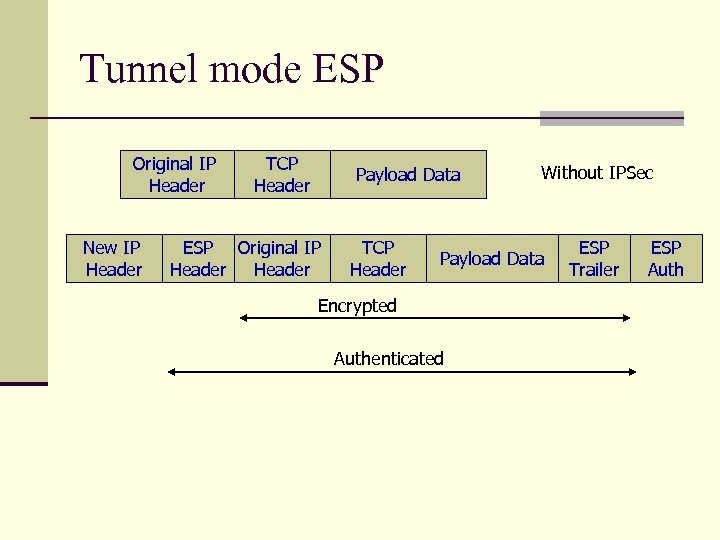 Tunnel mode ESP Original IP Header New IP Header TCP Header Payload Data ESP Original IP Header TCP Header Without IPSec Payload Data Encrypted Authenticated ESP Trailer ESP Auth
Tunnel mode ESP Original IP Header New IP Header TCP Header Payload Data ESP Original IP Header TCP Header Without IPSec Payload Data Encrypted Authenticated ESP Trailer ESP Auth
 IPSec Connections n Something triggers the connection n If no VPN connection exists: n IPsec will use ISAKMP/IKE Phase 1 to build a secure management connection. n Management connection is used so that the two peers can communicate with each other securely and can build secure data connections. n Using the secure management connection, the two IPsec peers will negotiate the security parameters that are used to build the secure data connections (Phase 2)
IPSec Connections n Something triggers the connection n If no VPN connection exists: n IPsec will use ISAKMP/IKE Phase 1 to build a secure management connection. n Management connection is used so that the two peers can communicate with each other securely and can build secure data connections. n Using the secure management connection, the two IPsec peers will negotiate the security parameters that are used to build the secure data connections (Phase 2)
 IPSec Connections n Once the data connections are built, the IPsec devices can use them to share user data securely n Management and data connections have a lifetime associated with them. n keying information is regenerated to provide for better security
IPSec Connections n Once the data connections are built, the IPsec devices can use them to share user data securely n Management and data connections have a lifetime associated with them. n keying information is regenerated to provide for better security
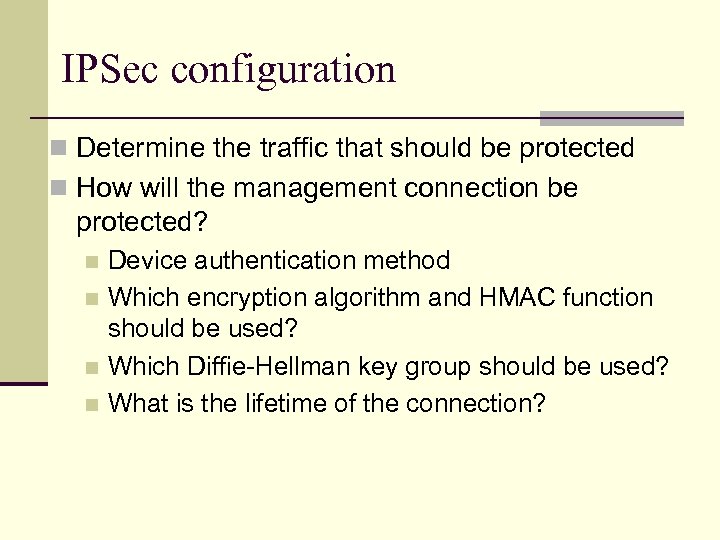 IPSec configuration n Determine the traffic that should be protected n How will the management connection be protected? Device authentication method n Which encryption algorithm and HMAC function should be used? n Which Diffie-Hellman key group should be used? n What is the lifetime of the connection? n
IPSec configuration n Determine the traffic that should be protected n How will the management connection be protected? Device authentication method n Which encryption algorithm and HMAC function should be used? n Which Diffie-Hellman key group should be used? n What is the lifetime of the connection? n
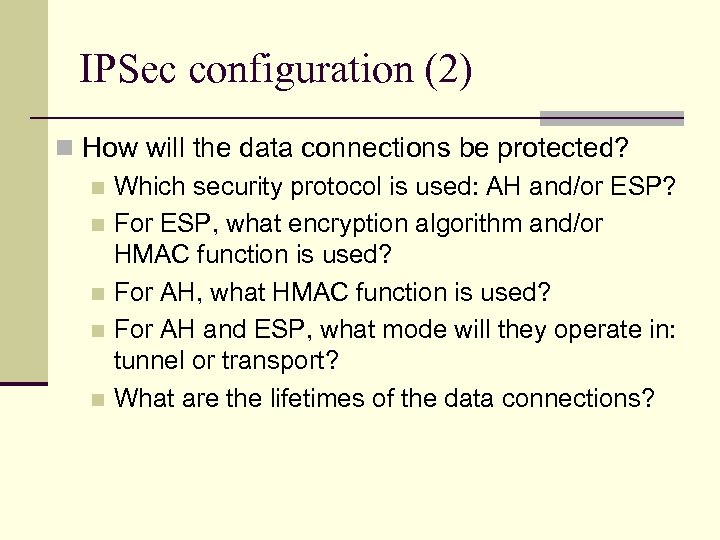 IPSec configuration (2) n How will the data connections be protected? n Which security protocol is used: AH and/or ESP? n For ESP, what encryption algorithm and/or HMAC function is used? n For AH, what HMAC function is used? n For AH and ESP, what mode will they operate in: tunnel or transport? n What are the lifetimes of the data connections?
IPSec configuration (2) n How will the data connections be protected? n Which security protocol is used: AH and/or ESP? n For ESP, what encryption algorithm and/or HMAC function is used? n For AH, what HMAC function is used? n For AH and ESP, what mode will they operate in: tunnel or transport? n What are the lifetimes of the data connections?
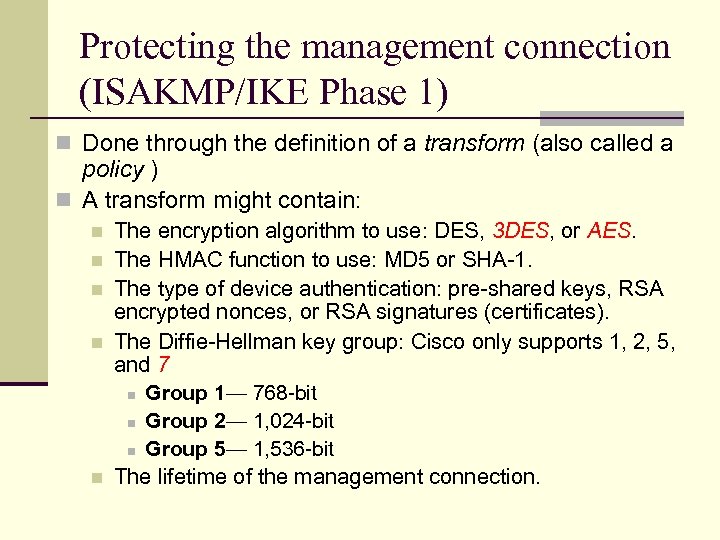 Protecting the management connection (ISAKMP/IKE Phase 1) n Done through the definition of a transform (also called a policy ) n A transform might contain: n n n The encryption algorithm to use: DES, 3 DES, or AES. The HMAC function to use: MD 5 or SHA-1. The type of device authentication: pre-shared keys, RSA encrypted nonces, or RSA signatures (certificates). The Diffie-Hellman key group: Cisco only supports 1, 2, 5, and 7 n Group 1— 768 -bit n Group 2— 1, 024 -bit n Group 5— 1, 536 -bit The lifetime of the management connection.
Protecting the management connection (ISAKMP/IKE Phase 1) n Done through the definition of a transform (also called a policy ) n A transform might contain: n n n The encryption algorithm to use: DES, 3 DES, or AES. The HMAC function to use: MD 5 or SHA-1. The type of device authentication: pre-shared keys, RSA encrypted nonces, or RSA signatures (certificates). The Diffie-Hellman key group: Cisco only supports 1, 2, 5, and 7 n Group 1— 768 -bit n Group 2— 1, 024 -bit n Group 5— 1, 536 -bit The lifetime of the management connection.
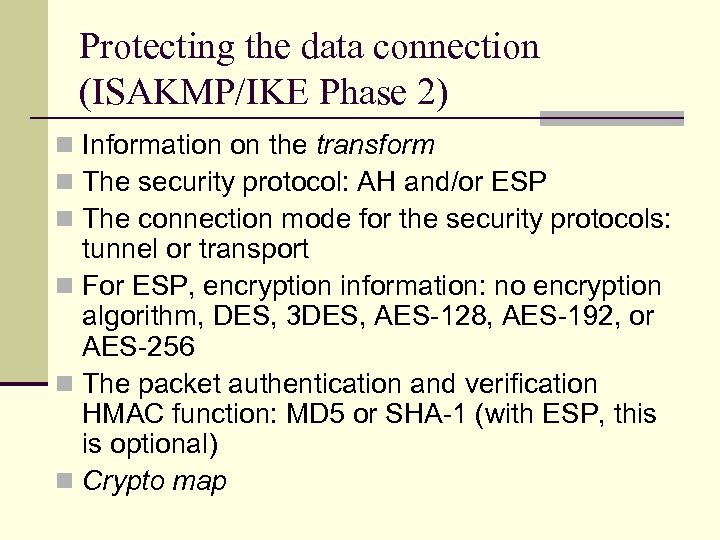 Protecting the data connection (ISAKMP/IKE Phase 2) n Information on the transform n The security protocol: AH and/or ESP n The connection mode for the security protocols: tunnel or transport n For ESP, encryption information: no encryption algorithm, DES, 3 DES, AES-128, AES-192, or AES-256 n The packet authentication and verification HMAC function: MD 5 or SHA-1 (with ESP, this is optional) n Crypto map
Protecting the data connection (ISAKMP/IKE Phase 2) n Information on the transform n The security protocol: AH and/or ESP n The connection mode for the security protocols: tunnel or transport n For ESP, encryption information: no encryption algorithm, DES, 3 DES, AES-128, AES-192, or AES-256 n The packet authentication and verification HMAC function: MD 5 or SHA-1 (with ESP, this is optional) n Crypto map
 Assignment Description n Establish a VPN tunnel using IPSec to protect the traffic flowing between two corporate LANs LAN 1 Internet LAN 2
Assignment Description n Establish a VPN tunnel using IPSec to protect the traffic flowing between two corporate LANs LAN 1 Internet LAN 2


