7c558499eda3f6198362f95fb70921cd.ppt
- Количество слайдов: 24
 Agenda l Course high-lights – Symmetric and asymmetric cryptography – Digital signatures and MACs – Certificates – Protocols Interactive l Non-interactive l – Smart-cards Apr 22, 2003 Mårten Trolin 1
Agenda l Course high-lights – Symmetric and asymmetric cryptography – Digital signatures and MACs – Certificates – Protocols Interactive l Non-interactive l – Smart-cards Apr 22, 2003 Mårten Trolin 1
 Symmetric vs. asymmetric cryptography l Symmetric ciphers – sender and recipient use the same key – Dkey(Ekey(m)) = m Substitution cipher is an example of a symmetric cipher l Impractical for big systems – number of keys is quadratic in the number of users l The solution – asymmtric algorithms. Think of a locked mailbox! Different keys for encryption and decryption l – Dprivate key(Epublic key(m)) = m Apr 22, 2003 Mårten Trolin 2
Symmetric vs. asymmetric cryptography l Symmetric ciphers – sender and recipient use the same key – Dkey(Ekey(m)) = m Substitution cipher is an example of a symmetric cipher l Impractical for big systems – number of keys is quadratic in the number of users l The solution – asymmtric algorithms. Think of a locked mailbox! Different keys for encryption and decryption l – Dprivate key(Epublic key(m)) = m Apr 22, 2003 Mårten Trolin 2
 Hash functions l A hash function computes a fixed length value from a variable length source – Example: Check sums in communication protocols – Indices in databases More convenient to handle a hash of a document instead of the document itself l We will consider cryptographically secure hash functions. l Apr 22, 2003 Mårten Trolin 3
Hash functions l A hash function computes a fixed length value from a variable length source – Example: Check sums in communication protocols – Indices in databases More convenient to handle a hash of a document instead of the document itself l We will consider cryptographically secure hash functions. l Apr 22, 2003 Mårten Trolin 3
 Properties of good hash functions l Let H be a hash function l One-way – Given v, unfeasible to compute an x such that H(x) = v l Collision-free – Infeasible to find x 1 and x 2 such that H(x 1) = H(x 2) and x 1 x 2 Apr 22, 2003 Mårten Trolin 4
Properties of good hash functions l Let H be a hash function l One-way – Given v, unfeasible to compute an x such that H(x) = v l Collision-free – Infeasible to find x 1 and x 2 such that H(x 1) = H(x 2) and x 1 x 2 Apr 22, 2003 Mårten Trolin 4
 Digital signatures l Used to ensure authenticity. l A digital signatures binds a document to a person. l In a public key infrastructure (PKI), a person produces a digital signature using his private key l The signature can be verified using the public key. Apr 22, 2003 Mårten Trolin 5
Digital signatures l Used to ensure authenticity. l A digital signatures binds a document to a person. l In a public key infrastructure (PKI), a person produces a digital signature using his private key l The signature can be verified using the public key. Apr 22, 2003 Mårten Trolin 5
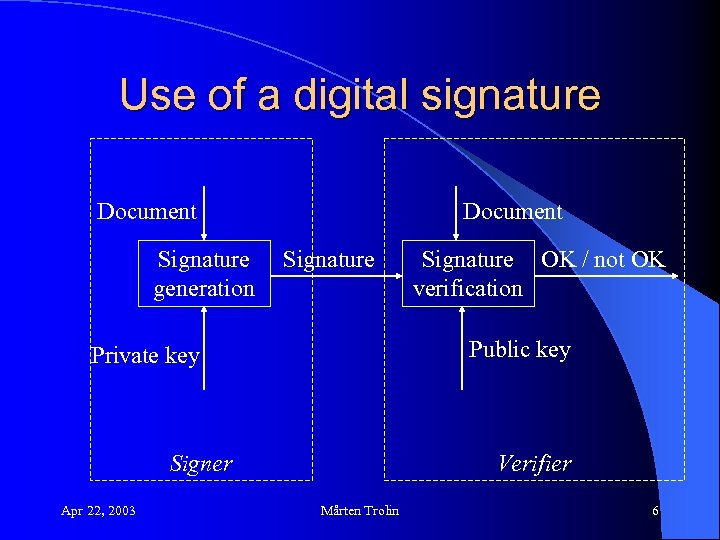 Use of a digital signature Document Signature generation Document Signature Public key Private key Signer Apr 22, 2003 Signature OK / not OK verification Verifier Mårten Trolin 6
Use of a digital signature Document Signature generation Document Signature Public key Private key Signer Apr 22, 2003 Signature OK / not OK verification Verifier Mårten Trolin 6
 Message Authentication Codes Digital signatures requires public/private keys l The same functionality can be achieved with symmetric keys l – Called MAC – Message Authentication Code – Signer and verifier uses the same key l Question: What are the advantages compared to digital signatures? What are the disadvantages? Apr 22, 2003 Mårten Trolin 7
Message Authentication Codes Digital signatures requires public/private keys l The same functionality can be achieved with symmetric keys l – Called MAC – Message Authentication Code – Signer and verifier uses the same key l Question: What are the advantages compared to digital signatures? What are the disadvantages? Apr 22, 2003 Mårten Trolin 7
 Two simple MACs Let Ekey, Dkey be a symmetric cipher, and let H be a hash function. Let m be the message to MAC and let k be the symmetric key. l First proposition: Compute a hash of the document and encrypt it l – Ek(H(m)) l Second proposition: Concatinate the message and the key and compute the hash – H(m k) Apr 22, 2003 Mårten Trolin 8
Two simple MACs Let Ekey, Dkey be a symmetric cipher, and let H be a hash function. Let m be the message to MAC and let k be the symmetric key. l First proposition: Compute a hash of the document and encrypt it l – Ek(H(m)) l Second proposition: Concatinate the message and the key and compute the hash – H(m k) Apr 22, 2003 Mårten Trolin 8
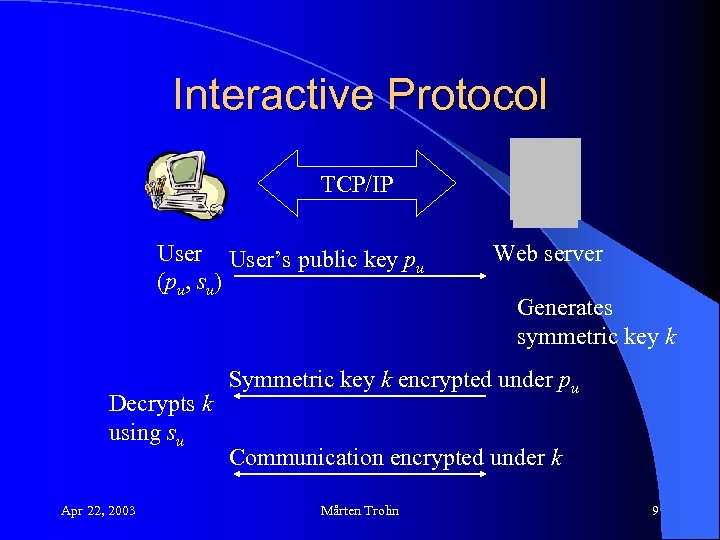 Interactive Protocol TCP/IP User’s public key p u (pu, su) Decrypts k using su Apr 22, 2003 Web server Generates symmetric key k Symmetric key k encrypted under pu Communication encrypted under k Mårten Trolin 9
Interactive Protocol TCP/IP User’s public key p u (pu, su) Decrypts k using su Apr 22, 2003 Web server Generates symmetric key k Symmetric key k encrypted under pu Communication encrypted under k Mårten Trolin 9
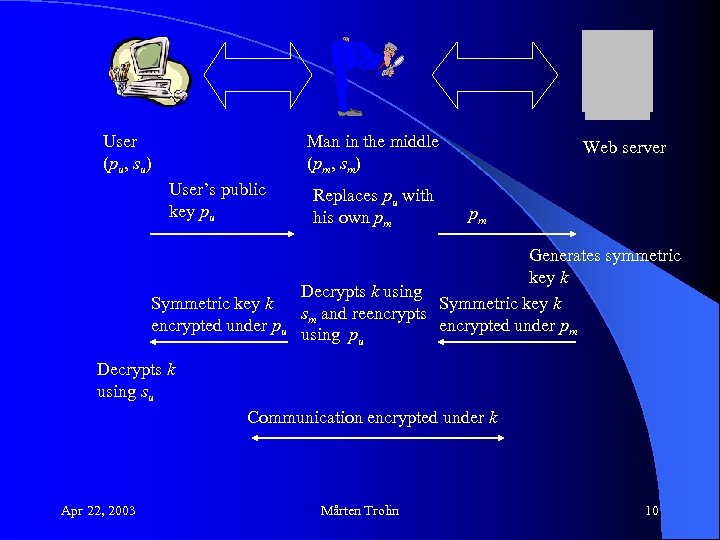 User (pu, su) Man in the middle (pm, sm) User’s public key pu Symmetric key k encrypted under pu Replaces pu with his own pm Web server pm Generates symmetric key k Decrypts k using Symmetric key k sm and reencrypts encrypted under pm using pu Decrypts k using su Communication encrypted under k Apr 22, 2003 Mårten Trolin 10
User (pu, su) Man in the middle (pm, sm) User’s public key pu Symmetric key k encrypted under pu Replaces pu with his own pm Web server pm Generates symmetric key k Decrypts k using Symmetric key k sm and reencrypts encrypted under pm using pu Decrypts k using su Communication encrypted under k Apr 22, 2003 Mårten Trolin 10
 Public key certificates l A public key certificate consists of – A public key – Information on the owner l Name, address, photograph, finger-print, credit card number, etc. – A signature on the above data by a trusted party l Trusted party could be the government, a bank, etc. Public information User’s public key Private information User’s Private key Apr 22, 2003 Identification data Mårten Trolin Digital signature by CA 11
Public key certificates l A public key certificate consists of – A public key – Information on the owner l Name, address, photograph, finger-print, credit card number, etc. – A signature on the above data by a trusted party l Trusted party could be the government, a bank, etc. Public information User’s public key Private information User’s Private key Apr 22, 2003 Identification data Mårten Trolin Digital signature by CA 11
 Certificate chains l Certificates can be chained – Each certificate in the chain is signed with the private key of the certificate above. If the user knows the root certificate, he can verify that each step is valid. l Using chains, the CA can outsource signing to other organizations it trusts without giving away its private key. l Apr 22, 2003 Mårten Trolin 12
Certificate chains l Certificates can be chained – Each certificate in the chain is signed with the private key of the certificate above. If the user knows the root certificate, he can verify that each step is valid. l Using chains, the CA can outsource signing to other organizations it trusts without giving away its private key. l Apr 22, 2003 Mårten Trolin 12
 Certificate chains l The end user certificates are verified by following the chain up to the root certificate authority (CA) – If every step in the chain is valid, the end user certificate is considered valid. Apr 22, 2003 Mårten Trolin 13
Certificate chains l The end user certificates are verified by following the chain up to the root certificate authority (CA) – If every step in the chain is valid, the end user certificate is considered valid. Apr 22, 2003 Mårten Trolin 13
 SSL/TLS l SSL (Secure Socket Layer) and TLS (Transport Layer Security) are standards for how to secure TCP/IP communications l TLS is a layer on top of the TCP layer Apr 22, 2003 Mårten Trolin 14
SSL/TLS l SSL (Secure Socket Layer) and TLS (Transport Layer Security) are standards for how to secure TCP/IP communications l TLS is a layer on top of the TCP layer Apr 22, 2003 Mårten Trolin 14
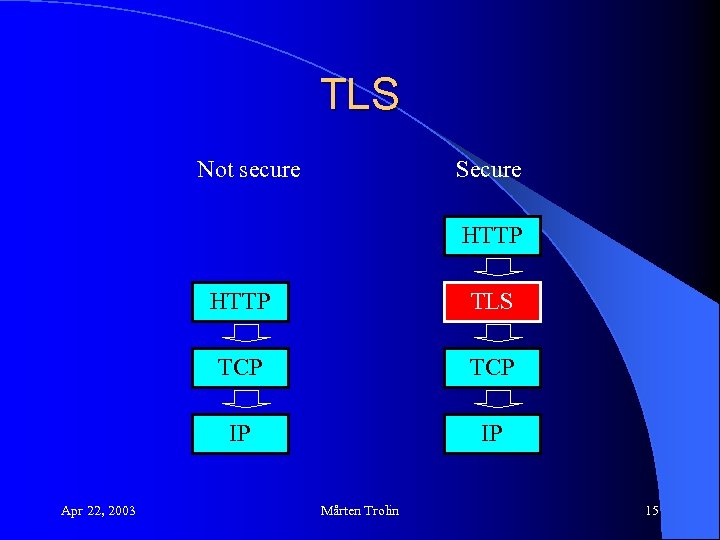 TLS Not secure Secure HTTP TCP IP Apr 22, 2003 TLS IP Mårten Trolin 15
TLS Not secure Secure HTTP TCP IP Apr 22, 2003 TLS IP Mårten Trolin 15
 TLS Handshake Client. Hello Server. Hello Certificate Server. Key. Exchange Server. Hello. Done Client. Key. Exchange Change. Cipher. Spec Finished Server Client Apr 22, 2003 Mårten Trolin 16
TLS Handshake Client. Hello Server. Hello Certificate Server. Key. Exchange Server. Hello. Done Client. Key. Exchange Change. Cipher. Spec Finished Server Client Apr 22, 2003 Mårten Trolin 16
 Non-interactive protocols l For interactive protocols, the symmetric key is decided in the handshake. For noninteractive protocols, this must be solved in another way. – The key cannot be negotiated. – Encrypt a session key using the recipients public key. Apr 22, 2003 Mårten Trolin 17
Non-interactive protocols l For interactive protocols, the symmetric key is decided in the handshake. For noninteractive protocols, this must be solved in another way. – The key cannot be negotiated. – Encrypt a session key using the recipients public key. Apr 22, 2003 Mårten Trolin 17
 Session key in non-interactive protocols For non-interactive protocols, the sender generates a session key. l The session key is encrypted using the recipient’s public key. l – Recipient’s public key must be known in advance. The message is encrypted with the (symmetric) session key. The encrypted message consists of the encrypted session key and the cipher text. l The recipient decrypts the session key with his private key and decrypts the message. l Apr 22, 2003 Mårten Trolin 18
Session key in non-interactive protocols For non-interactive protocols, the sender generates a session key. l The session key is encrypted using the recipient’s public key. l – Recipient’s public key must be known in advance. The message is encrypted with the (symmetric) session key. The encrypted message consists of the encrypted session key and the cipher text. l The recipient decrypts the session key with his private key and decrypts the message. l Apr 22, 2003 Mårten Trolin 18
 Pretty Good Privacy l Protocol overview – Symmetric session key encrypted with asymmetric key l Key management – Distributed, non-centralized l Trust model – Web of trust – Introducers Apr 22, 2003 Mårten Trolin 19
Pretty Good Privacy l Protocol overview – Symmetric session key encrypted with asymmetric key l Key management – Distributed, non-centralized l Trust model – Web of trust – Introducers Apr 22, 2003 Mårten Trolin 19
 Password generated keys – problems and solutions l Password generated keys suffer from the same general problem as passwords for authentication. – Number of passwords is relatively small – possible to create a list with all possible passwords and corresponding keys. Use a salt to avoid dictionary attacks. l Make key generation “slow”, to make brute-force attacks more time consuming. l Apr 22, 2003 Mårten Trolin 20
Password generated keys – problems and solutions l Password generated keys suffer from the same general problem as passwords for authentication. – Number of passwords is relatively small – possible to create a list with all possible passwords and corresponding keys. Use a salt to avoid dictionary attacks. l Make key generation “slow”, to make brute-force attacks more time consuming. l Apr 22, 2003 Mårten Trolin 20
 Generating keys l Key generation requires a good source of random bits – Bad key material makes system vulnerable to attacks. Has been done in practice. – Hardware generators provide the best source. – For end-user applications - some user interaction can be used (mouse movement, key strokes, etc. ) – Using system time for high security requirements is a bad idea! l For high-security applications, key generation should take place in a closed environment. Apr 22, 2003 Mårten Trolin 21
Generating keys l Key generation requires a good source of random bits – Bad key material makes system vulnerable to attacks. Has been done in practice. – Hardware generators provide the best source. – For end-user applications - some user interaction can be used (mouse movement, key strokes, etc. ) – Using system time for high security requirements is a bad idea! l For high-security applications, key generation should take place in a closed environment. Apr 22, 2003 Mårten Trolin 21
 Distributing symmetric keys Symmetric keys are very sensitive and must be distributed with great care. l Depending on how valueable the key is, different approaches are possible. l – Send the key to recipient by physically secure means, e. g. , by courier, by registered mail etc. – If a common key exists, send the new key encrypted under the common key. – Split the key into components and send the key components with different security officers. Apr 22, 2003 Mårten Trolin 22
Distributing symmetric keys Symmetric keys are very sensitive and must be distributed with great care. l Depending on how valueable the key is, different approaches are possible. l – Send the key to recipient by physically secure means, e. g. , by courier, by registered mail etc. – If a common key exists, send the new key encrypted under the common key. – Split the key into components and send the key components with different security officers. Apr 22, 2003 Mårten Trolin 22
 What Is a Smart-Card l. A smart-card is a small computer l Often placed on a credit-card sized plastic card l Can have contacts or be contact-less l Has a well-defined interface – Can have secret information that is protected from direct access l First Apr 22, 2003 appeared in the 1970 s Mårten Trolin 23
What Is a Smart-Card l. A smart-card is a small computer l Often placed on a credit-card sized plastic card l Can have contacts or be contact-less l Has a well-defined interface – Can have secret information that is protected from direct access l First Apr 22, 2003 appeared in the 1970 s Mårten Trolin 23
 Advantages with Smart-Cards l Can have secret data – Data used for internal computations and never revealed in clear – Example: PIN and keys can be stored on card l Can process data and save information – – Count transactions Check PIN and count unsuccessful tries Different behavior depending on geographic location Cryptographic functions l Apr 22, 2003 Uses the secret keys Mårten Trolin 24
Advantages with Smart-Cards l Can have secret data – Data used for internal computations and never revealed in clear – Example: PIN and keys can be stored on card l Can process data and save information – – Count transactions Check PIN and count unsuccessful tries Different behavior depending on geographic location Cryptographic functions l Apr 22, 2003 Uses the secret keys Mårten Trolin 24


