6528c992a9cd48a3458ef227da95a921.ppt
- Количество слайдов: 58
 Advances in Network Security Case Study: Intrusion Detection Max Lakshtanov Comp 529 T 7 -10 1
Advances in Network Security Case Study: Intrusion Detection Max Lakshtanov Comp 529 T 7 -10 1
 Intrusion Detection n Introduction and Background n Overview of Mobile Agents n Mobile Agents VS. Intruders n Other Intrusion Detection Techniques n Conclusion n Questions 2
Intrusion Detection n Introduction and Background n Overview of Mobile Agents n Mobile Agents VS. Intruders n Other Intrusion Detection Techniques n Conclusion n Questions 2
 Network Security: preventive and reactive n Preventive approach: n Prevent intrusions from occurring n User authentication – logins and passwords n Firewalls – filter network traffic n Reactive approach: n Intrusion Detection System (IDS) n How to detect intrusions n How to respond 3
Network Security: preventive and reactive n Preventive approach: n Prevent intrusions from occurring n User authentication – logins and passwords n Firewalls – filter network traffic n Reactive approach: n Intrusion Detection System (IDS) n How to detect intrusions n How to respond 3
 Firewalls Firewall is a security device that allows limited access out of and into one’s network from the Internet n Piece of hardware connected to a network for protection n Only permits approved traffic in and out of one’s local site n Allows administrator to select applicable services necessary to one’s business and screens out the rest n 4
Firewalls Firewall is a security device that allows limited access out of and into one’s network from the Internet n Piece of hardware connected to a network for protection n Only permits approved traffic in and out of one’s local site n Allows administrator to select applicable services necessary to one’s business and screens out the rest n 4
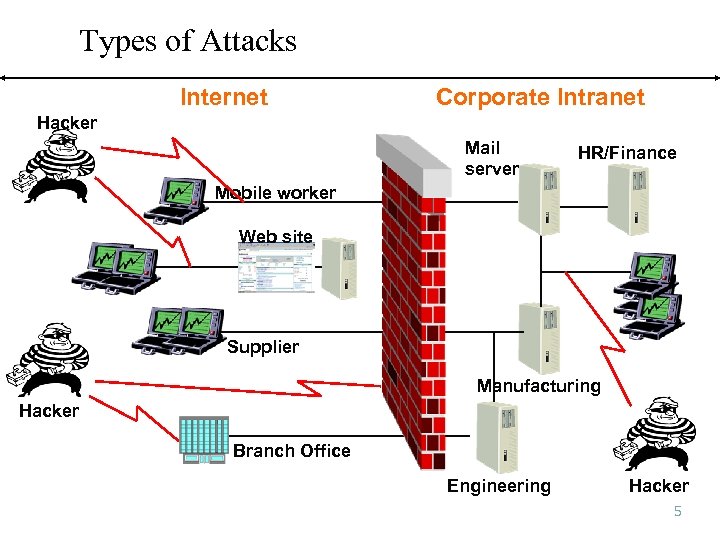 Types of Attacks Internet Corporate Intranet Hacker Mail server HR/Finance Mobile worker Web site Supplier Manufacturing Hacker Branch Office Engineering Hacker 5
Types of Attacks Internet Corporate Intranet Hacker Mail server HR/Finance Mobile worker Web site Supplier Manufacturing Hacker Branch Office Engineering Hacker 5
 Why firewalls are not enough? Not all access to the Internet occurs through the firewalls n Not all threats originate from outside the firewall n Firewalls are subject to attack themselves n Little protection against data-driven attacks (i. e. virus-infected programs or data files, as well as malicious Java applets and Active. X controls) n 6
Why firewalls are not enough? Not all access to the Internet occurs through the firewalls n Not all threats originate from outside the firewall n Firewalls are subject to attack themselves n Little protection against data-driven attacks (i. e. virus-infected programs or data files, as well as malicious Java applets and Active. X controls) n 6
 What is an Intrusion Detection System? Concept established in 1980 by J. P. Anderson n Abbreviated as IDS, it is a defense system, which detects hostile activities in a network n IDS complements firewalls by allowing a higher level of analysis of traffic on a network, and by monitoring its behavior of the sessions on the servers n Helps computer and network systems prepare for and deal with an attack n 7
What is an Intrusion Detection System? Concept established in 1980 by J. P. Anderson n Abbreviated as IDS, it is a defense system, which detects hostile activities in a network n IDS complements firewalls by allowing a higher level of analysis of traffic on a network, and by monitoring its behavior of the sessions on the servers n Helps computer and network systems prepare for and deal with an attack n 7
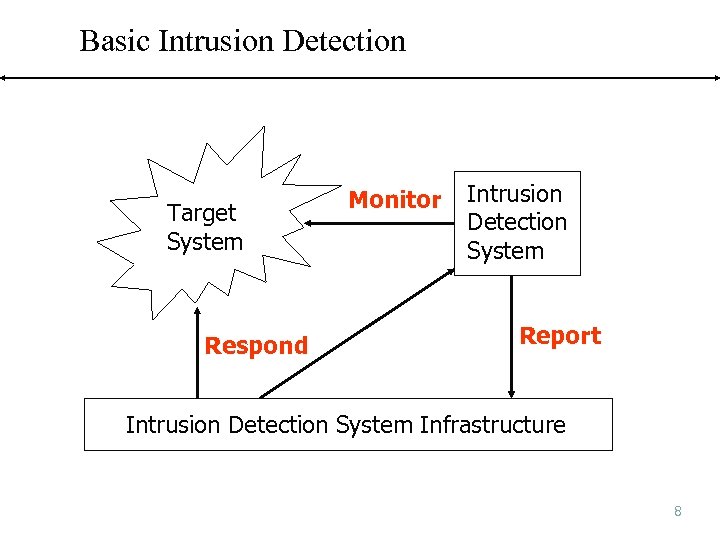 Basic Intrusion Detection Target System Respond Monitor Intrusion Detection System Report Intrusion Detection System Infrastructure 8
Basic Intrusion Detection Target System Respond Monitor Intrusion Detection System Report Intrusion Detection System Infrastructure 8
 Desirable characteristics Run continually n Fault tolerant n Resist subversion n Minimal overhead n Configurable n Adaptable n Scalable n Provide graceful degradation of service n Allow dynamic reconfiguration n 9
Desirable characteristics Run continually n Fault tolerant n Resist subversion n Minimal overhead n Configurable n Adaptable n Scalable n Provide graceful degradation of service n Allow dynamic reconfiguration n 9
 What does an IDS do? IDS inspects all inbound and outbound network activity and identifies suspicious patterns that may indicate a network or system attack n In a passive system, the IDS detects a potential security breach, logs the information and signals an alert n In a reactive system, the IDS logs off a user or reprograms the firewall to block network traffic from the suspected malicious source n 10
What does an IDS do? IDS inspects all inbound and outbound network activity and identifies suspicious patterns that may indicate a network or system attack n In a passive system, the IDS detects a potential security breach, logs the information and signals an alert n In a reactive system, the IDS logs off a user or reprograms the firewall to block network traffic from the suspected malicious source n 10
 First major type of IDS n Host based IDS n loaded n make n on each protected asset use of system resources disk space, RAM, CPU time n detect host-related activity n analyze operating system, application, and system audit trails n can be self-contained or remotely managed n some attacks cannot be detected at a single location 11
First major type of IDS n Host based IDS n loaded n make n on each protected asset use of system resources disk space, RAM, CPU time n detect host-related activity n analyze operating system, application, and system audit trails n can be self-contained or remotely managed n some attacks cannot be detected at a single location 11
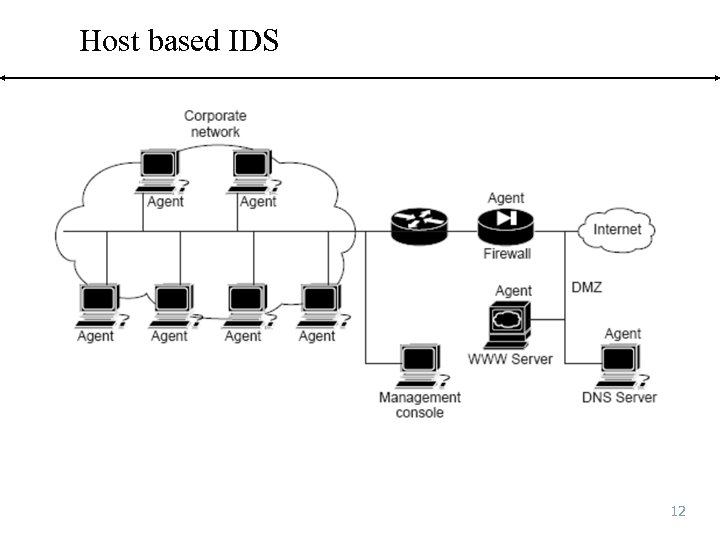 Host based IDS 12
Host based IDS 12
 Second major type of IDS n Network based IDS n monitor n usually activity on a specific network segment dedicated platforms with two components: n Sensor – passively analyzes network traffic n Management system n displays alarm information n configure the sensors n perform n high rules-based or expert system analysis network load scalability problems n problems with encrypted communication 13
Second major type of IDS n Network based IDS n monitor n usually activity on a specific network segment dedicated platforms with two components: n Sensor – passively analyzes network traffic n Management system n displays alarm information n configure the sensors n perform n high rules-based or expert system analysis network load scalability problems n problems with encrypted communication 13
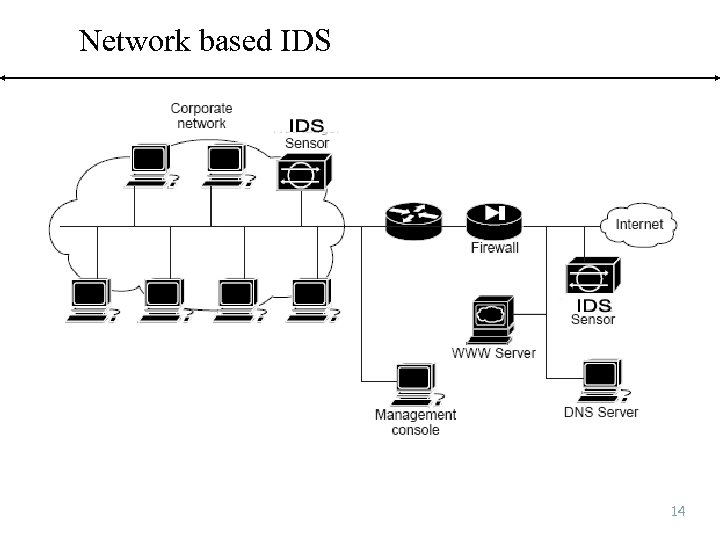 Network based IDS 14
Network based IDS 14
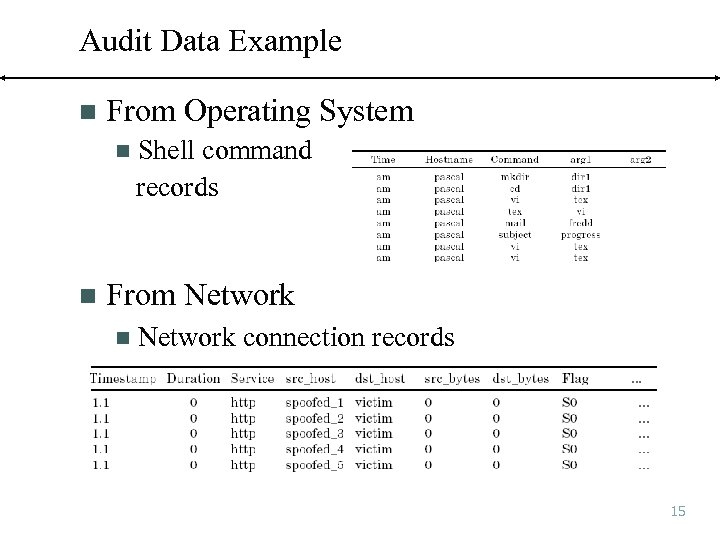 Audit Data Example n From Operating System n n Shell command records From Network n Network connection records 15
Audit Data Example n From Operating System n n Shell command records From Network n Network connection records 15
 What are False Positives? n n Occur when the system classifies an action as a possible intrusion when it is a legitimate action Any alert that was triggered incorrectly n alerts about telnet connections that are legitimate Common Causes n Abnormal traffic patterns n Too much traffic (High Bandwidth Connections) n Incorrectly configured software Results n Tend to clutter up the displays n Attacker may use this to cause Do. S attacks using auto responses 16
What are False Positives? n n Occur when the system classifies an action as a possible intrusion when it is a legitimate action Any alert that was triggered incorrectly n alerts about telnet connections that are legitimate Common Causes n Abnormal traffic patterns n Too much traffic (High Bandwidth Connections) n Incorrectly configured software Results n Tend to clutter up the displays n Attacker may use this to cause Do. S attacks using auto responses 16
 Analysis Techniques n Misuse Detection predetermined knowledge base n high levels of detection accuracy n minimal number of false positives n n Problems relies heavily on the thorough and correct construction of this knowledge base n variations of known attacks n intrusions not in knowledge base n traditionally requires human domain experts n 17
Analysis Techniques n Misuse Detection predetermined knowledge base n high levels of detection accuracy n minimal number of false positives n n Problems relies heavily on the thorough and correct construction of this knowledge base n variations of known attacks n intrusions not in knowledge base n traditionally requires human domain experts n 17
 Analysis Techniques n Anomaly Detection events unlike normal system behavior n variety of techniques including n n statistical modeling n neural networks n hidden Markov models baseline model that represents normal system behavior against which anomalous events can be distinguished n threshold of the range of normal behavior n 18
Analysis Techniques n Anomaly Detection events unlike normal system behavior n variety of techniques including n n statistical modeling n neural networks n hidden Markov models baseline model that represents normal system behavior against which anomalous events can be distinguished n threshold of the range of normal behavior n 18
 Anomaly Detection n Advantages ability to identify new and previously unseen attacks n automated, do not require expert knowledge of computer attacks n n Problems attacks that resemble normal behavior n higher numbers of false positives n n all anomalous events assumed to be intrusive n false positive if implementation errors 19
Anomaly Detection n Advantages ability to identify new and previously unseen attacks n automated, do not require expert knowledge of computer attacks n n Problems attacks that resemble normal behavior n higher numbers of false positives n n all anomalous events assumed to be intrusive n false positive if implementation errors 19
 Unrealistic Expectations n n n They are not silver bullets for security They can not compensate for weak identification and authentication mechanisms They can not conduct investigations of attacks without human intervention They can not compensate for weakness in network protocols, applications, systems, …. They can not analyze all of the traffic on a network They can not always deal with problems involving packet-level attacks 20
Unrealistic Expectations n n n They are not silver bullets for security They can not compensate for weak identification and authentication mechanisms They can not conduct investigations of attacks without human intervention They can not compensate for weakness in network protocols, applications, systems, …. They can not analyze all of the traffic on a network They can not always deal with problems involving packet-level attacks 20
 Problems of existing monolithic IDS n Central data collection and analysis n Single point of failure n Network traffic n Computational workload n Ad Hoc Networks n Possibility of distributed, coordinated attacks n Lack of common vocabulary or standards 21
Problems of existing monolithic IDS n Central data collection and analysis n Single point of failure n Network traffic n Computational workload n Ad Hoc Networks n Possibility of distributed, coordinated attacks n Lack of common vocabulary or standards 21
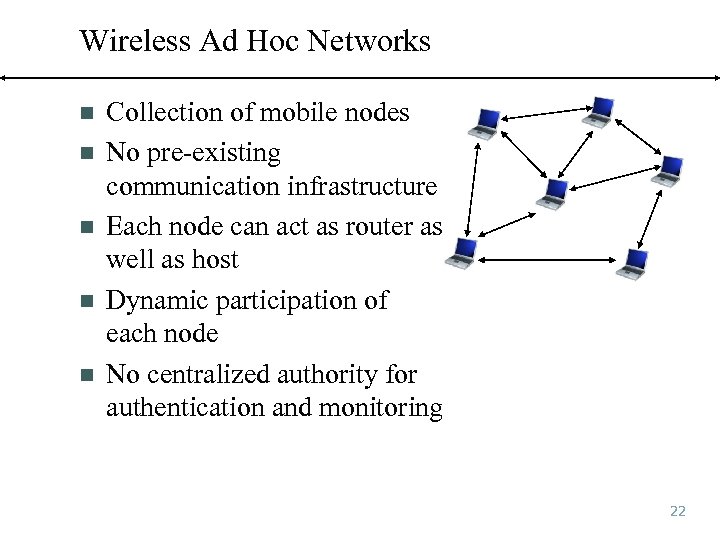 Wireless Ad Hoc Networks n n n Collection of mobile nodes No pre-existing communication infrastructure Each node can act as router as well as host Dynamic participation of each node No centralized authority for authentication and monitoring 22
Wireless Ad Hoc Networks n n n Collection of mobile nodes No pre-existing communication infrastructure Each node can act as router as well as host Dynamic participation of each node No centralized authority for authentication and monitoring 22
 Vulnerabilities of ad hoc networks n n Wireless communication (open media) Cooperation among nodes is necessary (lack of centralized author. ) Don’t rely on existing infrastructure Have many operational limitations: n n n Transmission Range and Bandwidth Energy, CPU, and Memory Autonomous units capable of roaming independently n n easily captured and compromised without physical protection very expensive and not scalable if physically protected 23
Vulnerabilities of ad hoc networks n n Wireless communication (open media) Cooperation among nodes is necessary (lack of centralized author. ) Don’t rely on existing infrastructure Have many operational limitations: n n n Transmission Range and Bandwidth Energy, CPU, and Memory Autonomous units capable of roaming independently n n easily captured and compromised without physical protection very expensive and not scalable if physically protected 23
 Vulnerabilities of ad hoc networks n n Usually used in situations where rapid deployment is necessary Usually deployed in hostile (not physically protected) places Dynamic topology change (due to mobility) Lack of key concentration points (e. g. switches and routers) n n No firewalls or gateways Difficult to distribute and update signatures (detection database) 24
Vulnerabilities of ad hoc networks n n Usually used in situations where rapid deployment is necessary Usually deployed in hostile (not physically protected) places Dynamic topology change (due to mobility) Lack of key concentration points (e. g. switches and routers) n n No firewalls or gateways Difficult to distribute and update signatures (detection database) 24
 ID Techniques n Mobile Agents n Haystack Algorithm n Indra n Detection at network layer n Multi-layer detection 25
ID Techniques n Mobile Agents n Haystack Algorithm n Indra n Detection at network layer n Multi-layer detection 25
 What are Mobile Agents? n n n executing programs that can migrate from machine to machine in a heterogeneous network under their own control correlate all suspicious events occurred in different monitored hosts may have these characteristics: n n n autonomous goal-driven reactive social adaptive mobile 26
What are Mobile Agents? n n n executing programs that can migrate from machine to machine in a heterogeneous network under their own control correlate all suspicious events occurred in different monitored hosts may have these characteristics: n n n autonomous goal-driven reactive social adaptive mobile 26
 Mobile Agent Characteristics n n n n can be programmed to satisfy one or more goals move independently from one device to another on a network generally serializable and persistent provide more accurate alarms dynamically increase/reduce the suspicion level of certain host or login user evade attackers can resurrect themselves if attacked 27
Mobile Agent Characteristics n n n n can be programmed to satisfy one or more goals move independently from one device to another on a network generally serializable and persistent provide more accurate alarms dynamically increase/reduce the suspicion level of certain host or login user evade attackers can resurrect themselves if attacked 27
 Components n Two Components Agent n Agent Platform n n The mobile agent contains code and state information needed for carrying out computation tasks on an agent platform 28
Components n Two Components Agent n Agent Platform n n The mobile agent contains code and state information needed for carrying out computation tasks on an agent platform 28
 Advantages of Mobile Agents n Reducing Network Load - move logic, not data n Overcoming Network Latency - agents operate directly on the host n Autonomous Execution - still function when portions of the IDS get destroyed or separated Platform Independence - inserts an OS independent layer between the hosts and the IDS using agents Dynamic Adaption - reconfigure at run-time n n n Upgradability - signature database and the detection algorithms are up-to-date n Scalability – reduce computational and network load 29
Advantages of Mobile Agents n Reducing Network Load - move logic, not data n Overcoming Network Latency - agents operate directly on the host n Autonomous Execution - still function when portions of the IDS get destroyed or separated Platform Independence - inserts an OS independent layer between the hosts and the IDS using agents Dynamic Adaption - reconfigure at run-time n n n Upgradability - signature database and the detection algorithms are up-to-date n Scalability – reduce computational and network load 29
 Problems of Mobile Agents n Security - several security implications that must be considered: n the host (and the agent platform) must be protected against malicious code n certificates, n agents can be modified/eavesdropped when they move over the network n encrypting n digital signatures agents mobile agents can be attacked by a malicious agent platform itself n difficult to fight when agents need unrestricted movement around the network 30
Problems of Mobile Agents n Security - several security implications that must be considered: n the host (and the agent platform) must be protected against malicious code n certificates, n agents can be modified/eavesdropped when they move over the network n encrypting n digital signatures agents mobile agents can be attacked by a malicious agent platform itself n difficult to fight when agents need unrestricted movement around the network 30
 Problems of Mobile Agents n Code Size n n n Complex piece of software Agents might get large Transferring agent’s code over the network takes time Only needed once, when hosts store agent code locally Performance n n n Often written in scripting or interpreted languages to be easily ported between different platforms. This mode of execution is very slow compared to native code. As an IDS has to process a large amount of data under very demanding timing constraints (near real-time), the use of MAs could degrade its performance. 31
Problems of Mobile Agents n Code Size n n n Complex piece of software Agents might get large Transferring agent’s code over the network takes time Only needed once, when hosts store agent code locally Performance n n n Often written in scripting or interpreted languages to be easily ported between different platforms. This mode of execution is very slow compared to native code. As an IDS has to process a large amount of data under very demanding timing constraints (near real-time), the use of MAs could degrade its performance. 31
 IDSs using agents n Autonomous Agents For Intrusion Detection (AAFID) at Purdue n Local Intrusion Detection System (LIDS) n Mobile Agent Intrusion Detection Systems (MAIDS) n Intrusion Detection Agent System (IDA) at IPA, Japan 32
IDSs using agents n Autonomous Agents For Intrusion Detection (AAFID) at Purdue n Local Intrusion Detection System (LIDS) n Mobile Agent Intrusion Detection Systems (MAIDS) n Intrusion Detection Agent System (IDA) at IPA, Japan 32
 MA Systems - AAFID: Autonomous Agents for Intrusion Detection 33
MA Systems - AAFID: Autonomous Agents for Intrusion Detection 33
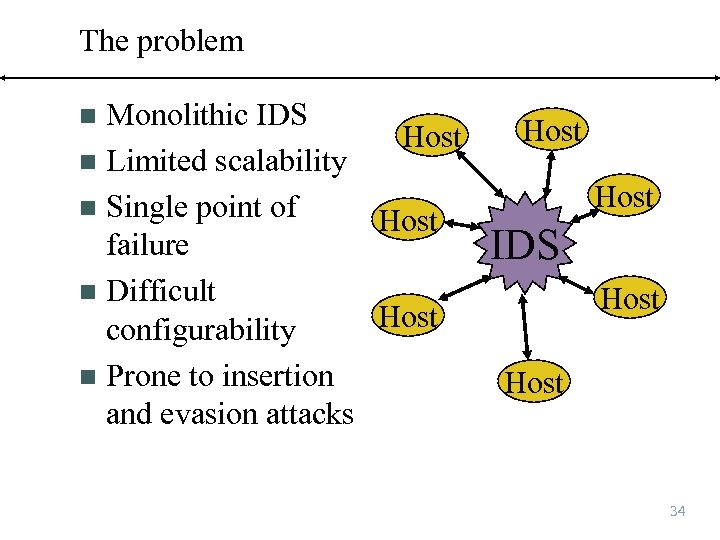 The problem Monolithic IDS Host n Limited scalability n Single point of Host failure n Difficult Host configurability n Prone to insertion and evasion attacks n Host IDS Host 34
The problem Monolithic IDS Host n Limited scalability n Single point of Host failure n Difficult Host configurability n Prone to insertion and evasion attacks n Host IDS Host 34
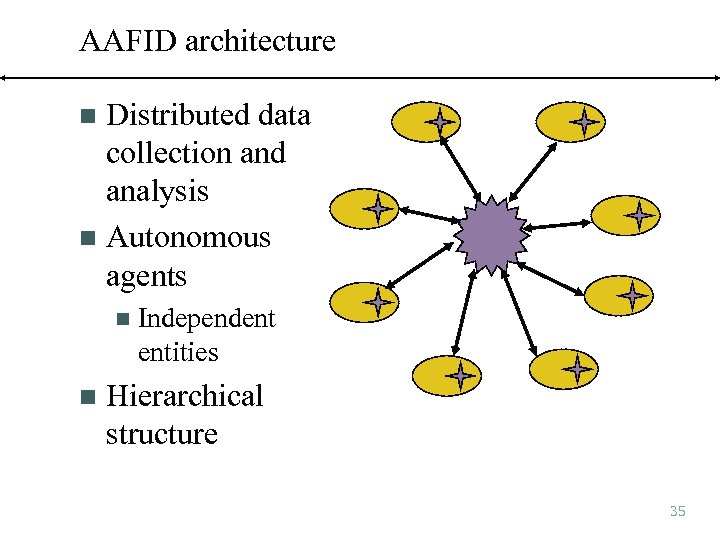 AAFID architecture Distributed data collection and analysis n Autonomous agents n n n Independent entities Hierarchical structure 35
AAFID architecture Distributed data collection and analysis n Autonomous agents n n n Independent entities Hierarchical structure 35
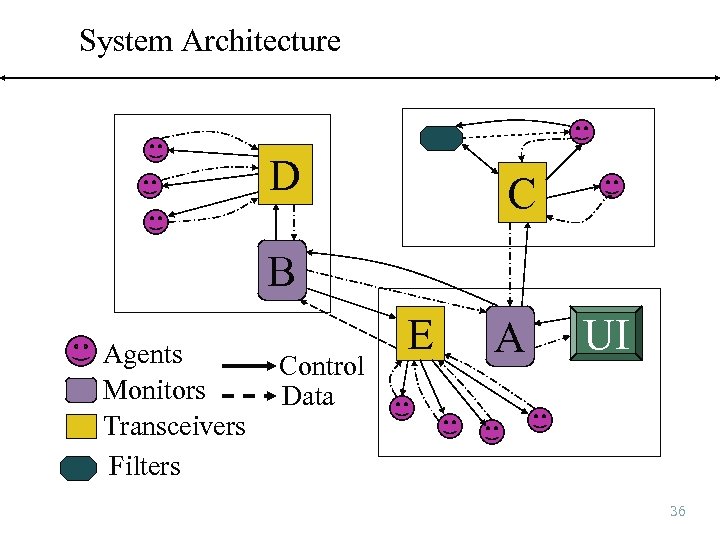 System Architecture D C B Agents Monitors Transceivers Filters Control Data E A UI 36
System Architecture D C B Agents Monitors Transceivers Filters Control Data E A UI 36
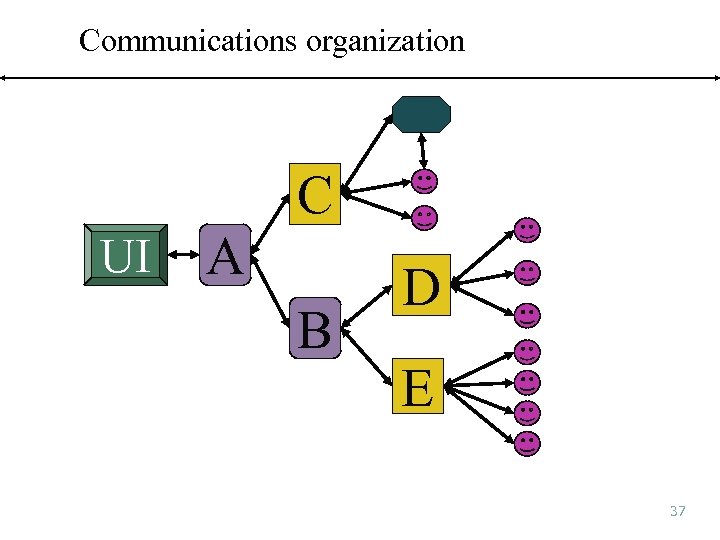 Communications organization C UI A B D E 37
Communications organization C UI A B D E 37
 What is an Agent? n Independently-running entity n Usually a separate process or thread Can keep state n May perform arbitrary actions n n n Can be very simple or very complex May exchange data with other entities 38
What is an Agent? n Independently-running entity n Usually a separate process or thread Can keep state n May perform arbitrary actions n n n Can be very simple or very complex May exchange data with other entities 38
 What is a Transceiver? Communications backbone for a host n Handles all the agents in a host n May do processing on data received from agents n Interacts with a monitor n 39
What is a Transceiver? Communications backbone for a host n Handles all the agents in a host n May do processing on data received from agents n Interacts with a monitor n 39
 What is a Monitor? Highest level entity n Main control and data processing entity n Handles one or more transceivers n Can control other monitors n Can be connected hierarchically to other monitors n May interact with a user interface n 40
What is a Monitor? Highest level entity n Main control and data processing entity n Handles one or more transceivers n Can control other monitors n Can be connected hierarchically to other monitors n May interact with a user interface n 40
 What is a Filter? n Platform and OS specific entity n Extract necessary data providing hardware and OS abstraction layer n Subscription-based mechanism n Allows for increased portability of agents 41
What is a Filter? n Platform and OS specific entity n Extract necessary data providing hardware and OS abstraction layer n Subscription-based mechanism n Allows for increased portability of agents 41
 AAFID 2 prototype Road-test the architecture n Focus on usability and flexibility n Run-time distribution of code n Little focus on performance n Provides infrastructure for development n Uses pipes and TCP for communication n Implemented in Perl 5 n n Easy portability, easy to install and run it 42
AAFID 2 prototype Road-test the architecture n Focus on usability and flexibility n Run-time distribution of code n Little focus on performance n Provides infrastructure for development n Uses pipes and TCP for communication n Implemented in Perl 5 n n Easy portability, easy to install and run it 42
 Development support APIs for development of Agents and Filters n Code generation tool for agents already exists n The APIs implement generic behavior, so implementers only need to add specific functionality. n 43
Development support APIs for development of Agents and Filters n Code generation tool for agents already exists n The APIs implement generic behavior, so implementers only need to add specific functionality. n 43
 Graphical User Interface Very simple support for starting and controlling entities n Implemented in Perl/Tk n n Current status: Prototype distributed to the public n ftp: //coast. cs. purdue. edu/pub/coast/AAFID/ n http: //www. cs. purdue. edu/coast/projects/auto nomous-agents. html 44
Graphical User Interface Very simple support for starting and controlling entities n Implemented in Perl/Tk n n Current status: Prototype distributed to the public n ftp: //coast. cs. purdue. edu/pub/coast/AAFID/ n http: //www. cs. purdue. edu/coast/projects/auto nomous-agents. html 44
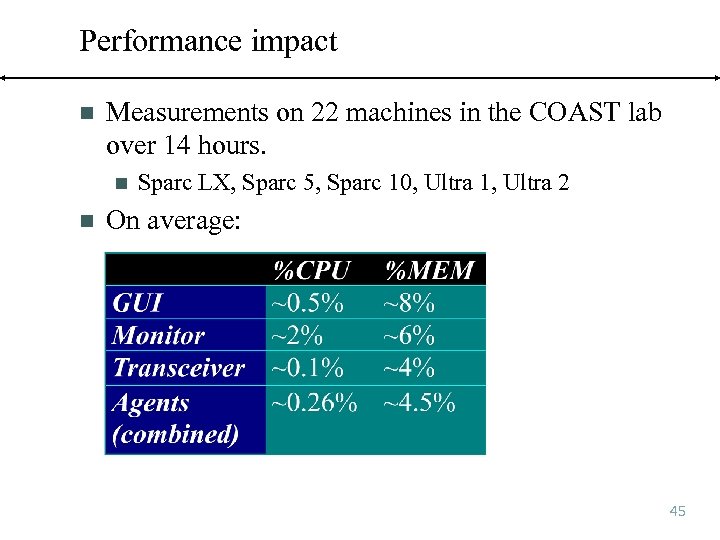 Performance impact n Measurements on 22 machines in the COAST lab over 14 hours. n n Sparc LX, Sparc 5, Sparc 10, Ultra 1, Ultra 2 On average: 45
Performance impact n Measurements on 22 machines in the COAST lab over 14 hours. n n Sparc LX, Sparc 5, Sparc 10, Ultra 1, Ultra 2 On average: 45
 Detection ARP cache poisoning n Writable user and configuration files n Suspicious sequences of commands n Accesses to network services n Health of system services n Repeated login failures n Configuration problems in ftp and www servers n 46
Detection ARP cache poisoning n Writable user and configuration files n Suspicious sequences of commands n Accesses to network services n Health of system services n Repeated login failures n Configuration problems in ftp and www servers n 46
 Benefits of AAFID Graceful degradation of service n Scalability n Easier to modify configuration n Information can be collected at the end host n Can combine host-based and networkbased approaches to intrusion detection n 47
Benefits of AAFID Graceful degradation of service n Scalability n Easier to modify configuration n Information can be collected at the end host n Can combine host-based and networkbased approaches to intrusion detection n 47
 Drawbacks of AAFID n Monitors may still be single points of failure n n n Ensure consistent information among redundant monitors Detection of intrusions at monitor level delayed until all information reaches the monitor Difficult to keep global state Data reduction is not implemented correctly n n Solution: Hierarchical structure, redundancy Still creates a lot of network traffic More difficult to do failure tolerance 48
Drawbacks of AAFID n Monitors may still be single points of failure n n n Ensure consistent information among redundant monitors Detection of intrusions at monitor level delayed until all information reaches the monitor Difficult to keep global state Data reduction is not implemented correctly n n Solution: Hierarchical structure, redundancy Still creates a lot of network traffic More difficult to do failure tolerance 48
 MA Systems - LIDS: Local Intrusion Detection System 49
MA Systems - LIDS: Local Intrusion Detection System 49
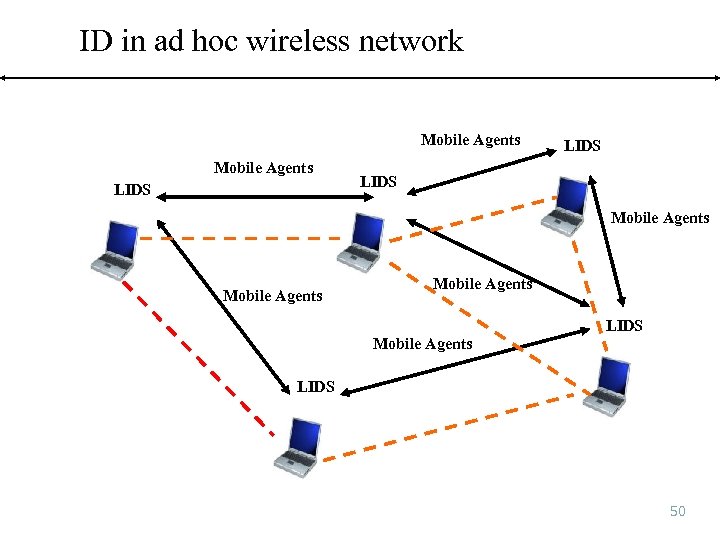 ID in ad hoc wireless network Mobile Agents LIDS Mobile Agents LIDS 50
ID in ad hoc wireless network Mobile Agents LIDS Mobile Agents LIDS 50
 Features of LIDS Reliable n Flexible n Behavior based n Blackboard-based architecture n Controlled by autonomous agents n Learning and adapting capability n Low maintenance cost n Uses building blocks of computational intelligence as intrusion analyzer n Low rate of false positives n 51
Features of LIDS Reliable n Flexible n Behavior based n Blackboard-based architecture n Controlled by autonomous agents n Learning and adapting capability n Low maintenance cost n Uses building blocks of computational intelligence as intrusion analyzer n Low rate of false positives n 51
 ID Systems Other intrusion detection techniques 52
ID Systems Other intrusion detection techniques 52
 Haystack Algorithm Host-based system n A statistical anomaly detection algorithm n Requires a designated node to act as a central administrator n Uses audit trail generated from host n Analyzes users’ session vectors n Weight-scoring with threshold vectors n Able to detect several types of intrusions n 53
Haystack Algorithm Host-based system n A statistical anomaly detection algorithm n Requires a designated node to act as a central administrator n Uses audit trail generated from host n Analyzes users’ session vectors n Weight-scoring with threshold vectors n Able to detect several types of intrusions n 53
 Indra - Intrusion Detection and Rapid Action A Peer-to-peer Approach n Makes use of cross-monitoring or “neighborhood watch” n Information on attempted attacks gathered by intended victims n Victim notify adjacent hosts on attack or peer nodes detect attack and sound alarm n Uses daemons n Web-of-trust model for certification of nodes n 54
Indra - Intrusion Detection and Rapid Action A Peer-to-peer Approach n Makes use of cross-monitoring or “neighborhood watch” n Information on attempted attacks gathered by intended victims n Victim notify adjacent hosts on attack or peer nodes detect attack and sound alarm n Uses daemons n Web-of-trust model for certification of nodes n 54
 Detection at network layer n Watchdog Verify that next node in path forwards packet n Listening in promiscuous mode n n Control Messages n n Adding two control messages to DSR protocol Neighborhood Watch Observing route protocol behavior n Listening to transmission of next node n Alarm messages n 55
Detection at network layer n Watchdog Verify that next node in path forwards packet n Listening in promiscuous mode n n Control Messages n n Adding two control messages to DSR protocol Neighborhood Watch Observing route protocol behavior n Listening to transmission of next node n Alarm messages n 55
 Multi-layer IDS (m. IDS) Detection on one layer can be initiated or aided by evidence from other layers. n Aggregation of evidence allows a more informed decision n Improved performance – higher true positive and lower false positive rates n 56
Multi-layer IDS (m. IDS) Detection on one layer can be initiated or aided by evidence from other layers. n Aggregation of evidence allows a more informed decision n Improved performance – higher true positive and lower false positive rates n 56
 Conclusion n Ø Ø Ø Ø Ø Mobile Agent Benefits Run continually Fault tolerant Resist subversion Minimal overhead Configurable Adaptable Scalable Provide graceful degradation of service Allow dynamic reconfiguration 57
Conclusion n Ø Ø Ø Ø Ø Mobile Agent Benefits Run continually Fault tolerant Resist subversion Minimal overhead Configurable Adaptable Scalable Provide graceful degradation of service Allow dynamic reconfiguration 57
 Questions & Answers Mobile Agents For Intrusion Detection 58
Questions & Answers Mobile Agents For Intrusion Detection 58


