480a264fecaa516ffc110cc2ea7e9bc0.ppt
- Количество слайдов: 29
 Advanced Intrusion Defense Joel Snyder Opus One jms@opus 1. com
Advanced Intrusion Defense Joel Snyder Opus One jms@opus 1. com
 Traditional perimeter technology is being… … Supplemented?
Traditional perimeter technology is being… … Supplemented?
 A firewall is not just a firewall anymore l Firewalls now have “advanced application intelligence” • Actually, they had that already, but the marketroids had to keep themselves busy. l Firewalls now are “intrusion prevention systems” • Isn’t every firewall an intrusion prevention system? l Firewalls now do virus scanning, content scanning, and ironing. l Application-layer firewalls are needed to protect legions of inadequate Web programmers.
A firewall is not just a firewall anymore l Firewalls now have “advanced application intelligence” • Actually, they had that already, but the marketroids had to keep themselves busy. l Firewalls now are “intrusion prevention systems” • Isn’t every firewall an intrusion prevention system? l Firewalls now do virus scanning, content scanning, and ironing. l Application-layer firewalls are needed to protect legions of inadequate Web programmers.
 A firewall is not just a firewall anymore, II l IDS has been replaced by IPS. • (No, I don’t believe that, I’m just repeating awful rumors. ) l Worms now outnumber viruses in your e-mail by a factor of 20 to 1. l Spam represents 50% to 75% of all e-mail you receive.
A firewall is not just a firewall anymore, II l IDS has been replaced by IPS. • (No, I don’t believe that, I’m just repeating awful rumors. ) l Worms now outnumber viruses in your e-mail by a factor of 20 to 1. l Spam represents 50% to 75% of all e-mail you receive.
 Key Question: Do you need this? l Do you need to buy (or upgrade) to a bigger, smarter, faster, l The answer you’ve been more capable firewall? waiting for… is on the l Do you need to buy an IPS? very next slide! l …an application layer firewall? l …a smarter IDS? l …an SSL VPN device? l Do I want an all-in-one thing? l Do I want individual parts?
Key Question: Do you need this? l Do you need to buy (or upgrade) to a bigger, smarter, faster, l The answer you’ve been more capable firewall? waiting for… is on the l Do you need to buy an IPS? very next slide! l …an application layer firewall? l …a smarter IDS? l …an SSL VPN device? l Do I want an all-in-one thing? l Do I want individual parts?
 Should I buy a lot of this new security stuff? And if I do buy this, what kind should I buy? And where should I put it? And which product should I buy? Answer: 42
Should I buy a lot of this new security stuff? And if I do buy this, what kind should I buy? And where should I put it? And which product should I buy? Answer: 42
 I can’t tell you what is right for your network l I can tell you what products are out there and what they are doing l But the hard work remains yours l I can also tell you what the trends are in these products So let’s look at what’s happening in the firewall business
I can’t tell you what is right for your network l I can tell you what products are out there and what they are doing l But the hard work remains yours l I can also tell you what the trends are in these products So let’s look at what’s happening in the firewall business
 March, 2004: Information Security sponsors research on new firewall technologies l Products from Check Point, Cyberguard, Net. Screen, Nortel Networks, Symantec, Secure Computing, Watchguard l Support from Andy Briney, Neil Roiter at Information Security http: //infosecuritymag. techtarget. com/
March, 2004: Information Security sponsors research on new firewall technologies l Products from Check Point, Cyberguard, Net. Screen, Nortel Networks, Symantec, Secure Computing, Watchguard l Support from Andy Briney, Neil Roiter at Information Security http: //infosecuritymag. techtarget. com/
![Firewalls have been around for a very long time “[AT&T’s gateway creates] a sort Firewalls have been around for a very long time “[AT&T’s gateway creates] a sort](https://present5.com/presentation/480a264fecaa516ffc110cc2ea7e9bc0/image-9.jpg) Firewalls have been around for a very long time “[AT&T’s gateway creates] a sort of crunchy shell around a soft, chewy center. ” (Bill Cheswick, Design of a Secure Internet Gateway, April, 1990) First firewalls deployed in Internet -connected organizations TIS toolkit commonly available “Firewalls and Internet Security” published Cisco buys PIX (Network Translation) Check. Point revenues cross $100 m Watch. Guard introduces 1 st FW appliance 1989 1991 1993 1995 1997 1999 2001 2003 2005
Firewalls have been around for a very long time “[AT&T’s gateway creates] a sort of crunchy shell around a soft, chewy center. ” (Bill Cheswick, Design of a Secure Internet Gateway, April, 1990) First firewalls deployed in Internet -connected organizations TIS toolkit commonly available “Firewalls and Internet Security” published Cisco buys PIX (Network Translation) Check. Point revenues cross $100 m Watch. Guard introduces 1 st FW appliance 1989 1991 1993 1995 1997 1999 2001 2003 2005
 Surely firewall makers have been busy since 1999? Clear market trends l Faster l Cheaper l Smaller • • New Guard: Net. Screen (Juniper), Watchguard, Sonic. WALL Old Guard: Cisco, Check Point Clear product trends l Add VPN features • • Site-to-site Remote Access (? ) l Add policy-based URL control • Websense-type l Add interfaces • No longer just inside, outside, DMZ
Surely firewall makers have been busy since 1999? Clear market trends l Faster l Cheaper l Smaller • • New Guard: Net. Screen (Juniper), Watchguard, Sonic. WALL Old Guard: Cisco, Check Point Clear product trends l Add VPN features • • Site-to-site Remote Access (? ) l Add policy-based URL control • Websense-type l Add interfaces • No longer just inside, outside, DMZ
 Shirley firewall makers have been busy since 1999? Clear market trends l Faster l Cheaper l Smaller • • New Guard: Net. Screen (Juniper), Watchguard, Sonic. WALL Old Guard: Cisco, Check Point Clear product trends l Add VPN features • • Site-to-site Remote Access (? ) l Add policy-based URL control • Websense-type l Add interfaces • No longer just inside, outside, DMZ
Shirley firewall makers have been busy since 1999? Clear market trends l Faster l Cheaper l Smaller • • New Guard: Net. Screen (Juniper), Watchguard, Sonic. WALL Old Guard: Cisco, Check Point Clear product trends l Add VPN features • • Site-to-site Remote Access (? ) l Add policy-based URL control • Websense-type l Add interfaces • No longer just inside, outside, DMZ
 Incremental improvements are not very exciting l Smaller, cheaper, faster: that’s great l VPNs, more interfaces: that’s great l But what have you done for me lately? l To answer that, we need to digress to the oldest battle in all of firewall-dom: proxy versus packet filter!
Incremental improvements are not very exciting l Smaller, cheaper, faster: that’s great l VPNs, more interfaces: that’s great l But what have you done for me lately? l To answer that, we need to digress to the oldest battle in all of firewall-dom: proxy versus packet filter!
 Arguments between Proxy and Stateful PF continued Proxy Stateful PF l More secure because you can look at application data stream l Faster to write l More secure because you have independent TCP stacks l Faster to run l Faster to adapt l Faster also means cheaper
Arguments between Proxy and Stateful PF continued Proxy Stateful PF l More secure because you can look at application data stream l Faster to write l More secure because you have independent TCP stacks l Faster to run l Faster to adapt l Faster also means cheaper
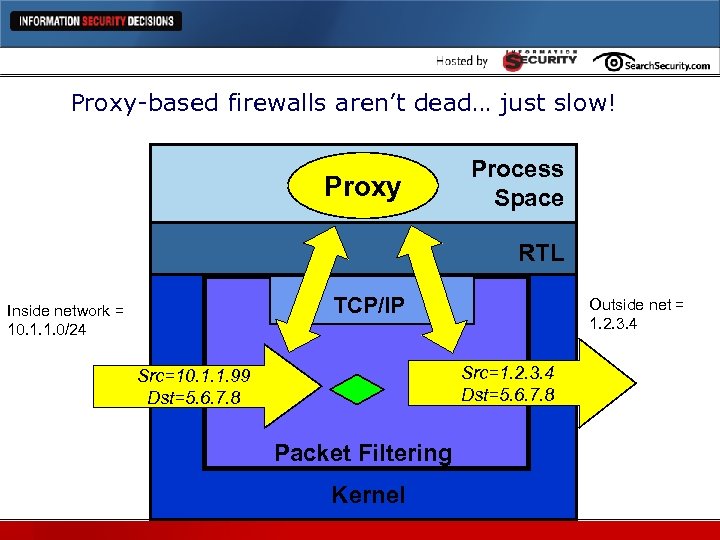 Proxy-based firewalls aren’t dead… just slow! Proxy Process Space RTL TCP/IP Inside network = 10. 1. 1. 0/24 Outside net = 1. 2. 3. 4 Src=1. 2. 3. 4 Dst=5. 6. 7. 8 Src=10. 1. 1. 99 Dst=5. 6. 7. 8 Packet Filtering Kernel
Proxy-based firewalls aren’t dead… just slow! Proxy Process Space RTL TCP/IP Inside network = 10. 1. 1. 0/24 Outside net = 1. 2. 3. 4 Src=1. 2. 3. 4 Dst=5. 6. 7. 8 Src=10. 1. 1. 99 Dst=5. 6. 7. 8 Packet Filtering Kernel
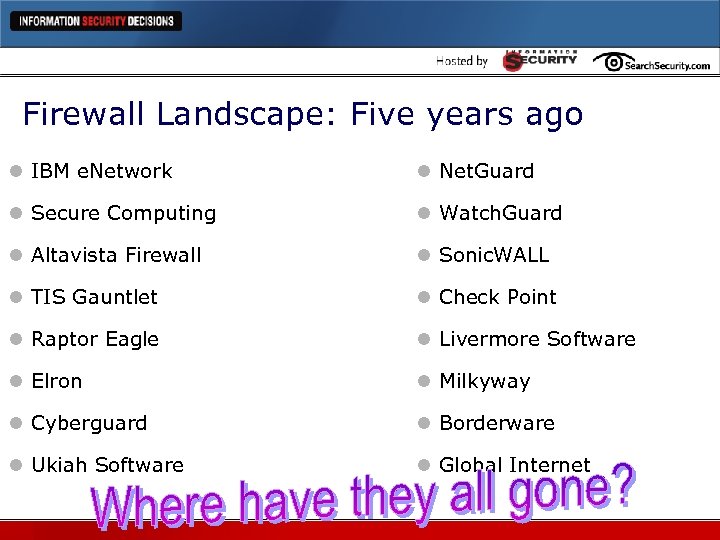 Firewall Landscape: Five years ago l IBM e. Network l Net. Guard l Secure Computing l Watch. Guard l Altavista Firewall l Sonic. WALL l TIS Gauntlet l Check Point l Raptor Eagle l Livermore Software l Elron l Milkyway l Cyberguard l Borderware l Ukiah Software l Global Internet
Firewall Landscape: Five years ago l IBM e. Network l Net. Guard l Secure Computing l Watch. Guard l Altavista Firewall l Sonic. WALL l TIS Gauntlet l Check Point l Raptor Eagle l Livermore Software l Elron l Milkyway l Cyberguard l Borderware l Ukiah Software l Global Internet
 Stateful Packet Filtering dominates the market Check Point Cisco Net. Screen Sonic. WALL Freeware-based products: Ipchains, IPF, Iptables, IPFW FW Newcomers: Fortinet, Toshiba, Ingate, Serv. Gate, many others IP Stateful Packet Filtering Kernel
Stateful Packet Filtering dominates the market Check Point Cisco Net. Screen Sonic. WALL Freeware-based products: Ipchains, IPF, Iptables, IPFW FW Newcomers: Fortinet, Toshiba, Ingate, Serv. Gate, many others IP Stateful Packet Filtering Kernel
 But, the core argument was never disputed l Proxy-based firewalls do have the possibility to give you more control because they maintain application-layer state information l The reality is that proxy-based firewalls rarely went very far down that path Why? Market demand, obviously…
But, the core argument was never disputed l Proxy-based firewalls do have the possibility to give you more control because they maintain application-layer state information l The reality is that proxy-based firewalls rarely went very far down that path Why? Market demand, obviously…
 Firewall Evolution: What we hoped for… l Additional granular controls on a wide variety of applications l Vastly improved centralized management systems l Intrusion detection and prevention functionality l More flexible deployment options
Firewall Evolution: What we hoped for… l Additional granular controls on a wide variety of applications l Vastly improved centralized management systems l Intrusion detection and prevention functionality l More flexible deployment options
 Firewall Evolution: What we found… l Additional granular controls on some a wide variety of applications l Limited intrusion detection and prevention functionality l Vastly improved centralized management systems l More flexible deployment options Why? Market demand, obviously…
Firewall Evolution: What we found… l Additional granular controls on some a wide variety of applications l Limited intrusion detection and prevention functionality l Vastly improved centralized management systems l More flexible deployment options Why? Market demand, obviously…
 Additional Granular Controls focused on a few applications l Everybody loves HTTP management • • Header filtering • Embedded Data blocking (Javascript) • Virus scanning, URL Filtering File type & MIME type blocking l Other applications are piecemeal • • FTP • • Vo. IP SMTP File Sharing
Additional Granular Controls focused on a few applications l Everybody loves HTTP management • • Header filtering • Embedded Data blocking (Javascript) • Virus scanning, URL Filtering File type & MIME type blocking l Other applications are piecemeal • • FTP • • Vo. IP SMTP File Sharing
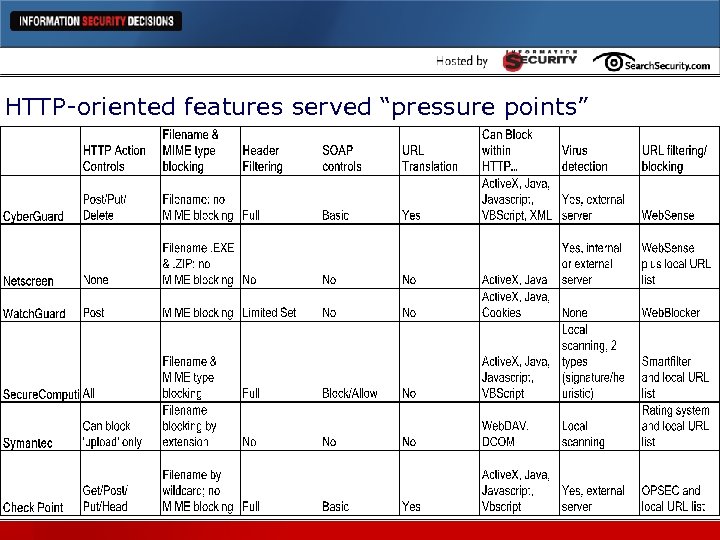 HTTP-oriented features served “pressure points”
HTTP-oriented features served “pressure points”
 Advanced Controls are diverse across products • Differentiating between “advanced” controls and “basic” controls was easy to do. • Proxy-based firewalls proved to be almost undistinguishable from their “insecure” stateful packet filtering brethren. • Vendors appear to be reactive, not proactive.
Advanced Controls are diverse across products • Differentiating between “advanced” controls and “basic” controls was easy to do. • Proxy-based firewalls proved to be almost undistinguishable from their “insecure” stateful packet filtering brethren. • Vendors appear to be reactive, not proactive.
 Virus Scans and Policy Controls are simple, right? l No! Some firewalls insisted on having virus and/or URL scanning happen “off box” l No! Some firewalls can’t configure where you scan for viruses l No! Some devices don’t have virus scanning l No! Some firewalls don’t support a local list of blocked URLs Conclusion: it’s not simple
Virus Scans and Policy Controls are simple, right? l No! Some firewalls insisted on having virus and/or URL scanning happen “off box” l No! Some firewalls can’t configure where you scan for viruses l No! Some devices don’t have virus scanning l No! Some firewalls don’t support a local list of blocked URLs Conclusion: it’s not simple
 We’ve learned how to write good GUIs, haven’t we? l Not in the firewall business, we haven’t l Additional granularity means additional thinking about resources l Products are … disappointing The firewall people have a lot to learn from the SSL VPN people
We’ve learned how to write good GUIs, haven’t we? l Not in the firewall business, we haven’t l Additional granularity means additional thinking about resources l Products are … disappointing The firewall people have a lot to learn from the SSL VPN people
 Centralized management has improved a bit l Folks who had it are doing slightly better than they were l Folks who didn’t have it now generally have something We’re still missing a general policy management system for firewalls Many of the centralized management tools have very rough edges
Centralized management has improved a bit l Folks who had it are doing slightly better than they were l Folks who didn’t have it now generally have something We’re still missing a general policy management system for firewalls Many of the centralized management tools have very rough edges
 “Intrusion” is the new buzzword in security Rate-based IPS technology l In firewalls, means “SYN flood protection” l May be smart (NS) l May include shunning (Sec. Comp, WG, CP) Content-based IPS technology l Based on IDS-style thinking l May have small signature base (NS, CP) l May be an “IDS with the IPS bit on” (Symantec)
“Intrusion” is the new buzzword in security Rate-based IPS technology l In firewalls, means “SYN flood protection” l May be smart (NS) l May include shunning (Sec. Comp, WG, CP) Content-based IPS technology l Based on IDS-style thinking l May have small signature base (NS, CP) l May be an “IDS with the IPS bit on” (Symantec)
 So what’s going on in the firewall business? l Products are diverging, not converging. l Personalities of products are distinct. l IPS is a step forward, but not challenging the world of standalone products. l Rate of change of established products is slow compared to new entries.
So what’s going on in the firewall business? l Products are diverging, not converging. l Personalities of products are distinct. l IPS is a step forward, but not challenging the world of standalone products. l Rate of change of established products is slow compared to new entries.
 What does this mean for me and my firewall? l Products are diverging l Personalities are distinct l IPS weaker than standalone l Change rate slow l Matching firewall to policy is hard; change in application or policy may mean changing product! l Aggressive adoption of new features unlikely in popular products; need new blood to overcome product inertia
What does this mean for me and my firewall? l Products are diverging l Personalities are distinct l IPS weaker than standalone l Change rate slow l Matching firewall to policy is hard; change in application or policy may mean changing product! l Aggressive adoption of new features unlikely in popular products; need new blood to overcome product inertia
 Advanced Intrusion Defense Joel Snyder Opus One jms@opus 1. com
Advanced Intrusion Defense Joel Snyder Opus One jms@opus 1. com


