 Advanced Cross Site Scripting Evil XSS Anton Rager Copyright© 2002 Avaya Inc. All rights reserved
Advanced Cross Site Scripting Evil XSS Anton Rager Copyright© 2002 Avaya Inc. All rights reserved
 Cross Site Scripting • 1 st Gen XSS was against public sites and ran against everyone that visited site – attacker uploads script content that everyone visiting page execs – Popups, redirects other annoyances – Relayed cookies to attacker • 2 nd Gen XSS focuses on sites that allow self-reflection XSS – User input modifies resulting page and can inject script commands into returned page (site search and echoed results) – Normally chained with a 1 st Gen attack on public site/email for site redirection with redirection URL forcing a XSS on 2 nd site – Cookies and other site-specific browser info leaked to attacker 2
Cross Site Scripting • 1 st Gen XSS was against public sites and ran against everyone that visited site – attacker uploads script content that everyone visiting page execs – Popups, redirects other annoyances – Relayed cookies to attacker • 2 nd Gen XSS focuses on sites that allow self-reflection XSS – User input modifies resulting page and can inject script commands into returned page (site search and echoed results) – Normally chained with a 1 st Gen attack on public site/email for site redirection with redirection URL forcing a XSS on 2 nd site – Cookies and other site-specific browser info leaked to attacker 2
 Cross Site Scripting • Types of information leakage – Client can reveal cookies to 3 rd party (session state, order info, etc) • http: //host/a. php? variable="> – Client can reveal posted form items to 3 rd party (user. ID/passwd, etc) •
Cross Site Scripting • Types of information leakage – Client can reveal cookies to 3 rd party (session state, order info, etc) • http: //host/a. php? variable="> – Client can reveal posted form items to 3 rd party (user. ID/passwd, etc) •
– Client can be tricked into accessing/posting spoofed info to trusted server • www. trustedserver. com/xss. asp? name =
3
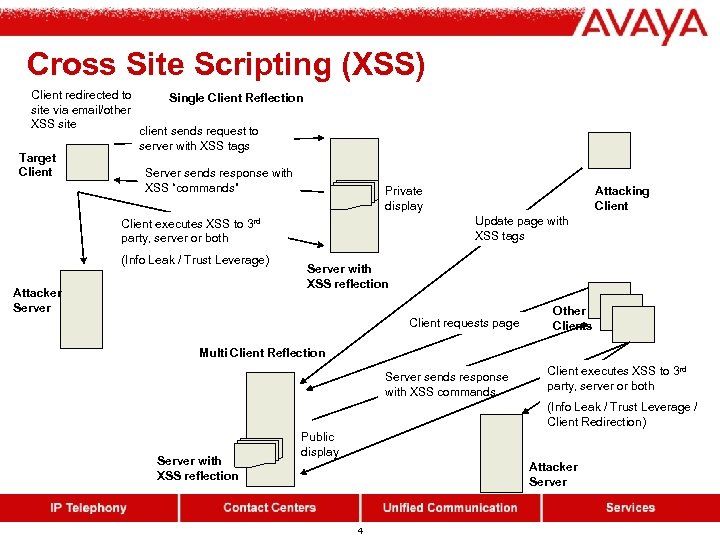 Cross Site Scripting (XSS) Client redirected to site via email/other XSS site Target Client Single Client Reflection client sends request to server with XSS tags Server sends response with XSS “commands” Private display Update page with XSS tags Client executes XSS to 3 rd party, server or both (Info Leak / Trust Leverage) Attacker Server Attacking Client Server with XSS reflection Client requests page Other Clients Multi Client Reflection Server sends response with XSS commands Client executes XSS to 3 rd party, server or both (Info Leak / Trust Leverage / Client Redirection) Server with XSS reflection Public display Attacker Server 4
Cross Site Scripting (XSS) Client redirected to site via email/other XSS site Target Client Single Client Reflection client sends request to server with XSS tags Server sends response with XSS “commands” Private display Update page with XSS tags Client executes XSS to 3 rd party, server or both (Info Leak / Trust Leverage) Attacker Server Attacking Client Server with XSS reflection Client requests page Other Clients Multi Client Reflection Server sends response with XSS commands Client executes XSS to 3 rd party, server or both (Info Leak / Trust Leverage / Client Redirection) Server with XSS reflection Public display Attacker Server 4
 Limitations of these attacks • Usually only get one transaction with XSS code against vulnerable site • Most attacks are only focused on collecting cookies • POST based forms are seldom leveraged – almost always use GET methods • Attacker does not know actual responses to client – Some experts recommend using POST, hidden form inputs and other session state info to limit XSS risks…. 5
Limitations of these attacks • Usually only get one transaction with XSS code against vulnerable site • Most attacks are only focused on collecting cookies • POST based forms are seldom leveraged – almost always use GET methods • Attacker does not know actual responses to client – Some experts recommend using POST, hidden form inputs and other session state info to limit XSS risks…. 5
 DOM Security Overview • Child Windows and same site trust • Scripts can interact between the two windows • Script content can be loaded from anywhere (RPC/Remote scripting is common) • Images can be loaded from anywhere • Javascript can either be within tags, loaded elsewhere via
DOM Security Overview • Child Windows and same site trust • Scripts can interact between the two windows • Script content can be loaded from anywhere (RPC/Remote scripting is common) • Images can be loaded from anywhere • Javascript can either be within tags, loaded elsewhere via