6eb0feee4276f4ff460c5149306d1170.ppt
- Количество слайдов: 33

Advance of Bank Trojan Nov 2005

Current threat from Bank Trojans § Steals online banking information; typically usernames and passwords. § PWSteal. JGinko targets Japanese banks. (Trojan. Spy. Win 32. Banker. vt [Kaspersky Lab], PWS-Jginko [Mc. Afee], TSPY_BANCOS. ANM [Trend Micro]) § These Trojans work closely and actively with Internet Explorer. 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Submission increase § Symantec gets almost 2 million submissions per year. § The rate of submissions is increasing. § Are Bank Trojan submissions increasing? 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
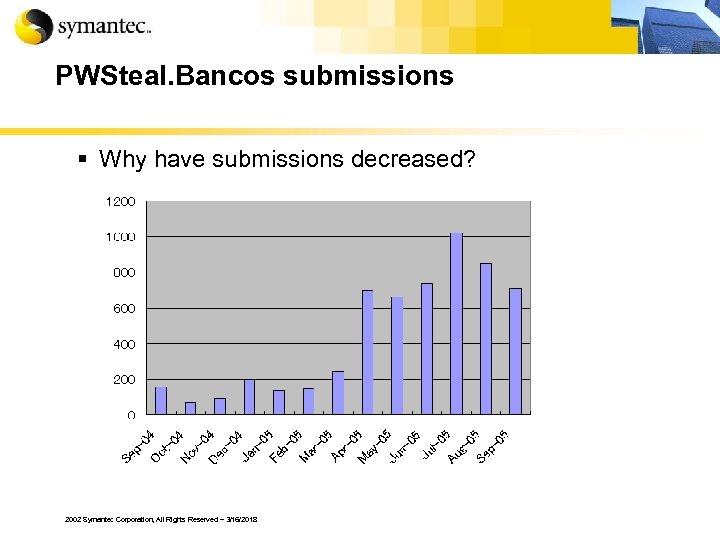
PWSteal. Bancos submissions § Why have submissions decreased? 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
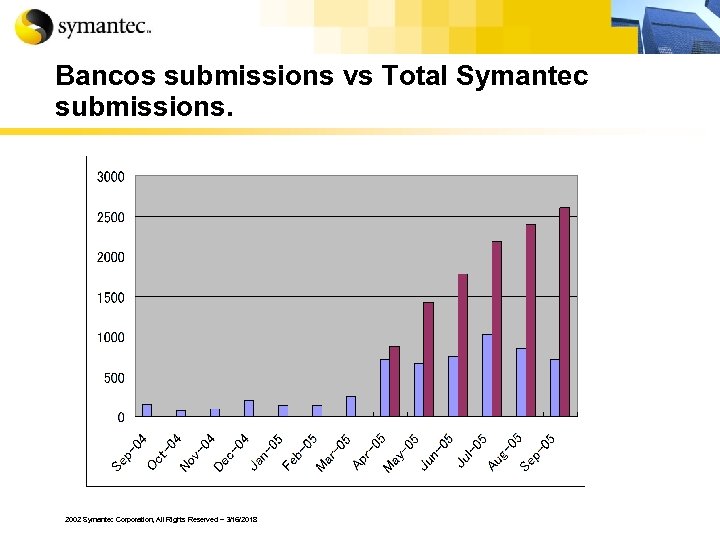
Bancos submissions vs Total Symantec submissions. 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
How samples are collected § User submissions § Honey pot § Web site routine patrol(Adware, Spyware) § Brightmail § BBS 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Japanese Banks VS Bank Trojan § PWSteal. Bancos originally targeted Brazilian Banks. § Then, support was added for German and English Banks. § PWSteal. Jginko targets only Japanese Banks. § PWSteal. Jginko monitors 27 domains. § PWSteal. Bancos. T monitors 2746 domains. 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

PWSteal. Jginko domains § resonabank. anser. or. jp, btm. co. jp, ebank. co. jp § japannetbank. co. jp, smbc. co. jp, yu-cho. japanpost. jp § ufjbank. co. jp, mizuhobank. co. jp § shinseibank. co. jp, iy-bank. co. jp § shinkinbanking. com, shinkin-webfb-hokkaido. jp § shinkin-webfb. jp § And more, more 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Other Bank Trojans also target rural banks § 82 bank. co. jp, akita-bank. co. jp § all. rokin. or. jp, toyotrustbank. co. jp § hyakugo. co. jp, chibabank. co. jp § fukuibank. co. jp, gunmabank. co. jp § hirogin. co. jp, hokugin. co. jp § joyobank. co. jp, nishigin. co. jp § And more, more 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
Security measures taken by Japanese Banks recently § Software Keyboard § Strong password requirements § Challenge and response with one-time encryption key § Prevent phishing mail § Login restricted by IP address § SSL 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
Advantage of Trojan over Key. Logger § These Trojans are not Key. Logger. Trojans § Stealth techniques can be used § Intercepts transaction information § Silent download § Silent update 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Bank Trojans are not Key. Logger. Trojan § Old Key. Loggers log key strokes and send logged data. § Difficult to know which application the user was using § Logs user error (passeo[Back Space]word ) § Difficult to know when the user changes to a different input field 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
Stealth techniques used by Bank Trojans § Works with Internet Explorer. § Firewall does not stop HTTP transaction of Internet Explorer. (BHO, Inject, layered service provider) § Injects itself into other process § Rootkit may hide files or protect them from security application § Hide packet traffic from system to avoid detection 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Intercept transaction § These Trojans can hook specific procedure calls § These Trojans can inject itself into an application § HTTPS is not secure if the data is intercepted before and after it is encrypted 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
Silent download/ Silent update techniques § Trojans may close Alerts from Windows Firewall § Delete Zone. Identifier settings § Add itself to Authorized Applications list, bypassing the firewall 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
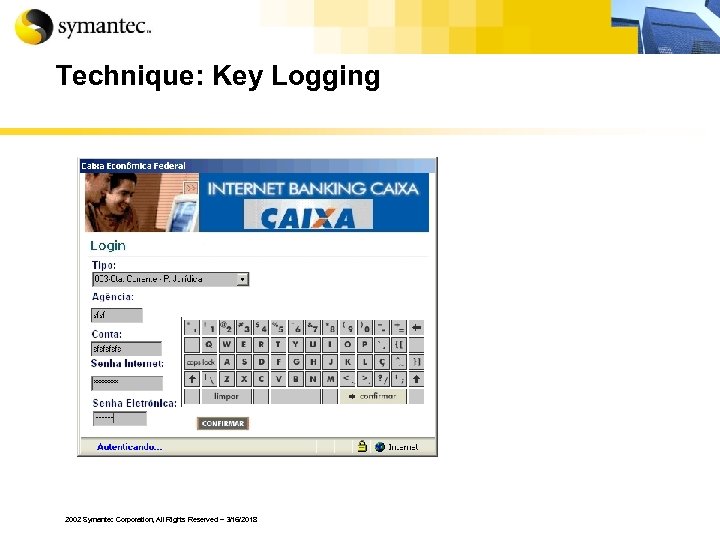
Technique: Key Logging 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
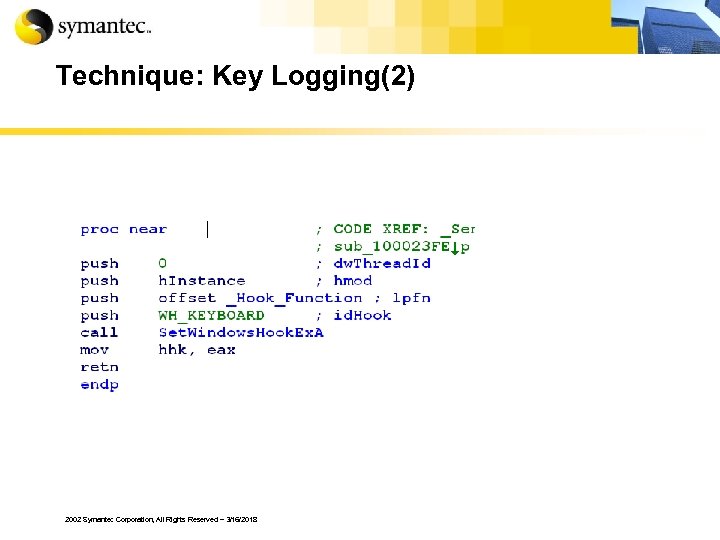
Technique: Key Logging(2) 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
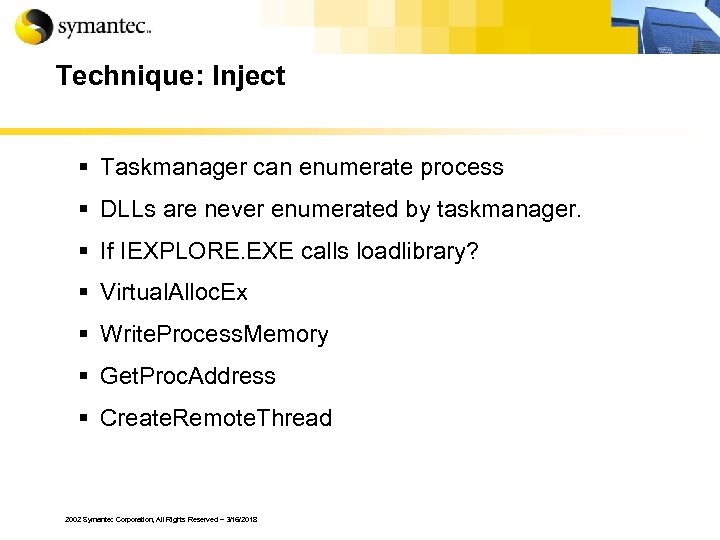
Technique: Inject § Taskmanager can enumerate process § DLLs are never enumerated by taskmanager. § If IEXPLORE. EXE calls loadlibrary? § Virtual. Alloc. Ex § Write. Process. Memory § Get. Proc. Address § Create. Remote. Thread 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Technique: BHO § A Browser helper object is an additional software component that is loaded when Internet Explorer starts. § When a BHO sends a data, It looks like the data is sent by Internet Explorer. § The BHO can’t be seen with Task manager. 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
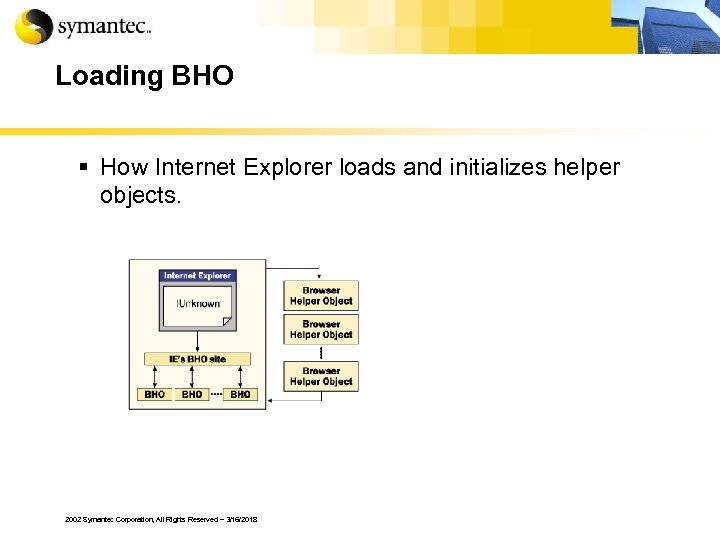
Loading BHO § How Internet Explorer loads and initializes helper objects. 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
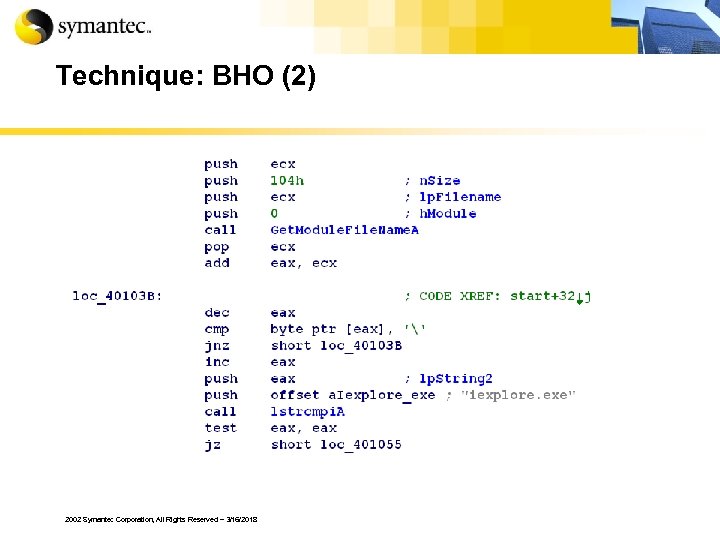
Technique: BHO (2) 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
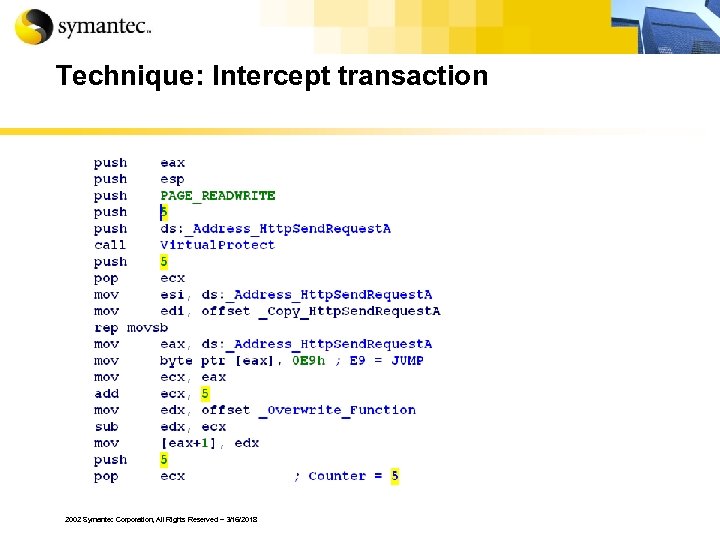
Technique: Intercept transaction 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
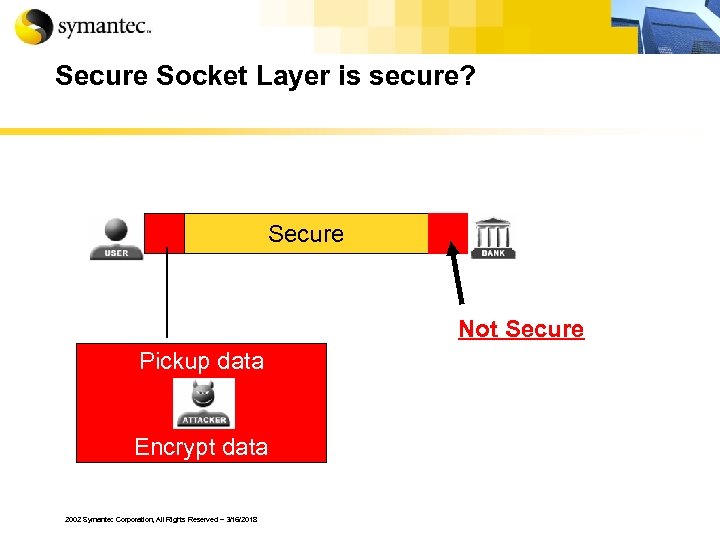
Secure Socket Layer is secure? Secure Not Secure Pickup data Encrypt data 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
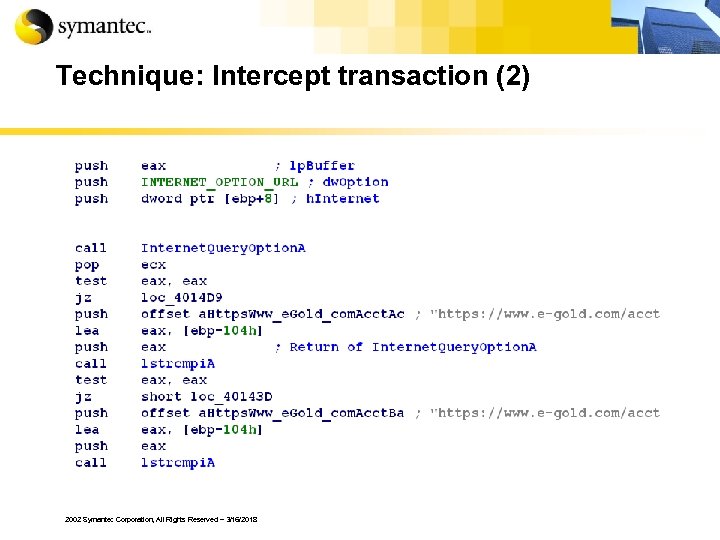
Technique: Intercept transaction (2) 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
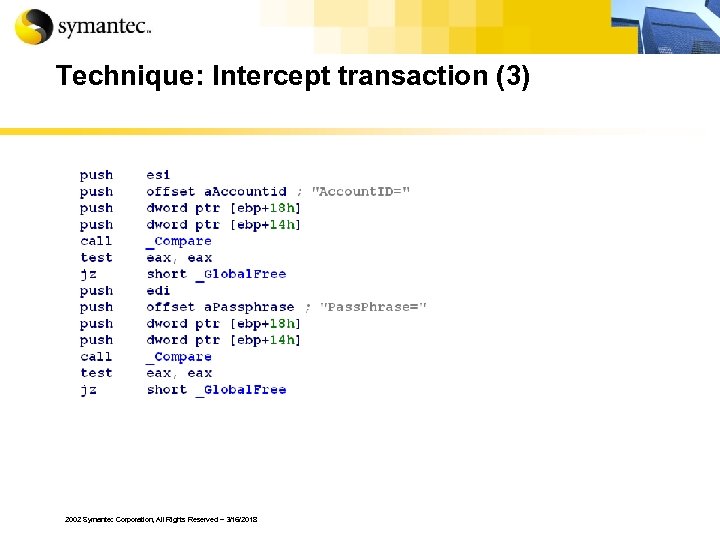
Technique: Intercept transaction (3) 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
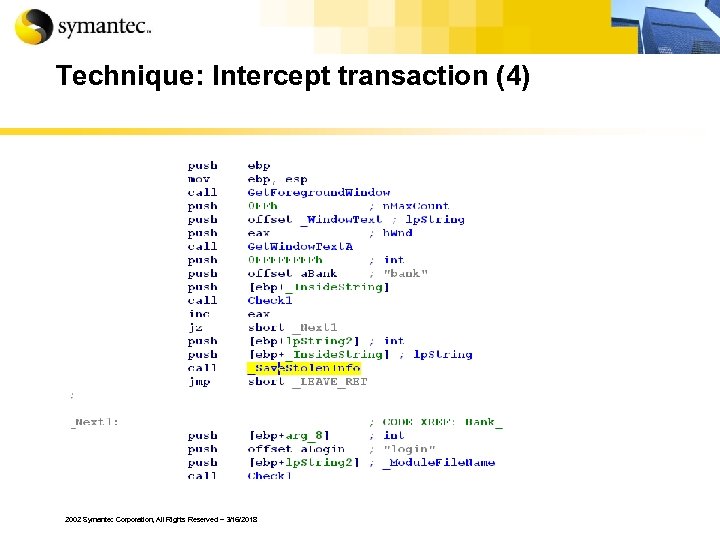
Technique: Intercept transaction (4) 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
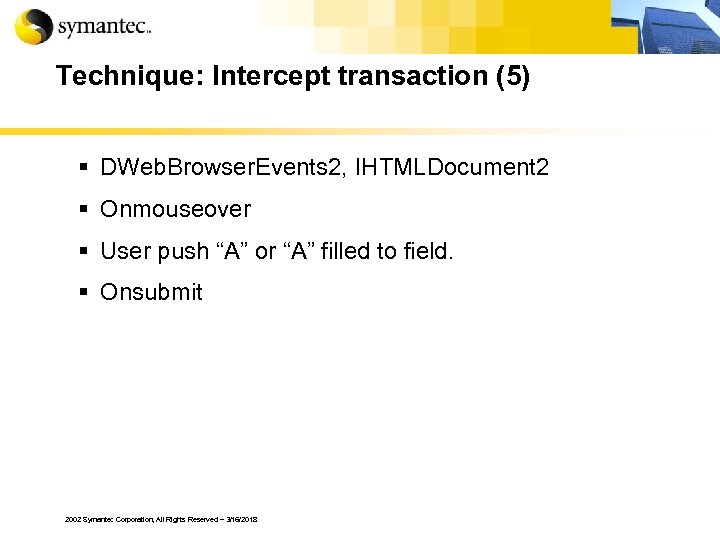
Technique: Intercept transaction (5) § DWeb. Browser. Events 2, IHTMLDocument 2 § Onmouseover § User push “A” or “A” filled to field. § Onsubmit 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
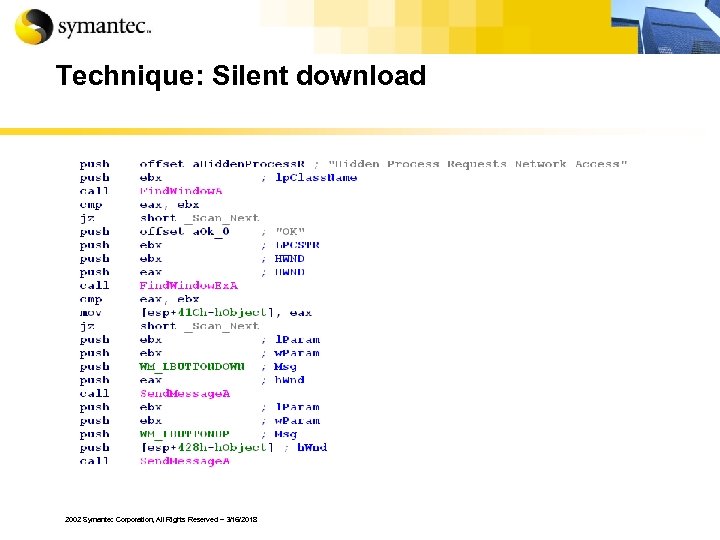
Technique: Silent download 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
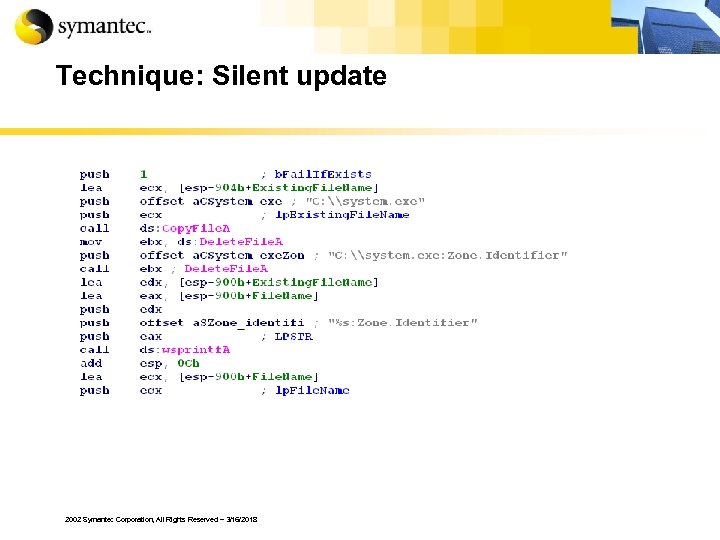
Technique: Silent update 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
Technique: Silent update (2) § HKEY_LOCAL_MACHINESYSTEMCurrent. Control SetServicesShared. AccessParametersFirewall. Poli cyStandard. ProfileAuthorized. ApplicationsList § Value: ": *: Enabled: " 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
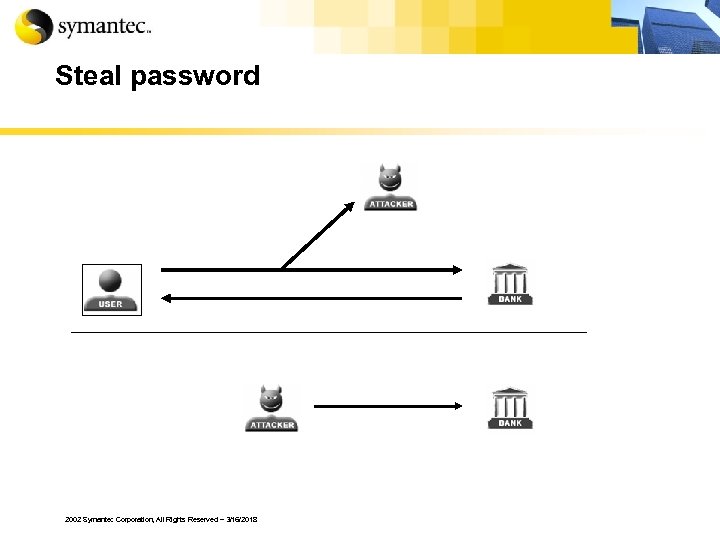
Steal password 2002 Symantec Corporation, All Rights Reserved – 3/16/2018
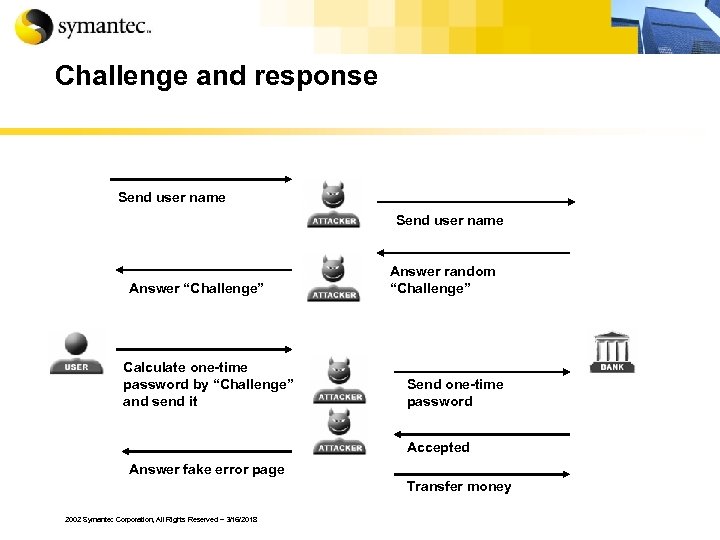
Challenge and response Send user name Answer “Challenge” Calculate one-time password by “Challenge” and send it Answer random “Challenge” Send one-time password Accepted Answer fake error page Transfer money 2002 Symantec Corporation, All Rights Reserved – 3/16/2018

Thank You! Hiroshi Shinotsuka Hiroshi_Shintosuka@symantec. com
6eb0feee4276f4ff460c5149306d1170.ppt