
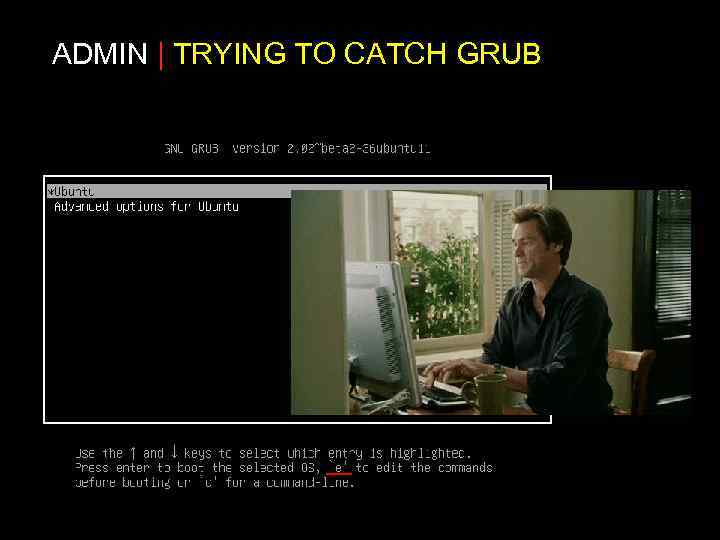
ADMIN | TRYING TO CATCH GRUB
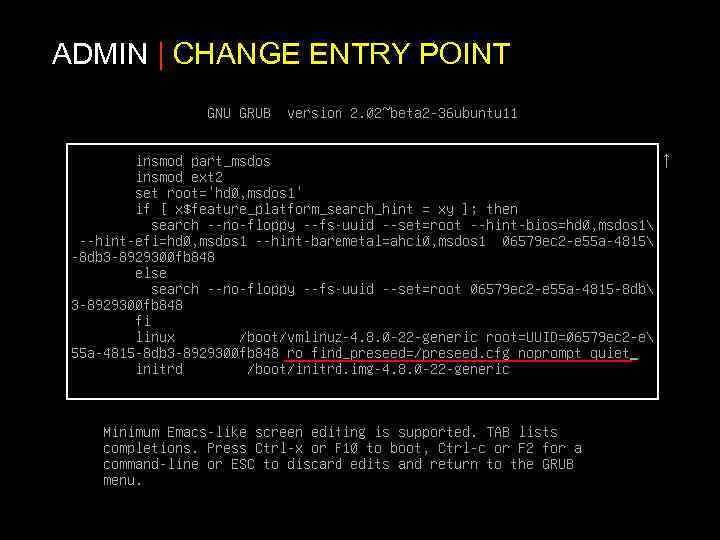
ADMIN | CHANGE ENTRY POINT
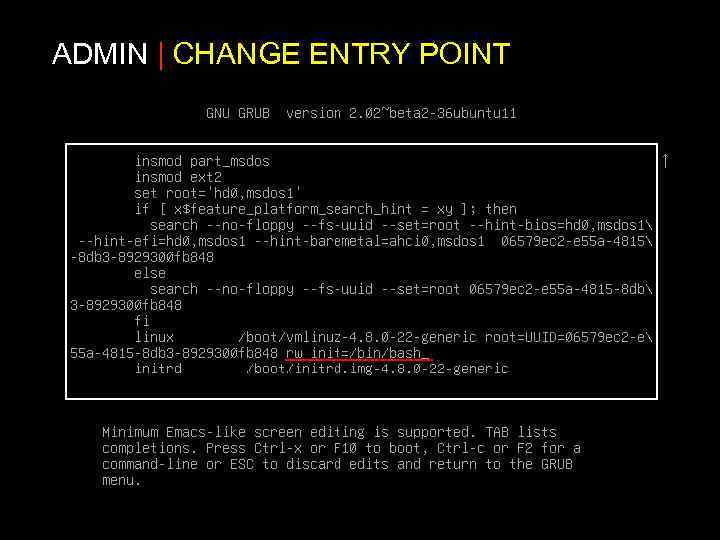
ADMIN | CHANGE ENTRY POINT
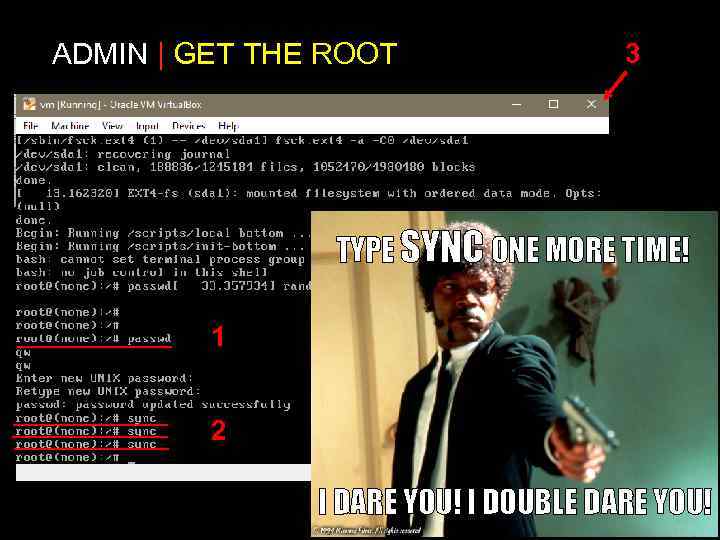
ADMIN | GET THE ROOT 3 TYPE SYNC ONE MORE TIME! 1 2 I DARE YOU! I DOUBLE DARE YOU!
ADMIN | LOOKING FOR SERVICES • Usual local folders: • /home/* • /var/www/html/* • /opt/* • Config files • /etc/init. d/* • /etc/systemd/* • /etc/nginx/sites-*/* • Containers: • docker • lxc lxd
![ADMIN | SYSTEMCTL root@shell : # systemctl [COMMAND] application. service Possible commands: • status ADMIN | SYSTEMCTL root@shell : # systemctl [COMMAND] application. service Possible commands: • status](https://present5.com/presentation/85457300_442260114/image-7.jpg)
ADMIN | SYSTEMCTL root@shell : # systemctl [COMMAND] application. service Possible commands: • status – get service status and latest logs • cat show – show service config file properties • start stop – to launch or kill the service • restart reload – (reload = get new config without restart) • enable disable – make service start on system startup Note: • . service can be omitted • config files placed at /etc/systemd/* (or usually /etc/systemd/system/*)

OK, I GOT THEM! WHAT’S NEXT? !
UPLOAD FROM VM Open the port on some host in the accessible network user@shell : # nc -l 31337 > service. tgz user@shell : # tar xfz service. tgz On the vulnbox: archivate service folder and cat it into the p root@vuln : # tar cfz service. tgz service_folder root@vuln : # cat service. tgz | nc <IP> 31337 Have no network access? It’s bad. Mmkay? Go to that slide.

NOTHING INTERESTING? PROBABLY IT’S CONTAINERED!
![LXC – LINUX CONTAINERS root@shell : # lxc-[COMMAND] –n container_name Possible commands: • ls LXC – LINUX CONTAINERS root@shell : # lxc-[COMMAND] –n container_name Possible commands: • ls](https://present5.com/presentation/85457300_442260114/image-11.jpg)
LXC – LINUX CONTAINERS root@shell : # lxc-[COMMAND] –n container_name Possible commands: • ls – list existing containers (use --fancy for nice out) • start stop – to launch or kill the container • attach – attach to the existing console • execute – exec the command inside (use lxc-execute -n name /bin/bash for new shell) Note: • Container FS is suited at /var/lib/lxc/containers/*
![LXD – MODER LXC HYPERVISOR root@shell : # lxc [COMMAND] container Possible commands: • LXD – MODER LXC HYPERVISOR root@shell : # lxc [COMMAND] container Possible commands: •](https://present5.com/presentation/85457300_442260114/image-12.jpg)
LXD – MODER LXC HYPERVISOR root@shell : # lxc [COMMAND] container Possible commands: • ls – list existing containers (already fancy) • start stop – to launch or kill the container • shell– attach to the existing console • exec – exec the command inside (use lxc exec name -- /bin/bash for new shell) • pull / push – get / put file from / to container (use lxc pull name/home. and u r awesome) • edit – edit file inside container • snapshot / restore - dump and restore from snapshot Note: • Container FS is suited at /var/lib/lxd/containers/*
![DOCKER root@shell : # docker [COMMAND] [opts] container [args] Possible commands: • • run DOCKER root@shell : # docker [COMMAND] [opts] container [args] Possible commands: • • run](https://present5.com/presentation/85457300_442260114/image-13.jpg)
DOCKER root@shell : # docker [COMMAND] [opts] container [args] Possible commands: • • run kill – to launch or kill the container ps – list running containers (ps -a for all existing) attach– attach to the existing console exec – exec the command inside (use lxc exec name -- /bin/bash for new shell) Note: • Will reset all changes on restart! Commit if them are necess • Important run keys: -it – run interactive with attach to current console) -d – demonize -p inside: outside – map port

OK! NOW WE NEED EXPLOITS! STEAL THEM FROM PCAP!
![I NEED SOME PCAPING! user@shell : $ tcpdump [options] [expression] • -i eth 0 I NEED SOME PCAPING! user@shell : $ tcpdump [options] [expression] • -i eth 0](https://present5.com/presentation/85457300_442260114/image-15.jpg)
I NEED SOME PCAPING! user@shell : $ tcpdump [options] [expression] • -i eth 0 : Listen on the eth 0 interface. • -q : Be less verbose (more quiet) with your output. • -s : Define the snaplength (size) of the capture in bytes. Use -s 0 to get everything, unless you are intentionally capturing less. • -w <capture_file> : Save the result to file • -С <size> : Only <size> mbytes in one capture • -G <nseconds> : New file name every <n_seconds> (use %H for hour, %M for minute and so on) • dst port 389 : capture only on specified port • tcp and not dst port 22: another expression example root@shell : # tcpdump -i eth 0 -s 0 -C 10 -w ‘trace_p 31337_’ port 31337 root@shell : # tcpdump -i eth 0 -s 0 -G 60 -w "trace_%H: %M: %S. pcap" port 3000
![I NEED SOME PCAPING! user@shell : $ tshark [options] • • -i eth 0 I NEED SOME PCAPING! user@shell : $ tshark [options] • • -i eth 0](https://present5.com/presentation/85457300_442260114/image-16.jpg)
I NEED SOME PCAPING! user@shell : $ tshark [options] • • -i eth 0 : Listen on the eth 0 interface. -f : Set capture filter (Wire. Shark syntax!) -w <capture_file> : Save the result to file -b <capture ring buffer option> : ▪ duration: value - switch to the next file after value seconds have elapsed, even if the current file is not completely filled up. ▪ filesize: value - switch to the next file after it reaches a size of value k. B. root@shell : # tshark- i eth 0 -w ‘trace_p 31337_’ -f ‘dst port eq 31337’ -b filesize: 1000 root@shell : # tshark -i wlan 0 -Y 'http. request. method == POST and tcp contains "password"' | grep password

FUTURE READING • Open. SSH • A tcpdump Primer with Examples • How to Use Wireshark to Capture, Filter and Inspect Packets
yalegko@sibears : $ echo “Thanx”

APPENDIX Some old slides about future administration

GET ACCESS TO NETWORK root@vm : # dhclient eth 0 • dhclient, provides a means for configuring one or more network interfaces using the Dynamic Host Configuration Protocol ANOTHER WAY root@vm : # ip a add dev <interface> <cidr> <interface> – interface currently connected to the network, usually eth 0 • • <cidr> – IP address and mask in a CIDR form, e. g. 10. 13. 203. 77/24 root@vm : # ip r add <subnet> via <gateway> <subnet> – subnet address in CIDR form, e. g. 10. 13. 0. 0/16 • • <gateway> – gateway that will be used to access that subnet, e. g. 10. 13. 203. 1
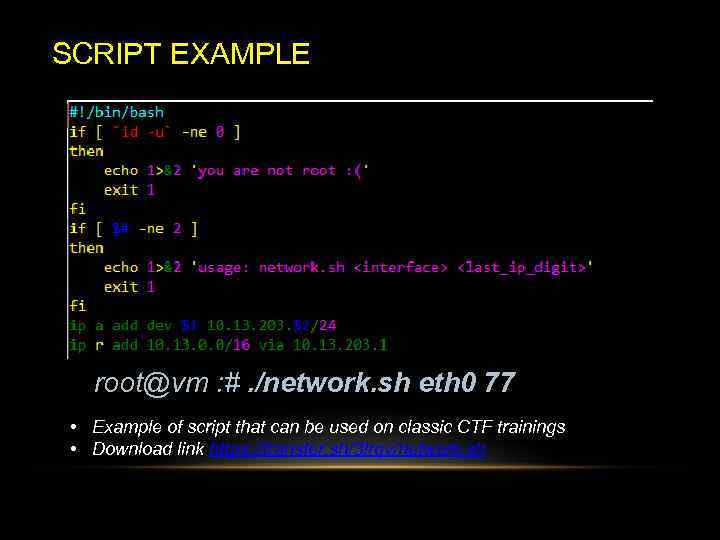
SCRIPT EXAMPLE root@vm : #. /network. sh eth 0 77 • Example of script that can be used on classic CTF trainings • Download link https: //transfer. sh/3 Irqv/network. sh
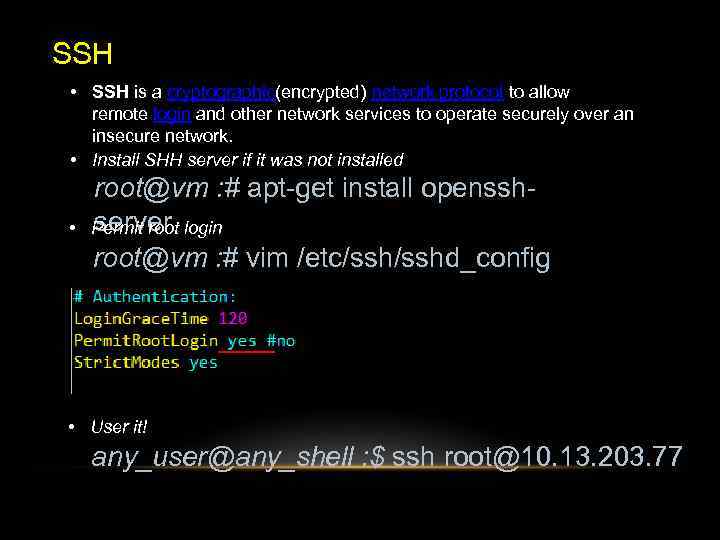
SSH • SSH is a cryptographic(encrypted) network protocol to allow remote login and other network services to operate securely over an insecure network. • Install SHH server if it was not installed • root@vm : # apt-get install opensshserver Permit root login root@vm : # vim /etc/sshd_config • User it! any_user@any_shell : $ ssh root@10. 13. 203. 77
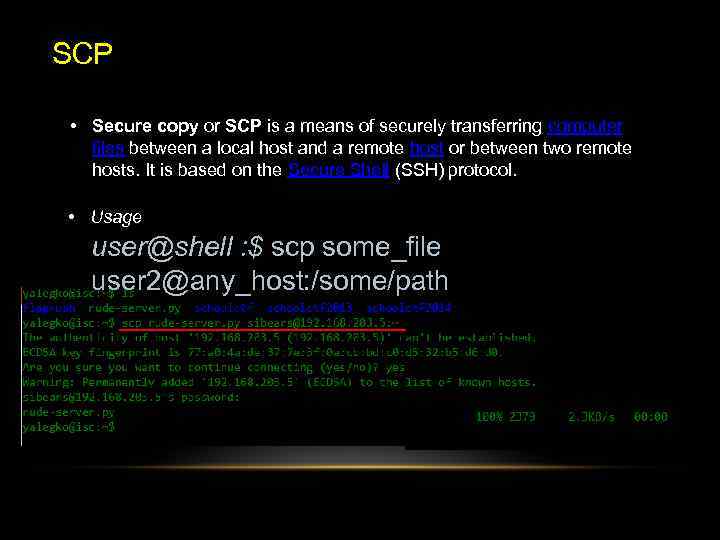
SCP • Secure copy or SCP is a means of securely transferring computer files between a local host and a remote host or between two remote hosts. It is based on the Secure Shell (SSH) protocol. • Usage user@shell : $ scp some_file user 2@any_host: /some/path
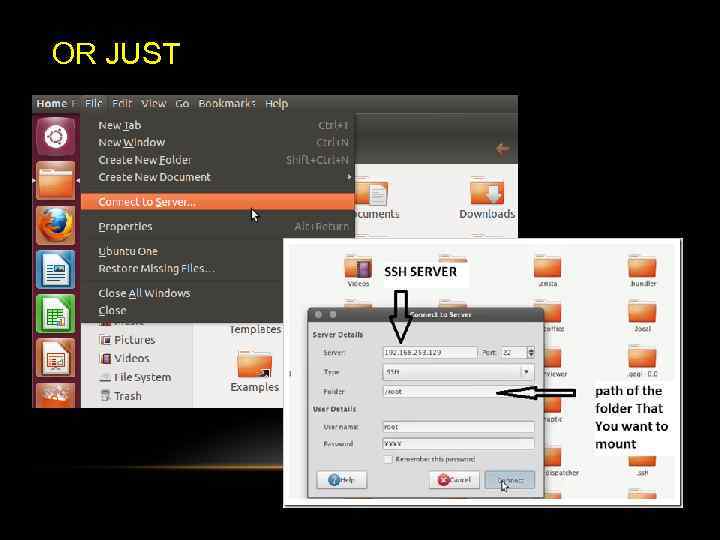
OR JUST

SHELL Looking for something > I need a file user@shell : $ find <directory> -name <pattern> • find - search for files which names matches the <pattern> in a directory hierarchy starting from <directory> user@shell : $ find /var/log -name *apache* > I need file’s content user@shell : $ grep <pattern> <file> • grep searches the named input <file>s (or standard input if no files are named) match to the given <pattern>. By default, grep prints the matching lines. user@shell : $ dmesg | grep error

SHELL Collecting system information > I need open sockets user@shell : $ ss • ss is used to dump socket statistics. It allows showing information similar to netstat. It can display more TCP and state informations than other tools. user@shell : $ ss –nlp | grep 31337 > I need running processes user@shell : $ ps • ps displays information about a selection of the active processes. user@shell : $ ps aux | grep python

SHELL Collecting system information > I need MOAR information user@shell : $ glances • glances is a free (LGPL) cross-platform curses-based monitoring tool which aims to present a maximum of information in a minimum of space, ideally to fit in a classical 80 x 24 terminal or higher to have additionnal information. Glances can adapt dynamically the displayed information depending on the terminal size. It can also work in a client/server mode for remote monitoring.

SHELL Parsing output. > I want only part of file or output user@shell : $ head [options] <file> user@shell : $ tail[options] <file> • head - output the first part of files ▪ -c K: print the first K bytes of each file ▪ -n K: print the first K lines of each file • tail - output the last part of files ▪ same as head root@shell : # tail /var/log/auth. log -n 11 | grep yalegko user@shell : $ ps aux | head -n 2

SHELL Parsing output. > I want only some fields user@shell : $ awk ‘{<commands>}’ • awk - pattern scanning and processing language ▪ print $n – prints n-th column of input user@shell : $ ps aux | grep rude_server | awk ‘{ print $2 }’ > I want to change something in input user@shell : $ sed [options] <script> • sed - stream editor filtering and transforming text ▪ s/old_word/new_word/ - substitute old_word to new_word user@shell : $ ps aux | grep yalegko | sed 's/yalegko/guest/'

SHELL Restart that damn service! > I want to kill existing process user@shell : $ kill [options] <pid> • kill - send a signal to a process user@shell : $ kill –s TERM 25880 > I want to stop/restart service root@shell : # service <service_name> [command] • service runs a System V init script or upstart job. root@shell : # service nginx restart
SHELL More information can be found in man user@shell : $ man <command>