0dd78efc776b98bfa46d1380c18124f1.ppt
- Количество слайдов: 37
 Activities of Information Security Research in Taiwan: TWISC and i. CAST Der-Tsai Lee Distinguished Research Fellow & Director Institute of Information Science Academia Sinica i. CAST 1
Activities of Information Security Research in Taiwan: TWISC and i. CAST Der-Tsai Lee Distinguished Research Fellow & Director Institute of Information Science Academia Sinica i. CAST 1
 Agenda • Introduction to TWISC – Organization – Research issues – Hosted activities • Introduction to i. CAST – Organization – Research issues – Joint conference • Conclusions i. CAST 2
Agenda • Introduction to TWISC – Organization – Research issues – Hosted activities • Introduction to i. CAST – Organization – Research issues – Joint conference • Conclusions i. CAST 2
 Introduction to TWISC i. CAST 3
Introduction to TWISC i. CAST 3
 Introduction to TWISC http: //www. twisc. org/ • Officially founded on April 1 st, 2005, funded by National Science Council (NSC) of Taiwan • Headquarter of TWISC – Center for Information Technology Innovation, Academia Sinica • Three physical centers established – Northern Taiwan: TWISC@NTUST • National Taiwan University of Science & Technology, since Nov. 2005 – Central Taiwan: TWISC@NCTU • National Chiao Tung University, since Oct. 2006 – Southern Taiwan: TWISC@NCKU • National Cheng Kung University, since Oct. 2006 i. CAST 4
Introduction to TWISC http: //www. twisc. org/ • Officially founded on April 1 st, 2005, funded by National Science Council (NSC) of Taiwan • Headquarter of TWISC – Center for Information Technology Innovation, Academia Sinica • Three physical centers established – Northern Taiwan: TWISC@NTUST • National Taiwan University of Science & Technology, since Nov. 2005 – Central Taiwan: TWISC@NCTU • National Chiao Tung University, since Oct. 2006 – Southern Taiwan: TWISC@NCKU • National Cheng Kung University, since Oct. 2006 i. CAST 4
 Objectives/Missions of TWISC • Advance the research and development of technologies in information security and related areas • Provide education and training, help build human resource capacity, and promote public awareness in information security • Collaborate with private sector to enhance local information security industry in security management and applications software development • Seek international collaborations to build a ubiquitous secure community i. CAST 5
Objectives/Missions of TWISC • Advance the research and development of technologies in information security and related areas • Provide education and training, help build human resource capacity, and promote public awareness in information security • Collaborate with private sector to enhance local information security industry in security management and applications software development • Seek international collaborations to build a ubiquitous secure community i. CAST 5
 Strategies for TWISC • Integrate resources and expertise among government, industry and academia to make comprehensive plans on how to foster security-related research effort, and help promote public awareness and capacity-building in information security • Strive for excellence in research and development of technologies in information security & keep abreast with the top-notch leading research institutions worldwide • Serve as a bridge for partnership among government, industry and academia, and as a catalyst of technology transfer in information security sector, and promote university-industry cooperative research in security-related applications • Build a framework for national/international collaboration, including exchange of scholars, researchers and students, and hosting of workshops and conferences i. CAST 6
Strategies for TWISC • Integrate resources and expertise among government, industry and academia to make comprehensive plans on how to foster security-related research effort, and help promote public awareness and capacity-building in information security • Strive for excellence in research and development of technologies in information security & keep abreast with the top-notch leading research institutions worldwide • Serve as a bridge for partnership among government, industry and academia, and as a catalyst of technology transfer in information security sector, and promote university-industry cooperative research in security-related applications • Build a framework for national/international collaboration, including exchange of scholars, researchers and students, and hosting of workshops and conferences i. CAST 6
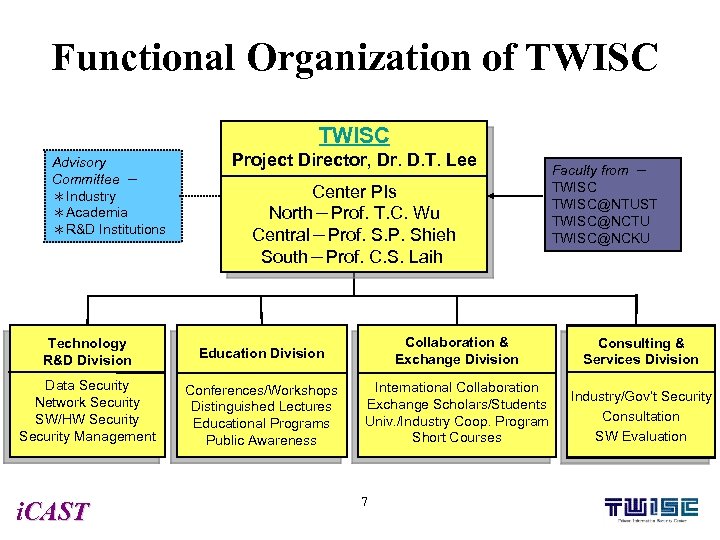 Functional Organization of TWISC Advisory Committee - *Industry *Academia *R&D Institutions Project Director, Dr. D. T. Lee Center PIs North-Prof. T. C. Wu Central-Prof. S. P. Shieh South-Prof. C. S. Laih Faculty from - TWISC@NTUST TWISC@NCTU TWISC@NCKU Technology R&D Division Education Division Collaboration & Exchange Division Consulting & Services Division Data Security Network Security SW/HW Security Management Conferences/Workshops Distinguished Lectures Educational Programs Public Awareness International Collaboration Exchange Scholars/Students Univ. /Industry Coop. Program Short Courses Industry/Gov’t Security Consultation SW Evaluation i. CAST 7
Functional Organization of TWISC Advisory Committee - *Industry *Academia *R&D Institutions Project Director, Dr. D. T. Lee Center PIs North-Prof. T. C. Wu Central-Prof. S. P. Shieh South-Prof. C. S. Laih Faculty from - TWISC@NTUST TWISC@NCTU TWISC@NCKU Technology R&D Division Education Division Collaboration & Exchange Division Consulting & Services Division Data Security Network Security SW/HW Security Management Conferences/Workshops Distinguished Lectures Educational Programs Public Awareness International Collaboration Exchange Scholars/Students Univ. /Industry Coop. Program Short Courses Industry/Gov’t Security Consultation SW Evaluation i. CAST 7
 Research Topics Coordinated by TWISC@NTUST • Major topics – Cryptography • Authentication/digital signature, cryptographic protocols • Cryptographic techniques for low-resource/mobile devices • Multivariate public key cryptography – Software/Hardware Security • Formal verification • Web-based application security assessment • Power analysis/hardware security assessment – Privacy protection • Healthcare or ubiquitous applications • Related topics – Smart card & RFID security – Network security – Security Management 8 i. CAST
Research Topics Coordinated by TWISC@NTUST • Major topics – Cryptography • Authentication/digital signature, cryptographic protocols • Cryptographic techniques for low-resource/mobile devices • Multivariate public key cryptography – Software/Hardware Security • Formal verification • Web-based application security assessment • Power analysis/hardware security assessment – Privacy protection • Healthcare or ubiquitous applications • Related topics – Smart card & RFID security – Network security – Security Management 8 i. CAST
 Research Topics Coordinated by TWISC@NCTU • Major topics – Wireless network security • IPv 6 security • Cryptographic protocols – Sensor network security • Remote security scanner • Related topics – Cryptography • 3 DES, AES • Theoretical proofs – Intrusion detection system – Information hiding & Watermarking – GSN-CERT (Government Service Network – Computer Emergency Response Team) i. CAST 9
Research Topics Coordinated by TWISC@NCTU • Major topics – Wireless network security • IPv 6 security • Cryptographic protocols – Sensor network security • Remote security scanner • Related topics – Cryptography • 3 DES, AES • Theoretical proofs – Intrusion detection system – Information hiding & Watermarking – GSN-CERT (Government Service Network – Computer Emergency Response Team) i. CAST 9
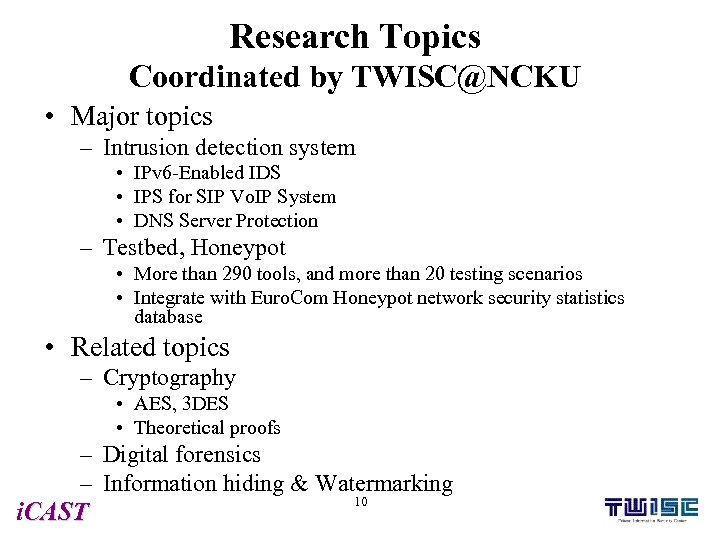 Research Topics Coordinated by TWISC@NCKU • Major topics – Intrusion detection system • IPv 6 -Enabled IDS • IPS for SIP Vo. IP System • DNS Server Protection – Testbed, Honeypot • More than 290 tools, and more than 20 testing scenarios • Integrate with Euro. Com Honeypot network security statistics database • Related topics – Cryptography • AES, 3 DES • Theoretical proofs – Digital forensics – Information hiding & Watermarking i. CAST 10
Research Topics Coordinated by TWISC@NCKU • Major topics – Intrusion detection system • IPv 6 -Enabled IDS • IPS for SIP Vo. IP System • DNS Server Protection – Testbed, Honeypot • More than 290 tools, and more than 20 testing scenarios • Integrate with Euro. Com Honeypot network security statistics database • Related topics – Cryptography • AES, 3 DES • Theoretical proofs – Digital forensics – Information hiding & Watermarking i. CAST 10
 Hosted Workshops and Conferences - SADFE 2005 • SADFE 2005 (First International Workshop on Systematic Approaches to Digital Forensic Engineering) Nov. 7 -10, 2005, Taipei, Taiwan http: //conf. ncku. edu. tw/sadfe/ i. CAST 11
Hosted Workshops and Conferences - SADFE 2005 • SADFE 2005 (First International Workshop on Systematic Approaches to Digital Forensic Engineering) Nov. 7 -10, 2005, Taipei, Taiwan http: //conf. ncku. edu. tw/sadfe/ i. CAST 11
 Hosted Workshops and Conferences - Asia. CCS'06 • ACM Symposium on Information, Computer and Communications Security (Asia. CCS'06) March 21 -23, 2006, Taipei, Taiwan http: //www. iis. sinica. edu. tw/asiaccs 06/ i. CAST 12
Hosted Workshops and Conferences - Asia. CCS'06 • ACM Symposium on Information, Computer and Communications Security (Asia. CCS'06) March 21 -23, 2006, Taipei, Taiwan http: //www. iis. sinica. edu. tw/asiaccs 06/ i. CAST 12
 Distinguished Lecture Series • Date: 2005/12/16 • Prof. Hideki IMAI Information and Systems Dept. of Institute of Industrial Science, University of Tokyo • Topic: Trends and Challenges for Securer Cryptography i. CAST 13
Distinguished Lecture Series • Date: 2005/12/16 • Prof. Hideki IMAI Information and Systems Dept. of Institute of Industrial Science, University of Tokyo • Topic: Trends and Challenges for Securer Cryptography i. CAST 13
 Distinguished Lecture Series Date: 2006/3/20 Prof. Doug Tygar, UC Berkeley Prof. Tzi-cker Chiueh, State Uni. Of New York at Stony Brook Topics: (1) Open problems and promising approaches in computer security (Prof. Tygar) (2) Software Security and Solutions : A Stony Brook Perspective ( Prof. Chiueh) i. CAST 14
Distinguished Lecture Series Date: 2006/3/20 Prof. Doug Tygar, UC Berkeley Prof. Tzi-cker Chiueh, State Uni. Of New York at Stony Brook Topics: (1) Open problems and promising approaches in computer security (Prof. Tygar) (2) Software Security and Solutions : A Stony Brook Perspective ( Prof. Chiueh) i. CAST 14
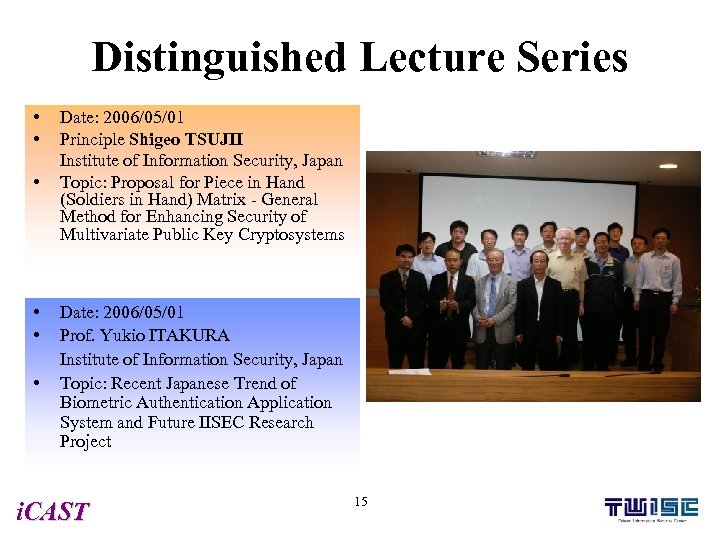 Distinguished Lecture Series • • • Date: 2006/05/01 Principle Shigeo TSUJII Institute of Information Security, Japan Topic: Proposal for Piece in Hand (Soldiers in Hand) Matrix - General Method for Enhancing Security of Multivariate Public Key Cryptosystems Date: 2006/05/01 Prof. Yukio ITAKURA Institute of Information Security, Japan Topic: Recent Japanese Trend of Biometric Authentication Application System and Future IISEC Research Project i. CAST 15
Distinguished Lecture Series • • • Date: 2006/05/01 Principle Shigeo TSUJII Institute of Information Security, Japan Topic: Proposal for Piece in Hand (Soldiers in Hand) Matrix - General Method for Enhancing Security of Multivariate Public Key Cryptosystems Date: 2006/05/01 Prof. Yukio ITAKURA Institute of Information Security, Japan Topic: Recent Japanese Trend of Biometric Authentication Application System and Future IISEC Research Project i. CAST 15
 Distinguished Lecture Series • • • i. CAST Date: 2006/06/01 Prof. Kwangjo Kim Information and Communications University, Korea Topic: Security Challenges in Ubiquitous Society 16
Distinguished Lecture Series • • • i. CAST Date: 2006/06/01 Prof. Kwangjo Kim Information and Communications University, Korea Topic: Security Challenges in Ubiquitous Society 16
 Distinguished Lecture Series • • • i. CAST Date: 2006/07/06 Prof. Adrian Perrig CMU, USA Topic: Security in Sensor Network: Industry Trends, Present and Future Research Direction 17
Distinguished Lecture Series • • • i. CAST Date: 2006/07/06 Prof. Adrian Perrig CMU, USA Topic: Security in Sensor Network: Industry Trends, Present and Future Research Direction 17
 Distinguished Lecture Series • • • i. CAST Date: 2006/08/04 Prof. Felix Wu UC Davis, USA Topic: Security and Robustness based on Nothing: A New Paradigm for Future Internet Design 18
Distinguished Lecture Series • • • i. CAST Date: 2006/08/04 Prof. Felix Wu UC Davis, USA Topic: Security and Robustness based on Nothing: A New Paradigm for Future Internet Design 18
 Distinguished Lecture Series • • • i. CAST Date: 2006/11/24 Prof. Rei Safavi-Naini University of Wollongong, Australia Topic: Post-Quantum Cryptography 19
Distinguished Lecture Series • • • i. CAST Date: 2006/11/24 Prof. Rei Safavi-Naini University of Wollongong, Australia Topic: Post-Quantum Cryptography 19
 Distinguished Lecture Series • • • i. CAST Date: 2007/01/03 Prof. Horace Yuen Northwestern University Topic: Quantum and Physical Cryptography 20
Distinguished Lecture Series • • • i. CAST Date: 2007/01/03 Prof. Horace Yuen Northwestern University Topic: Quantum and Physical Cryptography 20
 Distinguished Lecture Series Date: 2007/4/02 • Prof. Vincent Rijmen Graz University of Technology Institute for Applied Information Processing and Communications (IAIK) - Krypto Group • Topic: 10 years of Rijndael and Beyond l i. CAST 21
Distinguished Lecture Series Date: 2007/4/02 • Prof. Vincent Rijmen Graz University of Technology Institute for Applied Information Processing and Communications (IAIK) - Krypto Group • Topic: 10 years of Rijndael and Beyond l i. CAST 21
 Recent Invited Speakers - Prof. Kouichi SAKURAI, Kyushu University Topic: Cryptographic Infrastructures based on a Unique Device with Tamper-Resistant - Prof. George Mohay , Queensland University of Technology Topic: File system and network acquisition and analysis tools - Prof. Steve Schroeder , Seattle University, a pioneer in Cyber crime law enforcement Topic: Preparing to be an Expert Witness i. CAST 22
Recent Invited Speakers - Prof. Kouichi SAKURAI, Kyushu University Topic: Cryptographic Infrastructures based on a Unique Device with Tamper-Resistant - Prof. George Mohay , Queensland University of Technology Topic: File system and network acquisition and analysis tools - Prof. Steve Schroeder , Seattle University, a pioneer in Cyber crime law enforcement Topic: Preparing to be an Expert Witness i. CAST 22
 Workshop on Advanced Information Security Technology Date: 2006/01/20 -21 at NTUST Topic: Multivariate PKC Prof. Jintai Ding, University Prof. Christopher Wolf, Ecole of Cincinnati, USA 23 Normal Superieure, France i. CAST Prof. Bo-Yin Yang, Tamkang University Taiwan
Workshop on Advanced Information Security Technology Date: 2006/01/20 -21 at NTUST Topic: Multivariate PKC Prof. Jintai Ding, University Prof. Christopher Wolf, Ecole of Cincinnati, USA 23 Normal Superieure, France i. CAST Prof. Bo-Yin Yang, Tamkang University Taiwan
 Information Security Summer School (ISSS) Aug. 10~24, 2006 • Lecturers: Prof. Tzong-Chen Wu (NTUST), Prof. Chi-Sung Laih (NCKU), Prof. Bo-Yin Yang (Academia Sinica), Prof. Dan Bernstein (U. Illinois Chicago), Prof. Tanja Lange (Tech. U. Denmark), Prof. Claus Diem (U. Leipzig Germany), Dr. Rui Zhang (RCIS Japan), Dr. Takayuki Miyadera (RCIS Japan), Dr. Yutaka Oiwa (RCIS Japan), Prof. Jason Crampton (ISG UK), Prof. Keith Martin (ISG UK), Prof. Chris Mitchell (ISG UK), Prof. Keith Mayes (ISG UK) • Venue: National Taiwan University of Science and Technology (NTUST) • For more information see http: //www. twisc. org i. CAST 24
Information Security Summer School (ISSS) Aug. 10~24, 2006 • Lecturers: Prof. Tzong-Chen Wu (NTUST), Prof. Chi-Sung Laih (NCKU), Prof. Bo-Yin Yang (Academia Sinica), Prof. Dan Bernstein (U. Illinois Chicago), Prof. Tanja Lange (Tech. U. Denmark), Prof. Claus Diem (U. Leipzig Germany), Dr. Rui Zhang (RCIS Japan), Dr. Takayuki Miyadera (RCIS Japan), Dr. Yutaka Oiwa (RCIS Japan), Prof. Jason Crampton (ISG UK), Prof. Keith Martin (ISG UK), Prof. Chris Mitchell (ISG UK), Prof. Keith Mayes (ISG UK) • Venue: National Taiwan University of Science and Technology (NTUST) • For more information see http: //www. twisc. org i. CAST 24
 Information Security Summer School (ISSS) Aug. 6~16, 2007 • Lecturers: Prof. Chris Mitchell (ISG), Dr. Keith Mayes (ISG), Dr. Marc Joye (Thomson), Prof. Robert Deng (SMU), Prof. Kwangjo Kim (ICU), Prof. John Choi (Sangmyung), Dr. Chan Yeob Yeun (LG), Dr. Jonathan Millen(Mitre), Prof. Naoshi Sato (IISec), Prof. Tzong-Chen Wu (NTUST) • Venue: National Taiwan University of Science and Technology (NTUST) • For more information see http: //www. twisc. org i. CAST 25
Information Security Summer School (ISSS) Aug. 6~16, 2007 • Lecturers: Prof. Chris Mitchell (ISG), Dr. Keith Mayes (ISG), Dr. Marc Joye (Thomson), Prof. Robert Deng (SMU), Prof. Kwangjo Kim (ICU), Prof. John Choi (Sangmyung), Dr. Chan Yeob Yeun (LG), Dr. Jonathan Millen(Mitre), Prof. Naoshi Sato (IISec), Prof. Tzong-Chen Wu (NTUST) • Venue: National Taiwan University of Science and Technology (NTUST) • For more information see http: //www. twisc. org i. CAST 25
 11 th Information Security Conference (ISC 2008) • Venue: The Grand Hotel, Taipei, Taiwan • Dates: September, 2008 (TBD) • Hosted by CCISA (Chinese Cryptology and Information Security Association), TWISC, Academia Sinica, Industrial Technology Research Institute (ITRI), Institute for Information Industrial (III), etc. • Organizing Committee Members – – i. CAST Director Der-Tsai Lee (Academia Sinica) Prof. Tzong-Chen Wu (NTUST) Prof. Chin-Luang Lei (NTU) Vincent Rijmen (Technical University of Graz, Austria) 26
11 th Information Security Conference (ISC 2008) • Venue: The Grand Hotel, Taipei, Taiwan • Dates: September, 2008 (TBD) • Hosted by CCISA (Chinese Cryptology and Information Security Association), TWISC, Academia Sinica, Industrial Technology Research Institute (ITRI), Institute for Information Industrial (III), etc. • Organizing Committee Members – – i. CAST Director Der-Tsai Lee (Academia Sinica) Prof. Tzong-Chen Wu (NTUST) Prof. Chin-Luang Lei (NTU) Vincent Rijmen (Technical University of Graz, Austria) 26
 Introduction to i. CAST 27
Introduction to i. CAST 27
 Introduction to i. CAST http: //www. icast. org. tw/ • Officially founded on May 1 st, 2006, funded by National Science Council (NSC) of Taiwan • i. CAST is a team consisting of members from TWISC, Institute for Information Industry (III), Industrial Technology Research Institute (ITRI) and Chung Cheng Institute of Technology, National Defense University of Taiwan • Collaborated with members of Carnegie Mellon University (CMU) and University of California, Berkeley (UCB) on 11 projects • The research fields of such scholars include cryptology, network security, multimedia security, software security, and information security management i. CAST 28
Introduction to i. CAST http: //www. icast. org. tw/ • Officially founded on May 1 st, 2006, funded by National Science Council (NSC) of Taiwan • i. CAST is a team consisting of members from TWISC, Institute for Information Industry (III), Industrial Technology Research Institute (ITRI) and Chung Cheng Institute of Technology, National Defense University of Taiwan • Collaborated with members of Carnegie Mellon University (CMU) and University of California, Berkeley (UCB) on 11 projects • The research fields of such scholars include cryptology, network security, multimedia security, software security, and information security management i. CAST 28
 Missions for i. CAST • To do academic collaborative works and researches with CMU and UCB • To gain core technologies and develop prototypes jointly work with CMU and UCB • Cultivate the seeds of information security • Spread the knowledge of information security education • In the future, to do technology transfer to the industries in Taiwan to promote their self-capability • To dispatch professors and Ph. D students to CMU and UCB for the short-term and long-term study to enlarge global vision in further researching i. CAST 29
Missions for i. CAST • To do academic collaborative works and researches with CMU and UCB • To gain core technologies and develop prototypes jointly work with CMU and UCB • Cultivate the seeds of information security • Spread the knowledge of information security education • In the future, to do technology transfer to the industries in Taiwan to promote their self-capability • To dispatch professors and Ph. D students to CMU and UCB for the short-term and long-term study to enlarge global vision in further researching i. CAST 29
 Strategies for i. CAST • Two subgroups are formed in each researching group, one is focused on doing internal works in Taiwan’s site, and the other is focused on doing joint works in the campus of CMU/UCB • All works or core technologies are deliverable to journal/conference papers and prototype implementation – Papers will be submitted to SCI journals (with high impact factors) or top international conferences – Developed prototype should be portable to real system in practice i. CAST 30
Strategies for i. CAST • Two subgroups are formed in each researching group, one is focused on doing internal works in Taiwan’s site, and the other is focused on doing joint works in the campus of CMU/UCB • All works or core technologies are deliverable to journal/conference papers and prototype implementation – Papers will be submitted to SCI journals (with high impact factors) or top international conferences – Developed prototype should be portable to real system in practice i. CAST 30
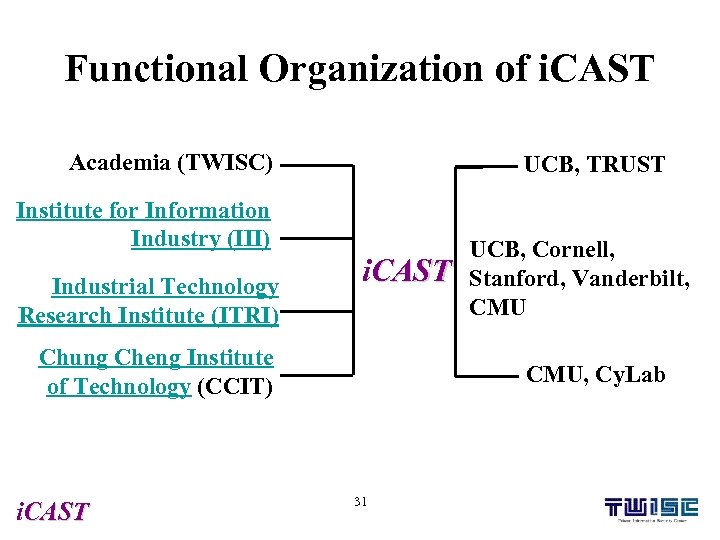 Functional Organization of i. CAST Academia (TWISC) UCB, TRUST Institute for Information Industry (III) Industrial Technology Research Institute (ITRI) i. CAST Chung Cheng Institute of Technology (CCIT) i. CAST UCB, Cornell, Stanford, Vanderbilt, CMU, Cy. Lab 31
Functional Organization of i. CAST Academia (TWISC) UCB, TRUST Institute for Information Industry (III) Industrial Technology Research Institute (ITRI) i. CAST Chung Cheng Institute of Technology (CCIT) i. CAST UCB, Cornell, Stanford, Vanderbilt, CMU, Cy. Lab 31
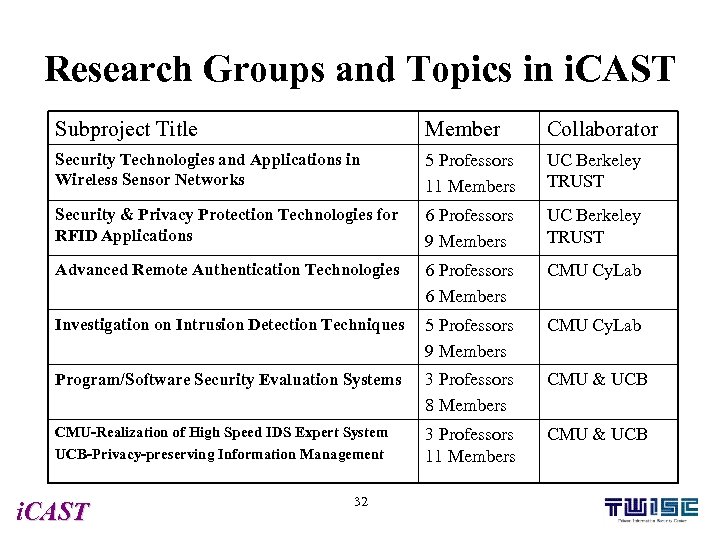 Research Groups and Topics in i. CAST Subproject Title Member Collaborator Security Technologies and Applications in Wireless Sensor Networks 5 Professors 11 Members UC Berkeley TRUST Security & Privacy Protection Technologies for RFID Applications 6 Professors 9 Members UC Berkeley TRUST Advanced Remote Authentication Technologies 6 Professors 6 Members CMU Cy. Lab Investigation on Intrusion Detection Techniques 5 Professors 9 Members CMU Cy. Lab Program/Software Security Evaluation Systems 3 Professors 8 Members CMU & UCB CMU-Realization of High Speed IDS Expert System UCB-Privacy-preserving Information Management 3 Professors 11 Members CMU & UCB i. CAST 32
Research Groups and Topics in i. CAST Subproject Title Member Collaborator Security Technologies and Applications in Wireless Sensor Networks 5 Professors 11 Members UC Berkeley TRUST Security & Privacy Protection Technologies for RFID Applications 6 Professors 9 Members UC Berkeley TRUST Advanced Remote Authentication Technologies 6 Professors 6 Members CMU Cy. Lab Investigation on Intrusion Detection Techniques 5 Professors 9 Members CMU Cy. Lab Program/Software Security Evaluation Systems 3 Professors 8 Members CMU & UCB CMU-Realization of High Speed IDS Expert System UCB-Privacy-preserving Information Management 3 Professors 11 Members CMU & UCB i. CAST 32
 Research Topics in i. CAST • Technologies & Applications in Wireless Sensor Networks (WSNs) • Security & Privacy Protection Technologies for RFID Applications • Investigation on Advanced Remote Authentication Technologies • Machine Learning Techniques in Intrusion Detection • Formal Security Analysis and Verification • Network-based Early Anomaly Detection of Intrusion • Privacy Protection Management Systems i. CAST 33
Research Topics in i. CAST • Technologies & Applications in Wireless Sensor Networks (WSNs) • Security & Privacy Protection Technologies for RFID Applications • Investigation on Advanced Remote Authentication Technologies • Machine Learning Techniques in Intrusion Detection • Formal Security Analysis and Verification • Network-based Early Anomaly Detection of Intrusion • Privacy Protection Management Systems i. CAST 33
 i. CAST/CMU/TRUST Joint Conference • • January 8 -10, 2007, Taipei, Taiwan June 4 -5, 2007, Taipei, Taiwan January , 2008, Taipei, Taiwan http: //www. icast. org. tw/events/conferencesand-workshops i. CAST 34
i. CAST/CMU/TRUST Joint Conference • • January 8 -10, 2007, Taipei, Taiwan June 4 -5, 2007, Taipei, Taiwan January , 2008, Taipei, Taiwan http: //www. icast. org. tw/events/conferencesand-workshops i. CAST 34
 Developed Prototypes • (RISE) RFID + ITS + Sensor Network+ Embedded Systems – A blood storage bag management system for healthcare, providing offsite tracking and on-site management • Asset Monitoring and Protection – Record the flowing objects and prevent from stealing assets in dormitory • Pi. SA (Pervasive i. CAST Security Angel) – Use PDA or cellular phone to authenticate the trustworthy website via visual random art • IDEAS (Intrusion Detection and Event Analysis System) – Based on machine learning and AI methods to analyze real-time network data • Security Monitor – Implemented on a Linux platform with a loadable kernel module to compute and update the probabilistic belief (inference engine) of the attack • Personal Privacy Guard (Ocean. Store) – Provide personalized privacy preference rules generation, reasoning, and refinement for personal information protection i. CAST 35
Developed Prototypes • (RISE) RFID + ITS + Sensor Network+ Embedded Systems – A blood storage bag management system for healthcare, providing offsite tracking and on-site management • Asset Monitoring and Protection – Record the flowing objects and prevent from stealing assets in dormitory • Pi. SA (Pervasive i. CAST Security Angel) – Use PDA or cellular phone to authenticate the trustworthy website via visual random art • IDEAS (Intrusion Detection and Event Analysis System) – Based on machine learning and AI methods to analyze real-time network data • Security Monitor – Implemented on a Linux platform with a loadable kernel module to compute and update the probabilistic belief (inference engine) of the attack • Personal Privacy Guard (Ocean. Store) – Provide personalized privacy preference rules generation, reasoning, and refinement for personal information protection i. CAST 35
 International Collaboration in TWISC i. CAST 36
International Collaboration in TWISC i. CAST 36
 Conclusions • TWISC is to serve as an R&D resource center to enhance technical competence, including Ubicomp security • TWISC is to enlarge human resource capacity and promote public awareness in information security • TWISC is to be a window for university-industry partnership and international collaboration in information security • TWISC represents integrated research capabilities in Taiwan, aiming to establish itself as a power house in information security, working closely with other renowned centers or laboratories worldwide. i. CAST 37
Conclusions • TWISC is to serve as an R&D resource center to enhance technical competence, including Ubicomp security • TWISC is to enlarge human resource capacity and promote public awareness in information security • TWISC is to be a window for university-industry partnership and international collaboration in information security • TWISC represents integrated research capabilities in Taiwan, aiming to establish itself as a power house in information security, working closely with other renowned centers or laboratories worldwide. i. CAST 37


