db7df02f0b56f1b3bbb69937a47ff79b.ppt
- Количество слайдов: 42

Active Networks – The Network Future By Samatha Gangapuram Prashant Shanti Kumar Harish Kumar Maringanti

Assigned Unenviable task Ø What Ø Why Ø How Ø Where

Active Networks – What ? No general agreement beyond buzz phrases. “Active networks explore the idea of allowing routing elements to be extensively programmed by the packets passing through them. ”
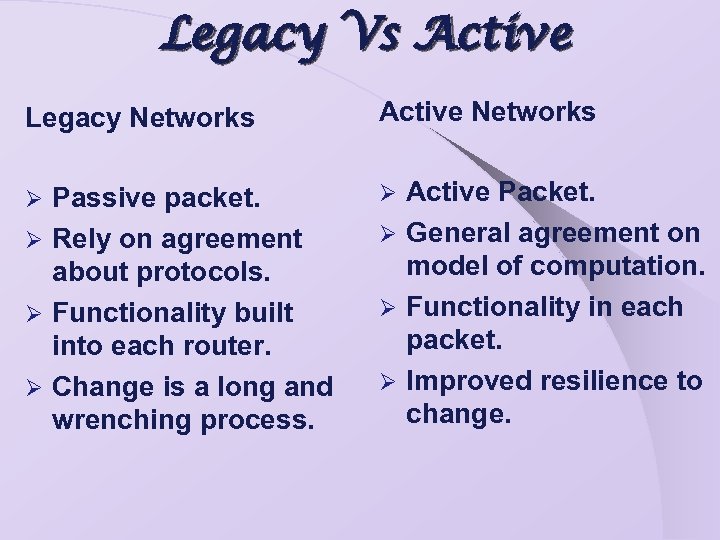
Legacy Vs Active Legacy Networks Active Networks Passive packet. Ø Rely on agreement about protocols. Ø Functionality built into each router. Ø Change is a long and wrenching process. Ø Ø Active Packet. Ø General agreement on model of computation. Ø Functionality in each packet. Ø Improved resilience to change.
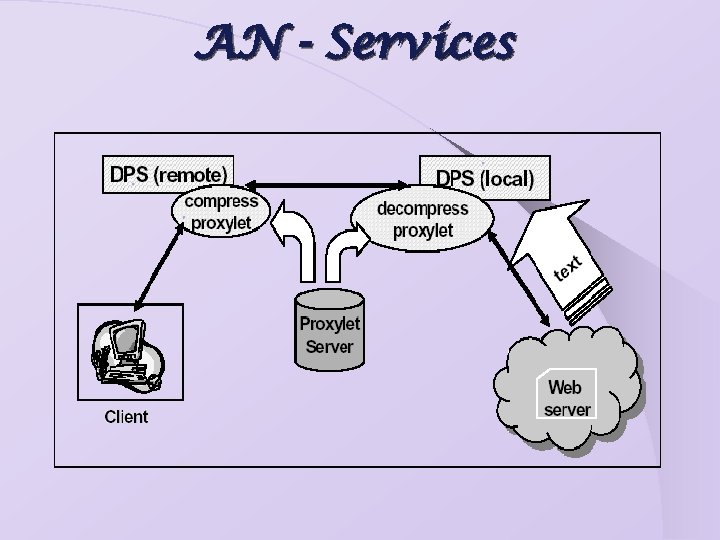
AN - Services

Active Networks – Why ? Ø Rapid deployment and development. Ø Creating and Tailoring network services. Ø Better performance. Ø Open to deploy and administer.

Active Networks – How ? AN Paradigms Programmable Switch Model Ø Capsule Model Ø Ad – hoc Model Ø
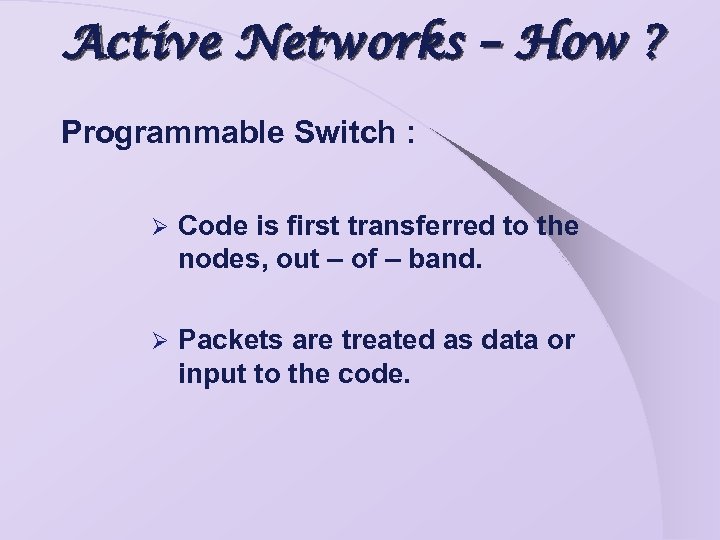
Active Networks – How ? Programmable Switch : Ø Code is first transferred to the nodes, out – of – band. Ø Packets are treated as data or input to the code.
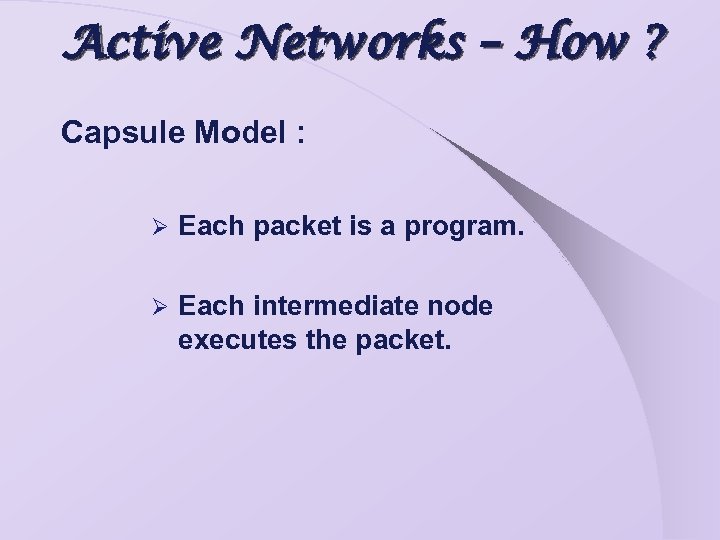
Active Networks – How ? Capsule Model : Ø Each packet is a program. Ø Each intermediate node executes the packet.
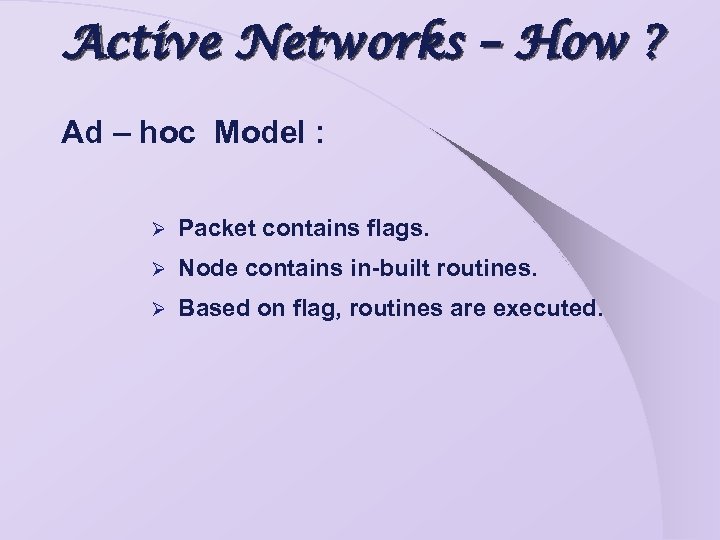
Active Networks – How ? Ad – hoc Model : Ø Packet contains flags. Ø Node contains in-built routines. Ø Based on flag, routines are executed.

A N - Terminologies Ø User Application (UA) Ø Active Application (AA) Ø Execution Environment (EE) Ø Node Operating System (Node. OS)

Node. OS The Node. OS is the base layer of any AN architecture. Ø It manages the resources of the active node and co-ordinates the resource demands. Ø Node. OS is also responsible for the enforcement of security policies. Examples SANE OS, JANOS, SCOUT, Exo. Kernel Ø

EE Nerve Center of the Active Node Responsible for all aspects of user-network interface. Ø Nature of programming model and abstractions supported. Ø Addressing and Naming facilities. Ø Examples Smart. Packets, ANTS, CANE

AA AA is a program and associated state capable of executing one or more activities in a node, to perform some particular service. Ø AA is necessarily “portable” and dynamically installable or removable. Ø Examples Active Reliable Multicasts, Protocol Boosters, Active Congestion Control.
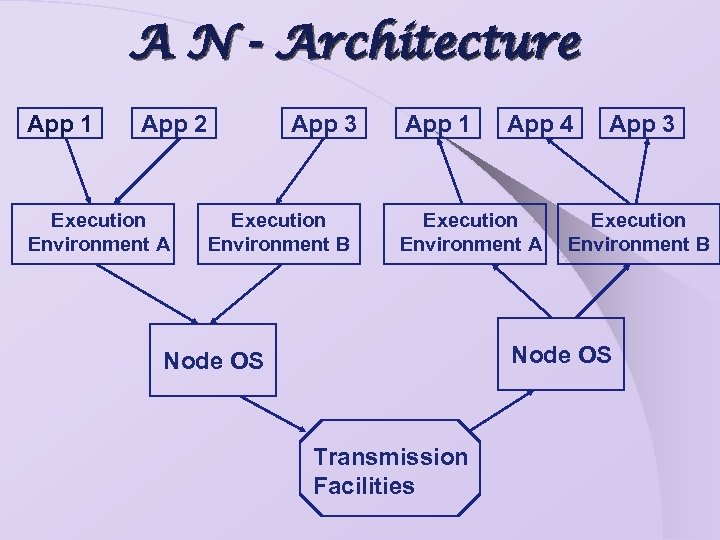
A N - Architecture App 1 App 2 Execution Environment A App 3 Execution Environment B App 1 App 4 Execution Environment A App 3 Execution Environment B Node OS Transmission Facilities
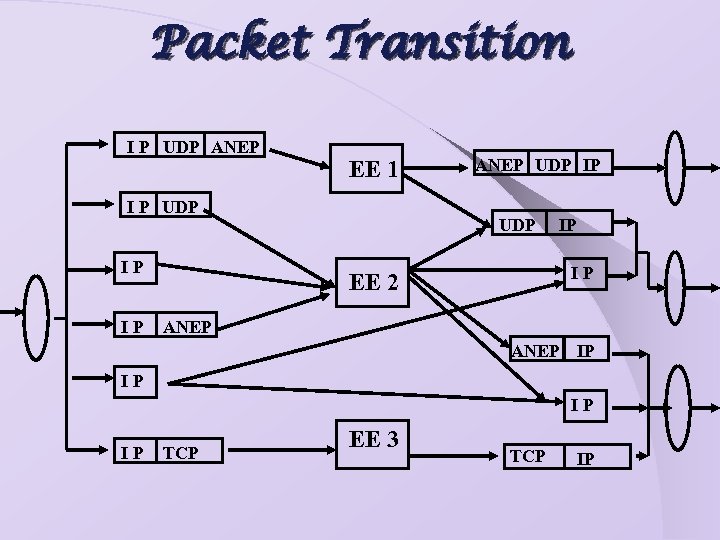
Packet Transition I P UDP ANEP EE 1 I P UDP IP IP ANEP UDP IP IP EE 2 ANEP IP IP TCP EE 3 TCP IP

Implementation Challenges Ø The network should be usable Ø The network should have high flexibility Ø The implementation should be secure Ø The network should have high performance

Killer Arguments Ø Efficiency Ø Resource Allocation Ø Security

Efficiency Hiccups: Ø Bandwidth demand is growing faster than CPU speed – bad idea to execute arbitrary programs on packets. Ø Most programming languages are interpreted – JAVA byte code, plain interpreter. Cure: ØDon’t propose AN for the core of the Internet. ØUse just-in-time compilation, native code. ØHybrid architectures (high speed AN!)

Resource Allocation Hiccups: Ø Fairness in queuing is a problem. Ø Cannot guarantee Qo. S. Ø Cannot control Looping packets. Cure: ØProvide distributed control (Scaling). Øresource reservation in advance, resource preemption. ØLimit capabilities of the active packet.

Security Ø Security cannot be limited to peripheral nodes. Ø Possible threats: Overload based Denial of Service Unauthorized access to the exposed control plane. Ø Secure Node doesn’t mean Secure Network.

Security at Node. OS Ø Security Enforcement through Authorizations. Ø Authorization policies are expressed in terms of Access Control Lists, which is a logical 3 - tuple of the form : <resource, user, permissions> Ø Node. OS has a security policy database and a policy enforcement engine.

Security at EE ØEach EE has it's own protection policy, possibly a security database and an enforcement engine. ØThe programming model that an EE supports must also be restricted to ensure network security. ØNo broad consensus on the division of responsibility for policy enforcement between the Node. OS and the EE.

Security in Switch. Ware Ø Uses ALIEN active loader. Ø Code Modules loaded on the fly. Ø Restricts access using namespaces. Ø Uses a language specification called CAML.

AN – APPLICATIONS Ø Network Management Ø Multicasting Ø Caching Ø Active Congestion Control Ø Security

Network Management ØNo polling required Ø"Patrol" and "first-aid" packets can track a problem and rectify it respectively. ØCode moved to node rather than data to management center Example: Delegated Management. Decentralization helps in scalability, reducing delays from responses and effective bandwidth utilization.

Multicasting Active internal nodes elegantly solve many current problems such as: Ø NACK implosion. Ø Concentrated load of retransmissions. ØDuplication of packets. Example: ARM Suppression of NACK & effective retransmission

Active Congestion Control Ø Selective dropping of units, packets or cells can be held very efficiently. Ø Multi-stream interaction. Example: APCI Backward compatibility with non-active nodes & on the fly routing employed.
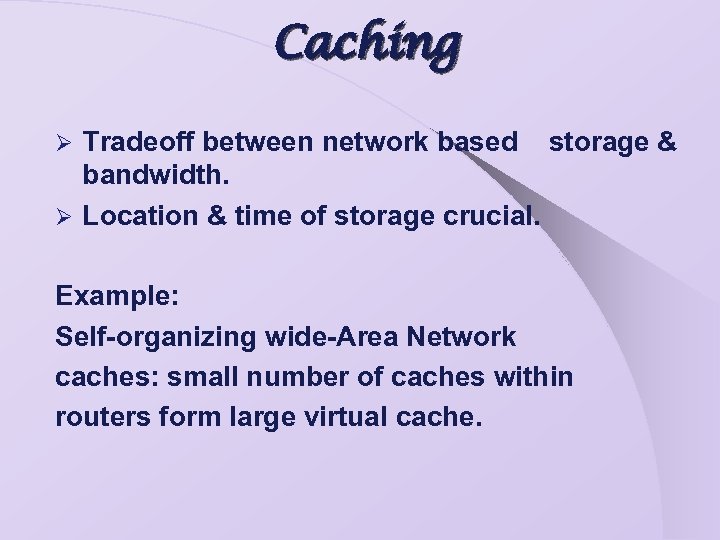
Caching Tradeoff between network based storage & bandwidth. Ø Location & time of storage crucial. Ø Example: Self-organizing wide-Area Network caches: small number of caches within routers form large virtual cache.

Security Ø Node – Packet conflict. Ø Node security by authentication of active packets & PCC(Proof Correct Code). Ø Packet security by Fault-tolerance & Encryption. Example: SANE

AN - Services Ø Ø Ø Video on Demand VPN Multimedia Conferencing Vo. IP / IP Telephony Active Firewalling
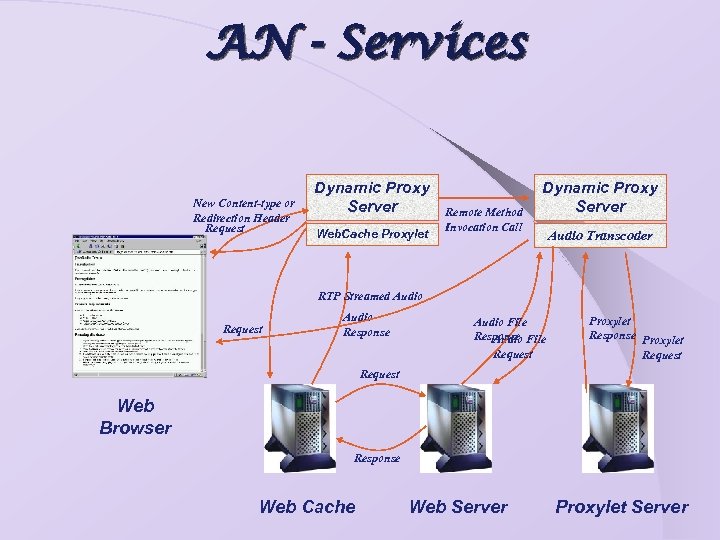
AN - Services New Content-type or Redirection Header Request Dynamic Proxy Server Web. Cache Proxylet Remote Method Invocation Call Dynamic Proxy Server Audio Transcoder RTP Streamed Audio Request Audio Response Audio File Response File Audio Request Proxylet Response Proxylet Request Web Browser Response Web Cache Web Server Proxylet Server

“Retrofitting" AN to IP The Active IP Option: Ø Option in the IP header alerts the router to look at the packet payload more closely. Active Network Encapsulation Protocol (ANEP): Ø Adds a header that directs the router.
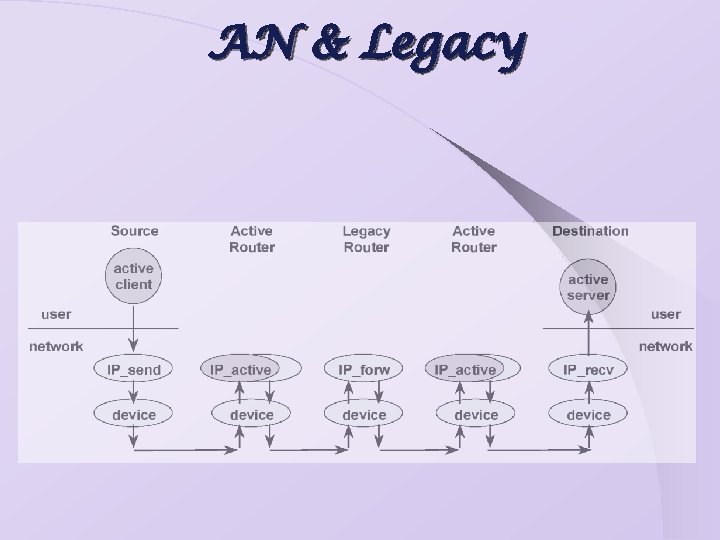
AN & Legacy

Smart. Packets – A Case Study Uses Capsule model: Code with IP packet ØPrograms must be completely self-contained. ØOperating environment provides security. Languages: Sprocket – A high level language Spanner – An assembly level language
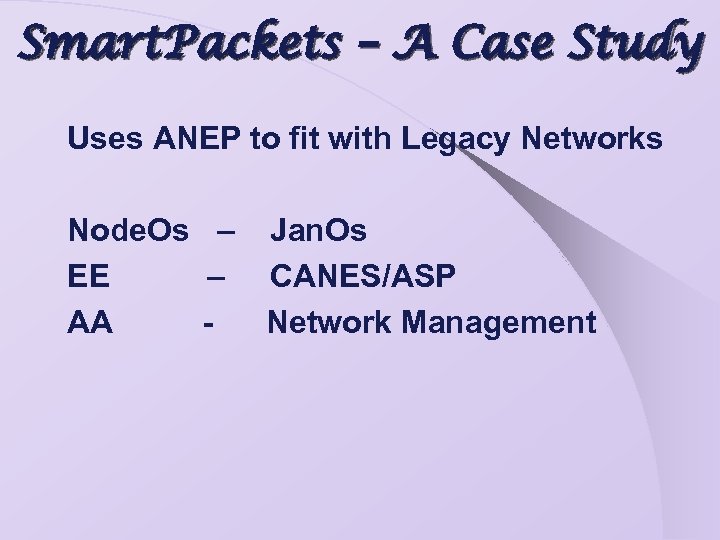
Smart. Packets – A Case Study Uses ANEP to fit with Legacy Networks Node. Os – Jan. Os EE – CANES/ASP AA Network Management

Smart. Packets – A Case Study Network Management Defines 4 types of packets: Ø Program Ø Data Ø Error Ø Message

Smart. Packets – A Case Study Security For Nodes: Ø Authentication of packet Ø Cryptographic hash of non-mutable fields For packets: Ø Redirection Ø Encryption

Smart. Packets – A Case Study Limitations Ø Packet size Ø Applications adaptability Scope Extending for other applications

Current Work Ø Ø Ø Ø Ø Active Nets at DARPA Active. Nets at MIT ANTS at Washington Switch. Ware at UPenn JANOS & OSkit at Utah Liquid Software at Arizona Panda at UCLA Net. Script at Columbia CANES at Georgia Tech Smart Packets at BBN

Conclusion Is Active Network really the future ?

References Darpa http: //www. darpa. mil/ito/psum 1999/J 044 -0. html Switchware http: //www. cis. upenn. edu/~switchware/ CANES http: //www. cc. gatech. edu/projects/canes/ www. ieee. org www. citeseer. com
db7df02f0b56f1b3bbb69937a47ff79b.ppt