2bac00959103cb30f28a21cb94f5721f.ppt
- Количество слайдов: 22

Active Directory and NT Kerberos Rooster JD Glaser

Introduction to NT Kerberos v 5 • • • What is NT Kerberos? How is it different from NTLM NT Kerberos vs MIT Kerberos Delegation and Client Authentication What does NT Kerberos look like on the wire? KTNet - A native NT Kerberos telnet server

What is NT Kerberos • NT’s new authentication system • MIT Kerberos v 5 - an Open Standard • Kerberos is the default authenticator in W 2 K domains • NTLM still used for compatibility – usually the weakest version

How is it different from NTLM • • Doesn’t use a password hash system Requires fewer authentication calls More sophisticated - Yes More secure? - Possibly in pure mode – Backwards compatibility hinders it – NTLM v 2 is strong in pure mode as well

NT Kerberos • Integrated with platform • Locates KDC via DNS - DNS server required for install • No support for DCE style cross-realm trust • No “raw” krb 5 API • Postdated tickets (not implemented) • Uses authdata field in ticket

Windows 2000 Kerberos standards • RFC-1510 • Kerberos change password protocol Kerberos set password protocol RC 4 -HMAC Kerberos Encryption type • PKINIT
Kerberos Interoperability Scenarios • Kerberos clients in a Win 2000 domain • Kerberos servers in a Win 2000 domain • Standalone Win 2000 systems in a Kerberos realm • Using a Kerberos realm as a resource domain • Using a Kerberos realm as an account domain
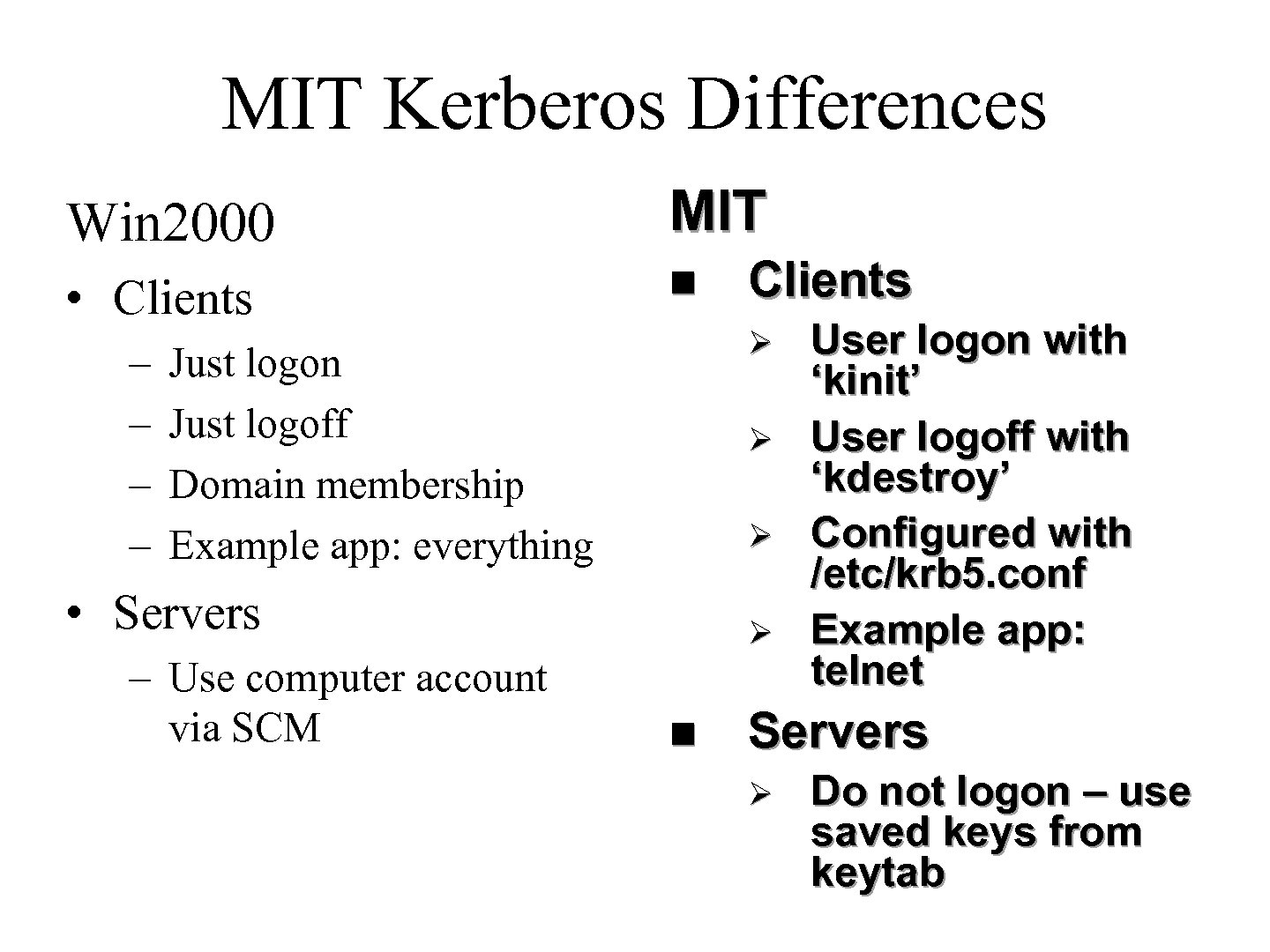
MIT Kerberos Differences Win 2000 MIT • Clients n – – Ø Just logon Just logoff Domain membership Example app: everything Ø Ø • Servers – Use computer account via SCM Clients Ø n User logon with ‘kinit’ User logoff with ‘kdestroy’ Configured with /etc/krb 5. conf Example app: telnet Servers Ø Do not logon – use saved keys from keytab
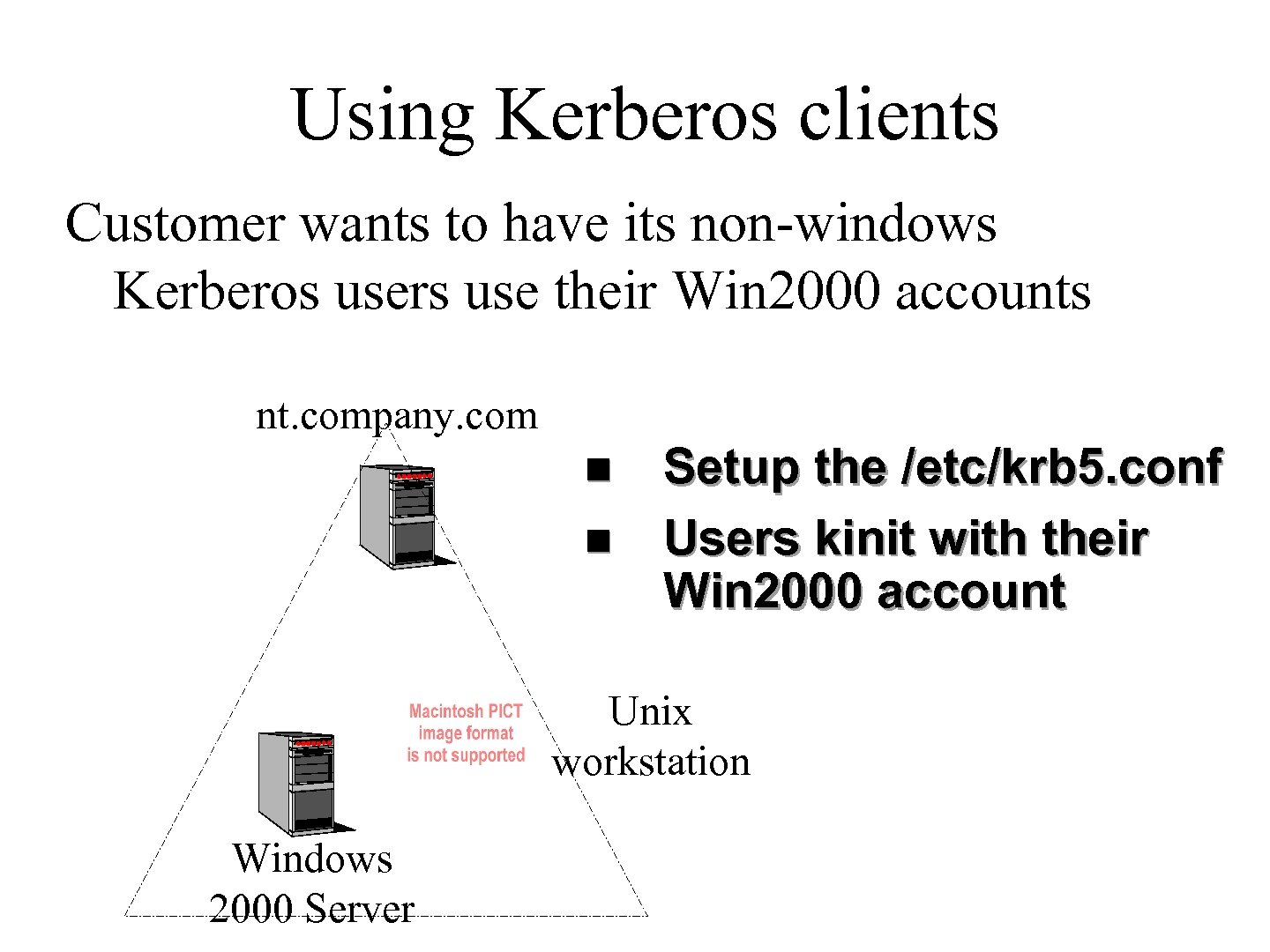
Using Kerberos clients Customer wants to have its non-windows Kerberos users use their Win 2000 accounts nt. company. com n n Setup the /etc/krb 5. conf Users kinit with their Win 2000 account Unix workstation Windows 2000 Server
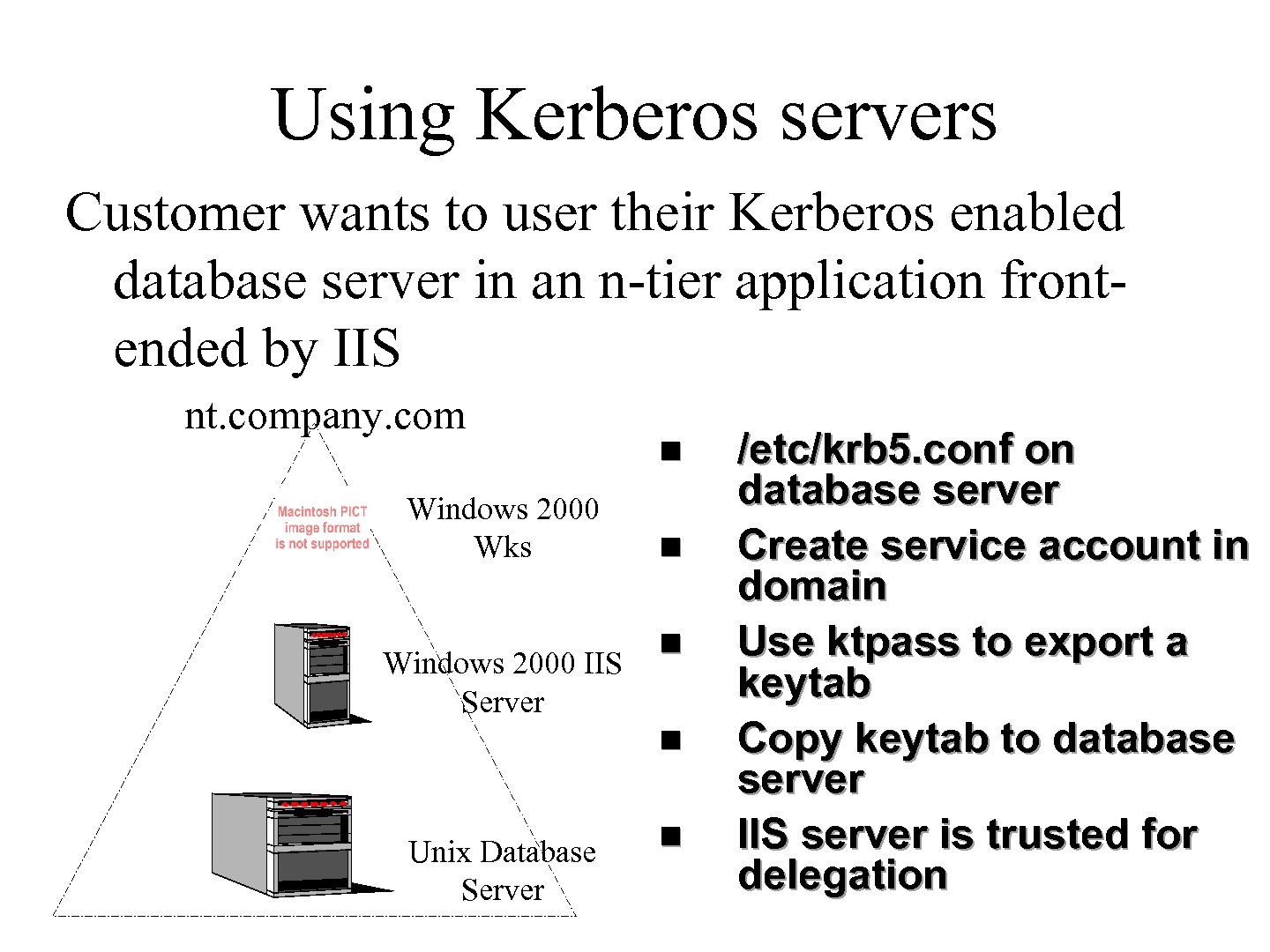
Using Kerberos servers Customer wants to user their Kerberos enabled database server in an n-tier application frontended by IIS nt. company. com Windows 2000 Wks Windows 2000 IIS Server n n Unix Database Server n /etc/krb 5. conf on database server Create service account in domain Use ktpass to export a keytab Copy keytab to database server IIS server is trusted for delegation
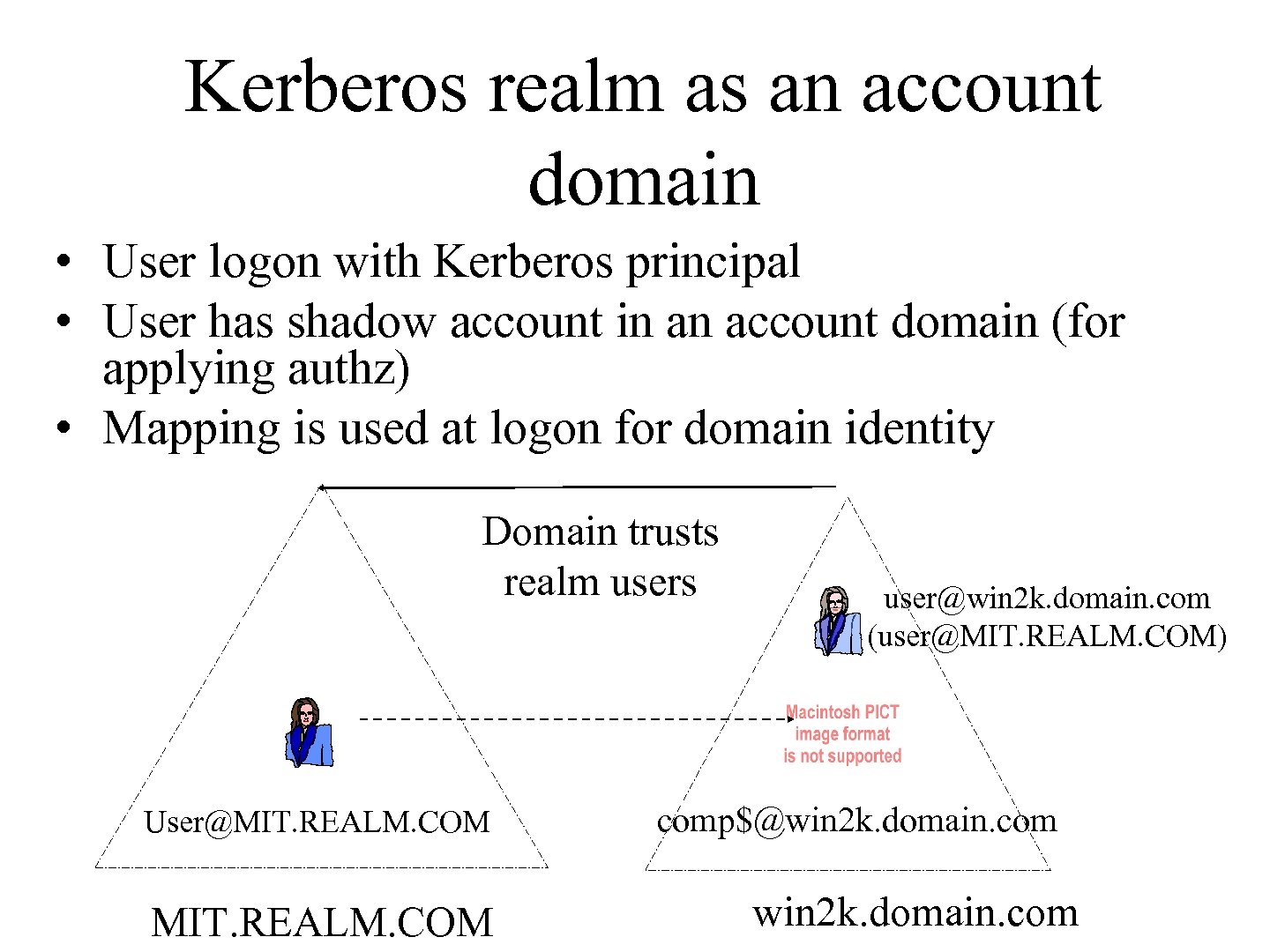
Kerberos realm as an account domain • User logon with Kerberos principal • User has shadow account in an account domain (for applying authz) • Mapping is used at logon for domain identity Domain trusts realm users User@MIT. REALM. COM user@win 2 k. domain. com (user@MIT. REALM. COM) comp$@win 2 k. domain. com
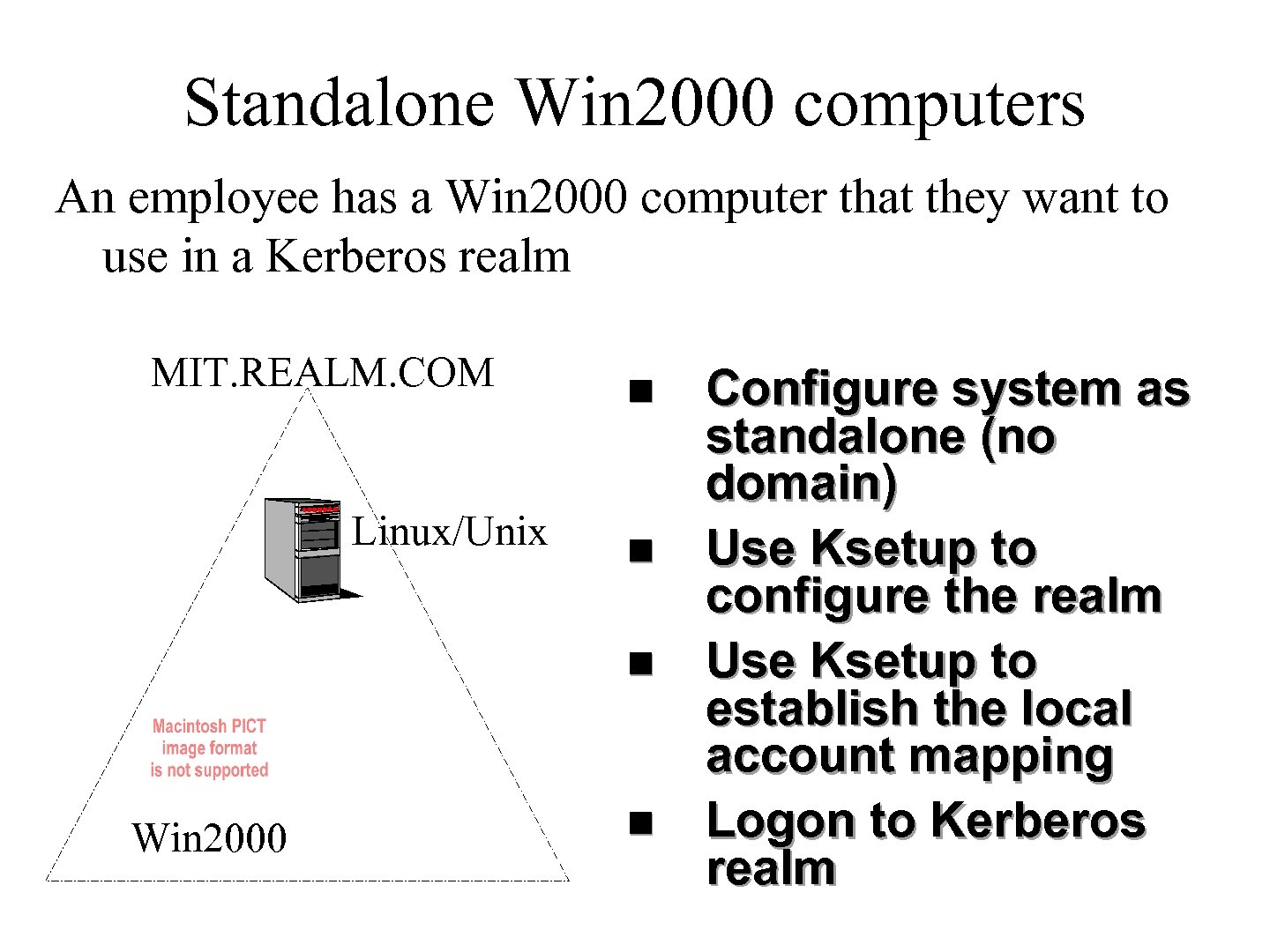
Standalone Win 2000 computers An employee has a Win 2000 computer that they want to use in a Kerberos realm MIT. REALM. COM Linux/Unix n n n Win 2000 n Configure system as standalone (no domain) Use Ksetup to configure the realm Use Ksetup to establish the local account mapping Logon to Kerberos realm

Trusting a Kerberos realm • Win 2000 users accessing services in Kerberos realms • Kerberos users accessing services in domains
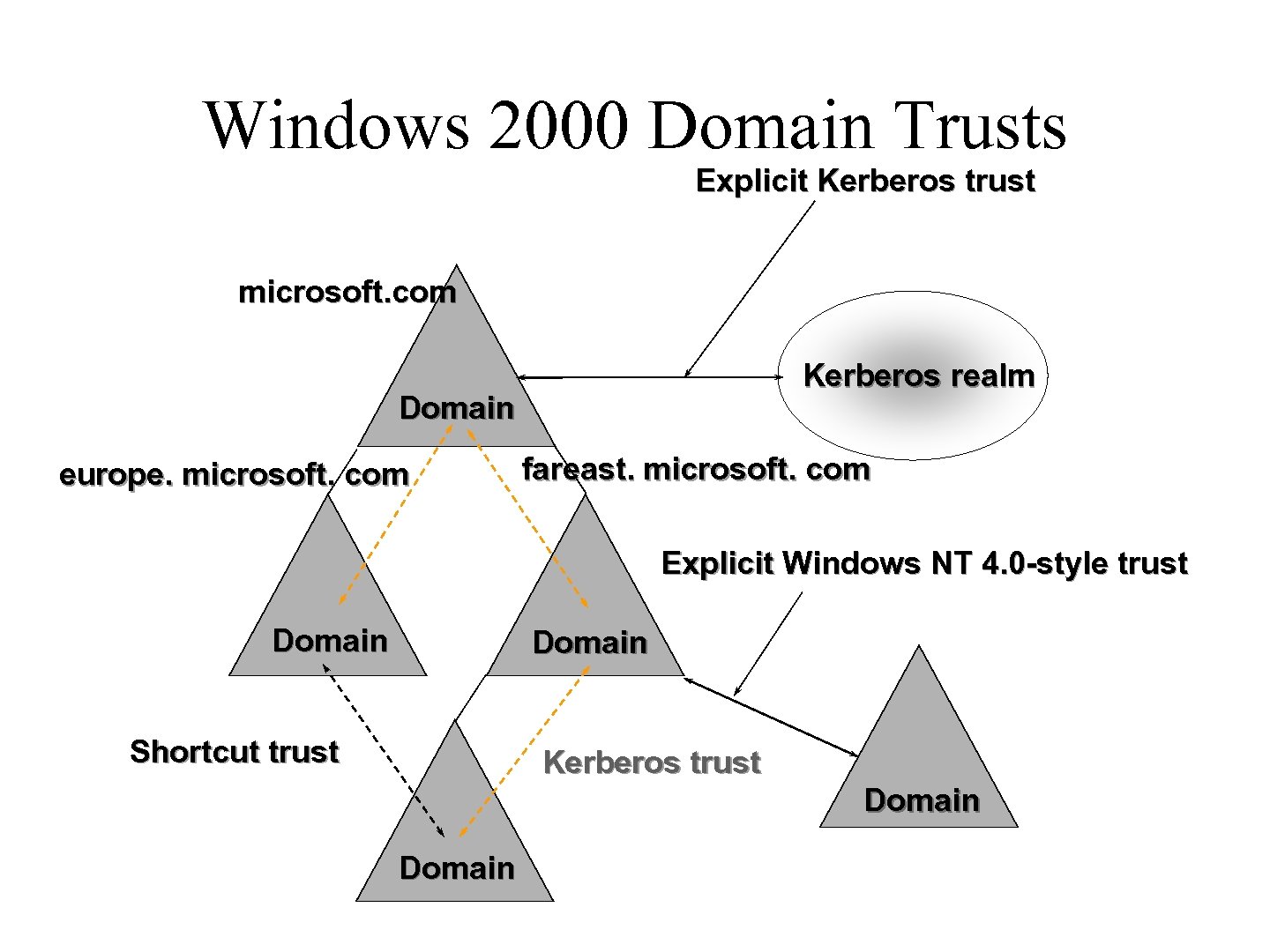
Windows 2000 Domain Trusts Explicit Kerberos trust microsoft. com Kerberos realm Domain europe. microsoft. com fareast. microsoft. com Explicit Windows NT 4. 0 -style trust Domain Shortcut trust Kerberos trust Domain
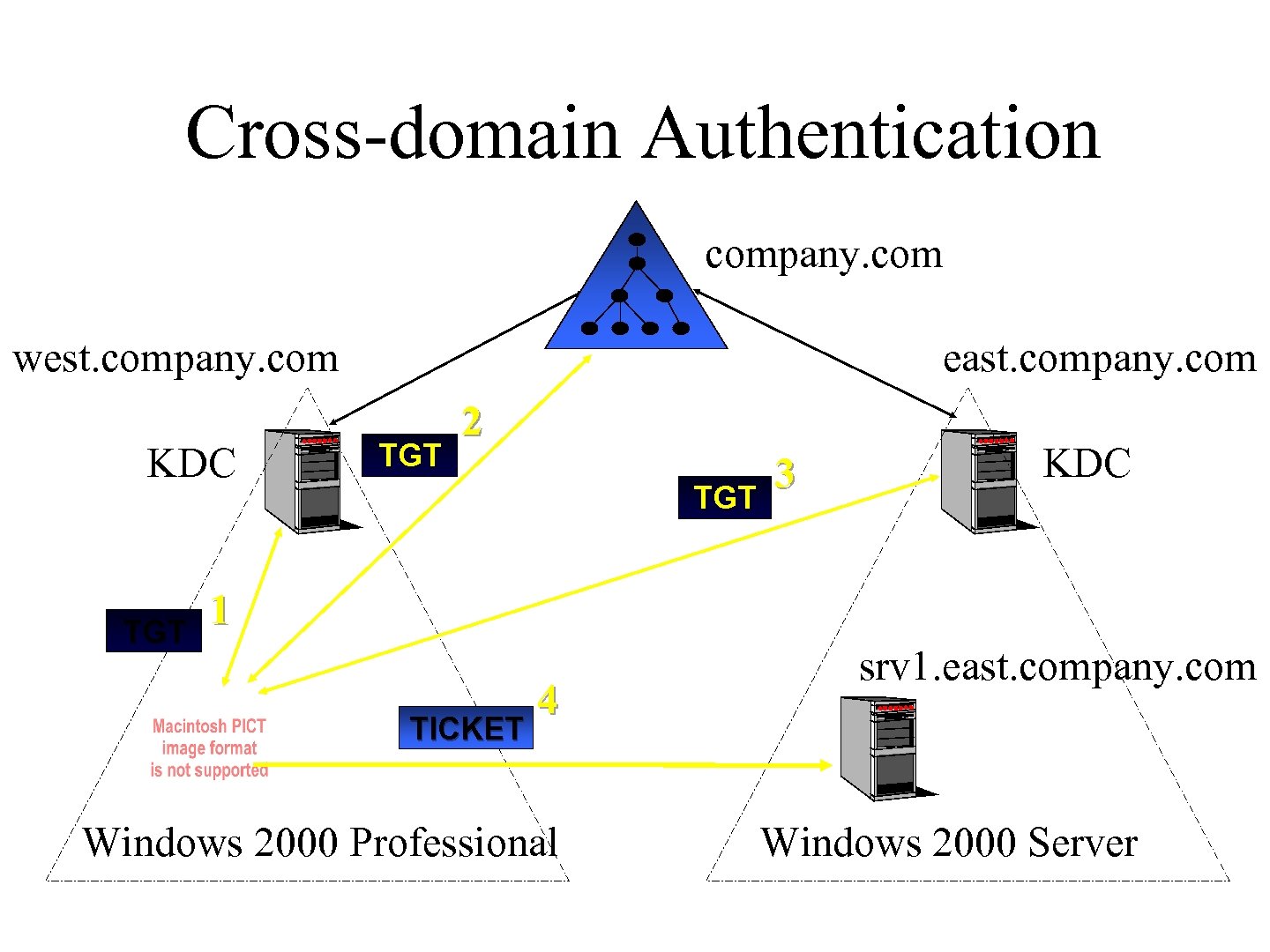
Cross-domain Authentication company. com west. company. com KDC TGT east. company. com TGT 2 TGT 3 KDC 1 TICKET 4 Windows 2000 Professional srv 1. east. company. com Windows 2000 Server
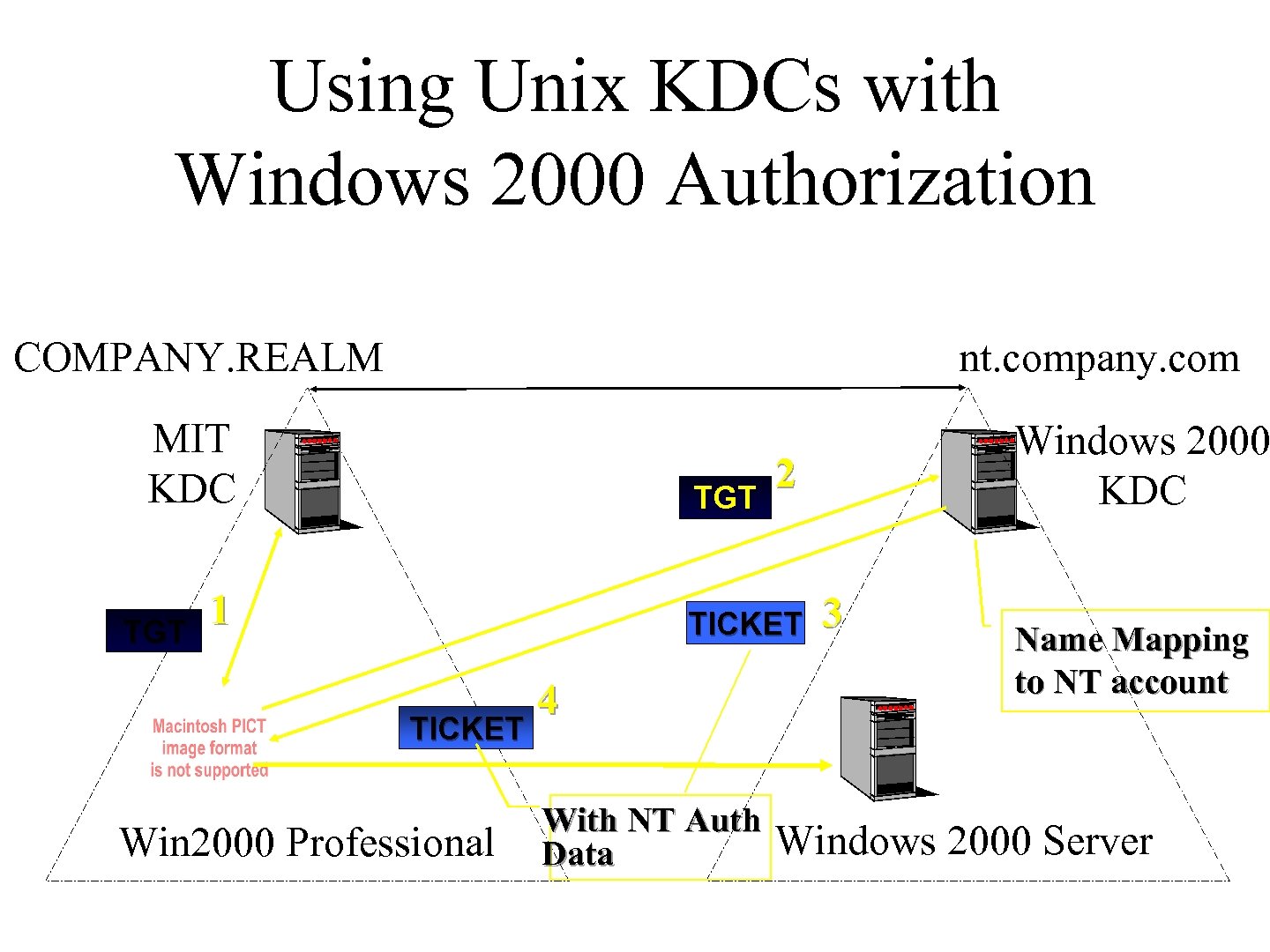
Using Unix KDCs with Windows 2000 Authorization COMPANY. REALM nt. company. com MIT KDC TGT 1 2 TICKET Win 2000 Professional 4 With NT Auth Data Windows 2000 KDC 3 Name Mapping to NT account Windows 2000 Server

NT Kerberos vs MIT Kerberos • NT caches the password for ticket renewal • It’s not certain whether NT uses ticket caching tracking stolen ‘replay’ tickets
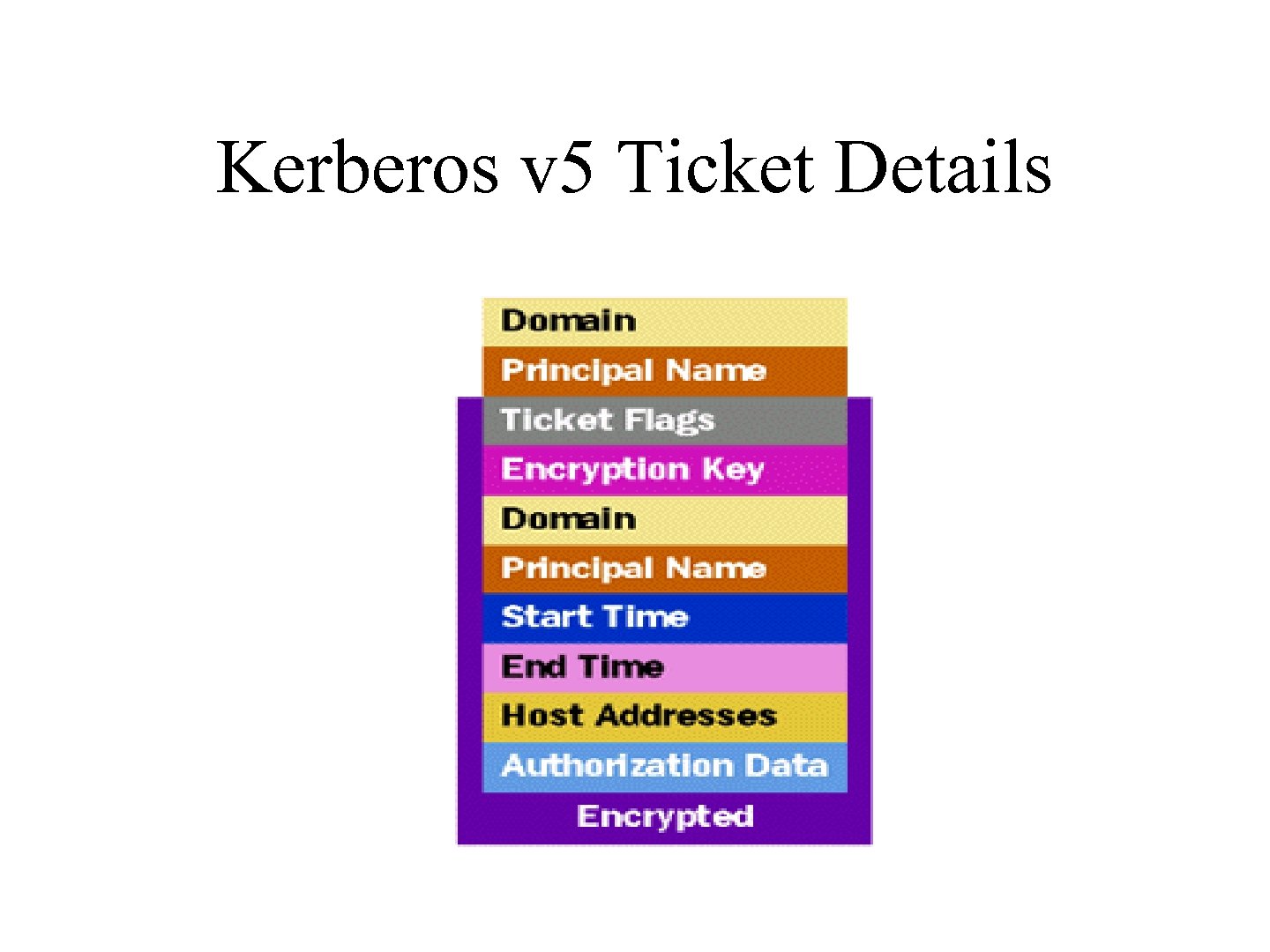
Kerberos v 5 Ticket Details
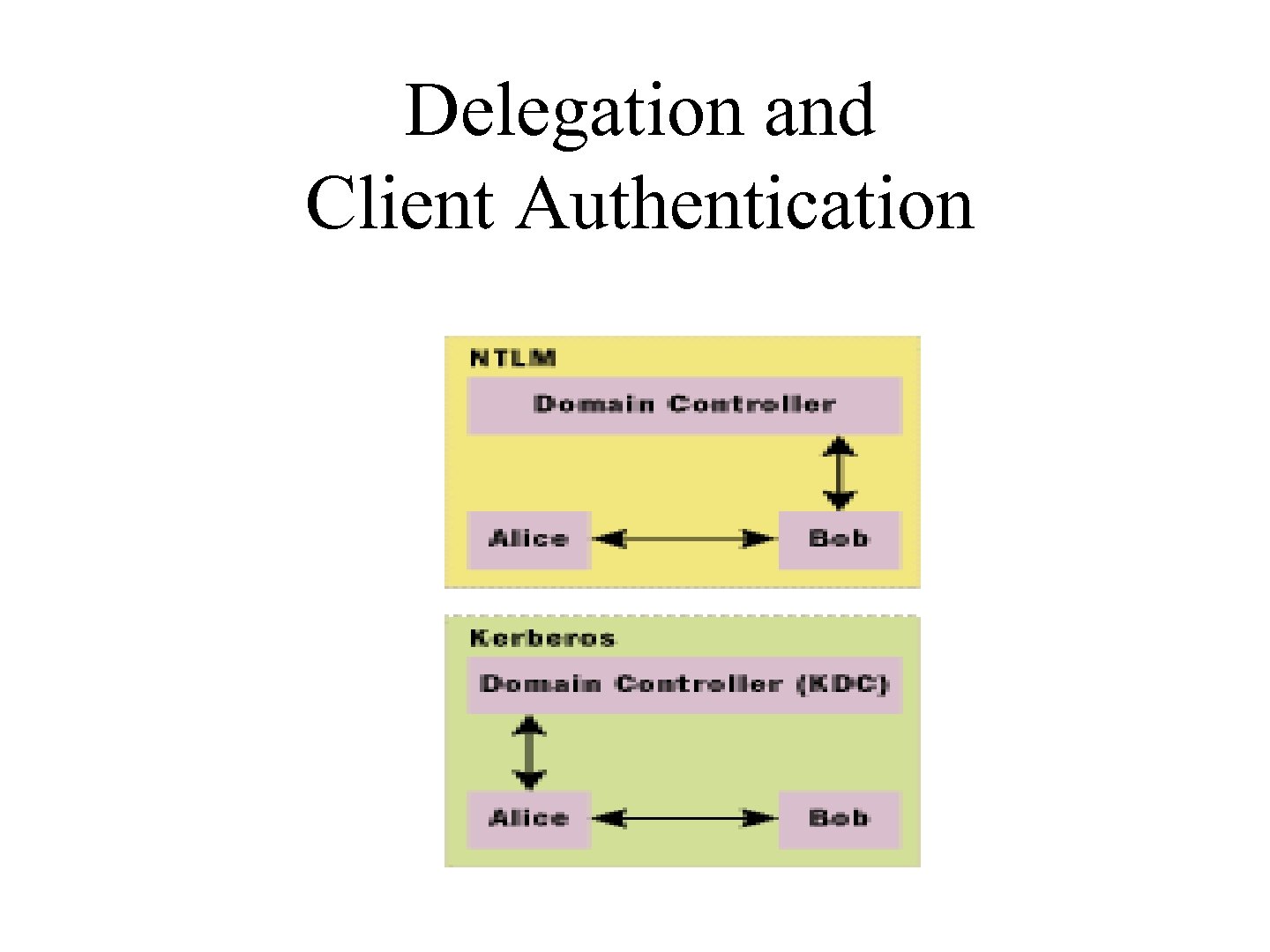
Delegation and Client Authentication

NT Kerberos On The Wire

Thank you Rooster, rooster@attrition. org JD Glaser, jd. glaser@foundstone. com

Appendix • John Brezak, PM - Microsoft – Kerberos Talk - MTB ‘ 99
2bac00959103cb30f28a21cb94f5721f.ppt