3136434a40a1db5f3a8fe66814a57501.ppt
- Количество слайдов: 39
 ACCOUNTING TECHNIQUES USED IN A FRAUD INVESTIGATION Mary Anne Basilone, CPA, CFE, MMT, MA Diane A. Matthews, Ph. D, CPA/CFF, CFE Carlow University Master of Science in Fraud & Forensics Bachelor of Science in Forensic Accounting Bachelor of Science in Accounting 1
ACCOUNTING TECHNIQUES USED IN A FRAUD INVESTIGATION Mary Anne Basilone, CPA, CFE, MMT, MA Diane A. Matthews, Ph. D, CPA/CFF, CFE Carlow University Master of Science in Fraud & Forensics Bachelor of Science in Forensic Accounting Bachelor of Science in Accounting 1
 TOPICS COVERED l INVESTIGATIVE l METHODS METHODOLOGY OF PROOF DIRECT l INDIRECT l l DIGITAL ANALYSIS TECHNIQUES 2
TOPICS COVERED l INVESTIGATIVE l METHODS METHODOLOGY OF PROOF DIRECT l INDIRECT l l DIGITAL ANALYSIS TECHNIQUES 2
 METHODOLOGY OVERVIEW STEPS IN CONDUCTING A COMPREHENSIVE FRAUD INVESTIGATION 3
METHODOLOGY OVERVIEW STEPS IN CONDUCTING A COMPREHENSIVE FRAUD INVESTIGATION 3
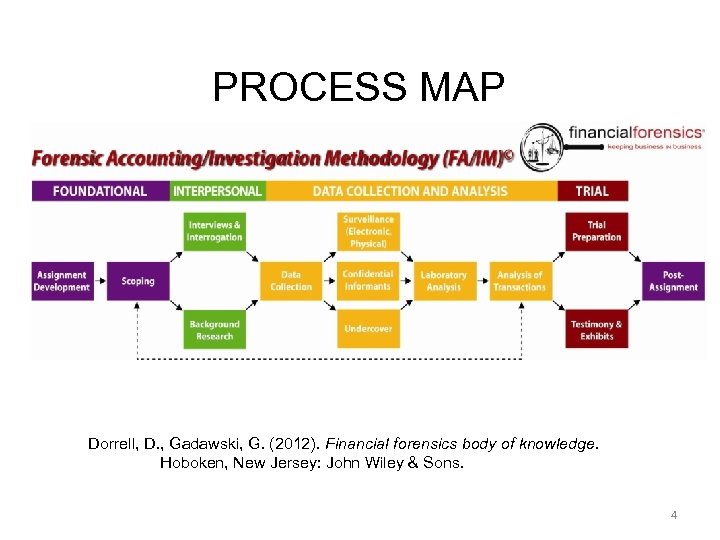 PROCESS MAP Dorrell, D. , Gadawski, G. (2012). Financial forensics body of knowledge. Hoboken, New Jersey: John Wiley & Sons. 4
PROCESS MAP Dorrell, D. , Gadawski, G. (2012). Financial forensics body of knowledge. Hoboken, New Jersey: John Wiley & Sons. 4
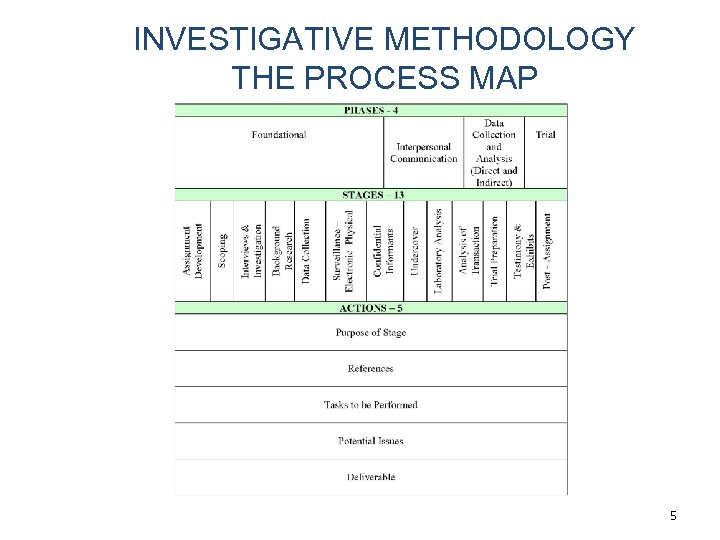 INVESTIGATIVE METHODOLOGY THE PROCESS MAP 5
INVESTIGATIVE METHODOLOGY THE PROCESS MAP 5
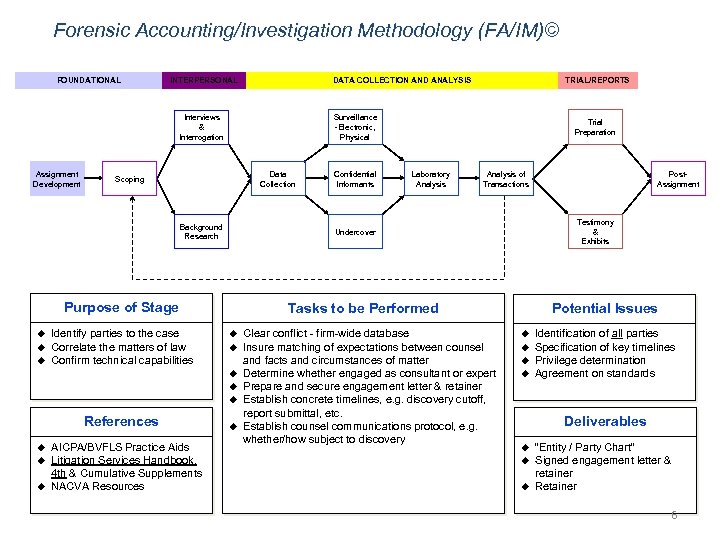 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Identify parties to the case Correlate the matters of law Confirm technical capabilities u u u u AICPA/BVFLS Practice Aids Litigation Services Handbook, 4 th & Cumulative Supplements NACVA Resources Laboratory Analysis of Transactions u Clear conflict - firm-wide database Insure matching of expectations between counsel and facts and circumstances of matter Determine whether engaged as consultant or expert Prepare and secure engagement letter & retainer Establish concrete timelines, e. g. discovery cutoff, report submittal, etc. Establish counsel communications protocol, e. g. whether/how subject to discovery Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Identification of all parties Specification of key timelines Privilege determination Agreement on standards Deliverables u u u “Entity / Party Chart” Signed engagement letter & retainer Retainer 6
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Identify parties to the case Correlate the matters of law Confirm technical capabilities u u u u AICPA/BVFLS Practice Aids Litigation Services Handbook, 4 th & Cumulative Supplements NACVA Resources Laboratory Analysis of Transactions u Clear conflict - firm-wide database Insure matching of expectations between counsel and facts and circumstances of matter Determine whether engaged as consultant or expert Prepare and secure engagement letter & retainer Establish concrete timelines, e. g. discovery cutoff, report submittal, etc. Establish counsel communications protocol, e. g. whether/how subject to discovery Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Identification of all parties Specification of key timelines Privilege determination Agreement on standards Deliverables u u u “Entity / Party Chart” Signed engagement letter & retainer Retainer 6
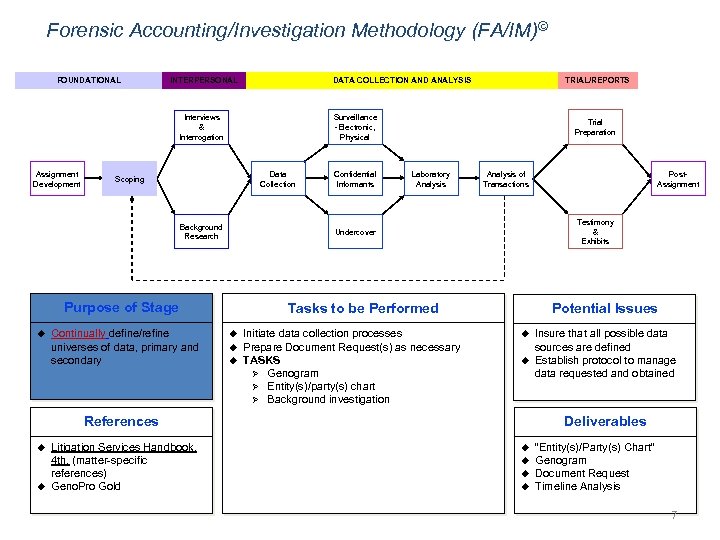 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Continually define/refine universes of data, primary and secondary Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u u Initiate data collection processes Prepare Document Request(s) as necessary TASKS Ø Genogram Ø Entity(s)/party(s) chart Ø Background investigation u u References u u Litigation Services Handbook, 4 th, (matter-specific references) Geno. Pro Gold Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS Insure that all possible data sources are defined Establish protocol to manage data requested and obtained Deliverables u u “Entity(s)/Party(s) Chart” Genogram Document Request Timeline Analysis 7
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Continually define/refine universes of data, primary and secondary Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u u Initiate data collection processes Prepare Document Request(s) as necessary TASKS Ø Genogram Ø Entity(s)/party(s) chart Ø Background investigation u u References u u Litigation Services Handbook, 4 th, (matter-specific references) Geno. Pro Gold Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS Insure that all possible data sources are defined Establish protocol to manage data requested and obtained Deliverables u u “Entity(s)/Party(s) Chart” Genogram Document Request Timeline Analysis 7
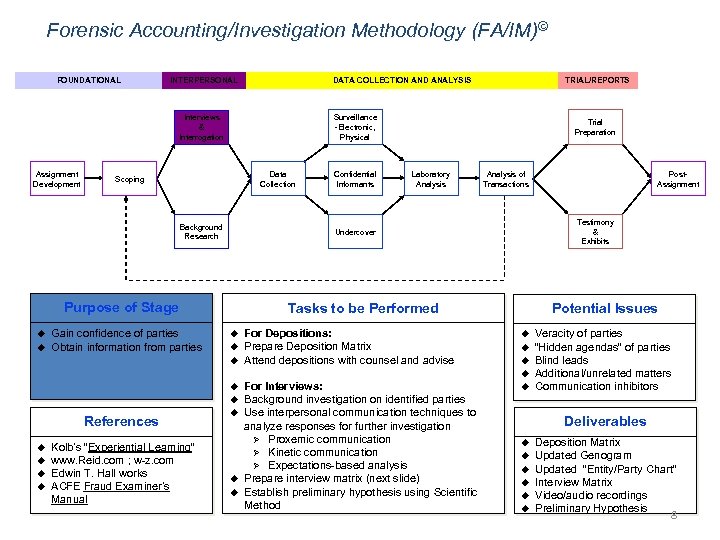 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Gain confidence of parties Obtain information from parties Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u u For Depositions: Prepare Deposition Matrix Attend depositions with counsel and advise u u u References u u Kolb’s “Experiential Learning” www. Reid. com ; w-z. com Edwin T. Hall works ACFE Fraud Examiner’s Manual u u u For Interviews: Background investigation on identified parties Use interpersonal communication techniques to analyze responses for further investigation Ø Proxemic communication Ø Kinetic communication Ø Expectations-based analysis Prepare interview matrix (next slide) Establish preliminary hypothesis using Scientific Method Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS u Veracity of parties “Hidden agendas” of parties Blind leads Additional/unrelated matters Communication inhibitors Deliverables u u u Deposition Matrix Updated Genogram Updated “Entity/Party Chart” Interview Matrix Video/audio recordings Preliminary Hypothesis 8
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Gain confidence of parties Obtain information from parties Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u u For Depositions: Prepare Deposition Matrix Attend depositions with counsel and advise u u u References u u Kolb’s “Experiential Learning” www. Reid. com ; w-z. com Edwin T. Hall works ACFE Fraud Examiner’s Manual u u u For Interviews: Background investigation on identified parties Use interpersonal communication techniques to analyze responses for further investigation Ø Proxemic communication Ø Kinetic communication Ø Expectations-based analysis Prepare interview matrix (next slide) Establish preliminary hypothesis using Scientific Method Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS u Veracity of parties “Hidden agendas” of parties Blind leads Additional/unrelated matters Communication inhibitors Deliverables u u u Deposition Matrix Updated Genogram Updated “Entity/Party Chart” Interview Matrix Video/audio recordings Preliminary Hypothesis 8
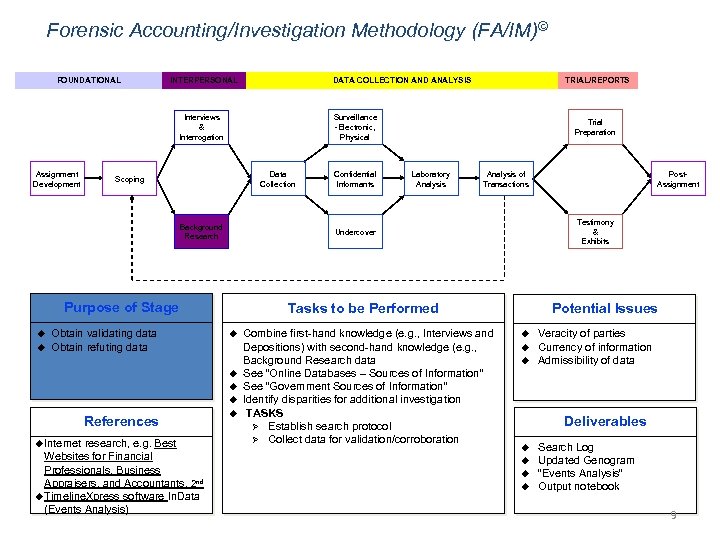 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain validating data Obtain refuting data u u Internet research, e. g. Best Websites for Financial Professionals, Business Appraisers, and Accountants, 2 nd u Timeline. Xpress software In. Data (Events Analysis) Laboratory Analysis of Transactions u Combine first-hand knowledge (e. g. , Interviews and Depositions) with second-hand knowledge (e. g. , Background Research data See “Online Databases – Sources of Information” See “Government Sources of Information” Identify disparities for additional investigation TASKS Ø Establish search protocol Ø Collect data for validation/corroboration Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Veracity of parties Currency of information Admissibility of data Deliverables u u Search Log Updated Genogram “Events Analysis” Output notebook 9
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain validating data Obtain refuting data u u Internet research, e. g. Best Websites for Financial Professionals, Business Appraisers, and Accountants, 2 nd u Timeline. Xpress software In. Data (Events Analysis) Laboratory Analysis of Transactions u Combine first-hand knowledge (e. g. , Interviews and Depositions) with second-hand knowledge (e. g. , Background Research data See “Online Databases – Sources of Information” See “Government Sources of Information” Identify disparities for additional investigation TASKS Ø Establish search protocol Ø Collect data for validation/corroboration Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Veracity of parties Currency of information Admissibility of data Deliverables u u Search Log Updated Genogram “Events Analysis” Output notebook 9
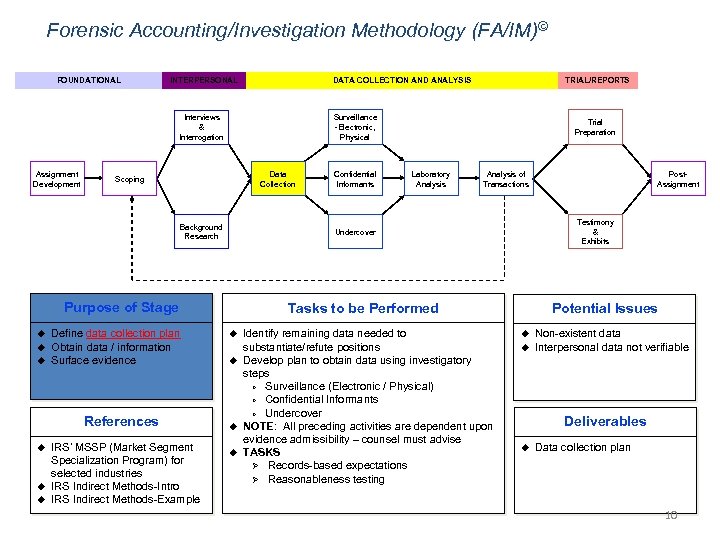 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Define data collection plan Obtain data / information Surface evidence References u u u IRS’ MSSP (Market Segment Specialization Program) for selected industries IRS Indirect Methods-Intro IRS Indirect Methods-Example Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u Identify remaining data needed to substantiate/refute positions Develop plan to obtain data using investigatory steps Ø Surveillance (Electronic / Physical) Ø Confidential Informants Ø Undercover NOTE: All preceding activities are dependent upon evidence admissibility – counsel must advise TASKS Ø Records-based expectations Ø Reasonableness testing Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS u u Non-existent data Interpersonal data not verifiable Deliverables u Data collection plan 10
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Define data collection plan Obtain data / information Surface evidence References u u u IRS’ MSSP (Market Segment Specialization Program) for selected industries IRS Indirect Methods-Intro IRS Indirect Methods-Example Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u Identify remaining data needed to substantiate/refute positions Develop plan to obtain data using investigatory steps Ø Surveillance (Electronic / Physical) Ø Confidential Informants Ø Undercover NOTE: All preceding activities are dependent upon evidence admissibility – counsel must advise TASKS Ø Records-based expectations Ø Reasonableness testing Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS u u Non-existent data Interpersonal data not verifiable Deliverables u Data collection plan 10
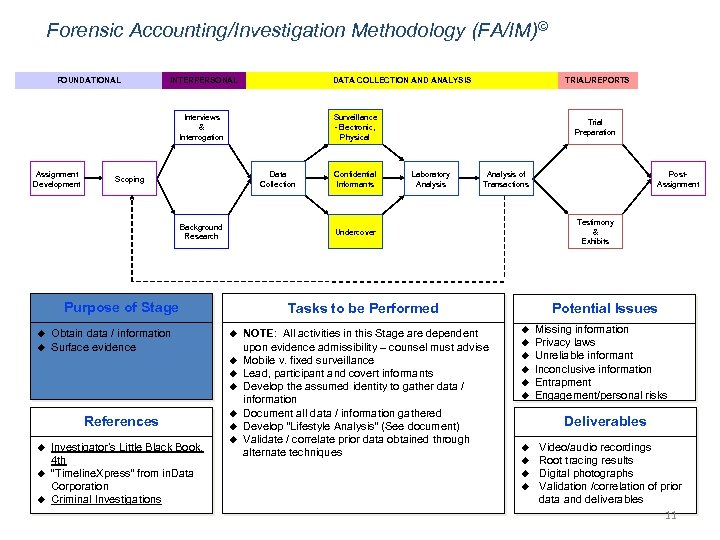 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain data / information Surface evidence u u u Investigator’s Little Black Book, 4 th “Timeline. Xpress” from in. Data Corporation Criminal Investigations Laboratory Analysis of Transactions u u u NOTE: All activities in this Stage are dependent upon evidence admissibility – counsel must advise Mobile v. fixed surveillance Lead, participant and covert informants Develop the assumed identity to gather data / information Document all data / information gathered Develop “Lifestyle Analysis” (See document) Validate / correlate prior data obtained through alternate techniques Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Missing information Privacy laws Unreliable informant Inconclusive information Entrapment Engagement/personal risks Deliverables u u Video/audio recordings Root tracing results Digital photographs Validation /correlation of prior data and deliverables 11
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain data / information Surface evidence u u u Investigator’s Little Black Book, 4 th “Timeline. Xpress” from in. Data Corporation Criminal Investigations Laboratory Analysis of Transactions u u u NOTE: All activities in this Stage are dependent upon evidence admissibility – counsel must advise Mobile v. fixed surveillance Lead, participant and covert informants Develop the assumed identity to gather data / information Document all data / information gathered Develop “Lifestyle Analysis” (See document) Validate / correlate prior data obtained through alternate techniques Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Missing information Privacy laws Unreliable informant Inconclusive information Entrapment Engagement/personal risks Deliverables u u Video/audio recordings Root tracing results Digital photographs Validation /correlation of prior data and deliverables 11
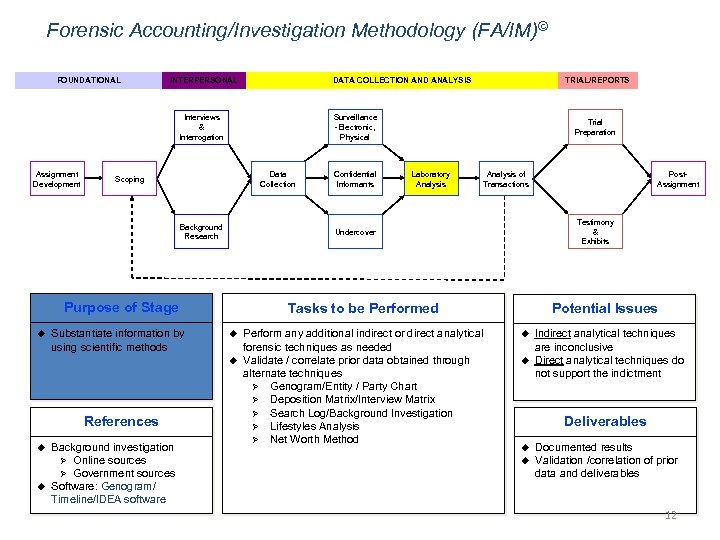 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Substantiate information by using scientific methods u u Background investigation Ø Online sources Ø Government sources Software: Genogram/ Timeline/IDEA software Laboratory Analysis of Transactions u Perform any additional indirect or direct analytical forensic techniques as needed Validate / correlate prior data obtained through alternate techniques Ø Genogram/Entity / Party Chart Ø Deposition Matrix/Interview Matrix Ø Search Log/Background Investigation Ø Lifestyles Analysis Ø Net Worth Method Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Indirect analytical techniques are inconclusive Direct analytical techniques do not support the indictment Deliverables u u Documented results Validation /correlation of prior data and deliverables 12
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Substantiate information by using scientific methods u u Background investigation Ø Online sources Ø Government sources Software: Genogram/ Timeline/IDEA software Laboratory Analysis of Transactions u Perform any additional indirect or direct analytical forensic techniques as needed Validate / correlate prior data obtained through alternate techniques Ø Genogram/Entity / Party Chart Ø Deposition Matrix/Interview Matrix Ø Search Log/Background Investigation Ø Lifestyles Analysis Ø Net Worth Method Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Indirect analytical techniques are inconclusive Direct analytical techniques do not support the indictment Deliverables u u Documented results Validation /correlation of prior data and deliverables 12
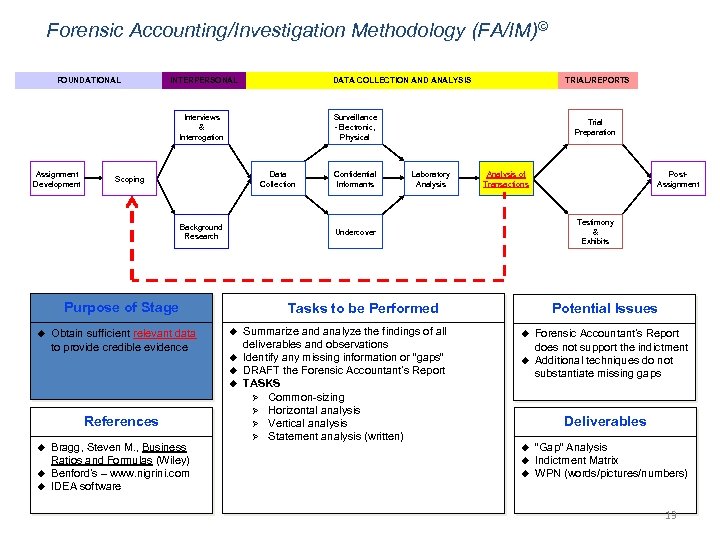 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Obtain sufficient relevant data to provide credible evidence u u u Bragg, Steven M. , Business Ratios and Formulas (Wiley) Benford’s – www. nigrini. com IDEA software Laboratory Analysis of Transactions Summarize and analyze the findings of all deliverables and observations Identify any missing information or “gaps” DRAFT the Forensic Accountant’s Report TASKS Ø Common-sizing Ø Horizontal analysis Ø Vertical analysis Ø Statement analysis (written) Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Forensic Accountant’s Report does not support the indictment Additional techniques do not substantiate missing gaps Deliverables u u u “Gap” Analysis Indictment Matrix WPN (words/pictures/numbers) 13
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Obtain sufficient relevant data to provide credible evidence u u u Bragg, Steven M. , Business Ratios and Formulas (Wiley) Benford’s – www. nigrini. com IDEA software Laboratory Analysis of Transactions Summarize and analyze the findings of all deliverables and observations Identify any missing information or “gaps” DRAFT the Forensic Accountant’s Report TASKS Ø Common-sizing Ø Horizontal analysis Ø Vertical analysis Ø Statement analysis (written) Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Forensic Accountant’s Report does not support the indictment Additional techniques do not substantiate missing gaps Deliverables u u u “Gap” Analysis Indictment Matrix WPN (words/pictures/numbers) 13
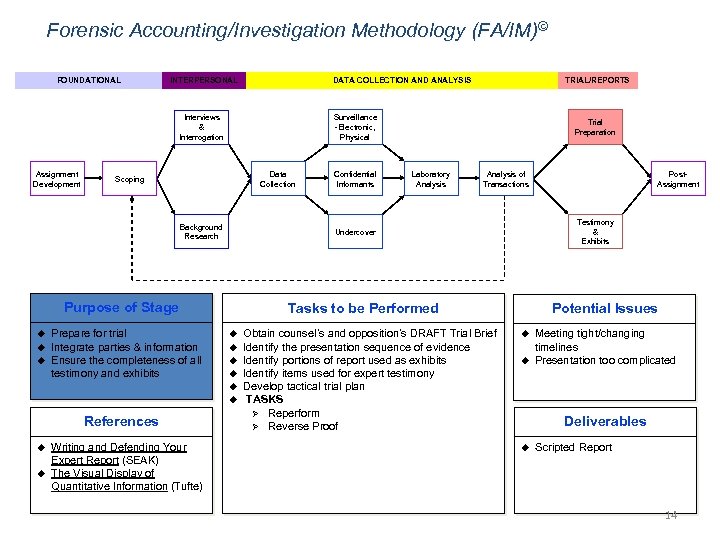 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Prepare for trial Integrate parties & information Ensure the completeness of all testimony and exhibits u u u u Writing and Defending Your Expert Report (SEAK) The Visual Display of Quantitative Information (Tufte) Laboratory Analysis of Transactions Obtain counsel’s and opposition’s DRAFT Trial Brief Identify the presentation sequence of evidence Identify portions of report used as exhibits Identify items used for expert testimony Develop tactical trial plan TASKS Ø Reperform Ø Reverse Proof Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Meeting tight/changing timelines Presentation too complicated Deliverables u Scripted Report 14
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u u Prepare for trial Integrate parties & information Ensure the completeness of all testimony and exhibits u u u u Writing and Defending Your Expert Report (SEAK) The Visual Display of Quantitative Information (Tufte) Laboratory Analysis of Transactions Obtain counsel’s and opposition’s DRAFT Trial Brief Identify the presentation sequence of evidence Identify portions of report used as exhibits Identify items used for expert testimony Develop tactical trial plan TASKS Ø Reperform Ø Reverse Proof Post. Assignment Testimony & Exhibits Potential Issues Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u Meeting tight/changing timelines Presentation too complicated Deliverables u Scripted Report 14
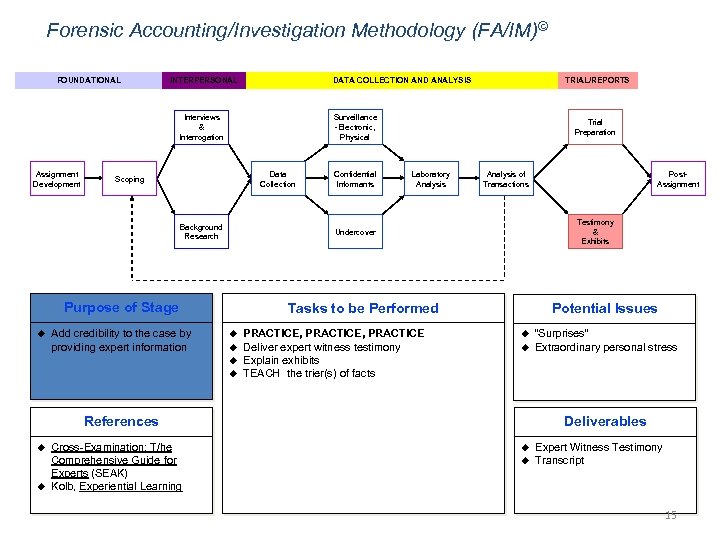 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Add credibility to the case by providing expert information Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u PRACTICE, PRACTICE Deliver expert witness testimony Explain exhibits TEACH the trier(s) of facts u u References u u Cross-Examination: T/he Comprehensive Guide for Experts (SEAK) Kolb, Experiential Learning Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS “Surprises” Extraordinary personal stress Deliverables u u Expert Witness Testimony Transcript 15
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research Add credibility to the case by providing expert information Confidential Informants Trial Preparation Laboratory Analysis of Transactions Potential Issues Tasks to be Performed u u PRACTICE, PRACTICE Deliver expert witness testimony Explain exhibits TEACH the trier(s) of facts u u References u u Cross-Examination: T/he Comprehensive Guide for Experts (SEAK) Kolb, Experiential Learning Post. Assignment Testimony & Exhibits Undercover Purpose of Stage u TRIAL/REPORTS “Surprises” Extraordinary personal stress Deliverables u u Expert Witness Testimony Transcript 15
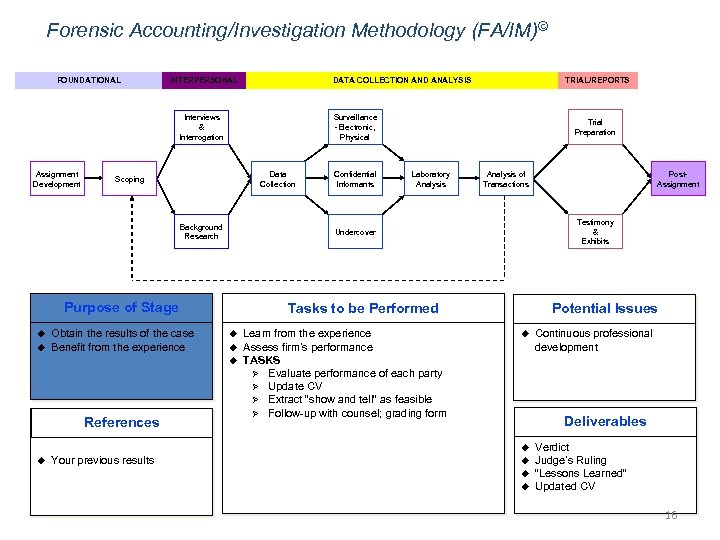 Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain the results of the case Benefit from the experience Laboratory Analysis of Transactions u u Learn from the experience Assess firm’s performance TASKS Ø Evaluate performance of each party Ø Update CV Ø Extract “show and tell” as feasible Ø Follow-up with counsel; grading form Potential Issues u Your previous results Continuous professional development Deliverables u u Post. Assignment Testimony & Exhibits Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Verdict Judge’s Ruling “Lessons Learned” Updated CV 16
Forensic Accounting/Investigation Methodology (FA/IM)© FOUNDATIONAL INTERPERSONAL DATA COLLECTION AND ANALYSIS Surveillance -Electronic, Physical Interviews & Interrogation Assignment Development Data Collection Scoping Background Research u Obtain the results of the case Benefit from the experience Laboratory Analysis of Transactions u u Learn from the experience Assess firm’s performance TASKS Ø Evaluate performance of each party Ø Update CV Ø Extract “show and tell” as feasible Ø Follow-up with counsel; grading form Potential Issues u Your previous results Continuous professional development Deliverables u u Post. Assignment Testimony & Exhibits Tasks to be Performed u References Confidential Informants Trial Preparation Undercover Purpose of Stage u TRIAL/REPORTS u u u Verdict Judge’s Ruling “Lessons Learned” Updated CV 16
 METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS l DIRECT METHODS SPECIFIC ITEM METHOD l FINANCIAL RELATIONSHIPS l FINANCIAL STATEMENT ANALYSIS l HORIZONTAL l VERTICAL l TREND l RATIO l CASH FLOW l 17
METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS l DIRECT METHODS SPECIFIC ITEM METHOD l FINANCIAL RELATIONSHIPS l FINANCIAL STATEMENT ANALYSIS l HORIZONTAL l VERTICAL l TREND l RATIO l CASH FLOW l 17
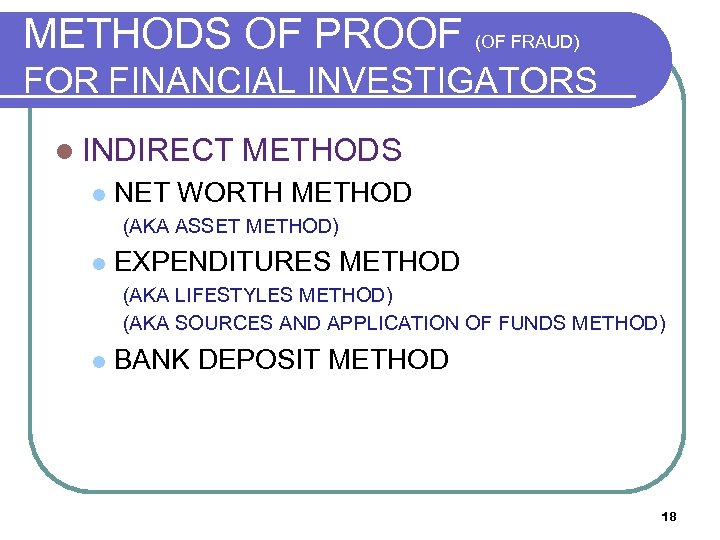 METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS l INDIRECT l METHODS NET WORTH METHOD (AKA ASSET METHOD) l EXPENDITURES METHOD (AKA LIFESTYLES METHOD) (AKA SOURCES AND APPLICATION OF FUNDS METHOD) l BANK DEPOSIT METHOD 18
METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS l INDIRECT l METHODS NET WORTH METHOD (AKA ASSET METHOD) l EXPENDITURES METHOD (AKA LIFESTYLES METHOD) (AKA SOURCES AND APPLICATION OF FUNDS METHOD) l BANK DEPOSIT METHOD 18
 METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS Information for specific industries l IRS’s Market Segment Specialization Program (MSSP) Audit Techniques Guides (ATGs) l l l Learn distinct , detailed practices in a particular industry Examination techniques Common & unique industry issues Business practices Terminology Example of market segments: l l Construction or entertainment industry Professions: lawyers or real estate agents 19
METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS Information for specific industries l IRS’s Market Segment Specialization Program (MSSP) Audit Techniques Guides (ATGs) l l l Learn distinct , detailed practices in a particular industry Examination techniques Common & unique industry issues Business practices Terminology Example of market segments: l l Construction or entertainment industry Professions: lawyers or real estate agents 19
 METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS Direct-Specific item method l l l Most common method Relies on specific transactions Uncovers specific financial transactions which relate to illegal activity, and to the suspect l l l Review books, records, bank accounts… directly traces a transaction Direct (vs circumstantial) proof Easiest to present @ trial Most difficult for the suspect to refute Example: Ghost employee on the payroll 20
METHODS OF PROOF (OF FRAUD) FOR FINANCIAL INVESTIGATORS Direct-Specific item method l l l Most common method Relies on specific transactions Uncovers specific financial transactions which relate to illegal activity, and to the suspect l l l Review books, records, bank accounts… directly traces a transaction Direct (vs circumstantial) proof Easiest to present @ trial Most difficult for the suspect to refute Example: Ghost employee on the payroll 20
 FINANCIAL STATEMENT ANALYSIS l NEED FOR FINANCIAL STATEMENT ANALYSIS COSO l REPORT TO THE NATIONS l l POWER OF FINANCIAL STATEMENT ANALYSIS
FINANCIAL STATEMENT ANALYSIS l NEED FOR FINANCIAL STATEMENT ANALYSIS COSO l REPORT TO THE NATIONS l l POWER OF FINANCIAL STATEMENT ANALYSIS
 FINANCIAL RELATIONSHIPS l SALES VERSUS COST OF GOOD SOLD l SALES VERSUS ACCOUNTS RECEIVABLE l SALES VERSUS INVENTORY l ASSETS VERSUS LIABILITIES
FINANCIAL RELATIONSHIPS l SALES VERSUS COST OF GOOD SOLD l SALES VERSUS ACCOUNTS RECEIVABLE l SALES VERSUS INVENTORY l ASSETS VERSUS LIABILITIES
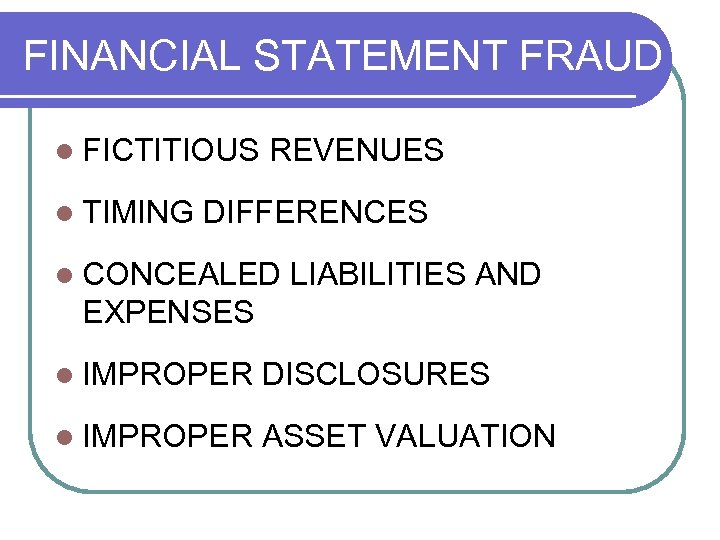 FINANCIAL STATEMENT FRAUD l FICTITIOUS l TIMING REVENUES DIFFERENCES l CONCEALED LIABILITIES AND EXPENSES l IMPROPER DISCLOSURES l IMPROPER ASSET VALUATION
FINANCIAL STATEMENT FRAUD l FICTITIOUS l TIMING REVENUES DIFFERENCES l CONCEALED LIABILITIES AND EXPENSES l IMPROPER DISCLOSURES l IMPROPER ASSET VALUATION
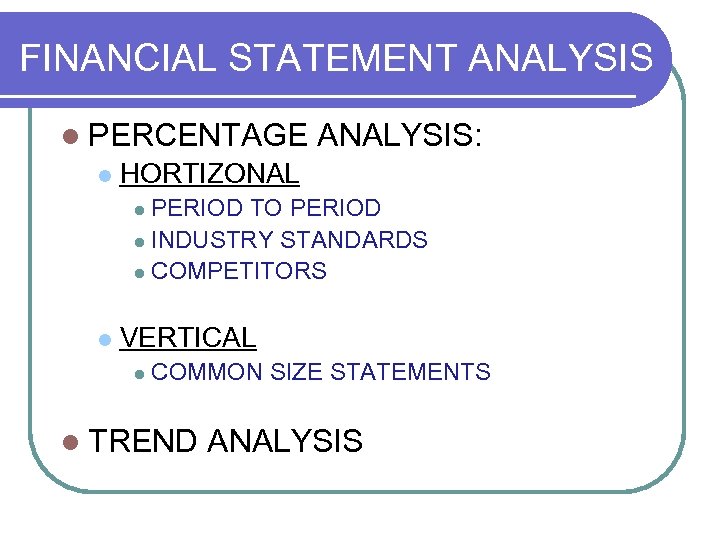 FINANCIAL STATEMENT ANALYSIS l PERCENTAGE l ANALYSIS: HORTIZONAL PERIOD TO PERIOD l INDUSTRY STANDARDS l COMPETITORS l l VERTICAL l COMMON SIZE STATEMENTS l TREND ANALYSIS
FINANCIAL STATEMENT ANALYSIS l PERCENTAGE l ANALYSIS: HORTIZONAL PERIOD TO PERIOD l INDUSTRY STANDARDS l COMPETITORS l l VERTICAL l COMMON SIZE STATEMENTS l TREND ANALYSIS
 FINANCIAL STATEMENT ANALYSIS CON’T l RATIO ANALYSIS LIQUIDITY l ASSET MANAGEMENT l DEBT MANAGEMENT l PROFITABILITY l l CASH FLOW ANALYSIS OPERATING l INVESTING l FINANCING l
FINANCIAL STATEMENT ANALYSIS CON’T l RATIO ANALYSIS LIQUIDITY l ASSET MANAGEMENT l DEBT MANAGEMENT l PROFITABILITY l l CASH FLOW ANALYSIS OPERATING l INVESTING l FINANCING l
 INDIRECT METHODS OF PROOF CIRCUMSTANTIAL PROOF l ADMISSIBLE IN COURT(1954 Supreme Court Holland v. U. S. ) l WHEN TO USE? l l l l Inadequate books/records Suspected: books do not reflect all income Significant increase in net worth Gross profit % changes significantly Expenses exceed reported income without cause Suspected income from unidentified sources is large 26
INDIRECT METHODS OF PROOF CIRCUMSTANTIAL PROOF l ADMISSIBLE IN COURT(1954 Supreme Court Holland v. U. S. ) l WHEN TO USE? l l l l Inadequate books/records Suspected: books do not reflect all income Significant increase in net worth Gross profit % changes significantly Expenses exceed reported income without cause Suspected income from unidentified sources is large 26
 INDIRECT METHODS OF PROOF SOURCES OF INFORMATION l l l l County courthouse: deeds of ownership, titles, liens, UCC filings The target Informants/associates Real estate records Bankruptcy records State motor vehicle records Loan applications l l l l Surveillance Credit card applications/statements Tax returns Insurance records Child support/divorce records Employment: salary, W-2 s Cancelled checks Deposit slips 27
INDIRECT METHODS OF PROOF SOURCES OF INFORMATION l l l l County courthouse: deeds of ownership, titles, liens, UCC filings The target Informants/associates Real estate records Bankruptcy records State motor vehicle records Loan applications l l l l Surveillance Credit card applications/statements Tax returns Insurance records Child support/divorce records Employment: salary, W-2 s Cancelled checks Deposit slips 27
 INDIRECT METHODS OF PROOF (O NET WORTH METHOD l Used to prove illicit income l l Person’s assets or expenditures exceed known sources of income 4 ways to dispose income: 1. 2. 3. 4. Save it Buy assets Pay off debt Spend it & rug d y in ses l sive g ca n exte nderin d Use ey lau mon 28
INDIRECT METHODS OF PROOF (O NET WORTH METHOD l Used to prove illicit income l l Person’s assets or expenditures exceed known sources of income 4 ways to dispose income: 1. 2. 3. 4. Save it Buy assets Pay off debt Spend it & rug d y in ses l sive g ca n exte nderin d Use ey lau mon 28
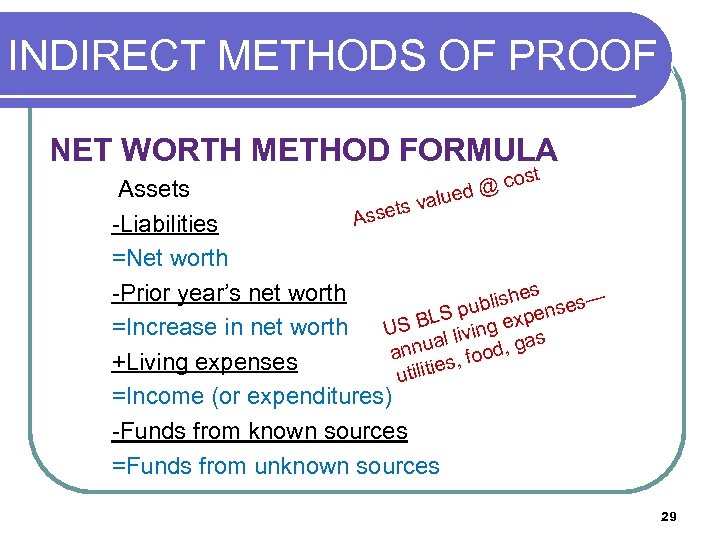 INDIRECT METHODS OF PROOF (O NET WORTH METHOD FORMULA co d@ ue st Assets al ets v Ass -Liabilities =Net worth es -Prior year’s net worth blish nses— pu BLS ing expe =Increase in net worth US liv nual ood, gas an s, f +Living expenses tilitie u =Income (or expenditures) -Funds from known sources =Funds from unknown sources 29
INDIRECT METHODS OF PROOF (O NET WORTH METHOD FORMULA co d@ ue st Assets al ets v Ass -Liabilities =Net worth es -Prior year’s net worth blish nses— pu BLS ing expe =Increase in net worth US liv nual ood, gas an s, f +Living expenses tilitie u =Income (or expenditures) -Funds from known sources =Funds from unknown sources 29
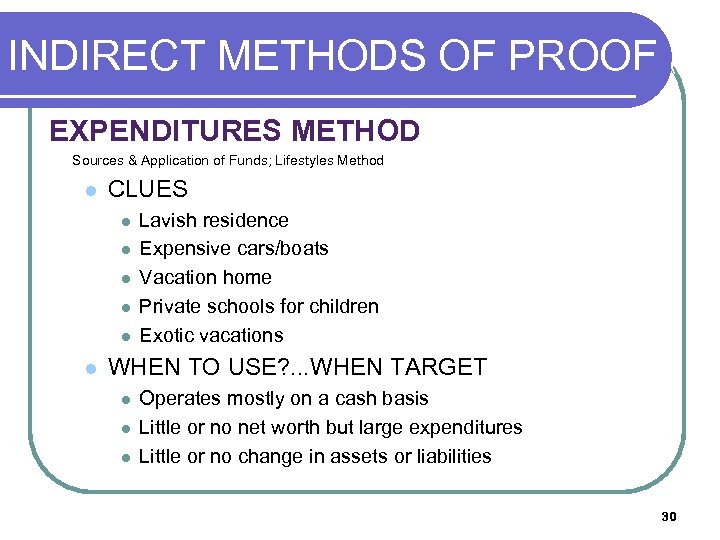 INDIRECT METHODS OF PROOF (O EXPENDITURES METHOD Sources & Application of Funds; Lifestyles Method l CLUES l l l Lavish residence Expensive cars/boats Vacation home Private schools for children Exotic vacations WHEN TO USE? . . . WHEN TARGET l l l Operates mostly on a cash basis Little or no net worth but large expenditures Little or no change in assets or liabilities 30
INDIRECT METHODS OF PROOF (O EXPENDITURES METHOD Sources & Application of Funds; Lifestyles Method l CLUES l l l Lavish residence Expensive cars/boats Vacation home Private schools for children Exotic vacations WHEN TO USE? . . . WHEN TARGET l l l Operates mostly on a cash basis Little or no net worth but large expenditures Little or no change in assets or liabilities 30
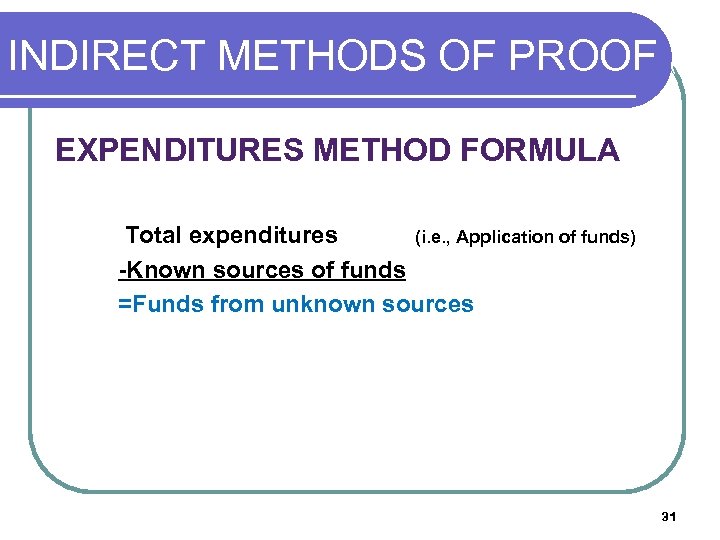 INDIRECT METHODS OF PROOF (O EXPENDITURES METHOD FORMULA Total expenditures (i. e. , Application of funds) -Known sources of funds =Funds from unknown sources 31
INDIRECT METHODS OF PROOF (O EXPENDITURES METHOD FORMULA Total expenditures (i. e. , Application of funds) -Known sources of funds =Funds from unknown sources 31
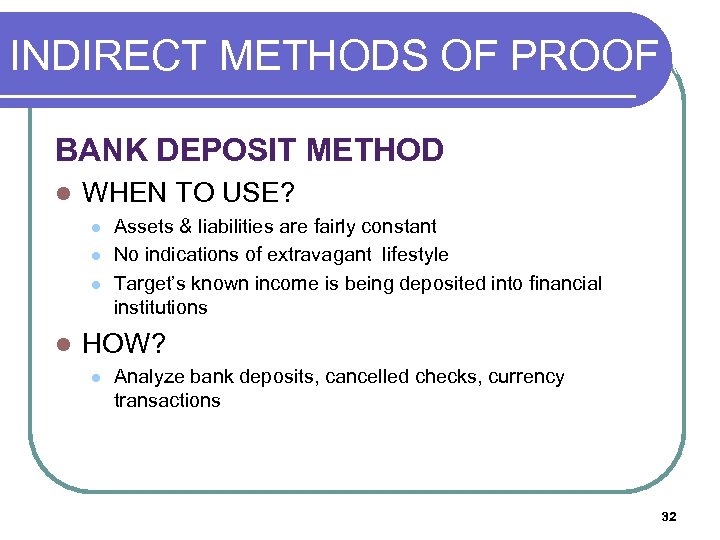 INDIRECT METHODS OF PROOF (O BANK DEPOSIT METHOD l WHEN TO USE? l l Assets & liabilities are fairly constant No indications of extravagant lifestyle Target’s known income is being deposited into financial institutions HOW? l Analyze bank deposits, cancelled checks, currency transactions 32
INDIRECT METHODS OF PROOF (O BANK DEPOSIT METHOD l WHEN TO USE? l l Assets & liabilities are fairly constant No indications of extravagant lifestyle Target’s known income is being deposited into financial institutions HOW? l Analyze bank deposits, cancelled checks, currency transactions 32
 INDIRECT METHODS OF PROOF (O BANK DEPOSIT METHOD FORMULA Total deposits to all accounts -Transfer and redeposits =Net deposits to all accounts +Cash expenditures =Total receipts from all sources -Funds from known sources =Funds from unknown or illegal sources 33
INDIRECT METHODS OF PROOF (O BANK DEPOSIT METHOD FORMULA Total deposits to all accounts -Transfer and redeposits =Net deposits to all accounts +Cash expenditures =Total receipts from all sources -Funds from known sources =Funds from unknown or illegal sources 33
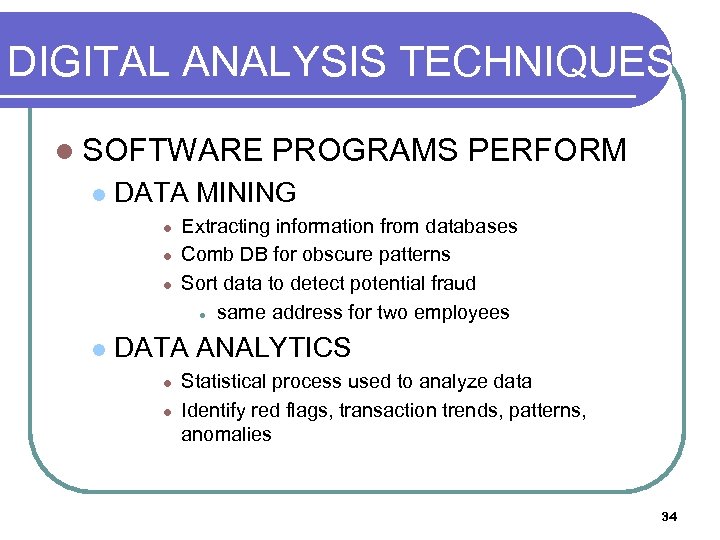 DIGITAL ANALYSIS TECHNIQUES l SOFTWARE l DATA MINING l l PROGRAMS PERFORM Extracting information from databases Comb DB for obscure patterns Sort data to detect potential fraud l same address for two employees DATA ANALYTICS l l Statistical process used to analyze data Identify red flags, transaction trends, patterns, anomalies 34
DIGITAL ANALYSIS TECHNIQUES l SOFTWARE l DATA MINING l l PROGRAMS PERFORM Extracting information from databases Comb DB for obscure patterns Sort data to detect potential fraud l same address for two employees DATA ANALYTICS l l Statistical process used to analyze data Identify red flags, transaction trends, patterns, anomalies 34
 DIGITAL ANALYSIS TECHNIQUES FUNCTIONS l l l l Sorting Record selection Joining files Multi-file processing Correlation analysis Date functions Graphing l l l Verifying multiples of a number Compliance verification Duplicate searches Vertical ratio analysis Horizontal ratio analysis 35
DIGITAL ANALYSIS TECHNIQUES FUNCTIONS l l l l Sorting Record selection Joining files Multi-file processing Correlation analysis Date functions Graphing l l l Verifying multiples of a number Compliance verification Duplicate searches Vertical ratio analysis Horizontal ratio analysis 35
 DIGITAL ANALYSIS TECHNIQUES FUNCTIONS l l l l Data file inquiry Random unit sampling Calculate totals Calculate averages Specific criteria searches Unusual item inquiries Link analysis graphics l l l Identify gaps in sequence Identify duplicates Differentiate normal patterns from suspect patterns Benford’s Law analysis Stratification 36
DIGITAL ANALYSIS TECHNIQUES FUNCTIONS l l l l Data file inquiry Random unit sampling Calculate totals Calculate averages Specific criteria searches Unusual item inquiries Link analysis graphics l l l Identify gaps in sequence Identify duplicates Differentiate normal patterns from suspect patterns Benford’s Law analysis Stratification 36
 DIGITAL ANALYSIS TECHNIQUES EXAMPLES Identify invoices w/o PO l Look for invoices from vendors not “approved” l Analyze claims paid by insurance providers l Look for high volume purchases from one vendor l Match names, addresses, phone numbers, SS numbers between employee and vendor files l Identify dormant accounts with activity l Search for large, rounded transaction values l 37
DIGITAL ANALYSIS TECHNIQUES EXAMPLES Identify invoices w/o PO l Look for invoices from vendors not “approved” l Analyze claims paid by insurance providers l Look for high volume purchases from one vendor l Match names, addresses, phone numbers, SS numbers between employee and vendor files l Identify dormant accounts with activity l Search for large, rounded transaction values l 37
 DIGITAL ANALYSIS TECHNIQUES COMMERCIAL SOFTWARE l l l l Excel ACL IDEA Active. Data for Excel Auto. Audit SNAP! Reporter Data. Watch’s Monarch for Windows Oversight Systems l Case Management Software—Analyst’s Notebook i 2; Lexis. Nexis Case. Map l Organize, evaluate, explore evidence Timeline Software— Timeline. Xpress (in. Data Corp) l Genogram--Geno. Pro l 38
DIGITAL ANALYSIS TECHNIQUES COMMERCIAL SOFTWARE l l l l Excel ACL IDEA Active. Data for Excel Auto. Audit SNAP! Reporter Data. Watch’s Monarch for Windows Oversight Systems l Case Management Software—Analyst’s Notebook i 2; Lexis. Nexis Case. Map l Organize, evaluate, explore evidence Timeline Software— Timeline. Xpress (in. Data Corp) l Genogram--Geno. Pro l 38
 ACCOUNTING TECHNIQUES USED IN A FRAUD INVESTIGATION Mary Anne Basilone, CPA, CFE, MMT, MA Chair, Accounting & Forensic Accounting Programs mabasilone@carlow. edu Diane A. Matthews, Ph. D, CPA/CFF, CFE Associate Dean, School of Management damatthews@carlow. edu 39
ACCOUNTING TECHNIQUES USED IN A FRAUD INVESTIGATION Mary Anne Basilone, CPA, CFE, MMT, MA Chair, Accounting & Forensic Accounting Programs mabasilone@carlow. edu Diane A. Matthews, Ph. D, CPA/CFF, CFE Associate Dean, School of Management damatthews@carlow. edu 39


