ba608c98619eab12fe3b9007730c8540.ppt
- Количество слайдов: 71
 ™: Access Novell Secure Overview and Competitive Comparisons www. novell. com Gabriel Waters Product Manager Novell, Inc. GWaters@novell. com
™: Access Novell Secure Overview and Competitive Comparisons www. novell. com Gabriel Waters Product Manager Novell, Inc. GWaters@novell. com
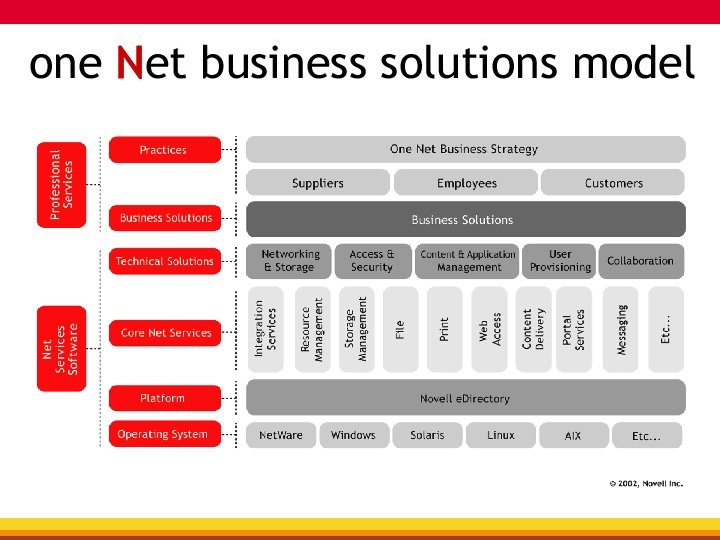
 Vision…one Net A world where networks of all types—corporate and public, intranets, extranets, and the Internet—work together as one Net and securely connect employees, customers, suppliers, and partners across organizational boundaries Mission To solve complex business and technical challenges with Net business solutions that enable people, processes, and systems to work together and our customers to profit from the opportunities of a networked world
Vision…one Net A world where networks of all types—corporate and public, intranets, extranets, and the Internet—work together as one Net and securely connect employees, customers, suppliers, and partners across organizational boundaries Mission To solve complex business and technical challenges with Net business solutions that enable people, processes, and systems to work together and our customers to profit from the opportunities of a networked world
 Many Systems, Many Accounts hp-ux OS/390
Many Systems, Many Accounts hp-ux OS/390
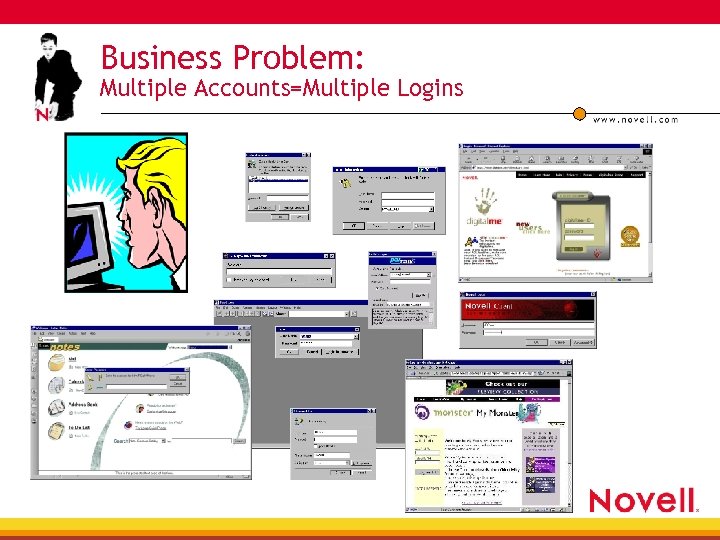 Business Problem: Multiple Accounts=Multiple Logins
Business Problem: Multiple Accounts=Multiple Logins
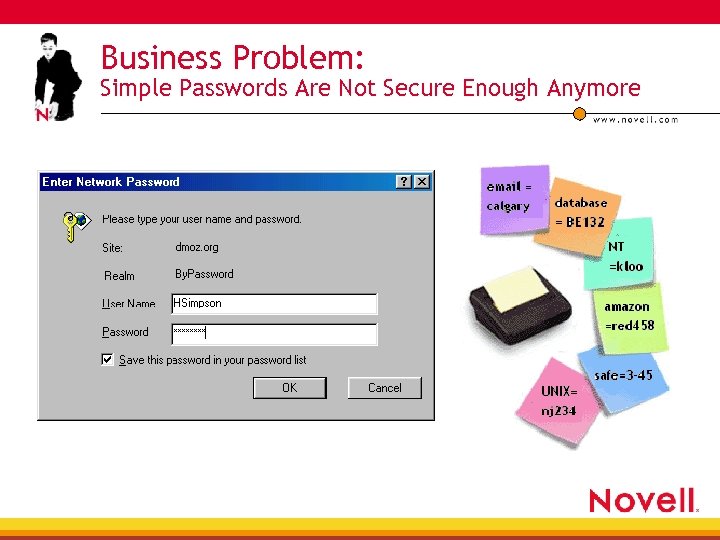 Business Problem: Simple Passwords Are Not Secure Enough Anymore
Business Problem: Simple Passwords Are Not Secure Enough Anymore
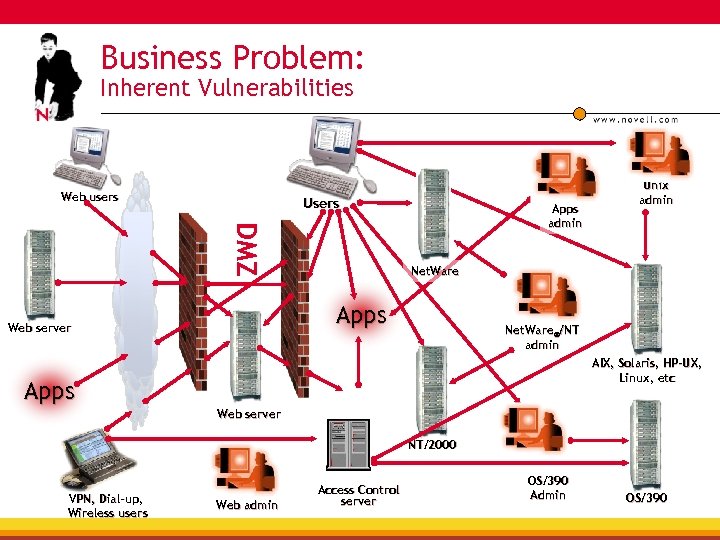 Business Problem: Inherent Vulnerabilities Web users Users DMZ Apps admin Net. Ware Apps Web server Unix admin Net. Ware®/NT admin AIX, Solaris, HP-UX, Linux, etc Apps Web server NT/2000 VPN, Dial-up, Wireless users Web admin Access Control server OS/390 Admin OS/390
Business Problem: Inherent Vulnerabilities Web users Users DMZ Apps admin Net. Ware Apps Web server Unix admin Net. Ware®/NT admin AIX, Solaris, HP-UX, Linux, etc Apps Web server NT/2000 VPN, Dial-up, Wireless users Web admin Access Control server OS/390 Admin OS/390
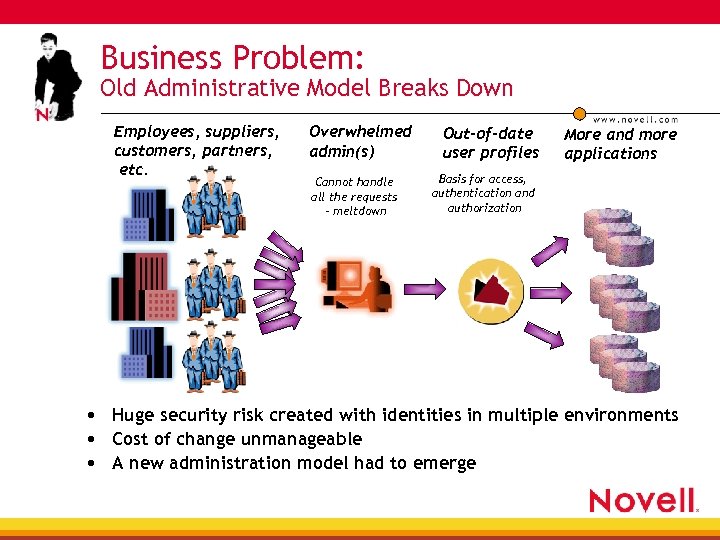 Business Problem: Old Administrative Model Breaks Down Employees, suppliers, customers, partners, etc. Overwhelmed admin(s) Cannot handle all the requests – meltdown Out-of-date user profiles More and more applications Basis for access, authentication and authorization • Huge security risk created with identities in multiple environments • Cost of change unmanageable • A new administration model had to emerge
Business Problem: Old Administrative Model Breaks Down Employees, suppliers, customers, partners, etc. Overwhelmed admin(s) Cannot handle all the requests – meltdown Out-of-date user profiles More and more applications Basis for access, authentication and authorization • Huge security risk created with identities in multiple environments • Cost of change unmanageable • A new administration model had to emerge
 Business Problem: Support Costs Are Increa$ing • The typical user spends as much as 44 hours per year performing multiple login tasks to access 4 applications » A 1996 study by the Network Applications Consortium • Most users can’t remember more than 3 passwords, yet are expected to remember 6 or more » Steven Foote, director of strategic research at Hurwitz Group • More than 30% of help desk costs are password related » Giga, Renee Woo, March 2001 • Password management costs between $200 and $300 per user each year » IDC
Business Problem: Support Costs Are Increa$ing • The typical user spends as much as 44 hours per year performing multiple login tasks to access 4 applications » A 1996 study by the Network Applications Consortium • Most users can’t remember more than 3 passwords, yet are expected to remember 6 or more » Steven Foote, director of strategic research at Hurwitz Group • More than 30% of help desk costs are password related » Giga, Renee Woo, March 2001 • Password management costs between $200 and $300 per user each year » IDC
 Paradise • Manage only one account for each user • Reduce administrative and support costs • Eliminate passwords • Increase security • Provide secure e. Business, enterprise, and legacy integration
Paradise • Manage only one account for each user • Reduce administrative and support costs • Eliminate passwords • Increase security • Provide secure e. Business, enterprise, and legacy integration
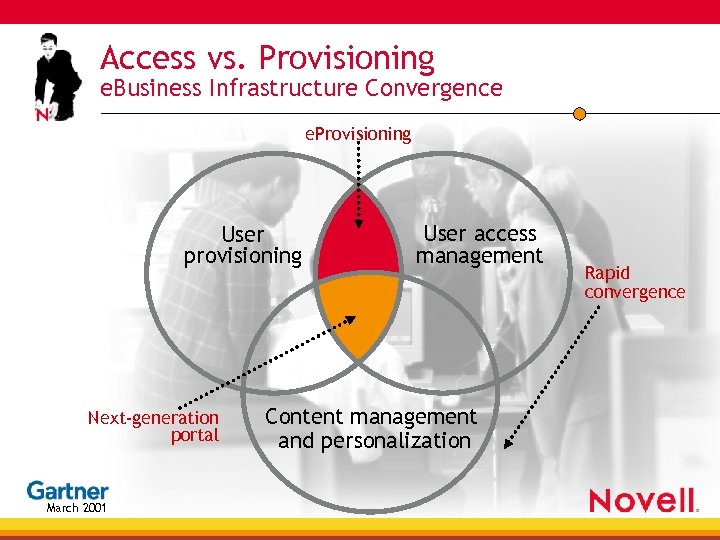 Access vs. Provisioning e. Business Infrastructure Convergence e. Provisioning User provisioning Next-generation portal March 2001 User access management Content management and personalization Rapid convergence
Access vs. Provisioning e. Business Infrastructure Convergence e. Provisioning User provisioning Next-generation portal March 2001 User access management Content management and personalization Rapid convergence
 What to Look for in an Access Management Solution • • • Intranet and extranet single sign-on Account provisioning Authentication and authorization management Advanced authentication support Directory-enabled Centralized administration Mobile and wireless user support Support for all data stores and security systems Customizable Broad platform support Market leadership
What to Look for in an Access Management Solution • • • Intranet and extranet single sign-on Account provisioning Authentication and authorization management Advanced authentication support Directory-enabled Centralized administration Mobile and wireless user support Support for all data stores and security systems Customizable Broad platform support Market leadership
 The Secure Access Solution • Managing authentication and authorization for web, wireless, dial-up, VPN, and client users to provide secure access and single sign-on to applications, databases, and platforms
The Secure Access Solution • Managing authentication and authorization for web, wireless, dial-up, VPN, and client users to provide secure access and single sign-on to applications, databases, and platforms
 What Is the Secure Access Solution? • A soft bundle of existing Novell products that have/are being further integrated on a common architecture, to create a scalable, reliable, and secure infrastructure for Novell and third-party Secure Access products
What Is the Secure Access Solution? • A soft bundle of existing Novell products that have/are being further integrated on a common architecture, to create a scalable, reliable, and secure infrastructure for Novell and third-party Secure Access products
 The Novell Solution
The Novell Solution
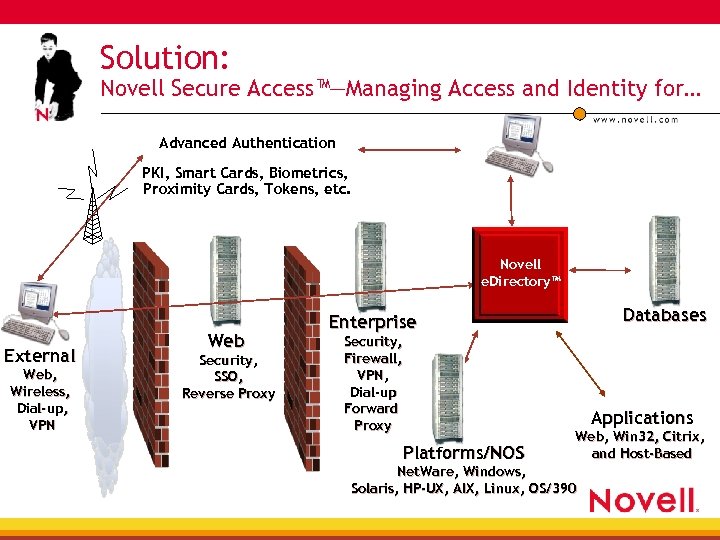 Solution: Novell Secure Access™—Managing Access and Identity for… Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory™ External Web, Wireless, Dial-up, VPN Web Security, SSO, Reverse Proxy Databases Enterprise Security, Firewall, VPN, Dial-up Forward Proxy Applications Platforms/NOS Web, Win 32, Citrix, and Host-Based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
Solution: Novell Secure Access™—Managing Access and Identity for… Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory™ External Web, Wireless, Dial-up, VPN Web Security, SSO, Reverse Proxy Databases Enterprise Security, Firewall, VPN, Dial-up Forward Proxy Applications Platforms/NOS Web, Win 32, Citrix, and Host-Based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
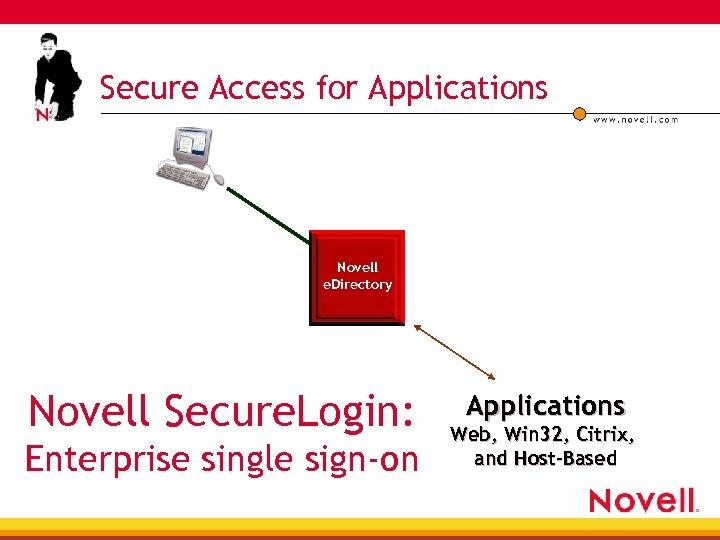 Secure Access for Applications Novell e. Directory Novell Secure. Login: Enterprise single sign-on Applications Web, Win 32, Citrix, and Host-Based
Secure Access for Applications Novell e. Directory Novell Secure. Login: Enterprise single sign-on Applications Web, Win 32, Citrix, and Host-Based
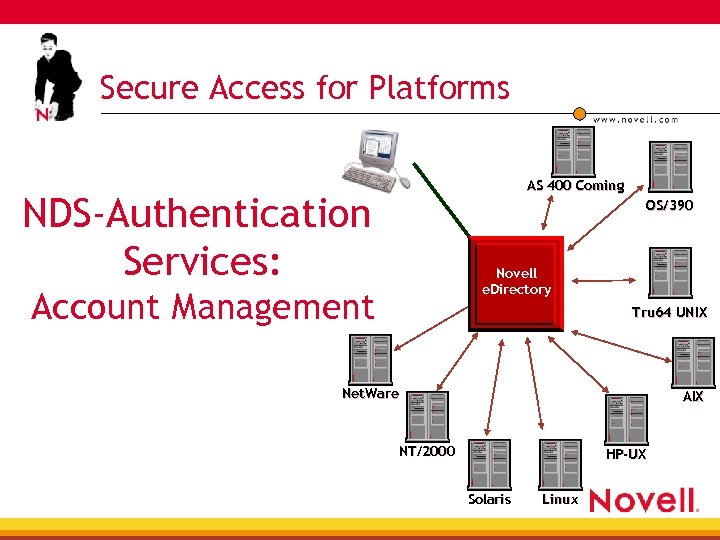 Secure Access for Platforms AS 400 Coming NDS-Authentication Services: OS/390 Novell e. Directory Account Management Tru 64 UNIX Net. Ware AIX NT/2000 HP-UX Solaris Linux
Secure Access for Platforms AS 400 Coming NDS-Authentication Services: OS/390 Novell e. Directory Account Management Tru 64 UNIX Net. Ware AIX NT/2000 HP-UX Solaris Linux
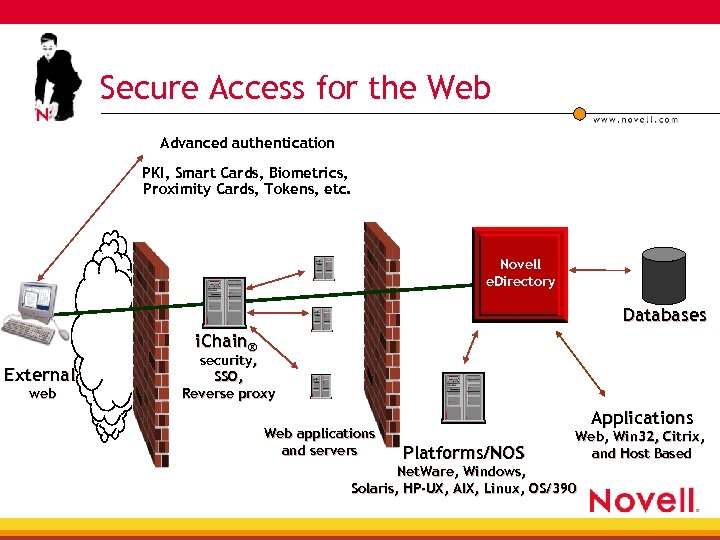 Secure Access for the Web Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Databases i. Chain® External web security, SSO, Reverse proxy Web applications and servers Applications Platforms/NOS Web, Win 32, Citrix, and Host Based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
Secure Access for the Web Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Databases i. Chain® External web security, SSO, Reverse proxy Web applications and servers Applications Platforms/NOS Web, Win 32, Citrix, and Host Based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
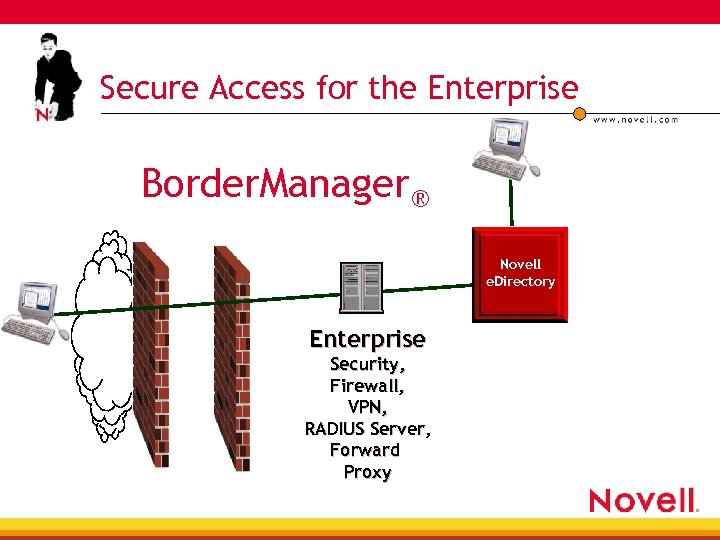 Secure Access for the Enterprise Border. Manager® Novell e. Directory Enterprise Security, Firewall, VPN, RADIUS Server, Forward Proxy
Secure Access for the Enterprise Border. Manager® Novell e. Directory Enterprise Security, Firewall, VPN, RADIUS Server, Forward Proxy
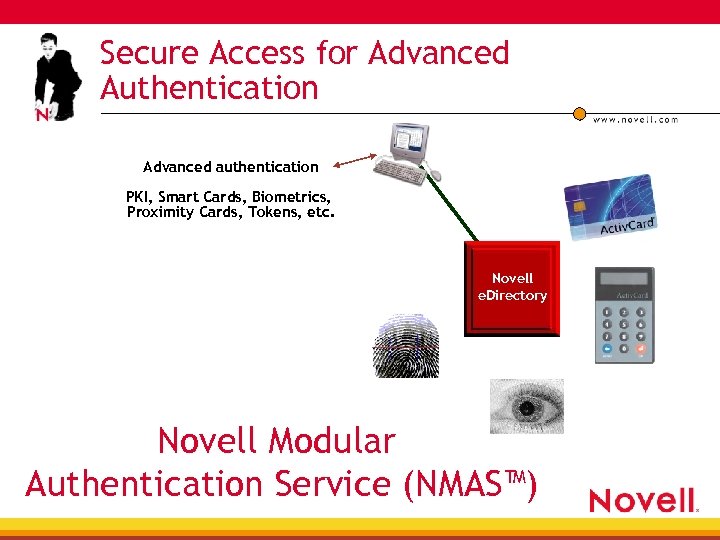 Secure Access for Advanced Authentication Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Novell Modular Authentication Service (NMAS™)
Secure Access for Advanced Authentication Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Novell Modular Authentication Service (NMAS™)
 The Novell Solution
The Novell Solution
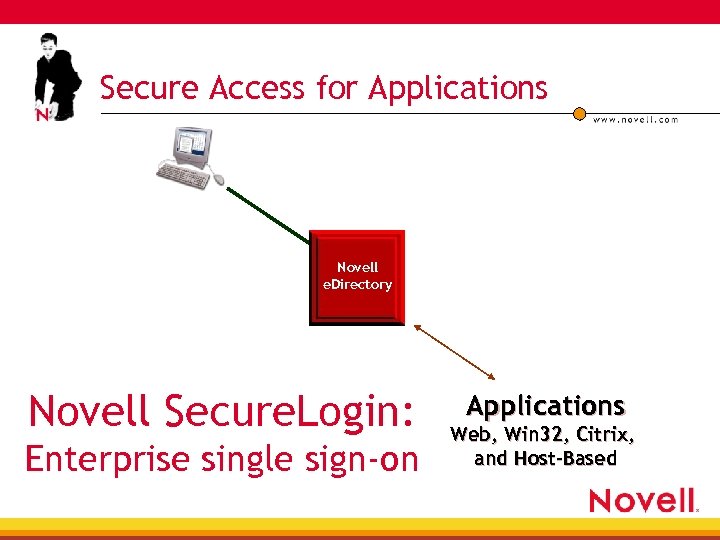 Secure Access for Applications Novell e. Directory Novell Secure. Login: Enterprise single sign-on Applications Web, Win 32, Citrix, and Host-Based
Secure Access for Applications Novell e. Directory Novell Secure. Login: Enterprise single sign-on Applications Web, Win 32, Citrix, and Host-Based
 What Is Novell Secure. Login? • A password management solution that single sign-on enables Windows, web, Citrix/Terminal Server, and host-based applications
What Is Novell Secure. Login? • A password management solution that single sign-on enables Windows, web, Citrix/Terminal Server, and host-based applications
 Novell Secure. Login Benefits • Simplifies the end-user experience 4 User only logs in once 4 Significantly reduces support costs • Secures access to applications 4 Users don’t have to remember many/weak passwords • Accelerate authentication 4 Users are more productive
Novell Secure. Login Benefits • Simplifies the end-user experience 4 User only logs in once 4 Significantly reduces support costs • Secures access to applications 4 Users don’t have to remember many/weak passwords • Accelerate authentication 4 Users are more productive
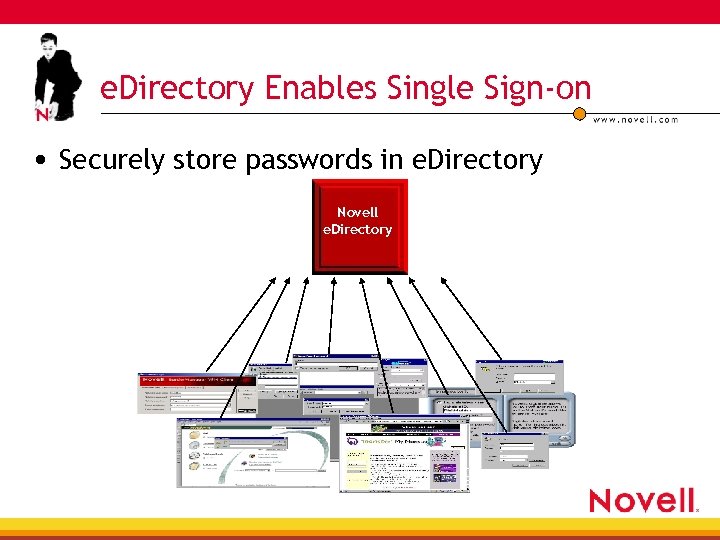 e. Directory Enables Single Sign-on • Securely store passwords in e. Directory Novell e. Directory
e. Directory Enables Single Sign-on • Securely store passwords in e. Directory Novell e. Directory
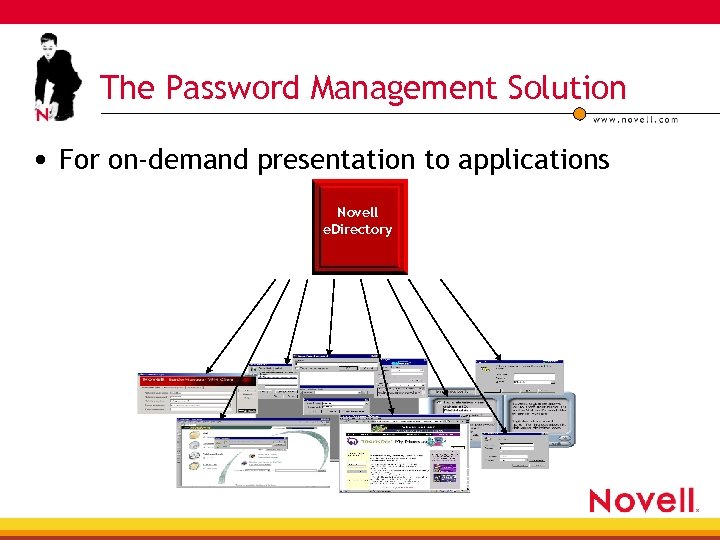 The Password Management Solution • For on-demand presentation to applications Novell e. Directory
The Password Management Solution • For on-demand presentation to applications Novell e. Directory
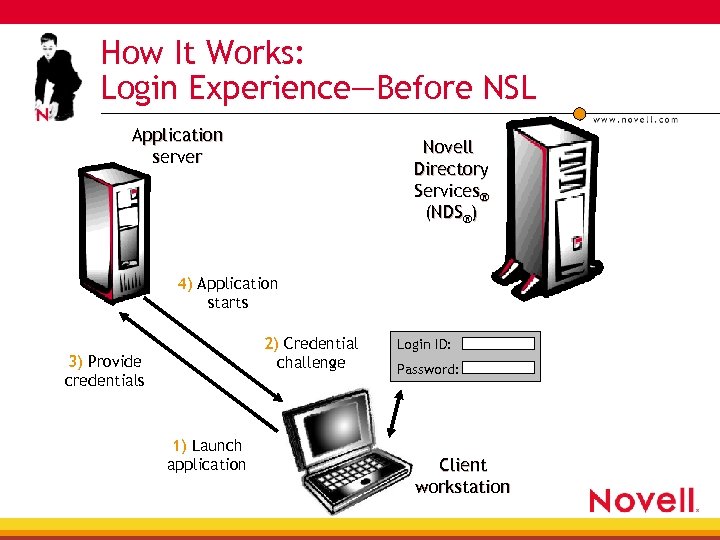 How It Works: Login Experience—Before NSL Application server Novell Directory Services® (NDS®) 4) Application starts 2) Credential challenge 3) Provide credentials 1) Launch application Login ID: Password: Client workstation
How It Works: Login Experience—Before NSL Application server Novell Directory Services® (NDS®) 4) Application starts 2) Credential challenge 3) Provide credentials 1) Launch application Login ID: Password: Client workstation
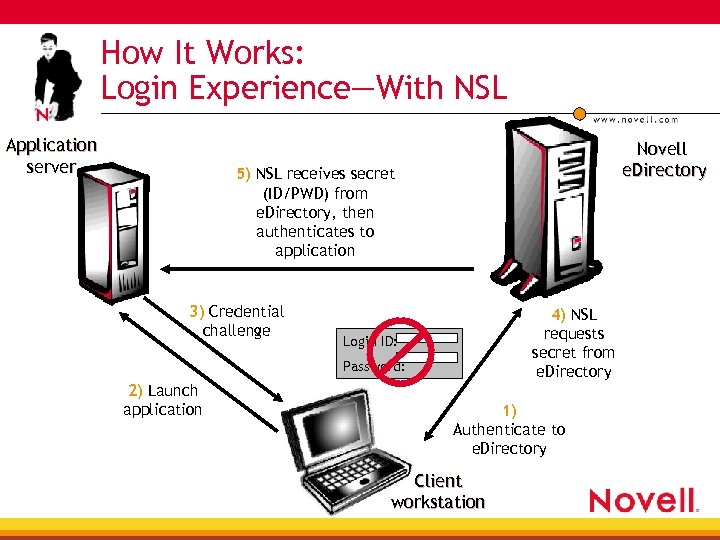 How It Works: Login Experience—With NSL Application server Novell e. Directory 5) NSL receives secret (ID/PWD) from e. Directory, then authenticates to application 3) Credential challenge 4) NSL requests secret from e. Directory Login ID: Password: 2) Launch application 1) Authenticate to e. Directory Client workstation
How It Works: Login Experience—With NSL Application server Novell e. Directory 5) NSL receives secret (ID/PWD) from e. Directory, then authenticates to application 3) Credential challenge 4) NSL requests secret from e. Directory Login ID: Password: 2) Launch application 1) Authenticate to e. Directory Client workstation
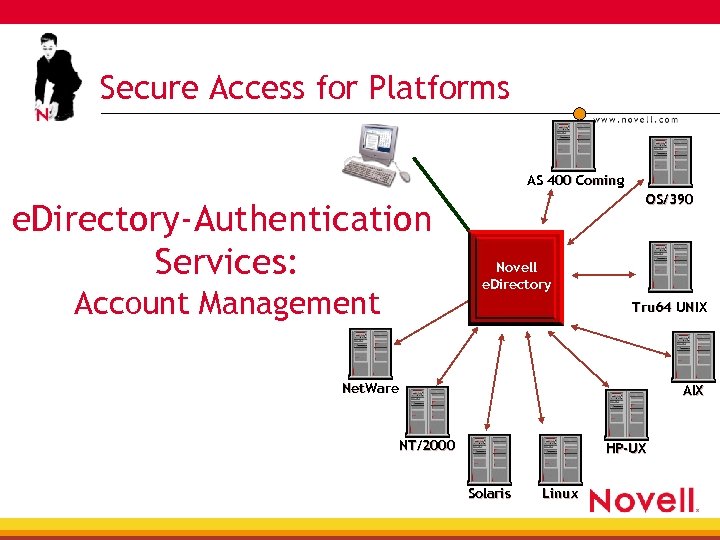 Secure Access for Platforms AS 400 Coming e. Directory-Authentication Services: Account Management OS/390 Novell e. Directory Tru 64 UNIX Net. Ware AIX NT/2000 HP-UX Solaris Linux
Secure Access for Platforms AS 400 Coming e. Directory-Authentication Services: Account Management OS/390 Novell e. Directory Tru 64 UNIX Net. Ware AIX NT/2000 HP-UX Solaris Linux
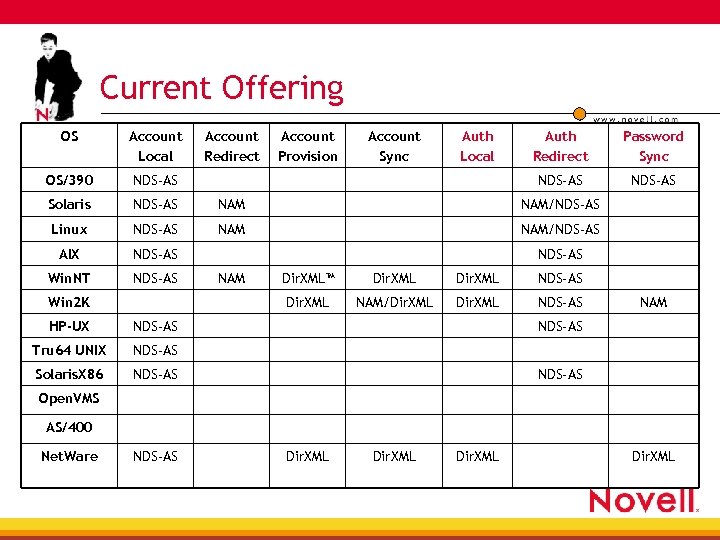 Current Offering OS Account Local Account Redirect Account Provision Account Sync Auth Local Auth Redirect Password Sync OS/390 NDS-AS Solaris NDS-AS NAM/NDS-AS Linux NDS-AS NAM/NDS-AS AIX NDS-AS Win. NT NDS-AS HP-UX Dir. XML NDS-AS NAM/Dir. XML NDS-AS NAM NDS-AS Solaris. X 86 Dir. XML NDS-AS Tru 64 UNIX Dir. XML™ Dir. XML Win 2 K NAM NDS-AS Open. VMS AS/400 Net. Ware NDS-AS Dir. XML
Current Offering OS Account Local Account Redirect Account Provision Account Sync Auth Local Auth Redirect Password Sync OS/390 NDS-AS Solaris NDS-AS NAM/NDS-AS Linux NDS-AS NAM/NDS-AS AIX NDS-AS Win. NT NDS-AS HP-UX Dir. XML NDS-AS NAM/Dir. XML NDS-AS NAM NDS-AS Solaris. X 86 Dir. XML NDS-AS Tru 64 UNIX Dir. XML™ Dir. XML Win 2 K NAM NDS-AS Open. VMS AS/400 Net. Ware NDS-AS Dir. XML
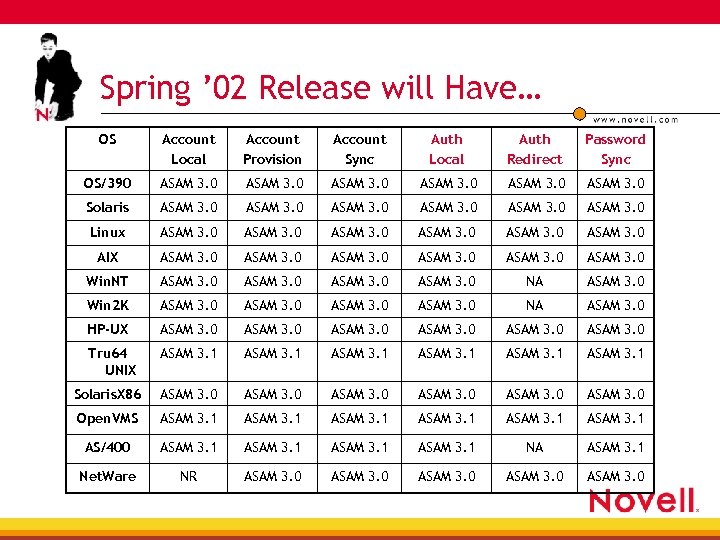 Spring ’ 02 Release will Have… OS Account Local Account Provision Account Sync Auth Local Auth Redirect Password Sync OS/390 ASAM 3. 0 Solaris ASAM 3. 0 Linux ASAM 3. 0 AIX ASAM 3. 0 Win. NT ASAM 3. 0 NA ASAM 3. 0 Win 2 K ASAM 3. 0 NA ASAM 3. 0 HP-UX ASAM 3. 0 Tru 64 UNIX ASAM 3. 1 Solaris. X 86 ASAM 3. 0 Open. VMS ASAM 3. 1 AS/400 ASAM 3. 1 NA ASAM 3. 1 Net. Ware NR ASAM 3. 0
Spring ’ 02 Release will Have… OS Account Local Account Provision Account Sync Auth Local Auth Redirect Password Sync OS/390 ASAM 3. 0 Solaris ASAM 3. 0 Linux ASAM 3. 0 AIX ASAM 3. 0 Win. NT ASAM 3. 0 NA ASAM 3. 0 Win 2 K ASAM 3. 0 NA ASAM 3. 0 HP-UX ASAM 3. 0 Tru 64 UNIX ASAM 3. 1 Solaris. X 86 ASAM 3. 0 Open. VMS ASAM 3. 1 AS/400 ASAM 3. 1 NA ASAM 3. 1 Net. Ware NR ASAM 3. 0
 What Is Novell Account Management? • Account integration for user and group accounts and password synchronization on Net. Ware, Windows, UNIX, Linux and MVS platforms
What Is Novell Account Management? • Account integration for user and group accounts and password synchronization on Net. Ware, Windows, UNIX, Linux and MVS platforms
 What’s the Value of Novell Account Management and NDS-AS? • Simplifies the complexity and cost of managing passwords 4 For Windows, UNIX and MVS systems and applications • Secures 4 Provides integrated security with unified passwords, single login, universal access controls, and distributed policies from the users platform of choice • Accelerates 4 Allows for flexible management so that administrators in corporate offices or decentralized branch offices can manage their respective users. IDs in a corporate-wide system
What’s the Value of Novell Account Management and NDS-AS? • Simplifies the complexity and cost of managing passwords 4 For Windows, UNIX and MVS systems and applications • Secures 4 Provides integrated security with unified passwords, single login, universal access controls, and distributed policies from the users platform of choice • Accelerates 4 Allows for flexible management so that administrators in corporate offices or decentralized branch offices can manage their respective users. IDs in a corporate-wide system
 What is Novell Account Management and e. Directory Authentication Services? • Redirection 4 Novell Account Management (NAM) • Redirect security account manager (SAM) registry to e. Directory • Redirect etc/pass, NIS+ to e. Directory using Pluggable Authentication Module (PAM) 4 NDS Authentication Services (NDS-AS) • Redirect RACF and ACF 2 (OS/390) security systems to e. Directory • Redirect etc/pass, NIS+ to NDS using Pluggable Authentication Module (PAM) • Synchronization 4 Novell Account Management • Dir. XML™-based, specialized configuration for Active Directory • Future offerings
What is Novell Account Management and e. Directory Authentication Services? • Redirection 4 Novell Account Management (NAM) • Redirect security account manager (SAM) registry to e. Directory • Redirect etc/pass, NIS+ to e. Directory using Pluggable Authentication Module (PAM) 4 NDS Authentication Services (NDS-AS) • Redirect RACF and ACF 2 (OS/390) security systems to e. Directory • Redirect etc/pass, NIS+ to NDS using Pluggable Authentication Module (PAM) • Synchronization 4 Novell Account Management • Dir. XML™-based, specialized configuration for Active Directory • Future offerings
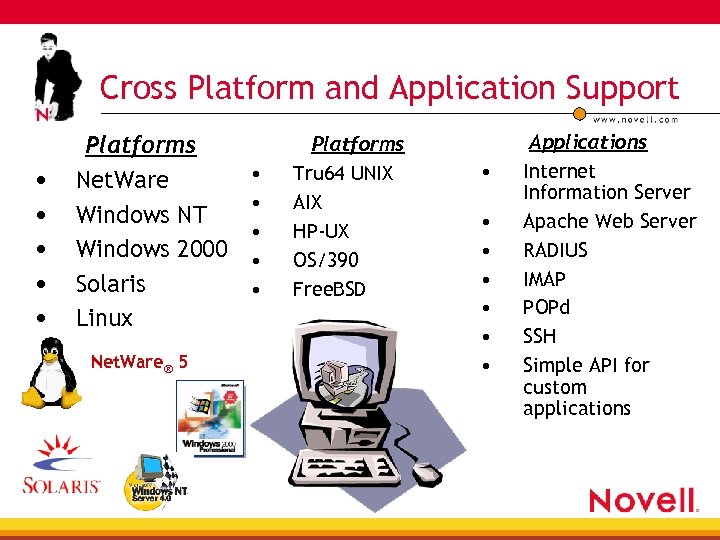 Cross Platform and Application Support • • • Platforms Net. Ware Windows NT Windows 2000 Solaris Linux Net. Ware® 5 • • • Platforms Tru 64 UNIX AIX HP-UX OS/390 Free. BSD • • Applications Internet Information Server Apache Web Server RADIUS IMAP POPd SSH Simple API for custom applications
Cross Platform and Application Support • • • Platforms Net. Ware Windows NT Windows 2000 Solaris Linux Net. Ware® 5 • • • Platforms Tru 64 UNIX AIX HP-UX OS/390 Free. BSD • • Applications Internet Information Server Apache Web Server RADIUS IMAP POPd SSH Simple API for custom applications
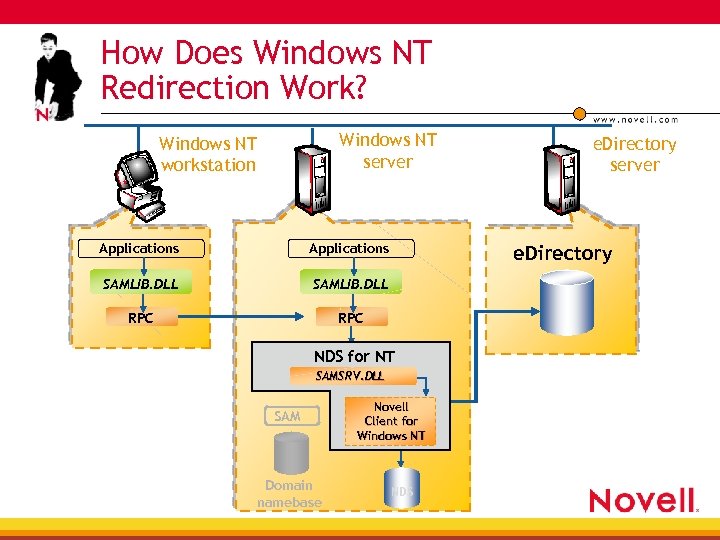 How Does Windows NT Redirection Work? Windows NT server Windows NT workstation Applications SAMLIB. DLL RPC e. Directory NDS for NT SAMSRV. DLL SAM Domain namebase e. Directory server Novell Client for Windows NT NDS
How Does Windows NT Redirection Work? Windows NT server Windows NT workstation Applications SAMLIB. DLL RPC e. Directory NDS for NT SAMSRV. DLL SAM Domain namebase e. Directory server Novell Client for Windows NT NDS
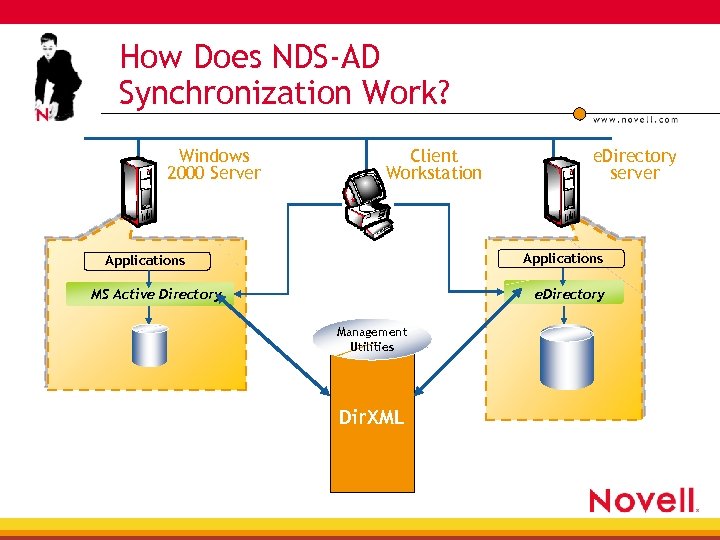 How Does NDS-AD Synchronization Work? Windows 2000 Server Client Workstation e. Directory server Applications MS Active Directory e. Directory Management Utilities Dir. XML
How Does NDS-AD Synchronization Work? Windows 2000 Server Client Workstation e. Directory server Applications MS Active Directory e. Directory Management Utilities Dir. XML
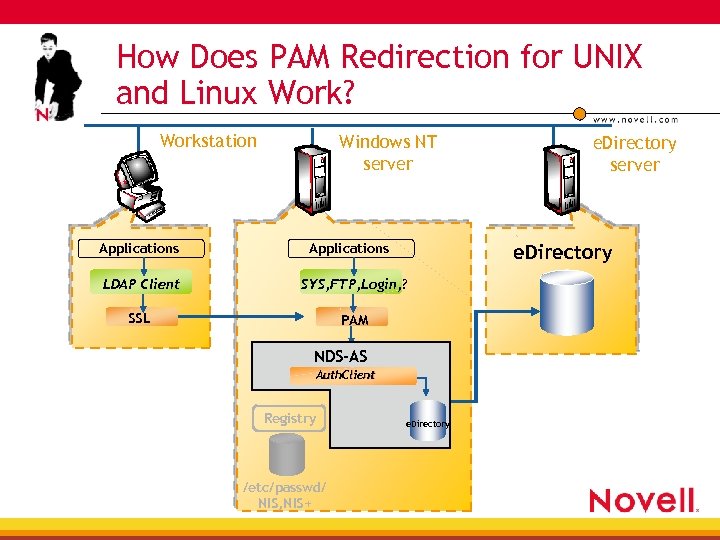 How Does PAM Redirection for UNIX and Linux Work? Workstation Applications Windows NT server e. Directory Applications LDAP Client SYS, FTP, Login, ? SSL PAM NDS-AS Auth. Client Registry /etc/passwd/ NIS, NIS+ e. Directory server e. Directory
How Does PAM Redirection for UNIX and Linux Work? Workstation Applications Windows NT server e. Directory Applications LDAP Client SYS, FTP, Login, ? SSL PAM NDS-AS Auth. Client Registry /etc/passwd/ NIS, NIS+ e. Directory server e. Directory
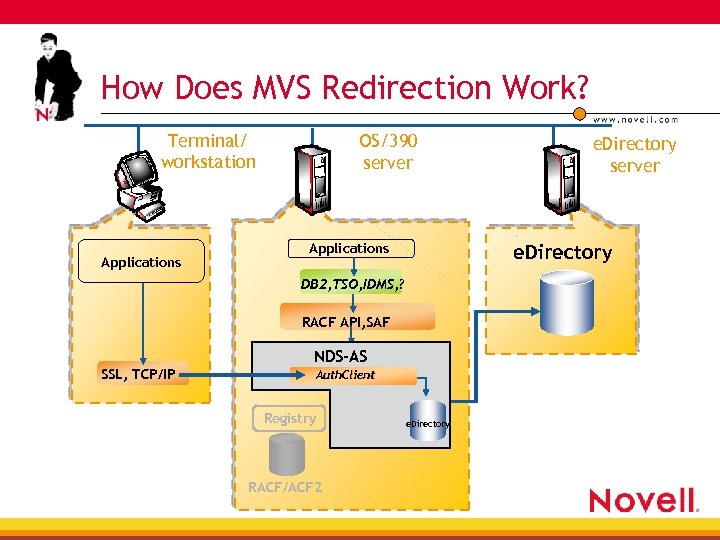 How Does MVS Redirection Work? Terminal/ workstation Applications OS/390 server e. Directory Applications DB 2, TSO, IDMS, ? RACF API, SAF NDS-AS SSL, TCP/IP Auth. Client Registry RACF/ACF 2 e. Directory server e. Directory
How Does MVS Redirection Work? Terminal/ workstation Applications OS/390 server e. Directory Applications DB 2, TSO, IDMS, ? RACF API, SAF NDS-AS SSL, TCP/IP Auth. Client Registry RACF/ACF 2 e. Directory server e. Directory
 Providing ROI • According to the Bangkok Post 2/09/2000 4 The value of single sign-on cannot be argued with, but its costs and implementation time can skyrocket for large companies with heterogeneous environments and different user needs 4 A survey by the Securities Industries Association of Washington, D. C. found that users spent on average 44. 4 hours a year just “logging in” 4 With NDS-AS they would have spent only 11. 1 hours • To quantify, this would represent a saving of over $800, 000 for a 1, 000 -user company
Providing ROI • According to the Bangkok Post 2/09/2000 4 The value of single sign-on cannot be argued with, but its costs and implementation time can skyrocket for large companies with heterogeneous environments and different user needs 4 A survey by the Securities Industries Association of Washington, D. C. found that users spent on average 44. 4 hours a year just “logging in” 4 With NDS-AS they would have spent only 11. 1 hours • To quantify, this would represent a saving of over $800, 000 for a 1, 000 -user company
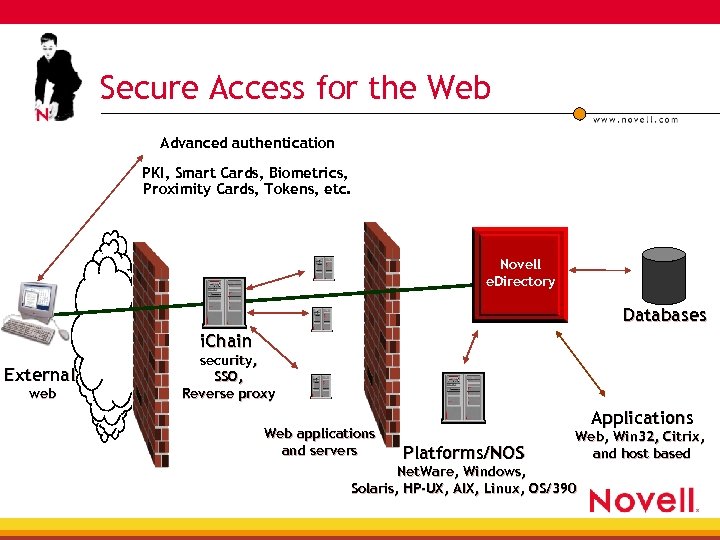 Secure Access for the Web Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Databases i. Chain External web security, SSO, Reverse proxy Web applications and servers Applications Platforms/NOS Web, Win 32, Citrix, and host based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
Secure Access for the Web Advanced authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Databases i. Chain External web security, SSO, Reverse proxy Web applications and servers Applications Platforms/NOS Web, Win 32, Citrix, and host based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
 What Is i. Chain? • i. Chain v 1. 5 is a directory enabled security and management infrastructure that provides the foundation for secured e. Business solutions
What Is i. Chain? • i. Chain v 1. 5 is a directory enabled security and management infrastructure that provides the foundation for secured e. Business solutions
 i. Chain Internet Caching Server • Primary access point for all users into the infrastructure using enhanced Reverse Proxy technology 4 Provides single sign-on to web resources 4 Provides acceleration with Cache Object Store (COS) 4 Maintains data confidentiality (SSLizer) • Forces SSL between browser and proxy • HTTP between proxy and web server • On/Off per accelerator
i. Chain Internet Caching Server • Primary access point for all users into the infrastructure using enhanced Reverse Proxy technology 4 Provides single sign-on to web resources 4 Provides acceleration with Cache Object Store (COS) 4 Maintains data confidentiality (SSLizer) • Forces SSL between browser and proxy • HTTP between proxy and web server • On/Off per accelerator
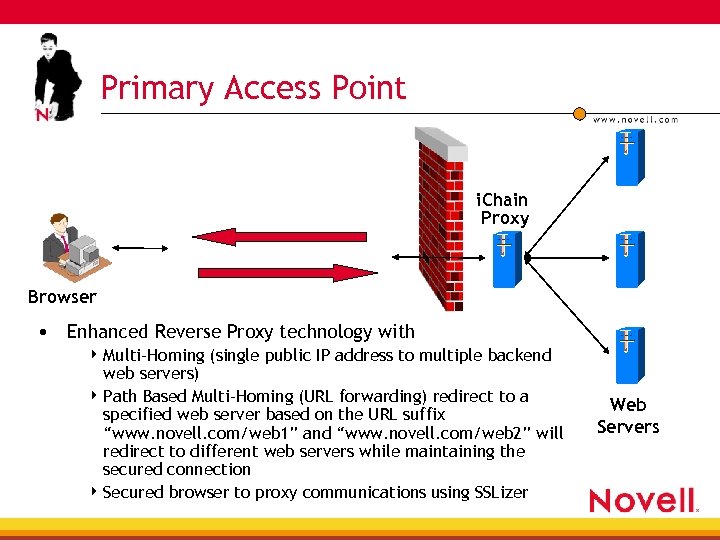 Primary Access Point SSL i. Chain Proxy Browser • Enhanced Reverse Proxy technology with 4 Multi-Homing (single public IP address to multiple backend web servers) 4 Path Based Multi-Homing (URL forwarding) redirect to a specified web server based on the URL suffix “www. novell. com/web 1” and “www. novell. com/web 2” will redirect to different web servers while maintaining the secured connection 4 Secured browser to proxy communications using SSLizer Web Servers
Primary Access Point SSL i. Chain Proxy Browser • Enhanced Reverse Proxy technology with 4 Multi-Homing (single public IP address to multiple backend web servers) 4 Path Based Multi-Homing (URL forwarding) redirect to a specified web server based on the URL suffix “www. novell. com/web 1” and “www. novell. com/web 2” will redirect to different web servers while maintaining the secured connection 4 Secured browser to proxy communications using SSLizer Web Servers
 Authentication Service • Standard browser-based access 4 4 Username and password over HTTPS Can authenticate with User. ID, e-mail or any LDAP field • Multiple authentication methods 4 4 4 One time passwords (within the same DNS domain) X. 509 certificates Future integration with NMAS (Novell Modular Authentication Services) will provide additional methods including Smart Card, Token and Biometric • Multi-factor authentication 4 Combination of authentication methods • Contextless Login
Authentication Service • Standard browser-based access 4 4 Username and password over HTTPS Can authenticate with User. ID, e-mail or any LDAP field • Multiple authentication methods 4 4 4 One time passwords (within the same DNS domain) X. 509 certificates Future integration with NMAS (Novell Modular Authentication Services) will provide additional methods including Smart Card, Token and Biometric • Multi-factor authentication 4 Combination of authentication methods • Contextless Login
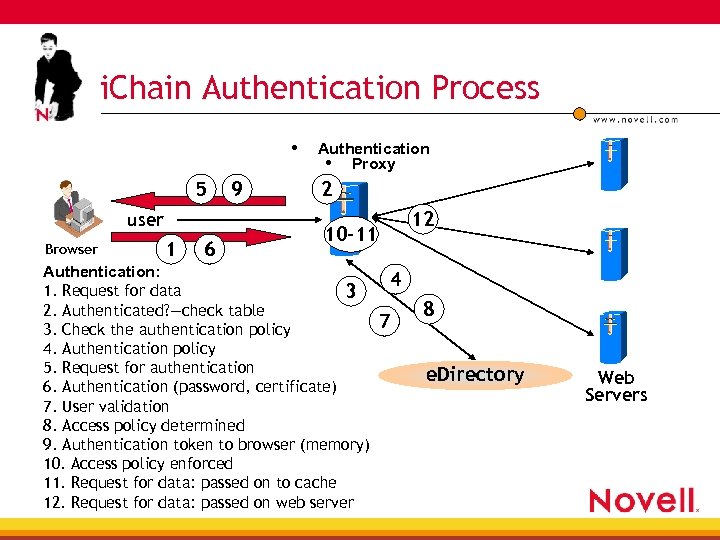 i. Chain Authentication Process • 5 user Browser 1 6 9 Authentication • Proxy 2 12 10 -11 Authentication: 1. Request for data 3 2. Authenticated? —check table 3. Check the authentication policy 4. Authentication policy 5. Request for authentication 6. Authentication (password, certificate) 7. User validation 8. Access policy determined 9. Authentication token to browser (memory) 10. Access policy enforced 11. Request for data: passed on to cache 12. Request for data: passed on web server 4 7 8 e. Directory Web Servers
i. Chain Authentication Process • 5 user Browser 1 6 9 Authentication • Proxy 2 12 10 -11 Authentication: 1. Request for data 3 2. Authenticated? —check table 3. Check the authentication policy 4. Authentication policy 5. Request for authentication 6. Authentication (password, certificate) 7. User validation 8. Access policy determined 9. Authentication token to browser (memory) 10. Access policy enforced 11. Request for data: passed on to cache 12. Request for data: passed on web server 4 7 8 e. Directory Web Servers
 Single Sign-on to Web Resources • i. Chain will forward (optional) a users logon name and password in the HTTP Authentication Header 4 Any web server using basic authentication will accept the credentials and authenticate the user • OLAC provides an option to use different logon credentials (name and password) 4 Two fields have been added “ICHAIN_UID” and “ICHAIN_PWD”, which can be mapped to any LDAP attribute
Single Sign-on to Web Resources • i. Chain will forward (optional) a users logon name and password in the HTTP Authentication Header 4 Any web server using basic authentication will accept the credentials and authenticate the user • OLAC provides an option to use different logon credentials (name and password) 4 Two fields have been added “ICHAIN_UID” and “ICHAIN_PWD”, which can be mapped to any LDAP attribute
 Data Confidentiality Service • Uses SSL encryption between browser and i. Chain server • Provided by the SSLizer 4 Secure transparent encryption 4 Eliminates need to use SSL service on web servers 4 Easy to setup 4 Performance boost for web servers—offloads web servers from having to run SSL encryption • No-Cache Setting
Data Confidentiality Service • Uses SSL encryption between browser and i. Chain server • Provided by the SSLizer 4 Secure transparent encryption 4 Eliminates need to use SSL service on web servers 4 Easy to setup 4 Performance boost for web servers—offloads web servers from having to run SSL encryption • No-Cache Setting
 Authorization Service • Authorizes access requests based on rules stored as objects in e. Directory 4 4 4 Leverages the e. Directory hierarchy and inheritance mechanisms Cached on i. Chain ICS server for improved performance “Public Access” can be allowed with no authentication point • Access Rules may be assigned to 4 4 Communities Groups Users Containers (O, OU, etc. )
Authorization Service • Authorizes access requests based on rules stored as objects in e. Directory 4 4 4 Leverages the e. Directory hierarchy and inheritance mechanisms Cached on i. Chain ICS server for improved performance “Public Access” can be allowed with no authentication point • Access Rules may be assigned to 4 4 Communities Groups Users Containers (O, OU, etc. )
 Secure Access for Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Novell Modular Authentication Service
Secure Access for Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Novell Modular Authentication Service
 What Is Novell Modular Authentication Service (NMAS)? • A single, cost-effective point of administration for managing, grading, and accessing all biometric, smart card, token, and digital certificate authentication to your enterprise
What Is Novell Modular Authentication Service (NMAS)? • A single, cost-effective point of administration for managing, grading, and accessing all biometric, smart card, token, and digital certificate authentication to your enterprise
 NMAS Benefits • Simplifies strong authentication 4 Manage multiple authentication methods centrally • Secures authentication 4 Encrypts authentication material 4 Provides an alternative to passwords • Accelerate authentication 4 Can automatically authenticate users
NMAS Benefits • Simplifies strong authentication 4 Manage multiple authentication methods centrally • Secures authentication 4 Encrypts authentication material 4 Provides an alternative to passwords • Accelerate authentication 4 Can automatically authenticate users
 NMAS Supported Methods • Passwords 4 e. Directory password, simple password Enhanced password 4 Activ. Card, Vasco, RSA, Secure. Computing 4 4 Entrust Verisign, Baltimore, XCert, etc. 4 Activ. Card, Arcot, Data Card, SPYRUS, RSA, etc. 4 Applied Biometrics, BAC, Bio. ID, Biometricate, DNP, Identix, Iridian, Saflink, Secu. Gen, System Needs, Visionsphere, others 4 • Token • X. 509 v 3 Certificate • Smart Card • Biometric (fingerprint, face, voice, iris, etc. )
NMAS Supported Methods • Passwords 4 e. Directory password, simple password Enhanced password 4 Activ. Card, Vasco, RSA, Secure. Computing 4 4 Entrust Verisign, Baltimore, XCert, etc. 4 Activ. Card, Arcot, Data Card, SPYRUS, RSA, etc. 4 Applied Biometrics, BAC, Bio. ID, Biometricate, DNP, Identix, Iridian, Saflink, Secu. Gen, System Needs, Visionsphere, others 4 • Token • X. 509 v 3 Certificate • Smart Card • Biometric (fingerprint, face, voice, iris, etc. )
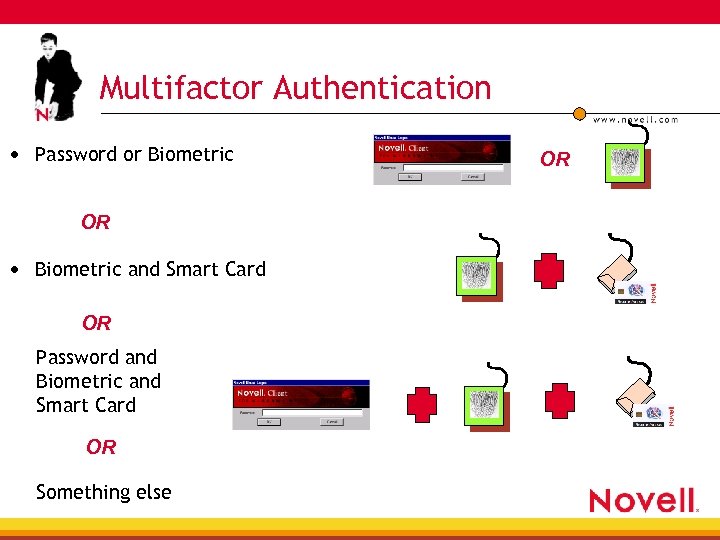 Multifactor Authentication • Password or Biometric OR • Biometric and Smart Card OR Password and Biometric and Smart Card OR Something else OR
Multifactor Authentication • Password or Biometric OR • Biometric and Smart Card OR Password and Biometric and Smart Card OR Something else OR
 What Is an NMAS Method? • Methods are digitally signed code for enabling and securing communication between authentication device and e. Directory 4 4 4 Only signed methods are loaded by NMAS server Allows management of methods between vendors Provides integrity check • Novell does not represent the quality of any login method it signs 4 4 You must determine the suitability of a login method for your security policy Perform due diligence on business and technical strengths of NMAS partner company
What Is an NMAS Method? • Methods are digitally signed code for enabling and securing communication between authentication device and e. Directory 4 4 4 Only signed methods are loaded by NMAS server Allows management of methods between vendors Provides integrity check • Novell does not represent the quality of any login method it signs 4 4 You must determine the suitability of a login method for your security policy Perform due diligence on business and technical strengths of NMAS partner company
 Universal Smart Card Method • Supports Digital Certificate Authentication via 4 PKCS#11 • Gem. Plus, Bull, Schlumberger, SPYRUS, etc. 4 Vendor specific Crypto Service Provider (CSP) • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate Date Validity 4 Intermediate Certificate Authorities 4 Trusted Root Certificate Authority 4 OCSP Validation coming
Universal Smart Card Method • Supports Digital Certificate Authentication via 4 PKCS#11 • Gem. Plus, Bull, Schlumberger, SPYRUS, etc. 4 Vendor specific Crypto Service Provider (CSP) • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate Date Validity 4 Intermediate Certificate Authorities 4 Trusted Root Certificate Authority 4 OCSP Validation coming
 Advanced X. 509 Certificate Method • Supports Digital Certificate authentication via 4 CAPI (Where Internet Explorer stores the keys) 4 PKCS#12 (Standard for protecting private key in a file) • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate date validity 4 Certificate chain supports authentication via any PKCS#12 digital certificate
Advanced X. 509 Certificate Method • Supports Digital Certificate authentication via 4 CAPI (Where Internet Explorer stores the keys) 4 PKCS#12 (Standard for protecting private key in a file) • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate date validity 4 Certificate chain supports authentication via any PKCS#12 digital certificate
 Entrust Method • Supports authentication via Entrust Profile and Entelligence Client • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate Date Validity 4 Certificate Chain
Entrust Method • Supports authentication via Entrust Profile and Entelligence Client • Validation 4 CRL (Certificate Revocation Lists) 4 Certificate Date Validity 4 Certificate Chain
 Enhanced Password Policy Method • Enforce strong password policy for e. Directory authentication 4 Dictionary search 4 Case sensitive 4 Minimum character requirements (alpha and numeric) 4 Minimum case requirements • Managed from same password policy object as SSO
Enhanced Password Policy Method • Enforce strong password policy for e. Directory authentication 4 Dictionary search 4 Case sensitive 4 Minimum character requirements (alpha and numeric) 4 Minimum case requirements • Managed from same password policy object as SSO
 Workstation Access Method • Allows Administrator to control how system behaves after inactivity 4 Support for automatic logout when smart card is removed 4 Can lock workstation OR 4 Can logout user entirely 4 Configurable for individual users 4 Enforced by administrator
Workstation Access Method • Allows Administrator to control how system behaves after inactivity 4 Support for automatic logout when smart card is removed 4 Can lock workstation OR 4 Can logout user entirely 4 Configurable for individual users 4 Enforced by administrator
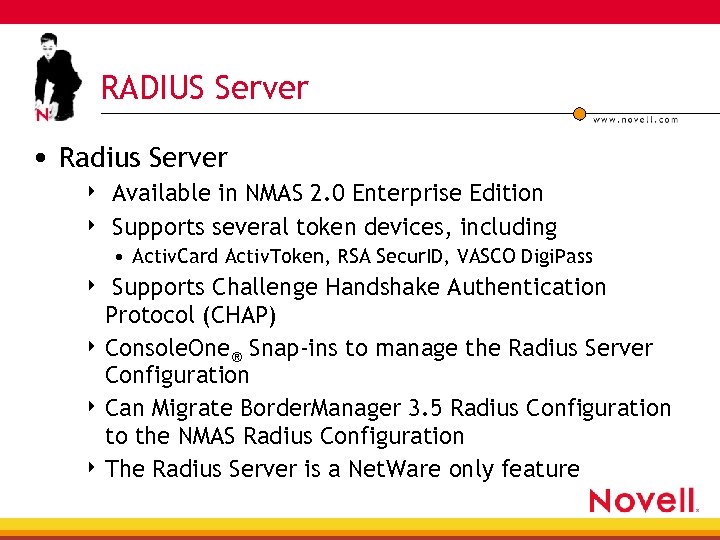 RADIUS Server • Radius Server 4 4 Available in NMAS 2. 0 Enterprise Edition Supports several token devices, including • Activ. Card Activ. Token, RSA Secur. ID, VASCO Digi. Pass Supports Challenge Handshake Authentication Protocol (CHAP) 4 Console. One® Snap-ins to manage the Radius Server Configuration 4 Can Migrate Border. Manager 3. 5 Radius Configuration to the NMAS Radius Configuration 4 The Radius Server is a Net. Ware only feature 4
RADIUS Server • Radius Server 4 4 Available in NMAS 2. 0 Enterprise Edition Supports several token devices, including • Activ. Card Activ. Token, RSA Secur. ID, VASCO Digi. Pass Supports Challenge Handshake Authentication Protocol (CHAP) 4 Console. One® Snap-ins to manage the Radius Server Configuration 4 Can Migrate Border. Manager 3. 5 Radius Configuration to the NMAS Radius Configuration 4 The Radius Server is a Net. Ware only feature 4
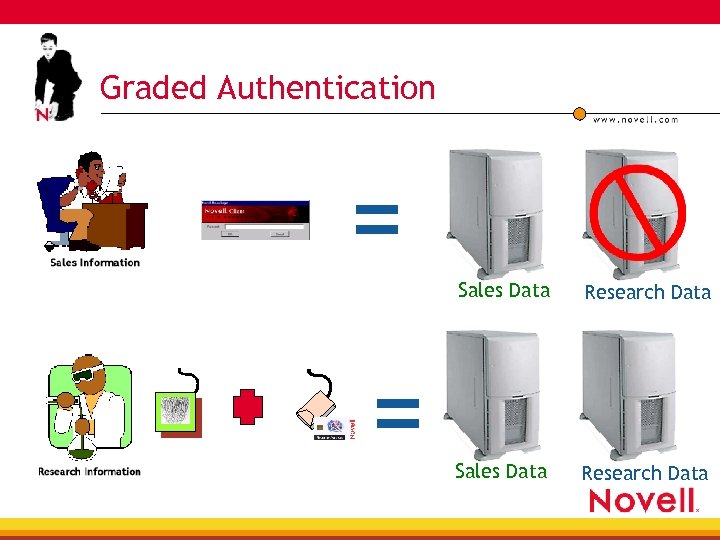 Graded Authentication = Sales Data = Research Data Sales Data Research Data
Graded Authentication = Sales Data = Research Data Sales Data Research Data
 Partners Consulting partners Security Partners Protocom
Partners Consulting partners Security Partners Protocom
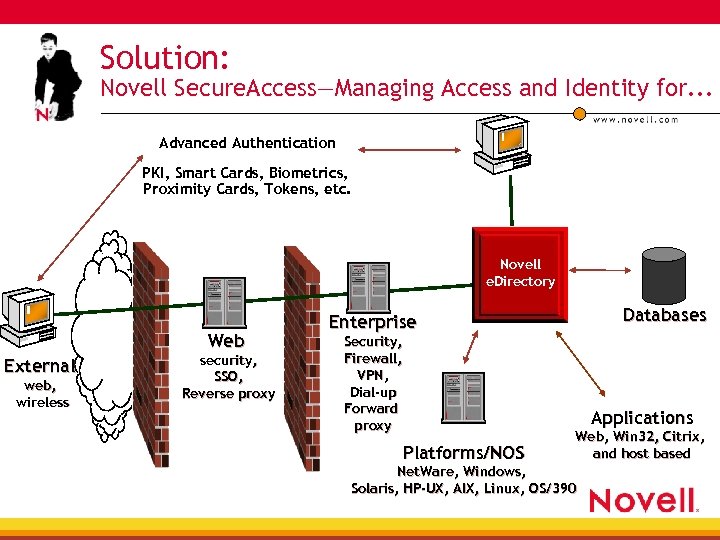 Solution: Novell Secure. Access—Managing Access and Identity for. . . Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Web External web, wireless security, SSO, Reverse proxy Databases Enterprise Security, Firewall, VPN, Dial-up Forward proxy Applications Platforms/NOS Web, Win 32, Citrix, and host based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
Solution: Novell Secure. Access—Managing Access and Identity for. . . Advanced Authentication PKI, Smart Cards, Biometrics, Proximity Cards, Tokens, etc. Novell e. Directory Web External web, wireless security, SSO, Reverse proxy Databases Enterprise Security, Firewall, VPN, Dial-up Forward proxy Applications Platforms/NOS Web, Win 32, Citrix, and host based Net. Ware, Windows, Solaris, HP-UX, AIX, Linux, OS/390
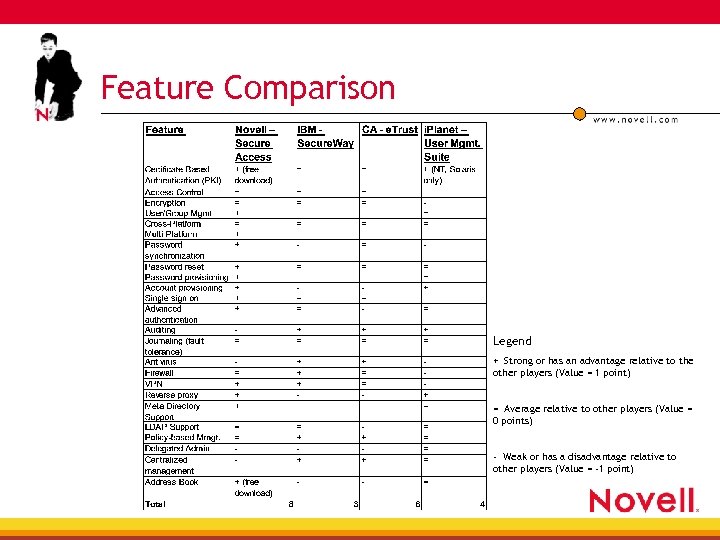 Feature Comparison Legend + Strong or has an advantage relative to the other players (Value = 1 point) = Average relative to other players (Value = 0 points) - Weak or has a disadvantage relative to other players (Value = -1 point)
Feature Comparison Legend + Strong or has an advantage relative to the other players (Value = 1 point) = Average relative to other players (Value = 0 points) - Weak or has a disadvantage relative to other players (Value = -1 point)
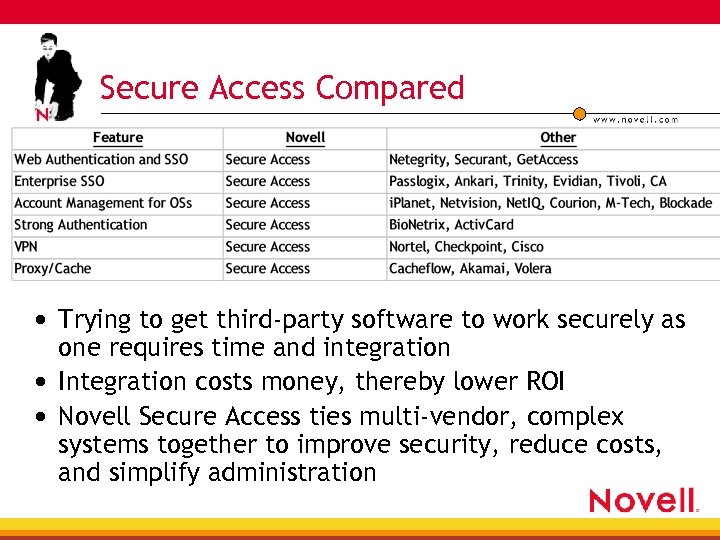 Secure Access Compared • Trying to get third-party software to work securely as one requires time and integration • Integration costs money, thereby lower ROI • Novell Secure Access ties multi-vendor, complex systems together to improve security, reduce costs, and simplify administration
Secure Access Compared • Trying to get third-party software to work securely as one requires time and integration • Integration costs money, thereby lower ROI • Novell Secure Access ties multi-vendor, complex systems together to improve security, reduce costs, and simplify administration
 Managing User’s Access • Regardless of where users are authenticating from, whether it is the web, wireless, dial-up, VPN, or traditional legacy environments, we can integrate and manage the identities of all those users 4 4 Secure authentication Consistent enforcement of access control rules Single sign-on Strong Audit trail • Novell can do this for Novell and third-party products to provision and control access to all applications, databases, platforms, and network resources
Managing User’s Access • Regardless of where users are authenticating from, whether it is the web, wireless, dial-up, VPN, or traditional legacy environments, we can integrate and manage the identities of all those users 4 4 Secure authentication Consistent enforcement of access control rules Single sign-on Strong Audit trail • Novell can do this for Novell and third-party products to provision and control access to all applications, databases, platforms, and network resources
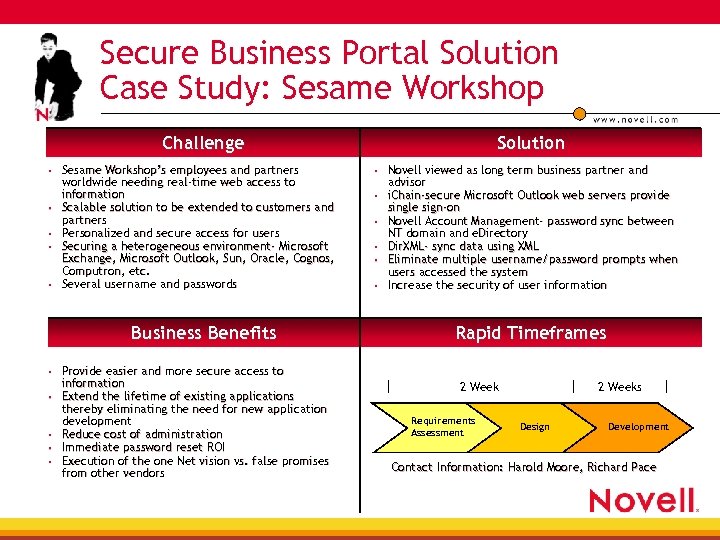 Secure Business Portal Solution Case Study: Sesame Workshop Challenge Sesame Workshop’s employees and partners worldwide needing real-time web access to information Scalable solution to be extended to customers and partners Personalized and secure access for users Securing a heterogeneous environment- Microsoft Exchange, Microsoft Outlook, Sun, Oracle, Cognos, Computron, etc. Computron, Several username and passwords Business Benefits Provide easier and more secure access to information Extend the lifetime of existing applications thereby eliminating the need for new application development Reduce cost of administration Immediate password reset ROI Execution of the one Net vision vs. false promises from other vendors Solution Novell viewed as long term business partner and advisor i. Chain-secure Microsoft Outlook web servers provide single sign-on sign. Novell Account Management- password sync between NT domain and e. Directory Dir. XML- sync data using XML Eliminate multiple username/password prompts when users accessed the system Increase the security of user information Rapid Timeframes 2 Week Requirements Assessment 2 Weeks Design Development Contact Information: Harold Moore, Richard Pace
Secure Business Portal Solution Case Study: Sesame Workshop Challenge Sesame Workshop’s employees and partners worldwide needing real-time web access to information Scalable solution to be extended to customers and partners Personalized and secure access for users Securing a heterogeneous environment- Microsoft Exchange, Microsoft Outlook, Sun, Oracle, Cognos, Computron, etc. Computron, Several username and passwords Business Benefits Provide easier and more secure access to information Extend the lifetime of existing applications thereby eliminating the need for new application development Reduce cost of administration Immediate password reset ROI Execution of the one Net vision vs. false promises from other vendors Solution Novell viewed as long term business partner and advisor i. Chain-secure Microsoft Outlook web servers provide single sign-on sign. Novell Account Management- password sync between NT domain and e. Directory Dir. XML- sync data using XML Eliminate multiple username/password prompts when users accessed the system Increase the security of user information Rapid Timeframes 2 Week Requirements Assessment 2 Weeks Design Development Contact Information: Harold Moore, Richard Pace
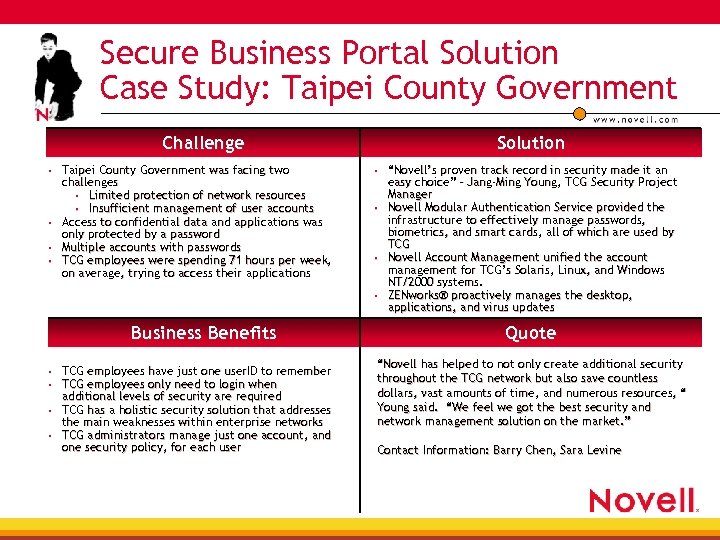 Secure Business Portal Solution Case Study: Taipei County Government Challenge Taipei County Government was facing two challenges Limited protection of network resources Insufficient management of user accounts Access to confidential data and applications was only protected by a password Multiple accounts with passwords TCG employees were spending 71 hours per week, on average, trying to access their applications Solution Business Benefits TCG employees have just one user. ID to remember user. ID TCG employees only need to login when additional levels of security are required TCG has a holistic security solution that addresses the main weaknesses within enterprise networks TCG administrators manage just one account, and one security policy, for each user “Novell’s proven track record in security made it an easy choice” – Jang-Ming Young, TCG Security Project Manager Novell Modular Authentication Service provided the infrastructure to effectively manage passwords, biometrics, and smart cards, all of which are used by TCG Novell Account Management unified the account management for TCG’s Solaris, Linux, and Windows NT/2000 systems. ZENworks® proactively manages the desktop, ZENworks® applications, and virus updates Quote “Novell has helped to not only create additional security throughout the TCG network but also save countless dollars, vast amounts of time, and numerous resources, “ Young said. “We feel we got the best security and network management solution on the market. ” Contact Information: Barry Chen, Sara Levine
Secure Business Portal Solution Case Study: Taipei County Government Challenge Taipei County Government was facing two challenges Limited protection of network resources Insufficient management of user accounts Access to confidential data and applications was only protected by a password Multiple accounts with passwords TCG employees were spending 71 hours per week, on average, trying to access their applications Solution Business Benefits TCG employees have just one user. ID to remember user. ID TCG employees only need to login when additional levels of security are required TCG has a holistic security solution that addresses the main weaknesses within enterprise networks TCG administrators manage just one account, and one security policy, for each user “Novell’s proven track record in security made it an easy choice” – Jang-Ming Young, TCG Security Project Manager Novell Modular Authentication Service provided the infrastructure to effectively manage passwords, biometrics, and smart cards, all of which are used by TCG Novell Account Management unified the account management for TCG’s Solaris, Linux, and Windows NT/2000 systems. ZENworks® proactively manages the desktop, ZENworks® applications, and virus updates Quote “Novell has helped to not only create additional security throughout the TCG network but also save countless dollars, vast amounts of time, and numerous resources, “ Young said. “We feel we got the best security and network management solution on the market. ” Contact Information: Barry Chen, Sara Levine



