L5_14_shortened.ppt
- Количество слайдов: 31
 Access Control Lists Lecture 5
Access Control Lists Lecture 5
 Access control lists (ACL, списки управління доступом) • A router acts as a packet filter when it forwards or denies packets according to filtering rules. • An ACL is a sequential list of permit (дозволити) or deny (відхилити) statements • Powerful way to control traffic into and out of the network. 2
Access control lists (ACL, списки управління доступом) • A router acts as a packet filter when it forwards or denies packets according to filtering rules. • An ACL is a sequential list of permit (дозволити) or deny (відхилити) statements • Powerful way to control traffic into and out of the network. 2
 ACL criteria • The ACL can extract the following information from the packet header, test it against its rules, and make “permit" or "deny" decisions based on: • • • Source IP address Destination IP address MAC address Protocol type TCP/UDP source and/or destination port 3
ACL criteria • The ACL can extract the following information from the packet header, test it against its rules, and make “permit" or "deny" decisions based on: • • • Source IP address Destination IP address MAC address Protocol type TCP/UDP source and/or destination port 3
 Tasks provided by ACLs: • Limit network traffic to increase network performance. • Provide traffic flow control. • Provide a basic level of security for network access. • Decide which types of traffic to forward or block at the router interfaces. • Control which areas a client can access on a network. 4
Tasks provided by ACLs: • Limit network traffic to increase network performance. • Provide traffic flow control. • Provide a basic level of security for network access. • Decide which types of traffic to forward or block at the router interfaces. • Control which areas a client can access on a network. 4
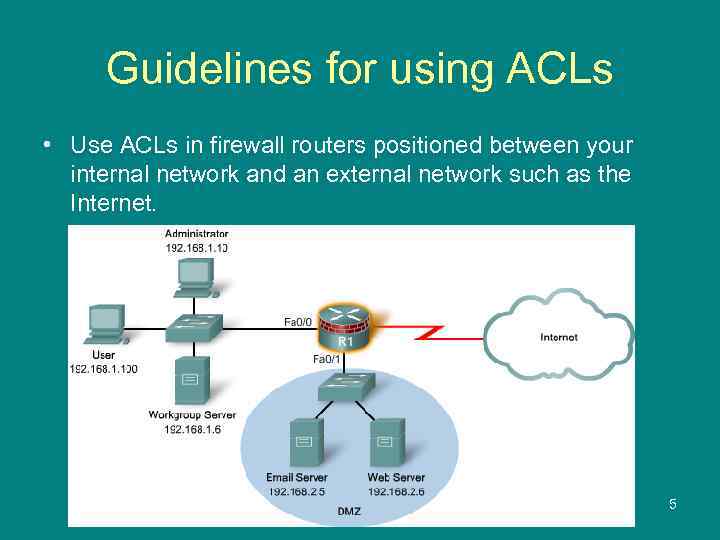 Guidelines for using ACLs • Use ACLs in firewall routers positioned between your internal network and an external network such as the Internet. 5
Guidelines for using ACLs • Use ACLs in firewall routers positioned between your internal network and an external network such as the Internet. 5
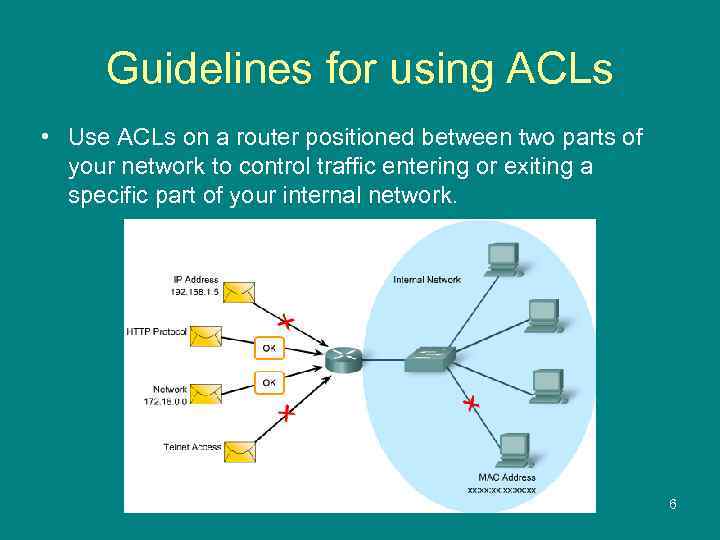 Guidelines for using ACLs • Use ACLs on a router positioned between two parts of your network to control traffic entering or exiting a specific part of your internal network. 6
Guidelines for using ACLs • Use ACLs on a router positioned between two parts of your network to control traffic entering or exiting a specific part of your internal network. 6
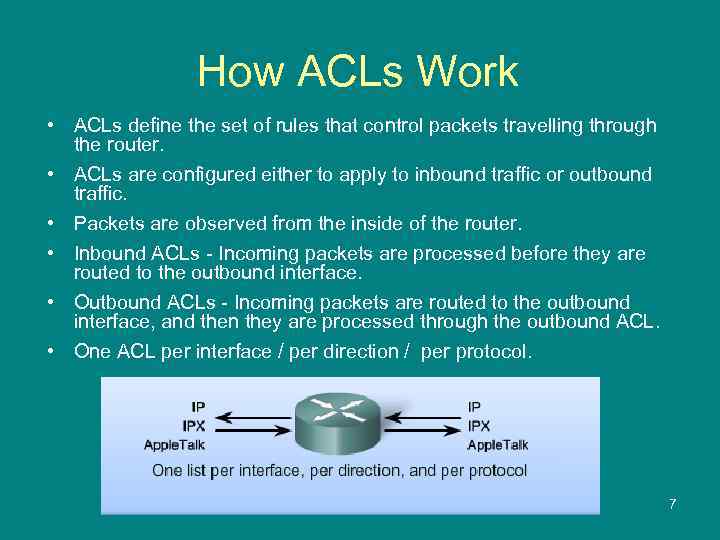 How ACLs Work • ACLs define the set of rules that control packets travelling through the router. • ACLs are configured either to apply to inbound traffic or outbound traffic. • Packets are observed from the inside of the router. • Inbound ACLs - Incoming packets are processed before they are routed to the outbound interface. • Outbound ACLs - Incoming packets are routed to the outbound interface, and then they are processed through the outbound ACL. • One ACL per interface / per direction / per protocol. 7
How ACLs Work • ACLs define the set of rules that control packets travelling through the router. • ACLs are configured either to apply to inbound traffic or outbound traffic. • Packets are observed from the inside of the router. • Inbound ACLs - Incoming packets are processed before they are routed to the outbound interface. • Outbound ACLs - Incoming packets are routed to the outbound interface, and then they are processed through the outbound ACL. • One ACL per interface / per direction / per protocol. 7
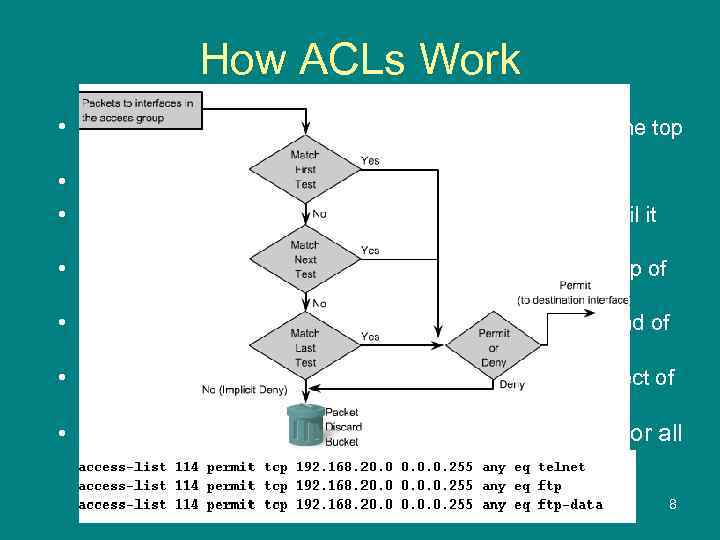 How ACLs Work • ACL statements operate in sequential order, from the top • • down, one statement at a time. Rules of the same ACL have the same ACL number. The router continues to process the ACL statements until it has a match. The most frequently used ACL rules are placed at the top of the list. If no matches are found when the router reaches the end of the list, the traffic is denied by default. • A single-entry ACL with only one deny entry has the effect of denying all traffic. • You must have at least one permit statement in an ACL or all traffic is blocked. 8
How ACLs Work • ACL statements operate in sequential order, from the top • • down, one statement at a time. Rules of the same ACL have the same ACL number. The router continues to process the ACL statements until it has a match. The most frequently used ACL rules are placed at the top of the list. If no matches are found when the router reaches the end of the list, the traffic is denied by default. • A single-entry ACL with only one deny entry has the effect of denying all traffic. • You must have at least one permit statement in an ACL or all traffic is blocked. 8
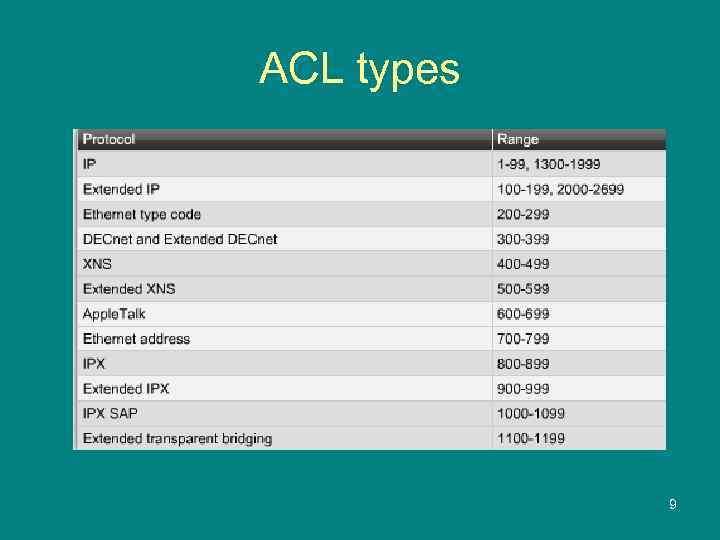 ACL types 9
ACL types 9
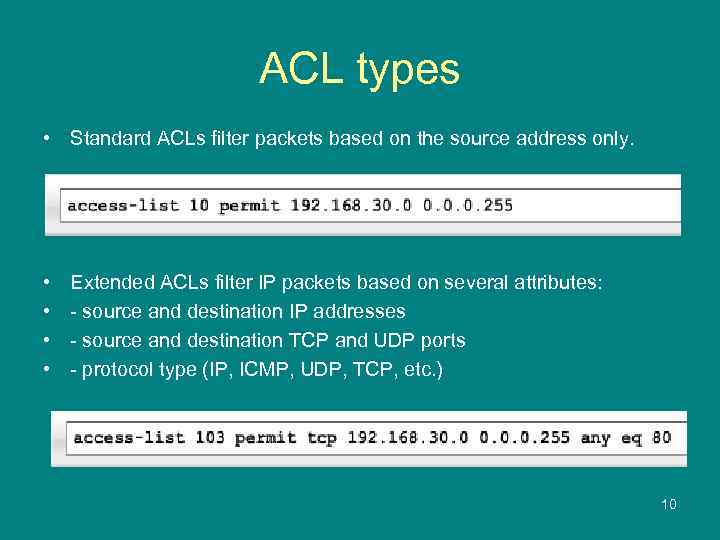 ACL types • Standard ACLs filter packets based on the source address only. • • Extended ACLs filter IP packets based on several attributes: - source and destination IP addresses - source and destination TCP and UDP ports - protocol type (IP, ICMP, UDP, TCP, etc. ) 10
ACL types • Standard ACLs filter packets based on the source address only. • • Extended ACLs filter IP packets based on several attributes: - source and destination IP addresses - source and destination TCP and UDP ports - protocol type (IP, ICMP, UDP, TCP, etc. ) 10
 ACL placement • Each ACL is bounded to the interface, where the packets will be checked in one of two directions (in or out). • Every ACL should be placed where it has the greatest impact on performance. • Placement must be determined in the context of where the control of the network administrator extends. • Locate extended ACLs as close as possible to the source of the traffic denied. This way, undesirable traffic is filtered without crossing the network infrastructure. • Because standard ACLs do not specify destination addresses, place them as close to the destination as possible. 11
ACL placement • Each ACL is bounded to the interface, where the packets will be checked in one of two directions (in or out). • Every ACL should be placed where it has the greatest impact on performance. • Placement must be determined in the context of where the control of the network administrator extends. • Locate extended ACLs as close as possible to the source of the traffic denied. This way, undesirable traffic is filtered without crossing the network infrastructure. • Because standard ACLs do not specify destination addresses, place them as close to the destination as possible. 11
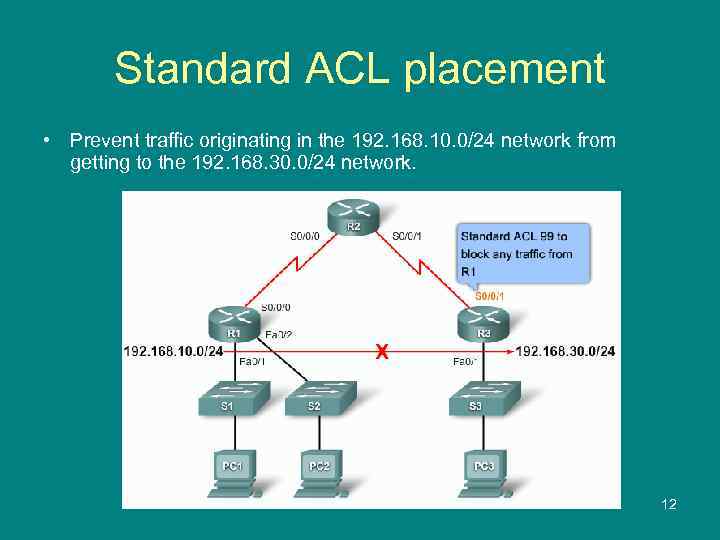 Standard ACL placement • Prevent traffic originating in the 192. 168. 10. 0/24 network from getting to the 192. 168. 30. 0/24 network. 12
Standard ACL placement • Prevent traffic originating in the 192. 168. 10. 0/24 network from getting to the 192. 168. 30. 0/24 network. 12
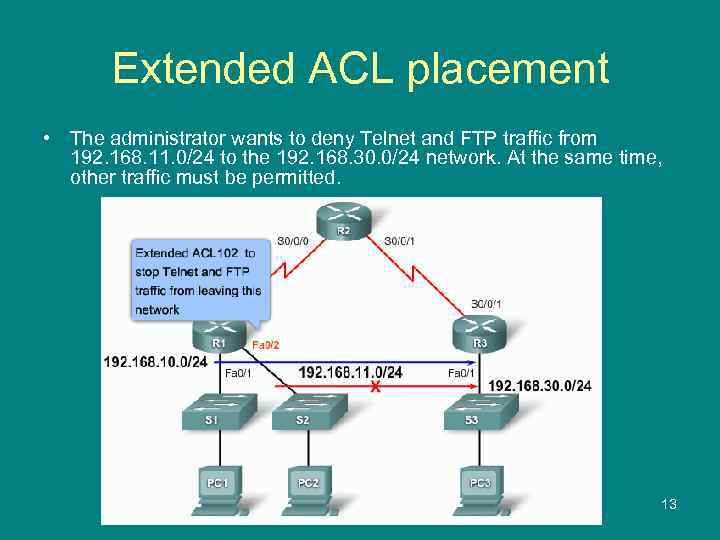 Extended ACL placement • The administrator wants to deny Telnet and FTP traffic from 192. 168. 11. 0/24 to the 192. 168. 30. 0/24 network. At the same time, other traffic must be permitted. 13
Extended ACL placement • The administrator wants to deny Telnet and FTP traffic from 192. 168. 11. 0/24 to the 192. 168. 30. 0/24 network. At the same time, other traffic must be permitted. 13
 Configuring Standard ACLs • To configure standard ACLs on a Cisco router, first create the list of conditions of the standard ACL and then activate the ACL on an interface. • Standard ACL statements are identified with a number in the range of 1 to 99. • The full syntax of the standard ACL command is as follows: • Router(config)#access-list {1 -99} [deny | permit] source-IP-address [source-wildcard mask] • After a standard ACL is configured, it is linked to an interface using the command: • Router(config)# interface type number • Router(config-if)#ip access-group {1 -99} {in | out} 14
Configuring Standard ACLs • To configure standard ACLs on a Cisco router, first create the list of conditions of the standard ACL and then activate the ACL on an interface. • Standard ACL statements are identified with a number in the range of 1 to 99. • The full syntax of the standard ACL command is as follows: • Router(config)#access-list {1 -99} [deny | permit] source-IP-address [source-wildcard mask] • After a standard ACL is configured, it is linked to an interface using the command: • Router(config)# interface type number • Router(config-if)#ip access-group {1 -99} {in | out} 14
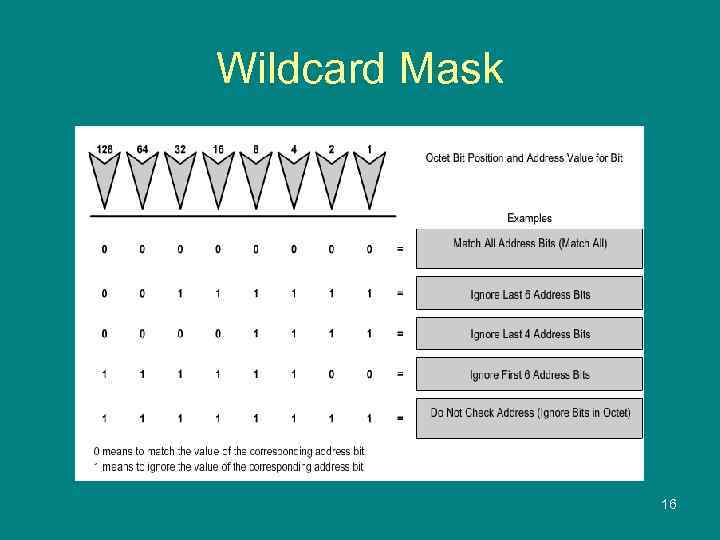
 Wildcard Masking • A wildcard mask (шаблон маски) is a string of binary digits telling the router which parts of the subnet number to look at. • Wildcard masks and subnet masks are both 32 bits long and use binary 1 s and 0 s. • Subnet masks use binary 1 s and 0 s to identify the network, subnet, and host portion of an IP address, respectively. • Wildcard masks use binary 1 s and 0 s to filter individual or groups of hosts to permit or deny access based on IP addresses. • Wildcard mask is sometimes an inverted subnet mask. • Wildcard masks use the following rules to match binary 1 s and 0 s: • Wildcard mask bit 0 - Match the corresponding bit value in the reference IP address. • Wildcard mask bit 1 - Ignore the corresponding bit value in the reference IP address. 15
Wildcard Masking • A wildcard mask (шаблон маски) is a string of binary digits telling the router which parts of the subnet number to look at. • Wildcard masks and subnet masks are both 32 bits long and use binary 1 s and 0 s. • Subnet masks use binary 1 s and 0 s to identify the network, subnet, and host portion of an IP address, respectively. • Wildcard masks use binary 1 s and 0 s to filter individual or groups of hosts to permit or deny access based on IP addresses. • Wildcard mask is sometimes an inverted subnet mask. • Wildcard masks use the following rules to match binary 1 s and 0 s: • Wildcard mask bit 0 - Match the corresponding bit value in the reference IP address. • Wildcard mask bit 1 - Ignore the corresponding bit value in the reference IP address. 15
 Wildcard Mask 16
Wildcard Mask 16
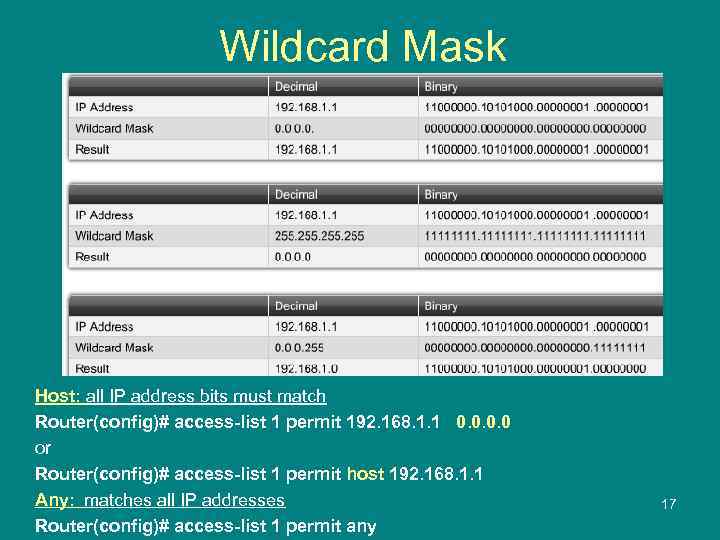 Wildcard Mask Host: all IP address bits must match Router(config)# access-list 1 permit 192. 168. 1. 1 0. 0 or Router(config)# access-list 1 permit host 192. 168. 1. 1 Any: matches all IP addresses Router(config)# access-list 1 permit any 17
Wildcard Mask Host: all IP address bits must match Router(config)# access-list 1 permit 192. 168. 1. 1 0. 0 or Router(config)# access-list 1 permit host 192. 168. 1. 1 Any: matches all IP addresses Router(config)# access-list 1 permit any 17
 Wildcard Mask Application 192. 168. 1. 0: 11000000. 10101000. 00000001 XOR 0. 0. 0. 255: Pattern: 00000000. 1111 11000000. 10101000. 00000001. XXXX Check: 192. 168. 1. 100: 11000000. 10101000. 00000001. 01100100 0. 0. 0. 255 Result: 00000000. 1111 11000000. 10101000. 00000001. XXXX MATCH!!!! 192. 168. 2. 1: 11000000. 10101000. 00000010. 01100100 Pattern: 11000000. 10101000. 00000001. XXXX No MATCH!!! 18
Wildcard Mask Application 192. 168. 1. 0: 11000000. 10101000. 00000001 XOR 0. 0. 0. 255: Pattern: 00000000. 1111 11000000. 10101000. 00000001. XXXX Check: 192. 168. 1. 100: 11000000. 10101000. 00000001. 01100100 0. 0. 0. 255 Result: 00000000. 1111 11000000. 10101000. 00000001. XXXX MATCH!!!! 192. 168. 2. 1: 11000000. 10101000. 00000010. 01100100 Pattern: 11000000. 10101000. 00000001. XXXX No MATCH!!! 18
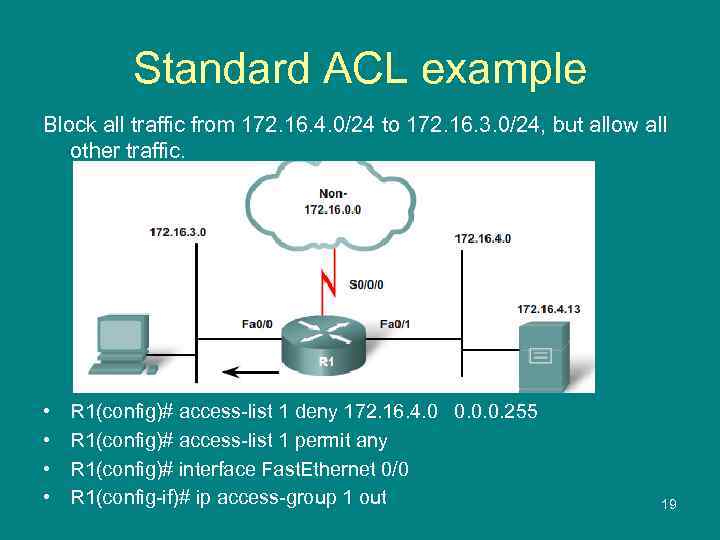 Standard ACL example Block all traffic from 172. 16. 4. 0/24 to 172. 16. 3. 0/24, but allow all other traffic. • • R 1(config)# access-list 1 deny 172. 16. 4. 0 0. 0. 0. 255 R 1(config)# access-list 1 permit any R 1(config)# interface Fast. Ethernet 0/0 R 1(config-if)# ip access-group 1 out 19
Standard ACL example Block all traffic from 172. 16. 4. 0/24 to 172. 16. 3. 0/24, but allow all other traffic. • • R 1(config)# access-list 1 deny 172. 16. 4. 0 0. 0. 0. 255 R 1(config)# access-list 1 permit any R 1(config)# interface Fast. Ethernet 0/0 R 1(config-if)# ip access-group 1 out 19
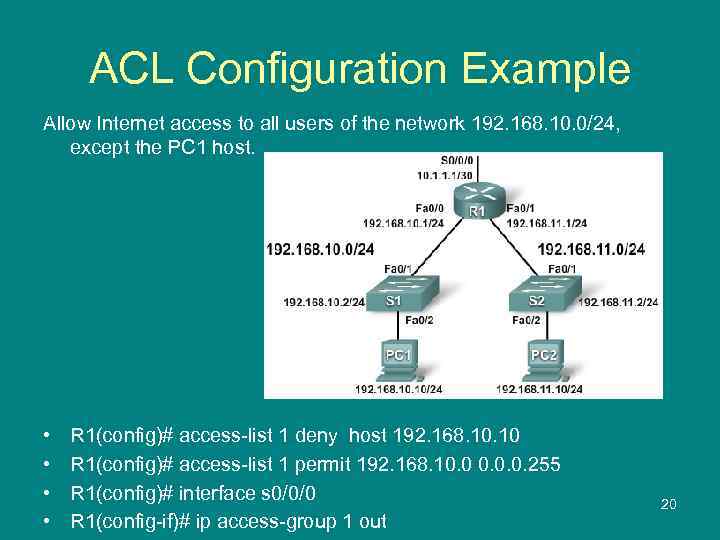 ACL Configuration Example Allow Internet access to all users of the network 192. 168. 10. 0/24, except the PC 1 host. • • R 1(config)# access-list 1 deny host 192. 168. 10 R 1(config)# access-list 1 permit 192. 168. 10. 0. 0. 255 R 1(config)# interface s 0/0/0 R 1(config-if)# ip access-group 1 out 20
ACL Configuration Example Allow Internet access to all users of the network 192. 168. 10. 0/24, except the PC 1 host. • • R 1(config)# access-list 1 deny host 192. 168. 10 R 1(config)# access-list 1 permit 192. 168. 10. 0. 0. 255 R 1(config)# interface s 0/0/0 R 1(config-if)# ip access-group 1 out 20
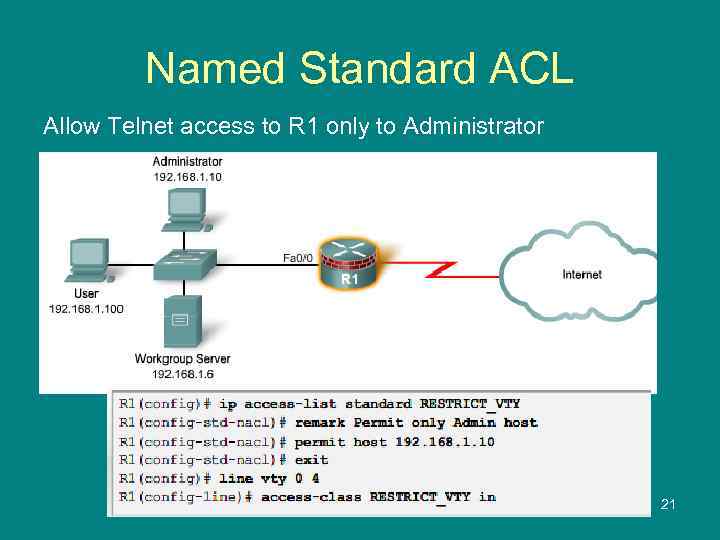 Named Standard ACL Allow Telnet access to R 1 only to Administrator 21
Named Standard ACL Allow Telnet access to R 1 only to Administrator 21
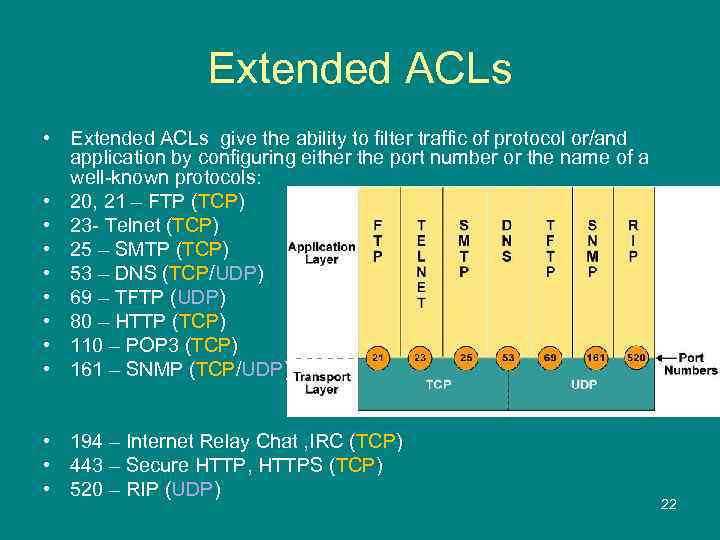 Extended ACLs • Extended ACLs give the ability to filter traffic of protocol or/and application by configuring either the port number or the name of a well-known protocols: • 20, 21 – FTP (TCP) • 23 - Telnet (TCP) • 25 – SMTP (TCP) • 53 – DNS (TCP/UDP) • 69 – TFTP (UDP) • 80 – HTTP (TCP) • 110 – POP 3 (TCP) • 161 – SNMP (TCP/UDP) • 194 – Internet Relay Chat , IRC (TCP) • 443 – Secure HTTP, HTTPS (TCP) • 520 – RIP (UDP) 22
Extended ACLs • Extended ACLs give the ability to filter traffic of protocol or/and application by configuring either the port number or the name of a well-known protocols: • 20, 21 – FTP (TCP) • 23 - Telnet (TCP) • 25 – SMTP (TCP) • 53 – DNS (TCP/UDP) • 69 – TFTP (UDP) • 80 – HTTP (TCP) • 110 – POP 3 (TCP) • 161 – SNMP (TCP/UDP) • 194 – Internet Relay Chat , IRC (TCP) • 443 – Secure HTTP, HTTPS (TCP) • 520 – RIP (UDP) 22
 Extended ACLs Configuration • The access-list global configuration command defines an extended ACL with a number in the range of 100 to 199. • The full syntax of the extended ACL command is as follows: • Router(config)# access-list {100 -199} {deny|permit} protocol source-IP-addr wildcard_mask destination-IP-addr wildcard_mask operator {port | protocol name}, where protocol – IP, TCP, UDP, ICMP, etc. operator - logical operations, such as equal= (eq), not equal ≠ (neq), greater than >(gt), and less than < (lt). port | protocol name – 20 / ftp, 23 / telnet, 80 / http, www, echo etc. • After the instructions of the extended ACL are configured, it is linked to an interface using the ip access-group command: • Router(config-if)#ip access-group {100 -199} {in | out} 23
Extended ACLs Configuration • The access-list global configuration command defines an extended ACL with a number in the range of 100 to 199. • The full syntax of the extended ACL command is as follows: • Router(config)# access-list {100 -199} {deny|permit} protocol source-IP-addr wildcard_mask destination-IP-addr wildcard_mask operator {port | protocol name}, where protocol – IP, TCP, UDP, ICMP, etc. operator - logical operations, such as equal= (eq), not equal ≠ (neq), greater than >(gt), and less than < (lt). port | protocol name – 20 / ftp, 23 / telnet, 80 / http, www, echo etc. • After the instructions of the extended ACL are configured, it is linked to an interface using the ip access-group command: • Router(config-if)#ip access-group {100 -199} {in | out} 23
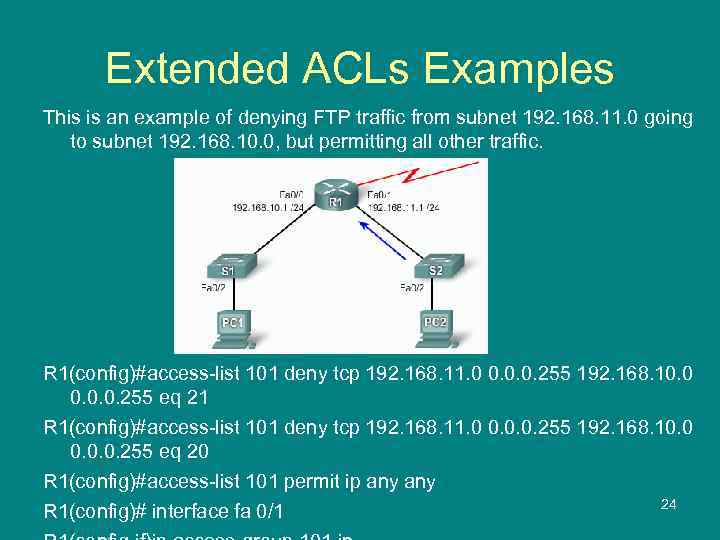 Extended ACLs Examples This is an example of denying FTP traffic from subnet 192. 168. 11. 0 going to subnet 192. 168. 10. 0, but permitting all other traffic. R 1(config)#access-list 101 deny tcp 192. 168. 11. 0 0. 0. 0. 255 192. 168. 10. 0. 0. 255 eq 21 R 1(config)#access-list 101 deny tcp 192. 168. 11. 0 0. 0. 0. 255 192. 168. 10. 0. 0. 255 eq 20 R 1(config)#access-list 101 permit ip any 24 R 1(config)# interface fa 0/1
Extended ACLs Examples This is an example of denying FTP traffic from subnet 192. 168. 11. 0 going to subnet 192. 168. 10. 0, but permitting all other traffic. R 1(config)#access-list 101 deny tcp 192. 168. 11. 0 0. 0. 0. 255 192. 168. 10. 0. 0. 255 eq 21 R 1(config)#access-list 101 deny tcp 192. 168. 11. 0 0. 0. 0. 255 192. 168. 10. 0. 0. 255 eq 20 R 1(config)#access-list 101 permit ip any 24 R 1(config)# interface fa 0/1
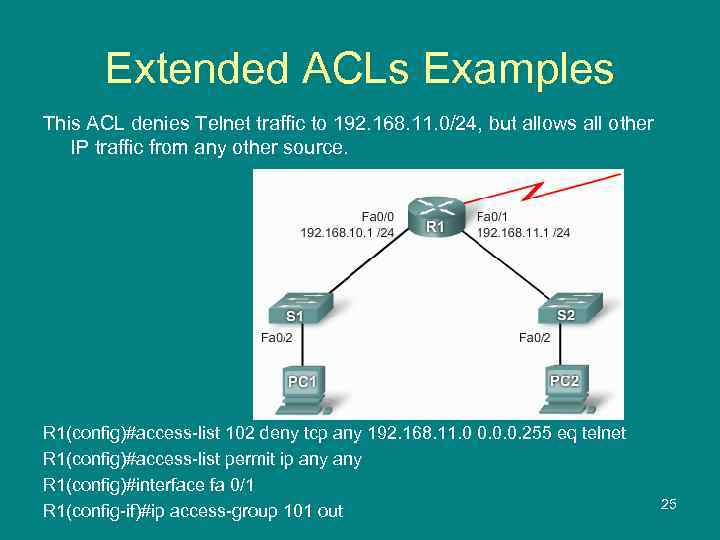 Extended ACLs Examples This ACL denies Telnet traffic to 192. 168. 11. 0/24, but allows all other IP traffic from any other source. R 1(config)#access-list 102 deny tcp any 192. 168. 11. 0 0. 0. 0. 255 eq telnet R 1(config)#access-list permit ip any R 1(config)#interface fa 0/1 R 1(config-if)#ip access-group 101 out 25
Extended ACLs Examples This ACL denies Telnet traffic to 192. 168. 11. 0/24, but allows all other IP traffic from any other source. R 1(config)#access-list 102 deny tcp any 192. 168. 11. 0 0. 0. 0. 255 eq telnet R 1(config)#access-list permit ip any R 1(config)#interface fa 0/1 R 1(config-if)#ip access-group 101 out 25
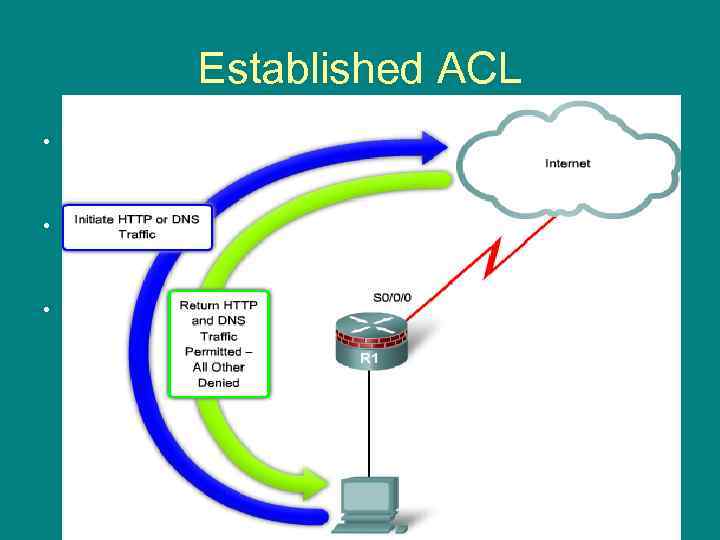 Established ACL • The basic idea of firewall is that all traffic from the outside should be blocked from entering the inside unless it is explicitly permitted by an ACL, or if it is returning traffic initiated from the inside of the network. • The established keyword forces the router to check whether the TCP connection was initiated from the inside. (ACK or RST control flag is set). • If not, it is assumed that the traffic is associated with a new connection initiated from the outside. 26
Established ACL • The basic idea of firewall is that all traffic from the outside should be blocked from entering the inside unless it is explicitly permitted by an ACL, or if it is returning traffic initiated from the inside of the network. • The established keyword forces the router to check whether the TCP connection was initiated from the inside. (ACK or RST control flag is set). • If not, it is assumed that the traffic is associated with a new connection initiated from the outside. 26
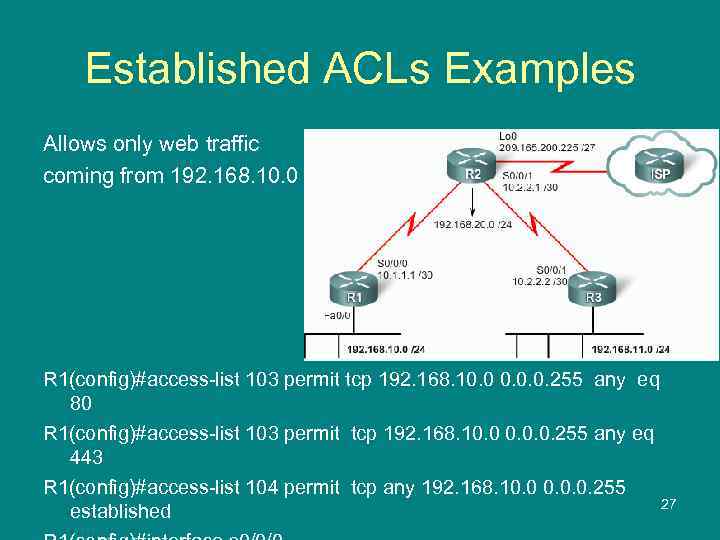 Established ACLs Examples Allows only web traffic coming from 192. 168. 10. 0 R 1(config)#access-list 103 permit tcp 192. 168. 10. 0. 0. 255 any eq 80 R 1(config)#access-list 103 permit tcp 192. 168. 10. 0. 0. 255 any eq 443 R 1(config)#access-list 104 permit tcp any 192. 168. 10. 0. 0. 255 27 established
Established ACLs Examples Allows only web traffic coming from 192. 168. 10. 0 R 1(config)#access-list 103 permit tcp 192. 168. 10. 0. 0. 255 any eq 80 R 1(config)#access-list 103 permit tcp 192. 168. 10. 0. 0. 255 any eq 443 R 1(config)#access-list 104 permit tcp any 192. 168. 10. 0. 0. 255 27 established
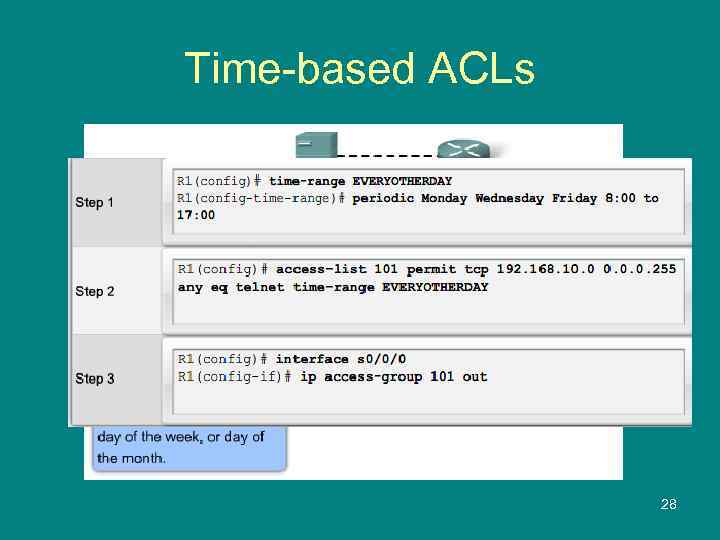 Time-based ACLs 28
Time-based ACLs 28
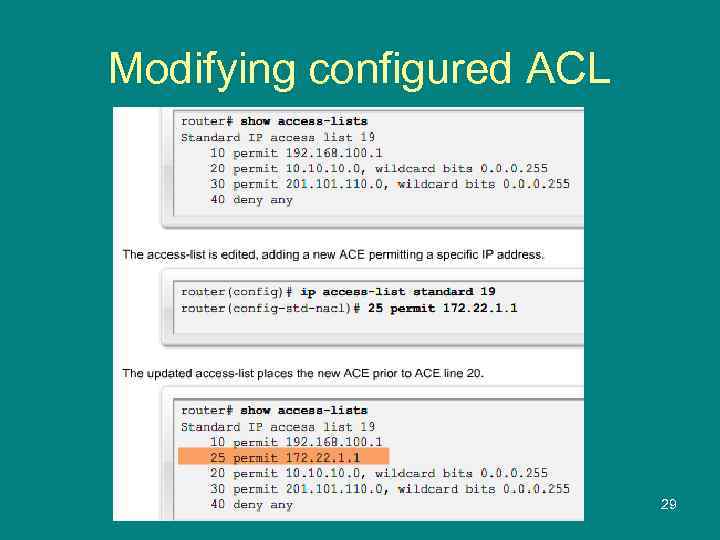 Modifying configured ACL 29
Modifying configured ACL 29
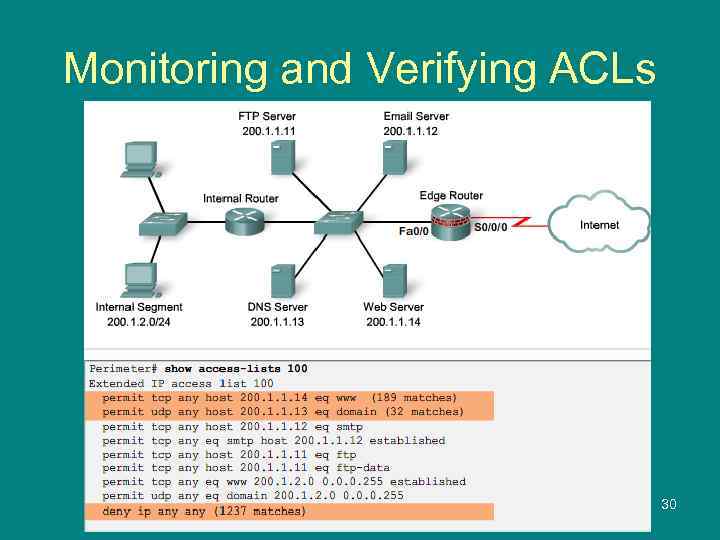 Monitoring and Verifying ACLs 30
Monitoring and Verifying ACLs 30
 Questions ? ? ? 31
Questions ? ? ? 31


