29c63e0dd2248b512db50eaeb0487381.ppt
- Количество слайдов: 31


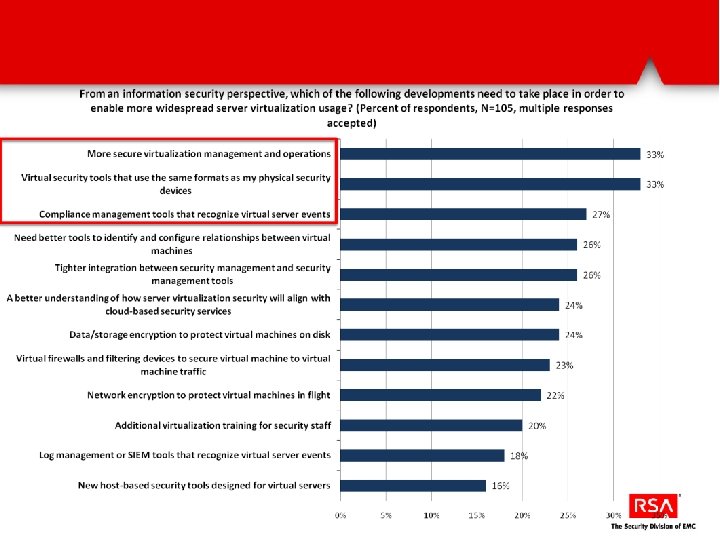

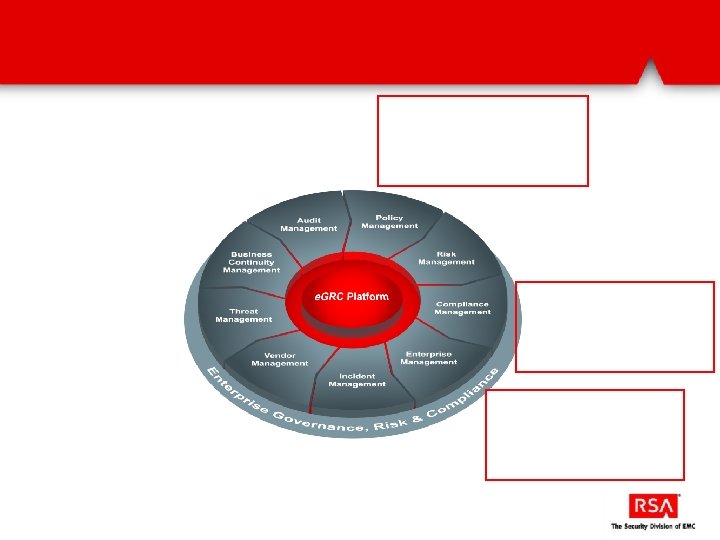
Accelerate/start virtualization of business critical apps to continue optimizing costs Manage risk and compliance while going from IT production to business production Lack of visibility into and control over security and compliance status of the virtual infrastructure Difficult to rationalize the complexity of compliance requirements across virtual and physical environments Lack of guidance and orchestration for securing virtual infrastructure comprehensively Lack of consistency in physical and virtual security increases cost and complexity of virtualization High cost and difficulty of responding to compliance audits for virtual environments Inefficient management of security and compliance across IT and security operations teams Fragmented views of data across hybrid infrastructure causes delays in identifying risk and compliance breaches/concerns


8
9



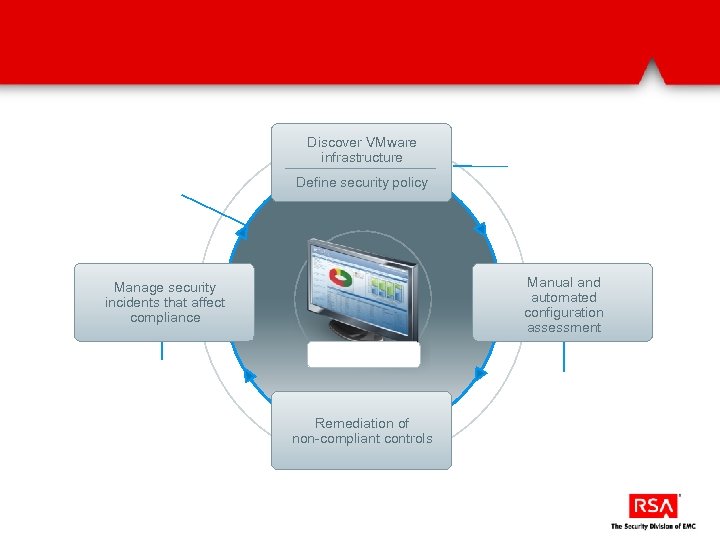
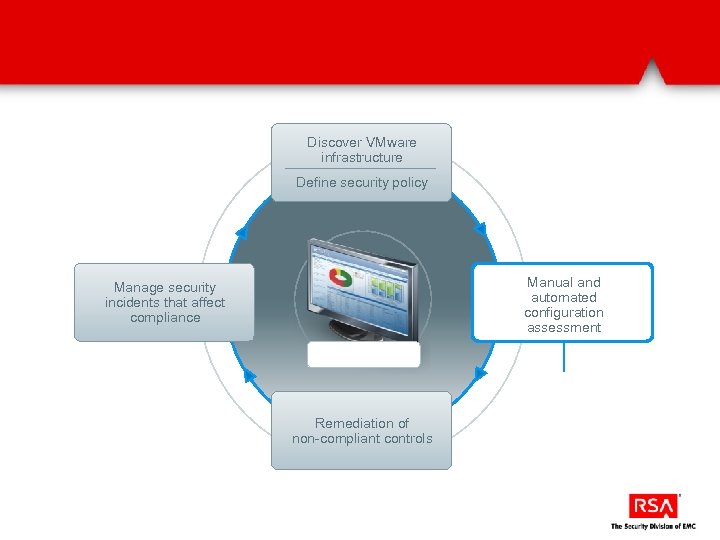
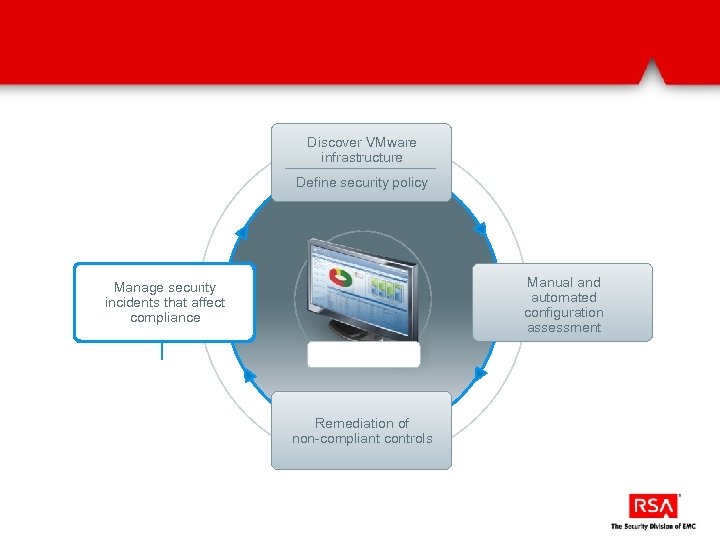
Discover VMware infrastructure Define security policy Manual and automated configuration assessment Manage security incidents that affect compliance Remediation of non-compliant controls
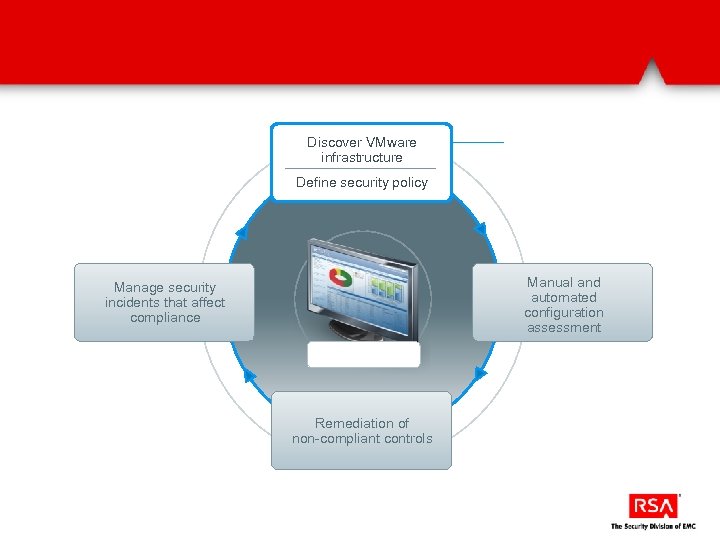
Discover VMware infrastructure Define security policy Manual and automated configuration assessment Manage security incidents that affect compliance Remediation of non-compliant controls
Discover VMware infrastructure Define security policy Manual and automated configuration assessment Manage security incidents that affect compliance Remediation of non-compliant controls
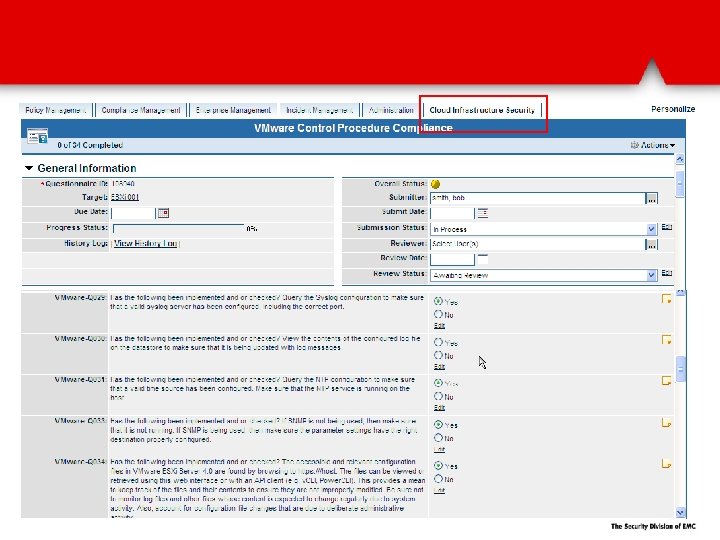
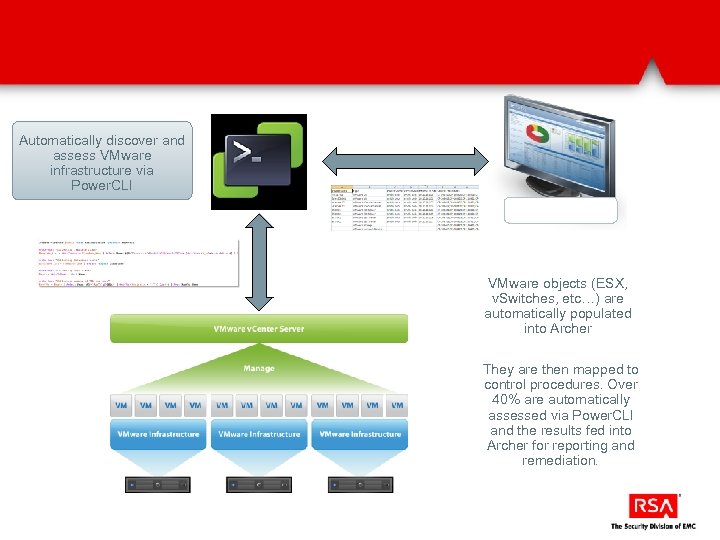
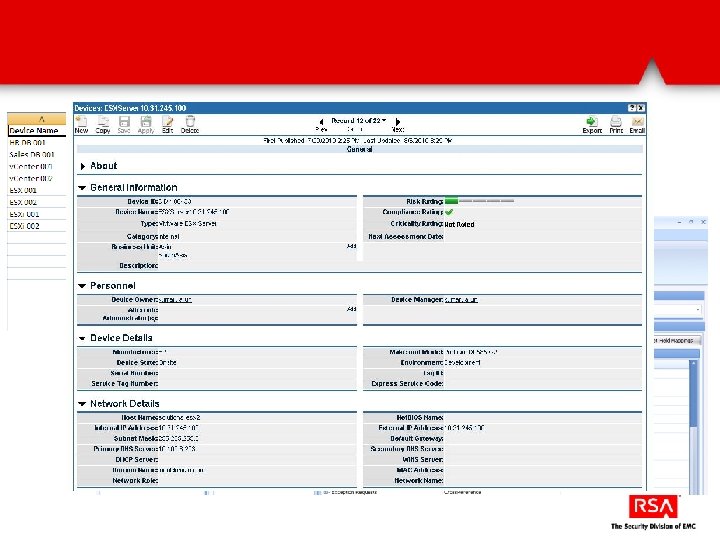
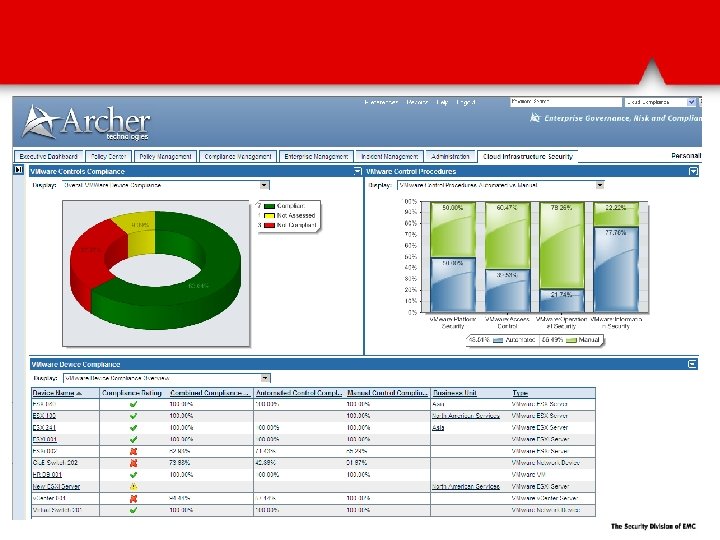
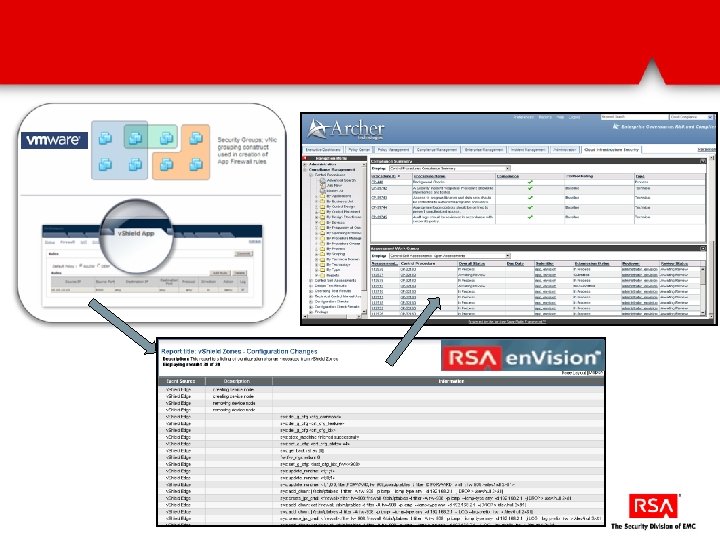
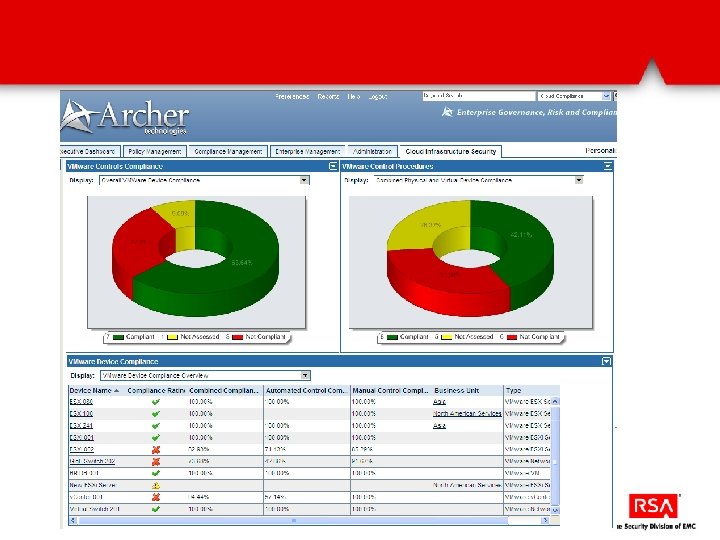
Automatically discover and assess VMware infrastructure via Power. CLI VMware objects (ESX, v. Switches, etc…) are automatically populated into Archer They are then mapped to control procedures. Over 40% are automatically assessed via Power. CLI and the results fed into Archer for reporting and remediation.
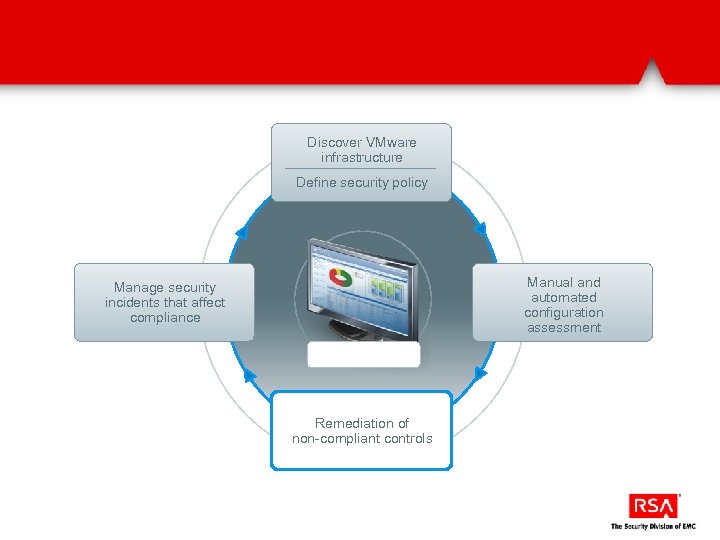
Discover VMware infrastructure Define security policy Manual and automated configuration assessment Manage security incidents that affect compliance Remediation of non-compliant controls
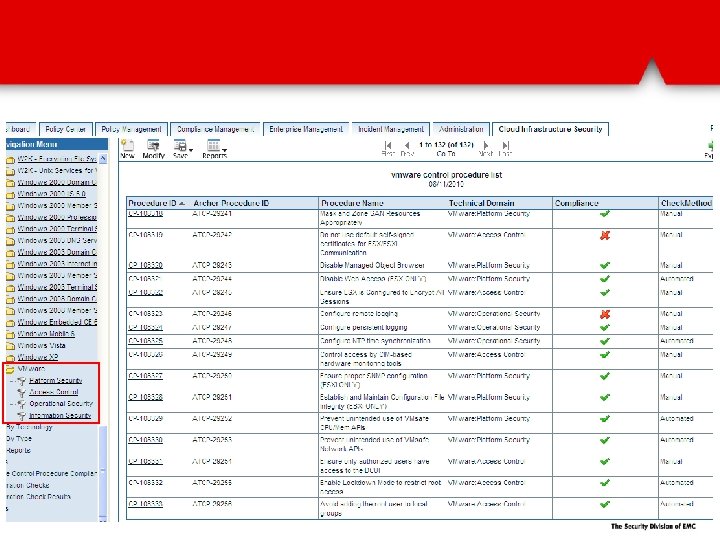
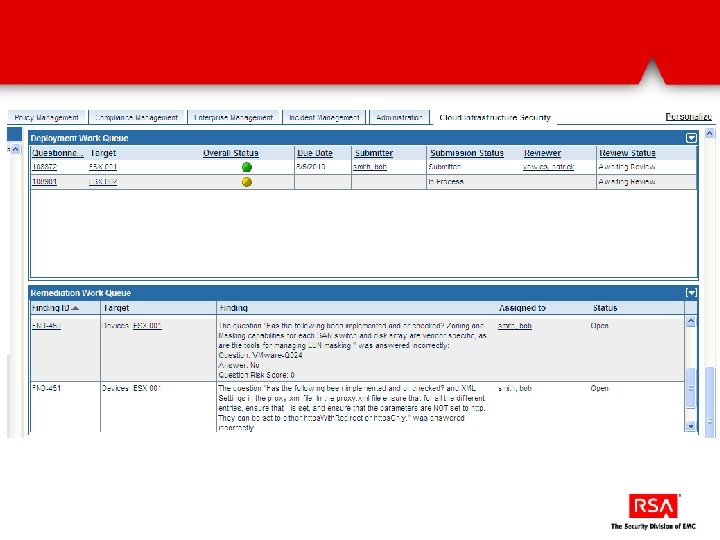
Discover VMware infrastructure Define security policy Manual and automated configuration assessment Manage security incidents that affect compliance Remediation of non-compliant controls


29c63e0dd2248b512db50eaeb0487381.ppt