4e7298b135d9b4fa214805ef6481f59b.ppt
- Количество слайдов: 83
 AAA Authentication, Authorization, and Accounting © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -1
AAA Authentication, Authorization, and Accounting © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -1
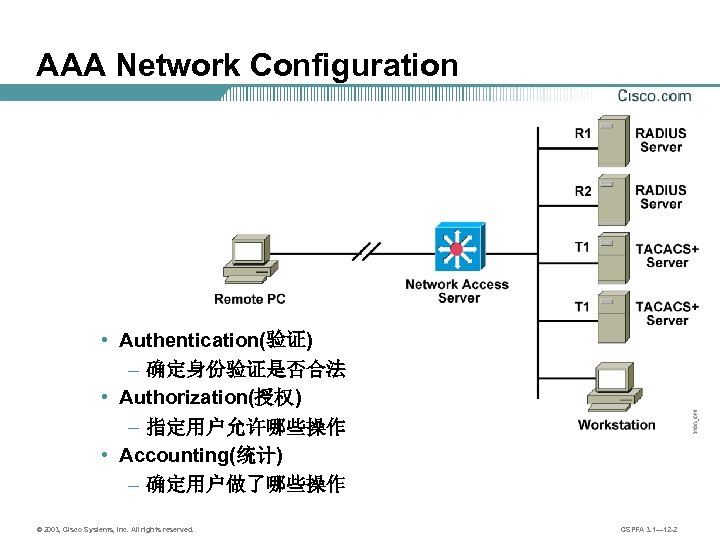 AAA Network Configuration • Authentication(验证) – 确定身份验证是否合法 • Authorization(授权) – 指定用户允许哪些操作 • Accounting(统计) – 确定用户做了哪些操作 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -2
AAA Network Configuration • Authentication(验证) – 确定身份验证是否合法 • Authorization(授权) – 指定用户允许哪些操作 • Accounting(统计) – 确定用户做了哪些操作 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -2
 AAA 认证流程的角色 CISCO 的AAA 认证流程的角色: AAA user: 远程访问者 AAA client: RAS接入 服务器 AAA server: ACS 服务器(或在RAS 服务器本地验证) AAA database: 数据库服务器(或在ACS 服务器上、或RAS 服 务器本地) 接入服务器和访问控制服务器可使用以下安全协议: TACACS+: 运行于TCP之上, cisco私有, 能将验证和授权分开 RADIUS: 运行于UDP上, 开放的协议, 不可将验证和授权分开 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -3
AAA 认证流程的角色 CISCO 的AAA 认证流程的角色: AAA user: 远程访问者 AAA client: RAS接入 服务器 AAA server: ACS 服务器(或在RAS 服务器本地验证) AAA database: 数据库服务器(或在ACS 服务器上、或RAS 服 务器本地) 接入服务器和访问控制服务器可使用以下安全协议: TACACS+: 运行于TCP之上, cisco私有, 能将验证和授权分开 RADIUS: 运行于UDP上, 开放的协议, 不可将验证和授权分开 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -3
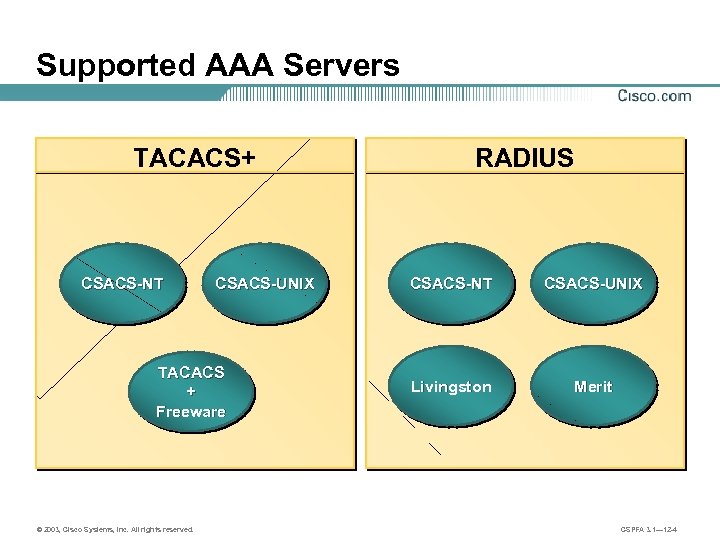 Supported AAA Servers TACACS+ CSACS-NT CSACS-UNIX TACACS + Freeware © 2003, Cisco Systems, Inc. All rights reserved. RADIUS CSACS-NT CSACS-UNIX Livingston Merit CSPFA 3. 1— 12 -4
Supported AAA Servers TACACS+ CSACS-NT CSACS-UNIX TACACS + Freeware © 2003, Cisco Systems, Inc. All rights reserved. RADIUS CSACS-NT CSACS-UNIX Livingston Merit CSPFA 3. 1— 12 -4
 Cisco Secure ACS 安装及基本配置 步骤 1、检查并调整计算机硬件配置,使其满足以下要求: Pentium Ⅲ 550 MHz 以上 256 M 内存 250 M 以上的剩余硬盘空间 步骤 2、检查windows 配置,安装Java run time(JRE)。 步骤 3、检查服务器到Cisco 设备的网络连接。 步骤 4、插入Cisco Secure ACS for windows 光盘,点击“Install”开始 安装,然后按照windows 的提示一步步地完成安装 步骤 5、在浏览器的地址栏里输入“http: //hostname or IP address : 2002”访问ACS 的web 配置页面。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -5
Cisco Secure ACS 安装及基本配置 步骤 1、检查并调整计算机硬件配置,使其满足以下要求: Pentium Ⅲ 550 MHz 以上 256 M 内存 250 M 以上的剩余硬盘空间 步骤 2、检查windows 配置,安装Java run time(JRE)。 步骤 3、检查服务器到Cisco 设备的网络连接。 步骤 4、插入Cisco Secure ACS for windows 光盘,点击“Install”开始 安装,然后按照windows 的提示一步步地完成安装 步骤 5、在浏览器的地址栏里输入“http: //hostname or IP address : 2002”访问ACS 的web 配置页面。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -5
 web 配置页面 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -6
web 配置页面 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -6
 ACS 各导航条配置的选项内容如下: 用户设置(User Setup):查看、创建、编辑、删除用户帐号。 组设置(Group Setup):查看、创建、编辑用户组设置。 共享配置组建(Shared Profile Components):一些可共享的授权组件,它们可以应用与 一个或多个用户或用户组。授权组建包括:Network Access Restriction(NAR)、Command authorization set 和PIX downloadable ACL。 网络配置(Network Configuration):查看、创建、编辑、删除网络服务器(网络设备, 如路由器、交换机等)的参数。 系统配置(System Configuration):启动或停止ACS 服务,创建或删除网络日志,控制ACS 数据库同步等。 接口配置(Interface Configuration):配置TACACS+和RADIUS 的选项。 管理控制(Administration Control):查看、创建、编辑、删除ACS 的管理员帐号参数。 外部数据库(External User Database):配置ACS 的外部数据库类型以及未知的用户策略。 报告和活动(Report and Activity):查看TACACS+和RADIUS 的审计报告、Failed Attempts 报告以及已经登陆的用户信息等。 在线文档(Online Documentation):提供关于Cisco Secure ACS 的更详细的文档。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -7
ACS 各导航条配置的选项内容如下: 用户设置(User Setup):查看、创建、编辑、删除用户帐号。 组设置(Group Setup):查看、创建、编辑用户组设置。 共享配置组建(Shared Profile Components):一些可共享的授权组件,它们可以应用与 一个或多个用户或用户组。授权组建包括:Network Access Restriction(NAR)、Command authorization set 和PIX downloadable ACL。 网络配置(Network Configuration):查看、创建、编辑、删除网络服务器(网络设备, 如路由器、交换机等)的参数。 系统配置(System Configuration):启动或停止ACS 服务,创建或删除网络日志,控制ACS 数据库同步等。 接口配置(Interface Configuration):配置TACACS+和RADIUS 的选项。 管理控制(Administration Control):查看、创建、编辑、删除ACS 的管理员帐号参数。 外部数据库(External User Database):配置ACS 的外部数据库类型以及未知的用户策略。 报告和活动(Report and Activity):查看TACACS+和RADIUS 的审计报告、Failed Attempts 报告以及已经登陆的用户信息等。 在线文档(Online Documentation):提供关于Cisco Secure ACS 的更详细的文档。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -7
 Cisco IOS AAA 认证基本配置 步骤 1、全局开启AAA 服务。 要使用AAA,就必须使用aaa new-model 全局配置命令启用AAA 服务。 Router(config)# aaa new-model 步骤 2、配置ACS 服务器的地址和AAA client 密码,其命令格式如下: AAA Client 和AAA Server 之间使用TACACS+协议时: tacacs-server host IP_address tacacs-server key AAA Client 和AAA Server 之间使用RADIUS 协议时: radius-server host IP_address radius-server key © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -8
Cisco IOS AAA 认证基本配置 步骤 1、全局开启AAA 服务。 要使用AAA,就必须使用aaa new-model 全局配置命令启用AAA 服务。 Router(config)# aaa new-model 步骤 2、配置ACS 服务器的地址和AAA client 密码,其命令格式如下: AAA Client 和AAA Server 之间使用TACACS+协议时: tacacs-server host IP_address tacacs-server key AAA Client 和AAA Server 之间使用RADIUS 协议时: radius-server host IP_address radius-server key © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -8
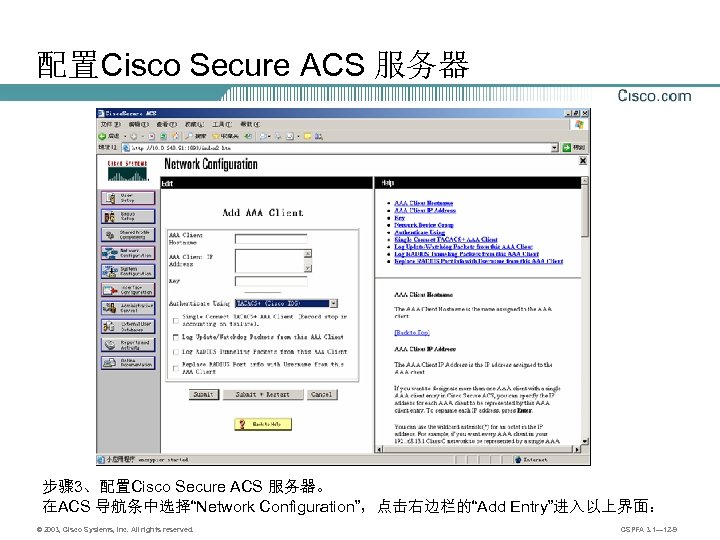 配置Cisco Secure ACS 服务器 步骤 3、配置Cisco Secure ACS 服务器。 在ACS 导航条中选择“Network Configuration”,点击右边栏的“Add Entry”进入以上界面: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -9
配置Cisco Secure ACS 服务器 步骤 3、配置Cisco Secure ACS 服务器。 在ACS 导航条中选择“Network Configuration”,点击右边栏的“Add Entry”进入以上界面: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -9
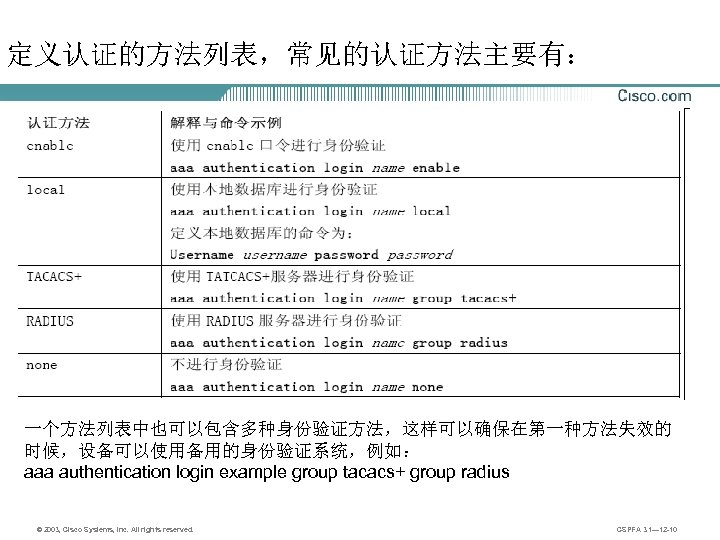 定义认证的方法列表,常见的认证方法主要有: 一个方法列表中也可以包含多种身份验证方法,这样可以确保在第一种方法失效的 时候,设备可以使用备用的身份验证系统,例如: aaa authentication login example group tacacs+ group radius © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -10
定义认证的方法列表,常见的认证方法主要有: 一个方法列表中也可以包含多种身份验证方法,这样可以确保在第一种方法失效的 时候,设备可以使用备用的身份验证系统,例如: aaa authentication login example group tacacs+ group radius © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -10
![配置与应用Authentication Switch(config)#aaa authentication login {default | list-name} method 1 [method 2. . . ] 配置与应用Authentication Switch(config)#aaa authentication login {default | list-name} method 1 [method 2. . . ]](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-11.jpg) 配置与应用Authentication Switch(config)#aaa authentication login {default | list-name} method 1 [method 2. . . ] • Creates a local authentication list创建认证列表 • Login 字符流认证模式(要配置设备, 进入IOS命令行的用户的访问方式) • Default 却省默认的认证方式 例 aaa authentication login default local 使用用本地数据库认证 Switch(config-line)#login authentication {default | list-name} • Applies the authentication list to a line(应用认证到线路下面) © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -11
配置与应用Authentication Switch(config)#aaa authentication login {default | list-name} method 1 [method 2. . . ] • Creates a local authentication list创建认证列表 • Login 字符流认证模式(要配置设备, 进入IOS命令行的用户的访问方式) • Default 却省默认的认证方式 例 aaa authentication login default local 使用用本地数据库认证 Switch(config-line)#login authentication {default | list-name} • Applies the authentication list to a line(应用认证到线路下面) © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -11
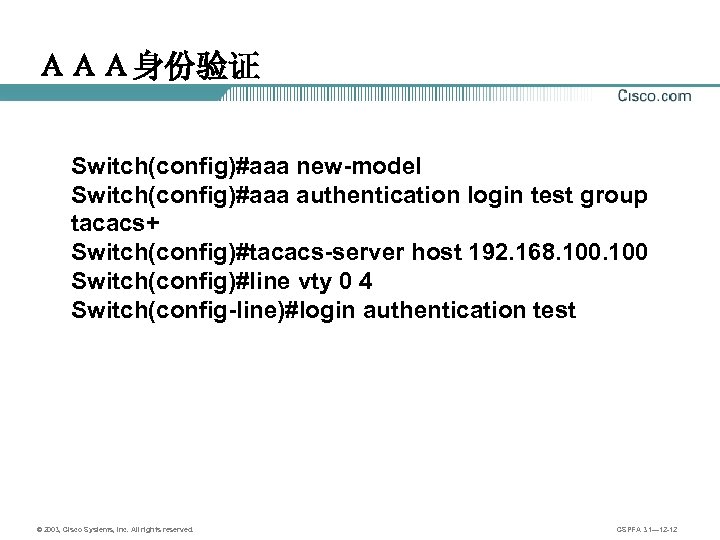 AAA身份验证 Switch(config)#aaa new-model Switch(config)#aaa authentication login test group tacacs+ Switch(config)#tacacs-server host 192. 168. 100 Switch(config)#line vty 0 4 Switch(config-line)#login authentication test © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -12
AAA身份验证 Switch(config)#aaa new-model Switch(config)#aaa authentication login test group tacacs+ Switch(config)#tacacs-server host 192. 168. 100 Switch(config)#line vty 0 4 Switch(config-line)#login authentication test © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -12
 Authorization--授权选项 授权代理(auth-proxy): 基于用户来应用安全策略.使用 授权代理时,用户访问网络前,通过WEB浏览器来向服务器证 明其身份.通过验证后,让用户访问. 命令(commands): 授权执行EXEC命令的权限.如,只 让普通用户执行show命令 网络(network): 网络授权应用于网络连接类型.如,远程 用户登录时,授予其访问PPP等网络协议的权限 反向登陆:反向TELNET会话,用于从控制台访问各种 线路 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -13
Authorization--授权选项 授权代理(auth-proxy): 基于用户来应用安全策略.使用 授权代理时,用户访问网络前,通过WEB浏览器来向服务器证 明其身份.通过验证后,让用户访问. 命令(commands): 授权执行EXEC命令的权限.如,只 让普通用户执行show命令 网络(network): 网络授权应用于网络连接类型.如,远程 用户登录时,授予其访问PPP等网络协议的权限 反向登陆:反向TELNET会话,用于从控制台访问各种 线路 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -13
 Authorization--授权方法 TACACS+:一种客户/服务器的方法.交换机路由 器的AAA授权后台程序通过与该服务器通信来确定各种 授权. RADUIS:与上者一样,也是一种客户/服务器模型 If-authentication: 使用这种方法,只要用户通过了身份验 证,便能访问任何功能 None: 在接口禁用授权 Local: 使用交换机和路由器中的用户名与口令数据库 可以使用username来配置本地数据库 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -14
Authorization--授权方法 TACACS+:一种客户/服务器的方法.交换机路由 器的AAA授权后台程序通过与该服务器通信来确定各种 授权. RADUIS:与上者一样,也是一种客户/服务器模型 If-authentication: 使用这种方法,只要用户通过了身份验 证,便能访问任何功能 None: 在接口禁用授权 Local: 使用交换机和路由器中的用户名与口令数据库 可以使用username来配置本地数据库 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -14
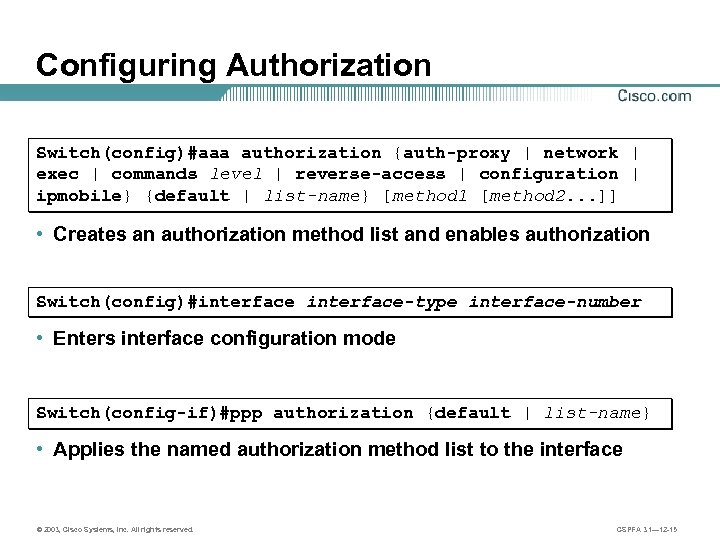 Configuring Authorization Switch(config)#aaa authorization {auth-proxy | network | exec | commands level | reverse-access | configuration | ipmobile} {default | list-name} [method 1 [method 2. . . ]] • Creates an authorization method list and enables authorization Switch(config)#interface-type interface-number • Enters interface configuration mode Switch(config-if)#ppp authorization {default | list-name} • Applies the named authorization method list to the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -15
Configuring Authorization Switch(config)#aaa authorization {auth-proxy | network | exec | commands level | reverse-access | configuration | ipmobile} {default | list-name} [method 1 [method 2. . . ]] • Creates an authorization method list and enables authorization Switch(config)#interface-type interface-number • Enters interface configuration mode Switch(config-if)#ppp authorization {default | list-name} • Applies the named authorization method list to the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -15
 对用户的等级进行授权 第一步:启用AAA,配置本地数据库,为不同的用户设置不同的权限 Router(config)#aaa new-model Router(config)#username user 1 privilege 1 password user 1 Router(config)#username user 2 privilege 7 password user 2 Router(config)#username user 3 privilege 15 password user 3 第二步:配置EXEC 会话授权的方法 Router(config)#aaa authorization exec cisco local 第三步:在虚拟终端线路上应用授权 Router(config)#line vty 0 4 Router(config-line)#authorization exec cisco 用户还可以对Cisco CLI 的命令权限级别进行修改,例如:clear line 命令的 默认级别为 15,但是我们可以使用privilege exec 命令将其权限修改为级别 7 Router(config)# privilege exec level 7 clear line © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -16
对用户的等级进行授权 第一步:启用AAA,配置本地数据库,为不同的用户设置不同的权限 Router(config)#aaa new-model Router(config)#username user 1 privilege 1 password user 1 Router(config)#username user 2 privilege 7 password user 2 Router(config)#username user 3 privilege 15 password user 3 第二步:配置EXEC 会话授权的方法 Router(config)#aaa authorization exec cisco local 第三步:在虚拟终端线路上应用授权 Router(config)#line vty 0 4 Router(config-line)#authorization exec cisco 用户还可以对Cisco CLI 的命令权限级别进行修改,例如:clear line 命令的 默认级别为 15,但是我们可以使用privilege exec 命令将其权限修改为级别 7 Router(config)# privilege exec level 7 clear line © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -16
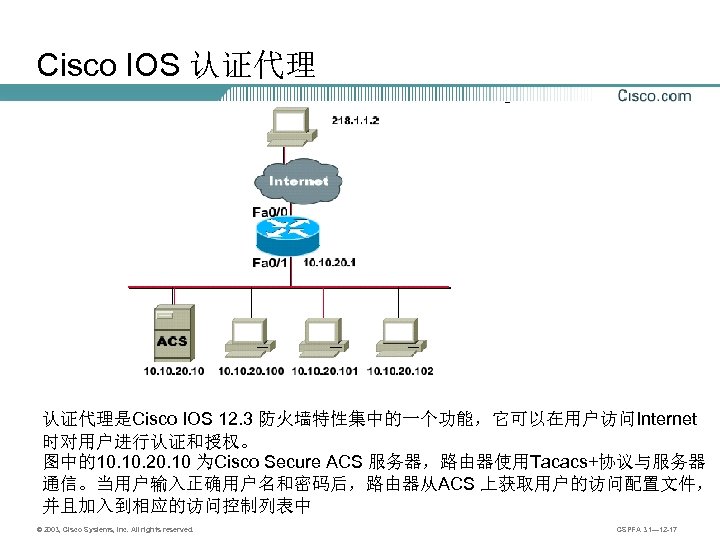 Cisco IOS 认证代理是Cisco IOS 12. 3 防火墙特性集中的一个功能,它可以在用户访问Internet 时对用户进行认证和授权。 图中的10. 20. 10 为Cisco Secure ACS 服务器,路由器使用Tacacs+协议与服务器 通信。当用户输入正确用户名和密码后,路由器从ACS 上获取用户的访问配置文件, 并且加入到相应的访问控制列表中 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -17
Cisco IOS 认证代理是Cisco IOS 12. 3 防火墙特性集中的一个功能,它可以在用户访问Internet 时对用户进行认证和授权。 图中的10. 20. 10 为Cisco Secure ACS 服务器,路由器使用Tacacs+协议与服务器 通信。当用户输入正确用户名和密码后,路由器从ACS 上获取用户的访问配置文件, 并且加入到相应的访问控制列表中 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -17
 第一步,启动AAA Router(config)# aaa new-model Router(config)# aaa authentication login default group tacacs+ Router(config)# aaa authorization auth-proxy default group tacacs+ Router(config)# tacacs-server host 10. 20. 10 key cisco © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -18
第一步,启动AAA Router(config)# aaa new-model Router(config)# aaa authentication login default group tacacs+ Router(config)# aaa authorization auth-proxy default group tacacs+ Router(config)# tacacs-server host 10. 20. 10 key cisco © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -18
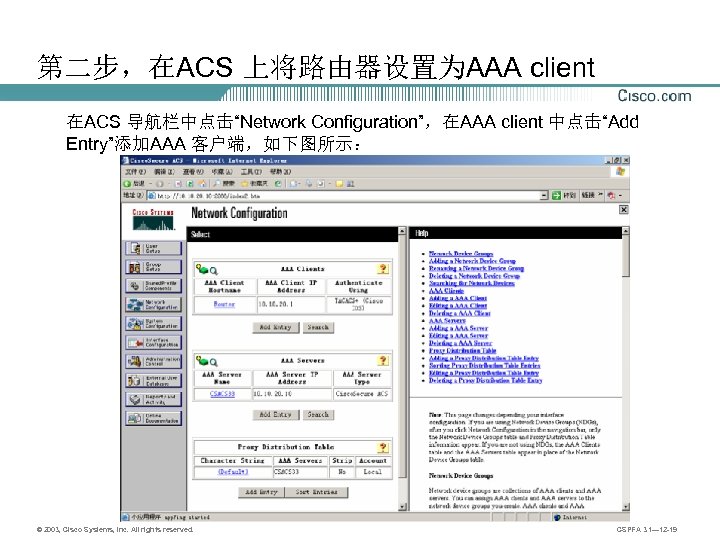 第二步,在ACS 上将路由器设置为AAA client 在ACS 导航栏中点击“Network Configuration”,在AAA client 中点击“Add Entry”添加AAA 客户端,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -19
第二步,在ACS 上将路由器设置为AAA client 在ACS 导航栏中点击“Network Configuration”,在AAA client 中点击“Add Entry”添加AAA 客户端,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -19
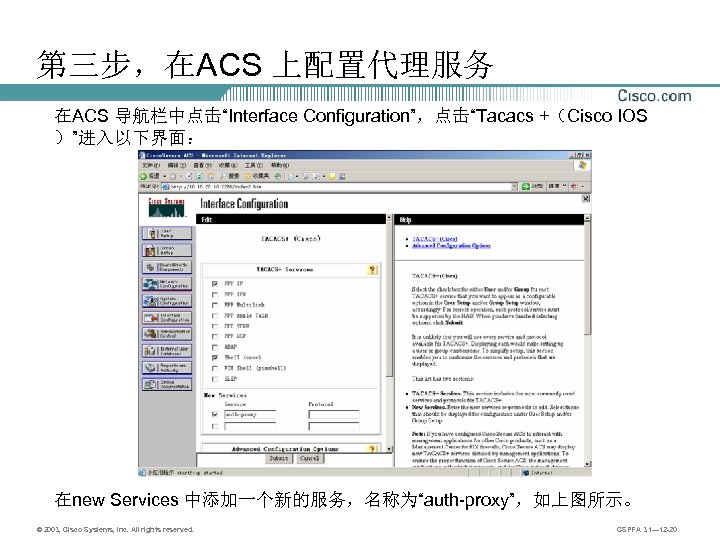 第三步,在ACS 上配置代理服务 在ACS 导航栏中点击“Interface Configuration”,点击“Tacacs +(Cisco IOS )”进入以下界面: 在new Services 中添加一个新的服务,名称为“auth-proxy”,如上图所示。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -20
第三步,在ACS 上配置代理服务 在ACS 导航栏中点击“Interface Configuration”,点击“Tacacs +(Cisco IOS )”进入以下界面: 在new Services 中添加一个新的服务,名称为“auth-proxy”,如上图所示。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -20
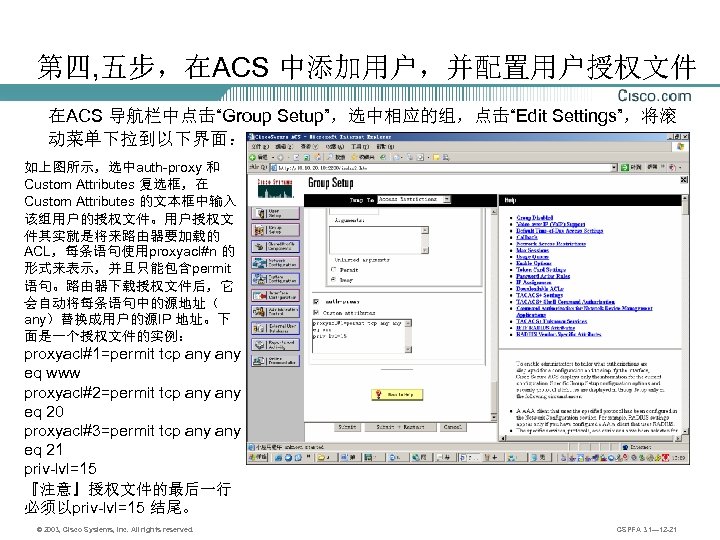 第四, 五步,在ACS 中添加用户,并配置用户授权文件 在ACS 导航栏中点击“Group Setup”,选中相应的组,点击“Edit Settings”,将滚 动菜单下拉到以下界面: 如上图所示,选中auth-proxy 和 Custom Attributes 复选框,在 Custom Attributes 的文本框中输入 该组用户的授权文件。用户授权文 件其实就是将来路由器要加载的 ACL,每条语句使用proxyacl#n 的 形式来表示,并且只能包含permit 语句。路由器下载授权文件后,它 会自动将每条语句中的源地址( any)替换成用户的源IP 地址。下 面是一个授权文件的实例: proxyacl#1=permit tcp any eq www proxyacl#2=permit tcp any eq 20 proxyacl#3=permit tcp any eq 21 priv-lvl=15 『注意』授权文件的最后一行 必须以priv-lvl=15 结尾。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -21
第四, 五步,在ACS 中添加用户,并配置用户授权文件 在ACS 导航栏中点击“Group Setup”,选中相应的组,点击“Edit Settings”,将滚 动菜单下拉到以下界面: 如上图所示,选中auth-proxy 和 Custom Attributes 复选框,在 Custom Attributes 的文本框中输入 该组用户的授权文件。用户授权文 件其实就是将来路由器要加载的 ACL,每条语句使用proxyacl#n 的 形式来表示,并且只能包含permit 语句。路由器下载授权文件后,它 会自动将每条语句中的源地址( any)替换成用户的源IP 地址。下 面是一个授权文件的实例: proxyacl#1=permit tcp any eq www proxyacl#2=permit tcp any eq 20 proxyacl#3=permit tcp any eq 21 priv-lvl=15 『注意』授权文件的最后一行 必须以priv-lvl=15 结尾。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -21
 第六步,在路由器上定义进站访问控制列表, 只允许到路由器的AAA 流量 Router(config)#access-list 101 permit tcp host 10. 20. 10 eq tacacs host 10. 20. 1 Router(config)#access-list 101 deny ip any Router(config-if)# access-list 100 permit tcp any eq tacacs any Router(config)#interface fa 0/1 Router(config-if)#ip access-group 101 in © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -22
第六步,在路由器上定义进站访问控制列表, 只允许到路由器的AAA 流量 Router(config)#access-list 101 permit tcp host 10. 20. 10 eq tacacs host 10. 20. 1 Router(config)#access-list 101 deny ip any Router(config-if)# access-list 100 permit tcp any eq tacacs any Router(config)#interface fa 0/1 Router(config-if)#ip access-group 101 in © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -22
 第七步,打开路由器的HTTP 服务器 第八步,配置认证代理规则 Router(config)# access-list 1 permit 10. 20. 0. 0. 255 !规定哪些主机使用认证代理上网 Router(config)# ip auth-proxy name cisco http list 1 Router(config)# interface fa 0/1 Router(config-if)# ip auth-proxy cisco Router(config-if)# exit Router(config)#ip http server router(config)#ip http authentication aaa © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -23
第七步,打开路由器的HTTP 服务器 第八步,配置认证代理规则 Router(config)# access-list 1 permit 10. 20. 0. 0. 255 !规定哪些主机使用认证代理上网 Router(config)# ip auth-proxy name cisco http list 1 Router(config)# interface fa 0/1 Router(config-if)# ip auth-proxy cisco Router(config-if)# exit Router(config)#ip http server router(config)#ip http authentication aaa © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -23
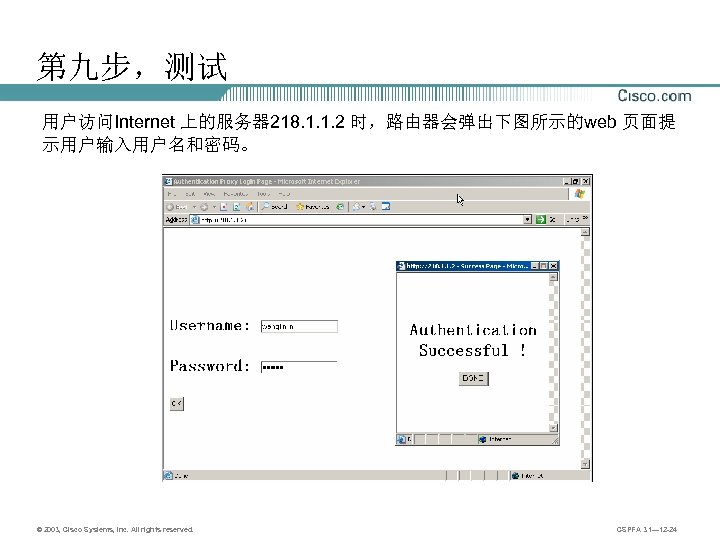 第九步,测试 用户访问Internet 上的服务器 218. 1. 1. 2 时,路由器会弹出下图所示的web 页面提 示用户输入用户名和密码。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -24
第九步,测试 用户访问Internet 上的服务器 218. 1. 1. 2 时,路由器会弹出下图所示的web 页面提 示用户输入用户名和密码。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -24
 Accounting- 统计 网络统计:提供所有PPP等会话的信息,包括数据包数 和字节数. 连接统计:提供从网络中发起的所有外出的连接 EXEC统计:提供网络介入服务器上用户会话信息,包 括用户名,日期,起始和结束时间等 系统统计:提供所有系统级事件信息,如,系统重起等 命令统计:提供在网络介入服务器上执行的特定权限的命 令信息 资源统计:提供通过了用户身份验证的呼叫的真实记录和 终止记录 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -25
Accounting- 统计 网络统计:提供所有PPP等会话的信息,包括数据包数 和字节数. 连接统计:提供从网络中发起的所有外出的连接 EXEC统计:提供网络介入服务器上用户会话信息,包 括用户名,日期,起始和结束时间等 系统统计:提供所有系统级事件信息,如,系统重起等 命令统计:提供在网络介入服务器上执行的特定权限的命 令信息 资源统计:提供通过了用户身份验证的呼叫的真实记录和 终止记录 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -25
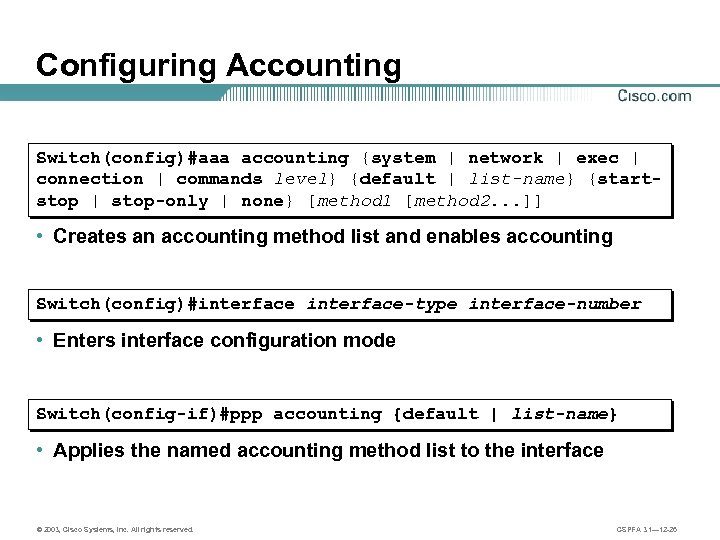 Configuring Accounting Switch(config)#aaa accounting {system | network | exec | connection | commands level} {default | list-name} {startstop | stop-only | none} [method 1 [method 2. . . ]] • Creates an accounting method list and enables accounting Switch(config)#interface-type interface-number • Enters interface configuration mode Switch(config-if)#ppp accounting {default | list-name} • Applies the named accounting method list to the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -26
Configuring Accounting Switch(config)#aaa accounting {system | network | exec | connection | commands level} {default | list-name} {startstop | stop-only | none} [method 1 [method 2. . . ]] • Creates an accounting method list and enables accounting Switch(config)#interface-type interface-number • Enters interface configuration mode Switch(config-if)#ppp accounting {default | list-name} • Applies the named accounting method list to the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -26
 AAA统计 Switch(config)#aaa new-model Switch(config)#aaa accounting exec default start-stop group tacacs+ Switch(config)#line vty 0 4 Switch(config)#accounting exec default 完成设置后,在ACS 的管理页面上点击“Report and activity”查看信息 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -27
AAA统计 Switch(config)#aaa new-model Switch(config)#aaa accounting exec default start-stop group tacacs+ Switch(config)#line vty 0 4 Switch(config)#accounting exec default 完成设置后,在ACS 的管理页面上点击“Report and activity”查看信息 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -27
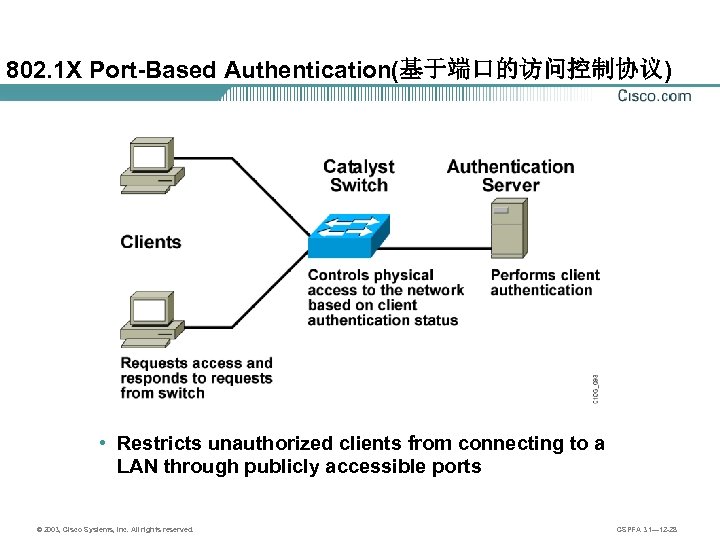 802. 1 X Port-Based Authentication(基于端口的访问控制协议) • Restricts unauthorized clients from connecting to a LAN through publicly accessible ports © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -28
802. 1 X Port-Based Authentication(基于端口的访问控制协议) • Restricts unauthorized clients from connecting to a LAN through publicly accessible ports © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -28
 IEEE 802. 1 x简介 IEEE 802. 1 x访问控制特性是一种基于行业标准的第 2层访问控制方法,提 供了集中管理功能。IEEE 802. 1 x访问控制特性还被广泛应用于无线网络 使用 802. 1 x的时候,在交换机接收器端口连接的 作站发送的数据包之前, 将请求身份验证服务器对 作站进行身份验证。在身份验证服务器验证 作站的身份之前,802. 1 x访问控制特性只允许EAPOL(Extensible Authentication Protocol over LAN,LAN上的可扩展身份验证协议)通信流 通过 作站连接的端口。通过身份验证后,常规通信流才能通过该端口 基于端口的802. 1 x身份验证涉及3种设备: l 客户(client)---使用 802. 1 x请求网络对其进行身份验证的 作站。当 前,只有Microsoft Windows XP和Windows 2003内置了对 802. 1 x支持功 能 l身份验证服务器(Authentication server)---负责验证交换机转发的客 户请求。当前,身份验证服务器是安装了EAPOL扩展的RADIUS服务器。 l交换机---负责将客户请求转发给身份验证服务器,并在客户通过身份验 证后授予其访问网络的权限。在 802. 1 x运行期间,交换机实际上是代理 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -29
IEEE 802. 1 x简介 IEEE 802. 1 x访问控制特性是一种基于行业标准的第 2层访问控制方法,提 供了集中管理功能。IEEE 802. 1 x访问控制特性还被广泛应用于无线网络 使用 802. 1 x的时候,在交换机接收器端口连接的 作站发送的数据包之前, 将请求身份验证服务器对 作站进行身份验证。在身份验证服务器验证 作站的身份之前,802. 1 x访问控制特性只允许EAPOL(Extensible Authentication Protocol over LAN,LAN上的可扩展身份验证协议)通信流 通过 作站连接的端口。通过身份验证后,常规通信流才能通过该端口 基于端口的802. 1 x身份验证涉及3种设备: l 客户(client)---使用 802. 1 x请求网络对其进行身份验证的 作站。当 前,只有Microsoft Windows XP和Windows 2003内置了对 802. 1 x支持功 能 l身份验证服务器(Authentication server)---负责验证交换机转发的客 户请求。当前,身份验证服务器是安装了EAPOL扩展的RADIUS服务器。 l交换机---负责将客户请求转发给身份验证服务器,并在客户通过身份验 证后授予其访问网络的权限。在 802. 1 x运行期间,交换机实际上是代理 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -29
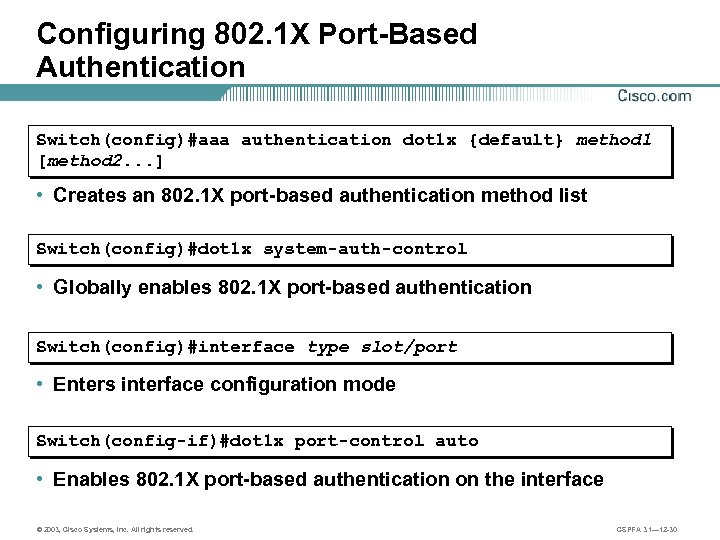 Configuring 802. 1 X Port-Based Authentication Switch(config)#aaa authentication dot 1 x {default} method 1 [method 2. . . ] • Creates an 802. 1 X port-based authentication method list Switch(config)#dot 1 x system-auth-control • Globally enables 802. 1 X port-based authentication Switch(config)#interface type slot/port • Enters interface configuration mode Switch(config-if)#dot 1 x port-control auto • Enables 802. 1 X port-based authentication on the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -30
Configuring 802. 1 X Port-Based Authentication Switch(config)#aaa authentication dot 1 x {default} method 1 [method 2. . . ] • Creates an 802. 1 X port-based authentication method list Switch(config)#dot 1 x system-auth-control • Globally enables 802. 1 X port-based authentication Switch(config)#interface type slot/port • Enters interface configuration mode Switch(config-if)#dot 1 x port-control auto • Enables 802. 1 X port-based authentication on the interface © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -30
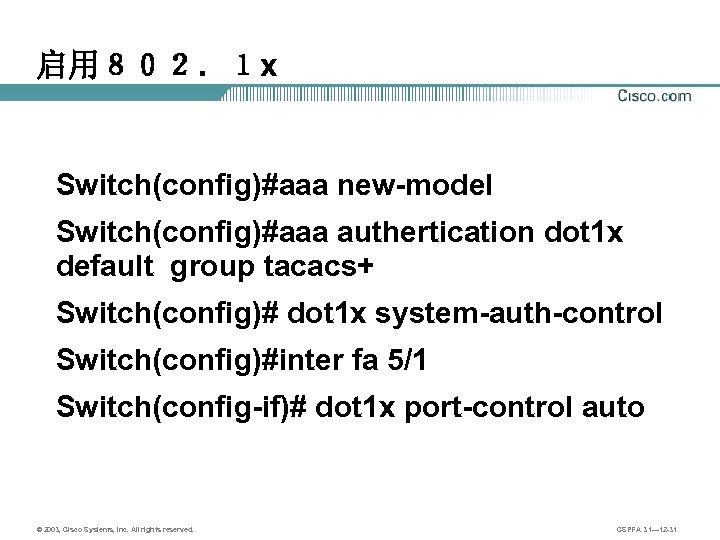 启用802.1 x Switch(config)#aaa new-model Switch(config)#aaa authertication dot 1 x default group tacacs+ Switch(config)# dot 1 x system-auth-control Switch(config)#inter fa 5/1 Switch(config-if)# dot 1 x port-control auto © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -31
启用802.1 x Switch(config)#aaa new-model Switch(config)#aaa authertication dot 1 x default group tacacs+ Switch(config)# dot 1 x system-auth-control Switch(config)#inter fa 5/1 Switch(config-if)# dot 1 x port-control auto © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -31
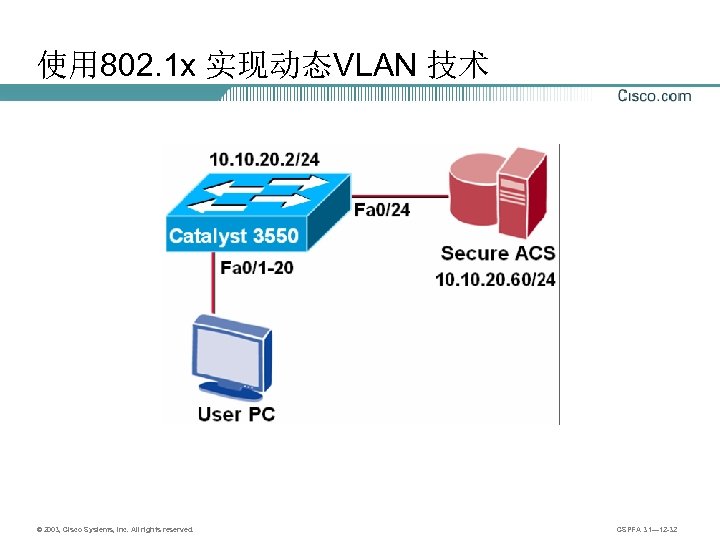 使用 802. 1 x 实现动态VLAN 技术 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -32
使用 802. 1 x 实现动态VLAN 技术 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -32
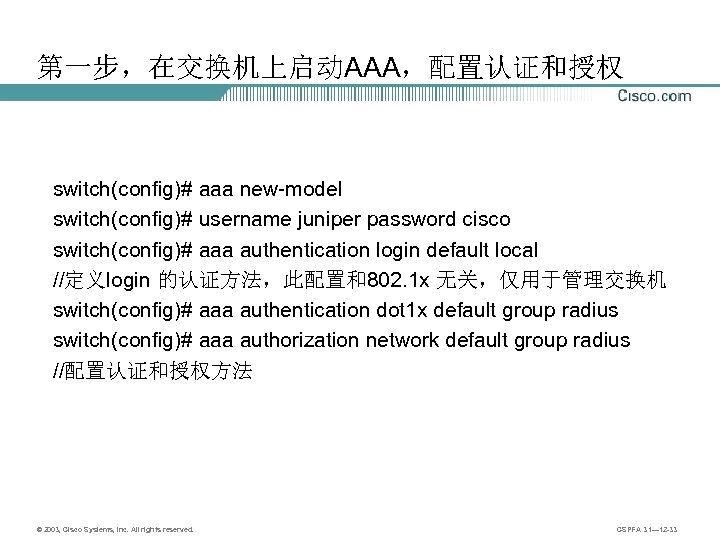 第一步,在交换机上启动AAA,配置认证和授权 switch(config)# aaa new-model switch(config)# username juniper password cisco switch(config)# aaa authentication login default local //定义login 的认证方法,此配置和802. 1 x 无关,仅用于管理交换机 switch(config)# aaa authentication dot 1 x default group radius switch(config)# aaa authorization network default group radius //配置认证和授权方法 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -33
第一步,在交换机上启动AAA,配置认证和授权 switch(config)# aaa new-model switch(config)# username juniper password cisco switch(config)# aaa authentication login default local //定义login 的认证方法,此配置和802. 1 x 无关,仅用于管理交换机 switch(config)# aaa authentication dot 1 x default group radius switch(config)# aaa authorization network default group radius //配置认证和授权方法 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -33
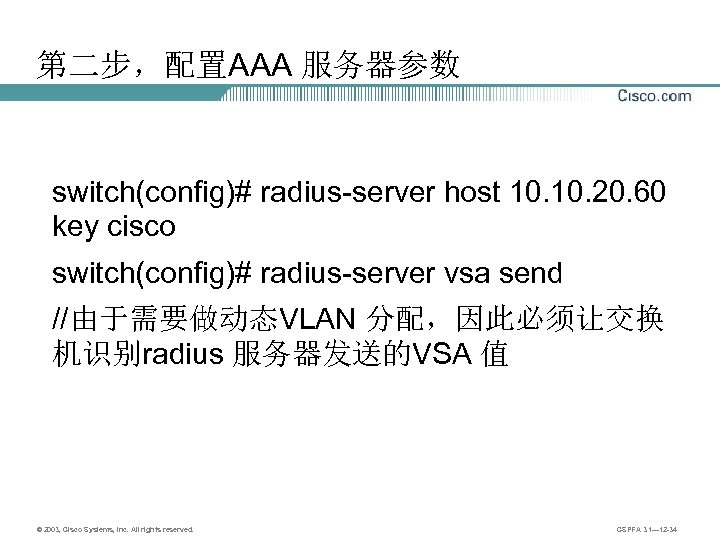 第二步,配置AAA 服务器参数 switch(config)# radius-server host 10. 20. 60 key cisco switch(config)# radius-server vsa send //由于需要做动态VLAN 分配,因此必须让交换 机识别radius 服务器发送的VSA 值 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -34
第二步,配置AAA 服务器参数 switch(config)# radius-server host 10. 20. 60 key cisco switch(config)# radius-server vsa send //由于需要做动态VLAN 分配,因此必须让交换 机识别radius 服务器发送的VSA 值 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -34
 第三步,启动 802. 1 x switch(config)# dot 1 x system-control //全局开启 802. 1 x switch(config)# interface range fa 0/1 – 20 switch(config-if-range)# switchport mode access switch(config-if-range)# spanning-tree portfast switch(config-if-range)# dot 1 x port-control auto //在端口上开启 802. 1 x © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -35
第三步,启动 802. 1 x switch(config)# dot 1 x system-control //全局开启 802. 1 x switch(config)# interface range fa 0/1 – 20 switch(config-if-range)# switchport mode access switch(config-if-range)# spanning-tree portfast switch(config-if-range)# dot 1 x port-control auto //在端口上开启 802. 1 x © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -35
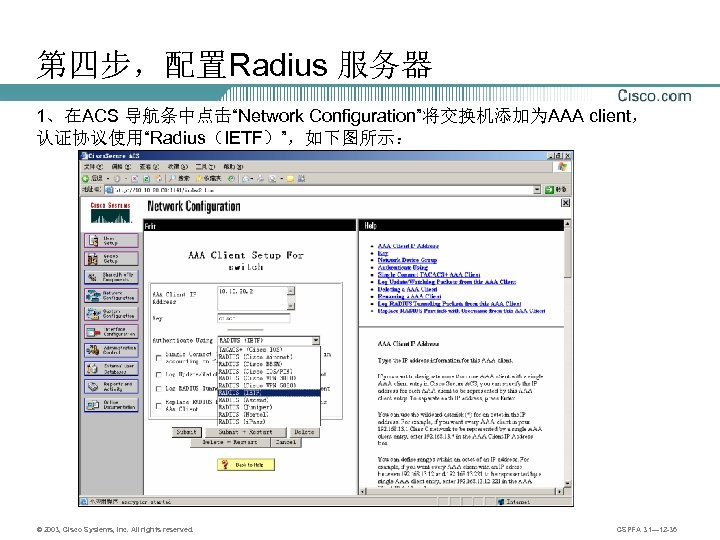 第四步,配置Radius 服务器 1、在ACS 导航条中点击“Network Configuration”将交换机添加为AAA client, 认证协议使用“Radius(IETF)”,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -36
第四步,配置Radius 服务器 1、在ACS 导航条中点击“Network Configuration”将交换机添加为AAA client, 认证协议使用“Radius(IETF)”,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -36
![2、在ACS 导航条中点击“Interface Configuration”,点击“Radius(IETF)”进入以下界面: 选中“ [064] Tunnel-Type ” 、“ [065] Tunnel-Medium-Type ” 、“ [081] Tunnel-Private-Group-ID”复选框,点击“submit”。 2、在ACS 导航条中点击“Interface Configuration”,点击“Radius(IETF)”进入以下界面: 选中“ [064] Tunnel-Type ” 、“ [065] Tunnel-Medium-Type ” 、“ [081] Tunnel-Private-Group-ID”复选框,点击“submit”。](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-37.jpg) 2、在ACS 导航条中点击“Interface Configuration”,点击“Radius(IETF)”进入以下界面: 选中“ [064] Tunnel-Type ” 、“ [065] Tunnel-Medium-Type ” 、“ [081] Tunnel-Private-Group-ID”复选框,点击“submit”。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -37
2、在ACS 导航条中点击“Interface Configuration”,点击“Radius(IETF)”进入以下界面: 选中“ [064] Tunnel-Type ” 、“ [065] Tunnel-Medium-Type ” 、“ [081] Tunnel-Private-Group-ID”复选框,点击“submit”。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -37
![3、在ACS 导航条中点击“User Setup”添加用户并且分配到相应的组中。 4、在ACS 导航条中点击“Group Setup”编辑组设置,将“[064] Tunnel-Type”标签 1 的 值设置为“VLAN”,将“[065] Tunnel-Medium-Type” 标签 1 的值设置为“ 3、在ACS 导航条中点击“User Setup”添加用户并且分配到相应的组中。 4、在ACS 导航条中点击“Group Setup”编辑组设置,将“[064] Tunnel-Type”标签 1 的 值设置为“VLAN”,将“[065] Tunnel-Medium-Type” 标签 1 的值设置为“](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-38.jpg) 3、在ACS 导航条中点击“User Setup”添加用户并且分配到相应的组中。 4、在ACS 导航条中点击“Group Setup”编辑组设置,将“[064] Tunnel-Type”标签 1 的 值设置为“VLAN”,将“[065] Tunnel-Medium-Type” 标签 1 的值设置为“ 802”,将“[081] Tunnel-Private-Group-ID” 标签 1 的值设置为该组用户所对应的VLAN ID。如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -38
3、在ACS 导航条中点击“User Setup”添加用户并且分配到相应的组中。 4、在ACS 导航条中点击“Group Setup”编辑组设置,将“[064] Tunnel-Type”标签 1 的 值设置为“VLAN”,将“[065] Tunnel-Medium-Type” 标签 1 的值设置为“ 802”,将“[081] Tunnel-Private-Group-ID” 标签 1 的值设置为该组用户所对应的VLAN ID。如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -38
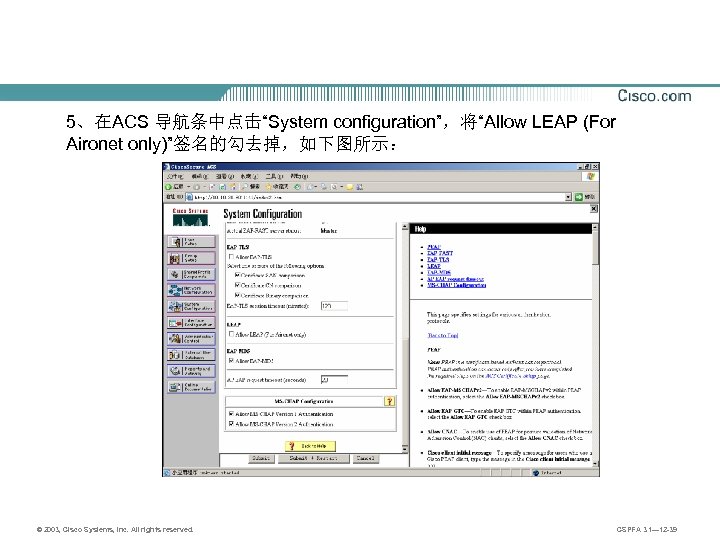 5、在ACS 导航条中点击“System configuration”,将“Allow LEAP (For Aironet only)”签名的勾去掉,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -39
5、在ACS 导航条中点击“System configuration”,将“Allow LEAP (For Aironet only)”签名的勾去掉,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -39
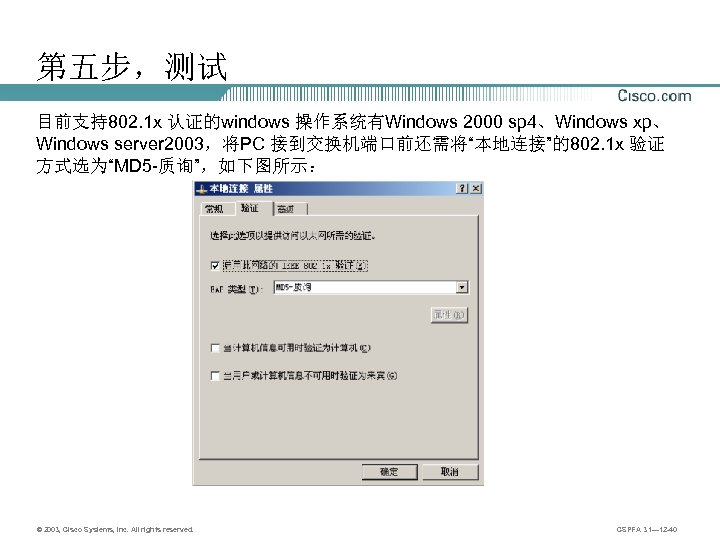 第五步,测试 目前支持802. 1 x 认证的windows 操作系统有Windows 2000 sp 4、Windows xp、 Windows server 2003,将PC 接到交换机端口前还需将“本地连接”的802. 1 x 验证 方式选为“MD 5 -质询”,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -40
第五步,测试 目前支持802. 1 x 认证的windows 操作系统有Windows 2000 sp 4、Windows xp、 Windows server 2003,将PC 接到交换机端口前还需将“本地连接”的802. 1 x 验证 方式选为“MD 5 -质询”,如下图所示: © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -40
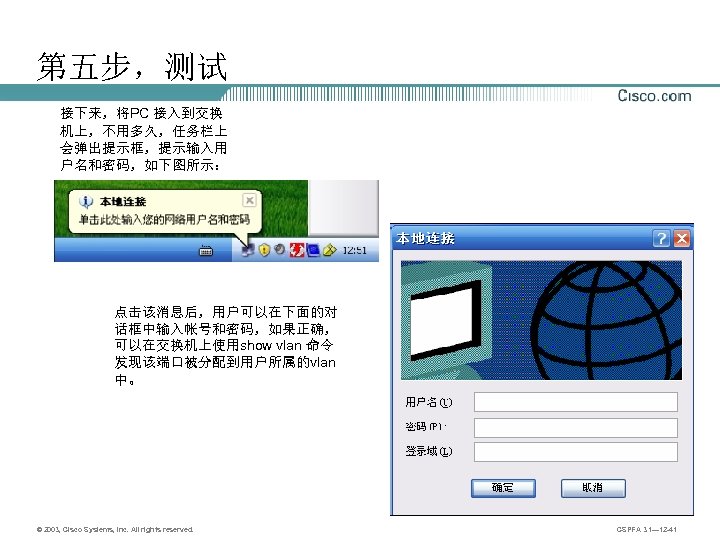 第五步,测试 接下来,将PC 接入到交换 机上,不用多久,任务栏上 会弹出提示框,提示输入用 户名和密码,如下图所示: 点击该消息后,用户可以在下面的对 话框中输入帐号和密码,如果正确, 可以在交换机上使用show vlan 命令 发现该端口被分配到用户所属的vlan 中。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -41
第五步,测试 接下来,将PC 接入到交换 机上,不用多久,任务栏上 会弹出提示框,提示输入用 户名和密码,如下图所示: 点击该消息后,用户可以在下面的对 话框中输入帐号和密码,如果正确, 可以在交换机上使用show vlan 命令 发现该端口被分配到用户所属的vlan 中。 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -41
 PIX----AAA Authentication, Authorization, and Accounting © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -42
PIX----AAA Authentication, Authorization, and Accounting © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -42
 Authentication, Authorization, and Accounting • Authentication – Who you are – Can exist without authorization • Authorization – What you can do – Requires authentication • Accounting – What you did © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -43
Authentication, Authorization, and Accounting • Authentication – Who you are – Can exist without authorization • Authorization – What you can do – Requires authentication • Accounting – What you did © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -43
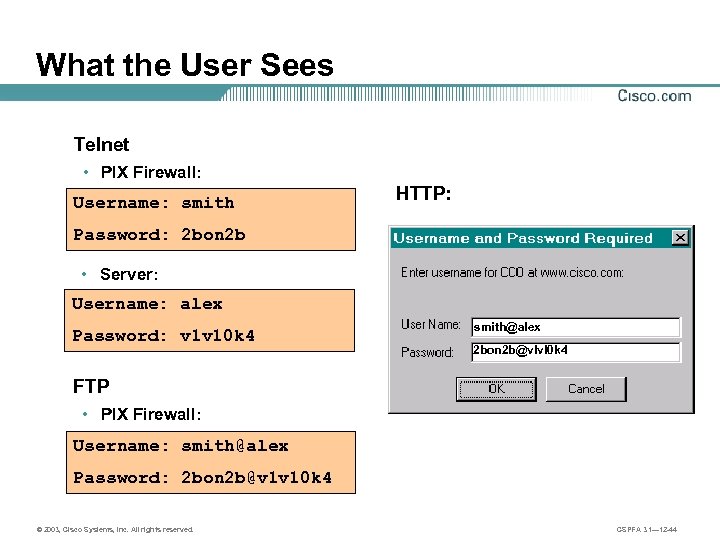 What the User Sees Telnet • PIX Firewall: Username: smith HTTP: Password: 2 bon 2 b • Server: Username: alex Password: v 1 v 10 k 4 smith@alex 2 bon 2 b@vlvl 0 k 4 FTP • PIX Firewall: Username: smith@alex Password: 2 bon 2 b@v 1 v 10 k 4 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -44
What the User Sees Telnet • PIX Firewall: Username: smith HTTP: Password: 2 bon 2 b • Server: Username: alex Password: v 1 v 10 k 4 smith@alex 2 bon 2 b@vlvl 0 k 4 FTP • PIX Firewall: Username: smith@alex Password: 2 bon 2 b@v 1 v 10 k 4 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -44
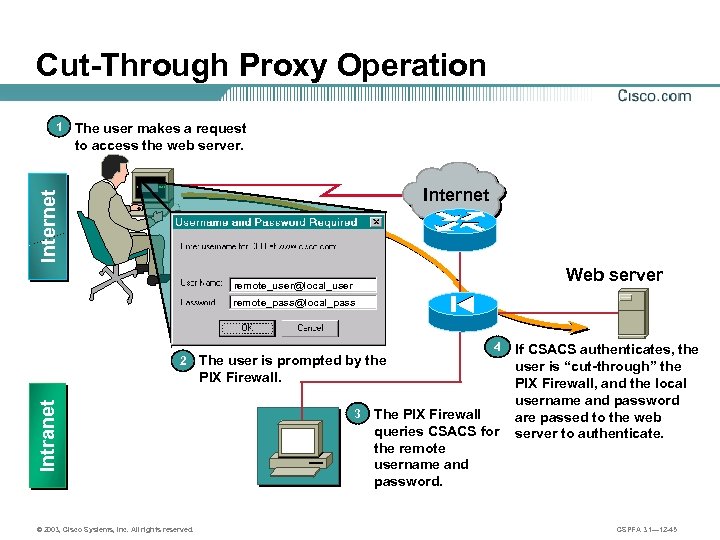 Cut-Through Proxy Operation The user makes a request to access the web server. Internet 1 Web server remote_user@local_user remote_pass@local_pass The user is prompted by the PIX Firewall. Intranet 2 3 4 The PIX Firewall queries CSACS for the remote username and password. If CSACS authenticates, the user is “cut-through” the PIX Firewall, and the local username and password are passed to the web server to authenticate. CSACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -45
Cut-Through Proxy Operation The user makes a request to access the web server. Internet 1 Web server remote_user@local_user remote_pass@local_pass The user is prompted by the PIX Firewall. Intranet 2 3 4 The PIX Firewall queries CSACS for the remote username and password. If CSACS authenticates, the user is “cut-through” the PIX Firewall, and the local username and password are passed to the web server to authenticate. CSACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -45
 Installation of CSACS for Windows NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -46
Installation of CSACS for Windows NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -46
 Installation Wizard © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -47
Installation Wizard © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -47
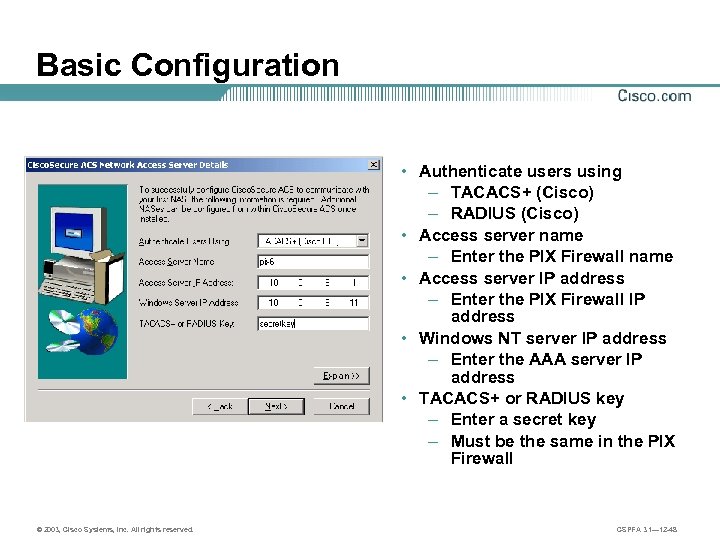 Basic Configuration • Authenticate users using – TACACS+ (Cisco) – RADIUS (Cisco) • Access server name – Enter the PIX Firewall name • Access server IP address – Enter the PIX Firewall IP address • Windows NT server IP address – Enter the AAA server IP address • TACACS+ or RADIUS key – Enter a secret key – Must be the same in the PIX Firewall © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -48
Basic Configuration • Authenticate users using – TACACS+ (Cisco) – RADIUS (Cisco) • Access server name – Enter the PIX Firewall name • Access server IP address – Enter the PIX Firewall IP address • Windows NT server IP address – Enter the AAA server IP address • TACACS+ or RADIUS key – Enter a secret key – Must be the same in the PIX Firewall © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -48
 Authentication Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -49
Authentication Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -49
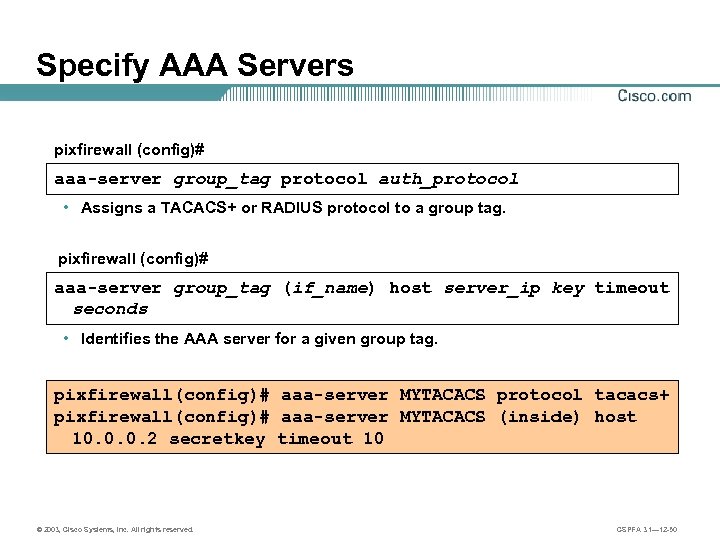 Specify AAA Servers pixfirewall (config)# aaa-server group_tag protocol auth_protocol • Assigns a TACACS+ or RADIUS protocol to a group tag. pixfirewall (config)# aaa-server group_tag (if_name) host server_ip key timeout seconds • Identifies the AAA server for a given group tag. pixfirewall(config)# aaa-server MYTACACS protocol tacacs+ pixfirewall(config)# aaa-server MYTACACS (inside) host 10. 0. 0. 2 secretkey timeout 10 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -50
Specify AAA Servers pixfirewall (config)# aaa-server group_tag protocol auth_protocol • Assigns a TACACS+ or RADIUS protocol to a group tag. pixfirewall (config)# aaa-server group_tag (if_name) host server_ip key timeout seconds • Identifies the AAA server for a given group tag. pixfirewall(config)# aaa-server MYTACACS protocol tacacs+ pixfirewall(config)# aaa-server MYTACACS (inside) host 10. 0. 0. 2 secretkey timeout 10 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -50
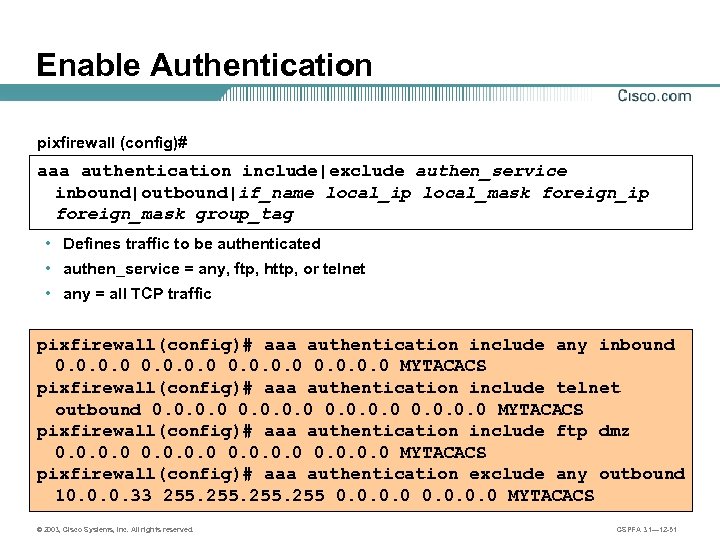 Enable Authentication pixfirewall (config)# aaa authentication include|exclude authen_service inbound|outbound|if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic to be authenticated • authen_service = any, ftp, http, or telnet • any = all TCP traffic pixfirewall(config)# aaa authentication include any inbound 0. 0 MYTACACS pixfirewall(config)# aaa authentication include telnet outbound 0. 0 MYTACACS pixfirewall(config)# aaa authentication include ftp dmz 0. 0 MYTACACS pixfirewall(config)# aaa authentication exclude any outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -51
Enable Authentication pixfirewall (config)# aaa authentication include|exclude authen_service inbound|outbound|if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic to be authenticated • authen_service = any, ftp, http, or telnet • any = all TCP traffic pixfirewall(config)# aaa authentication include any inbound 0. 0 MYTACACS pixfirewall(config)# aaa authentication include telnet outbound 0. 0 MYTACACS pixfirewall(config)# aaa authentication include ftp dmz 0. 0 MYTACACS pixfirewall(config)# aaa authentication exclude any outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -51
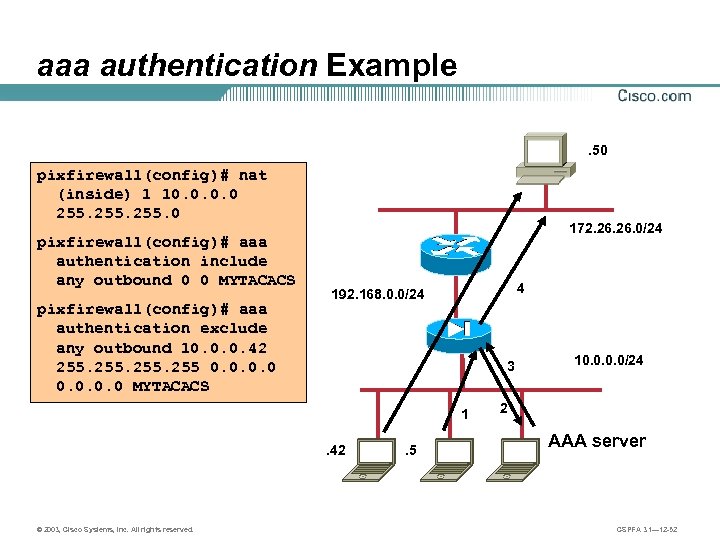 aaa authentication Example. 50 pixfirewall(config)# nat (inside) 1 10. 0 255. 0 pixfirewall(config)# aaa authentication include any outbound 0 0 MYTACACS pixfirewall(config)# aaa authentication exclude any outbound 10. 0. 0. 42 255 0. 0 MYTACACS 172. 26. 0/24 4 192. 168. 0. 0/24 3 1. 42 © 2003, Cisco Systems, Inc. All rights reserved. . 5 10. 0/24 2 AAA server CSPFA 3. 1— 12 -52
aaa authentication Example. 50 pixfirewall(config)# nat (inside) 1 10. 0 255. 0 pixfirewall(config)# aaa authentication include any outbound 0 0 MYTACACS pixfirewall(config)# aaa authentication exclude any outbound 10. 0. 0. 42 255 0. 0 MYTACACS 172. 26. 0/24 4 192. 168. 0. 0/24 3 1. 42 © 2003, Cisco Systems, Inc. All rights reserved. . 5 10. 0/24 2 AAA server CSPFA 3. 1— 12 -52
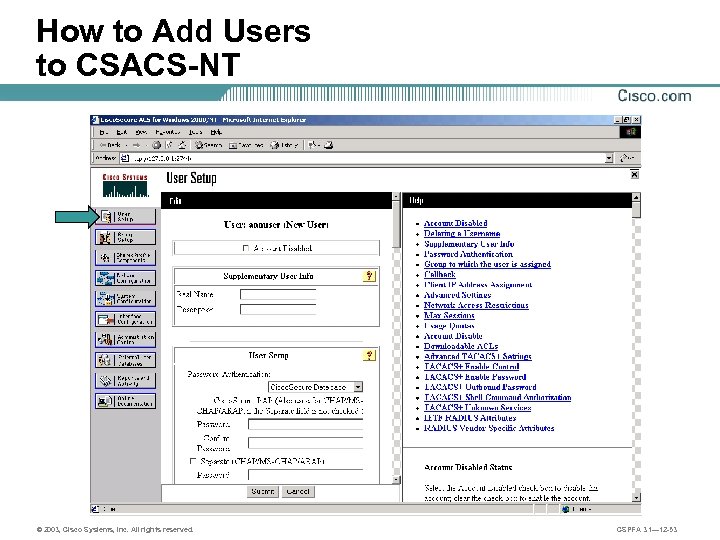 How to Add Users to CSACS-NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -53
How to Add Users to CSACS-NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -53
 Authentication of Non-Telnet, FTP, or HTTP Traffic • Option 1—Authenticate first by accessing a Telnet, FTP, or HTTP server before accessing other services. • Option 2—Authenticate to the PIX Firewall virtual Telnet service before accessing other services. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -54
Authentication of Non-Telnet, FTP, or HTTP Traffic • Option 1—Authenticate first by accessing a Telnet, FTP, or HTTP server before accessing other services. • Option 2—Authenticate to the PIX Firewall virtual Telnet service before accessing other services. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -54
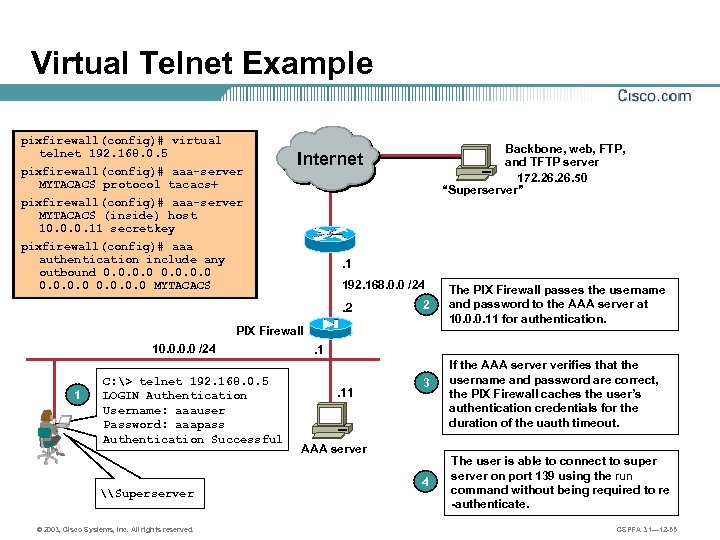 Virtual Telnet Example pixfirewall(config)# virtual telnet 192. 168. 0. 5 pixfirewall(config)# aaa-server MYTACACS protocol tacacs+ Backbone, web, FTP, and TFTP server 172. 26. 50 “Superserver” Internet pixfirewall(config)# aaa-server MYTACACS (inside) host 10. 0. 0. 11 secretkey pixfirewall(config)# aaa authentication include any outbound 0. 0 MYTACACS . 1 192. 168. 0. 0 /24 . 2 2 PIX Firewall 10. 0 /24 1 C: > telnet 192. 168. 0. 5 LOGIN Authentication Username: aaauser Password: aaapass Authentication Successful \Superserver © 2003, Cisco Systems, Inc. All rights reserved. The PIX Firewall passes the username and password to the AAA server at 10. 0. 0. 11 for authentication. . 1. 11 3 AAA server 4 If the AAA server verifies that the username and password are correct, the PIX Firewall caches the user’s authentication credentials for the duration of the uauth timeout. The user is able to connect to super server on port 139 using the run command without being required to re -authenticate. CSPFA 3. 1— 12 -55
Virtual Telnet Example pixfirewall(config)# virtual telnet 192. 168. 0. 5 pixfirewall(config)# aaa-server MYTACACS protocol tacacs+ Backbone, web, FTP, and TFTP server 172. 26. 50 “Superserver” Internet pixfirewall(config)# aaa-server MYTACACS (inside) host 10. 0. 0. 11 secretkey pixfirewall(config)# aaa authentication include any outbound 0. 0 MYTACACS . 1 192. 168. 0. 0 /24 . 2 2 PIX Firewall 10. 0 /24 1 C: > telnet 192. 168. 0. 5 LOGIN Authentication Username: aaauser Password: aaapass Authentication Successful \Superserver © 2003, Cisco Systems, Inc. All rights reserved. The PIX Firewall passes the username and password to the AAA server at 10. 0. 0. 11 for authentication. . 1. 11 3 AAA server 4 If the AAA server verifies that the username and password are correct, the PIX Firewall caches the user’s authentication credentials for the duration of the uauth timeout. The user is able to connect to super server on port 139 using the run command without being required to re -authenticate. CSPFA 3. 1— 12 -55
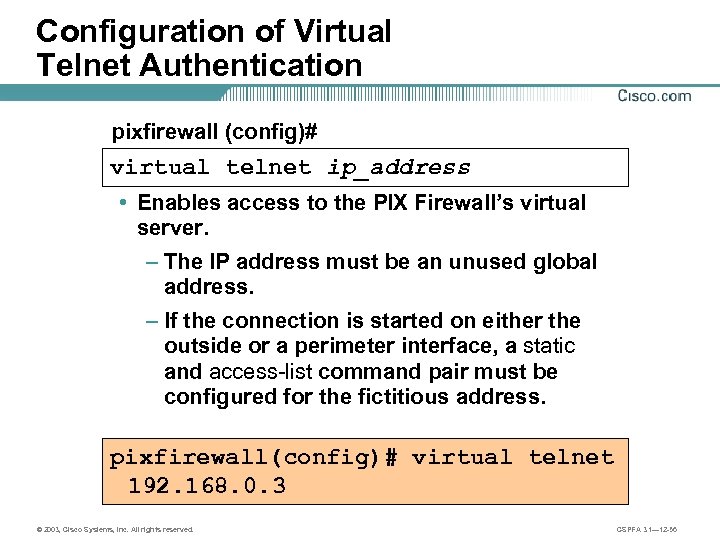 Configuration of Virtual Telnet Authentication pixfirewall (config)# virtual telnet ip_address • Enables access to the PIX Firewall’s virtual server. – The IP address must be an unused global address. – If the connection is started on either the outside or a perimeter interface, a static and access-list command pair must be configured for the fictitious address. pixfirewall(config)# virtual telnet 192. 168. 0. 3 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -56
Configuration of Virtual Telnet Authentication pixfirewall (config)# virtual telnet ip_address • Enables access to the PIX Firewall’s virtual server. – The IP address must be an unused global address. – If the connection is started on either the outside or a perimeter interface, a static and access-list command pair must be configured for the fictitious address. pixfirewall(config)# virtual telnet 192. 168. 0. 3 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -56
 Virtual HTTP • Virtual HTTP solves the problem of HTTP requests failing when web servers require credentials that differ from those required by the PIX Firewall’s AAA server. • When virtual HTTP is enabled, it redirects the browser to authenticate first to a virtual web server on the PIX Firewall. • After authentication, the PIX Firewall forwards the web request to the intended web server. • Virtual HTTP is transparent to the user. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -57
Virtual HTTP • Virtual HTTP solves the problem of HTTP requests failing when web servers require credentials that differ from those required by the PIX Firewall’s AAA server. • When virtual HTTP is enabled, it redirects the browser to authenticate first to a virtual web server on the PIX Firewall. • After authentication, the PIX Firewall forwards the web request to the intended web server. • Virtual HTTP is transparent to the user. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -57
![Configuration of Virtual HTTP Authentication pixfirewall (config)# virtual http ip_address [warn] • Enables access Configuration of Virtual HTTP Authentication pixfirewall (config)# virtual http ip_address [warn] • Enables access](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-58.jpg) Configuration of Virtual HTTP Authentication pixfirewall (config)# virtual http ip_address [warn] • Enables access to the PIX Firewall’s virtual server. – For inbound clients, the IP address must be an unused global address. – If the connection is started on either the outside or a perimeter interface, a static and access-list command pair must be configured for the fictitious address. pixfirewall(config)# virtual http 192. 168. 0. 3 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -58
Configuration of Virtual HTTP Authentication pixfirewall (config)# virtual http ip_address [warn] • Enables access to the PIX Firewall’s virtual server. – For inbound clients, the IP address must be an unused global address. – If the connection is started on either the outside or a perimeter interface, a static and access-list command pair must be configured for the fictitious address. pixfirewall(config)# virtual http 192. 168. 0. 3 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -58
 Authentication of Console Access pixfirewall (config)# aaa authentication [serial | enable | telnet | ssh | http] console group_tag • Defines a console access method that requires authentication. pixfirewall(config)# console MYTACACS pixfirewall(config)# console MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. aaa authentication serial aaa authentication enable aaa authentication telnet aaa authentication ssh aaa authentication http CSPFA 3. 1— 12 -59
Authentication of Console Access pixfirewall (config)# aaa authentication [serial | enable | telnet | ssh | http] console group_tag • Defines a console access method that requires authentication. pixfirewall(config)# console MYTACACS pixfirewall(config)# console MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. aaa authentication serial aaa authentication enable aaa authentication telnet aaa authentication ssh aaa authentication http CSPFA 3. 1— 12 -59
![How to Change the Authentication Timeouts pixfirewall (config)# timeout uauth hh: mm: ss [absolute|inactivity] How to Change the Authentication Timeouts pixfirewall (config)# timeout uauth hh: mm: ss [absolute|inactivity]](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-60.jpg) How to Change the Authentication Timeouts pixfirewall (config)# timeout uauth hh: mm: ss [absolute|inactivity] • Sets the time interval before users will be required to reauthenticate – Absolute—Time interval starts at user login – Inactivity—Time interval for inactive sessions (no traffic) pixfirewall(config)# timeout uauth 3: 00 absolute pixfirewall(config)# timeout uauth 0: 30: 00 inactivity © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -60
How to Change the Authentication Timeouts pixfirewall (config)# timeout uauth hh: mm: ss [absolute|inactivity] • Sets the time interval before users will be required to reauthenticate – Absolute—Time interval starts at user login – Inactivity—Time interval for inactive sessions (no traffic) pixfirewall(config)# timeout uauth 3: 00 absolute pixfirewall(config)# timeout uauth 0: 30: 00 inactivity © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -60
![How to Change the Authentication Prompts pixfirewall (config)# auth-prompt [accept | reject | prompt] How to Change the Authentication Prompts pixfirewall (config)# auth-prompt [accept | reject | prompt]](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-61.jpg) How to Change the Authentication Prompts pixfirewall (config)# auth-prompt [accept | reject | prompt] string • Defines the prompt users see when authenticating • Defines the message users get when they successfully or unsuccessfully authenticate • By default, only the username and password prompts are seen pixfirewall(config)# auth-prompt Please Authenticate to the Firewall pixfirewall(config)# auth-prompt reject Authentication Failed, Try Again pixfirewall(config)# auth-prompt accept You’ve been Authenticated © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -61
How to Change the Authentication Prompts pixfirewall (config)# auth-prompt [accept | reject | prompt] string • Defines the prompt users see when authenticating • Defines the message users get when they successfully or unsuccessfully authenticate • By default, only the username and password prompts are seen pixfirewall(config)# auth-prompt Please Authenticate to the Firewall pixfirewall(config)# auth-prompt reject Authentication Failed, Try Again pixfirewall(config)# auth-prompt accept You’ve been Authenticated © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -61
 Authorization Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -62
Authorization Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -62
 Enable Authorization pixfirewall (config)# aaa authorization include | exclude author_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic that requires AAA server authorization • author_service = any, ftp, http, or telnet • any = All TCP traffic pixfirewall(config)# aaa authorization include ftp outbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization exclude ftp outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -63
Enable Authorization pixfirewall (config)# aaa authorization include | exclude author_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic that requires AAA server authorization • author_service = any, ftp, http, or telnet • any = All TCP traffic pixfirewall(config)# aaa authorization include ftp outbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization exclude ftp outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -63
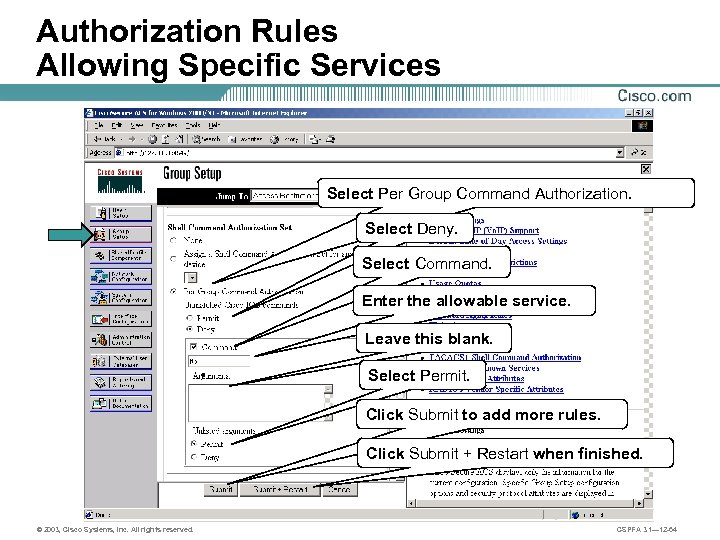 Authorization Rules Allowing Specific Services Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Leave this blank. Select Permit. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -64
Authorization Rules Allowing Specific Services Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Leave this blank. Select Permit. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -64
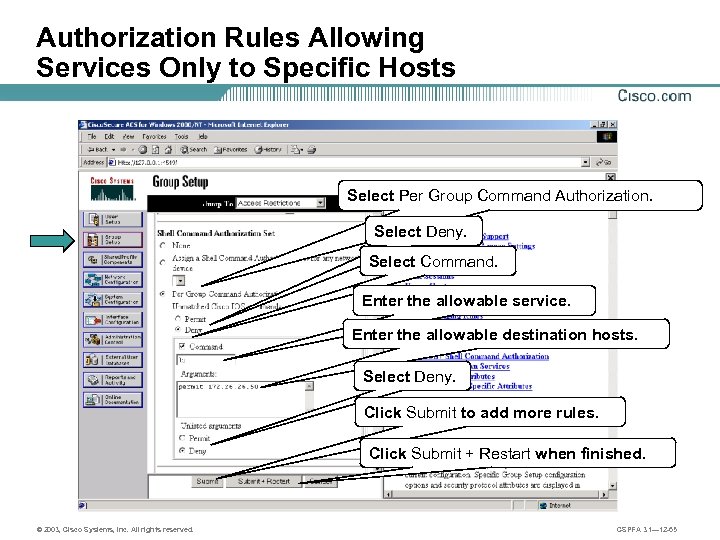 Authorization Rules Allowing Services Only to Specific Hosts Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Enter the allowable destination hosts. Select Deny. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -65
Authorization Rules Allowing Services Only to Specific Hosts Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Enter the allowable destination hosts. Select Deny. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -65
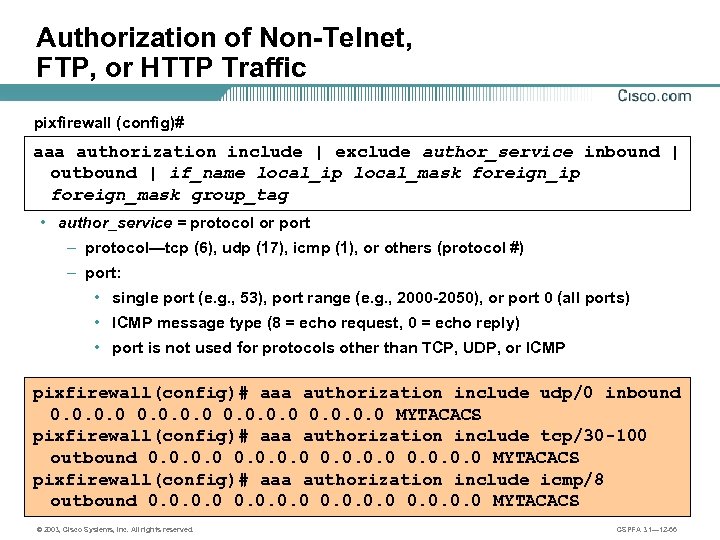 Authorization of Non-Telnet, FTP, or HTTP Traffic pixfirewall (config)# aaa authorization include | exclude author_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • author_service = protocol or port – protocol—tcp (6), udp (17), icmp (1), or others (protocol #) – port: • single port (e. g. , 53), port range (e. g. , 2000 -2050), or port 0 (all ports) • ICMP message type (8 = echo request, 0 = echo reply) • port is not used for protocols other than TCP, UDP, or ICMP pixfirewall(config)# aaa authorization include udp/0 inbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization include tcp/30 -100 outbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization include icmp/8 outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -66
Authorization of Non-Telnet, FTP, or HTTP Traffic pixfirewall (config)# aaa authorization include | exclude author_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • author_service = protocol or port – protocol—tcp (6), udp (17), icmp (1), or others (protocol #) – port: • single port (e. g. , 53), port range (e. g. , 2000 -2050), or port 0 (all ports) • ICMP message type (8 = echo request, 0 = echo reply) • port is not used for protocols other than TCP, UDP, or ICMP pixfirewall(config)# aaa authorization include udp/0 inbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization include tcp/30 -100 outbound 0. 0 MYTACACS pixfirewall(config)# aaa authorization include icmp/8 outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -66
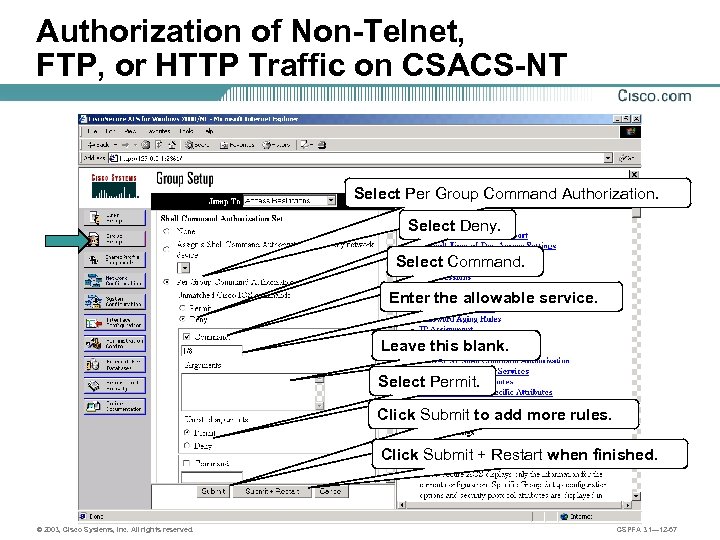 Authorization of Non-Telnet, FTP, or HTTP Traffic on CSACS-NT Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Leave this blank. Select Permit. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -67
Authorization of Non-Telnet, FTP, or HTTP Traffic on CSACS-NT Select Per Group Command Authorization. Select Deny. Select Command. Enter the allowable service. Leave this blank. Select Permit. Click Submit to add more rules. Click Submit + Restart when finished. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -67
 Downloadable ACLs © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -68
Downloadable ACLs © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -68
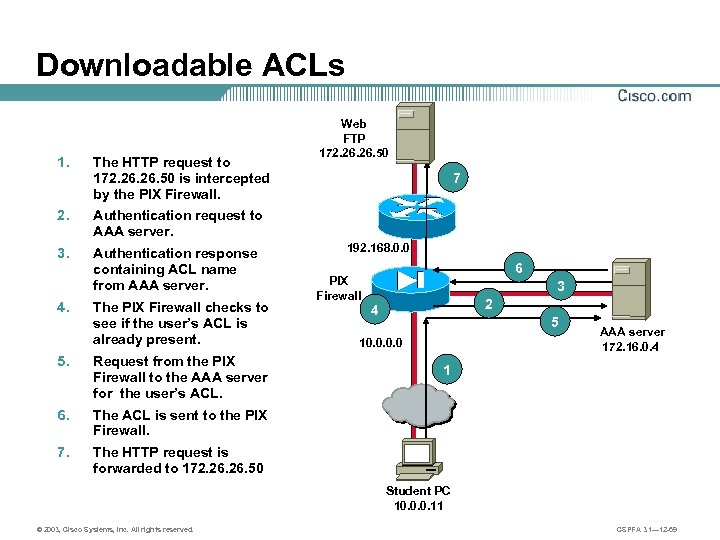 Downloadable ACLs 1. The HTTP request to 172. 26. 50 is intercepted by the PIX Firewall. 2. Authentication response containing ACL name from AAA server. 7 Authentication request to AAA server. 3. Web FTP 172. 26. 50 4. The PIX Firewall checks to see if the user’s ACL is already present. 5. Request from the PIX Firewall to the AAA server for the user’s ACL. 6 PIX Firewall 3 2 4 5 10. 0 AAA server 172. 16. 0. 4 The ACL is sent to the PIX Firewall. 7. 192. 168. 0. 0 The HTTP request is forwarded to 172. 26. 50 1 Student PC 10. 0. 0. 11 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -69
Downloadable ACLs 1. The HTTP request to 172. 26. 50 is intercepted by the PIX Firewall. 2. Authentication response containing ACL name from AAA server. 7 Authentication request to AAA server. 3. Web FTP 172. 26. 50 4. The PIX Firewall checks to see if the user’s ACL is already present. 5. Request from the PIX Firewall to the AAA server for the user’s ACL. 6 PIX Firewall 3 2 4 5 10. 0 AAA server 172. 16. 0. 4 The ACL is sent to the PIX Firewall. 7. 192. 168. 0. 0 The HTTP request is forwarded to 172. 26. 50 1 Student PC 10. 0. 0. 11 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -69
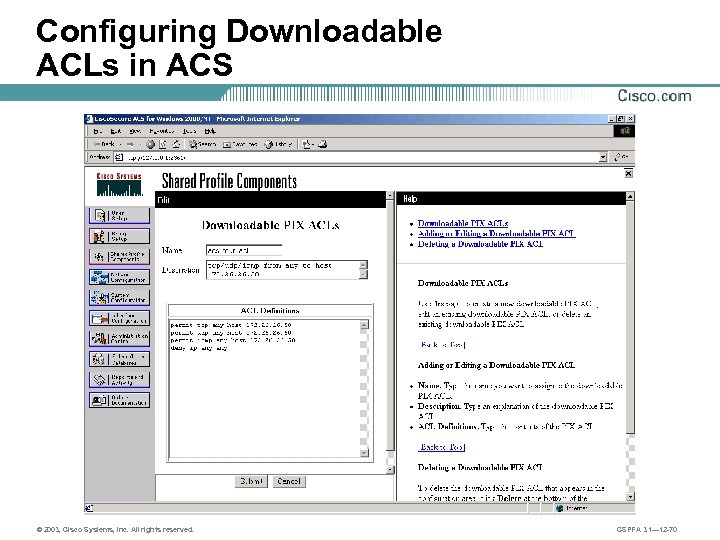 Configuring Downloadable ACLs in ACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -70
Configuring Downloadable ACLs in ACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -70
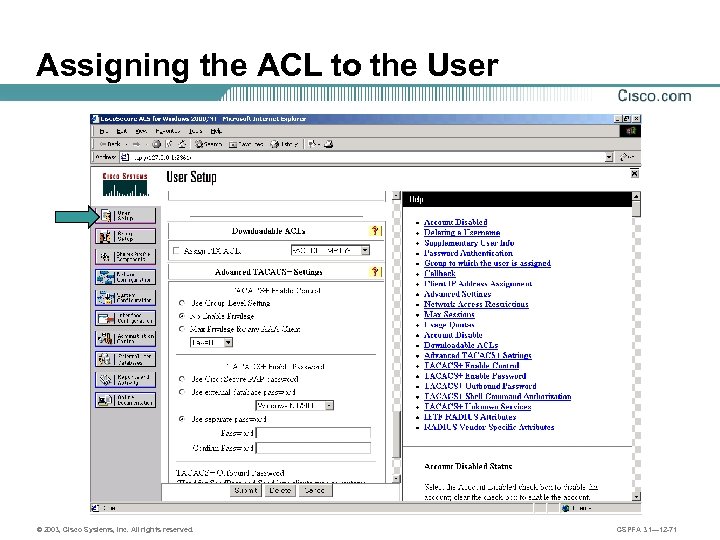 Assigning the ACL to the User © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -71
Assigning the ACL to the User © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -71
 Accounting Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -72
Accounting Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -72
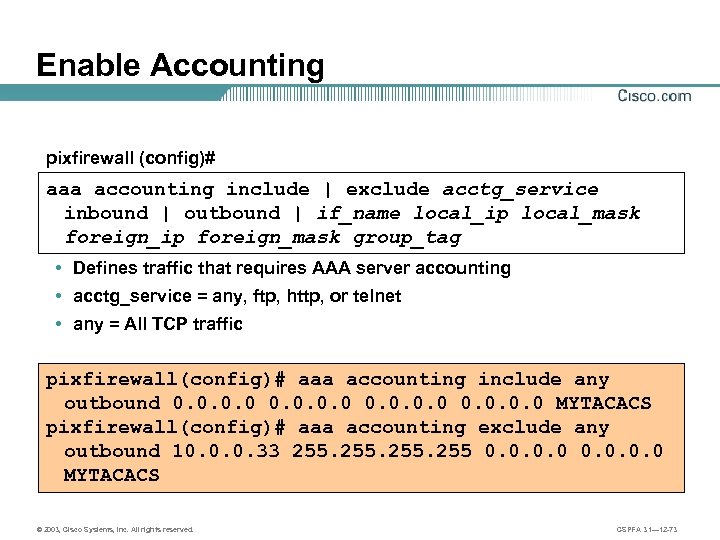 Enable Accounting pixfirewall (config)# aaa accounting include | exclude acctg_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic that requires AAA server accounting • acctg_service = any, ftp, http, or telnet • any = All TCP traffic pixfirewall(config)# aaa accounting include any outbound 0. 0 MYTACACS pixfirewall(config)# aaa accounting exclude any outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -73
Enable Accounting pixfirewall (config)# aaa accounting include | exclude acctg_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • Defines traffic that requires AAA server accounting • acctg_service = any, ftp, http, or telnet • any = All TCP traffic pixfirewall(config)# aaa accounting include any outbound 0. 0 MYTACACS pixfirewall(config)# aaa accounting exclude any outbound 10. 0. 0. 33 255 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -73
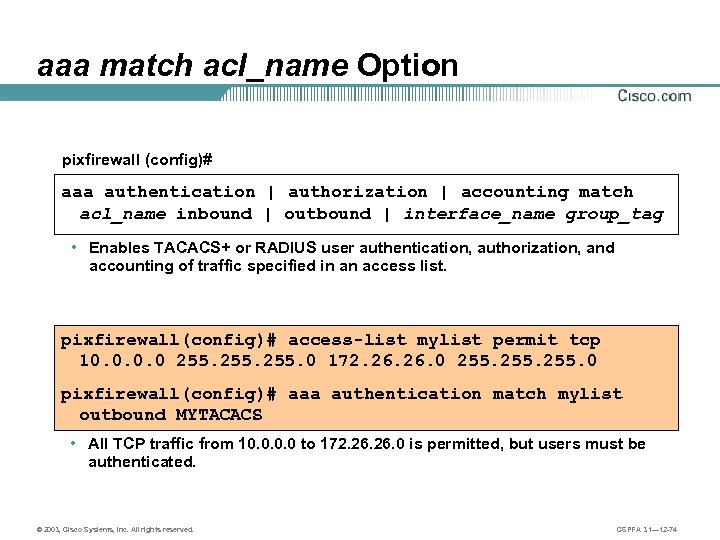 aaa match acl_name Option pixfirewall (config)# aaa authentication | authorization | accounting match acl_name inbound | outbound | interface_name group_tag • Enables TACACS+ or RADIUS user authentication, authorization, and accounting of traffic specified in an access list. pixfirewall(config)# access-list mylist permit tcp 10. 0 255. 0 172. 26. 0 255. 0 pixfirewall(config)# aaa authentication match mylist outbound MYTACACS • All TCP traffic from 10. 0 to 172. 26. 0 is permitted, but users must be authenticated. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -74
aaa match acl_name Option pixfirewall (config)# aaa authentication | authorization | accounting match acl_name inbound | outbound | interface_name group_tag • Enables TACACS+ or RADIUS user authentication, authorization, and accounting of traffic specified in an access list. pixfirewall(config)# access-list mylist permit tcp 10. 0 255. 0 172. 26. 0 255. 0 pixfirewall(config)# aaa authentication match mylist outbound MYTACACS • All TCP traffic from 10. 0 to 172. 26. 0 is permitted, but users must be authenticated. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -74
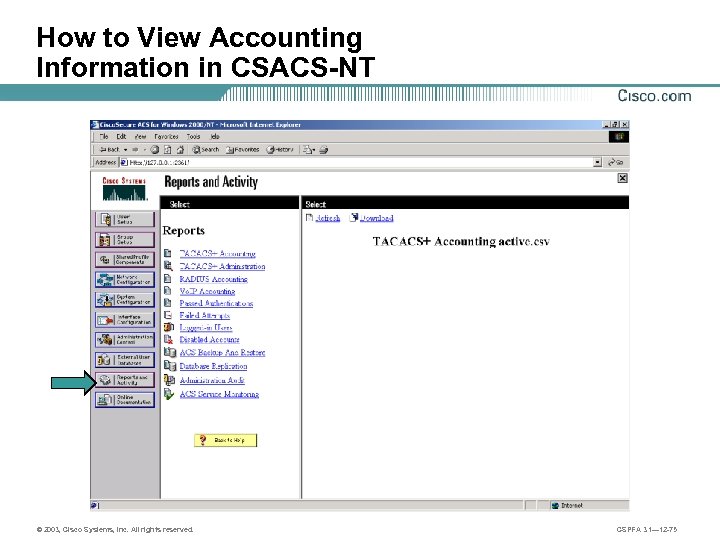 How to View Accounting Information in CSACS-NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -75
How to View Accounting Information in CSACS-NT © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -75
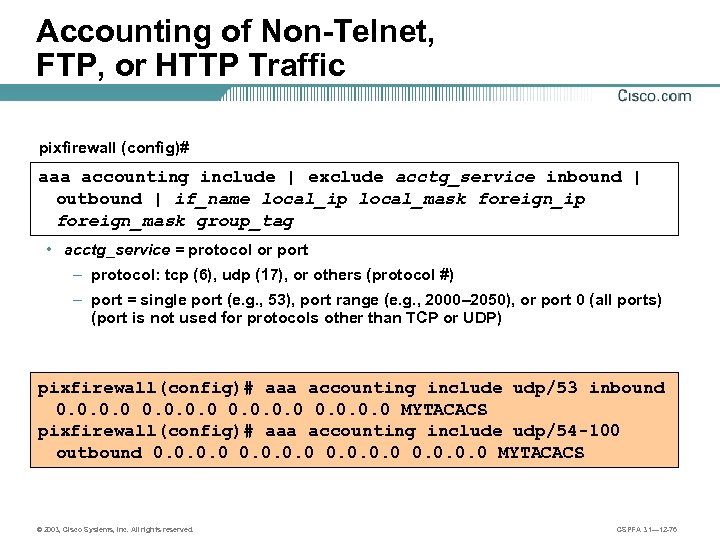 Accounting of Non-Telnet, FTP, or HTTP Traffic pixfirewall (config)# aaa accounting include | exclude acctg_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • acctg_service = protocol or port – protocol: tcp (6), udp (17), or others (protocol #) – port = single port (e. g. , 53), port range (e. g. , 2000– 2050), or port 0 (all ports) (port is not used for protocols other than TCP or UDP) pixfirewall(config)# aaa accounting include udp/53 inbound 0. 0 MYTACACS pixfirewall(config)# aaa accounting include udp/54 -100 outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -76
Accounting of Non-Telnet, FTP, or HTTP Traffic pixfirewall (config)# aaa accounting include | exclude acctg_service inbound | outbound | if_name local_ip local_mask foreign_ip foreign_mask group_tag • acctg_service = protocol or port – protocol: tcp (6), udp (17), or others (protocol #) – port = single port (e. g. , 53), port range (e. g. , 2000– 2050), or port 0 (all ports) (port is not used for protocols other than TCP or UDP) pixfirewall(config)# aaa accounting include udp/53 inbound 0. 0 MYTACACS pixfirewall(config)# aaa accounting include udp/54 -100 outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -76
 Troubleshooting the AAA Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -77
Troubleshooting the AAA Configuration © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -77
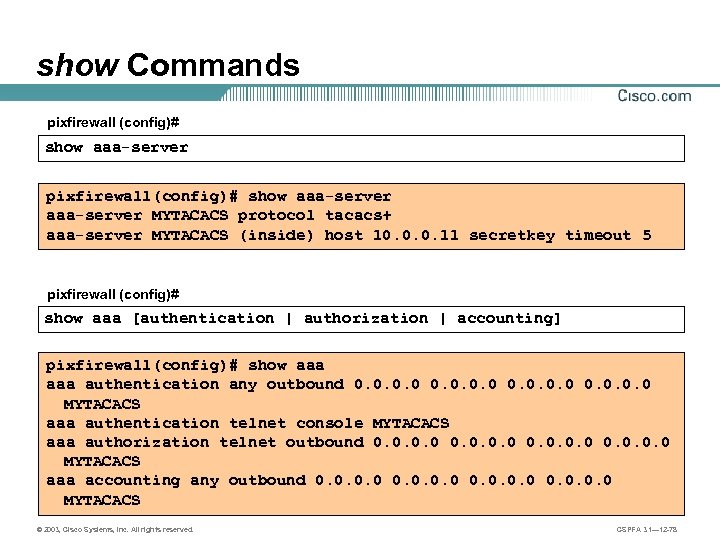 show Commands pixfirewall (config)# show aaa-server pixfirewall(config)# show aaa-server MYTACACS protocol tacacs+ aaa-server MYTACACS (inside) host 10. 0. 0. 11 secretkey timeout 5 pixfirewall (config)# show aaa [authentication | authorization | accounting] pixfirewall(config)# show aaa authentication any outbound 0. 0 MYTACACS aaa authentication telnet console MYTACACS aaa authorization telnet outbound 0. 0 MYTACACS aaa accounting any outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -78
show Commands pixfirewall (config)# show aaa-server pixfirewall(config)# show aaa-server MYTACACS protocol tacacs+ aaa-server MYTACACS (inside) host 10. 0. 0. 11 secretkey timeout 5 pixfirewall (config)# show aaa [authentication | authorization | accounting] pixfirewall(config)# show aaa authentication any outbound 0. 0 MYTACACS aaa authentication telnet console MYTACACS aaa authorization telnet outbound 0. 0 MYTACACS aaa accounting any outbound 0. 0 MYTACACS © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -78
![show Commands (cont. ) pixfirewall (config)# show auth-prompt [prompt | accept | reject] pixfirewall(config)# show Commands (cont. ) pixfirewall (config)# show auth-prompt [prompt | accept | reject] pixfirewall(config)#](https://present5.com/presentation/4e7298b135d9b4fa214805ef6481f59b/image-79.jpg) show Commands (cont. ) pixfirewall (config)# show auth-prompt [prompt | accept | reject] pixfirewall(config)# show auth-prompt auth-prompt accept auth-prompt reject auth-prompt Authenticate to the Firewall You’ve been Authenticated Authentication Failed pixfirewall (config)# show timeout uauth pixfirewall(config)# show timeout uauth 3: 00 absolute uauth 0: 30: 00 inactivity pixfirewall (config)# show virtual [http | telnet] pixfirewall(config)# show virtual http 192. 168. 0. 2 virtual telnet 192. 168. 0. 2 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -79
show Commands (cont. ) pixfirewall (config)# show auth-prompt [prompt | accept | reject] pixfirewall(config)# show auth-prompt auth-prompt accept auth-prompt reject auth-prompt Authenticate to the Firewall You’ve been Authenticated Authentication Failed pixfirewall (config)# show timeout uauth pixfirewall(config)# show timeout uauth 3: 00 absolute uauth 0: 30: 00 inactivity pixfirewall (config)# show virtual [http | telnet] pixfirewall(config)# show virtual http 192. 168. 0. 2 virtual telnet 192. 168. 0. 2 © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -79
 Summary © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -80
Summary © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -80
 Summary • Authentication is who you are, authorization is what you can do, and accounting is what you did. • The PIX Firewall supports the following AAA protocols: TACACS+ and RADIUS. • Users are authenticated with Telnet, FTP, or HTTP by the PIX Firewall. • Cut-through proxy technology allows users through the PIX Firewall after authenticating. • Two steps must be taken to enable AAA: – Configure AAA on the PIX Firewall. – Install and configure CSACS on a server. • Downloadable ACLs enable you to enter an ACL once, in CSACS, and then load that ACL to any number of PIX Firewalls during user authentication. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -81
Summary • Authentication is who you are, authorization is what you can do, and accounting is what you did. • The PIX Firewall supports the following AAA protocols: TACACS+ and RADIUS. • Users are authenticated with Telnet, FTP, or HTTP by the PIX Firewall. • Cut-through proxy technology allows users through the PIX Firewall after authenticating. • Two steps must be taken to enable AAA: – Configure AAA on the PIX Firewall. – Install and configure CSACS on a server. • Downloadable ACLs enable you to enter an ACL once, in CSACS, and then load that ACL to any number of PIX Firewalls during user authentication. © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -81
 Lab Exercise © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -82
Lab Exercise © 2003, Cisco Systems, Inc. All rights reserved. CSPFA 3. 1— 12 -82
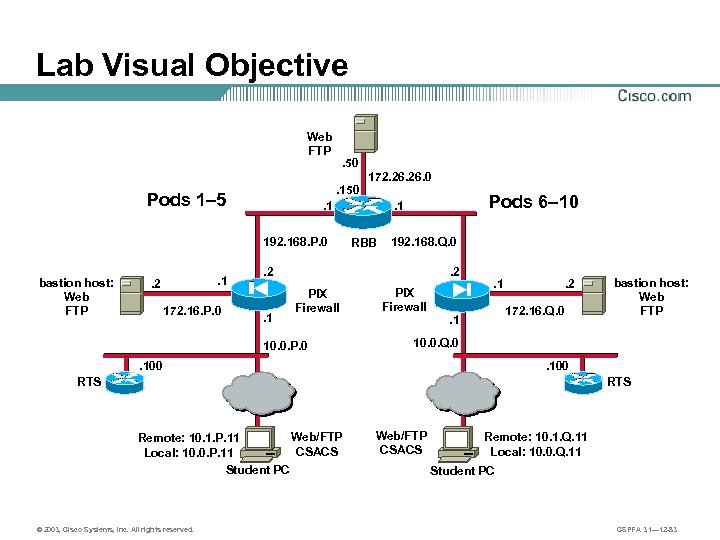 Lab Visual Objective Web FTP . 50 Pods 1– 5 . 1 . 2 172. 16. P. 0 Pods 6– 10 . 1 192. 168. P. 0 bastion host: Web FTP 172. 26. 0 . 150 RBB 192. 168. Q. 0 . 2 . 1 . 2 PIX Firewall 10. 0. P. 0 PIX Firewall . 1 . 2 172. 16. Q. 0 . 1 bastion host: Web FTP 10. 0. Q. 0 . 100 RTS Web/FTP Remote: 10. 1. P. 11 CSACS Local: 10. 0. P. 11 Student PC © 2003, Cisco Systems, Inc. All rights reserved. Web/FTP CSACS Remote: 10. 1. Q. 11 Local: 10. 0. Q. 11 Student PC CSPFA 3. 1— 12 -83
Lab Visual Objective Web FTP . 50 Pods 1– 5 . 1 . 2 172. 16. P. 0 Pods 6– 10 . 1 192. 168. P. 0 bastion host: Web FTP 172. 26. 0 . 150 RBB 192. 168. Q. 0 . 2 . 1 . 2 PIX Firewall 10. 0. P. 0 PIX Firewall . 1 . 2 172. 16. Q. 0 . 1 bastion host: Web FTP 10. 0. Q. 0 . 100 RTS Web/FTP Remote: 10. 1. P. 11 CSACS Local: 10. 0. P. 11 Student PC © 2003, Cisco Systems, Inc. All rights reserved. Web/FTP CSACS Remote: 10. 1. Q. 11 Local: 10. 0. Q. 11 Student PC CSPFA 3. 1— 12 -83


