c8cb52810a74d14427e5e334e9137bb3.ppt
- Количество слайдов: 23
 A Two-Server Auction Scheme Ari Juels and Mike Szydlo Financial Cryptography ‘ 02 12 March 2002
A Two-Server Auction Scheme Ari Juels and Mike Szydlo Financial Cryptography ‘ 02 12 March 2002
 Auctions increasingly popular u 2. 6 million new auctions per day on e. Bay in 2000 – About three auctions per year for every inhabitant of U. S. u Attempted auctions (and hoaxes) in ‘ 99: – A healthy kidney (high bid: $5. 7 million) – A military rocket launcher – 200 pounds of cocaine – A team of software engineers – A baby (high bid: $109, 100) – A teenage boy selling his virginity (high bid: $10 million)
Auctions increasingly popular u 2. 6 million new auctions per day on e. Bay in 2000 – About three auctions per year for every inhabitant of U. S. u Attempted auctions (and hoaxes) in ‘ 99: – A healthy kidney (high bid: $5. 7 million) – A military rocket launcher – 200 pounds of cocaine – A team of software engineers – A baby (high bid: $109, 100) – A teenage boy selling his virginity (high bid: $10 million)
 popular with all sorts. . . Diebenkorn Shilling Case Draws FBI Probe The fallout from Kenneth A. Walton's failed e. Bay auction of a "great big wild abstract painting" continues today… Former Sotheby's chairman guilty BBC News, 6 December 2001 The former chairman of auction house Sotheby's has been found guilty in New York of conspiring to fix art prices after two days of jury deliberations.
popular with all sorts. . . Diebenkorn Shilling Case Draws FBI Probe The fallout from Kenneth A. Walton's failed e. Bay auction of a "great big wild abstract painting" continues today… Former Sotheby's chairman guilty BBC News, 6 December 2001 The former chairman of auction house Sotheby's has been found guilty in New York of conspiring to fix art prices after two days of jury deliberations.
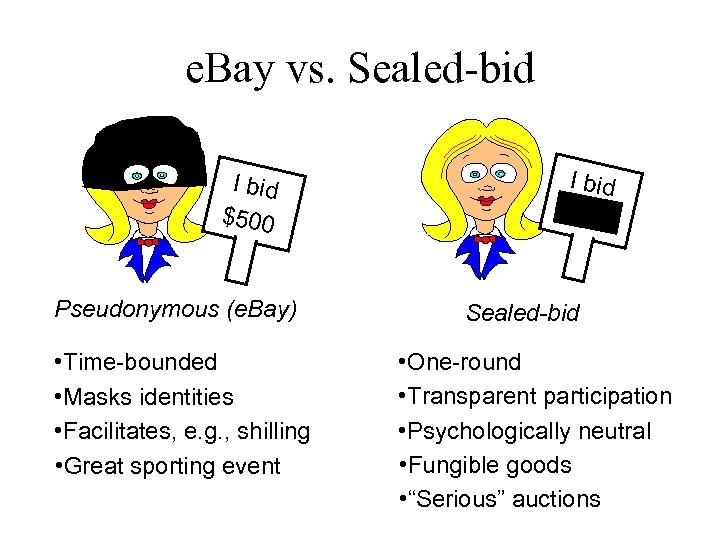 e. Bay vs. Sealed-bid I bid $500 Pseudonymous (e. Bay) • Time-bounded • Masks identities • Facilitates, e. g. , shilling • Great sporting event I bid $500 Sealed-bid • One-round • Transparent participation • Psychologically neutral • Fungible goods • “Serious” auctions
e. Bay vs. Sealed-bid I bid $500 Pseudonymous (e. Bay) • Time-bounded • Masks identities • Facilitates, e. g. , shilling • Great sporting event I bid $500 Sealed-bid • One-round • Transparent participation • Psychologically neutral • Fungible goods • “Serious” auctions
 Sealed-Bid Auctions Alice Cate Bob Duke
Sealed-Bid Auctions Alice Cate Bob Duke
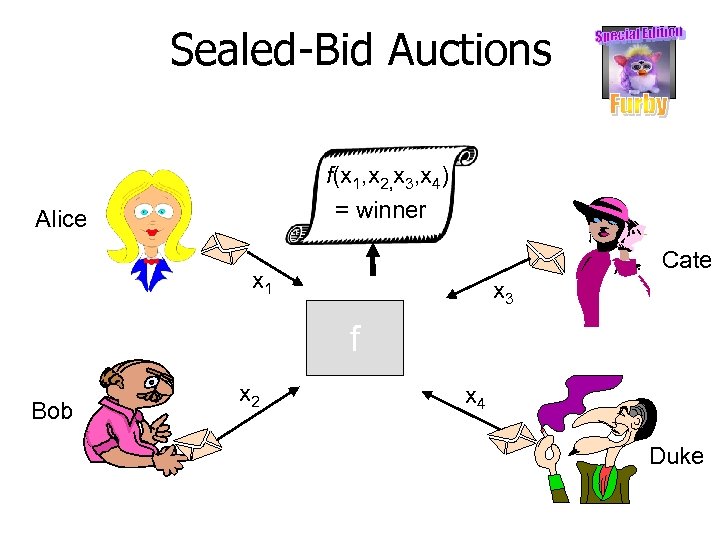 Sealed-Bid Auctions f(x 1, x 2, x 3, x 4) = winner Alice Cate x 1 x 3 f Bob x 2 x 4 Duke
Sealed-Bid Auctions f(x 1, x 2, x 3, x 4) = winner Alice Cate x 1 x 3 f Bob x 2 x 4 Duke
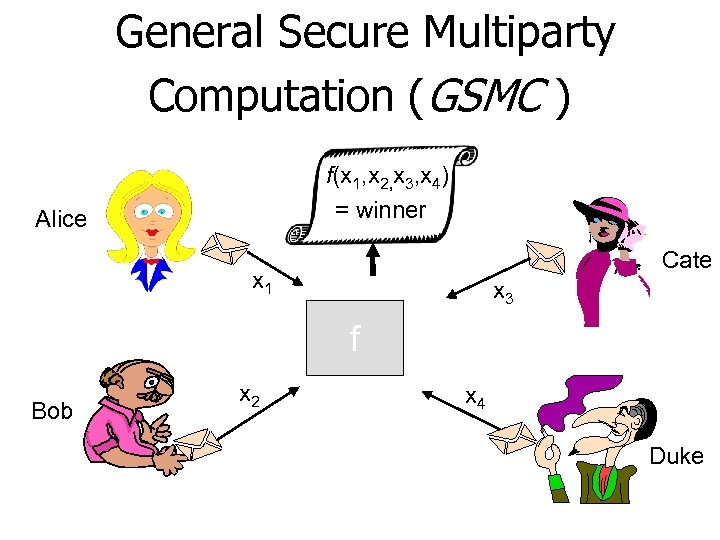 General Secure Multiparty Computation (GSMC ) f(x 1, x 2, x 3, x 4) = winner Alice Cate x 1 x 3 f Bob x 2 x 4 Duke
General Secure Multiparty Computation (GSMC ) f(x 1, x 2, x 3, x 4) = winner Alice Cate x 1 x 3 f Bob x 2 x 4 Duke
 The Literature on -Bid Auctions u Sealed Most sealed-bid systems get away from inefficiencies of GSMC – Weakened trust models – Specifying function f as “maximum” u Some tailor GSMC to auctions – JJ 00 – NPS 99 (Naor, Pinkas, and Sumner)
The Literature on -Bid Auctions u Sealed Most sealed-bid systems get away from inefficiencies of GSMC – Weakened trust models – Specifying function f as “maximum” u Some tailor GSMC to auctions – JJ 00 – NPS 99 (Naor, Pinkas, and Sumner)
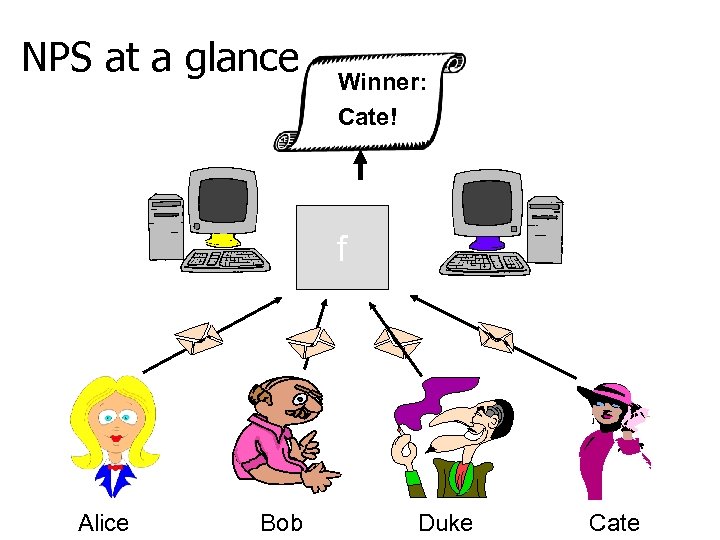 NPS at a glance Winner: Cate! f Alice Bob Duke Cate
NPS at a glance Winner: Cate! f Alice Bob Duke Cate
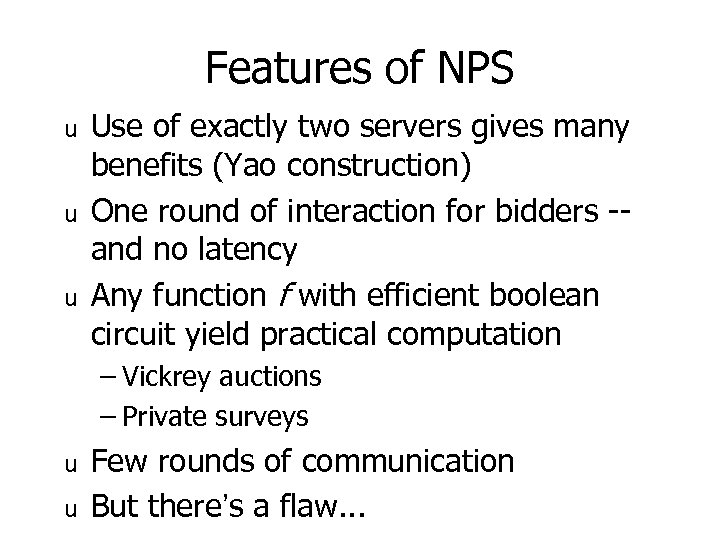 Features of NPS u u u Use of exactly two servers gives many benefits (Yao construction) One round of interaction for bidders -and no latency Any function f with efficient boolean circuit yield practical computation – Vickrey auctions – Private surveys u u Few rounds of communication But there’s a flaw. . .
Features of NPS u u u Use of exactly two servers gives many benefits (Yao construction) One round of interaction for bidders -and no latency Any function f with efficient boolean circuit yield practical computation – Vickrey auctions – Private surveys u u Few rounds of communication But there’s a flaw. . .
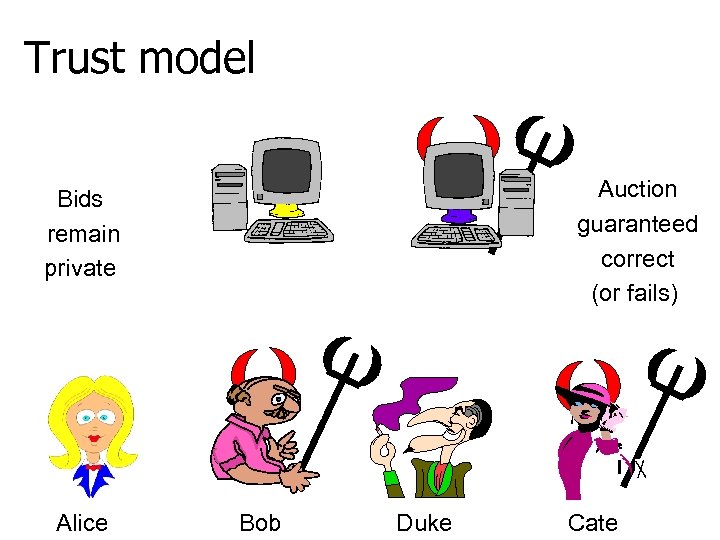 Trust model Auction guaranteed correct (or fails) Bids remain private Alice Bob Duke Cate
Trust model Auction guaranteed correct (or fails) Bids remain private Alice Bob Duke Cate
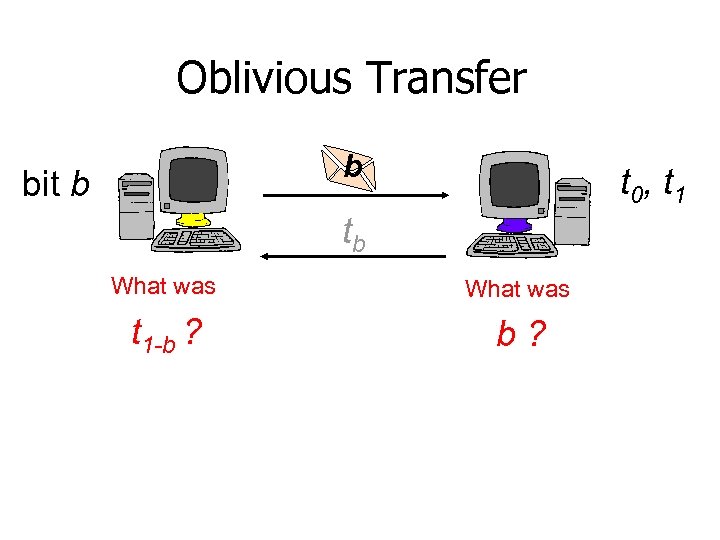 Oblivious Transfer b bit b t 0, t 1 tb What was t 1 -b ? b?
Oblivious Transfer b bit b t 0, t 1 tb What was t 1 -b ? b?
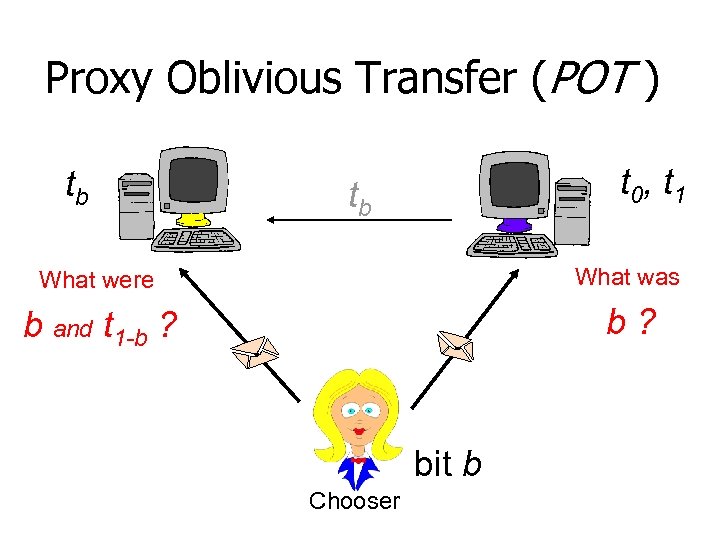 Proxy Oblivious Transfer (POT ) tb t 0, t 1 tb What were What was b and t 1 -b ? bit b Chooser
Proxy Oblivious Transfer (POT ) tb t 0, t 1 tb What were What was b and t 1 -b ? bit b Chooser
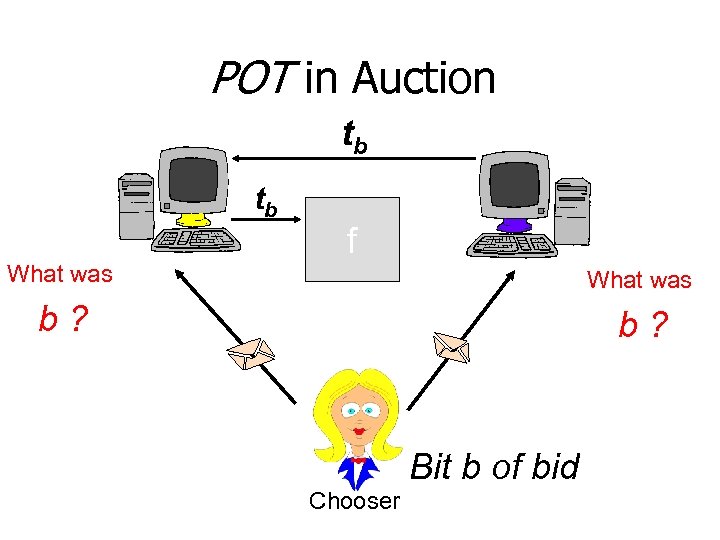 POT in Auction tb tb What was f What was b? Bit b of bid Chooser
POT in Auction tb tb What was f What was b? Bit b of bid Chooser
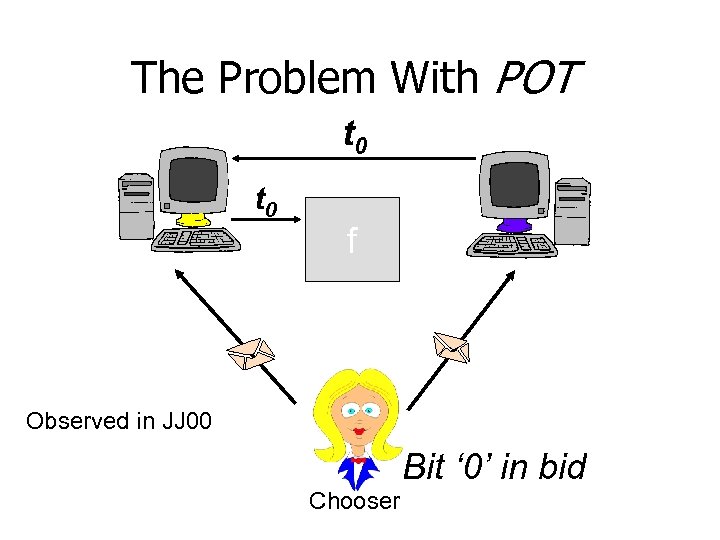 The Problem With POT t 0 f Observed in JJ 00 Bit ‘ 0’ in bid Chooser
The Problem With POT t 0 f Observed in JJ 00 Bit ‘ 0’ in bid Chooser
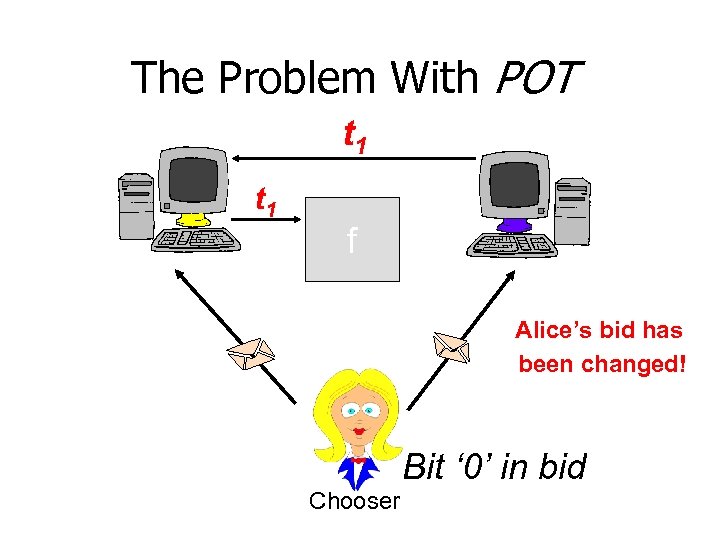 The Problem With POT t 1 f Alice’s bid has been changed! Bit ‘ 0’ in bid Chooser
The Problem With POT t 1 f Alice’s bid has been changed! Bit ‘ 0’ in bid Chooser
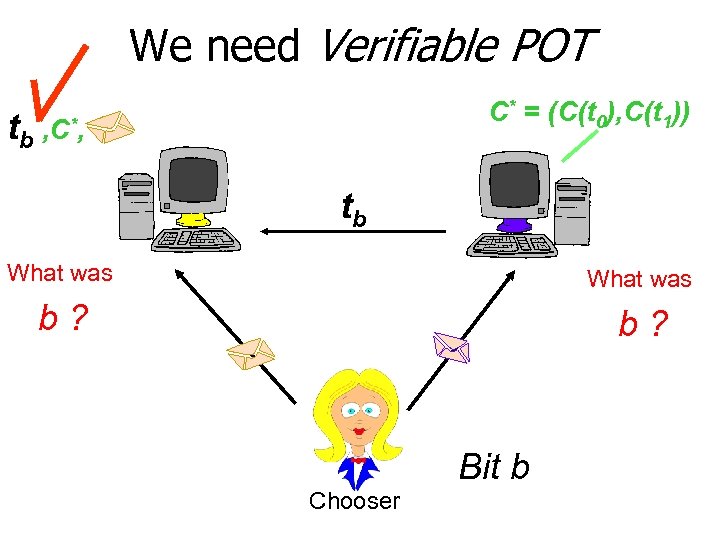 We need Verifiable POT C* = (C(t 0), C(t 1)) tb , C*, tb What was b? Bit b Chooser
We need Verifiable POT C* = (C(t 0), C(t 1)) tb , C*, tb What was b? Bit b Chooser
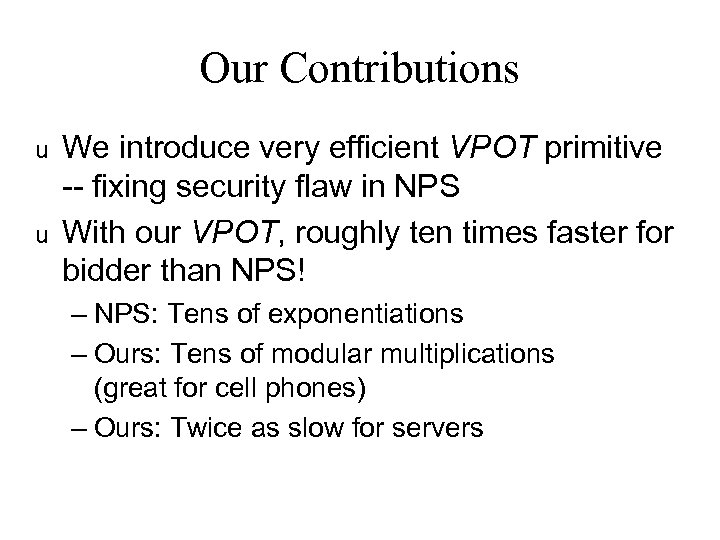 Our Contributions u u We introduce very efficient VPOT primitive -- fixing security flaw in NPS With our VPOT, roughly ten times faster for bidder than NPS! – NPS: Tens of exponentiations – Ours: Tens of modular multiplications (great for cell phones) – Ours: Twice as slow for servers
Our Contributions u u We introduce very efficient VPOT primitive -- fixing security flaw in NPS With our VPOT, roughly ten times faster for bidder than NPS! – NPS: Tens of exponentiations – Ours: Tens of modular multiplications (great for cell phones) – Ours: Twice as slow for servers
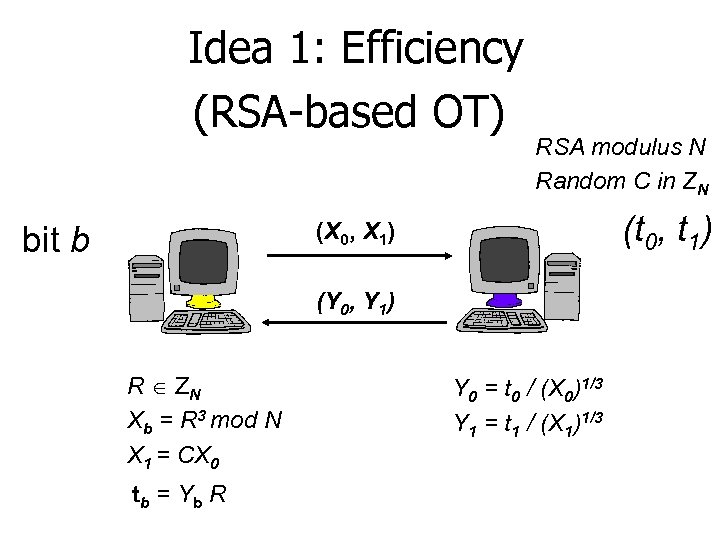 Idea 1: Efficiency (RSA-based OT) RSA modulus N Random C in ZN (t 0, t 1) (X 0, X 1) bit b (Y 0, Y 1) R ZN Xb = R 3 mod N X 1 = CX 0 tb = Y b R Y 0 = t 0 / (X 0)1/3 Y 1 = t 1 / (X 1)1/3
Idea 1: Efficiency (RSA-based OT) RSA modulus N Random C in ZN (t 0, t 1) (X 0, X 1) bit b (Y 0, Y 1) R ZN Xb = R 3 mod N X 1 = CX 0 tb = Y b R Y 0 = t 0 / (X 0)1/3 Y 1 = t 1 / (X 1)1/3
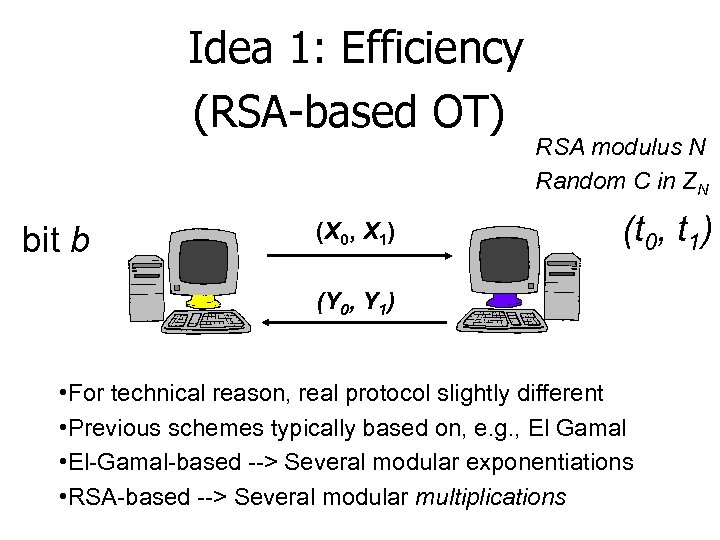 Idea 1: Efficiency (RSA-based OT) bit b (X 0, X 1) RSA modulus N Random C in ZN (t 0, t 1) (Y 0, Y 1) • For technical reason, real protocol slightly different • Previous schemes typically based on, e. g. , El Gamal • El-Gamal-based --> Several modular exponentiations • RSA-based --> Several modular multiplications
Idea 1: Efficiency (RSA-based OT) bit b (X 0, X 1) RSA modulus N Random C in ZN (t 0, t 1) (Y 0, Y 1) • For technical reason, real protocol slightly different • Previous schemes typically based on, e. g. , El Gamal • El-Gamal-based --> Several modular exponentiations • RSA-based --> Several modular multiplications
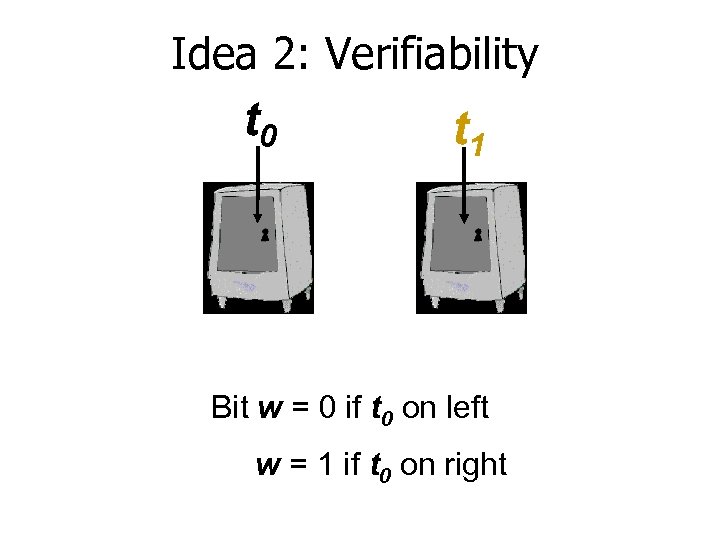 Idea 2: Verifiability t 0 t 1 Bit w = 0 if t 0 on left w = 1 if t 0 on right
Idea 2: Verifiability t 0 t 1 Bit w = 0 if t 0 on left w = 1 if t 0 on right
 Idea 2: Verifiability u. Prove ordering of vaults = Prove fact about single bit w u. Key tool: Goldwasser-Micali ‘ 84
Idea 2: Verifiability u. Prove ordering of vaults = Prove fact about single bit w u. Key tool: Goldwasser-Micali ‘ 84
 Conclusion u u u NPS clever, practical approach to sealedbid auctions With VPOT, we can bring NPS ideas to fruition High efficiency for weak bidding devices, e. g. , cell phones
Conclusion u u u NPS clever, practical approach to sealedbid auctions With VPOT, we can bring NPS ideas to fruition High efficiency for weak bidding devices, e. g. , cell phones


