763c153ac6b162df8dc11686ee365539.ppt
- Количество слайдов: 30

A Social Semantic Infrastructure for Decentralised Systems Based on Specification-Carrying Code and Trust Giovanna Di Marzo Serugendo University of Geneva, Switzerland SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 1
Outline • Semantic Infrastructure – « Specification-Carrying Code » (SCC) – Service-oriented architecture • Social Infrastructure – Trust-Based Systems • Social Semantic Infrastructure – SCC + Trust SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 2

Applications • Wireless / Ad hoc Networks – Bluetooth / Wi. Fi / Ad hoc networks of PDAs – Sensor Networks • Grid • Agent-Based Systems • Ambient Intelligence – End-user services based on an invisible intelligent techonology • Virtual shopping, visa detection, traffic management • Autonomic Computing – Self-management systems • Large Scale Security Systems SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 3

Applications • Characteristics – Based on autonomous entities • Ex: PDAs, Agents – – – Uncertain environment Decentralised Large number of components Dynamic environment Need for adaptability Social dimension • Interactions, discovery, negociations, transactions SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 4

Issues • Interactions with unknown entities (semantics) – Understanding – Interoperability • Management of uncertainty (social) – Malicious entities • Exhibit desirable characteristics, but … – Good faith entities • Fail because: software error, lack of toner, paper jam, … • Adaptability to changing environment • Control / Design of decentralised behaviour – Good properties have to emerge – Bad properties to be avoided! SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 5

Specification-Carrying Code • Interaction with unknown entities – No common design / No common API • Idea: communication is based on a formal specification of the behaviour of a peer entity – Software « carries » a formal description of its own functional behaviour – Communication occurs without API – Formal specification defines the semantics of the behaviour SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 6

SCC - Principle • Scenario – Publication of specifications • Services requested / Services proposed – Specification matching • Proposed service matches requested service – Service realised in an anonymous / asynchronous / nondeterministic manner • Interest – Minimum basis for communication • Specification language (for expressing concepts) – Interaction with new software / with unknown software – No central control (self-assembly) SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 7
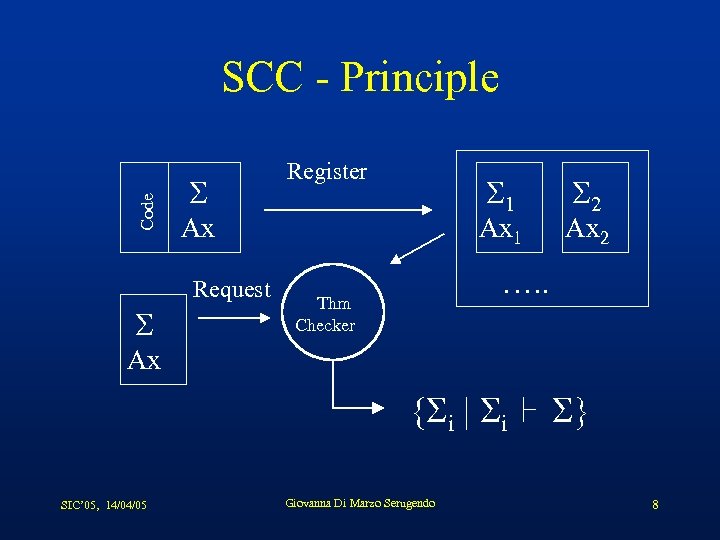
Code SCC - Principle S S 1 Ax Request S Register Ax 1 S 2 Ax 2 …. . Thm Checker Ax {Si | Si S} SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 8
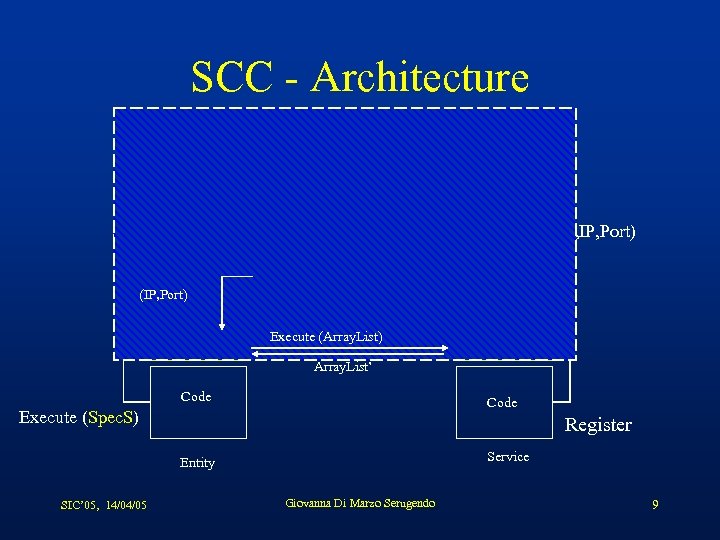
SCC - Architecture Reg. Ex Search (Spec. S) (IP, Port) Code. WR/Spec. E Spec. S Prolog HOL Spec. S, (IP, Port) Register (Spec. S, IP, Port) Service Manager Execute (Array. List) Code. WR/Spec. S Array. List’ Code Execute (Spec. S) Register Service Entity SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 9

SCC – Keywords • Registration (Functionality: ``File. System´´: ``Read´´, Behaviour: String : ``return´´ : String, Qo. S: ``local´´, [3, 2, 1]) • Request (Functionality: ``File. System´´: ``Read´´, Behaviour: ``my. File. html´´ : ``return´´ : String, Qo. S: ``local´´, [3, 2, 1]) SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 10

SCC – Reg. Ex • Registration • Request <specs> <description active="true"> <content> Sorting service </content> </description> <regex active="true"> <name>(? i)w*sortw*</name> <params>String*</params> <result>String*</result> </regex> </specs> <specs> <description active="true"> <content>Sorting request </content> </description> <regex active="true"> <name>sort</name> <params>String*</params> <result>String*</result> </regex> </specs> SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 11
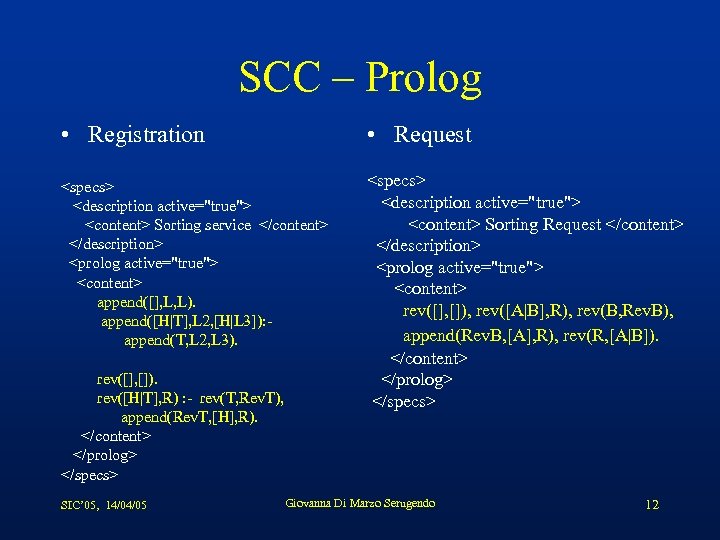
SCC – Prolog • Registration • Request <specs> <description active="true"> <content> Sorting Request </content> </description> <prolog active="true"> <content> rev([], []), rev([A|B], R), rev(B, Rev. B), append(Rev. B, [A], R), rev(R, [A|B]). </content> rev([], []). </prolog> rev([H|T], R) : - rev(T, Rev. T), </specs> <specs> <description active="true"> <content> Sorting service </content> </description> <prolog active="true"> <content> append([], L, L). append([H|T], L 2, [H|L 3]): append(T, L 2, L 3). append(Rev. T, [H], R). </content> </prolog> </specs> SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 12

SCC – Alternatives • Specification ü ü ü – – – Keywords Regular Expressions (syntactic) Prolog (SWIProlog) HOL (Isabelle Thm Prover – meta-ontology) Jena (Logic + ontology) Common Simple Logic • Architecture ü Publication of specifications (asynchronous / anonymous / nondeterministic) – Direct exchange of specifications (interaction decisions) • Service Discovery – JXTA protocols – Géo-positioning • Information contained in the specification – Functional – Non-functional, security, reputation, positioning, etc, SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 13

SCC - Advantages • Interaction/Interoperability with unknown peers • Integration with new entities • Ontology+Semantics • Service Combination • Robustness • Resilience SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 14

SCC for Unanticipated Run-time Code Evolution • Code changes during its execution (without stopping the application) • Non anticipated evolution – Non anticipated by the programmer • Distribution on the fly • Experiments – Web Server • 160 different versions of the server, with only 4 stops – Tic-Tac-toe for Open Days • Changes done to the application during the play SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 15

SCC for Autonomic Computing • Self-configuration (installation, configuration, integration) – SCC expresses high-level configuration policies • Installation needs • Seamless integration of new entities • Self-repair (error detection, diagnostic, repair) – Generation of correct code from SCC – Replace error code with code having matching specification – Checking of code against specification SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 16

SCC for Autonomic Computing • Self-optimisation (parameters) – SCC expresses optimisation policies • Parameters description • Permanent optimisation of parameters depending on the context • Self-protection (detection and response to attacks) – SCC expresses security policies • Conditions regulating services delivery • Signatures of attacks / Response schema SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 17
SCC vs PCC vs Trust • SCC – Code is decoupled from specification – No guarantee that the code satisfies the specification – It is the same with APIs! • Proof Carrying Code (PCC) [Necula 00] – Code « carries » the proof that it is correct • Low level (no infinite loop, no division by zero) • Not at the functional level • No specification – What happens if the code/proof are malicious? – What happens if the code/proof are in good faith, but the code fails? • Trust – Adaptation mechanism based on experience and observation SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 18

Trust-based Systems • Human notion of trust – Uncertainty and partial knowledge – Human beings make choices, take decisions, learn by experience, adapt their behavior – Decisions implicitly rely on trust: • Peers • Legal institutions • Business companies • Idea – Human-like trust-based access control – To learn about peer behavior – To dynamically adapt access control policies SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 19

Trust-based Systems • Software entities – Part of decentralised and distributed systems – Autonomous, roaming – Highly changing environment • Information changes and is not permanently valid – – Interactions occur locally Partial knowledge about the entities, and the environment Take decisions with local and incomplete knowledge Trust-based schema helps evaluating: • Good faith, correct functioning SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 20
Trust-based Model (1) • Principals: – interacting set of entities (human/computers, trusted or untrusted) • Local trust values: – Principals maintain local trust values about other principals • Evidence – Direct observations: evaluated outcome of an interaction – Recommendations: asked or received (indirect observation) SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 21
Trust-based Model (2) • Scenario – Request of interaction – Decision making process • Recognise principal • Evaluate trust value, evidence, risk implied by requested interaction • Application of Control Policy – After interaction: trust value updated on the basis of evaluated outcome of the interaction • Trust evolves with time – allows to adapt behaviour of principal SECURE – IST Funded Project (2002 -2004) SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 22

Issues • Autonomous Systems • Needs – Interaction with unknown entities – Exchange of capabilities: • To learn about peer behavior • Issues – Malicious entities • Exhibit desirable characteristics, but … – Good Faith entities • Fail because: software error, lack of toner, paper jam, … • Idea – Combination of specifications and trust SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 23
SCC and Trust-based model • Human behavior – Communication through semantic information • Autonomous software: Entities carry specification describing their functional and non-functional behavior – Decisions despite uncertainty • Autonomous software: Trust formation and evolution SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 24

SCC and Trust-based model • Request for collaboration and exchange of Specification – Principals learn services provided by other principals • Decision to interact – Evaluation of specifications, past direct observations, received recommendations, local trust value, risk implied by interaction • Trust update – Evaluation (positive or negative) of outcome of interaction – Spreading of recommendations SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 25
Example: Printers and PDAs • Set of printers (not predefined) • Set of computers (using printers, not predefined) • Exchange of capabilities before interactions – Postscript/double-sided • Storing of interactions outcome – Only single-sided, no printing • Local trust value computation and update • Propagation of recommendations • Risks: – Losing time using a far located printer, printer runs out of paper, etc. SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 26
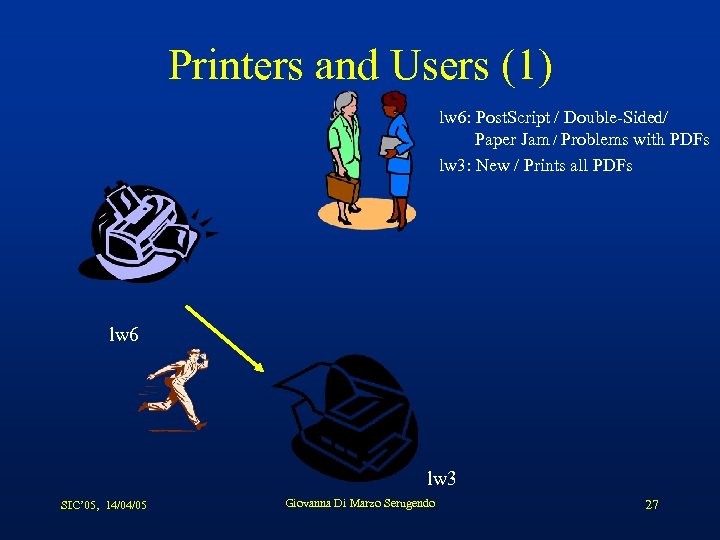
Printers and Users (1) lw 6: Post. Script / Double-Sided/ Paper Jam / Problems with PDFs lw 3: New / Prints all PDFs lw 6 lw 3 SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 27
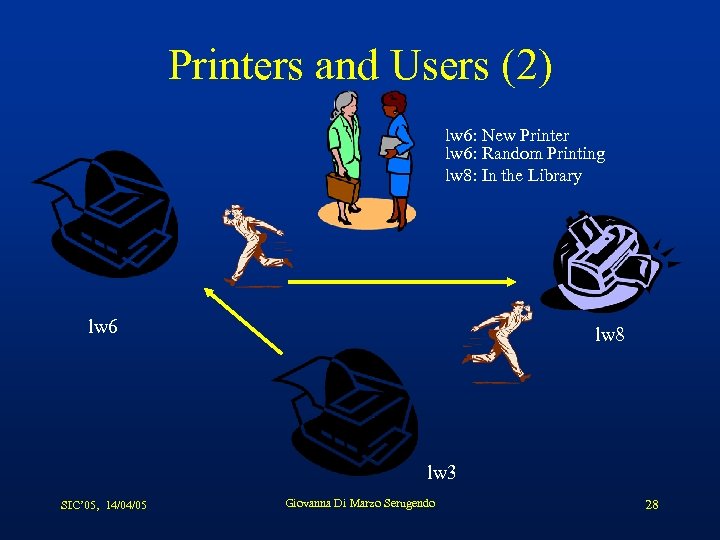
Printers and Users (2) lw 6: New Printer lw 6: Random Printing lw 8: In the Library lw 6 lw 8 lw 3 SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 28
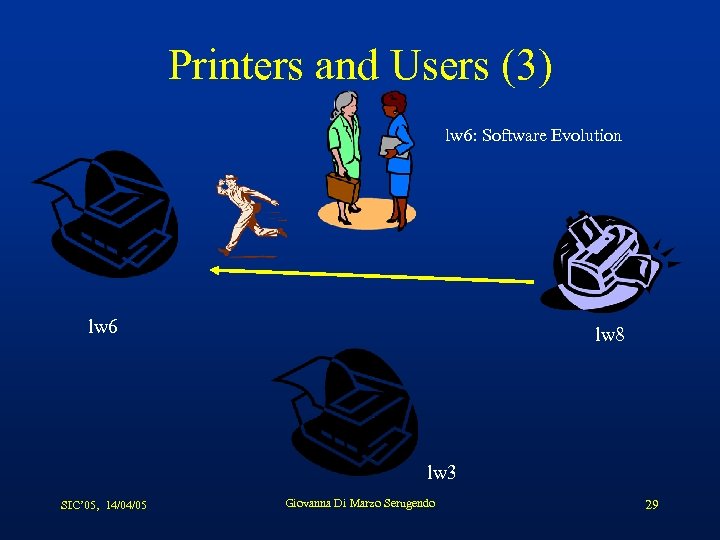
Printers and Users (3) lw 6: Software Evolution lw 6 lw 8 lw 3 SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 29

Conclusion • SCC – Simple specifications of behavior – Implementation through a middleware infrastructure • Trust-based model – Defined and implemented as part of EU Funded project – SECURE • Future work – Own specification language (pre- post- conditions, parameters mapping) – Large scale examples – “Google” services SIC’ 05, 14/04/05 Giovanna Di Marzo Serugendo 30
763c153ac6b162df8dc11686ee365539.ppt