8be7a3ef192ec92c21c6dac003717e12.ppt
- Количество слайдов: 14
“A Service-enabled Access Control Model for Distributed Data” Mark Turner, Philip Woodall Pennine Forum - 16 th September 2004

Overview § The IBHIS Project § Data as a Service § Access Control § Introduction § Domain/Technical Challenges § Service-enabled Data Access Control Model § Reference/Architectural Models § Implementation § Future Work § Inference § Conclusions IBHIS - 2 -
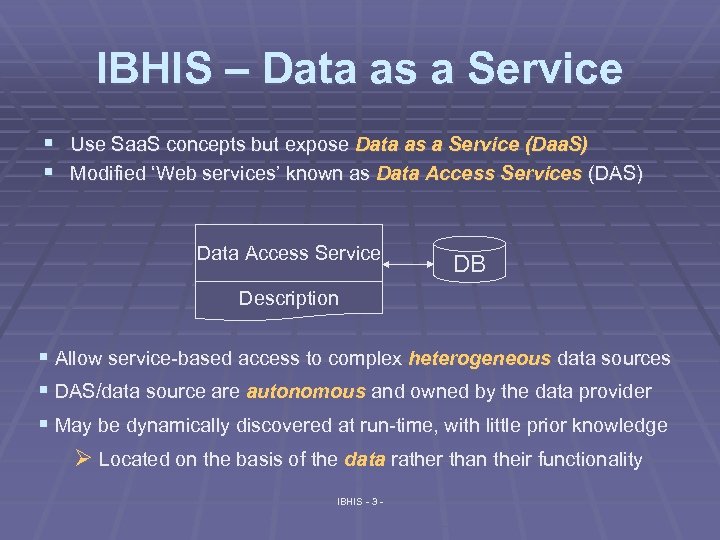
IBHIS – Data as a Service § Use Saa. S concepts but expose Data as a Service (Daa. S) § Modified ‘Web services’ known as Data Access Services (DAS) Data Access Service DB Description § Allow service-based access to complex heterogeneous data sources § DAS/data source are autonomous and owned by the data provider § May be dynamically discovered at run-time, with little prior knowledge Ø Located on the basis of the data rather than their functionality IBHIS - 3 -
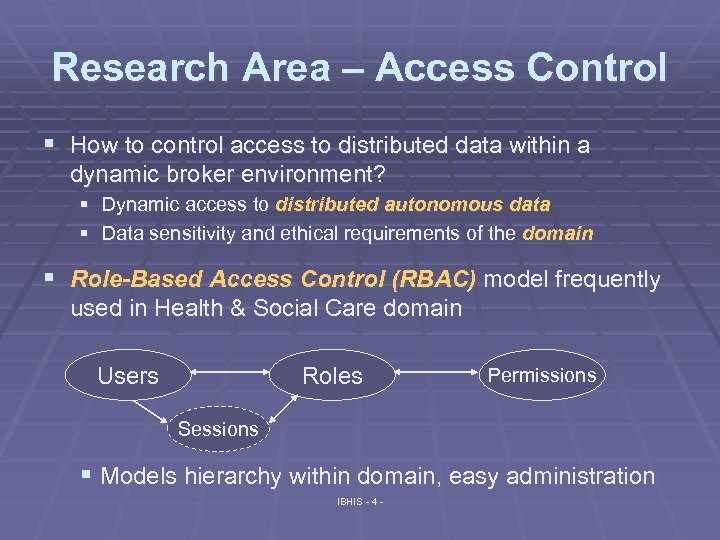
Research Area – Access Control § How to control access to distributed data within a dynamic broker environment? § Dynamic access to distributed autonomous data § Data sensitivity and ethical requirements of the domain § Role-Based Access Control (RBAC) model frequently used in Health & Social Care domain Users Roles Permissions Sessions § Models hierarchy within domain, easy administration IBHIS - 4 -

Domain Challenges § RBAC has limitations for the healthcare domain § § § Access to data in emergency situations Fine-grained, content-based rules Access depends upon individual identities and teams Contextual and environmental constraints Transfer of authority by mandate § A number of these issues have been solved § But not in any one access control model § Solution: Create new model by integrating features from existing models IBHIS - 5 -
Service-enabled Data Access Control § A new access control model to meet our requirements : § S-DAC (Service-enabled Data Access Control) § Integrates important features from existing models: § Role-based Access Control [Ferraiolo et al. , 2001] § NIST Standard – Activation, Dynamic Separation of Duties § Team-based access control [Georgiadis et al. , 2001] § Teams of users § Tees Confidentiality Model [Longstaff et al. , 2003] § Emergency overrides § OASIS [Bacon & Moody, 2002] § Appointment paradigm IBHIS - 6 -
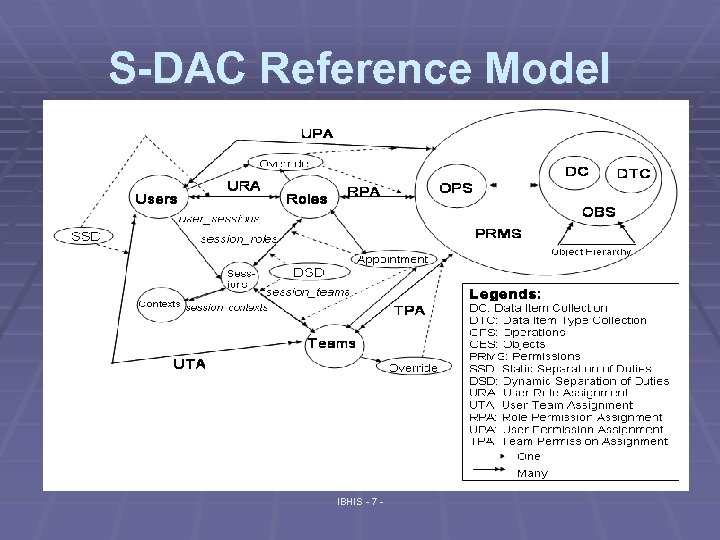
S-DAC Reference Model IBHIS - 7 -

Technical Challenges § Autonomy § Each data source will have individual access control concepts, and subjects (Roles, Teams) 1. Requires a Mapping between global and local concepts § Dynamic, run-time enforcement § Data access policies are unknown at design time § Data Access Services § Service Descriptions must allow for discovery of DAS policies § Existing technologies are lacking § Service Description – WSDL § Partial authorisations of queries, Attribute/content level IBHIS - 8 -
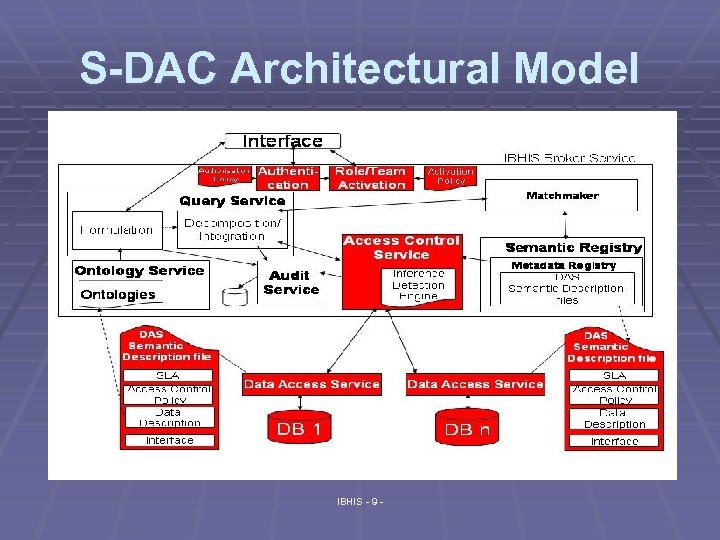
S-DAC Architectural Model IBHIS - 9 -

Future Work § Investigation into general applicability of model § Criminology § Administrative interface § Evaluation § Review against Domain and Technical requirements § Evaluation by experts in Health domain § Complexity of administration § Evaluate prototype implementation [Kitchenham et al. , 2003] § Inference… IBHIS - 10 -
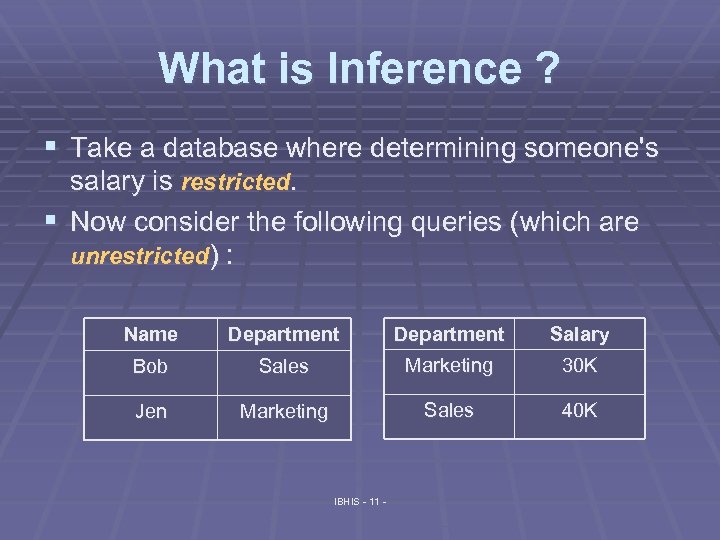
What is Inference ? § Take a database where determining someone's salary is restricted. § Now consider the following queries (which are unrestricted) : Name Department Salary Bob Sales Marketing 30 K Jen Marketing Sales 40 K IBHIS - 11 -

Research § Papers considered the inference problem in single multilevel databases. § Web-based inference has received little attention. § Integration of data from heterogeneous sources § Dynamic integration - unknown schemas § Autonomous data sources § Possible to use IBHIS as a platform for developing an inference detection system? § Links with access control models IBHIS - 12 -

Conclusion § IBHIS Access Control Model – S-DAC § Roles, Teams, Identities, Contexts, Emergency overrides § Transfer of Authority § Successfully implemented as part of IBHIS prototype § § § Web Services technologies Dynamic authorisation of content of SOAP documents Policies built using existing XML languages, with extensions § Inference § Dynamic broker environment, heterogeneous distributed sources IBHIS - 13 -

References ► ► ► ► ► Bacon, J. and Moody, K. , “Toward open, secure, widely distributed services”, CACM, 45(6), June 2002, pp. 59 -64 Georgiadis C. , Mavridis I. , Pangalos G. and Thomas, R. , “Flexible Team-based Access Control Using Contexts”, in Proceedings of the 6 th ACM Symposium on Access Control Models and Technologies (SACMAT 2001), ACM SIGSAC, Chantilly, VA, U. S. A, May 2001 D F Ferraiolo, R Sandhu, S Gavrila, D R Kuhn, R Chandramouli (2001) “Proposed NIST Standard for Role-Based Access Control”, ACM TISSEC, Vol. 4, No 3. Kitchenham, B. , Linkman, S. , and Linkman, S. , ‘Evaluating Novel Software Engineering Tools’, In Proceedings of EASE 2003, Keele University, 8 th-10 th April 2003 Kudo, M. , and Hada, S. , "Access Control Model with Provisional Actions", IEICE Trans. Fundamentals, Vol. E 84 -A, 2001 Longstaff, J. J, Lockyer, M. A. , and Nicholas, J. , “The Tees Confidentiality Model: an authorisation model for identities and roles”, ACM SACMAT 2003, Como, Italy Turner et al. , “Using Web Services to create an Information Broker”, to appear in Proceedings of ICSE 2004, IEEE Computer Society Press UK NHS Patient Confidentiality process; Details: http: //www. nhsia. nhs. uk/confidentiality/pages/consultation/ XACML Profile for Role-based Access Control (RBAC); Details: http: //docs. oasisopen. org/xacml/cd-xacml-rbac-profile-01. pdf IBHIS - 14 -
8be7a3ef192ec92c21c6dac003717e12.ppt