1976067f63877be9ca68c831d06543ae.ppt
- Количество слайдов: 28

A Secure Communication Protocol For Wireless Biosensor Networks Masters Thesis by Krishna Kumar Venkatasubramanian Committee: Dr. Sandeep Gupta Dr. Rida Bazzi Dr. Hessam Sarjoughian 1

Overview n n n n Introduction Problem Statement System Model Proposed Protocols Security Analysis Implementation Conclusions & Future Work 2
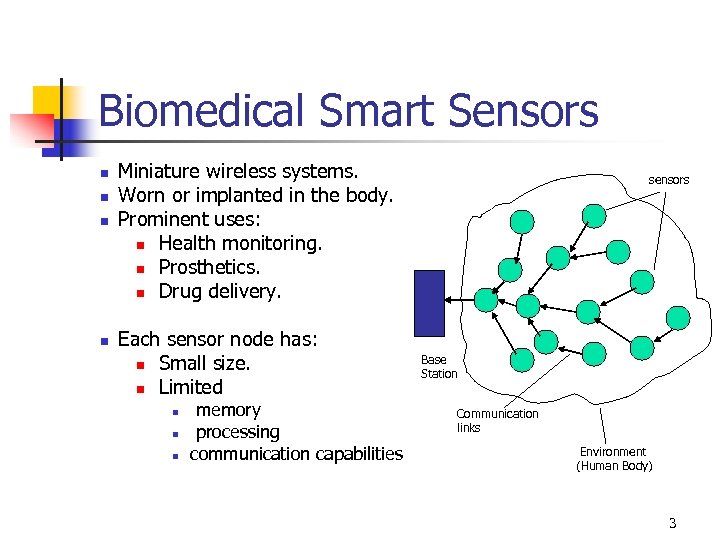
Biomedical Smart Sensors n n Miniature wireless systems. Worn or implanted in the body. Prominent uses: n Health monitoring. n Prosthetics. n Drug delivery. Each sensor node has: n Small size. n Limited n n n memory processing communication capabilities sensors Base Station Communication links Environment (Human Body) 3

Motivation for biosensor security n Collect sensitive medical data. n Legal requirement (HIPAA). n Attacks by malicious entity: n Generate fake emergency warnings. n Prevent legitimate warnings from being reported. n Battery power depletion. n Excessive heating in the tissue. 4

Problem Statement n Direct communication to the BS can be prohibitive. n To minimize communication costs, biosensors can be organized into specific topologies. n Cluster topology is one of the energy-efficient communication topologies for sensor networks [HCB 00]. n Traditional cluster formation protocol is not secure. n We want to develop protocols which allow for secure cluster formation in biosensor networks. 5
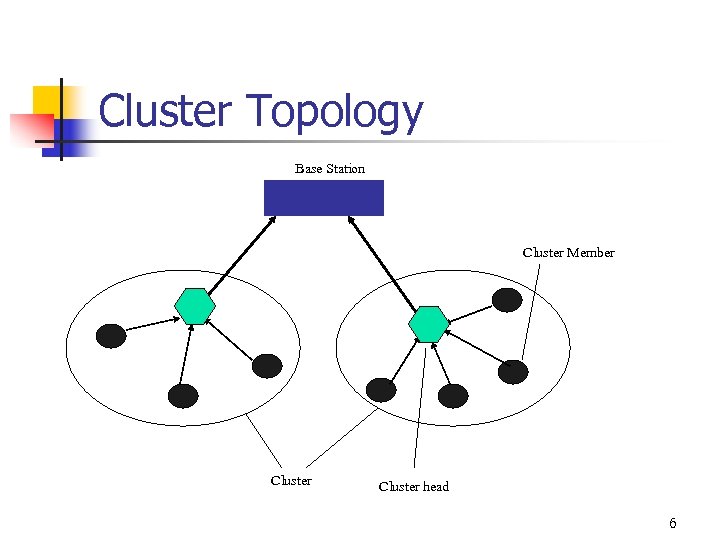
Cluster Topology Base Station Cluster Member Cluster head 6
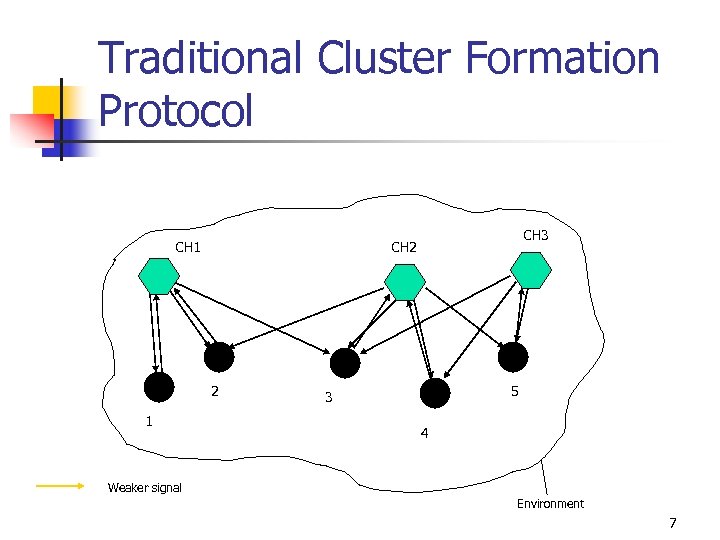
Traditional Cluster Formation Protocol CH 1 2 1 CH 3 CH 2 5 3 4 Weaker signal Environment 7
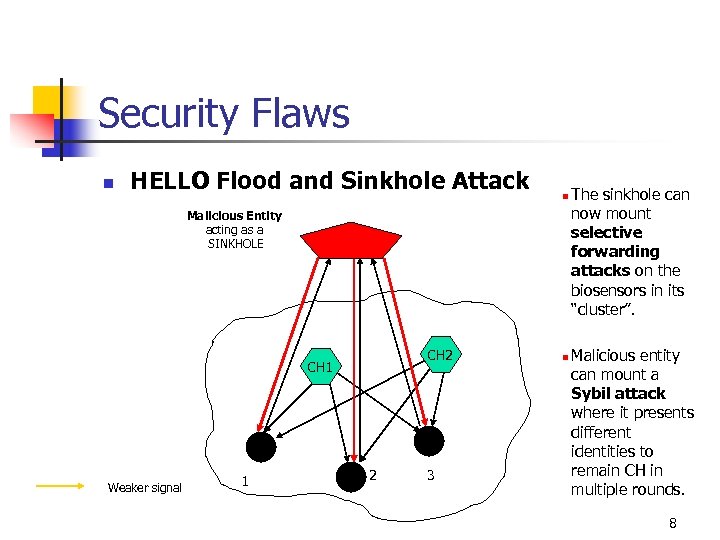
Security Flaws n HELLO Flood and Sinkhole Attack n Malicious Entity acting as a SINKHOLE CH 2 CH 1 Weaker signal 1 2 3 n The sinkhole can now mount selective forwarding attacks on the biosensors in its “cluster”. Malicious entity can mount a Sybil attack where it presents different identities to remain CH in multiple rounds. 8
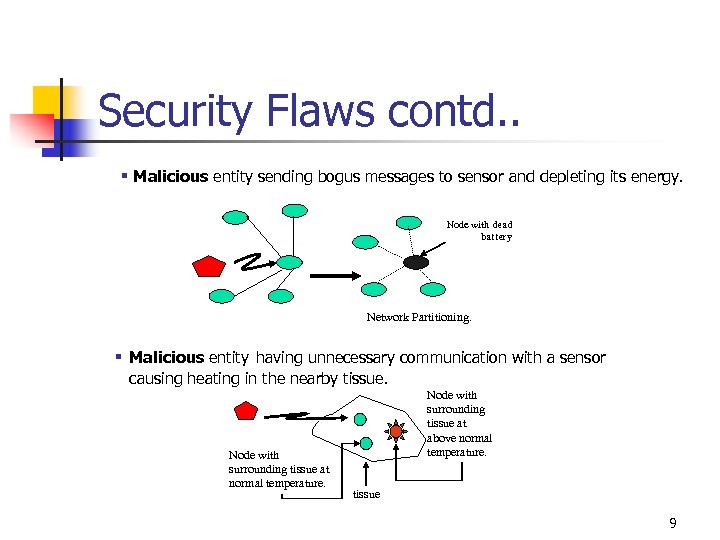
Security Flaws contd. . § Malicious entity sending bogus messages to sensor and depleting its energy. Node with dead battery Network Partitioning. § Malicious entity having unnecessary communication with a sensor causing heating in the nearby tissue. Node with surrounding tissue at normal temperature. Node with surrounding tissue at above normal temperature. tissue 9
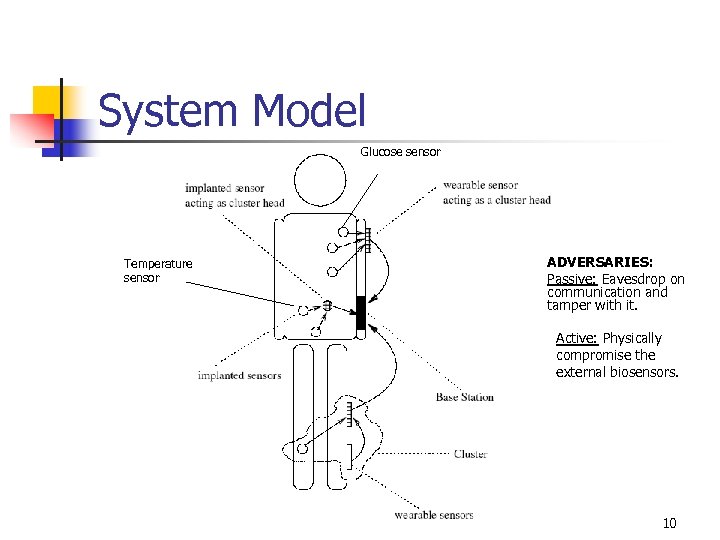
System Model Glucose sensor Temperature sensor ADVERSARIES: Passive: Eavesdrop on communication and tamper with it. Active: Physically compromise the external biosensors. 10

Trust Assumptions n n n The wireless communication is broadcast in nature and not trusted. The biosensors do not trust each other. Base Station is assumed not to be compromised. 11
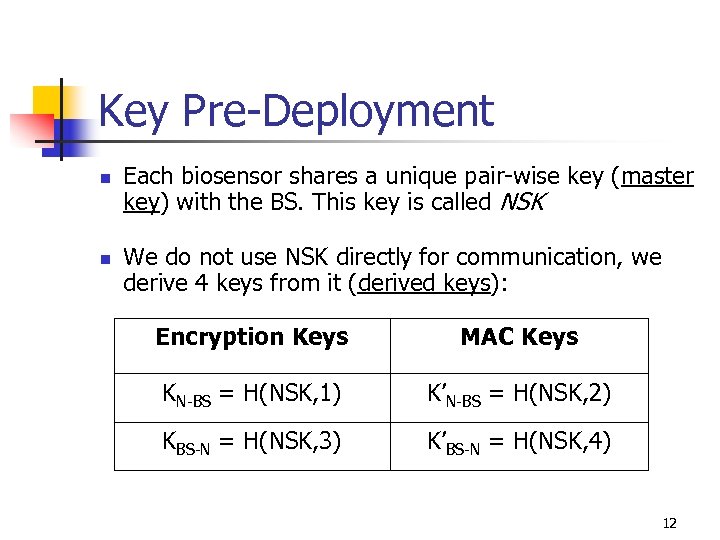
Key Pre-Deployment n n Each biosensor shares a unique pair-wise key (master key) with the BS. This key is called NSK We do not use NSK directly for communication, we derive 4 keys from it (derived keys): Encryption Keys MAC Keys KN-BS = H(NSK, 1) K’N-BS = H(NSK, 2) KBS-N = H(NSK, 3) K’BS-N = H(NSK, 4) 12
Biometrics n Physiological parameters like heart rate and body glucose. n n Used for securing/authenticating communication between two biosensors which do not share any secret. Usage Assumptions: n Only biosensors in and on the body can measure biometrics. n There is a specific pre-defined biometric that all biosensors can measure. 13
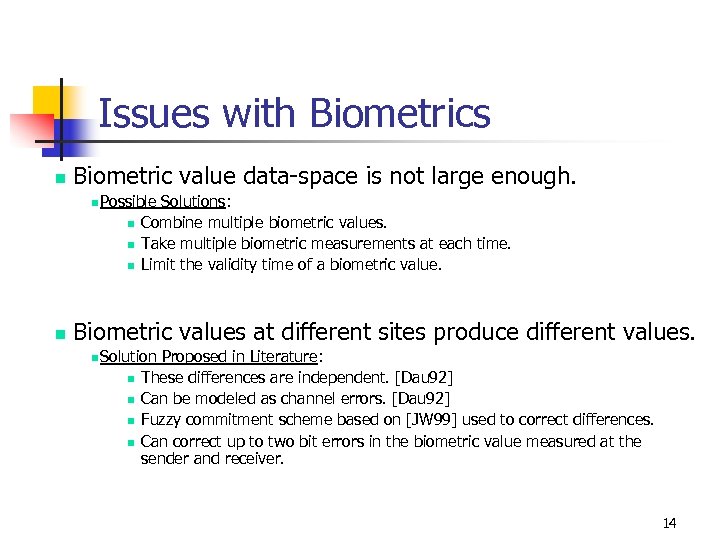
Issues with Biometrics n Biometric value data-space is not large enough. n Possible n n Solutions: Combine multiple biometric values. Take multiple biometric measurements at each time. Limit the validity time of a biometric value. Biometric values at different sites produce different values. n Solution n n Proposed in Literature: These differences are independent. [Dau 92] Can be modeled as channel errors. [Dau 92] Fuzzy commitment scheme based on [JW 99] used to correct differences. Can correct up to two bit errors in the biometric value measured at the sender and receiver. 14
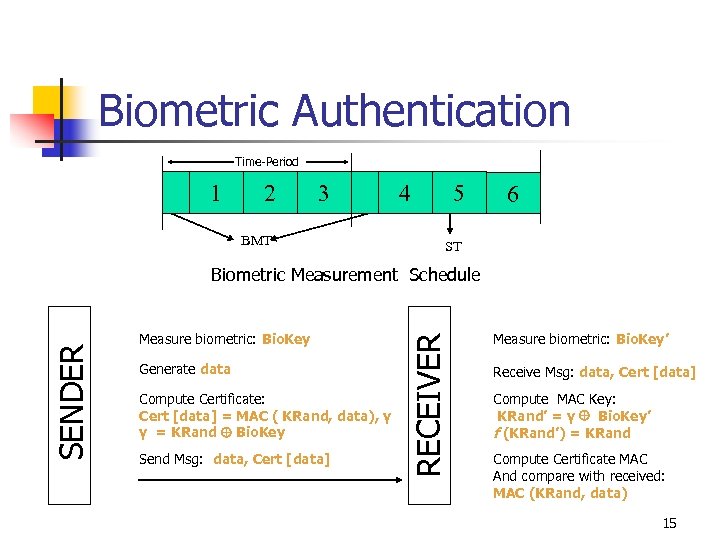
Biometric Authentication Time-Period 1 2 3 BMT 4 5 6 ST Measure biometric: Bio. Key Generate data Compute Certificate: Cert [data] = MAC ( KRand, data), γ γ = KRand Bio. Key Send Msg: data, Cert [data] RECEIVER SENDER Biometric Measurement Schedule Measure biometric: Bio. Key’ Receive Msg: data, Cert [data] Compute MAC Key: KRand’ = γ Bio. Key’ f (KRand’) = KRand Compute Certificate MAC And compare with received: MAC (KRand, data) 15
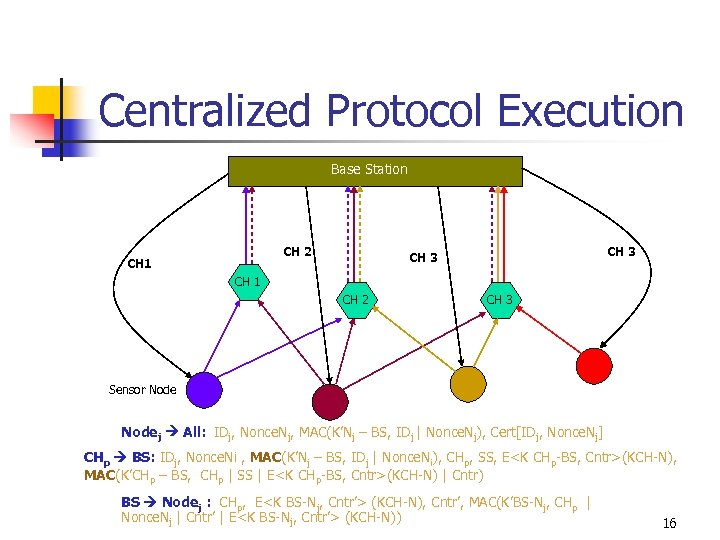
Centralized Protocol Execution Base Station CH 2 CH 1 CH 3 CH 1 CH 2 CH 3 Sensor Nodej All: IDj, Nonce. Nj, MAC(K’Nj – BS, IDj | Nonce. Nj), Cert[IDj, Nonce. Nj] CHp BS: IDj, Nonce. Ni , MAC(K’Nj – BS, IDj | Nonce. Ni), CHp, SS, E<K CHp-BS, Cntr>(KCH-N), MAC(K’CHp – BS, CHp | SS | E<K CHp-BS, Cntr>(KCH-N) | Cntr) BS Nodej : CHp, E<K BS-Nj, Cntr’> (KCH-N), Cntr’, MAC(K’BS-Nj, CHp | Nonce. Nj | Cntr’ | E<K BS-Nj, Cntr’> (KCH-N)) 16
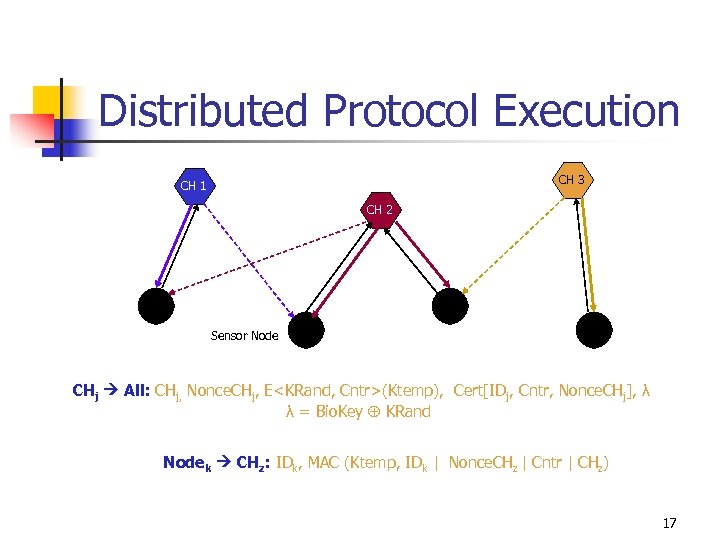
Distributed Protocol Execution CH 3 CH 1 CH 2 Sensor Node CHj All: CHj, Nonce. CHj, E<KRand, Cntr>(Ktemp), Cert[IDj, Cntr, Nonce. CHj], λ λ = Bio. Key KRand Nodek CHz: IDk, MAC (Ktemp, IDk | Nonce. CHz | Cntr | CHz) 17

Extensions n Distribute keys based on attributes. n Allows efficient data communication. n The BS distributes the keys. n For centralized ABK, sent during cluster formation. n For distributed separate step needed. 18

Security Analysis (Passive Adversary) n Hello Flood and Sinkhole Attack Centralized: n n Malicious entity does not have appropriate keys to pose as legitimate CH. Distributed: n Malicious entity cannot compute biometric certificate. 19
Security Analysis (Passive Adversary) n Sybil Attack n n No entity can become part of network without having appropriate keys. Identity Spoofing n n n Cannot pose as BS, no pair-wise (derived) keys. Cannot pose as CH, no keys to authenticate data to BS. Cannot pose as sensor node, cannot measure biometric to fool CH. 20
Security Analysis (Active Adversary) n CH compromise n n n Centralized: Security policy at BS to limit number of sensor nodes in a cluster. Distributed: Need intruder monitoring scheme. Sensor Node compromise n Intruder monitoring scheme needed for both protocols. 21

Implementation n We have implemented the two cluster formation protocols and their extensions. n The implementation was done on the Mica 2 sensor motes. n We used Tiny. OS sensor operating system for writing our programs. n For security primitives Tiny. Sec used. 22

Implementation contd. . n Encryption – Skip. Jack n Message Authentication Code – CBC-MAC n We had 4 sensor nodes 3 CH and 1 BS in our implementation. n We simulated two main attacks on our implementation, both of which failed: n n HELLO Flood attack. Identity spoofing of sensor node to infiltrate the network. 23
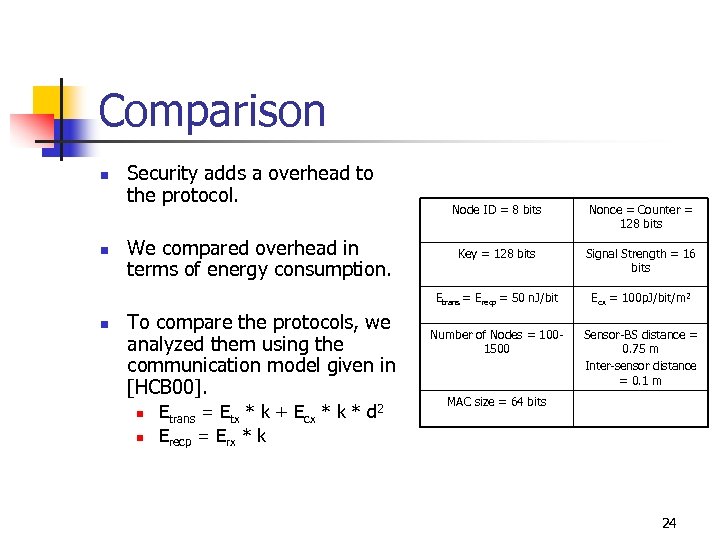
Comparison n Security adds a overhead to the protocol. n We compared overhead in terms of energy consumption. To compare the protocols, we analyzed them using the communication model given in [HCB 00]. n n Etrans = Etx * k + Ecx * k * d 2 Erecp = Erx * k Nonce = Counter = 128 bits Key = 128 bits Signal Strength = 16 bits Etrans = Erecp = 50 n. J/bit n Node ID = 8 bits Ecx = 100 p. J/bit/m 2 Number of Nodes = 1001500 Sensor-BS distance = 0. 75 m Inter-sensor distance = 0. 1 m MAC size = 64 bits 24
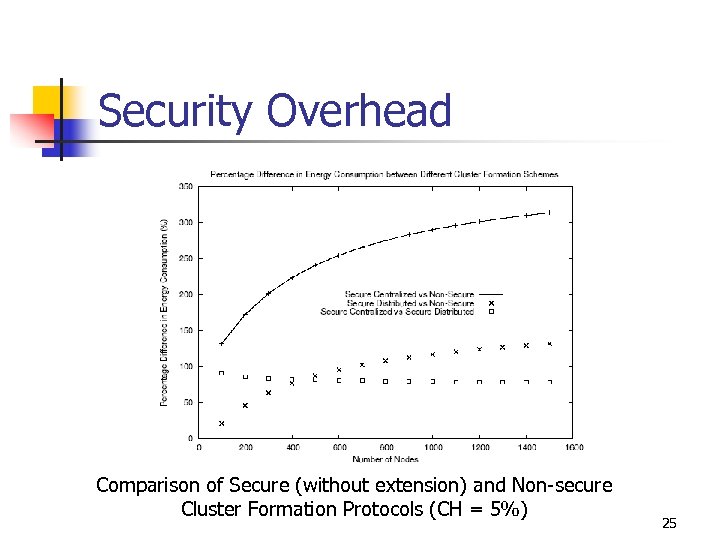
Security Overhead Comparison of Secure (without extension) and Non-secure Cluster Formation Protocols (CH = 5%) 25
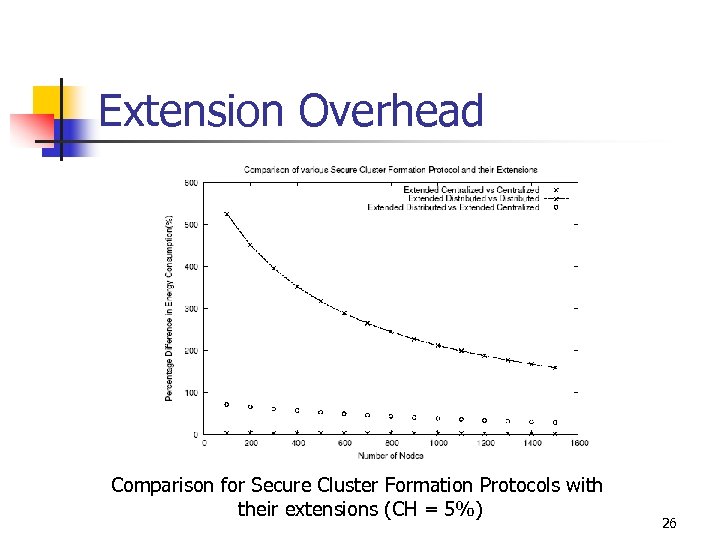
Extension Overhead Comparison for Secure Cluster Formation Protocols with their extensions (CH = 5%) 26
Conclusions & Future Work n Protocols developed successfully prevent many of the potent attacks on the traditional cluster formation protocol. n Biometric based authentication used for ensuring authentication without previous key exchange. n Biometrics not traditionally random and schemes are needed to randomize them. n Better error correction schemes are needed which can correct larger differences in measured biometrics. 27
![Reference [JW 99] Ari Juels and Martin Wattenberg. “A fuzzy commitment scheme”. 1999. [Dau Reference [JW 99] Ari Juels and Martin Wattenberg. “A fuzzy commitment scheme”. 1999. [Dau](https://present5.com/presentation/1976067f63877be9ca68c831d06543ae/image-28.jpg)
Reference [JW 99] Ari Juels and Martin Wattenberg. “A fuzzy commitment scheme”. 1999. [Dau 92] J. Daugman, “High Confidence personal identification by rapid video analysis of iris texture”, IEEE International Carnahan Conference on Security Technology, pp 50 -60, 1992. [LGW 01] L. Schwiebert, S. K. S. Gupta, J. Weinmann et al. , “Research Challenges in Wireless Networks of Biomedical Sensors”, The Seventh Annual International Conference on Mobile Computing and Networking, pp 151 -165, Rome Italy, July 2001. [HCB 00] W. Rabiner Heinzelman, A. Chandrakasan, and H. Balakrishnan, “Energy-Efficient Communication Protocol for Wireless Microsensor Networks”, Proceedings of the 33 rd International Conference on System Sciences (HICSS '00), January 2000. 28
1976067f63877be9ca68c831d06543ae.ppt