1b759809d128031392074b5fce26649b.ppt
- Количество слайдов: 26
 A sceptical look at copyright and DRM Dr. Ian Brown FRSA MRIIA University College London
A sceptical look at copyright and DRM Dr. Ian Brown FRSA MRIIA University College London
 Overview Where did copyright go wrong? n “Trusted” computing n The technical problems with DRM n Legislative “fixes” n Goodbye to fair use n
Overview Where did copyright go wrong? n “Trusted” computing n The technical problems with DRM n Legislative “fixes” n Goodbye to fair use n
 Origins n n Statute of Anne, 1710: “for the encouragement of learned men to compose and write useful books ” US Constitution, 1789: “To promote the progress of science and useful arts” Droit d’auteur: “a work of creation is intimately linked with its creator. The work cannot be separated from its author, like a child from his father. ” Stationer’s Guild, 1557: no “seditious and heretical books, rhymes and treatises”
Origins n n Statute of Anne, 1710: “for the encouragement of learned men to compose and write useful books ” US Constitution, 1789: “To promote the progress of science and useful arts” Droit d’auteur: “a work of creation is intimately linked with its creator. The work cannot be separated from its author, like a child from his father. ” Stationer’s Guild, 1557: no “seditious and heretical books, rhymes and treatises”
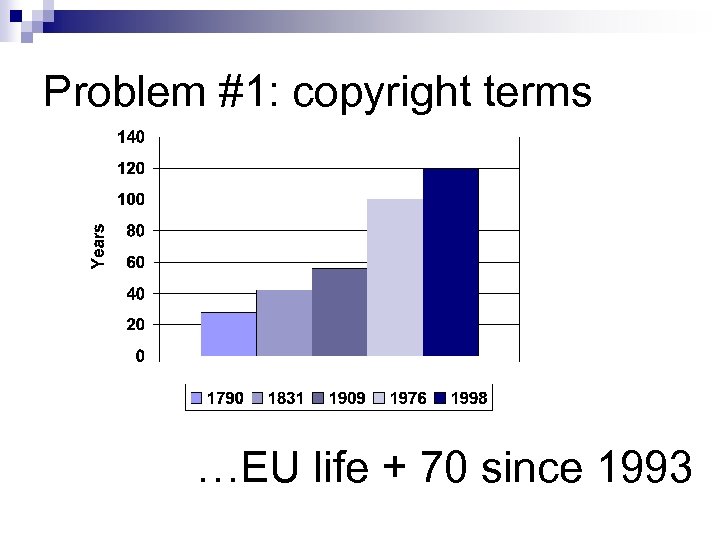 Problem #1: copyright terms …EU life + 70 since 1993
Problem #1: copyright terms …EU life + 70 since 1993
 The drivers behind copyright • Mickey debuted in 1928, and copyright would have expired 2003 -2005 • US Congress passed Copyright Term Extension Act in 1998 postponing until 2023: http: //www. eagleforum. org/column/1998/nov 98/98 -11 -25. html • Peter Pan has perpetual rights in UK
The drivers behind copyright • Mickey debuted in 1928, and copyright would have expired 2003 -2005 • US Congress passed Copyright Term Extension Act in 1998 postponing until 2023: http: //www. eagleforum. org/column/1998/nov 98/98 -11 -25. html • Peter Pan has perpetual rights in UK
 Problem #2: Internet hysteria n n n “the VCR is to the American film producer and the American public as the Boston strangler is to the woman home alone. ” –Jack Valenti Mid-90 s reaction of copyright industries: technical and legal “The piracy of software is responsible for annual global revenue losses of more than $4 billion. The piracy of computer games cheats the gaming industry out of more than a billion dollars a year. And the piracy of songs has left the music industry fighting for its digital life, thanks to a pillaging that reached levels of more than a billion songs a month. ” –Peter Chernin
Problem #2: Internet hysteria n n n “the VCR is to the American film producer and the American public as the Boston strangler is to the woman home alone. ” –Jack Valenti Mid-90 s reaction of copyright industries: technical and legal “The piracy of software is responsible for annual global revenue losses of more than $4 billion. The piracy of computer games cheats the gaming industry out of more than a billion dollars a year. And the piracy of songs has left the music industry fighting for its digital life, thanks to a pillaging that reached levels of more than a billion songs a month. ” –Peter Chernin
 Digital Rights Management Wide range of technologies that allow publishers to control the use of digital media n Restricts reproduction, but also viewing, printing, clipboard functions etc n Present in Windows Media Player, Adobe e-books, Real. Player etc n
Digital Rights Management Wide range of technologies that allow publishers to control the use of digital media n Restricts reproduction, but also viewing, printing, clipboard functions etc n Present in Windows Media Player, Adobe e-books, Real. Player etc n
 DRM basic technology Media data is encrypted and only accessible by licensed players that control usage n Licensed users given keys to decrypt tied to player n Media can be watermarked with usage instructions and/or user information n
DRM basic technology Media data is encrypted and only accessible by licensed players that control usage n Licensed users given keys to decrypt tied to player n Media can be watermarked with usage instructions and/or user information n
 DRM a hard problem n n Media data has to be decrypted at some point to be useful Watermarks can be removed, especially with many original files to compare and players to test with Bits are bits, and PCs are general purpose computers Legacy equipment won’t disappear for many years
DRM a hard problem n n Media data has to be decrypted at some point to be useful Watermarks can be removed, especially with many original files to compare and players to test with Bits are bits, and PCs are general purpose computers Legacy equipment won’t disappear for many years
 Previous DRM “solutions” Secure Digital Music Initiative n CD protection n CSS n
Previous DRM “solutions” Secure Digital Music Initiative n CD protection n CSS n
 New “trusted” architectures Intel/IBM/HP/etc in TCPA/TCG: machine state auth to 3 rd parties; encrypted data only accessible in identical state; encrypted device links n Microsoft Palladium/NGSCB: “curtained” apps, secure drivers, DRM everywhere n Migrating to PDAs/mobiles/watches n
New “trusted” architectures Intel/IBM/HP/etc in TCPA/TCG: machine state auth to 3 rd parties; encrypted data only accessible in identical state; encrypted device links n Microsoft Palladium/NGSCB: “curtained” apps, secure drivers, DRM everywhere n Migrating to PDAs/mobiles/watches n
 Fundamental technical problems The analogue “hole” – watermarking n Break Once Play Anywhere n File-sharing won’t stop n
Fundamental technical problems The analogue “hole” – watermarking n Break Once Play Anywhere n File-sharing won’t stop n
 Legislative “fixes” WIPO 1996 treaties n Digital Millennium Copyright Act 1998 n European Union Copyright Directive 2001 n WTO TRIPS 1994 can lead to trade sanctions n
Legislative “fixes” WIPO 1996 treaties n Digital Millennium Copyright Act 1998 n European Union Copyright Directive 2001 n WTO TRIPS 1994 can lead to trade sanctions n
 EU Copyright Directive 2001/29/EC of the European Parliament and of the Council of 22 May 2001 on the Harmonisation of Certain Aspects of Copyright and Related Rights in the Information Society n Provides for rights over reproduction, communication to the public and distribution (Articles 2— 4) n
EU Copyright Directive 2001/29/EC of the European Parliament and of the Council of 22 May 2001 on the Harmonisation of Certain Aspects of Copyright and Related Rights in the Information Society n Provides for rights over reproduction, communication to the public and distribution (Articles 2— 4) n
 EUCD Article 6 n n n 6. 1: “Member States shall provide adequate legal protection against the circumvention of any effective technological measures” 6. 2: bans “manufacture, import, distribution, sale, rental, advertisement for sale or rental, or possession for commercial purposes of devices, products or components or the provision of services” Purpose is irrelevant Finland, France, UK 2 years prison; Portugal 3 years; France 150, 000€ fine Only Germany, Denmark, Finland UK have research exemptions
EUCD Article 6 n n n 6. 1: “Member States shall provide adequate legal protection against the circumvention of any effective technological measures” 6. 2: bans “manufacture, import, distribution, sale, rental, advertisement for sale or rental, or possession for commercial purposes of devices, products or components or the provision of services” Purpose is irrelevant Finland, France, UK 2 years prison; Portugal 3 years; France 150, 000€ fine Only Germany, Denmark, Finland UK have research exemptions
 EUCD Article 7 n 7. 1: “Member States shall provide for adequate legal protection against any person knowingly performing without authority… the removal or alteration of any electronic rights-management information”
EUCD Article 7 n 7. 1: “Member States shall provide for adequate legal protection against any person knowingly performing without authority… the removal or alteration of any electronic rights-management information”
 Existing problems “I think a lot of people didn't realize that it would have this potential chilling effect on vulnerability research. ” –Richard Clarke n Use to enforce accessory controls (Lexmark, Aibo, Playstation) n Rewriting the copyright bargain n
Existing problems “I think a lot of people didn't realize that it would have this potential chilling effect on vulnerability research. ” –Richard Clarke n Use to enforce accessory controls (Lexmark, Aibo, Playstation) n Rewriting the copyright bargain n
 Potential problems Electronic book burning n Reduced software diversity – security and competition risks n Personal and national sovereignty n Privacy n
Potential problems Electronic book burning n Reduced software diversity – security and competition risks n Personal and national sovereignty n Privacy n
 Problem #3: disappearing fair use Private copy n Teaching/research n Parody n Disabled persons n
Problem #3: disappearing fair use Private copy n Teaching/research n Parody n Disabled persons n
 EUCD Article 5 n n n Long list of permissible exceptions (unlike US) 5. 1 “Temporary acts of reproduction referred to in Article 2, which are transient or incidental [and] an integral and essential part of a technological process…” 5. 2: exceptions to Art. 2 5. 3: exceptions to Art. 3 5. 4: any of the above may apply to Art. 4
EUCD Article 5 n n n Long list of permissible exceptions (unlike US) 5. 1 “Temporary acts of reproduction referred to in Article 2, which are transient or incidental [and] an integral and essential part of a technological process…” 5. 2: exceptions to Art. 2 5. 3: exceptions to Art. 3 5. 4: any of the above may apply to Art. 4
 Fair use and DRM DMCA and EUCD both ban DRM circumvention, even for fair use n EUCD requests “voluntary measures” from rightsholders n If not forthcoming, most member states allow appeal to national tribunal (except Netherlands) n
Fair use and DRM DMCA and EUCD both ban DRM circumvention, even for fair use n EUCD requests “voluntary measures” from rightsholders n If not forthcoming, most member states allow appeal to national tribunal (except Netherlands) n
 Abolishing digital fair use “On-demand services” (“members of the public may access them from a place and at a time individually chosen by them”) exempt from fair use n Could include anything accessed over Internet n Contractual access – also see UCITA n
Abolishing digital fair use “On-demand services” (“members of the public may access them from a place and at a time individually chosen by them”) exempt from fair use n Could include anything accessed over Internet n Contractual access – also see UCITA n
 Problems for free software Accessing a protected file may be circumvention (e. g. De. CSS) if not authorised by rightsholder (despite Software Directive) n Therefore free software could be classed as a circumvention device, with severe penalties n
Problems for free software Accessing a protected file may be circumvention (e. g. De. CSS) if not authorised by rightsholder (despite Software Directive) n Therefore free software could be classed as a circumvention device, with severe penalties n
 More problems Growing numbers of file formats may require reboot into Windows to access (Intel hardware prevents OS virtualisation) n Including Office 2003 and later n Society may need protection from TPMs rather than the other way around n
More problems Growing numbers of file formats may require reboot into Windows to access (Intel hardware prevents OS virtualisation) n Including Office 2003 and later n Society may need protection from TPMs rather than the other way around n
 Even worse law coming EU Directive on IPR Enforcement: abolishes right to silence in IP cases; allows injunctions against ISPs; civil litigants can freeze bank accounts and search premises n See fipr. org for analysis n
Even worse law coming EU Directive on IPR Enforcement: abolishes right to silence in IP cases; allows injunctions against ISPs; civil litigants can freeze bank accounts and search premises n See fipr. org for analysis n
 Final thoughts n n “Be very glad that your PC is insecure – it means that after you buy it, you can break into it and install whatever software you want. What YOU want, not what Sony or Warner or AOL wants. ” – John Gilmore “"If we can find some way to [stop filesharing] without destroying their machines, we'd be interested in hearing about that. If that's the only way, then I'm all for destroying their machines. ” – Senator Orrin Hatch (writer of Our Gracious Lord, Climb Inside His Loving Arms, and How His Glory Shines)
Final thoughts n n “Be very glad that your PC is insecure – it means that after you buy it, you can break into it and install whatever software you want. What YOU want, not what Sony or Warner or AOL wants. ” – John Gilmore “"If we can find some way to [stop filesharing] without destroying their machines, we'd be interested in hearing about that. If that's the only way, then I'm all for destroying their machines. ” – Senator Orrin Hatch (writer of Our Gracious Lord, Climb Inside His Loving Arms, and How His Glory Shines)


