a22cbc2248b6c71debb7174facda0483.ppt
- Количество слайдов: 38

A Scalable Secure Development Program 1 Rajiv Sharma, CSSLP Sr. Principal Program Manager, Oracle Global Product Security Front Range OWASP Conference, March 22 nd, 2012 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Agenda • • 2 Importance of Software Security What is Software Security Assurance? Oracle Software Security Assurance Cultivating Security Community in Development Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

• • 3 Importance of Software Security What is Software Security Assurance? Oracle Software Security Assurance Cultivating Security Community in Development Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

IT Security Challenges… It’s not just about malicious hackers! Complex regulatory and privacy frameworks Continued requirement to demonstrate compliance Difficulty of managing risks in global everchanging business environment Increasingly complex security requirements for networked applications and systems Need for maintaining “security in depth” Potential risks associated with insider threats 4 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
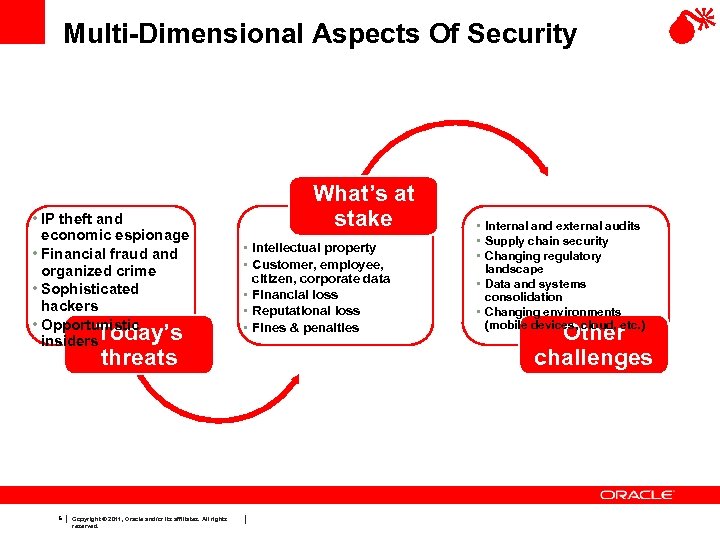
Multi-Dimensional Aspects Of Security • IP theft and economic espionage • Financial fraud and organized crime • Sophisticated hackers • Opportunistic insiders. Today’s threats 5 Copyright © 2011, Oracle and/or its affiliates. All rights reserved. What’s at stake • Intellectual property • Customer, employee, citizen, corporate data • Financial loss • Reputational loss • Fines & penalties • Internal and external audits • Supply chain security • Changing regulatory landscape • Data and systems consolidation • Changing environments (mobile devices, cloud, etc. ) Other challenges

Security In Depth Considerations • How degraded is your overall security posture when individual security mechanisms fail, are compromised or circumvented? • How degraded is your overall security posture when system environment and use cases change? 6 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Security In Depth Considerations üHow effective are your security controls? üHave you been able to set proper security controls on each layer of your IT infrastructure to ensure a security in depth posture? üHow many of these IT security controls are softwareenforced? Have they been turned ON? üWill these security features function as you expect? üIs your software free of security defects? 7 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
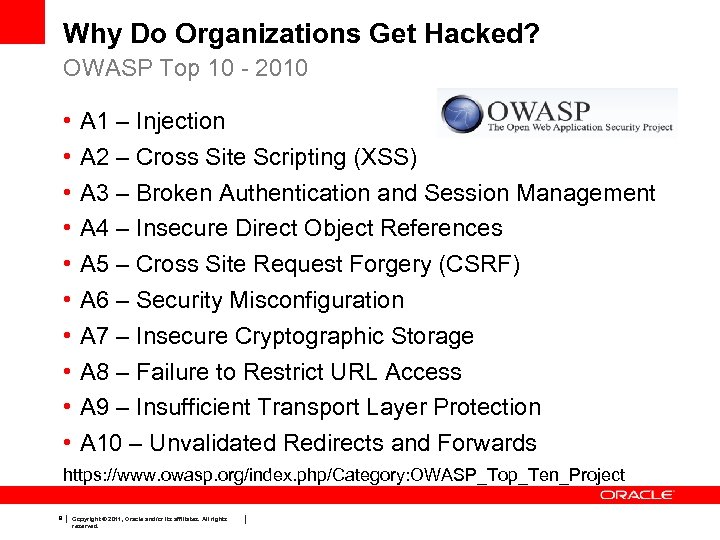
Why Do Organizations Get Hacked? OWASP Top 10 - 2010 • • • A 1 – Injection A 2 – Cross Site Scripting (XSS) A 3 – Broken Authentication and Session Management A 4 – Insecure Direct Object References A 5 – Cross Site Request Forgery (CSRF) A 6 – Security Misconfiguration A 7 – Insecure Cryptographic Storage A 8 – Failure to Restrict URL Access A 9 – Insufficient Transport Layer Protection A 10 – Unvalidated Redirects and Forwards https: //www. owasp. org/index. php/Category: OWASP_Top_Ten_Project 8 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Why Do Organizations Get Hacked? Keeping up with security patches is good security practice • Would you knowingly run on a vulnerable system for an extended period of time? – The publication of security fixes by vendors often result in making potentially malicious hackers aware of the flaw: • Reverse-engineering of the fixes for the purpose of developing malware or exploits • Inclusion of the exploit in hacking toolsets (e. g. , Metasploit) – Apply security patches in a timely fashion – Keeping up with newer releases is also good security practice! • Newer releases may include additional fixes, which cannot always be backported to previous releases • And of course… Follow your vendor’s deployment recommendations 9 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

• • 10 Importance of Software Security What is Software Security Assurance? Oracle Software Security Assurance Cultivating Security Community in Development Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Software Security Assurance Definition The process of ensuring that software is designed to operate at a level of security that is consistent with the potential harm that could result from the loss, inaccuracy, alteration, unavailability, or misuse of the data and resources that it uses, controls, and protects. http: //en. wikipedia. org/wiki/Software_Security_Assurance 11 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Importance of Software Security Assurance Customers must be assured that: 1. The software they purchase from their vendors is designed and developed securely, e. g. : • • Does the software do what it is designed to do and nothing more? How resilient to threats is software? 2. The vendors have effective procedures to deal with security vulnerabilities and provide ongoing security assurance in their products. 12 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

What Is Software Security Assurance? Implications for software 1. Software must have been designed securely – – Security must be “built in, not bolted on” Software must provide adequate security controls (e. g. reflecting the data it will store, the threat environment in which it will operate, etc. ) 2. Software must have been securely developed – – Secure design and coding principles must have been followed Software must have been developed in a secure environment under a securely designed development process 3. Software must provide reasonably secure posture by default – 13 Hardening instructions must be documented and available Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

What Is Software Security Assurance? Implications for software vendor/developer • Security must be embedded in the organization’s DNA • Organization must recognize that there is no “magic bullet” but that security is an ongoing commitment 14 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

• • 15 Importance of Software Security What is Software Security Assurance? Oracle Software Security Assurance Cultivating Security Community in Development Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Oracle Software Security Assurance Definition Oracle Software Security Assurance (OSSA) encompasses all the constantly-evolving processes, procedures, and technologies implemented by Oracle to ensure that Oracle’s products are meeting our customers’ security requirements, while providing for the most cost-effective ownership experience. 16 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
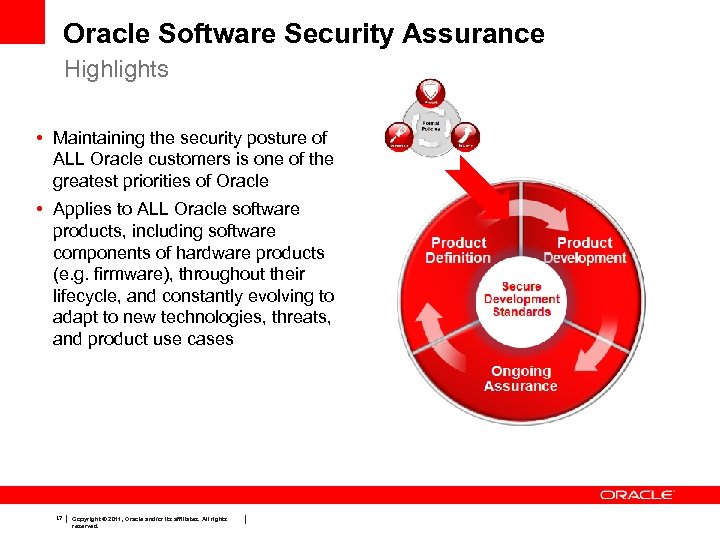
Oracle Software Security Assurance Highlights • Maintaining the security posture of ALL Oracle customers is one of the greatest priorities of Oracle • Applies to ALL Oracle software products, including software components of hardware products (e. g. firmware), throughout their lifecycle, and constantly evolving to adapt to new technologies, threats, and product use cases 17 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
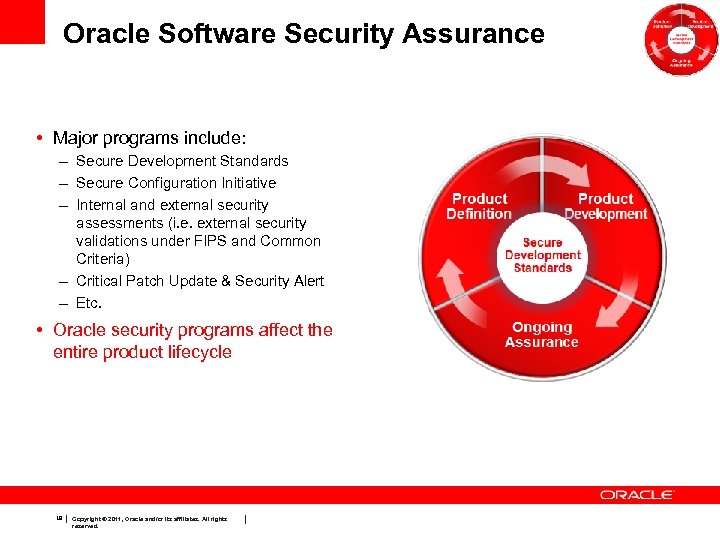
Oracle Software Security Assurance • Major programs include: – Secure Development Standards – Secure Configuration Initiative – Internal and external security assessments (i. e. external security validations under FIPS and Common Criteria) – Critical Patch Update & Security Alert – Etc. • Oracle security programs affect the entire product lifecycle 18 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
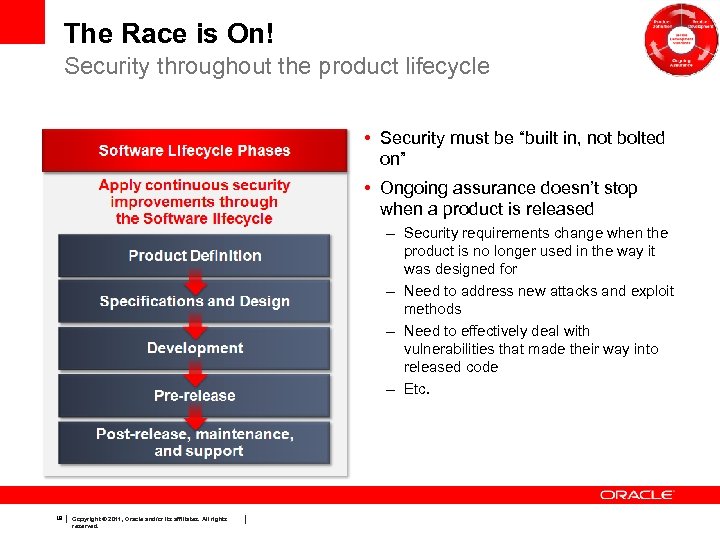
The Race is On! Security throughout the product lifecycle • Security must be “built in, not bolted on” • Ongoing assurance doesn’t stop when a product is released – Security requirements change when the product is no longer used in the way it was designed for – Need to address new attacks and exploit methods – Need to effectively deal with vulnerabilities that made their way into released code – Etc. 19 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
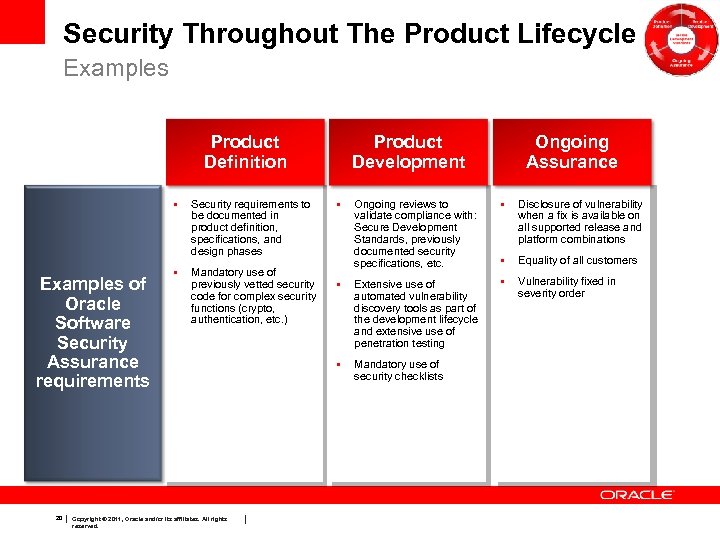
Security Throughout The Product Lifecycle Examples Product Definition • Examples of Oracle Software Security Assurance requirements 20 Security requirements to be documented in product definition, specifications, and design phases • Mandatory use of previously vetted security code for complex security functions (crypto, authentication, etc. ) Copyright © 2011, Oracle and/or its affiliates. All rights reserved. Product Development • Ongoing Assurance Ongoing reviews to validate compliance with: Secure Development Standards, previously documented security specifications, etc. • Disclosure of vulnerability when a fix is available on all supported release and platform combinations • Equality of all customers • Extensive use of automated vulnerability discovery tools as part of the development lifecycle and extensive use of penetration testing • Vulnerability fixed in severity order • Mandatory use of security checklists

Secure Development Standards • Codified security standards are at the core of Oracle Software Security Assurance • Coding guidelines – Secure coding principles – Examples of what not to do – Requirements to use previously vetted security code for complex security functions (crypto, authentication, etc. ) – Minimum secure design requirements (e. g. , weak/old crypt algorithms are banned) – Etc. • Mandatory training 21 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Product Definition • Security requirements are expressed as early as design and engineering specifications phases • Security requirements include: – Requirements born from Secure Coding Standards – Product-specific requirements (such as those resulting from new security features) • Established security criteria must be satisfied and reviewed at each step of the development and release process 22 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Product Development • Ongoing reviews to validate compliance with: – Secure Coding Standards – Previously documented security specifications • Additional design reviews for security • Extensive use of scanning and testing tools to provide ongoing feedback to development team in regards to quality of produced code – Proactive security testing – Destructive security testing 23 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Ongoing Assurance • Security testing take place throughout useful life of the product – Pre-release security scanning and testing: • Automated and ad hoc tests throughout development phase • Compliance with security release checklist is mandatory before release – Post-release security activities: • Targeted security review to assess resistance to new and emerging threats, or validate absence of vulnerabilities • Submission of security flaws by customers and security researchers – Ethical hacking (internal security assessment) • Updated secure configuration best practices are available online • Independent Security Evaluations – Common Criteria (ISO-15408) , FIPS 140 -2 24 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
Oracle Vulnerability Remediation Practices Introduction • While our #1 priority is the prevention of security vulnerabilities in released code, Oracle has very mature security vulnerability remediation practices – Security patching is a “necessary evil” and most public evidence of ongoing assurance effort: • Need to address vulnerabilities uncovered during ongoing assurance effort • Need to address vulnerabilities resulting from new attack methods or use case scenario by our customers • Need to address vulnerabilities reported by external security researchers – Critical Patch Update program is designed to maintain the security posture of Oracle customers at lowest possible cost for them 25 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

• • 26 Importance of Software Security What is Software Security Assurance? Oracle Software Security Assurance Cultivating Security Community in Development Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Cultivating Security Community in Development • Security is a strategic requirement defined by the Global Product Security organization – – – Braintrust for security topics and expertise Definition and enforcement of Secure Coding Standards Security review in support of M&A activities Development and maintenance of core security modules Lead ongoing assurance activities Definition and delivery of security training programs (including remedial effort when required) – Report into the Chief Security Officer • Security at Oracle follows a mostly decentralized model to reflect the differences in products and the development groups that produce them 27 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
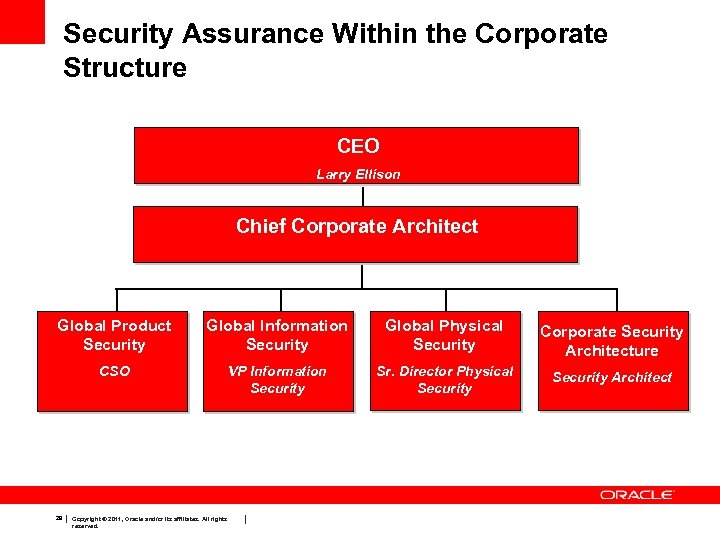
Security Assurance Within the Corporate Structure CEO Larry Ellison Chief Corporate Architect Global Product Security Global Information Security Global Physical Security Corporate Security Architecture CSO VP Information Security Sr. Director Physical Security Architect 28 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
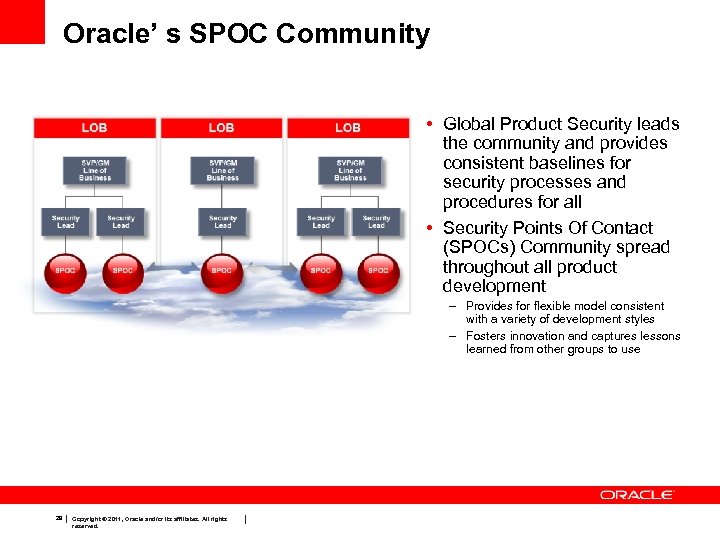
Oracle’ s SPOC Community • Global Product Security leads the community and provides consistent baselines for security processes and procedures for all • Security Points Of Contact (SPOCs) Community spread throughout all product development – Provides for flexible model consistent with a variety of development styles – Fosters innovation and captures lessons learned from other groups to use 29 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
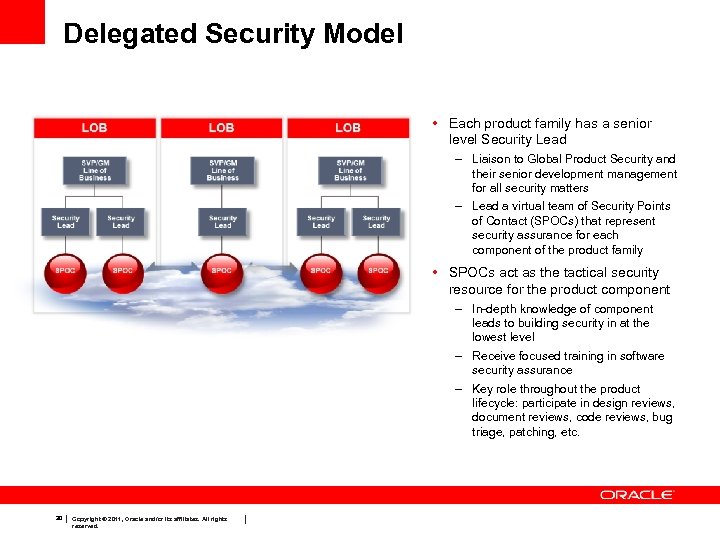
Delegated Security Model • Each product family has a senior level Security Lead – Liaison to Global Product Security and their senior development management for all security matters – Lead a virtual team of Security Points of Contact (SPOCs) that represent security assurance for each component of the product family • SPOCs act as the tactical security resource for the product component – In-depth knowledge of component leads to building security in at the lowest level – Receive focused training in software security assurance – Key role throughout the product lifecycle: participate in design reviews, document reviews, code reviews, bug triage, patching, etc. 30 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
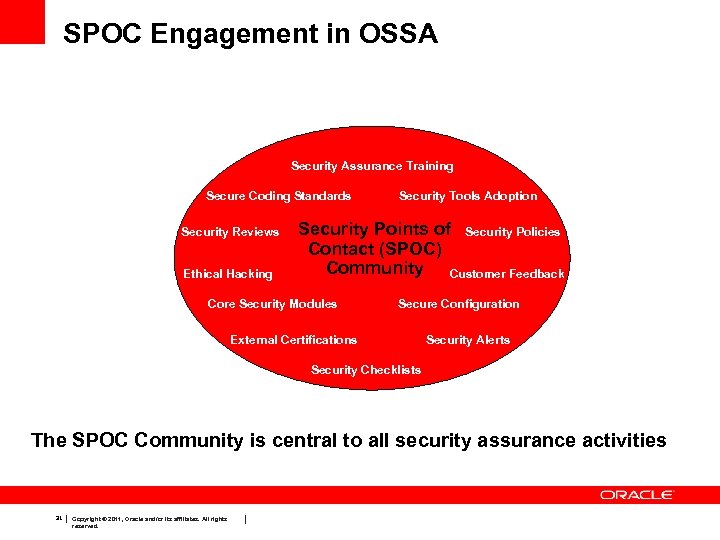
SPOC Engagement in OSSA Security Assurance Training Secure Coding Standards Security Reviews Ethical Hacking Security Tools Adoption Security Points of Security Policies Contact (SPOC) Community Customer Feedback Core Security Modules Secure Configuration External Certifications Security Alerts Security Checklists The SPOC Community is central to all security assurance activities 31 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Security Points of Contact (SPOCs) • Key role to achieve baking security in • Flexible model, accommodates a variety of development styles • Security experts within each product component team – – – Professional security resource in each product development team In-depth knowledge of component(s) represented Receive focused training in security assurance Liaison between Security Lead and Global Product Security Participate in design reviews, document reviews, code reviews, bug triage • Responsible for and report compliance status for each component in each major product release – Automated Security Checklist System – Security reviews with Security Lead and Global Product Security 32 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Responsibilities of the SPOC • Apply licensed 3 rd-party code security updates to component • Read security alerts from partner vendors and act as necessary for the component • Apply latest Critical Patch Updates and security fixes for underlying Oracle components • Monitor hacker exploits and news • Ensure component security bugs are included in the next Critical Patch Update • Knowledge of publicly known security bugs in old releases of the component and verify that all are fixed in the current release • Communicate all security news to the development team 33 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

The Ideal SPOC • Avoids potential security vulnerabilities and associated costs for patching – for both Oracle and the customer • Guards Oracle’s reputation and sales against security issues • Ensures the government and regulatory requirements in the security area are satisfied 34 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Binding the Community Together • SPOC identification “tag” in corporate directory • Monthly SPOC newsletter – More than SPOCs, widely read • Annual SPOC Summits – Internal and External Speakers • Comprehensive, centralized Global Product Security wiki – Key component is the Secure Coding Practices • SPOC Web Conferences on specific topics • Internal Oracle Social group for SPOCs • Ora. Tweet for security-related questions 35 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Community Membership is Growing • • • Not just Development SPOCs…. QA SPOCs Architects Security Features Developers Other Groups – IT organizations – Consultants – Saa. S Staff 36 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

Q&A 37 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.

38 Copyright © 2011, Oracle and/or its affiliates. All rights reserved.
a22cbc2248b6c71debb7174facda0483.ppt