78e7aad3f0dd6001897c3eb1e93b58ce.ppt
- Количество слайдов: 17

A Routing-Driven Elliptic Curve Cryptography Based Key Management Scheme for Heterogeneous Sensor Networks Author: Xiaojiang Du, Guizani M. , Yang Xiao and Hsiao-Hwa Chen Source: Wireless Communications, IEEE, vol. 8, no. 3, pp. 1223 -1229, 2009 Presenter: Yung-Chih Lu Date: 2010/07/13

Outline Introduction n Related Work n Ø L. Eschenauer and V. Gligor. “A Key-Management Scheme for Distributed Sensor Networks. ” In Proc. 9 th ACM Conference on Computerand Communication Security, pp. 41 -47, Nov. 2002. Proposed Scheme n Performance Evaluaton n Security Analysis n Conclusion & Comment n
Introduction(1/6) MANET (Mobile Ad Hoc Network) WSN (Wireless Sensor Network)
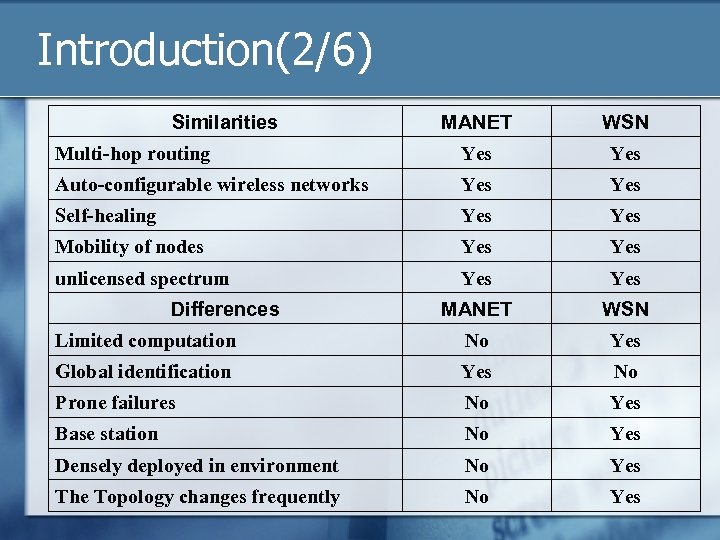
Introduction(2/6) Similarities MANET WSN Multi-hop routing Yes Auto-configurable wireless networks Yes Self-healing Yes Mobility of nodes Yes unlicensed spectrum Yes MANET WSN Limited computation No Yes Global identification Yes No Prone failures No Yes Base station No Yes Densely deployed in environment No Yes The Topology changes frequently No Yes Differences
Introduction(3/6) n Sensor node constraints Ø Battery power • • Ø Ø Ø n Computational energy consumption Communication energy consumption Transmission range Memory space Tamper protection Evaluation/Comparison metrics Ø Ø Ø Resilience against node capture Addition Revocation Supported network size suite all needs
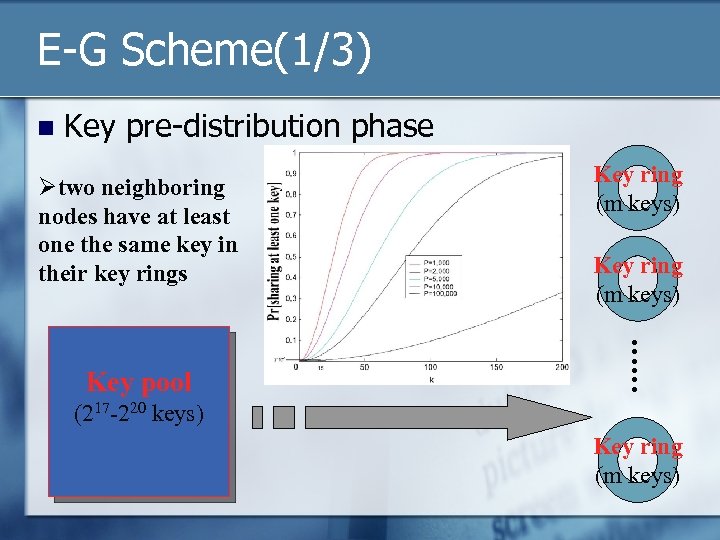
E-G Scheme(1/3) n Key pre-distribution phase Øtwo neighboring nodes have at least one the same key in their key rings Key ring (m keys) …… Key pool Key ring (m keys) (217 -220 keys) Key ring (m keys)
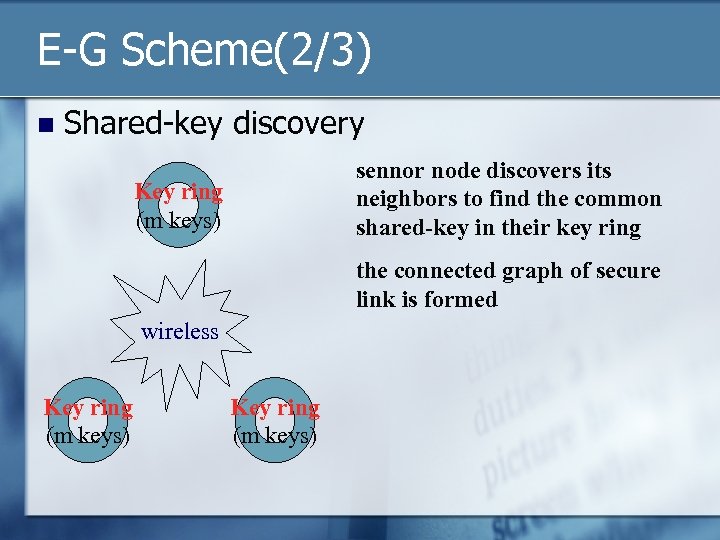
E-G Scheme(2/3) n Shared-key discovery sennor node discovers its neighbors to find the common shared-key in their key ring Key ring (m keys) the connected graph of secure link is formed wireless Key ring (m keys)
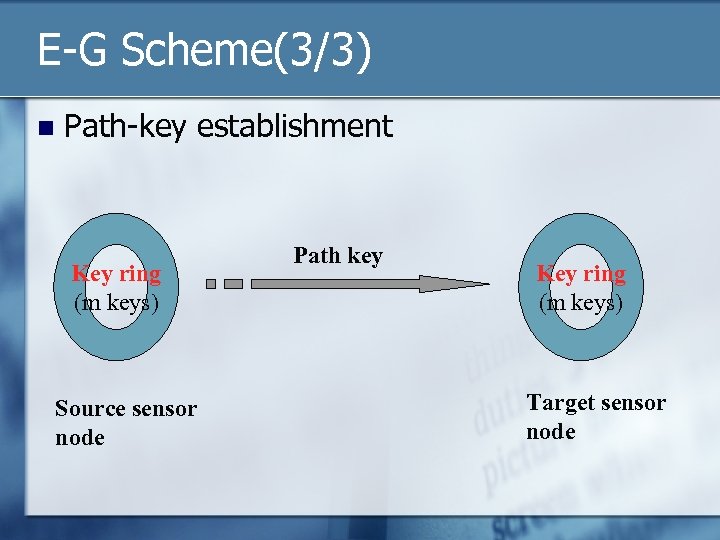
E-G Scheme(3/3) n Path-key establishment Key ring (m keys) Source sensor node Path key Key ring (m keys) Target sensor node
![Proposed Scheme(1/4) n Centralized Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location) Proposed Scheme(1/4) n Centralized Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location)](https://present5.com/presentation/78e7aad3f0dd6001897c3eb1e93b58ce/image-9.jpg)
Proposed Scheme(1/4) n Centralized Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location) (6)DKRL[EKUL[Ku, v]] = Ku, v (4) disseminates the parent-child relationships to all L-sensors (5)Send EKUL[Ku, v] (2)DKUL[EKRL [Key-request message ]] = Key-request message (3)run Centralized MST algorithm to determine the tree structure
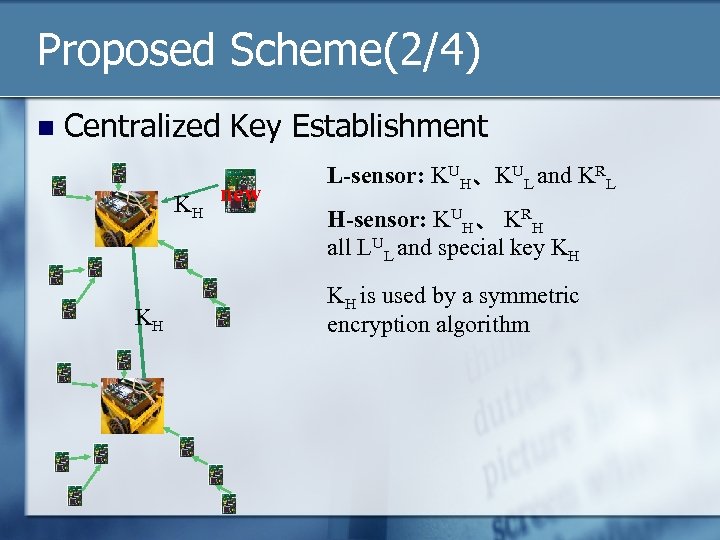
Proposed Scheme(2/4) n Centralized Key Establishment KH new KH L-sensor: KUH、KUL and KRL H-sensor: KUH、 KRH all LUL and special key KH KH is used by a symmetric encryption algorithm
![Proposed Scheme(3/4) n Distributed Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location) Proposed Scheme(3/4) n Distributed Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location)](https://present5.com/presentation/78e7aad3f0dd6001897c3eb1e93b58ce/image-11.jpg)
Proposed Scheme(3/4) n Distributed Key Establishment (1)Send EKRL[Key-request message ] (L-sensor ID and location) (6)Proves the authenticity of a public key (4) disseminates the parent-child relationships to all L-sensors (5)Send public key certificate EKRH[KUL] (2)DKUL[EKRL [Key-request message ]] = Key-request message (3)run Centralized MST algorithm to determine the tree structure
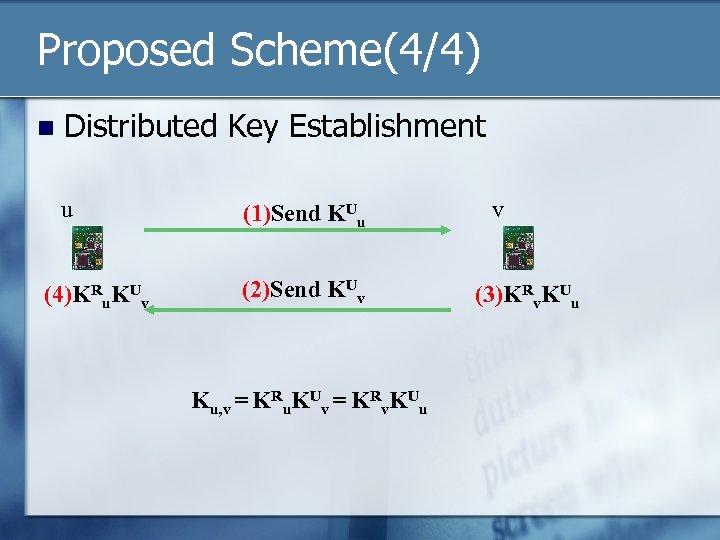
Proposed Scheme(4/4) n Distributed Key Establishment u (4)KRu. KUv (1)Send KUu (2)Send KUv Ku, v = KRu. KUv = KRv. KUu v (3)KRv. KUu
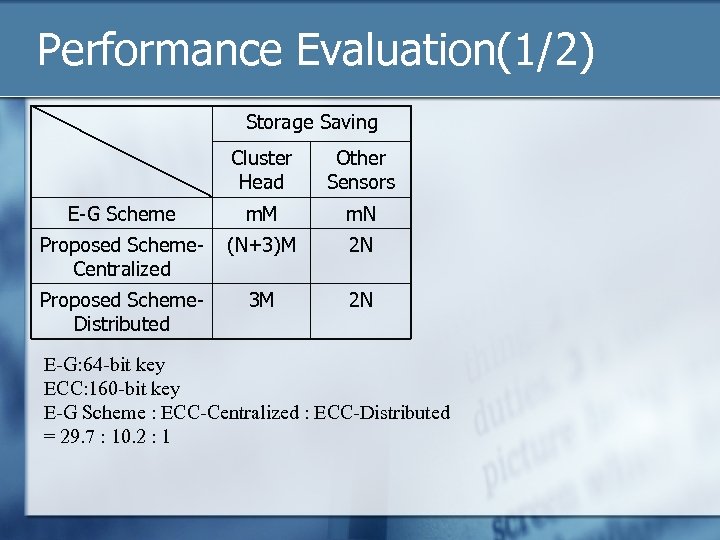
Performance Evaluation(1/2) Storage Saving Cluster Head Other Sensors E-G Scheme m. M m. N Proposed Scheme. Centralized (N+3)M 2 N Proposed Scheme. Distributed 3 M 2 N E-G: 64 -bit key ECC: 160 -bit key E-G Scheme : ECC-Centralized : ECC-Distributed = 29. 7 : 10. 2 : 1
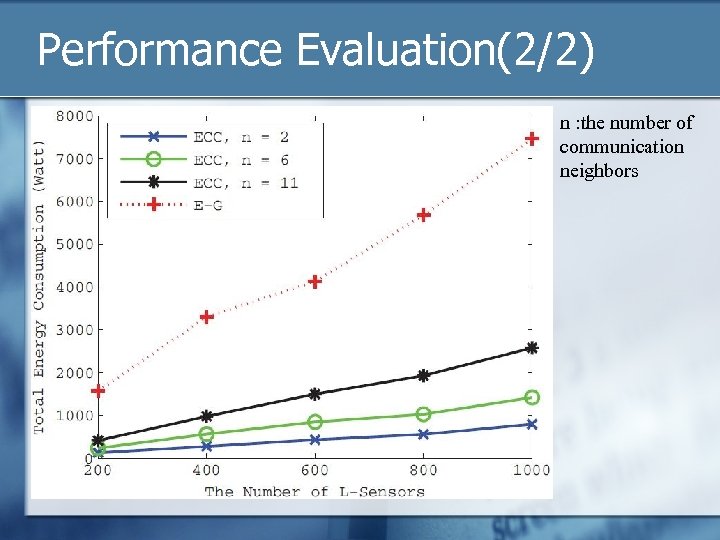
Performance Evaluation(2/2) n : the number of communication neighbors
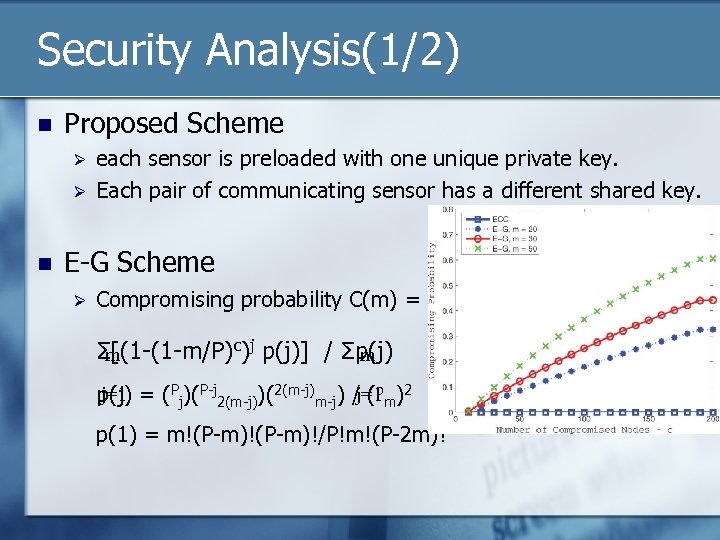
Security Analysis(1/2) n Proposed Scheme Ø Ø n each sensor is preloaded with one unique private key. Each pair of communicating sensor has a different shared key. E-G Scheme Ø Compromising probability C(m) = Σ[(1 -(1 -m/P)c)j p(j)] / Σp(j) m m j=1 p(j) = (Pj)(P-j 2(m-j))(2(m-j) /j=1 m)2 (p p(1) = m!(P-m)!/P!m!(P-2 m)!
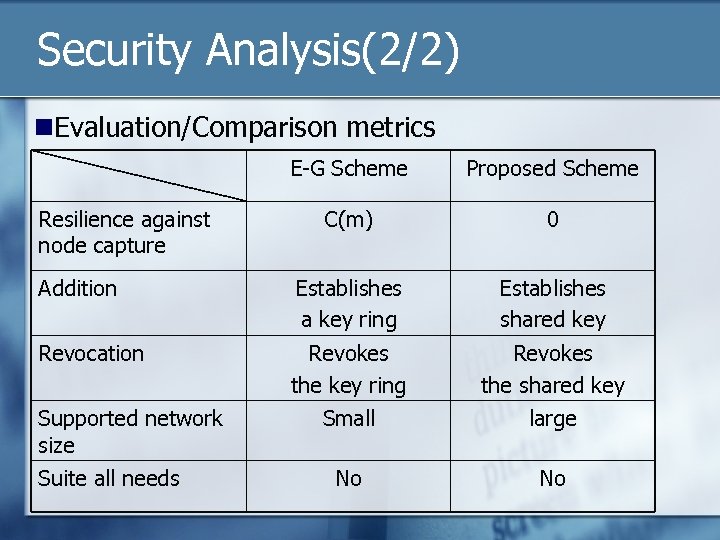
Security Analysis(2/2) n. Evaluation/Comparison metrics E-G Scheme Proposed Scheme C(m) 0 Addition Establishes a key ring Establishes shared key Revocation Revokes the key ring Revokes the shared key Small large No No Resilience against node capture Supported network size Suite all needs

Conclusion & Comment n n n A sensor only communicates with a small portion of its neighbors Proposed scheme significantly reduces sensor storage Proposed scheme significantly reduces Communication overhead Energy consumption while achieving better performance How to manages special key KH
78e7aad3f0dd6001897c3eb1e93b58ce.ppt