59db1bb429e709da329090b9d13fd802.ppt
- Количество слайдов: 19
 A PKI Certificate Policy for Higher Education A Work in Progress Draft 0. 010 David L. Wasley University the President Office of of California University of California
A PKI Certificate Policy for Higher Education A Work in Progress Draft 0. 010 David L. Wasley University the President Office of of California University of California
 Certificate Policy is … v The basis of trust between unrelated entities v Not a “contract” v A framework that informs/constrains a PKI implementation v A way of giving advice to Relying Parties v One of a number of related documents, incl. l l Certification Practices Directory Policy 2
Certificate Policy is … v The basis of trust between unrelated entities v Not a “contract” v A framework that informs/constrains a PKI implementation v A way of giving advice to Relying Parties v One of a number of related documents, incl. l l Certification Practices Directory Policy 2
 Goals v. A “generic” CP for higher ed PKI v Compatible with the Federal BCA policy v Simple (relatively) to implement at the “Rudimentary” level (PKI Lite) v Specific requirements intended to foster interdomain trust v All implementation specific details deferred to associated Certification Practices Statement 3
Goals v. A “generic” CP for higher ed PKI v Compatible with the Federal BCA policy v Simple (relatively) to implement at the “Rudimentary” level (PKI Lite) v Specific requirements intended to foster interdomain trust v All implementation specific details deferred to associated Certification Practices Statement 3
 PKI Players v Policy l Management Authority (PMA) Responsible for developing end enforcing policy v Certificate l l Authority (CA) Operational unit(s) Term also applies to the entire set of functions v Registration l Authority (RA) Optional delegated responsibility for I & A v Relying Parties 4
PKI Players v Policy l Management Authority (PMA) Responsible for developing end enforcing policy v Certificate l l Authority (CA) Operational unit(s) Term also applies to the entire set of functions v Registration l Authority (RA) Optional delegated responsibility for I & A v Relying Parties 4
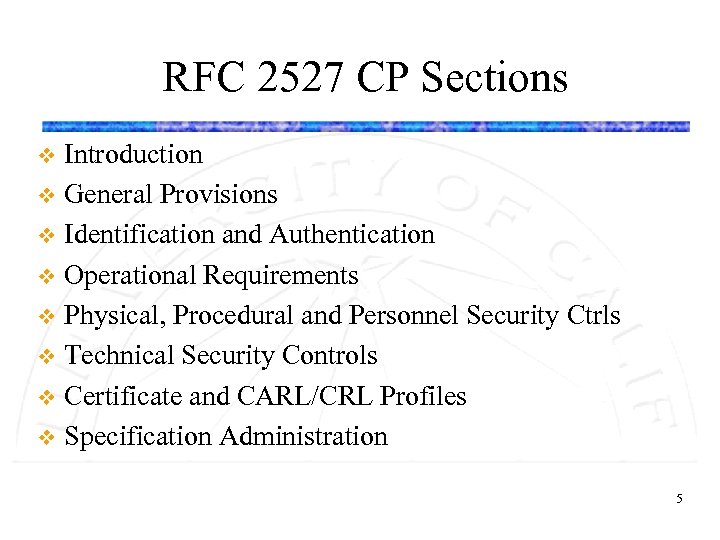 RFC 2527 CP Sections Introduction v General Provisions v Identification and Authentication v Operational Requirements v Physical, Procedural and Personnel Security Ctrls v Technical Security Controls v Certificate and CARL/CRL Profiles v Specification Administration v 5
RFC 2527 CP Sections Introduction v General Provisions v Identification and Authentication v Operational Requirements v Physical, Procedural and Personnel Security Ctrls v Technical Security Controls v Certificate and CARL/CRL Profiles v Specification Administration v 5
 Introduction v Distinction between CP and CPS v CP is transitive throughout the hierarchy l Authorizing CA has responsibility for authorized CA v Document l identity OID for the CP and OIDs for each LOA v On-line copy of CP and CPS must be signed v Community served may be any defined in the CPS l Relying Party can’t make assumptions unless so stated 6
Introduction v Distinction between CP and CPS v CP is transitive throughout the hierarchy l Authorizing CA has responsibility for authorized CA v Document l identity OID for the CP and OIDs for each LOA v On-line copy of CP and CPS must be signed v Community served may be any defined in the CPS l Relying Party can’t make assumptions unless so stated 6
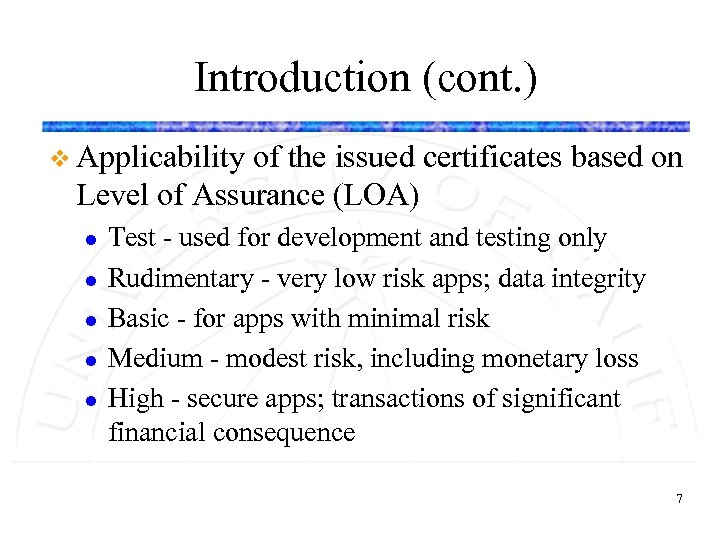 Introduction (cont. ) v Applicability of the issued certificates based on Level of Assurance (LOA) l l l Test - used for development and testing only Rudimentary - very low risk apps; data integrity Basic - for apps with minimal risk Medium - modest risk, including monetary loss High - secure apps; transactions of significant financial consequence 7
Introduction (cont. ) v Applicability of the issued certificates based on Level of Assurance (LOA) l l l Test - used for development and testing only Rudimentary - very low risk apps; data integrity Basic - for apps with minimal risk Medium - modest risk, including monetary loss High - secure apps; transactions of significant financial consequence 7
 General Provisions v Obligations l l CA, RA, Subscriber, Relying Party, Repository RP is problematic since there is no “contract” s In some cases a contract may be needed, e. g. FERPA v Liability l l limited to $1, 000 Considered necessary to indicate trustworthiness v Audit l of the parties requirements Must be performed by qualified third party Results must be made available 8
General Provisions v Obligations l l CA, RA, Subscriber, Relying Party, Repository RP is problematic since there is no “contract” s In some cases a contract may be needed, e. g. FERPA v Liability l l limited to $1, 000 Considered necessary to indicate trustworthiness v Audit l of the parties requirements Must be performed by qualified third party Results must be made available 8
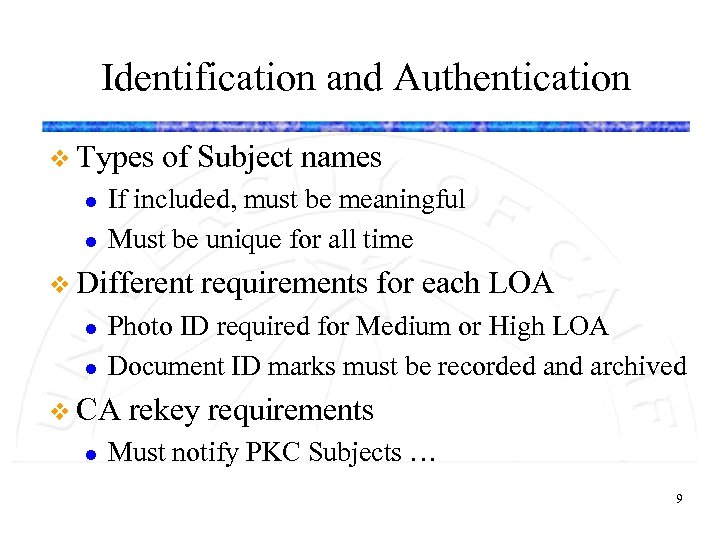 Identification and Authentication v Types l l of Subject names If included, must be meaningful Must be unique for all time v Different l l Photo ID required for Medium or High LOA Document ID marks must be recorded and archived v CA l requirements for each LOA rekey requirements Must notify PKC Subjects … 9
Identification and Authentication v Types l l of Subject names If included, must be meaningful Must be unique for all time v Different l l Photo ID required for Medium or High LOA Document ID marks must be recorded and archived v CA l requirements for each LOA rekey requirements Must notify PKC Subjects … 9
 Operational Requirements v CA may not generate key pairs for Subjects v PKC acceptance for Med/High require signature v PKC Suspension or Revocation l l Suspension not used Revocation required at Basic or higher LOA s s Requires standard CRL; allows for OCSP Relying Party required to check for revocation 10
Operational Requirements v CA may not generate key pairs for Subjects v PKC acceptance for Med/High require signature v PKC Suspension or Revocation l l Suspension not used Revocation required at Basic or higher LOA s s Requires standard CRL; allows for OCSP Relying Party required to check for revocation 10
 Operational Requirements (cont. ) v Security l l Everything that might affect the CA or RA Simple for Rudimentary v Records l l Audit Procedure Archival Up to 20 years + 6 months for High LOA (Electronic archive is an activity unto itself) v Disaster Recovery Requirements v CA Termination Process 11
Operational Requirements (cont. ) v Security l l Everything that might affect the CA or RA Simple for Rudimentary v Records l l Audit Procedure Archival Up to 20 years + 6 months for High LOA (Electronic archive is an activity unto itself) v Disaster Recovery Requirements v CA Termination Process 11
![Physical, Procedural and Personnel Security Controls v CA l l Roles [may change] Administrator Physical, Procedural and Personnel Security Controls v CA l l Roles [may change] Administrator](https://present5.com/presentation/59db1bb429e709da329090b9d13fd802/image-12.jpg) Physical, Procedural and Personnel Security Controls v CA l l Roles [may change] Administrator - sysadmin; installs & configures Officer - approves issuance and revocation of PKCs Operator - routine system operation & backup Auditor - reviews syslogs; oversees external audit v Separation of roles required at higher LOAs v Some tasks require action by 2 out of 4 persons 12
Physical, Procedural and Personnel Security Controls v CA l l Roles [may change] Administrator - sysadmin; installs & configures Officer - approves issuance and revocation of PKCs Operator - routine system operation & backup Auditor - reviews syslogs; oversees external audit v Separation of roles required at higher LOAs v Some tasks require action by 2 out of 4 persons 12
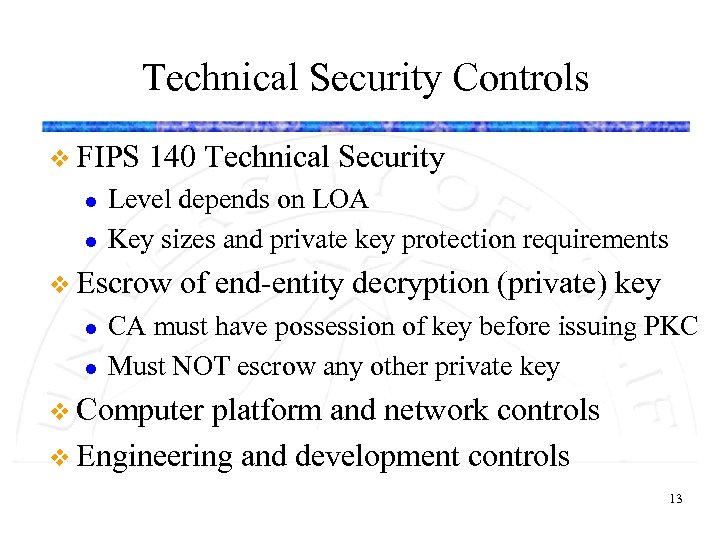 Technical Security Controls v FIPS l l 140 Technical Security Level depends on LOA Key sizes and private key protection requirements v Escrow l l of end-entity decryption (private) key CA must have possession of key before issuing PKC Must NOT escrow any other private key v Computer platform and network controls v Engineering and development controls 13
Technical Security Controls v FIPS l l 140 Technical Security Level depends on LOA Key sizes and private key protection requirements v Escrow l l of end-entity decryption (private) key CA must have possession of key before issuing PKC Must NOT escrow any other private key v Computer platform and network controls v Engineering and development controls 13
 Certificate and CARL/CRL Profiles v Certificate l l l Details in CPS Cert. Policy. ID is the LOA OID CPSuri points to the on-line signed CPS s l profile is x. 509 v 3 or higher CPS specifies CP OID and URL where it can be found Certificate serial number must be unique across all PKCs issued by this CA v CARL/CRL is x. 509 v 2 or higher 14
Certificate and CARL/CRL Profiles v Certificate l l l Details in CPS Cert. Policy. ID is the LOA OID CPSuri points to the on-line signed CPS s l profile is x. 509 v 3 or higher CPS specifies CP OID and URL where it can be found Certificate serial number must be unique across all PKCs issued by this CA v CARL/CRL is x. 509 v 2 or higher 14
 Specification Administration v Specifies how the PMA changes or updates this policy document, etc. v See also the Bibliography and Glossary 15
Specification Administration v Specifies how the PMA changes or updates this policy document, etc. v See also the Bibliography and Glossary 15
 Other Policy Documents v Certification l l All specific details, e. g. community, I&A, etc. HE draft example begun … v Directory l l Policy Statement As critical as the credential Includes access controls, element definitions, etc… v Business l Practices Statement Policy Provisions The basis for the institution to issue credentials 16
Other Policy Documents v Certification l l All specific details, e. g. community, I&A, etc. HE draft example begun … v Directory l l Policy Statement As critical as the credential Includes access controls, element definitions, etc… v Business l Practices Statement Policy Provisions The basis for the institution to issue credentials 16
 Similar CPs for Comparison v Federal BCA Certificate Policy v European PKI certificate policy v Globus Grid CP v Draft Model Interstate Certificate Policy v Commercial PKI CPs (very different) v CP for the State of Washington v NACHA CARAT guidelines 17
Similar CPs for Comparison v Federal BCA Certificate Policy v European PKI certificate policy v Globus Grid CP v Draft Model Interstate Certificate Policy v Commercial PKI CPs (very different) v CP for the State of Washington v NACHA CARAT guidelines 17
 HE CP Status v Draft l in process for 9 months Will be vetted to wider audience ASAP v Companion HEBCA CP needs to be reviewed to ensure compatibility v Generic OIDs may be acquired for CP, LOAs v Example CPS(s) will be generated v Notes for CA implementers will be created v See http: //www. educause. edu/hepki/ 18
HE CP Status v Draft l in process for 9 months Will be vetted to wider audience ASAP v Companion HEBCA CP needs to be reviewed to ensure compatibility v Generic OIDs may be acquired for CP, LOAs v Example CPS(s) will be generated v Notes for CA implementers will be created v See http: //www. educause. edu/hepki/ 18
 Acknowledgements v Richard Guida, Federal PKI Council v Ken Klingenstein and the I 2 HEPKI-PAG v Judith Boettcher, CREN v Dan Burke, Legal Council, CREN v Scott Fullerton -- Wisconsin-Madison v Art Vandenburg -- Georgia State v Support: Renee Frost, Ellen Vaughan, Nate Klingenstein (I 2), Michelle Gildea (CREN) 19
Acknowledgements v Richard Guida, Federal PKI Council v Ken Klingenstein and the I 2 HEPKI-PAG v Judith Boettcher, CREN v Dan Burke, Legal Council, CREN v Scott Fullerton -- Wisconsin-Madison v Art Vandenburg -- Georgia State v Support: Renee Frost, Ellen Vaughan, Nate Klingenstein (I 2), Michelle Gildea (CREN) 19


