22d891d38838b0d0dc97abf93ee3a739.ppt
- Количество слайдов: 40
 A New Approach to DNS Security (DNSSEC) Author: Giuseppe Ateniese Stefan Mangard Presenter: Liu, Xiaotao
A New Approach to DNS Security (DNSSEC) Author: Giuseppe Ateniese Stefan Mangard Presenter: Liu, Xiaotao
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 What is the DNS • • • Domain Name System Distributed ‘database’ to resolve domain names Labels translate to Resource Records • • • Address (A) Mail hosts (MX) Text (TXT) and much more…. Resource records stored in zones Highly scalable
What is the DNS • • • Domain Name System Distributed ‘database’ to resolve domain names Labels translate to Resource Records • • • Address (A) Mail hosts (MX) Text (TXT) and much more…. Resource records stored in zones Highly scalable
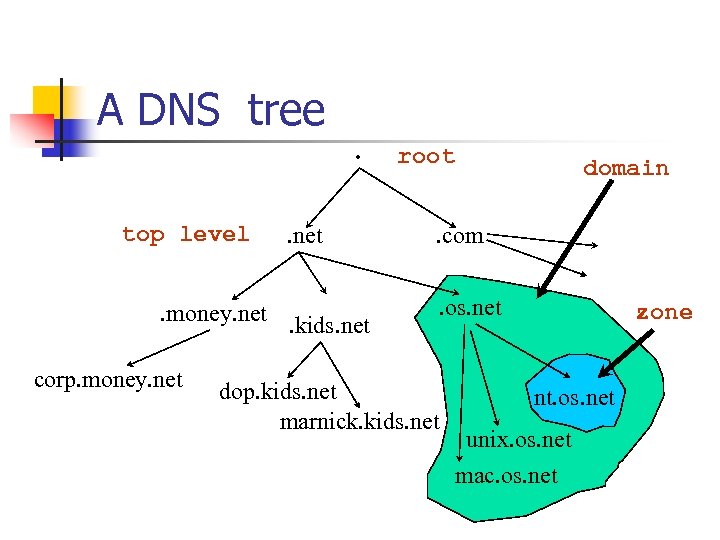 A DNS tree. top level . net . money. net. kids. net corp. money. net root domain . com. os. net dop. kids. net marnick. kids. net zone nt. os. net unix. os. net mac. os. net
A DNS tree. top level . net . money. net. kids. net corp. money. net root domain . com. os. net dop. kids. net marnick. kids. net zone nt. os. net unix. os. net mac. os. net
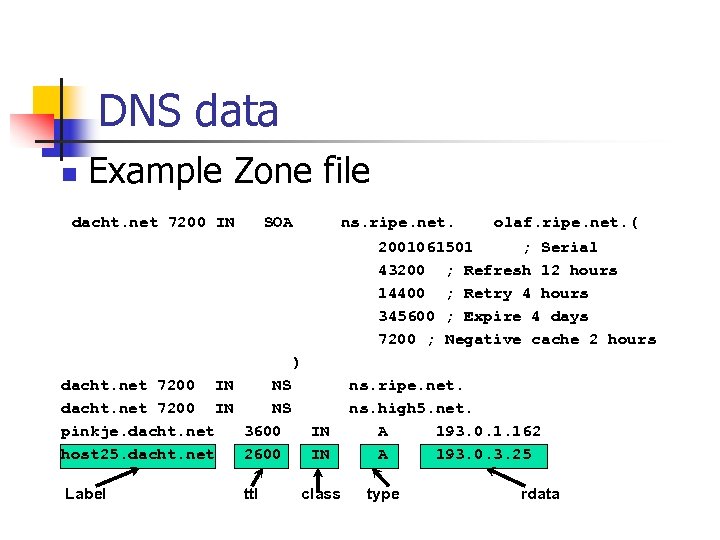 DNS data n Example Zone file dacht. net 7200 IN SOA ns. ripe. net. olaf. ripe. net. ( 2001061501 ; Serial 43200 ; Refresh 12 hours 14400 ; Retry 4 hours 345600 ; Expire 4 days 7200 ; Negative cache 2 hours ) dacht. net 7200 IN NS pinkje. dacht. net 3600 IN host 25. dacht. net 2600 IN Label ttl class ns. ripe. net. ns. high 5. net. A 193. 0. 1. 162 A 193. 0. 3. 25 type rdata
DNS data n Example Zone file dacht. net 7200 IN SOA ns. ripe. net. olaf. ripe. net. ( 2001061501 ; Serial 43200 ; Refresh 12 hours 14400 ; Retry 4 hours 345600 ; Expire 4 days 7200 ; Negative cache 2 hours ) dacht. net 7200 IN NS pinkje. dacht. net 3600 IN host 25. dacht. net 2600 IN Label ttl class ns. ripe. net. ns. high 5. net. A 193. 0. 1. 162 A 193. 0. 3. 25 type rdata
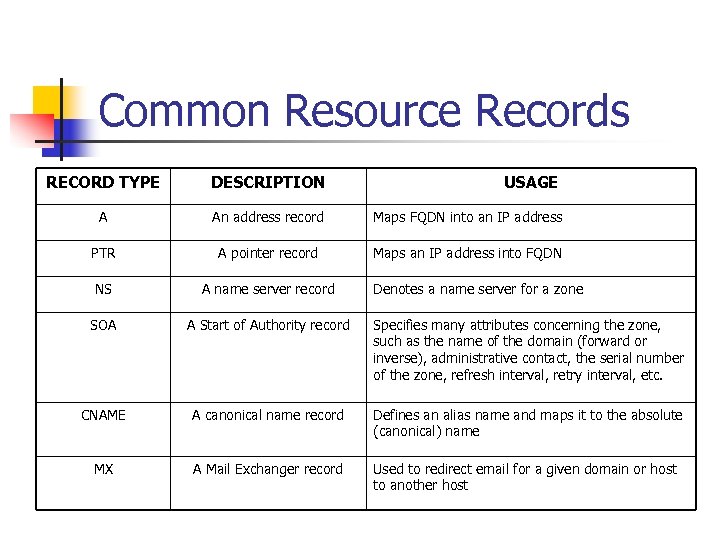 Common Resource Records RECORD TYPE DESCRIPTION USAGE A An address record Maps FQDN into an IP address PTR A pointer record Maps an IP address into FQDN NS A name server record SOA A Start of Authority record Specifies many attributes concerning the zone, such as the name of the domain (forward or inverse), administrative contact, the serial number of the zone, refresh interval, retry interval, etc. CNAME A canonical name record Defines an alias name and maps it to the absolute (canonical) name MX A Mail Exchanger record Used to redirect email for a given domain or host to another host Denotes a name server for a zone
Common Resource Records RECORD TYPE DESCRIPTION USAGE A An address record Maps FQDN into an IP address PTR A pointer record Maps an IP address into FQDN NS A name server record SOA A Start of Authority record Specifies many attributes concerning the zone, such as the name of the domain (forward or inverse), administrative contact, the serial number of the zone, refresh interval, retry interval, etc. CNAME A canonical name record Defines an alias name and maps it to the absolute (canonical) name MX A Mail Exchanger record Used to redirect email for a given domain or host to another host Denotes a name server for a zone
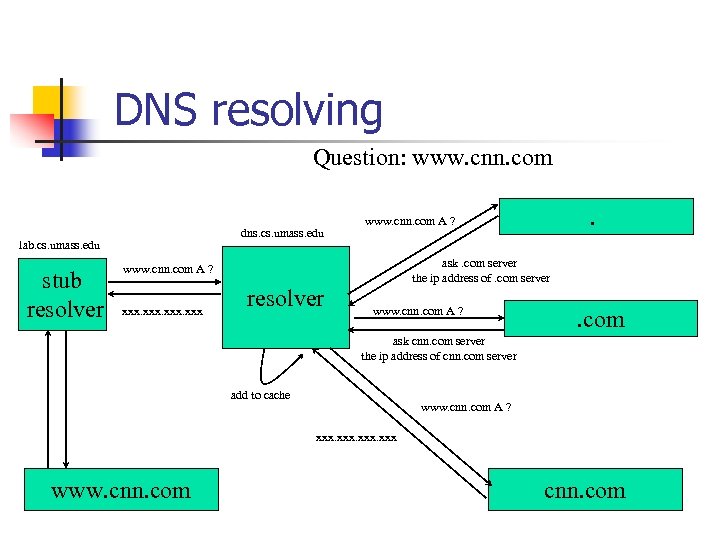 DNS resolving Question: www. cnn. com dns. cs. umass. edu lab. cs. umass. edu stub resolver ask. com server the ip address of. com server www. cnn. com A ? xxx . www. cnn. com A ? resolver www. cnn. com A ? . com ask cnn. com server the ip address of cnn. com server add to cache www. cnn. com A ? xxx www. cnn. com
DNS resolving Question: www. cnn. com dns. cs. umass. edu lab. cs. umass. edu stub resolver ask. com server the ip address of. com server www. cnn. com A ? xxx . www. cnn. com A ? resolver www. cnn. com A ? . com ask cnn. com server the ip address of cnn. com server add to cache www. cnn. com A ? xxx www. cnn. com
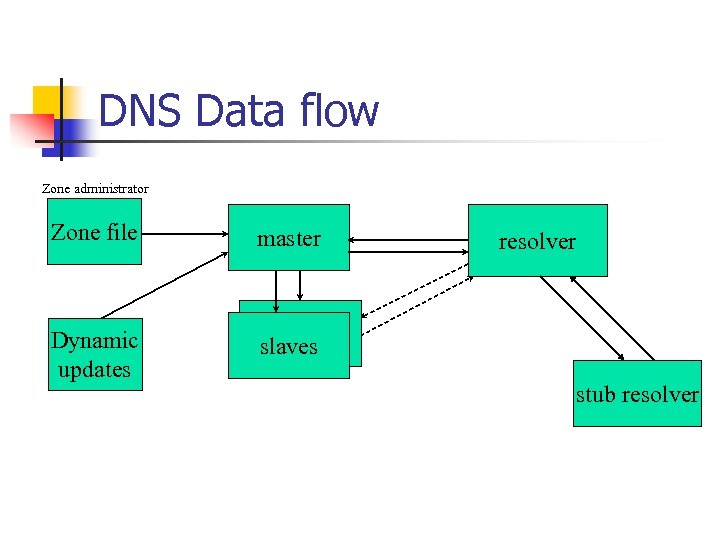 DNS Data flow Zone administrator Zone file master Dynamic updates slaves resolver stub resolver
DNS Data flow Zone administrator Zone file master Dynamic updates slaves resolver stub resolver
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
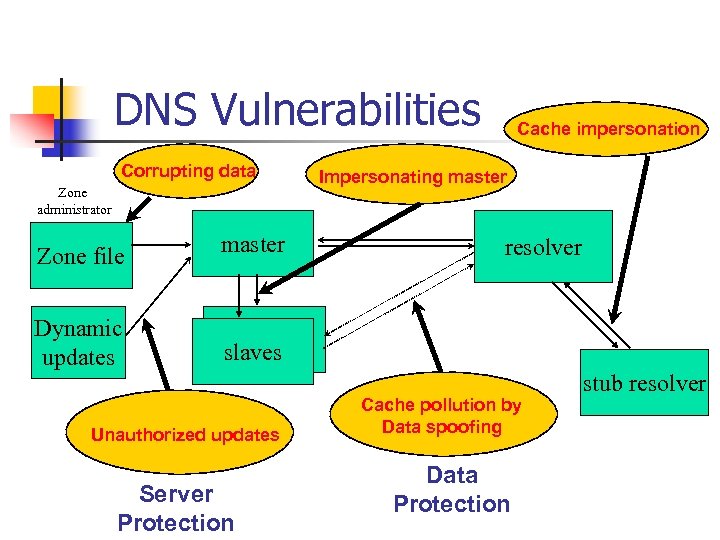 DNS Vulnerabilities Corrupting data Zone administrator Zone file master Dynamic updates Cache impersonation Impersonating master slaves Unauthorized updates Server Protection resolver Cache pollution by Data spoofing Data Protection stub resolver
DNS Vulnerabilities Corrupting data Zone administrator Zone file master Dynamic updates Cache impersonation Impersonating master slaves Unauthorized updates Server Protection resolver Cache pollution by Data spoofing Data Protection stub resolver
 Why DNSSEC • • • DNSSEC protects against data spoofing and corruption DNSSEC also provides mechanisms to authenticate servers and requests DNSSEC provides mechanisms to establish authenticity and integrity
Why DNSSEC • • • DNSSEC protects against data spoofing and corruption DNSSEC also provides mechanisms to authenticate servers and requests DNSSEC provides mechanisms to establish authenticity and integrity
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 PK-DNSSEC (Public Key) • The DNS servers sign (digitally encrypt)the hash of resource record set with its private keys • Resouce record set: The set of resource records of the same type. • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY)
PK-DNSSEC (Public Key) • The DNS servers sign (digitally encrypt)the hash of resource record set with its private keys • Resouce record set: The set of resource records of the same type. • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY)
 DNSSEC new RRs • 2 Public key related RRs • • • One RR for internal consistency (authenticated denial of data) • • SIG signature over RRset made using private key KEY public key, needed for verifying a SIG over a RRset, signed by the parent’s private key NXT RR to indicate which RRset is the next one in the zone For non DNSSEC public keys: CERT
DNSSEC new RRs • 2 Public key related RRs • • • One RR for internal consistency (authenticated denial of data) • • SIG signature over RRset made using private key KEY public key, needed for verifying a SIG over a RRset, signed by the parent’s private key NXT RR to indicate which RRset is the next one in the zone For non DNSSEC public keys: CERT
 SIG RRs • Cover each resource record set with a public-key signature which is stored as a resource record called SIG RR • SIG RRs are computed for every RRset in a zone file and stored • Add the corresponding pre-calculated signature for each RRset in answers to queries • Must include the entire RRset in an answer, otherwise the resolver could not verify the signature
SIG RRs • Cover each resource record set with a public-key signature which is stored as a resource record called SIG RR • SIG RRs are computed for every RRset in a zone file and stored • Add the corresponding pre-calculated signature for each RRset in answers to queries • Must include the entire RRset in an answer, otherwise the resolver could not verify the signature
 SIG(0) • Use public-key signature to sign the whole message each time the server responses the queries • Provide integrity protection and authentication of the whole message • Can be scaled to provide authentication of query requests • Not be practical to use on a large scale environment
SIG(0) • Use public-key signature to sign the whole message each time the server responses the queries • Provide integrity protection and authentication of the whole message • Can be scaled to provide authentication of query requests • Not be practical to use on a large scale environment
 Compare SIG RRs with SIG(0) • More computation on DNS server caused by SIG(0) • More network traffic caused by SIG RRs • More storage need by SIG RRs
Compare SIG RRs with SIG(0) • More computation on DNS server caused by SIG(0) • More network traffic caused by SIG RRs • More storage need by SIG RRs
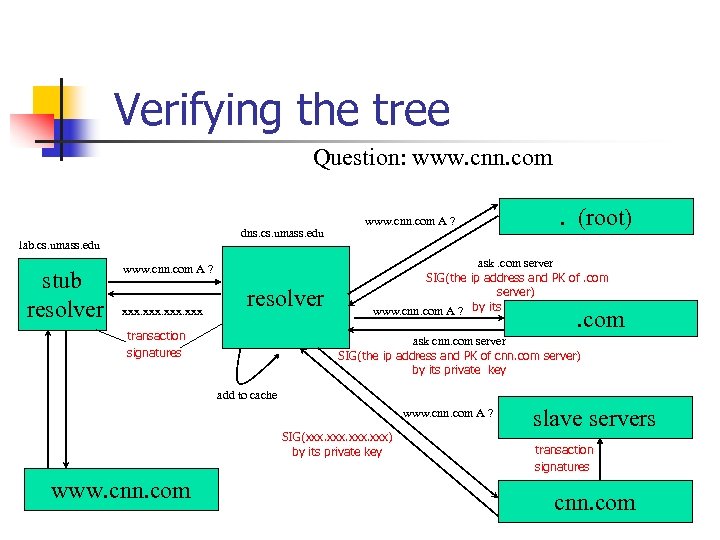 Verifying the tree Question: www. cnn. com dns. cs. umass. edu lab. cs. umass. edu stub resolver www. cnn. com A ? xxx resolver transaction signatures www. cnn. com A ? . (root) ask. com server SIG(the ip address and PK of. com server) by its private key www. cnn. com A ? . com ask cnn. com server SIG(the ip address and PK of cnn. com server) by its private key add to cache www. cnn. com A ? SIG(xxx. xxx) by its private key www. cnn. com slave servers transaction signatures cnn. com
Verifying the tree Question: www. cnn. com dns. cs. umass. edu lab. cs. umass. edu stub resolver www. cnn. com A ? xxx resolver transaction signatures www. cnn. com A ? . (root) ask. com server SIG(the ip address and PK of. com server) by its private key www. cnn. com A ? . com ask cnn. com server SIG(the ip address and PK of cnn. com server) by its private key add to cache www. cnn. com A ? SIG(xxx. xxx) by its private key www. cnn. com slave servers transaction signatures cnn. com
 Verifying • Verify a SIG over data using the public KEY • DNS data is signed with the private key • Verify the SIG with the KEY mentioned in the SIG record • The key can be found in the DNS or can be locally configured
Verifying • Verify a SIG over data using the public KEY • DNS data is signed with the private key • Verify the SIG with the KEY mentioned in the SIG record • The key can be found in the DNS or can be locally configured
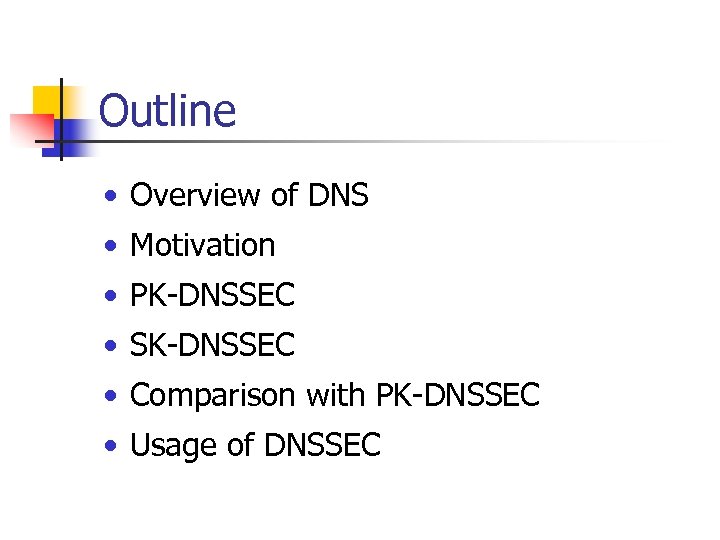 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 SK-DNSSEC (Symmetric Certificates) • The usage of symmetric ciphers through AES or Blowfish in CBC mode. • The usage of symmetric signatures via MAC functions. • Combine encryption techniques with MAC functions as Ek(m, MACl(m)). • Each message contains a nonce to avoid replay attack. A nonce is pair of a random number and a timestamp.
SK-DNSSEC (Symmetric Certificates) • The usage of symmetric ciphers through AES or Blowfish in CBC mode. • The usage of symmetric signatures via MAC functions. • Combine encryption techniques with MAC functions as Ek(m, MACl(m)). • Each message contains a nonce to avoid replay attack. A nonce is pair of a random number and a timestamp.
 SK-DNSSEC (cont. ) • Given the DNS tree of domains, each node shares a key with its parent, called master key • The root domain has an asymmetric key pair(public and private key) as well as its own master key that is not shared with any others • The resolvers must have an authentic copy of root’s public key
SK-DNSSEC (cont. ) • Given the DNS tree of domains, each node shares a key with its parent, called master key • The root domain has an asymmetric key pair(public and private key) as well as its own master key that is not shared with any others • The resolvers must have an authentic copy of root’s public key
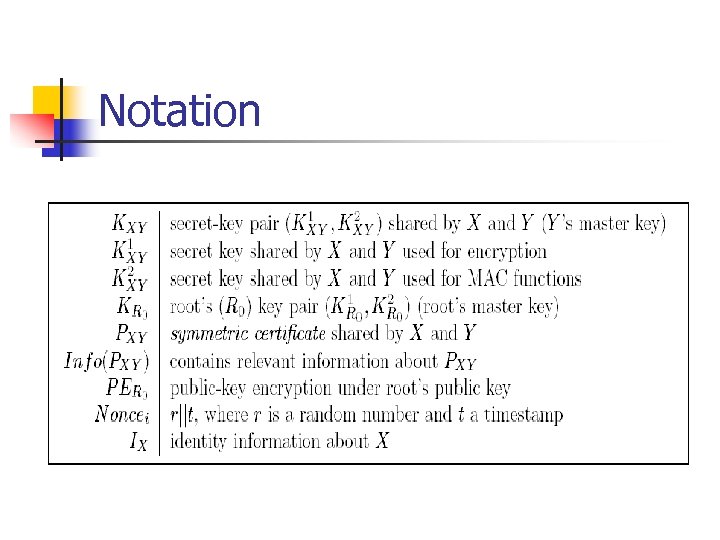 Notation
Notation
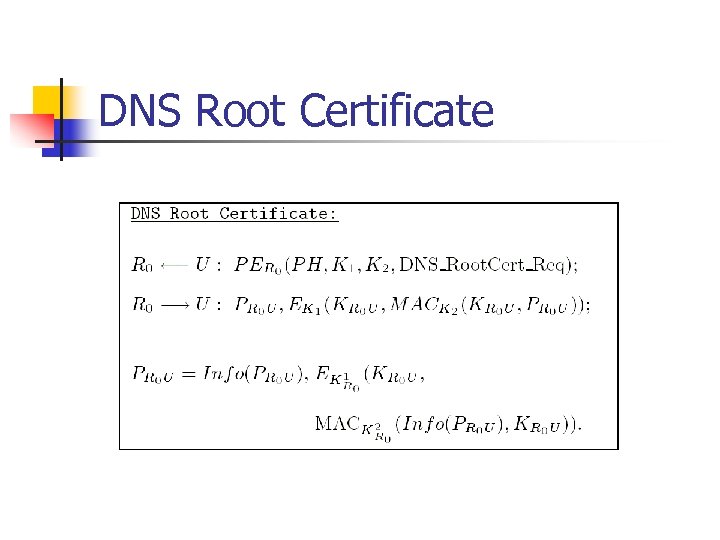 DNS Root Certificate
DNS Root Certificate
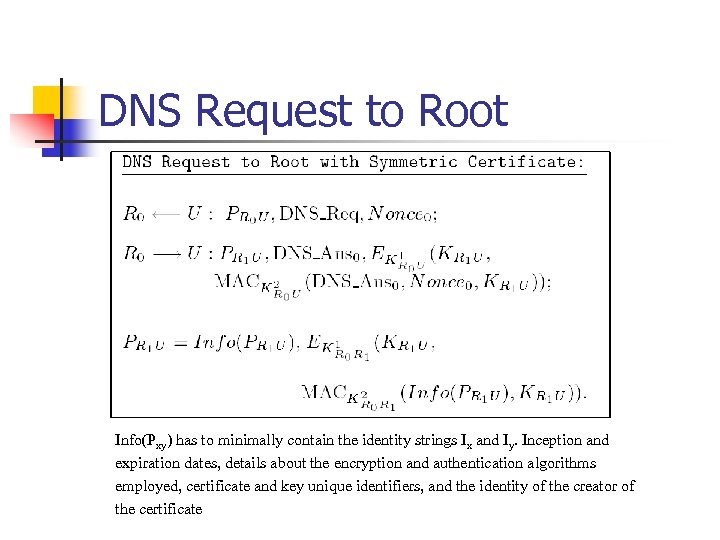 DNS Request to Root Info(Pxy) has to minimally contain the identity strings Ix and Iy. Inception and expiration dates, details about the encryption and authentication algorithms employed, certificate and key unique identifiers, and the identity of the creator of the certificate
DNS Request to Root Info(Pxy) has to minimally contain the identity strings Ix and Iy. Inception and expiration dates, details about the encryption and authentication algorithms employed, certificate and key unique identifiers, and the identity of the creator of the certificate
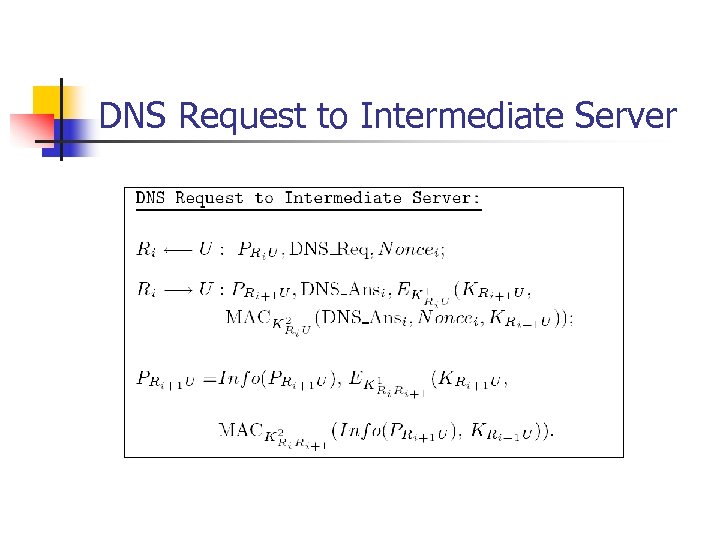 DNS Request to Intermediate Server
DNS Request to Intermediate Server
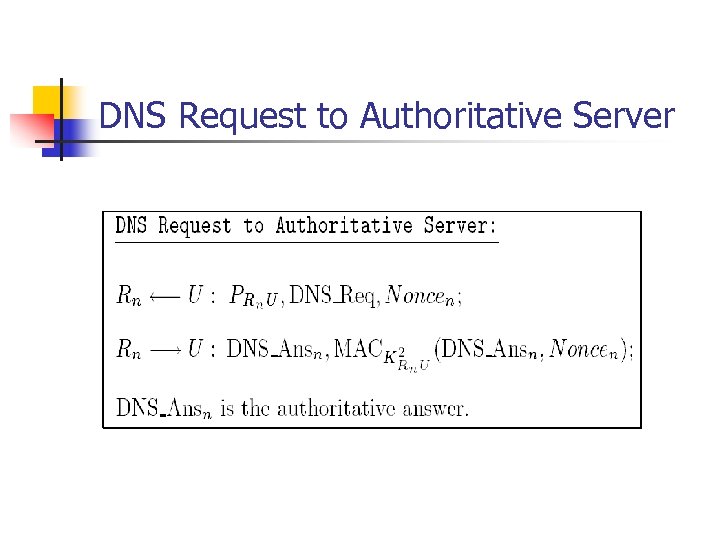 DNS Request to Authoritative Server
DNS Request to Authoritative Server
 For mutual authentication For any 0 i n
For mutual authentication For any 0 i n
 The problem of PK and SK DNSSEC • In SK-DNSSEC, the root servers need to decrypt the message encrypted by the public key • In PK-DNSSEC, the potential increase of network traffic due to larger DNS messages • In PK-DNSSEC, the high cost of verifying the public-key digital signatures at the resolvers side
The problem of PK and SK DNSSEC • In SK-DNSSEC, the root servers need to decrypt the message encrypted by the public key • In PK-DNSSEC, the potential increase of network traffic due to larger DNS messages • In PK-DNSSEC, the high cost of verifying the public-key digital signatures at the resolvers side
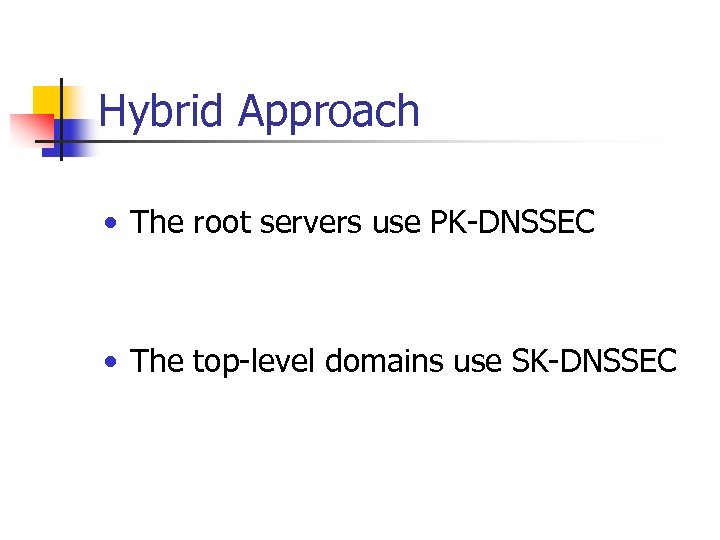 Hybrid Approach • The root servers use PK-DNSSEC • The top-level domains use SK-DNSSEC
Hybrid Approach • The root servers use PK-DNSSEC • The top-level domains use SK-DNSSEC
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 Efficiency • PK-DNSSEC with SIG RR. For each RRset in the answer, a pre-calculated SIG RR is included • PK-DNSSEC with SIG(0). DNS messages do not contain SIG RRs, but are rather signed as a whole by SIG(0)-type signature. • SK-DNSSEC. DNS messages are secured by symmetric signatures and encryption.
Efficiency • PK-DNSSEC with SIG RR. For each RRset in the answer, a pre-calculated SIG RR is included • PK-DNSSEC with SIG(0). DNS messages do not contain SIG RRs, but are rather signed as a whole by SIG(0)-type signature. • SK-DNSSEC. DNS messages are secured by symmetric signatures and encryption.
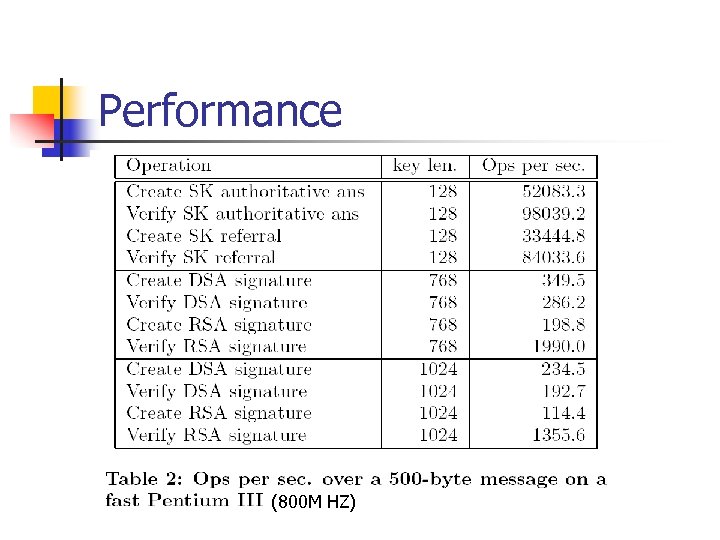 Performance (800 M HZ)
Performance (800 M HZ)
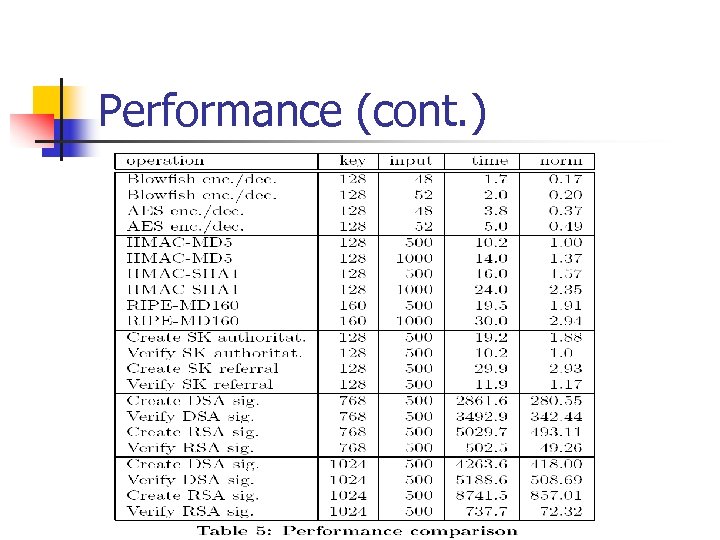 Performance (cont. )
Performance (cont. )
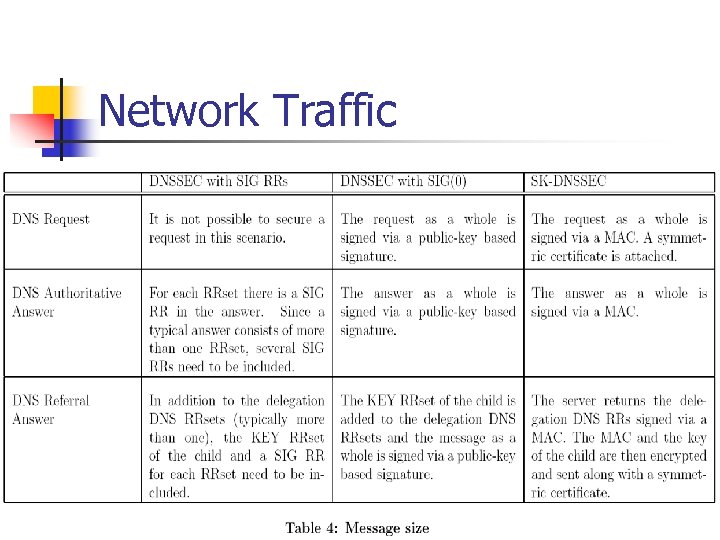 Network Traffic
Network Traffic
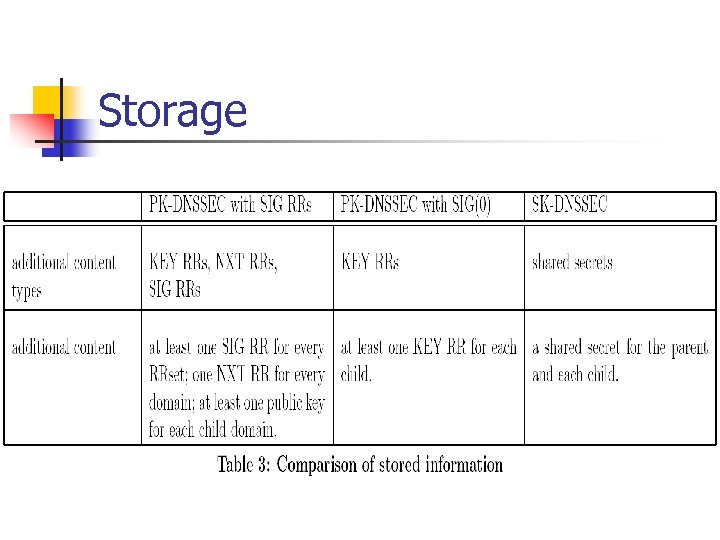 Storage
Storage
 Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
Outline • Overview of DNS • Motivation • PK-DNSSEC • SK-DNSSEC • Comparison with PK-DNSSEC • Usage of DNSSEC
 Public-key Distribution System • Global real time availability • Easy access to DNS • Scalability • Hierarchical organization • Globally unique names • Globally unique host name • Cryptographic binding of name and key • KEY RR binds DNS names with keys
Public-key Distribution System • Global real time availability • Easy access to DNS • Scalability • Hierarchical organization • Globally unique names • Globally unique host name • Cryptographic binding of name and key • KEY RR binds DNS names with keys
 Q&A Thank You!
Q&A Thank You!


