012594a535e10fd45109e0a2d8bc516f.ppt
- Количество слайдов: 40
 A Methodology to Evaluate the Trustworthiness and Security Compliance of Cloud Service Providers Sasko Ristov Ss. Cyril and Methodius University, Skopje, Macedonia
A Methodology to Evaluate the Trustworthiness and Security Compliance of Cloud Service Providers Sasko Ristov Ss. Cyril and Methodius University, Skopje, Macedonia
 Abstract Define a new methodology to evaluate the CSPs in different cloud deployment models according to the cloud consumers’ needs. Introduce a factor trustworthiness beside the availability. quantify the trustworthiness and the security of potential CSPs Evaluate the security compliance of CSPs with cloud security challenges for different cloud deployment models. 2 CSA CEE Summit 2016, Ljubljana, Slovenia
Abstract Define a new methodology to evaluate the CSPs in different cloud deployment models according to the cloud consumers’ needs. Introduce a factor trustworthiness beside the availability. quantify the trustworthiness and the security of potential CSPs Evaluate the security compliance of CSPs with cloud security challenges for different cloud deployment models. 2 CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness Evaluation of most common CSPs’ Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together On-premise and Cloud Security Compliance Quantification Conclusion 3 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness Evaluation of most common CSPs’ Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together On-premise and Cloud Security Compliance Quantification Conclusion 3 CSA CEE Summit 2016, Ljubljana, Slovenia
 State of the art - Cloud Computing How to choose a CSP? Standardisation Still in infancy period Bigger players enforce the standards Many challenges performance, security and data privacy, law compliance, different cost and indemnification 4 if the CSP does not meet the SLA conditions CSA CEE Summit 2016, Ljubljana, Slovenia
State of the art - Cloud Computing How to choose a CSP? Standardisation Still in infancy period Bigger players enforce the standards Many challenges performance, security and data privacy, law compliance, different cost and indemnification 4 if the CSP does not meet the SLA conditions CSA CEE Summit 2016, Ljubljana, Slovenia
 Open issues Interoperability Portability multiple server platforms 5 CSA CEE Summit 2016, Ljubljana, Slovenia
Open issues Interoperability Portability multiple server platforms 5 CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness Evaluation of most common CSPs’ Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together On-premise and Cloud Security Compliance Quantification Conclusion 6 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness Evaluation of most common CSPs’ Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together On-premise and Cloud Security Compliance Quantification Conclusion 6 CSA CEE Summit 2016, Ljubljana, Slovenia
![Evaluate CSP Performance variability [Iosup 2011] [Gusev / Ristov 2013], [Gusev / Ristov 2012] Evaluate CSP Performance variability [Iosup 2011] [Gusev / Ristov 2013], [Gusev / Ristov 2012]](https://present5.com/presentation/012594a535e10fd45109e0a2d8bc516f/image-7.jpg) Evaluate CSP Performance variability [Iosup 2011] [Gusev / Ristov 2013], [Gusev / Ristov 2012] Vertical scaling horizontal scaling Superlinear performance 7 Same VM – different performance in various time Buy less, achieve more CSA CEE Summit 2016, Ljubljana, Slovenia
Evaluate CSP Performance variability [Iosup 2011] [Gusev / Ristov 2013], [Gusev / Ristov 2012] Vertical scaling horizontal scaling Superlinear performance 7 Same VM – different performance in various time Buy less, achieve more CSA CEE Summit 2016, Ljubljana, Slovenia
 Evaluate CSP Security CSA Cloud Control Matrix (CCM) 3. 0. 1 Confidentiality, integrity and availability are concerns Different cloud deployment models Different security issues [Bhadauria 2012] Cloud improves RTO and RPO 8 Customer must check if a CSP meets its RTO and RPO CSA CEE Summit 2016, Ljubljana, Slovenia
Evaluate CSP Security CSA Cloud Control Matrix (CCM) 3. 0. 1 Confidentiality, integrity and availability are concerns Different cloud deployment models Different security issues [Bhadauria 2012] Cloud improves RTO and RPO 8 Customer must check if a CSP meets its RTO and RPO CSA CEE Summit 2016, Ljubljana, Slovenia
 Evaluate CSP Prices Pay as you consume Linear model Different price for 9 Windows / Linux Performance Traffic CSA CEE Summit 2016, Ljubljana, Slovenia
Evaluate CSP Prices Pay as you consume Linear model Different price for 9 Windows / Linux Performance Traffic CSA CEE Summit 2016, Ljubljana, Slovenia
 Evaluate CSP Trustworthiness CSPs guarantee very high availability of their services at least 99. 9% guarantee maximum 8. 77 hours of downtime per year. This high guarantee does not imply that they comply with their SLAs. some even 100% CSPs' downtime is much greater Cloud consumer's costs cannot be indemnified by CSP's. Service availability is not a decisive factor for many cloud consumers. 10 interested in lower cost for an acceptable level of availability. CSA CEE Summit 2016, Ljubljana, Slovenia
Evaluate CSP Trustworthiness CSPs guarantee very high availability of their services at least 99. 9% guarantee maximum 8. 77 hours of downtime per year. This high guarantee does not imply that they comply with their SLAs. some even 100% CSPs' downtime is much greater Cloud consumer's costs cannot be indemnified by CSP's. Service availability is not a decisive factor for many cloud consumers. 10 interested in lower cost for an acceptable level of availability. CSA CEE Summit 2016, Ljubljana, Slovenia
 CSP Trustworthiness Improve the trustworthiness Certify with some security standard ISO 27001: 2005 Ristov / Gusev 2012 New methodology for security evaluation of on-premise systems and cloud computing Iaa. S, Paa. S and Saa. S Security evaluation of open source cloud frameworks 11 [Ristov 2013] CSA CEE Summit 2016, Ljubljana, Slovenia
CSP Trustworthiness Improve the trustworthiness Certify with some security standard ISO 27001: 2005 Ristov / Gusev 2012 New methodology for security evaluation of on-premise systems and cloud computing Iaa. S, Paa. S and Saa. S Security evaluation of open source cloud frameworks 11 [Ristov 2013] CSA CEE Summit 2016, Ljubljana, Slovenia
 Other methodologies for Trustworthiness Cheng 2012 Tanimoto 2011 Risk Avoidance, Risk Mitigation, Risk Acceptance, and Risk Transference Santos 2009 Trusted Cloud Service Platform Architecture Trusted cloud computing platform Bhensook and Senivongse 2012 12 weighted scoring model CSA CEE Summit 2016, Ljubljana, Slovenia
Other methodologies for Trustworthiness Cheng 2012 Tanimoto 2011 Risk Avoidance, Risk Mitigation, Risk Acceptance, and Risk Transference Santos 2009 Trusted Cloud Service Platform Architecture Trusted cloud computing platform Bhensook and Senivongse 2012 12 weighted scoring model CSA CEE Summit 2016, Ljubljana, Slovenia
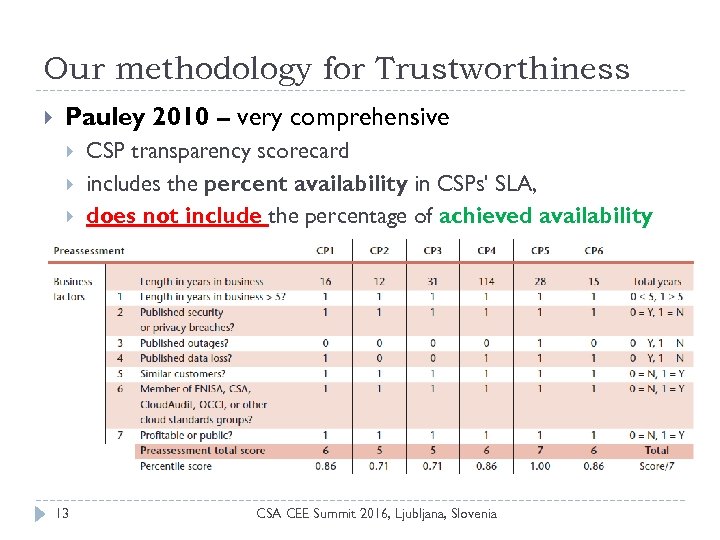 Our methodology for Trustworthiness Pauley 2010 – very comprehensive 13 CSP transparency scorecard includes the percent availability in CSPs' SLA, does not include the percentage of achieved availability CSA CEE Summit 2016, Ljubljana, Slovenia
Our methodology for Trustworthiness Pauley 2010 – very comprehensive 13 CSP transparency scorecard includes the percent availability in CSPs' SLA, does not include the percentage of achieved availability CSA CEE Summit 2016, Ljubljana, Slovenia
 Our methodology for Trustworthiness Achieved availability = reliability Choose the most reliable and trustworthy CSP, rather than the one that guarantee the greatest availability or indemnification. 14 CSA CEE Summit 2016, Ljubljana, Slovenia
Our methodology for Trustworthiness Achieved availability = reliability Choose the most reliable and trustworthy CSP, rather than the one that guarantee the greatest availability or indemnification. 14 CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 15 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 15 CSA CEE Summit 2016, Ljubljana, Slovenia
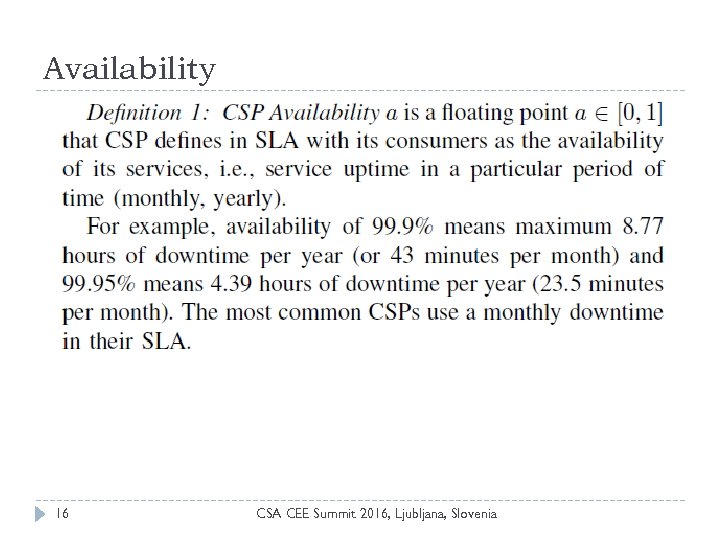 Availability 16 CSA CEE Summit 2016, Ljubljana, Slovenia
Availability 16 CSA CEE Summit 2016, Ljubljana, Slovenia
 Indemnification Google Microsoft offers credits and subscription extension, offers money reimbursement. Mission critical data and application unavailability can provide a grater loss than CSP's indemnification. 17 CSA CEE Summit 2016, Ljubljana, Slovenia
Indemnification Google Microsoft offers credits and subscription extension, offers money reimbursement. Mission critical data and application unavailability can provide a grater loss than CSP's indemnification. 17 CSA CEE Summit 2016, Ljubljana, Slovenia
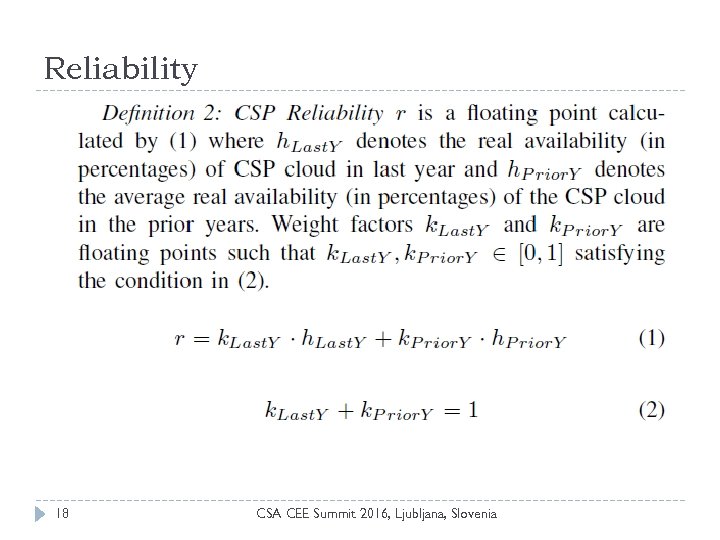 Reliability 18 CSA CEE Summit 2016, Ljubljana, Slovenia
Reliability 18 CSA CEE Summit 2016, Ljubljana, Slovenia
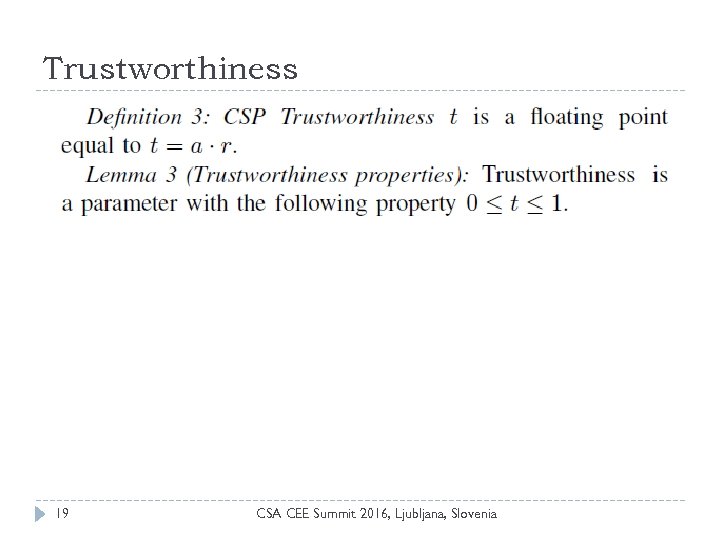 Trustworthiness 19 CSA CEE Summit 2016, Ljubljana, Slovenia
Trustworthiness 19 CSA CEE Summit 2016, Ljubljana, Slovenia
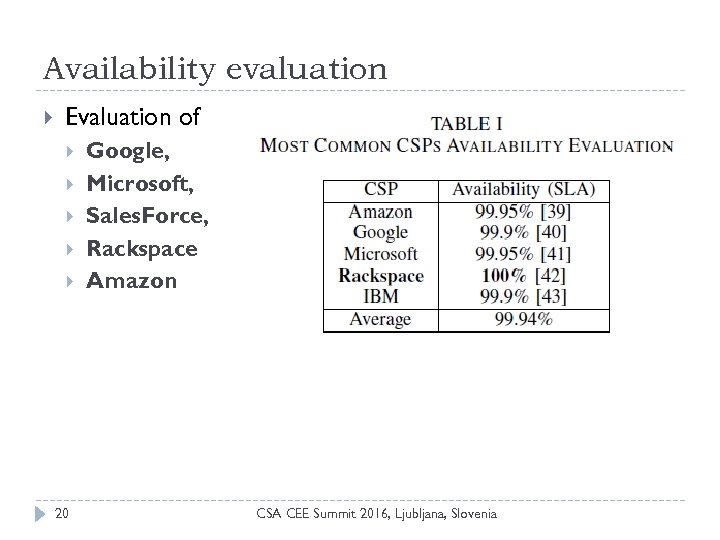 Availability evaluation Evaluation of 20 Google, Microsoft, Sales. Force, Rackspace Amazon CSA CEE Summit 2016, Ljubljana, Slovenia
Availability evaluation Evaluation of 20 Google, Microsoft, Sales. Force, Rackspace Amazon CSA CEE Summit 2016, Ljubljana, Slovenia
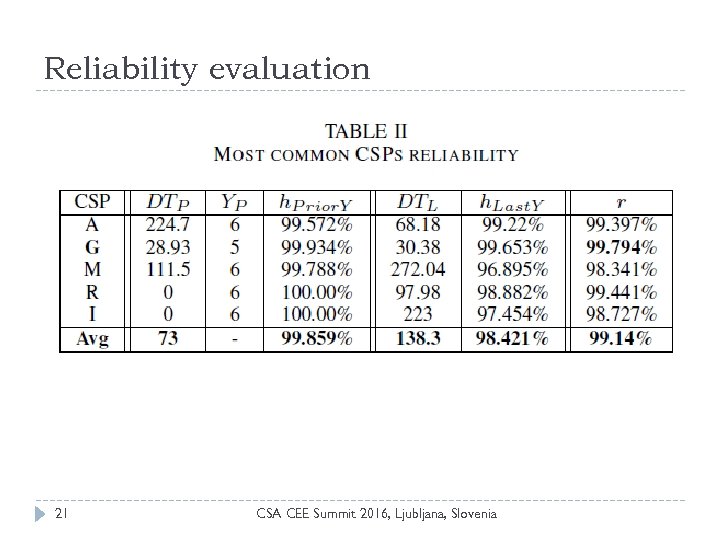 Reliability evaluation 21 CSA CEE Summit 2016, Ljubljana, Slovenia
Reliability evaluation 21 CSA CEE Summit 2016, Ljubljana, Slovenia
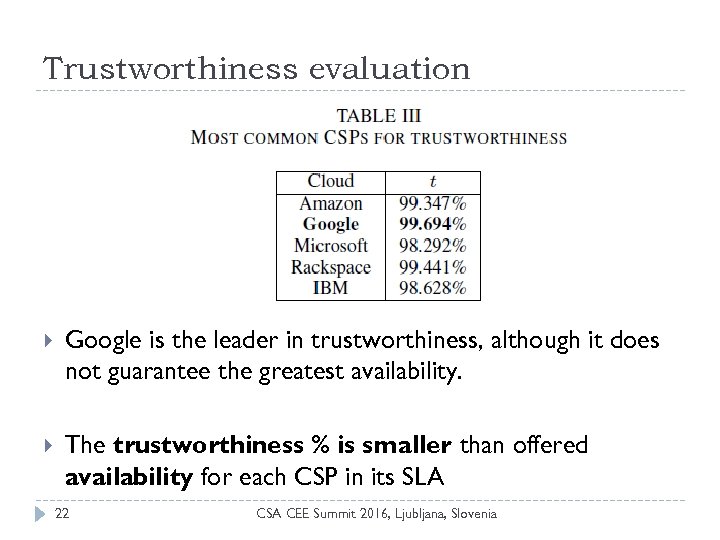 Trustworthiness evaluation Google is the leader in trustworthiness, although it does not guarantee the greatest availability. The trustworthiness % is smaller than offered availability for each CSP in its SLA 22 CSA CEE Summit 2016, Ljubljana, Slovenia
Trustworthiness evaluation Google is the leader in trustworthiness, although it does not guarantee the greatest availability. The trustworthiness % is smaller than offered availability for each CSP in its SLA 22 CSA CEE Summit 2016, Ljubljana, Slovenia
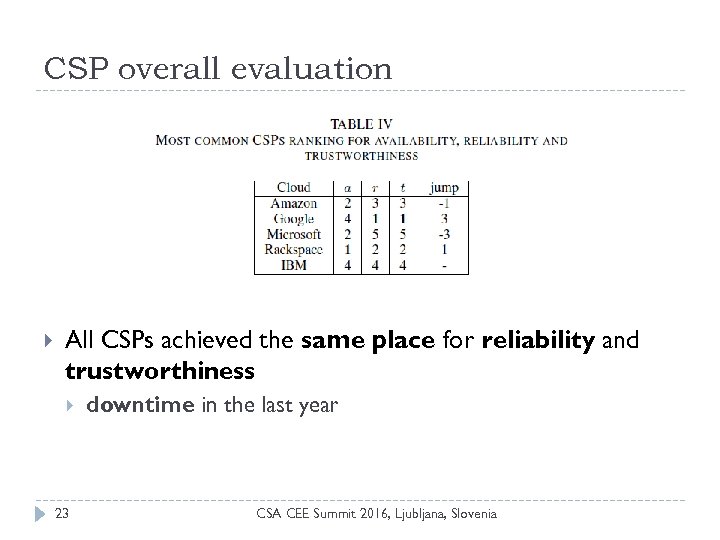 CSP overall evaluation All CSPs achieved the same place for reliability and trustworthiness 23 downtime in the last year CSA CEE Summit 2016, Ljubljana, Slovenia
CSP overall evaluation All CSPs achieved the same place for reliability and trustworthiness 23 downtime in the last year CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 24 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 24 CSA CEE Summit 2016, Ljubljana, Slovenia
 ISMS CSPs can mitigate the risks of security incidents if they implement some international security standards Some CSPs offer security features to their consumers ISMS Metrics 3 1 In-depth audit or certified with some audit standard such as SAS 70 or COBIT 0 25 ISO 27001 or NIST 800 -53 or equivalent No ISMS implemented CSA CEE Summit 2016, Ljubljana, Slovenia
ISMS CSPs can mitigate the risks of security incidents if they implement some international security standards Some CSPs offer security features to their consumers ISMS Metrics 3 1 In-depth audit or certified with some audit standard such as SAS 70 or COBIT 0 25 ISO 27001 or NIST 800 -53 or equivalent No ISMS implemented CSA CEE Summit 2016, Ljubljana, Slovenia
 Cloud. Cert Having ISMS is not enough ISO 27001 is not fully compliant with additional cloud security challenges Cloud. Cert parameter determining a level of the CSA Security, Trust & Assurance Registry (STAR) level Introduce ISO 27017 in Cloud. Cert ? ! 26 CSA CEE Summit 2016, Ljubljana, Slovenia
Cloud. Cert Having ISMS is not enough ISO 27001 is not fully compliant with additional cloud security challenges Cloud. Cert parameter determining a level of the CSA Security, Trust & Assurance Registry (STAR) level Introduce ISO 27017 in Cloud. Cert ? ! 26 CSA CEE Summit 2016, Ljubljana, Slovenia
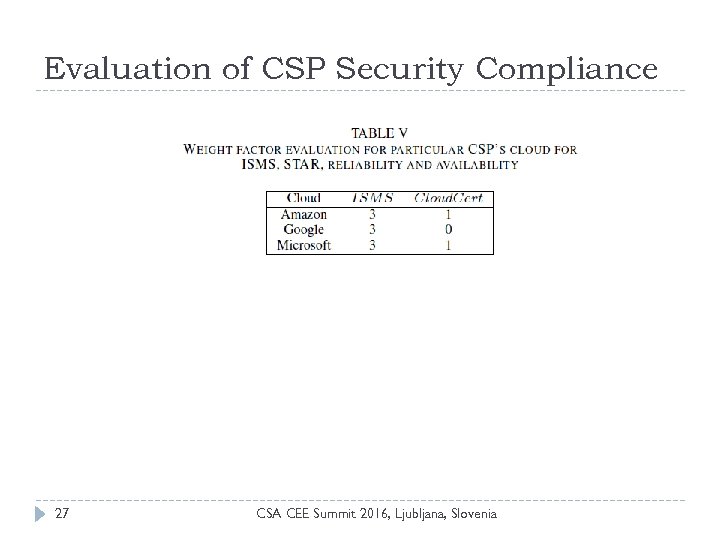 Evaluation of CSP Security Compliance 27 CSA CEE Summit 2016, Ljubljana, Slovenia
Evaluation of CSP Security Compliance 27 CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 28 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 28 CSA CEE Summit 2016, Ljubljana, Slovenia
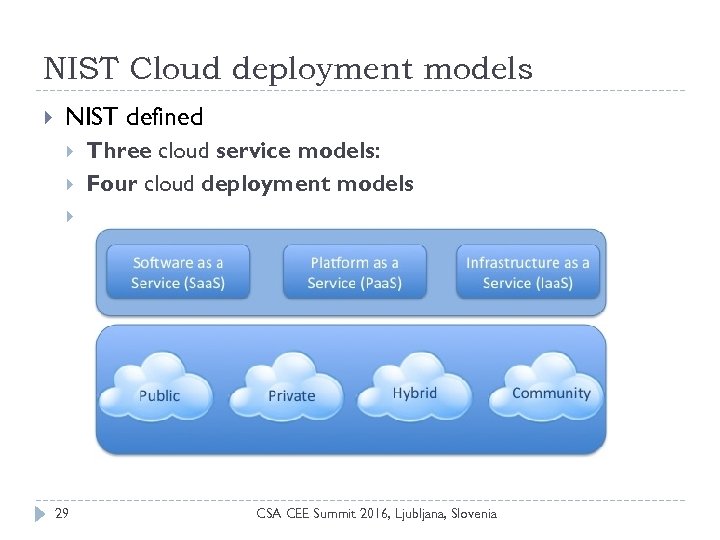 NIST Cloud deployment models NIST defined Three cloud service models: Four cloud deployment models 29 CSA CEE Summit 2016, Ljubljana, Slovenia
NIST Cloud deployment models NIST defined Three cloud service models: Four cloud deployment models 29 CSA CEE Summit 2016, Ljubljana, Slovenia
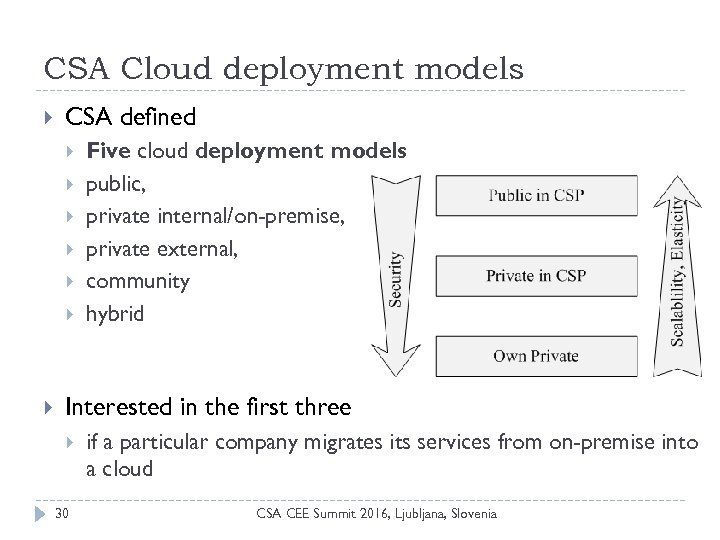 CSA Cloud deployment models CSA defined Five cloud deployment models public, private internal/on-premise, private external, community hybrid Interested in the first three 30 if a particular company migrates its services from on-premise into a cloud CSA CEE Summit 2016, Ljubljana, Slovenia
CSA Cloud deployment models CSA defined Five cloud deployment models public, private internal/on-premise, private external, community hybrid Interested in the first three 30 if a particular company migrates its services from on-premise into a cloud CSA CEE Summit 2016, Ljubljana, Slovenia
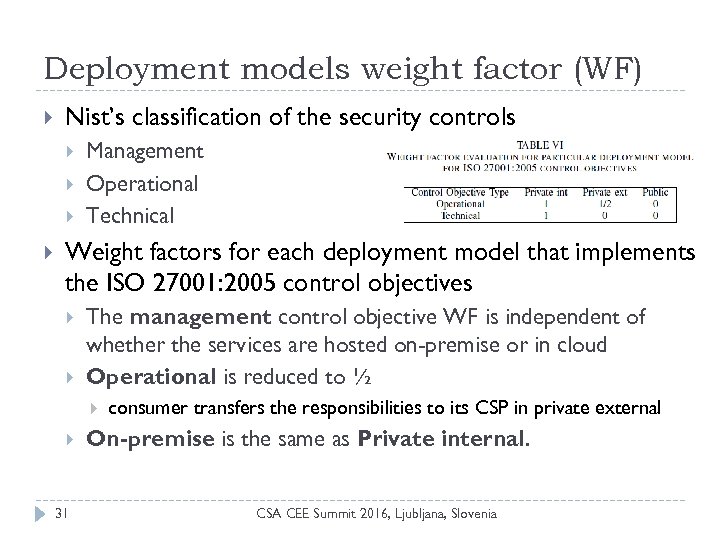 Deployment models weight factor (WF) Nist’s classification of the security controls Management Operational Technical Weight factors for each deployment model that implements the ISO 27001: 2005 control objectives The management control objective WF is independent of whether the services are hosted on-premise or in cloud Operational is reduced to ½ 31 consumer transfers the responsibilities to its CSP in private external On-premise is the same as Private internal. CSA CEE Summit 2016, Ljubljana, Slovenia
Deployment models weight factor (WF) Nist’s classification of the security controls Management Operational Technical Weight factors for each deployment model that implements the ISO 27001: 2005 control objectives The management control objective WF is independent of whether the services are hosted on-premise or in cloud Operational is reduced to ½ 31 consumer transfers the responsibilities to its CSP in private external On-premise is the same as Private internal. CSA CEE Summit 2016, Ljubljana, Slovenia
 ISO 27001 Control objective evaluation 17 control objectives are evaluated as operational 9 as technical control objectives 32 CSA CEE Summit 2016, Ljubljana, Slovenia
ISO 27001 Control objective evaluation 17 control objectives are evaluated as operational 9 as technical control objectives 32 CSA CEE Summit 2016, Ljubljana, Slovenia
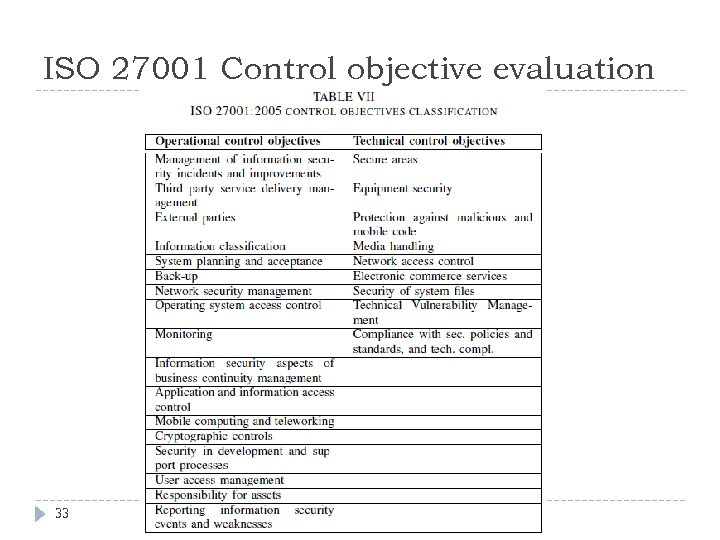 ISO 27001 Control objective evaluation 33 CSA CEE Summit 2016, Ljubljana, Slovenia
ISO 27001 Control objective evaluation 33 CSA CEE Summit 2016, Ljubljana, Slovenia
 ISO 27001 Control objective evaluation Example of evaluation Operating system access controls the access to operating systems completely in internal private cloud (both guest and host operating systems). controls the access to operating systems partially in external private cloud (only guest operating systems) and evaluate with 1/2 does not control the access to operating systems in public cloud (neither guest nor host) 34 evaluate with 1; evaluate it with 0. CSA CEE Summit 2016, Ljubljana, Slovenia
ISO 27001 Control objective evaluation Example of evaluation Operating system access controls the access to operating systems completely in internal private cloud (both guest and host operating systems). controls the access to operating systems partially in external private cloud (only guest operating systems) and evaluate with 1/2 does not control the access to operating systems in public cloud (neither guest nor host) 34 evaluate with 1; evaluate it with 0. CSA CEE Summit 2016, Ljubljana, Slovenia
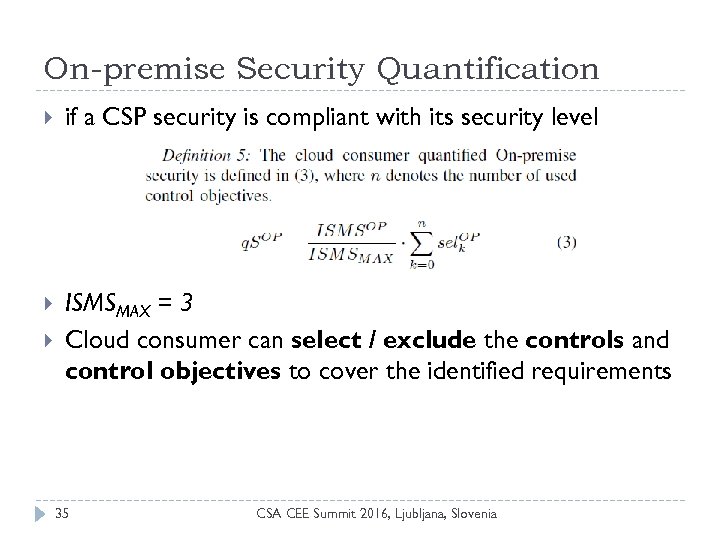 On-premise Security Quantification if a CSP security is compliant with its security level ISMSMAX = 3 Cloud consumer can select / exclude the controls and control objectives to cover the identified requirements 35 CSA CEE Summit 2016, Ljubljana, Slovenia
On-premise Security Quantification if a CSP security is compliant with its security level ISMSMAX = 3 Cloud consumer can select / exclude the controls and control objectives to cover the identified requirements 35 CSA CEE Summit 2016, Ljubljana, Slovenia
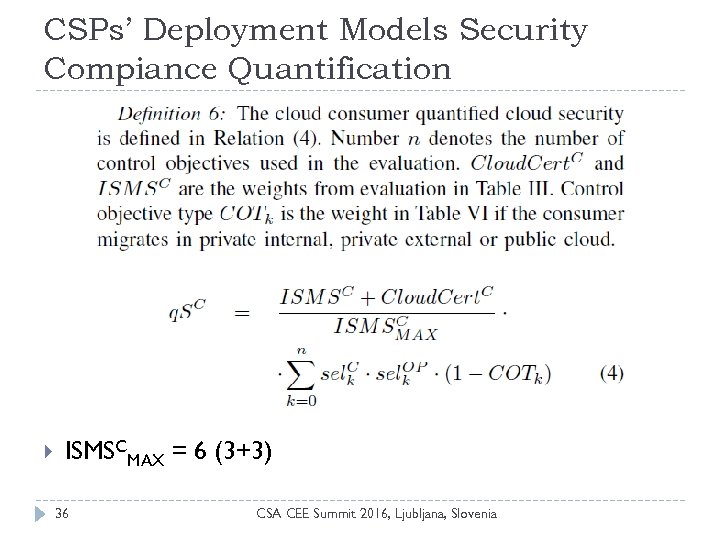 CSPs’ Deployment Models Security Compiance Quantification ISMSCMAX = 6 (3+3) 36 CSA CEE Summit 2016, Ljubljana, Slovenia
CSPs’ Deployment Models Security Compiance Quantification ISMSCMAX = 6 (3+3) 36 CSA CEE Summit 2016, Ljubljana, Slovenia
 CSPs’ Deployment Models Security Compiance Quantification Since the cloud consumer transfers some of the responsibilities to CSP, its COTk is opposite, i. e. , 1 – COTk 37 CSA CEE Summit 2016, Ljubljana, Slovenia
CSPs’ Deployment Models Security Compiance Quantification Since the cloud consumer transfers some of the responsibilities to CSP, its COTk is opposite, i. e. , 1 – COTk 37 CSA CEE Summit 2016, Ljubljana, Slovenia
 Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 38 CSA CEE Summit 2016, Ljubljana, Slovenia
Agenda State of the art Related work Methodology for CSP’s Trustworthiness A Methodology for Evaluation of CSP Security Compliance Putting it all together Evaluation of most common CSPs’ Trustworthiness On-premise and Cloud Security Compliance Quantification Conclusion 38 CSA CEE Summit 2016, Ljubljana, Slovenia
 Discussion / Conclusion ISO 27001 is more detailed standard compared to the COBIT certificate Do not include the CSPs' employees certificates into our evaluation since implementing the ISMS assures the employee security awareness COBIT or other related certificates is evaluated with 1, ISO 27001 or NIST SP 800 -53 with 3. all employees should have CISSP, CISM or other security certification; otherwise this control is irrelevant consumer should trust more on comprehend external audit of relevant certified authorities, rather than CSP's employees Compliance with different cloud deployment models 39 CSA CEE Summit 2016, Ljubljana, Slovenia
Discussion / Conclusion ISO 27001 is more detailed standard compared to the COBIT certificate Do not include the CSPs' employees certificates into our evaluation since implementing the ISMS assures the employee security awareness COBIT or other related certificates is evaluated with 1, ISO 27001 or NIST SP 800 -53 with 3. all employees should have CISSP, CISM or other security certification; otherwise this control is irrelevant consumer should trust more on comprehend external audit of relevant certified authorities, rather than CSP's employees Compliance with different cloud deployment models 39 CSA CEE Summit 2016, Ljubljana, Slovenia
 40 CSA CEE Summit 2016, Ljubljana, Slovenia
40 CSA CEE Summit 2016, Ljubljana, Slovenia


