 A hacker Grid technology Security issues Andrey Nifatov sparcsolaris@mail 333. com
A hacker Grid technology Security issues Andrey Nifatov sparcsolaris@mail 333. com
 Terms • Globus is a US government-funded project that provides software tools that allow you to build grids and grid-based applications. • Grid is a distributed computational tool that allows you to use geographically distributed resources for single computational project. * “Grid computing : A practical guide to technology and applications”
Terms • Globus is a US government-funded project that provides software tools that allow you to build grids and grid-based applications. • Grid is a distributed computational tool that allows you to use geographically distributed resources for single computational project. * “Grid computing : A practical guide to technology and applications”
 Virtual Organization • The wide spectrum of problems, are associated with resource sharing for virtual organization • VOs “share geographically distributed recourses, assuming the absence of global controller, and an existing trust relationship”
Virtual Organization • The wide spectrum of problems, are associated with resource sharing for virtual organization • VOs “share geographically distributed recourses, assuming the absence of global controller, and an existing trust relationship”
 Virtual Organization • VO can be large or small, static or dynamic • They may be only created to solve specific problem
Virtual Organization • VO can be large or small, static or dynamic • They may be only created to solve specific problem
 Virtual Organization
Virtual Organization
 Differences between Grids and the older distributed tools • Grid supports varied systems • Grid could involve almost unlimited number of computational resources (the Internet) • Security was considered a primary focus
Differences between Grids and the older distributed tools • Grid supports varied systems • Grid could involve almost unlimited number of computational resources (the Internet) • Security was considered a primary focus
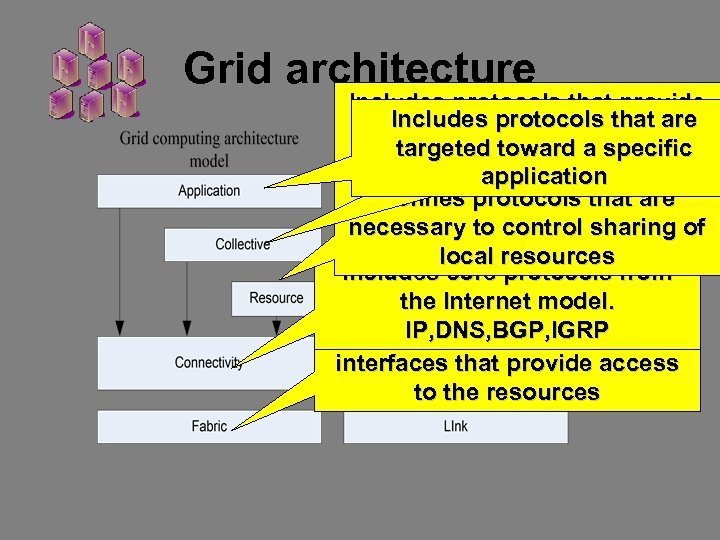 Grid architecture Includes protocols that provide Includes protocols that are system oriented capabilities targeted toward a specific application Defines protocols that are necessary to control sharing of local resources Includes core protocols from the Internet model. IP, DNS, BGP, IGRP Includes protocols and interfaces that provide access to the resources
Grid architecture Includes protocols that provide Includes protocols that are system oriented capabilities targeted toward a specific application Defines protocols that are necessary to control sharing of local resources Includes core protocols from the Internet model. IP, DNS, BGP, IGRP Includes protocols and interfaces that provide access to the resources
 Globus uses Certificate Authority • All grid resources need to be signed by a CA. • Registrant Authority works together with CA. • The RA approves or rejects request for certificate and forwards information to CA.
Globus uses Certificate Authority • All grid resources need to be signed by a CA. • Registrant Authority works together with CA. • The RA approves or rejects request for certificate and forwards information to CA.
 Certificate Authority • Before CA can sign certificates for others, it must sign and issue certificates for itself. • CA randomly generates its own key pair • CA protects its private key • CA creates its own certificate its info • CA signs its certificate with its private key
Certificate Authority • Before CA can sign certificates for others, it must sign and issue certificates for itself. • CA randomly generates its own key pair • CA protects its private key • CA creates its own certificate its info • CA signs its certificate with its private key
 Certificate Authority A hacker • Thus, its private key is sensitive to attacks from hackers. • The most famous way to protect involves special hardware which doesn’t have network connection. The private key is stored inside the hardware and never leaves it. The hardware could support a smart card processor, if this is not very expensive tool. If this is not the case, dedicated hardware CA may be involved.
Certificate Authority A hacker • Thus, its private key is sensitive to attacks from hackers. • The most famous way to protect involves special hardware which doesn’t have network connection. The private key is stored inside the hardware and never leaves it. The hardware could support a smart card processor, if this is not very expensive tool. If this is not the case, dedicated hardware CA may be involved.
 Grid certificate • • • Provides identity Contains your information Contains your public key Will be used to decrypt the SSL session ID Has unique Distinguished Name (DN) Also called X. 509
Grid certificate • • • Provides identity Contains your information Contains your public key Will be used to decrypt the SSL session ID Has unique Distinguished Name (DN) Also called X. 509
 Remote delegation: Grid proxy • Acts as yourself: • Submits a request to the foreign host on your behalf. Also called remote delegation • Store proxy’s private key on the remote machine
Remote delegation: Grid proxy • Acts as yourself: • Submits a request to the foreign host on your behalf. Also called remote delegation • Store proxy’s private key on the remote machine
 Conclusion • Supercomputers are expensive and A hacker specialized • Grid computers solve problems by A hacker using multiple computes instead of a single computer. • This shift produces a dramatic A hacker increase in the speed and decrease in A hacker the cost. • However, it is also a shift from an environment that is secure by definition to one that is public and secured like the Internet. Thus, security issues were considered a primary focus on the way to developing this tool.
Conclusion • Supercomputers are expensive and A hacker specialized • Grid computers solve problems by A hacker using multiple computes instead of a single computer. • This shift produces a dramatic A hacker increase in the speed and decrease in A hacker the cost. • However, it is also a shift from an environment that is secure by definition to one that is public and secured like the Internet. Thus, security issues were considered a primary focus on the way to developing this tool.