83c08692b7d620d63c5421cde341d610.ppt
- Количество слайдов: 20
 A Curriculum Development for Information Security Manager Using DACUM Ki-Yoon Kim Kwangwoon University, Korea min 1203@daisy. kwangwoon. ac. kr Ken Surendran Southeast Missouri State University ksurendran@semovm. semo. edu
A Curriculum Development for Information Security Manager Using DACUM Ki-Yoon Kim Kwangwoon University, Korea min 1203@daisy. kwangwoon. ac. kr Ken Surendran Southeast Missouri State University ksurendran@semovm. semo. edu
 CONTENTS 1. 2. 3. 4. 5. INTRODUCTION (ISM) JOB ANALYSIS METHODOLOGY RESULTS OF JOB ANALYSIS ON ISM (INFORMATION SECURITY MANAGER) CURRICULUM DEVELOPMENT FOR ISM CONCLUSION
CONTENTS 1. 2. 3. 4. 5. INTRODUCTION (ISM) JOB ANALYSIS METHODOLOGY RESULTS OF JOB ANALYSIS ON ISM (INFORMATION SECURITY MANAGER) CURRICULUM DEVELOPMENT FOR ISM CONCLUSION
 1. INTRODUCTION • In information and technology security, a risk is any hazard or danger to which a system or its components (e. g. , hardware, software, information, or data) is subjected. • The job of an ISM (Information Security Manager) to ensure confidentiality, integrity, and availability, which could be compromised when those risks actually surface. • DACUM (Developing A CUrriculu. M) is a job analysis method used to create descriptions for new education /training programs.
1. INTRODUCTION • In information and technology security, a risk is any hazard or danger to which a system or its components (e. g. , hardware, software, information, or data) is subjected. • The job of an ISM (Information Security Manager) to ensure confidentiality, integrity, and availability, which could be compromised when those risks actually surface. • DACUM (Developing A CUrriculu. M) is a job analysis method used to create descriptions for new education /training programs.
 2. JOB ANALYSIS METHODOLOGY 2. 1 DACUM - a Job Analysis Method 2. 2 DACUM Process for ISM
2. JOB ANALYSIS METHODOLOGY 2. 1 DACUM - a Job Analysis Method 2. 2 DACUM Process for ISM
 2. 1 DACUM - a Job Analysis Method • What is DACUM? : DACUM (Developing A Curriculum) is a job analysis technique. The DACUM process is used to determine the competencies that should be addressed in a training curriculum for a specific occupation. • When: Dec. 1999 – Jan. 2000 • Where: KRIVET (Korea Research Institute of Vocational Education and Training) in Korea • Who: DACUM committee consisting of 5 employees (ISMs) and 5 professors • How: DACUM process (modified) • Why: A Curriculum Development for ISM
2. 1 DACUM - a Job Analysis Method • What is DACUM? : DACUM (Developing A Curriculum) is a job analysis technique. The DACUM process is used to determine the competencies that should be addressed in a training curriculum for a specific occupation. • When: Dec. 1999 – Jan. 2000 • Where: KRIVET (Korea Research Institute of Vocational Education and Training) in Korea • Who: DACUM committee consisting of 5 employees (ISMs) and 5 professors • How: DACUM process (modified) • Why: A Curriculum Development for ISM
 • • Facilitator – Computer Science Education Subject matter Experts: five; – Security R&D Manager– 1 – Security product implementer – 1 – Security Managers – 2 – Consultant (Security Integration) – 1 – Professors – 5: MIS – 2; CS-2: CE – 1. (Korea Inst of Info Security & Cryptology)
• • Facilitator – Computer Science Education Subject matter Experts: five; – Security R&D Manager– 1 – Security product implementer – 1 – Security Managers – 2 – Consultant (Security Integration) – 1 – Professors – 5: MIS – 2; CS-2: CE – 1. (Korea Inst of Info Security & Cryptology)
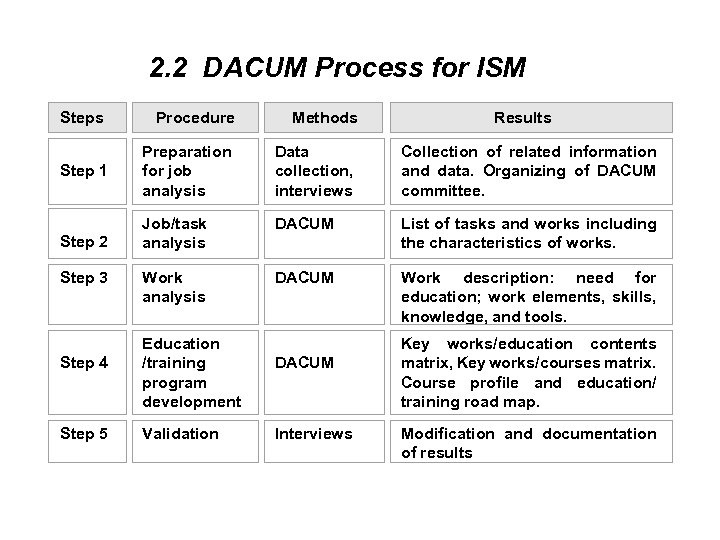 2. 2 DACUM Process for ISM Steps Procedure Methods Step 1 Preparation for job analysis Data collection, interviews Step 2 Step 3 Step 4 Step 5 Results Collection of related information and data. Organizing of DACUM committee. Job/task DACUM analysis List of tasks and works including the characteristics of works. Work analysis Work description: need for education; work elements, skills, knowledge, and tools. Education /training program development Validation DACUM Interviews Key works/education contents matrix, Key works/courses matrix. Course profile and education/ training road map. Modification and documentation of results
2. 2 DACUM Process for ISM Steps Procedure Methods Step 1 Preparation for job analysis Data collection, interviews Step 2 Step 3 Step 4 Step 5 Results Collection of related information and data. Organizing of DACUM committee. Job/task DACUM analysis List of tasks and works including the characteristics of works. Work analysis Work description: need for education; work elements, skills, knowledge, and tools. Education /training program development Validation DACUM Interviews Key works/education contents matrix, Key works/courses matrix. Course profile and education/ training road map. Modification and documentation of results
 3. RESULTS OF JOB ANALYSIS ON INFORMATION SECURITY MANAGER 3. 1 3. 2 3. 3 3. 4 Job of ISM Job Description and Work List of ISM Key works (relating to education) Example of Work description : Risk Analysis (Draft Occupational description – not discussed here)
3. RESULTS OF JOB ANALYSIS ON INFORMATION SECURITY MANAGER 3. 1 3. 2 3. 3 3. 4 Job of ISM Job Description and Work List of ISM Key works (relating to education) Example of Work description : Risk Analysis (Draft Occupational description – not discussed here)
 3. 1 Job of Information Security Manager Task A. Security policy A-1. Analysis of security requirements B. Risk management B-1. Risk analysis C. Safeguard Implementa -tion & training C-1. Safeguard implementa -tion D. Safeguard management D-1. Operation & Maintenance Work A-2. Document security policy B-2. Selection of safeguard B-3. Test of selected safeguard B-4. Development of security guideline C-2. Education and training D-2. Security udit a & review B-5. Security aggregate planning D-3. Emergency Response to security incidents D-4. Monitoring
3. 1 Job of Information Security Manager Task A. Security policy A-1. Analysis of security requirements B. Risk management B-1. Risk analysis C. Safeguard Implementa -tion & training C-1. Safeguard implementa -tion D. Safeguard management D-1. Operation & Maintenance Work A-2. Document security policy B-2. Selection of safeguard B-3. Test of selected safeguard B-4. Development of security guideline C-2. Education and training D-2. Security udit a & review B-5. Security aggregate planning D-3. Emergency Response to security incidents D-4. Monitoring
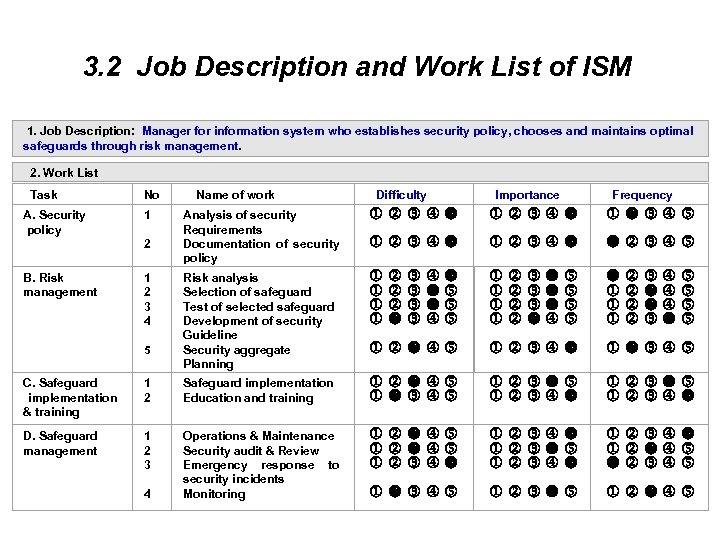 3. 2 Job Description and Work List of ISM 1. Job Description: Manager for information system who establishes security policy, chooses and maintains optimal safeguards through risk management. 2. Work List Task No Name of work Difficulty Importance Frequency A. Security policy 1 2 Analysis of security Requirements Documentation of security policy B. Risk management 1 2 3 4 5 Risk analysis Selection of safeguard Test of selected safeguard Development of security Guideline Security aggregate Planning C. Safeguard implementation & training 1 2 Safeguard implementation Education and training D. Safeguard management 1 2 3 4 Operations & Maintenance Security audit & Review Emergency response to security incidents Monitoring
3. 2 Job Description and Work List of ISM 1. Job Description: Manager for information system who establishes security policy, chooses and maintains optimal safeguards through risk management. 2. Work List Task No Name of work Difficulty Importance Frequency A. Security policy 1 2 Analysis of security Requirements Documentation of security policy B. Risk management 1 2 3 4 5 Risk analysis Selection of safeguard Test of selected safeguard Development of security Guideline Security aggregate Planning C. Safeguard implementation & training 1 2 Safeguard implementation Education and training D. Safeguard management 1 2 3 4 Operations & Maintenance Security audit & Review Emergency response to security incidents Monitoring
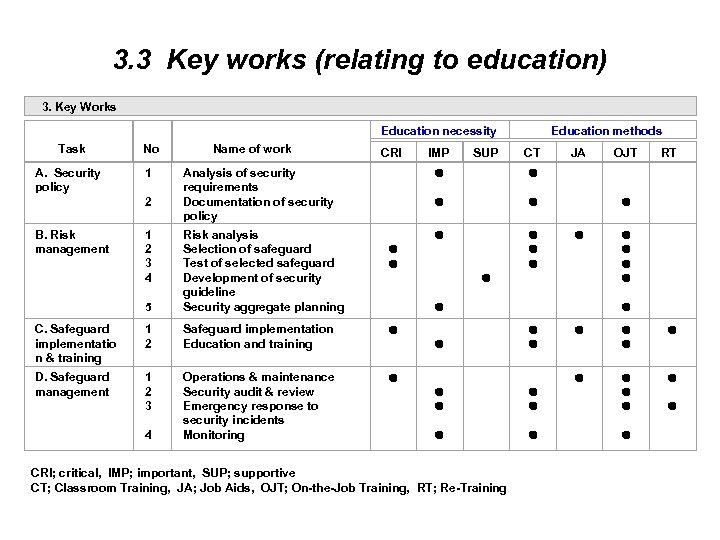 3. 3 Key works (relating to education) 3. Key Works Task No Name of work Education necessity Education methods CRI IMP SUP CT JA OJT RT A. Security policy 1 2 Analysis of security requirements Documentation of security policy B. Risk management 1 2 3 4 5 Risk analysis Selection of safeguard Test of selected safeguard Development of security guideline Security aggregate planning C. Safeguard implementatio n & training 1 2 Safeguard implementation Education and training D. Safeguard management 1 2 3 4 Operations & maintenance Security audit & review Emergency response to security incidents Monitoring CRI; critical, IMP; important, SUP; supportive CT; Classroom Training, JA; Job Aids, OJT; On-the-Job Training, RT; Re-Training
3. 3 Key works (relating to education) 3. Key Works Task No Name of work Education necessity Education methods CRI IMP SUP CT JA OJT RT A. Security policy 1 2 Analysis of security requirements Documentation of security policy B. Risk management 1 2 3 4 5 Risk analysis Selection of safeguard Test of selected safeguard Development of security guideline Security aggregate planning C. Safeguard implementatio n & training 1 2 Safeguard implementation Education and training D. Safeguard management 1 2 3 4 Operations & maintenance Security audit & review Emergency response to security incidents Monitoring CRI; critical, IMP; important, SUP; supportive CT; Classroom Training, JA; Job Aids, OJT; On-the-Job Training, RT; Re-Training
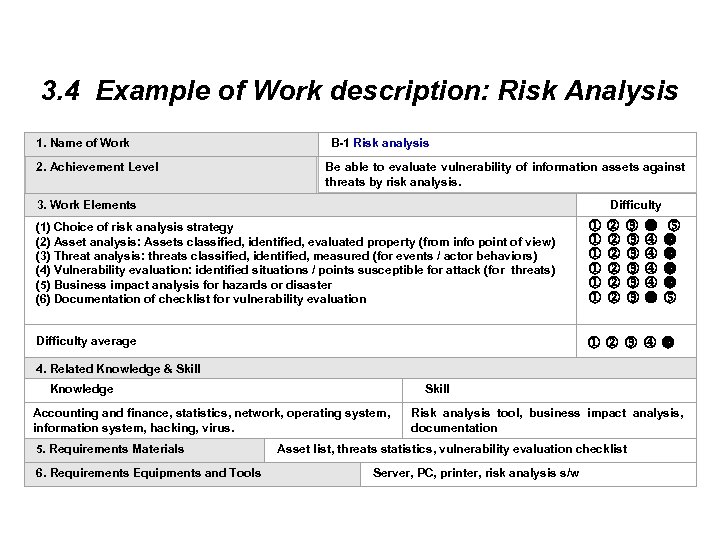 3. 4 Example of Work description: Risk Analysis 1. Name of Work B-1 Risk analysis 2. Achievement Level Be able to evaluate vulnerability of information assets against threats by risk analysis. 3. Work Elements Difficulty (1) Choice of risk analysis strategy (2) Asset analysis: Assets classified, identified, evaluated property (from info point of view) (3) Threat analysis: threats classified, identified, measured (for events / actor behaviors) (4) Vulnerability evaluation: identified situations / points susceptible for attack (for threats) (5) Business impact analysis for hazards or disaster (6) Documentation of checklist for vulnerability evaluation Difficulty average 4. Related Knowledge & Skill Knowledge Skill Accounting and finance, statistics, network, operating system, information system, hacking, virus. Risk analysis tool, business impact analysis, documentation 5. Requirements Materials 6. Requirements Equipments and Tools Asset list, threats statistics, vulnerability evaluation checklist Server, PC, printer, risk analysis s/w
3. 4 Example of Work description: Risk Analysis 1. Name of Work B-1 Risk analysis 2. Achievement Level Be able to evaluate vulnerability of information assets against threats by risk analysis. 3. Work Elements Difficulty (1) Choice of risk analysis strategy (2) Asset analysis: Assets classified, identified, evaluated property (from info point of view) (3) Threat analysis: threats classified, identified, measured (for events / actor behaviors) (4) Vulnerability evaluation: identified situations / points susceptible for attack (for threats) (5) Business impact analysis for hazards or disaster (6) Documentation of checklist for vulnerability evaluation Difficulty average 4. Related Knowledge & Skill Knowledge Skill Accounting and finance, statistics, network, operating system, information system, hacking, virus. Risk analysis tool, business impact analysis, documentation 5. Requirements Materials 6. Requirements Equipments and Tools Asset list, threats statistics, vulnerability evaluation checklist Server, PC, printer, risk analysis s/w
 4. CURRICULUM DEVELOPMENT FOR ISM 4. 1 Key Works/Education Contents Matrix 4. 2 Key Works/Courses Matrix 4. 3 Example of Course Profile : Network Security I 4. 4 Education Training Road Map
4. CURRICULUM DEVELOPMENT FOR ISM 4. 1 Key Works/Education Contents Matrix 4. 2 Key Works/Courses Matrix 4. 3 Example of Course Profile : Network Security I 4. 4 Education Training Road Map
 4. 1. Education Contents 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. Information security law and standards Information system analysis and design System security technology Database Operating system Network security Intrusion detection and interception Network security technology Virus Hacking case Web security E-commerce security Accounting and finance Statistics Risk analysis Decision theory Cryptology
4. 1. Education Contents 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. Information security law and standards Information system analysis and design System security technology Database Operating system Network security Intrusion detection and interception Network security technology Virus Hacking case Web security E-commerce security Accounting and finance Statistics Risk analysis Decision theory Cryptology
 Key work / education contents mapping • Key Works Education Contents* 0 0 0 0 0 1 1 1 1 1 • • • • 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 Analysis of security requirements * * * Documentations of security policy * * Risk analysis * * * * Selection of safeguards * * * * * * Test of selected safeguard * * * * Security aggregate planning * * * * * Safeguard Implementation * * * * * * Education and training * * * Operation & maintenance * * Security audit & review * * Emergency response to incidents * * Monitoring * * * * *
Key work / education contents mapping • Key Works Education Contents* 0 0 0 0 0 1 1 1 1 1 • • • • 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 Analysis of security requirements * * * Documentations of security policy * * Risk analysis * * * * Selection of safeguards * * * * * * Test of selected safeguard * * * * Security aggregate planning * * * * * Safeguard Implementation * * * * * * Education and training * * * Operation & maintenance * * Security audit & review * * Emergency response to incidents * * Monitoring * * * * *
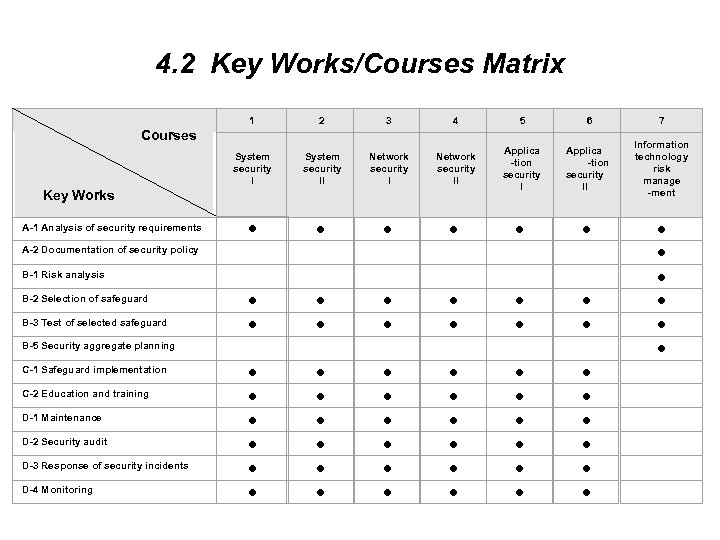 4. 2 Key Works/Courses Matrix Courses Key Works 1 2 3 4 5 6 7 System security II Network security II Applica -tion security I Applica -tion security II Information technology risk manage -ment A-1 Analysis of security requirements A-2 Documentation of security policy B-1 Risk analysis B-2 Selection of safeguard B-3 Test of selected safeguard C-1 Safeguard implementation C-2 Education and training D-1 Maintenance D-2 Security audit D-3 Response of security incidents D-4 Monitoring B-5 Security aggregate planning
4. 2 Key Works/Courses Matrix Courses Key Works 1 2 3 4 5 6 7 System security II Network security II Applica -tion security I Applica -tion security II Information technology risk manage -ment A-1 Analysis of security requirements A-2 Documentation of security policy B-1 Risk analysis B-2 Selection of safeguard B-3 Test of selected safeguard C-1 Safeguard implementation C-2 Education and training D-1 Maintenance D-2 Security audit D-3 Response of security incidents D-4 Monitoring B-5 Security aggregate planning
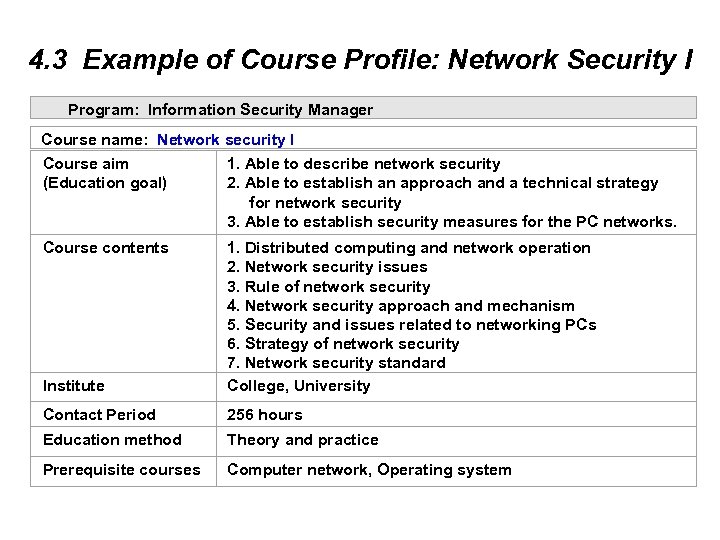 4. 3 Example of Course Profile: Network Security I Program: Information Security Manager Course name: Network security I Course aim 1. Able to describe network security (Education goal) 2. Able to establish an approach and a technical strategy for network security 3. Able to establish security measures for the PC networks. Course contents Institute 1. Distributed computing and network operation 2. Network security issues 3. Rule of network security 4. Network security approach and mechanism 5. Security and issues related to networking PCs 6. Strategy of network security 7. Network security standard College, University Contact Period 256 hours Education method Theory and practice Prerequisite courses Computer network, Operating system
4. 3 Example of Course Profile: Network Security I Program: Information Security Manager Course name: Network security I Course aim 1. Able to describe network security (Education goal) 2. Able to establish an approach and a technical strategy for network security 3. Able to establish security measures for the PC networks. Course contents Institute 1. Distributed computing and network operation 2. Network security issues 3. Rule of network security 4. Network security approach and mechanism 5. Security and issues related to networking PCs 6. Strategy of network security 7. Network security standard College, University Contact Period 256 hours Education method Theory and practice Prerequisite courses Computer network, Operating system
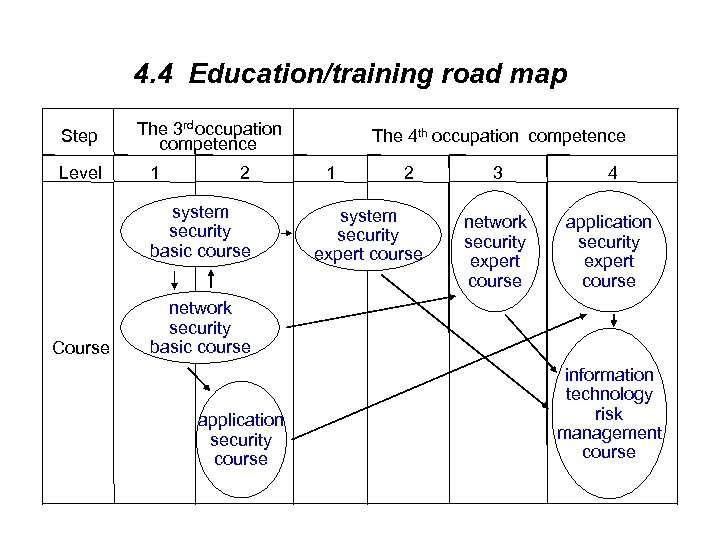 4. 4 Education/training road map Step Level The 3 rd occupation competence 1 2 system security basic course Course The 4 th occupation competence 1 2 system security expert course 3 4 network security expert course application security expert course network security basic course application security course information technology risk management course
4. 4 Education/training road map Step Level The 3 rd occupation competence 1 2 system security basic course Course The 4 th occupation competence 1 2 system security expert course 3 4 network security expert course application security expert course network security basic course application security course information technology risk management course
 5. CONCLUSION • • • There are 4 tasks and 13 works in the job of ISM. The 4 tasks of ISM are security policy (with two works), risk management (with five works), safeguard choice (two works), and safeguard maintenance management (four works). There are 18 education contents and 7 education courses in the education/training program for ISM. The primary methodological contribution has been the combination of DACUM and interviews including the final validation step in which the committee reviewed the feedback from industry and the academia. DACUM being a cost-effective approach this technique can be applied even to other educational programs to fine-tune them using the validation step. But, the worker-oriented instruments for job analysis have several limitations.
5. CONCLUSION • • • There are 4 tasks and 13 works in the job of ISM. The 4 tasks of ISM are security policy (with two works), risk management (with five works), safeguard choice (two works), and safeguard maintenance management (four works). There are 18 education contents and 7 education courses in the education/training program for ISM. The primary methodological contribution has been the combination of DACUM and interviews including the final validation step in which the committee reviewed the feedback from industry and the academia. DACUM being a cost-effective approach this technique can be applied even to other educational programs to fine-tune them using the validation step. But, the worker-oriented instruments for job analysis have several limitations.
 Questions? • Further work: on issues relating to ISM occupation • Question Time
Questions? • Further work: on issues relating to ISM occupation • Question Time


