d75d4083a3b07df3a212defd723646f3.ppt
- Количество слайдов: 109

A Blueprint for Handling Sensitive Data: Security, Privacy, and Other Considerations David Escalante Director, Computer Policy & Security Boston College Monday, July 30, 2007, 8: 30 am-12: 00 pm Campus Technology 2007 Washington, DC

Seminar Goals At the end of this session: You should feel comfortable discussing common cybersecurity risks plaguing higher education and computer users in general. You will have a list of key strategies to pursue for stopping the leakage of confidential/sensitive data. You will be introduced to several security resources and best practices to help you apply the key strategies.

Agenda (1) Overview and Introductions Creating a Security Risk-Aware Culture Defining Institutional Data Types Clarifying Responsibility and Accountability Reducing Access to Data Not Absolutely Essential

Agenda (2) Establishing & Implementing Stricter Controls Providing Awareness and Training Managing Sensitive Data Outreach Programs Verifying Compliance Putting It All Together Evaluation and Wrap-Up

Icebreaker Human Scavenger Hunt Instructions: § Take a moment to read entire list (front and back) § Obtain as many signatures as possible in the time allotted § An individual may sign your sheet only once § Fill in the blanks when space is provided

The Blueprint Confidential Data Handling Blueprint Purpose To provide a list of key strategies to follow for stopping the leakage of confidential/sensitive data. To provide a toolkit that constructs resources pertaining to confidential/sensitive data handling. https: //wiki. internet 2. edu/confluence/display/ secguide/Confidential+Data+Handling+Blueprint
The Blueprint Confidential Data Handling Blueprint Introduction Steps and ensuing sub-items are intended to provide a general roadmap Institutions will be at varying stages of progress Organized in a sequence that allows you to logically follow through each step Each item is recommended as an effective practice; state/local legal requirements, institutional policy, or campus culture might leave each institution approaching this differently
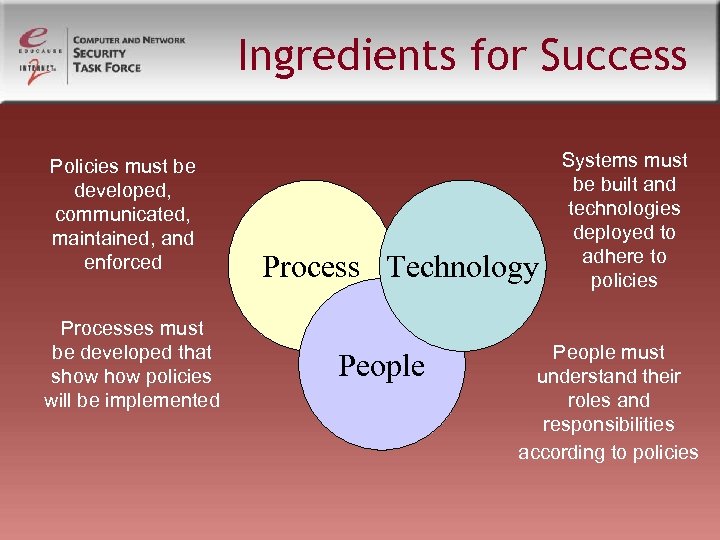
Ingredients for Success Policies must be developed, communicated, maintained, and enforced Processes must be developed that show policies will be implemented Process Technology People Systems must be built and technologies deployed to adhere to policies People must understand their roles and responsibilities according to policies

Step 1 Create a security risk-aware culture that includes an information security risk management program Sub-steps 1. 1 Institution-wide security risk management program 1. 2 Roles and responsibilities defined for overall information security at the central and distributed level 1. 3 Executive leadership support in the form of policies and governance actions

Step 1 Create a security risk-aware culture that includes an information security risk management program Sub-steps 1. 1 Institution-wide security risk management program 1. 2 Roles and responsibilities defined for overall information security at the central and distributed level 1. 3 Executive leadership support in the form of policies and governance actions
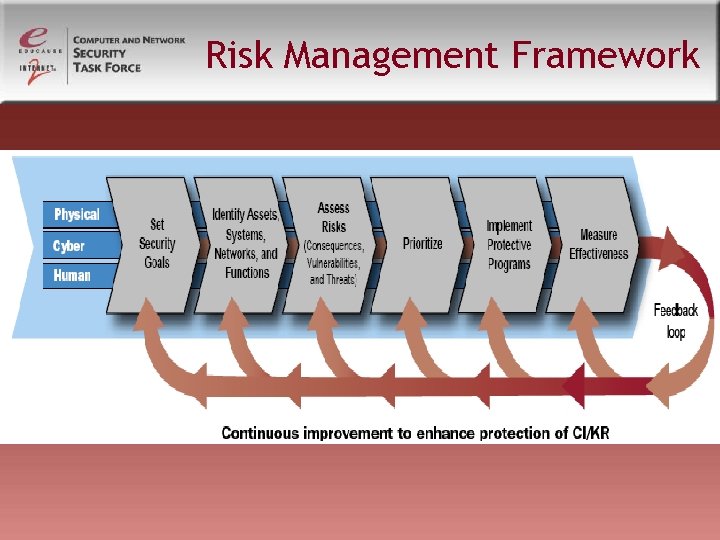
Risk Management Framework

Risk Assessment Framework Phase 0: Establish Risk Assessment Criteria for the Identification and Prioritization of Critical Assets Phase 1: Develop Initial Security Strategies Phase 2: Technological View – Identify Infrastructure Vulnerabilities Phase 3: Develop Security Strategy and Plans
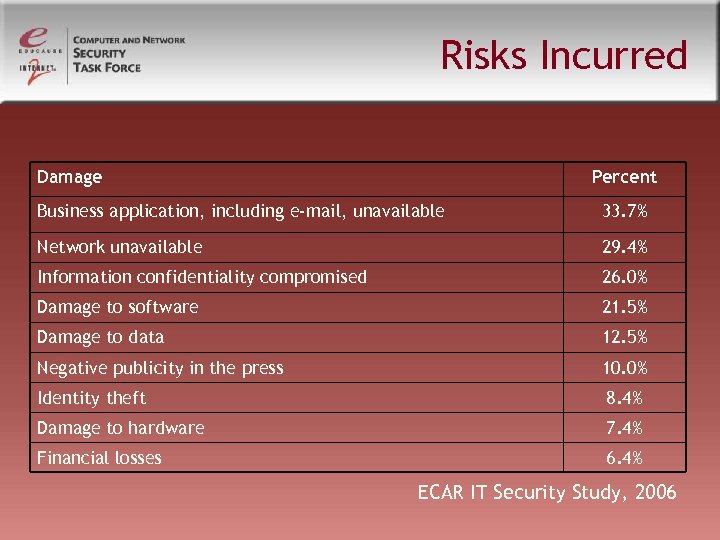
Risks Incurred Damage Percent Business application, including e-mail, unavailable 33. 7% Network unavailable 29. 4% Information confidentiality compromised 26. 0% Damage to software 21. 5% Damage to data 12. 5% Negative publicity in the press 10. 0% Identity theft 8. 4% Damage to hardware 7. 4% Financial losses 6. 4% ECAR IT Security Study, 2006

Risk Assessments 55 percent do some type of risk assessment But less than 9 percent cover all institutional systems and data. ECAR IT Security Study, 2006

Step 1 Create a security risk-aware culture that includes an information security risk management program Sub-steps 1. 1 Institution-wide security risk management program 1. 2 Roles and responsibilities defined for overall information security at the central and distributed level 1. 3 Executive leadership support in the form of policies and governance actions

Best Practices & Metrics Information Security Program Elements: Governance § Boards/Senior Executives/Shared Governance Management § Directors and Managers Technical § Central and Distributed IT Support Staff CISWG Final Report on Best Practices & Metrics

Governance Oversee Risk Management and Compliance Programs Pertaining to Information Security (e. g. , Sarbanes-Oxley, HIPAA, Gramm-Leach-Bliley) Approve and Adopt Broad Information Security Program Principles and Approve Assignment of Key Managers Responsible for Information Security Strive to Protect the Interests of all Stakeholders Dependent on Information Security Review Information Security Policies Regarding Strategic Partners and Other Third-parties Strive to Ensure Business Continuity Review Provisions for Internal and External Audits of the Information Security Program Collaborate with Management to Specify the Information Security Metrics to be Reported to the Board CISWG Final Report on Best Practices & Metrics

Management Establish Information Security Management Policies and Controls and Monitor Compliance Assign Information Security Roles, Responsibilities, Required Skills, and Enforce Role-based Information Access Privileges Assess Information Risks, Establish Risk Thresholds and Actively Manage Risk Mitigation Ensure Implementation of Information Security Requirements for Strategic Partners and Other Third-parties Identify and Classify Information Assets Implement and Test Business Continuity Plans Approve Information Systems Architecture during Acquisition, Development, Operations, and Maintenance Protect the Physical Environment Ensure Internal and External Audits of the Information Security Program with Timely Follow-up Collaborate with Security Staff to Specify the Information Security Metrics to be Reported to Management CISWG Final Report on Best Practices & Metrics

Technical User Identification and Authentication User Account Management User Privileges Configuration Management Event and Activity Logging and Monitoring Communications, Email, and Remote Access Security Malicious Code Protection, Including Viruses, Worms, and Trojans Software Change Management, including Patching Firewalls Data Encryption Backup and Recovery Incident and Vulnerability Detection and Response Collaborate with Management to Specify the Technical Metrics to be Reported to Management CISWG Final Report on Best Practices & Metrics

Responsibility for IT Security Officer (up to 35% from 22%) CIO (up to 14% from 8%) Other IT Directors (down to 50% from 67%)

IT Security Plan 11. 2 percent - a comprehensive IT security plan is in place 66. 6 percent - a partial plan is in place 20. 4 percent - no IT security plan is in place ECAR IT Security Study, 2006

Characteristics of Successful IT Security Programs Institutions with IT security plans in place characterize their IT security programs as more successful and feel more secure today. The respondents who believe their institution provides necessary resources give higher ratings for IT security program success and their current sense of IT security. The biggest barrier to IT security is lack of resources (64. 4 percent) and especially at smaller institutions, followed by an academic culture of openness and autonomy (49. 6 percent), and lack of awareness (36. 4 percent). ECAR IT Security Study, 2006

Step 1 Create a security risk-aware culture that includes an information security risk management program Sub-steps 1. 1 Institution-wide security risk management program 1. 2 Roles and responsibilities defined for overall information security at the central and distributed level 1. 3 Executive leadership support in the form of policies and governance actions

Information Security Governance If businesses, educational institutions, and nonprofit organizations are to make significant progress securing their information assets, executives must make information security an integral part of core business operations. There is no better way to accomplish this goal than to highlight it as part of the existing internal controls and policies that constitute corporate governance. Information Security Governance Report: Executive Summary

Info. Sec Governance Self Assessment Organizational Reliance on IT § E. g. , What is the impact of major system downtime on operations? Risk Management § E. g. , Has your organization conducted a risk assessment and identified critical assets? People § E. g. , Is there a person or organization that has information security as their primary duty? Processes § E. g. , Do you have official written information security policies and procedures? Technology § E. g. , Is sensitive data encrypted? Information Security Governance Assessment Tool for Higher Education

Policies in Place Individual employee responsibilities for information security practices (73%) Protection of organizational assets (73%) Managing privacy issues, including breaches of personal information (72%) Incident reporting and response (69%) Disaster recovery contingency planning (68%)

Policies in Place Investigation and correction of the causes of security failures (68%) Notification of security events to: individuals, the law, etc. (67%) Sharing, storing, and transmitting data (51%) Data classification, retention, and destruction (51%) Identity Management (50%)

Step 2 Define institutional data types Sub-steps 2. 1 Compliance with applicable federal and state laws and regulations - as well as contractual obligations - related to privacy and security of data held by the institution (also consider applicable international laws) 2. 2 Data classification schema developed with input from legal counsel and data stewards 2. 3 Data classification schema assigned to institutional data to the extent possible or necessary

Step 2 Define institutional data types Sub-steps 2. 1 Compliance with applicable federal and state laws and regulations - as well as contractual obligations - related to privacy and security of data held by the institution (also consider applicable international laws) 2. 2 Data classification schema developed with input from legal counsel and data stewards 2. 3 Data classification schema assigned to institutional data to the extent possible or necessary
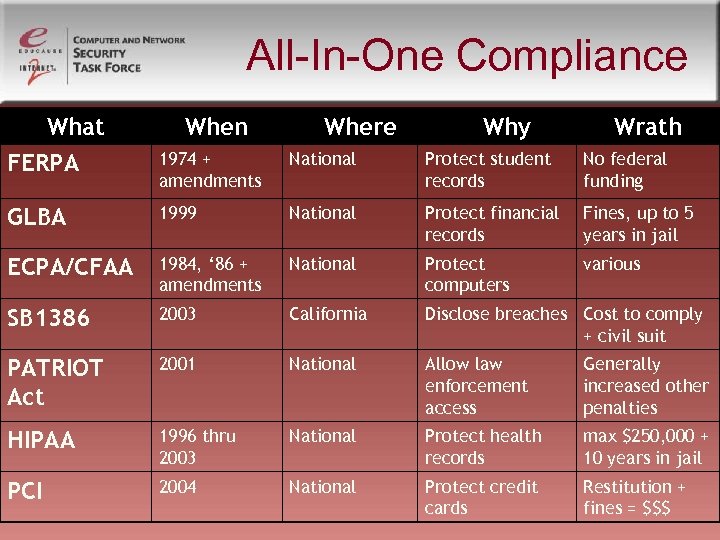
All-In-One Compliance What FERPA When Where Why Wrath 1974 + amendments National Protect student records No federal funding GLBA 1999 National Protect financial records Fines, up to 5 years in jail ECPA/CFAA 1984, ‘ 86 + amendments National Protect computers various SB 1386 2003 California Disclose breaches Cost to comply + civil suit PATRIOT Act 2001 National Allow law enforcement access Generally increased other penalties HIPAA 1996 thru 2003 National Protect health records max $250, 000 + 10 years in jail PCI 2004 National Protect credit cards Restitution + fines = $$$

Step 2 Define institutional data types Sub-steps 2. 1 Compliance with applicable federal and state laws and regulations - as well as contractual obligations - related to privacy and security of data held by the institution (also consider applicable international laws) 2. 2 Data classification schema developed with input from legal counsel and data stewards 2. 3 Data classification schema assigned to institutional data to the extent possible or necessary

Data Classification Policy Provides the framework necessary to: Identify and classify data in order to assess risk and implement an appropriate level of security protection based on categorization. Comply with legislation, regulations, and internal policies that govern the protection of data. Facilitate and make the Incident Response process more efficient. The level in which the data is classified determines the level of response.
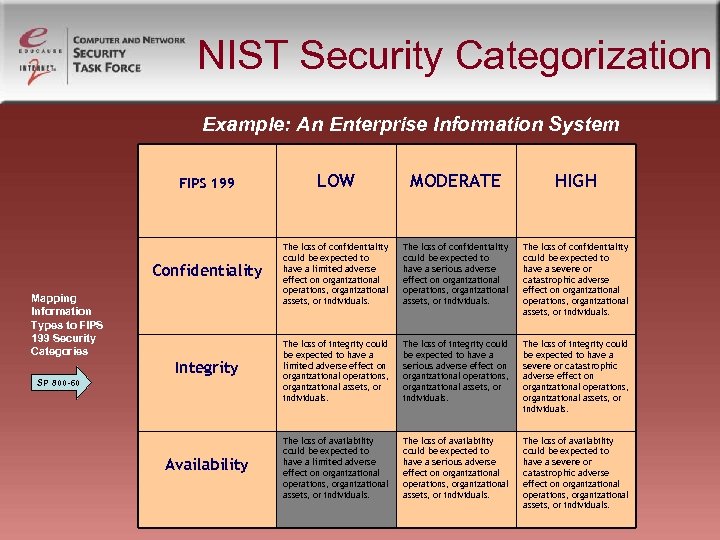
NIST Security Categorization Example: An Enterprise Information System FIPS 199 LOW MODERATE HIGH Confidentiality The loss of confidentiality could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. The loss of confidentiality could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The loss of confidentiality could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. Integrity The loss of integrity could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. The loss of integrity could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The loss of integrity could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. Availability The loss of availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. The loss of availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. The loss of availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. Mapping Information Types to FIPS 199 Security Categories SP 800 -60
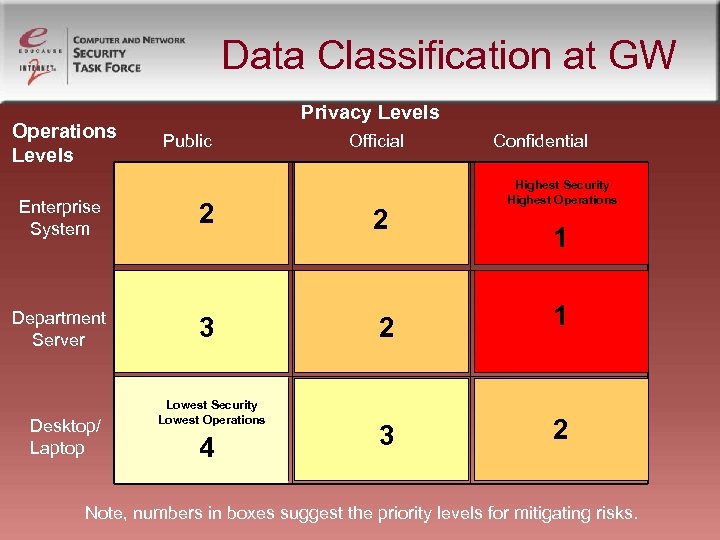
Data Classification at GW Operations Levels Privacy Levels Public Official Confidential Highest Security Highest Operations Enterprise System 2 2 Department Server 3 2 1 3 2 Desktop/ Laptop Lowest Security Lowest Operations 4 1 Note, numbers in boxes suggest the priority levels for mitigating risks.
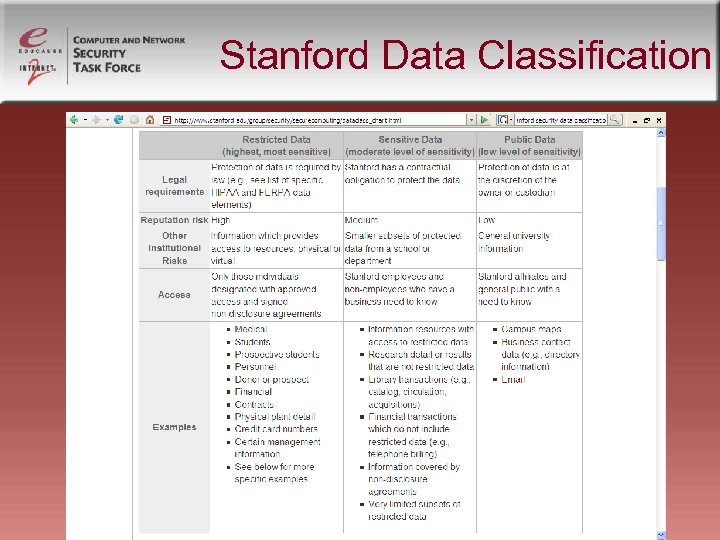
Stanford Data Classification
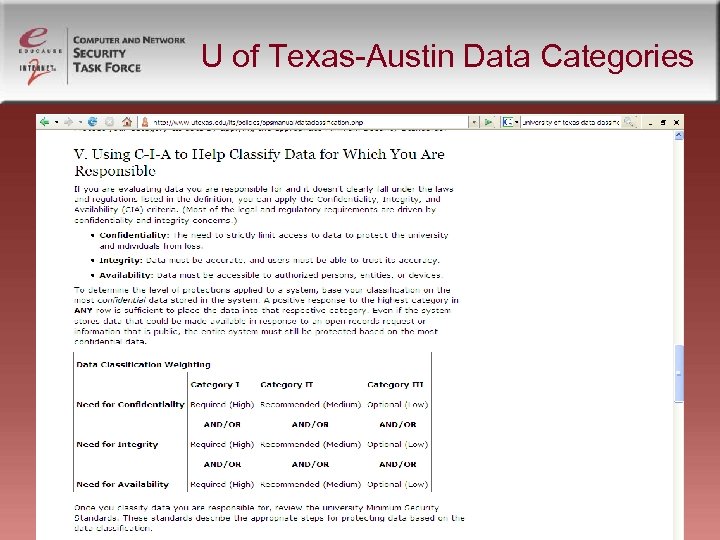
U of Texas-Austin Data Categories
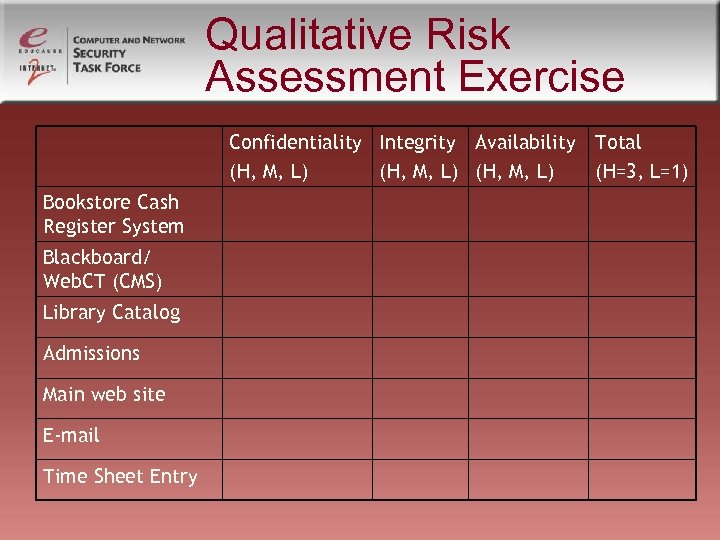
Qualitative Risk Assessment Exercise Confidentiality Integrity Availability Total (H, M, L) (H=3, L=1) Bookstore Cash Register System Blackboard/ Web. CT (CMS) Library Catalog Admissions Main web site E-mail Time Sheet Entry
BREAK

Step 3 Clarify responsibilities and accountability for safeguarding confidential/sensitive data Sub-steps 3. 1 Data stewardship roles and responsibilities 3. 2 Legally binding third party agreements that assign responsibility for secure data handling

Step 3 Clarify responsibilities and accountability for safeguarding confidential/sensitive data Sub-steps 3. 1 Data stewardship roles and responsibilities 3. 2 Legally binding third party agreements that assign responsibility for secure data handling

Example – University of North Carolina Data Trustee: Data trustees are senior University officials (or their designees) who have planning and policy-level responsibility for data within their functional areas and management responsibilities for defined segments of institutional data. Responsibilities include assigning data stewards, participating in establishing policies, and promoting data resource management for the good of the entire University. Data Steward: Data stewards are University officials having direct operational-level responsibility for information management – usually department directors. Data stewards are responsible for data access and policy implementation issues. Data Custodian: Information Technology Services is the data custodian. The custodian is responsible for providing a secure infrastructure in support of the data, including, but not limited to, providing physical security, backup and recovery processes, granting access privileges to system users as authorized by data trustees or their designees (usually the data stewards), and implementing and administering controls over the information. Data User: Data users are individuals who need and use University data as part of their assigned duties or in fulfillment of assigned roles or functions within the University community. Individuals who are given access to sensitive data have a position of special trust and as such are responsible for protecting the security and integrity of those data. http: //its. uncg. edu/Policy_Manual/Data/

Step 3 Clarify responsibilities and accountability for safeguarding confidential/sensitive data Sub-steps 3. 1 Data stewardship roles and responsibilities 3. 2 Legally binding third party agreements that assign responsibility for secure data handling

Outsourced Data Handling Some Drivers § Security of Commercial Software – addressed elsewhere (Step 7. 4) § Incidents: Mishandling by 3 rd Parties § GLB Act: Oversight of Service Providers § PCI requirement § Federal Contracts and Grant Sample Contract Language § E-mail instructor for a copy

Step 4 Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps 4. 1 Data collection processes (including forms) should request only the minimum necessary confidential/sensitive information 4. 2 Application outputs (e. g. , queries, hard copy reports, etc. ) should provide only the minimum necessary confidential/sensitive information 4. 3 Inventory and review access to existing confidential/sensitive data on servers, desktops, and mobile devices

Step 4 continued… Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps continued 4. 4 Eliminate unnecessary confidential/sensitive data on servers, desktops, and mobile devices 4. 5 Eliminate dependence on SSNs as primary identifiers and as a form of authentication* *Note: SSNs may need to be used for certain things (e. g. , student employees, student financial aid, etc. ) and we recommend that schools limit the use of SSNs to necessary processes only.

Step 4 Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps 4. 1 Data collection processes (including forms) should request only the minimum necessary confidential/sensitive information 4. 2 Application outputs (e. g. , queries, hard copy reports, etc. ) should provide only the minimum necessary confidential/sensitive information 4. 3 Inventory and review access to existing confidential/sensitive data on servers, desktops, and mobile devices

Fair Information Practices and Privacy General Principles of Fair Information Practice: § § § § Openness Individual Participation Collection Limitation Data Quality Finality Security Accountability Privacy Statements Privacy Policies

Step 4 Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps 4. 1 Data collection processes (including forms) should request only the minimum necessary confidential/sensitive information 4. 2 Application outputs (e. g. , queries, hard copy reports, etc. ) should provide only the minimum necessary confidential/sensitive information 4. 3 Inventory and review access to existing confidential/sensitive data on servers, desktops, and mobile devices

Step 4 Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps 4. 1 Data collection processes (including forms) should request only the minimum necessary confidential/sensitive information 4. 2 Application outputs (e. g. , queries, hard copy reports, etc. ) should provide only the minimum necessary confidential/sensitive information 4. 3 Inventory and review access to existing confidential/sensitive data on servers, desktops, and mobile devices

Step 4 continued… Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps continued 4. 4 Eliminate unnecessary confidential/sensitive data on servers, desktops, and mobile devices 4. 5 Eliminate dependence on SSNs as primary identifiers and as a form of authentication* *Note: SSNs may need to be used for certain things (e. g. , student employees, student financial aid, etc. ) and we recommend that schools limit the use of SSNs to necessary processes only.

Solutions Safety Analyzer (George Washington University) § Sensitive Data Detection • SSNs with heuristics • Credit Card numbers with Luhn algorithm validation § Compromise Detection • Trojan file detection • Kernel-level rootkit detection • IR-related data harvesting Spider (Cornell University) SENF! (Sensitive Number Finder) (University of Texas at Austin)

Step 4 continued… Reduce access to confidential/sensitive data not absolutely essential to institutional processes Sub-steps continued 4. 4 Eliminate unnecessary confidential/sensitive data on servers, desktops, and mobile devices 4. 5 Eliminate dependence on SSNs as primary identifiers and as a form of authentication* *Note: SSNs may need to be used for certain things (e. g. , student employees, student financial aid, etc. ) and we recommend that schools limit the use of SSNs to necessary processes only.
Elimination of SSNs Federal and state law requires the collection of your Social Security number (SSN) for certain purposes (for example, IRS reporting forms). However, widespread use of an individual's SSN is a major privacy concern. With incidents of identity theft increasing, steps to secure an individual's SSN become more important. A large number of colleges and universities use SSNs as primary identifiers for faculty, staff, and students, which exposes institutions to risk because of changing legal and security environments. Therefore, many institutions are planning for the migration away from SSN use as a primary identifier. Undertaking such a task raises issues, challenges, and opportunities for any institution. EDUCAUSE has identified links concerning the elimination of SSNs as primary identifiers that may be useful to the higher education community. http: //www. educause. edu/Browse/645? PARENT_ID=701
Where to be with SSNs requested only when essential SSN access authorized to least # of people University Processes & Supporting Systems Clear SSN use policy exists Responsibilities for SSN protection well communicated Compliance verification processes in place SSNs provided only when essential SSNs stored only in highly secured devices and file cabinets

Step 5 Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps 5. 1 Inventory and review/remediate security of devices 5. 2 Configuration standards for applications, servers, desktops, and mobile devices 5. 3 Network level protections 5. 4 Encryption strategies for data in transit and at rest

Step 5 continued… Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps continued 5. 5 Policies regarding confidential/sensitive data on mobile devices and home computers and for data archival/storage 5. 6 Identity management and resource provisioning processes 5. 7 Secure disposal of equipment and data 5. 8 Consider background checks on individuals handling confidential/sensitive data

Step 5 Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps 5. 1 Inventory and review/remediate security of devices 5. 2 Configuration standards for applications, servers, desktops, and mobile devices 5. 3 Network level protections 5. 4 Encryption strategies for data in transit and at rest

Inventory Devices Network Registration (Net. Reg) § Commercial NAC solutions (Cisco, etc) Commercial desktop management products § Altiris, etc. Manual Inventories Review Security of Devices* § Network vulnerability scans § Local tools such as Microsoft’s Baseline Security Analyzer (MBSA) § Manage your anti-virus for review/remediate *which ones? ? ?

Step 5 Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps 5. 1 Inventory and review/remediate security of devices 5. 2 Configuration standards for applications, servers, desktops, and mobile devices 5. 3 Network level protections 5. 4 Encryption strategies for data in transit and at rest
Configuration Standards There are recommendations available from various sources on the Internet § Vendors themselves § Center for Internet Security (http: //www. cisecurity. org/) § NSA (http: //www. nsa. gov/snac/) How to Implement at your institution § Use your own published procedures § Publish links to sources above § Create and use “Images” Don’t Forget Applications § § Web servers Mail servers FTP servers Consider standards as part of the Software Development Life Cycle

Step 5 Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps 5. 1 Inventory and review/remediate security of devices 5. 2 Configuration standards for applications, servers, desktops, and mobile devices 5. 3 Network level protections 5. 4 Encryption strategies for data in transit and at rest
Network Level Protections Intrusion Detection System § Snort, Dragon, NFR Intrusion Prevention System § Tipping Point, Intrushield Extrusion Prevention System § Vontu, Reconnecx, Fidelis Database protection systems § Guardium, Tizor, etc. Network Anomaly Detection § Q 1 Radar, Arbor, Mazu, etc. (flow analysis)

Step 5 Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps 5. 1 Inventory and review/remediate security of devices 5. 2 Configuration standards for applications, servers, desktops, and mobile devices 5. 3 Network level protections 5. 4 Encryption strategies for data in transit and at rest
Encryption & Data in Transit Strategies for Data in Transit § Encrypt before sending(e. g. PGP) § Encrypt on the fly (e. g. SSL) Issues for Data in Transit § Key exchange § Performance § Choice of algorithm Protocols § SSL § SSH § Proprietary (in which case check the algorithm)
Encryption and Data at Rest Problems with Data at Rest § Theft by a network intruder § Physical theft -- for example, a laptop Data at Rest Strategies § Whole disk encryption § File encryption Issues § Key escrow § Cost if not using O/S vendor’s file encryption § Very low adoption rate in higher ed market

Step 5 continued… Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps continued 5. 5 Policies regarding confidential/sensitive data on mobile devices and home computers and for data archival/storage 5. 6 Identity management and resource provisioning processes 5. 7 Secure disposal of equipment and data 5. 8 Consider background checks on individuals handling confidential/sensitive data

Data on Mobile Devices Data has wings § § PDAs and music players USB memory fobs Cyber-cafes Home computers Compensating Policy § Written mandates § Practical assistance Enforcement or checking is exceedingly difficult § Which does not mean you should not do it, if nothing else it can be used to justify discipline

Protection of Mobile Data OMB Memo: Protection of Sensitive Agency Information http: //www. whitehouse. gov/omb/memoranda/fy 2006/m 06 -16. pdf NIST Checklist: Protection of Remote Information

Step 5 continued… Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps continued 5. 5 Policies regarding confidential/sensitive data on mobile devices and home computers and for data archival/storage 5. 6 Identity management and resource provisioning processes 5. 7 Secure disposal of equipment and data 5. 8 Consider background checks on individuals handling confidential/sensitive data

ID Management Access control lists (ACLs) Account creation Account deletion Process issues Fragmentation can be addressed § By process improvement § Via technology Rich area of research & development Also commercial solutions § Active Directory § LDAP solutions

EDUCAUSE Identity Management Resources Recent Library Submissions (3) CIC Identity Management Conference Session: Federated Identity Management and Sharing Resources (2007) by Jim Phelps, IT Architect in Academia Identity Management Conference Report (2007)by Committee on Institutional Cooperation A Report on the Identity Management Summit (2007) by Norma Holland, Ann West and Steve Worona, EDUCAUSE Most Popular Library Content (3) Top-Ten IT Issues, 2006 (2006) by Barbara I. Dewey, Peter B. De. Blois, and the 2006 EDUCAUSE Current Issues Committee, EDUCAUSE Safeguarding the Tower: IT Security in Higher Education 2006 (2006) by Robert B. Kvavik, with John Voloudakis, ECAR Identity Management in Higher Education: A Baseline Study (2006) by Ronald Yanosky, with Gail Salaway, ECAR http: //www. educause. edu/Browse/645? PARENT_ID=679

Step 5 continued… Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps continued 5. 5 Policies regarding confidential/sensitive data on mobile devices and home computers and for data archival/storage 5. 6 Identity management and resource provisioning processes 5. 7 Secure disposal of equipment and data 5. 8 Consider background checks on individuals handling confidential/sensitive data

Equipment and Data Disposal Classic examples are lost backup tapes Magnetic media destruction can be done physically (sledgehammer) or magnetically (degaussed or multi-pass formatted) or both Do not ignore hard-copy data § Shredders This step can be both expensive and inconvenient

Data Sanitization Guidelines NIST Special Publication 800 -88 Guidelines for Media Sanitization http: //csrc. nist. gov/publications/nistpubs/80088/NISTSP 800 -88_rev 1. pdf EDUCAUSE/Internet 2 Security Task Force Practical Data Sanitization Guidelines for Higher Education https: //wiki. internet 2. edu/confluence/display/secgui de/Guidelines+for+Data+Sanitization Michigan State University Best Practices in Disposal of Computers and Electronic Storage Media http: //computing. msu. edu/msd/documents/safecom puterdisposal. pdf

Step 5 continued… Establish and implement stricter controls for safeguarding confidential/sensitive data Sub-steps continued 5. 5 Policies regarding confidential/sensitive data on mobile devices and home computers and for data archival/storage 5. 6 Identity management and resource provisioning processes 5. 7 Secure disposal of equipment and data 5. 8 Consider background checks on individuals handling confidential/sensitive data

Background Checks Kinds of checks § § Criminal Credit Resume Education Why? How? § Do you save it once it’s complete? § Do results stay in H/R or go to hiring manager? § If running criminal checks, how wide a net do you cast and how legitimate can you be?
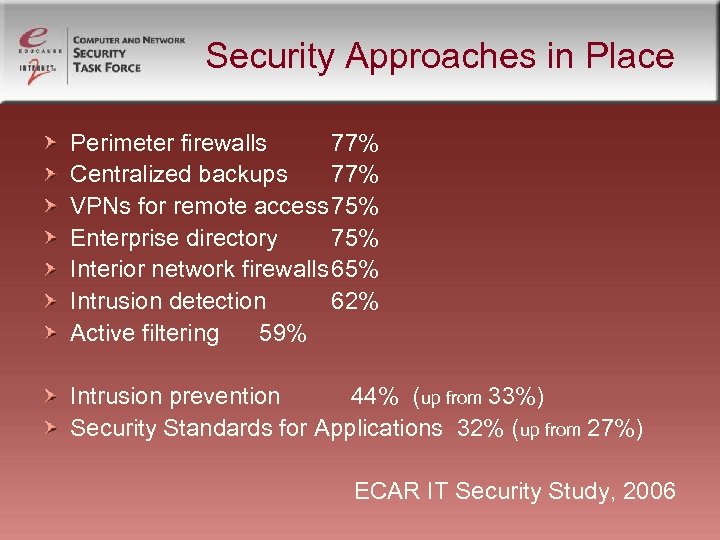
Security Approaches in Place Perimeter firewalls 77% Centralized backups 77% VPNs for remote access 75% Enterprise directory 75% Interior network firewalls 65% Intrusion detection 62% Active filtering 59% Intrusion prevention 44% (up from 33%) Security Standards for Applications 32% (up from 27%) ECAR IT Security Study, 2006

Step 6 Provide awareness and training Sub-steps 6. 1 Make confidential/sensitive data handlers aware of privacy and security requirements 6. 2 Require acknowledgement by data users of their responsibility for safeguarding such data 6. 3 Enhance general privacy and security awareness programs to specifically address safeguarding confidential/sensitive data 6. 4 Collaboration mechanisms such as e-mail have strengths and limitations in terms of access control, which must be clearly communicated and understood so that the data will be safe-guarded

Awareness & Training Who needs “awareness” (consciousnessraising)? All Users! § § § Executives Faculty Staff Students Users of Sensitive Data IT Staff Training (skills development) § Especially for data stewards, IT staff, and information security team
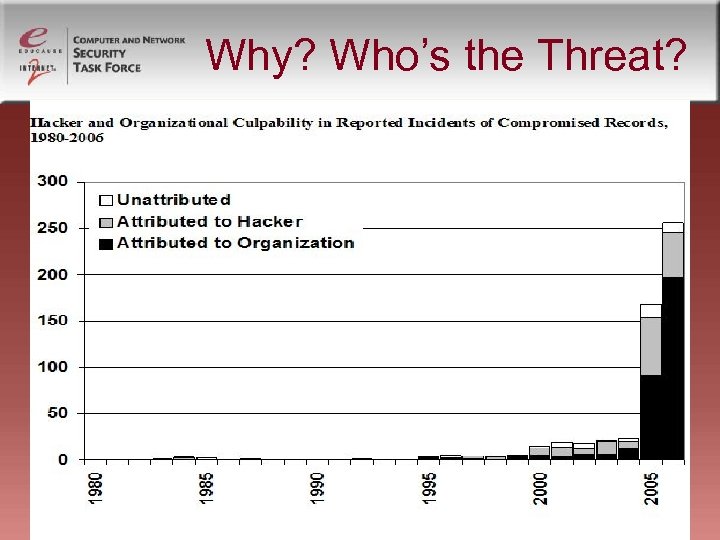
Why? Who’s the Threat?

Cybersecurity Awareness Resources CD The Awareness and Training Working Group of the EDUCAUSE/Internet 2 Security Task Force compiled cybersecurity awareness resources distributed on a CD which are now on the web site. The resources were collected to showcase the variety of security awareness efforts underway at institutions of higher education and to provide resources for colleges and universities that are looking to jump-start a program for their organization.

What’s on the Web Site? Book Marks Brochures Checklists Flyers Games Government Resources Handouts Industry Resources Links to School’s Security Web Page(s) Pamphlets Post Cards Presentations Security Awareness Documents Security Cards Security Tools Security Quizzes Surveys Videos
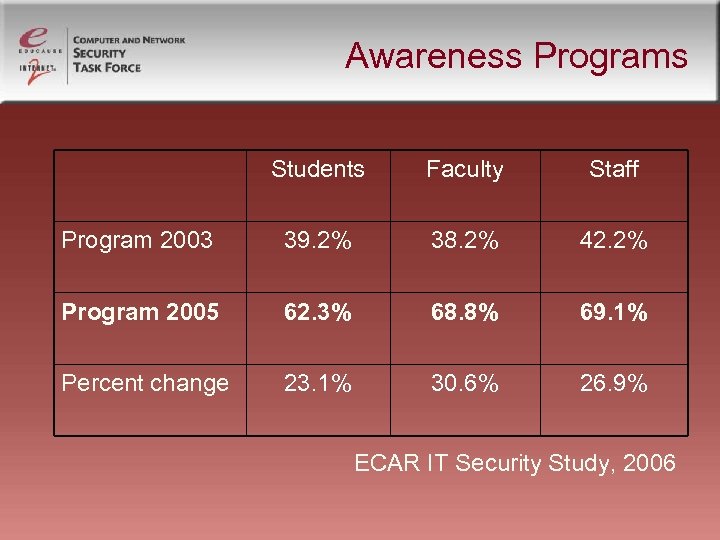
Awareness Programs Students Faculty Staff Program 2003 39. 2% 38. 2% 42. 2% Program 2005 62. 3% 68. 8% 69. 1% Percent change 23. 1% 30. 6% 26. 9% ECAR IT Security Study, 2006
When I Go To U. Va…. http: //www. itc. virginia. edu/pubs/docs/Resp. Comp/videos/when-I-go-to-UVA-lg. mov

Security Awareness Exercise Outline a Plan for a Security Awareness Campaign About Managing Sensitive Data 1. 2. 3. 4. 5. Who is your target audience? How will you market it? What are your key messages? What method of delivery will you use? How will you measure its effectiveness?

Step 7 Verify compliance routinely with your policies and procedures Sub-steps 7. 1 Routinely test network-connected devices and services for weaknesses in operating systems, applications, and encryption 7. 2 Routinely scan servers, desktops, mobile devices, and networks containing confidential/sensitive data to verify compliance 7. 3 Routinely audit access privileges 7. 4 Procurement procedures and contract language to ensure proper data handling is maintained

Step 7 continued… Verify compliance routinely with your policies and procedures Sub-steps continued 7. 5 System development methodologies that prevent new data handling problems from being introduced into the environment 7. 6 Utilize audit function within the institution to verify compliance 7. 7 Incident response policies and procedures 7. 8 Conduct regular meetings with stakeholders such as data stewards, legal counsel, compliance officers, public safety, public relations, and IT groups to review institutional risk and compliance and to revise existing policies and procedures as needed

Step 7 Verify compliance routinely with your policies and procedures Sub-steps 7. 1 Routinely test network-connected devices and services for weaknesses in operating systems, applications, and encryption 7. 2 Routinely scan servers, desktops, mobile devices, and networks containing confidential/sensitive data to verify compliance 7. 3 Routinely audit access privileges 7. 4 Procurement procedures and contract language to ensure proper data handling is maintained
Routine Testing Network Admission Control (NAC) Test(s) at network registration But not all weaknesses are caught by commercial testing programs (scanners) Encryption can be tricky § Network sniffing § Examine configuration files Applications can imply things like rerunning regression testing after changes

Step 7 Verify compliance routinely with your policies and procedures Sub-steps 7. 1 Routinely test network-connected devices and services for weaknesses in operating systems, applications, and encryption 7. 2 Routinely scan servers, desktops, mobile devices, and networks containing confidential/sensitive data to verify compliance 7. 3 Routinely audit access privileges 7. 4 Procurement procedures and contract language to ensure proper data handling is maintained

Routine Scanning Vulnerability Scanners § § Nessus ISS GFI LANGuard e. Eye Retina Local confidential data scanners* § GW Safety Analyzer § Cornell Spider § U. Texas SENF (Sensitive Number Finder) *follow-up on 4. 3

Step 7 Verify compliance routinely with your policies and procedures Sub-steps 7. 1 Routinely test network-connected devices and services for weaknesses in operating systems, applications, and encryption 7. 2 Routinely scan servers, desktops, mobile devices, and networks containing confidential/sensitive data to verify compliance 7. 3 Routinely audit access privileges 7. 4 Procurement procedures and contract language to ensure proper data handling is maintained

Routine Audits Copy your external auditors What persons, groups, or roles have access? § Should have access? Check terminated employees against list Transfers to new internal jobs as well Unclear as to wisdom of letting them know you’re coming

Step 7 Verify compliance routinely with your policies and procedures Sub-steps 7. 1 Routinely test network-connected devices and services for weaknesses in operating systems, applications, and encryption 7. 2 Routinely scan servers, desktops, mobile devices, and networks containing confidential/sensitive data to verify compliance 7. 3 Routinely audit access privileges 7. 4 Procurement procedures and contract language to ensure proper data handling is maintained

Procurement Practices Contracts in the U. S. establish your rights - very few rights are guaranteed Are any vendors subject to your policies, or to any other statute governing their handling of your data? Does their contract acknowledge this? How are the vendors liable? § Your judgment, theirs, or a court’s?

Step 7 continued… Verify compliance routinely with your policies and procedures Sub-steps continued 7. 5 System development methodologies that prevent new data handling problems from being introduced into the environment 7. 6 Utilize audit function within the institution to verify compliance 7. 7 Incident response policies and procedures 7. 8 Conduct regular meetings with stakeholders such as data stewards, legal counsel, compliance officers, public safety, public relations, and IT groups to review institutional risk and compliance and to revise existing policies and procedures as needed

System Development Add security to your software development life cycle When § § Requirements Vendor analysis or architecture development Test Turnover Consider canned methodologies only if they incorporate security

Step 7 continued… Verify compliance routinely with your policies and procedures Sub-steps continued 7. 5 System development methodologies that prevent new data handling problems from being introduced into the environment 7. 6 Utilize audit function within the institution to verify compliance 7. 7 Incident response policies and procedures 7. 8 Conduct regular meetings with stakeholders such as data stewards, legal counsel, compliance officers, public safety, public relations, and IT groups to review institutional risk and compliance and to revise existing policies and procedures as needed
Audit Function Auditor -- friend or enemy? Audit reports generally go higher in the organization than security memos Audit staff has some skills at compliance and testing against a process or procedure Use them to double-check yourself and to check things that you can’t due to time or political constraints

Step 7 continued… Verify compliance routinely with your policies and procedures Sub-steps continued 7. 5 System development methodologies that prevent new data handling problems from being introduced into the environment 7. 6 Utilize audit function within the institution to verify compliance 7. 7 Incident response policies and procedures 7. 8 Conduct regular meetings with stakeholders such as data stewards, legal counsel, compliance officers, public safety, public relations, and IT groups to review institutional risk and compliance and to revise existing policies and procedures as needed

Incident Response An incident response structure is a necessity Rich vein of material on this -- blueprint has links Cut down time data is exposed

Step 7 continued… Verify compliance routinely with your policies and procedures Sub-steps continued 7. 5 System development methodologies that prevent new data handling problems from being introduced into the environment 7. 6 Utilize audit function within the institution to verify compliance 7. 7 Incident response policies and procedures 7. 8 Conduct regular meetings with stakeholders such as data stewards, legal counsel, compliance officers, public safety, public relations, and IT groups to review institutional risk and compliance and to revise existing policies and procedures as needed

Continuous Improvement Keep it current Keep them current Keep within the law Keep exploiting new technology

FTC Guide: Protecting Personal Information Take stock. Know what personal information you have in your files and on your computers. Scale down. Keep only what you need for your business. Lock it. Protect the information that you keep. Pitch it. Properly dispose of what you no longer need. Plan ahead. Create a plan to respond to security incidents.

Putting it All Together Moving from Planning to Action!

The Blueprint Discussion § How will you use the blueprint? § Do you have suggestions to improve it? § Do you have resources or effective practices to submit?

Wrap-Up Question & Answer Seminar Evaluation & Feedback Program ends at 12: 00 pm

For more information David Escalante Email: david. escalante@bc. edu Phone: 617 -552 -6060 EDUCAUSE/Internet 2 Security Task Force www. educause. edu/security EDUCAUSE Center for Applied Research www. educause. edu/ECAR Blueprint for Handling Sensitive Data wiki. internet 2. edu/confluence/display/secguide

Case Study Group Discussion: 1. Who do you need to include (or other consult) as part of the emergency meeting? 2. What core messages will you plan to deliver at the press conference? 3. What kinds of questions should you anticipate from reporters or potential victims?
d75d4083a3b07df3a212defd723646f3.ppt