a481315d12fe34e445a221b77a3a1a78.ppt
- Количество слайдов: 89
8. Advances in Web Engineering a. SOA b. Security for e-Commerce SWE 444 - Internet & Web Application Development 1

Introduction to SOA Environments by Dennis Smith and Grace Lewis Software Engineering Institute SWE 444 - Internet & Web Application Development 8. 2
What is SOA? Service-oriented architecture is a way of designing systems that enables • Cost-efficiency • Agility • Adaptability • Leverage of legacy investments SWE 444 - Internet & Web Application Development 3

Services are reusable components that represent business tasks. • Customer lookup • Account lookup • Credit card validation • Credit check • Hotel reservation • Interest calculation Services can be • Globally distributed across organizations • Reconfigured into new business processes SWE 444 - Internet & Web Application Development 4
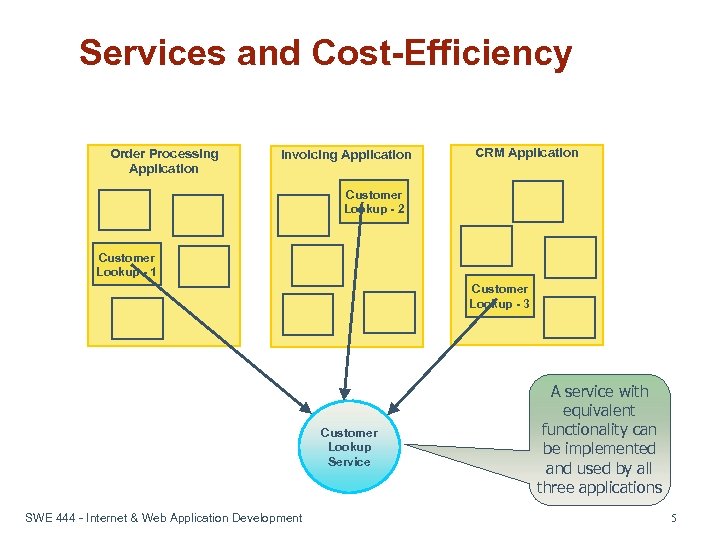
Services and Cost-Efficiency Order Processing Application Invoicing Application CRM Application Customer Lookup - 2 Customer Lookup - 1 Customer Lookup - 3 Customer Lookup Service SWE 444 - Internet & Web Application Development A service with equivalent functionality can be implemented and used by all three applications 5
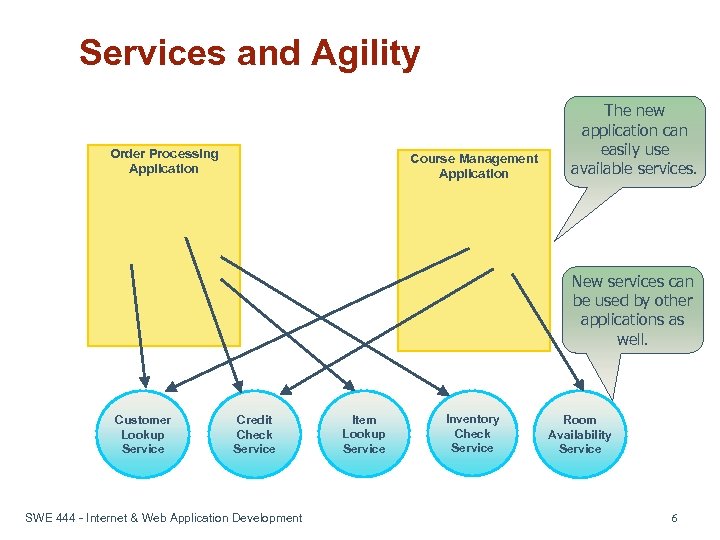
Services and Agility Order Processing Application Course Management Application The new application can easily use available services. New services can be used by other applications as well. Customer Lookup Service Credit Check Service SWE 444 - Internet & Web Application Development Item Lookup Service Inventory Check Service Room Availability Service 6
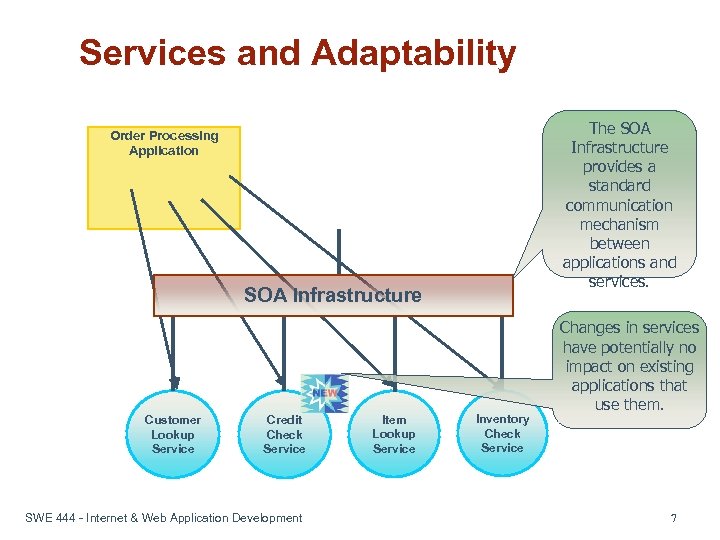
Services and Adaptability The SOA Infrastructure provides a standard communication mechanism between applications and services. Order Processing Application SOA Infrastructure Customer Lookup Service Credit Check Service SWE 444 - Internet & Web Application Development Item Lookup Service Inventory Check Service Changes in services have potentially no impact on existing applications that use them. 7
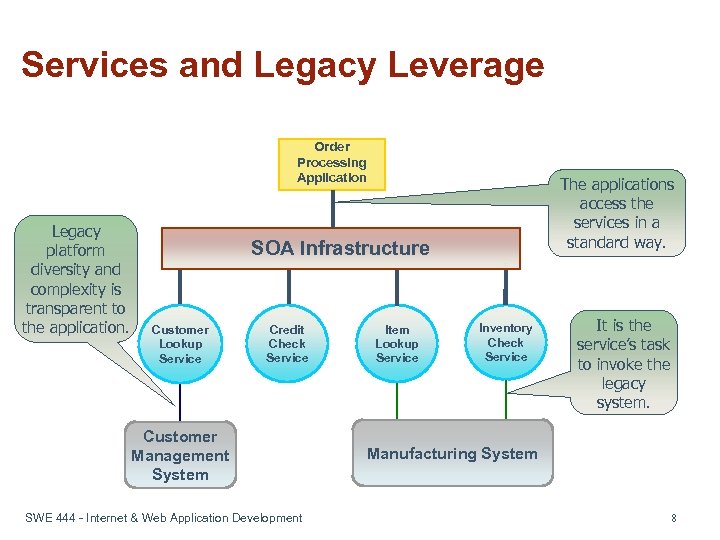
Services and Legacy Leverage Order Processing Application Legacy platform diversity and complexity is transparent to the application. The applications access the services in a standard way. SOA Infrastructure Customer Lookup Service Credit Check Service Customer Management System SWE 444 - Internet & Web Application Development Item Lookup Service Inventory Check Service It is the service’s task to invoke the legacy system. Manufacturing System 8
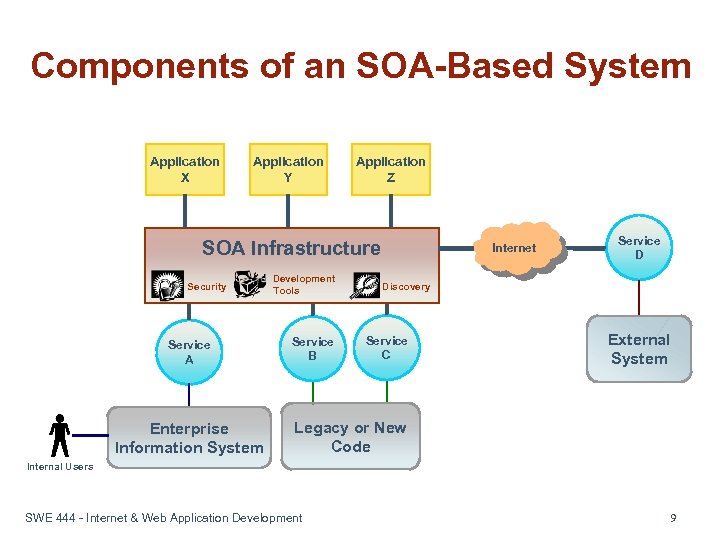
Components of an SOA-Based System Application X Application Y Application Z SOA Infrastructure Security Service A Enterprise Information System Development Tools Service B Internet Service D Discovery Service C External System Legacy or New Code Internal Users SWE 444 - Internet & Web Application Development 9

In Summary … SOA is an approach to software development where • Services provide reusable functionality with well-defined interfaces. • An SOA infrastructure enables discovery, composition and invocation of services. • Applications are built using functionality from available services. If managed well, SOA adoption can lead to • Cost-efficiency • Agility • Adaptability • Leverage of legacy investments The hard part is the “if managed well”. SWE 444 - Internet & Web Application Development 10
An SOA Provides The Complete Architecture For A System SOA is an architectural pattern/style/paradigm and not the architecture of the system itself. An architectural pattern provides guidance that embodies best practices. • The concrete elements and their interactions are the architecture of the system. Any number of systems can be developed based on an architectural pattern. • An architecture based on SOA inherits both the good and the bad. Corollary: SOA cannot be bought off-the shelf. • System qualities have to be built into the architecture of the system. • Decisions have to be made—service design and implementation, technologies, tradeoffs. SWE 444 - Internet & Web Application Development 11

Using XML and WSDL Guarantees Interoperability Among Web Services Provided by Multiple Organizations Web Services enable syntactic interoperability • XML Schema defines structure and data types • WSDL defines the interfaces: operations, parameters and return values Web Services do not guarantee semantic interoperability • XML and WSDL do not define the meaning of data • WSDL does not define what a service does • How to describe the meaning of Web Service inputs and outputs in a formal manner - Active research area—unresolved issues Interoperability needs agreement on both syntax and semantics SWE 444 - Internet & Web Application Development 12
It Is Easy To Develop Applications Based on Services It is relatively easy to build services to work with a particular infrastructure … but designing a “good” service might not be that easy. • From a implementation standpoint - Ease depends on tool availability for SOA infrastructure – There is plenty of guidance and excellent tool support to implement, deploy, and manage services for Web Services - Most difficult part is composition—data mismatches • From a design standpoint - Designing a service interface in a way that it can be used easily in many contexts is a much harder task. – Not many best practices for designing services - Have to anticipate potential users and usage patterns SWE 444 - Internet & Web Application Development 13

It is Easy to Compose Services Dynamically at Runtime Current technologies have not advanced to the point that this is possible in production environments. Requires the use of a common ontology by service providers and client applications within a domain Requires the construction of extremely intelligent applications that • Construct the right queries for the discovery of services • Compose services when there is not a single service that can process the request • Provide the right data to invoke a service that was discovered at runtime SWE 444 - Internet & Web Application Development 14
Web Services Web services is one mechanism for implementing an SOAbased system. • Service interfaces are described using Web Services Description Language (WSDL) • Data is transmitted using SOAP over HTTP • UDDI is optionally used as the directory service Because it is the most common mechanism, it is often equated to SOA. SWE 444 - Internet & Web Application Development 15
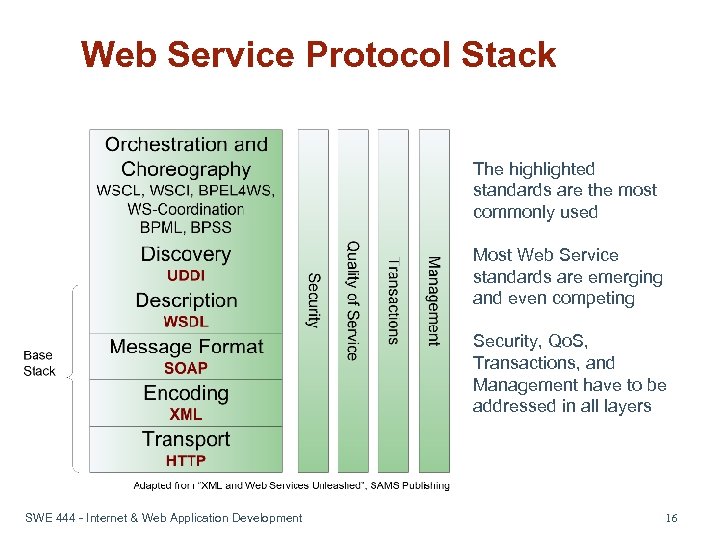
Web Service Protocol Stack The highlighted standards are the most commonly used Most Web Service standards are emerging and even competing Security, Qo. S, Transactions, and Management have to be addressed in all layers SWE 444 - Internet & Web Application Development 16
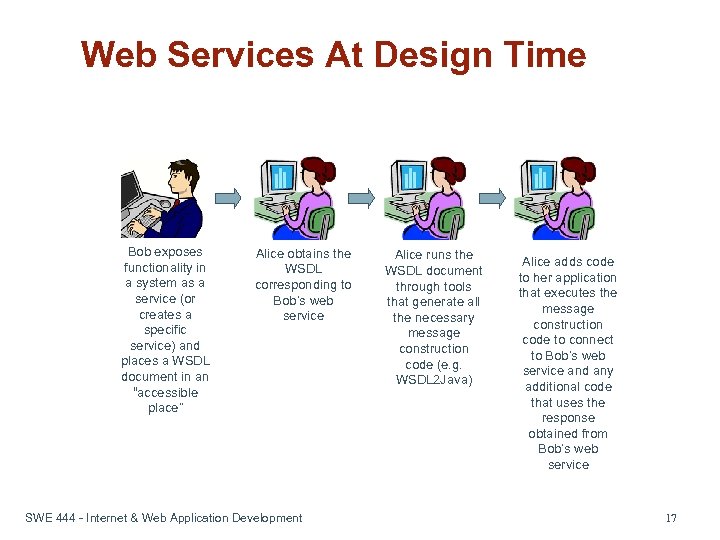
Web Services At Design Time Bob exposes functionality in a system as a service (or creates a specific service) and places a WSDL document in an “accessible place” Alice obtains the WSDL corresponding to Bob’s web service SWE 444 - Internet & Web Application Development Alice runs the WSDL document through tools that generate all the necessary message construction code (e. g. WSDL 2 Java) Alice adds code to her application that executes the message construction code to connect to Bob’s web service and any additional code that uses the response obtained from Bob’s web service 17
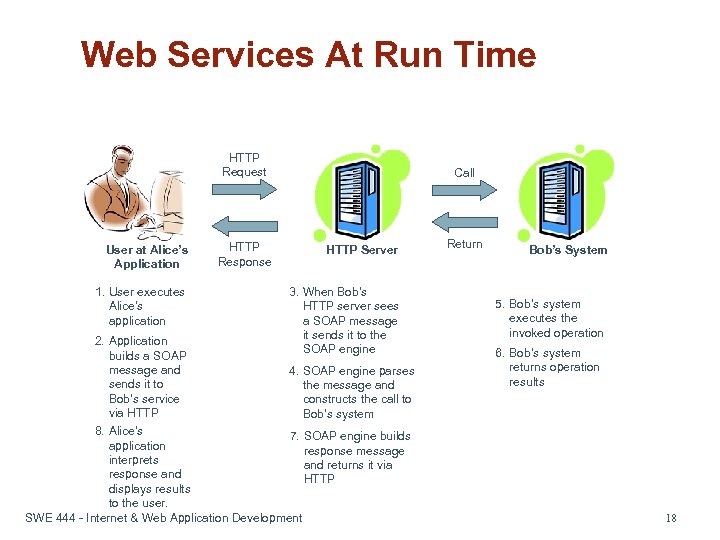
Web Services At Run Time HTTP Request User at Alice’s Application 1. User executes Alice’s application HTTP Response Call HTTP Server 3. When Bob’s HTTP server sees a SOAP message it sends it to the SOAP engine 2. Application builds a SOAP message and 4. SOAP engine parses sends it to the message and Bob’s service constructs the call to via HTTP Bob’s system 8. Alice’s 7. SOAP engine builds application response message interprets and returns it via response and HTTP displays results to the user. SWE 444 - Internet & Web Application Development Return Bob’s System 5. Bob’s system executes the invoked operation 6. Bob’s system returns operation results 18
Static vs. Dynamic With today’s technology, discovery and composition of services are done at design time—Static • Developer discovers services and obtains addresses • Developer writes code to invoke the services located at these addresses There is a great amount of research to enable discovery and composition at runtime—Dynamic • Application discovers services and obtains addresses • Application contains code to invoke the discovered services and “knows” what information to provide There a lot of “In-Between” techniques • Application discovers services but requires user intervention to select services and provide the required information • Portals are configured such that “portlets” correspond to services SWE 444 - Internet & Web Application Development 19
In Summary … Web Services are the most currently used approach to SOA implementation. • Basic infrastructure standards are fairly stable • More higher level standards are emerging Web Services are not the only approach to SOA implementation. SWE 444 - Internet & Web Application Development 20
Components of an SOA-Based Systems 1. Services 2. Applications 3. SOA Infrastructure SWE 444 - Internet & Web Application Development 21
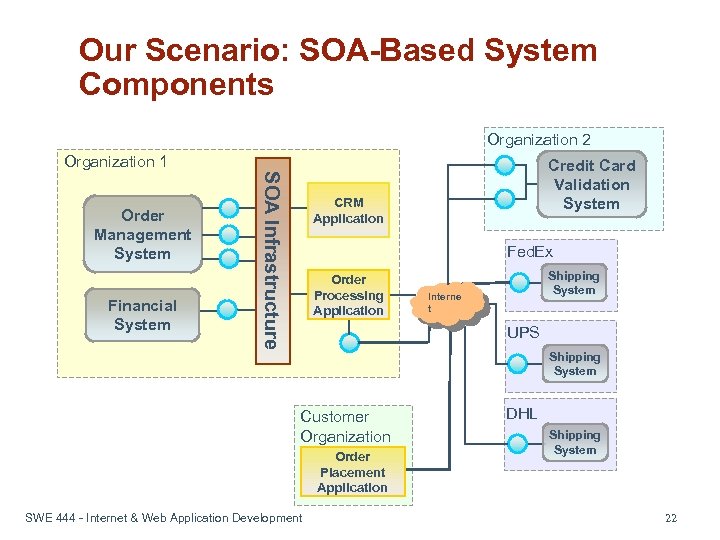
Our Scenario: SOA-Based System Components Organization 2 Organization 1 Financial System SOA Infrastructure Order Management System Credit Card Validation System CRM Application Fed. Ex Order Processing Application Shipping System Interne t UPS Shipping System Customer Organization Order Placement Application SWE 444 - Internet & Web Application Development DHL Shipping System 22
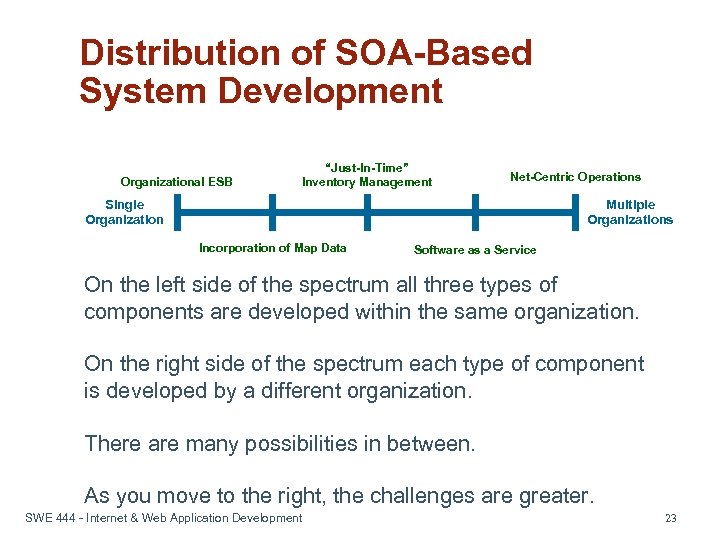
Distribution of SOA-Based System Development Organizational ESB “Just-In-Time” Inventory Management Net-Centric Operations Single Organization Multiple Organizations Incorporation of Map Data Software as a Service On the left side of the spectrum all three types of components are developed within the same organization. On the right side of the spectrum each type of component is developed by a different organization. There are many possibilities in between. As you move to the right, the challenges are greater. SWE 444 - Internet & Web Application Development 23
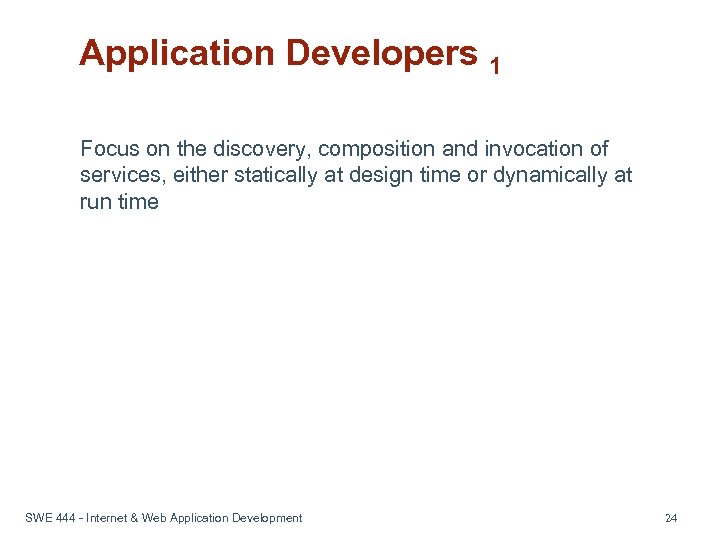
Application Developers 1 Focus on the discovery, composition and invocation of services, either statically at design time or dynamically at run time SWE 444 - Internet & Web Application Development 24
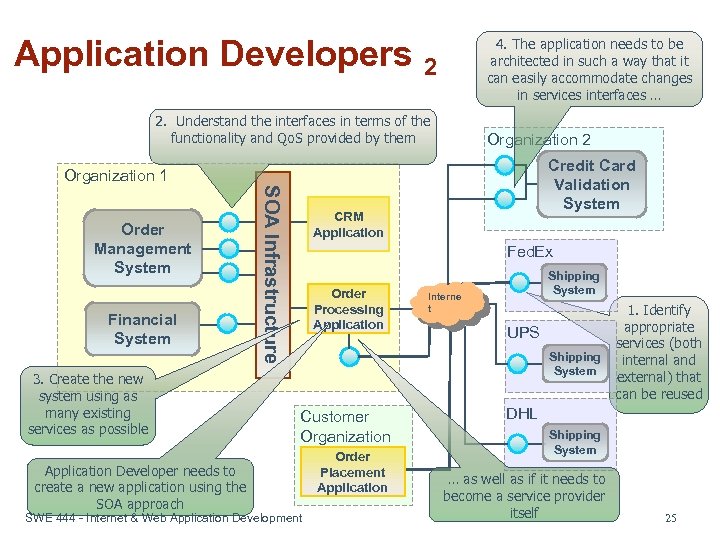
Application Developers 2 4. The application needs to be architected in such a way that it can easily accommodate changes in services interfaces … 2. Understand the interfaces in terms of the functionality and Qo. S provided by them Organization 2 Credit Card Validation System Organization 1 Financial System 3. Create the new system using as many existing services as possible Application Developer needs to create a new application using the SOA approach SOA Infrastructure Order Management System CRM Application Fed. Ex Order Processing Application Shipping System Interne t UPS Shipping System Customer Organization SWE 444 - Internet & Web Application Development Order Placement Application 1. Identify appropriate services (both internal and external) that can be reused DHL Shipping System … as well as if it needs to become a service provider itself 25

Tasks for Application Developers Understand the SOA infrastructure Discover appropriate services to be incorporated into applications Retrieve service description documentation Invoke the identified services in applications • Data conversions • Error handling • Availability handling Test the services for correctness in the context of the application being developed SWE 444 - Internet & Web Application Development 26

Service Developers Focus on the description and granularity of services so that applications can easily locate and use them with acceptable Quality of Service (Qo. S) SWE 444 - Internet & Web Application Development 27
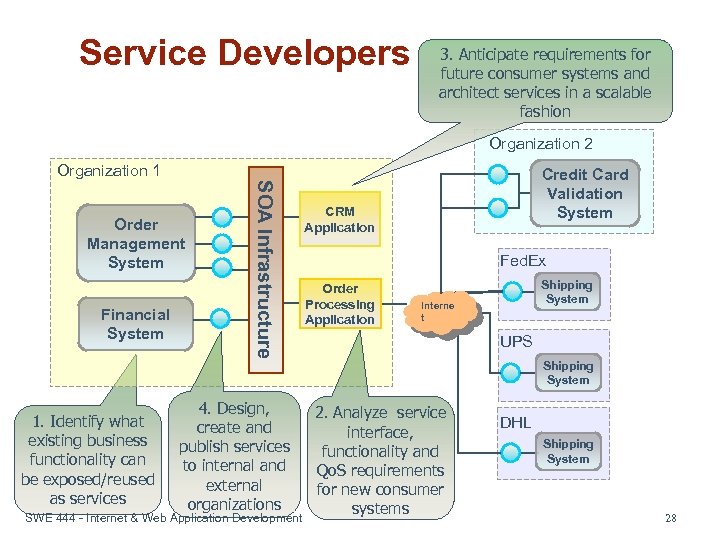
Service Developers 3. Anticipate requirements for future consumer systems and architect services in a scalable fashion Organization 2 Organization 1 Financial System 1. Identify what existing business functionality can be exposed/reused as services SOA Infrastructure Order Management System 4. Design, create and publish services to internal and external organizations SWE 444 - Internet & Web Application Development Credit Card Validation System CRM Application Fed. Ex Order Processing Application Shipping System Interne t UPS Shipping System 2. Analyze service interface, functionality and Qo. S requirements for new consumer systems DHL Shipping System 28

Tasks for Service Developers Understand requirements of potential service users Understand SOA infrastructure Develop code that receives the service request, translates it into calls into new or existing systems, and produces a response Describe and publish the service Develop service initialization code and operational procedures • Service-Level Agreements (SLAs) are a topic of current interest among service providers. SWE 444 - Internet & Web Application Development 29
Infrastructure Developers Focus on providing a stable infrastructure • Standards • Common services • Development tools NOTE: The Enterprise Service Bus (ESB) is an example of an infrastructure designed to support the SOA paradigm. SWE 444 - Internet & Web Application Development 30
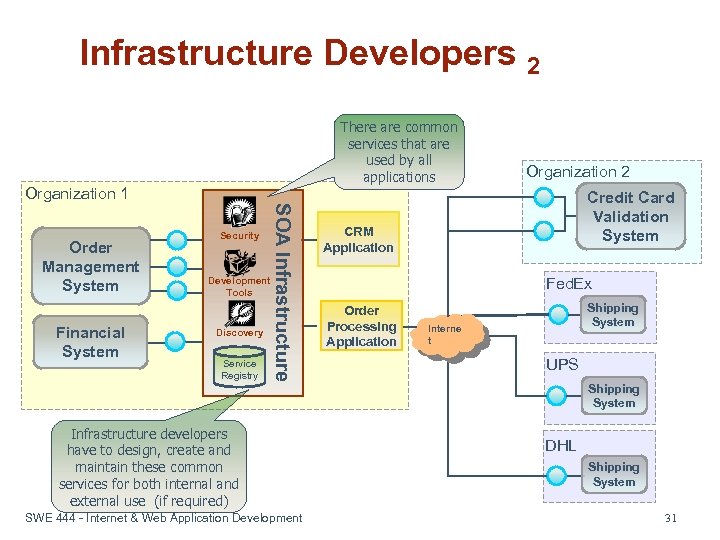
Infrastructure Developers 2 There are common services that are used by all applications Organization 1 Financial System Development Tools Discovery Service Registry SOA Infrastructure Order Management System Security Infrastructure developers have to design, create and maintain these common services for both internal and external use (if required) SWE 444 - Internet & Web Application Development Organization 2 Credit Card Validation System CRM Application Fed. Ex Order Processing Application Shipping System Interne t UPS Shipping System DHL Shipping System 31

Tasks for Infrastructure Developers Selection of standards to implement as part of the infrastructure Development of a set of common infrastructure services for discovery, communication, security, etc. Identification and development of binding mechanisms to satisfy the largest set of potential service users Provision of tools for application and service developers Documentation and support for the infrastructure SWE 444 - Internet & Web Application Development 32

The Potential Problem If the three types of components are developed within the same organization, the challenges are less. • Simpler communication between developers (or might even be the same developers) However, it is becoming increasingly common for these three types of components to be developed independently by separate organizations. • Decisions made locally by any one of these development groups can have an effect on the other groups. SWE 444 - Internet & Web Application Development 33

Sample Consequences of Decisions: Service Granularity 1 The granularity of service interfaces can affect the end-toend performance of an So. S because services are executed across a network as an exchange of a service request and a service response. • If service interfaces are too coarse-grained, clients will receive more data than they need in their response message. • If service interfaces are too fine-grained, clients will have to make multiple trips to the service to get all the data they need. SWE 444 - Internet & Web Application Development 34
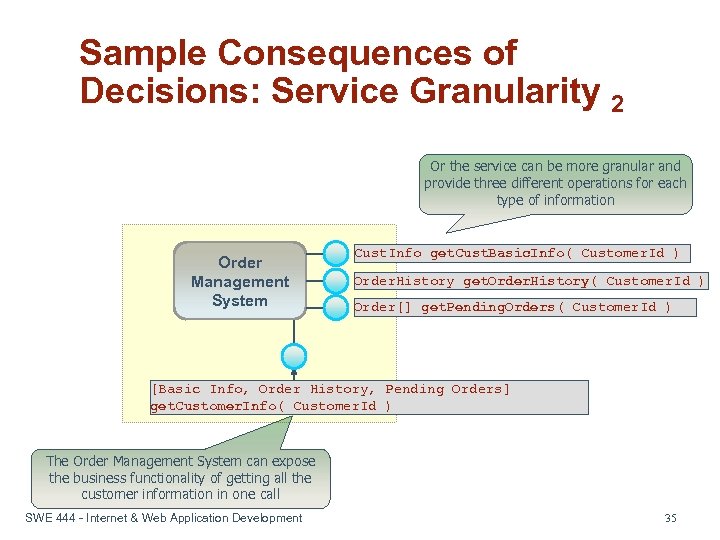
Sample Consequences of Decisions: Service Granularity 2 Or the service can be more granular and provide three different operations for each type of information Order Management System Cust. Info get. Cust. Basic. Info( Customer. Id ) Order. History get. Order. History( Customer. Id ) Order[] get. Pending. Orders( Customer. Id ) [Basic Info, Order History, Pending Orders] get. Customer. Info( Customer. Id ) The Order Management System can expose the business functionality of getting all the customer information in one call SWE 444 - Internet & Web Application Development 35

Sample Consequences of Decisions: Requirements 1 If service developers do not understand functionality and Qo. S needs of potential users of services, they might end up developing and deploying services that are never used SWE 444 - Internet & Web Application Development 36
In Summary … SOA-based systems are about more than just technology. SOA-based systems development requires 1. Strategic approach to SOA implementation • Alignment with business goals 2. SOA governance • Policies, coordination and guidance for SOA infrastructure providers, service providers, and application developers 3. Realistic technology evaluation • Context-based technology evaluations 4. Change of mindset • Different development and implementation approach SWE 444 - Internet & Web Application Development 37

Security for e-Commerce SWE 444 - Internet & Web Application Development 8. 38

Definition of e-Commerce n E-commerce involves digitally enabled commercial transactions between and among organizations and individuals n Digitally enabled transactions include all transactions mediated by digital technology n Commercial transactions involve the exchange of value across organizational or individual boundaries in return for products or services n e-Commerce vs. e-Business ¨ ¨ E-Commerce: direct financial electronic transaction (e. g. , ordering a book on Amazon. com) E-Business: use of the Internet and the Web to better support any current manner of doing business.

Seven Unique Features of e-Commerce n Is ubiquitous (available everywhere, all the time) n Offers global reach (across cultural/national boundaries) n Operates according to universal standards (lowers market entry for merchants and search costs for consumers) n Provides information richness (more powerful selling environment) n Is interactive (can simulate face-to-face experience, but on global scale) n Increases information density (amount and quality of information available to all market participants) n Permits personalization/customization

Types of e-Commerce n Classified by nature of market relationship ¨ ¨ ¨ n Business-to-Consumer (B 2 C) Business-to-Business (B 2 B) Consumer-to-Consumer (C 2 C) Classified by type of technology used ¨ ¨ Peer-to-Peer (P 2 P) Mobile commerce (M-commerce)

Advantages n Quick n Easy n Time Saver n Variety of choices n Comparison

Disadvantages n Security --- very important n Speed of internet access n Malfunction of website n Physically touching the product n Shipping and handling n Who to deal with when customer is not satisfied

Dimensions of e-Commerce Security n Integrity: ability to ensure that information being displayed on a Web site or transmitted/received over the Internet has not been altered in any way by an unauthorized party n Nonrepudiation: ability to ensure that e-commerce participants do not deny (repudiate) online actions n Authenticity: ability to identify the identity of a person or entity with whom you are dealing on the Internet n Confidentiality: ability to ensure that messages and data are available only to those authorized to view them n Privacy: ability to control use of information a customer provides about himself or herself to merchant n Availability: ability to ensure that an e-commerce site continues to function as intended
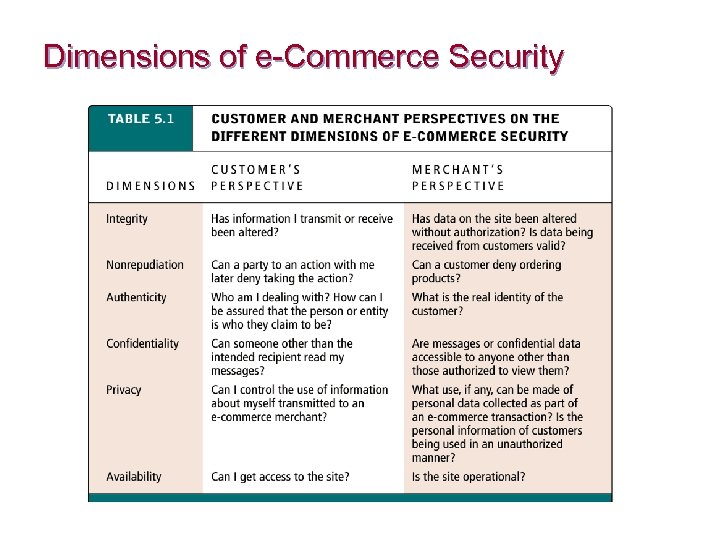
Dimensions of e-Commerce Security

Security Threats in the e-Commerce Environment n Three key points of vulnerability: ¨ ¨ ¨ n Client Server Communications channel Most common threats: ¨ ¨ ¨ ¨ Malicious code Hacking and cybervandalism Credit card fraud/theft Spoofing Denial of service attacks Sniffing Insider jobs
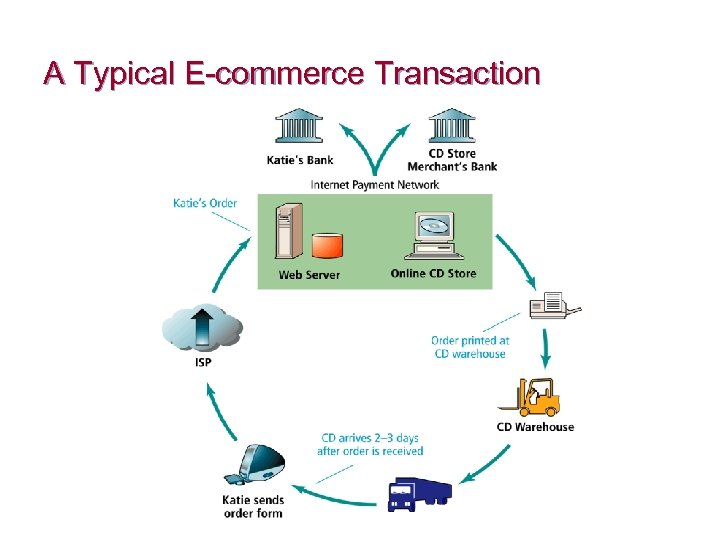
A Typical E-commerce Transaction
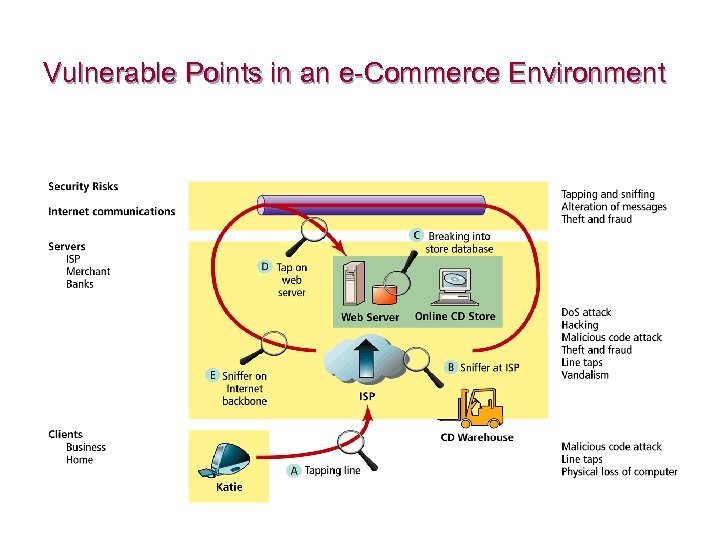
Vulnerable Points in an e-Commerce Environment

Technology Solutions n Protecting Internet communications (encryption) n Securing channels of communication (SSL, S-HTTP, VPNs) n Protecting networks (firewalls) n Protecting servers and clients
Protecting Internet Communications: Encryption n Encryption: The process of transforming plain text or data into cipher text that cannot be read by anyone other than the sender and receiver n Purpose: ¨ ¨ n Secure stored information Secure information transmission Provides: ¨ ¨ Message integrity Nonrepudiation Authentication Confidentiality

Cryptography n Cryptography is the science or study of secret writing (cipher texts) ¨ n Basic idea: convert clear text (also called plain text – the original message) to ciphertext (the encrypted message) Three Main Categories ¨ Secret Key (Symmetric Encryption) Ø ¨ Public/Private Key (Asymmetric Encryption) Ø ¨ single key is used to encrypt and decrypt information two keys are used: one for encryption (public key) and one for decryption (private key) One-way Function ¨ information is encrypted to produce a “digest” of the original information that can be used later to prove its authenticity
Symmetric Key Encryption n Also known as secret key encryption n Both the sender and receiver use the same digital key to encrypt and decrypt message n Requires a different set of keys for each transaction n Data Encryption Standard (DES): Most widely used symmetric key encryption today; uses 56 -bit encryption key; other types use 128 -bit keys up through 2048 bits n Other known symmetrical algorithms ¨ Triple DES, DESX, GDES, RDES Ø ¨ RC 2, RC 4, RC 5 Ø ¨ variable length up to 2048 bits IDEA - basis of PGP Ø ¨ 168 bit key 128 bit key Blowfish Ø variable length up to 448 bits
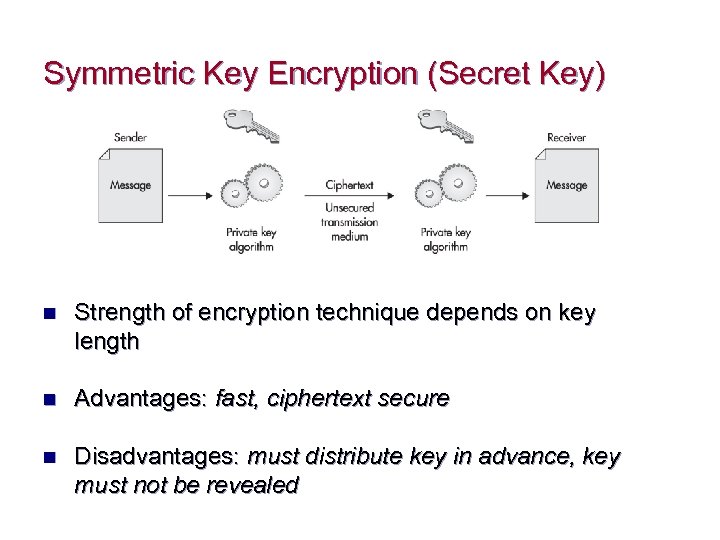
Symmetric Key Encryption (Secret Key) n Strength of encryption technique depends on key length n Advantages: fast, ciphertext secure n Disadvantages: must distribute key in advance, key must not be revealed
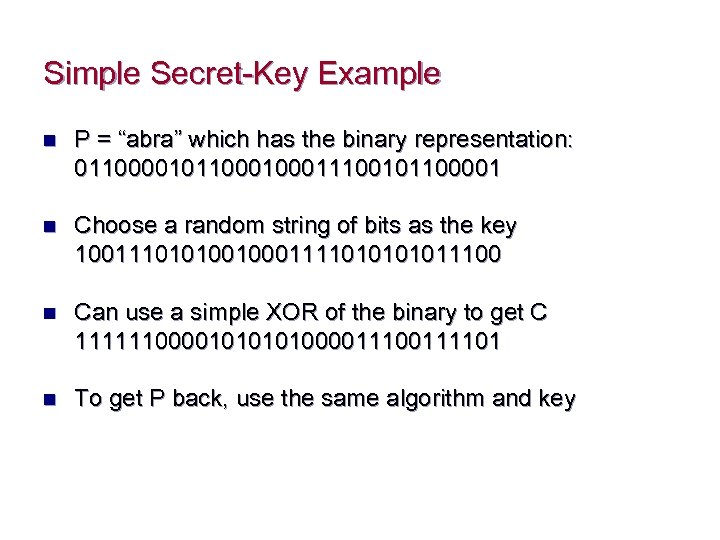
Simple Secret-Key Example n P = “abra” which has the binary representation: 0110000101100011100101100001 n Choose a random string of bits as the key 1001110101001000111101011100 n Can use a simple XOR of the binary to get C 11111100001010000111101 n To get P back, use the same algorithm and key
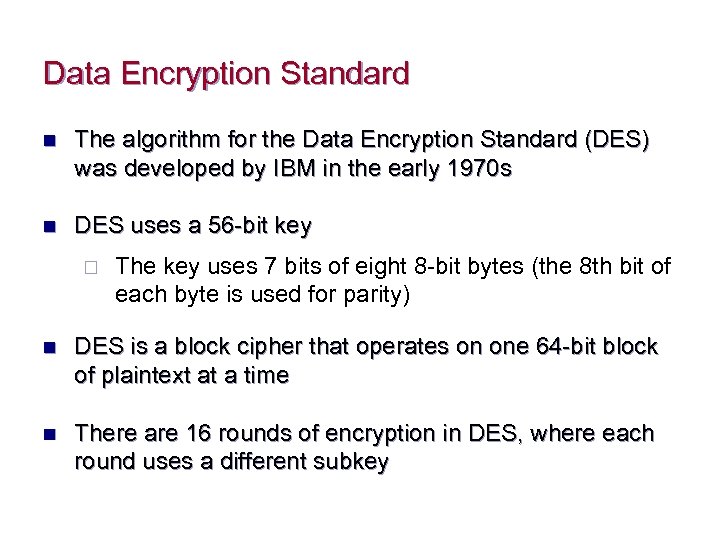
Data Encryption Standard n The algorithm for the Data Encryption Standard (DES) was developed by IBM in the early 1970 s n DES uses a 56 -bit key ¨ The key uses 7 bits of eight 8 -bit bytes (the 8 th bit of each byte is used for parity) n DES is a block cipher that operates on one 64 -bit block of plaintext at a time n There are 16 rounds of encryption in DES, where each round uses a different subkey
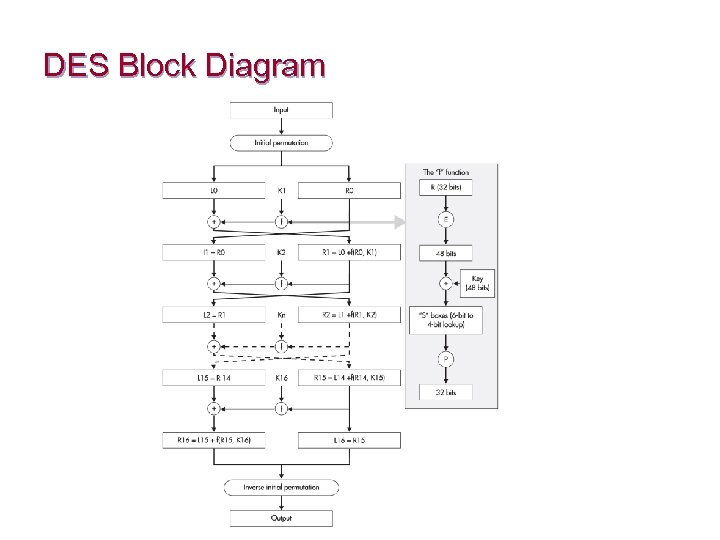
DES Block Diagram

Public Key Encryption n Probably most significant advance in the 3000 year history of cryptography n Public key cryptography solves symmetric key encryption problem of having to exchange secret key n Uses two mathematically related digital keys – public key (widely disseminated) and private key (kept secret by owner) n Both keys are used to encrypt and decrypt message n Once key is used to encrypt message, same key cannot be used to decrypt message n For example, sender uses recipient’s public key to encrypt message; recipient uses his/her private key to decrypt it n Most common algorithm is the RSA algorithm with key lengths from 512 to 1024 bits
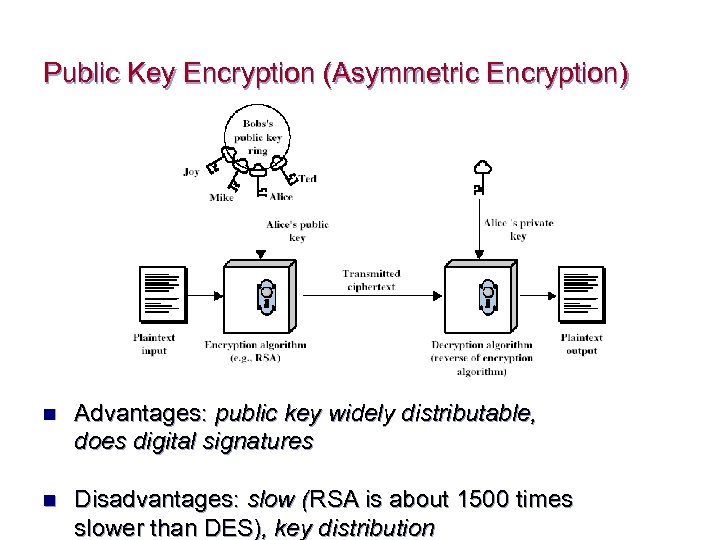
Public Key Encryption (Asymmetric Encryption) n Advantages: public key widely distributable, does digital signatures n Disadvantages: slow (RSA is about 1500 times slower than DES), key distribution
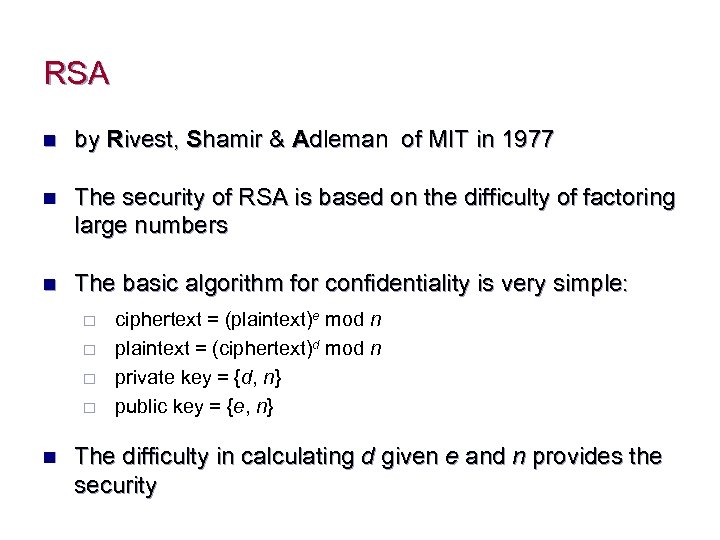
RSA n by Rivest, Shamir & Adleman of MIT in 1977 n The security of RSA is based on the difficulty of factoring large numbers n The basic algorithm for confidentiality is very simple: ¨ ¨ n ciphertext = (plaintext)e mod n plaintext = (ciphertext)d mod n private key = {d, n} public key = {e, n} The difficulty in calculating d given e and n provides the security

Generating RSA keys n To generate an RSA key pair, follow these steps: ¨ ¨ Choose two prime numbers p and q and keep them secret Calculate n = p x q Calculate φ(n) = (p - 1)(q - 1) Select e such that e is relatively prime to φ(n) Ø ¨ ¨ ¨ gcd (φ(n), e) = 1; 1< e <φ(n) Calculate d = e -1 mod φ(n) Public Key KU = {e, n} Private Key KR = {d, n}
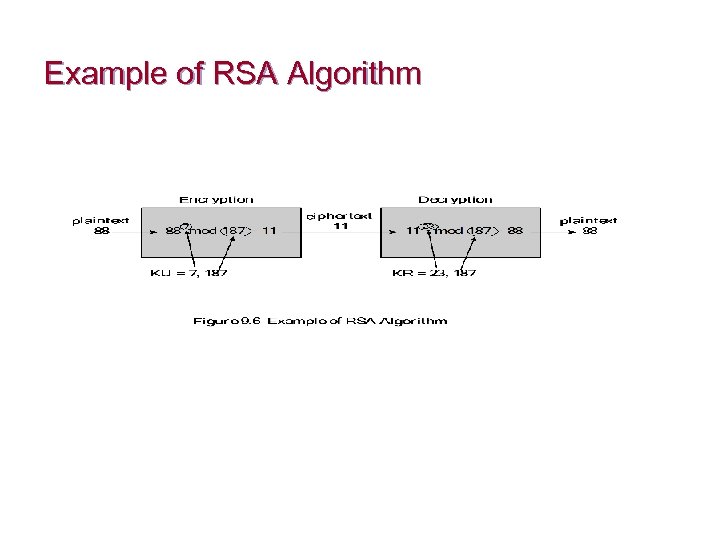
Example of RSA Algorithm

One-Way Function n non-reversible “quick” encryption n produces a fixed length value called a hash or message digest n used to authenticate contents of a message n Common message digest functions ¨ MD 4 and MD 5 Ø ¨ produces 128 bit hashes SHA Ø produces 160 bit hashes
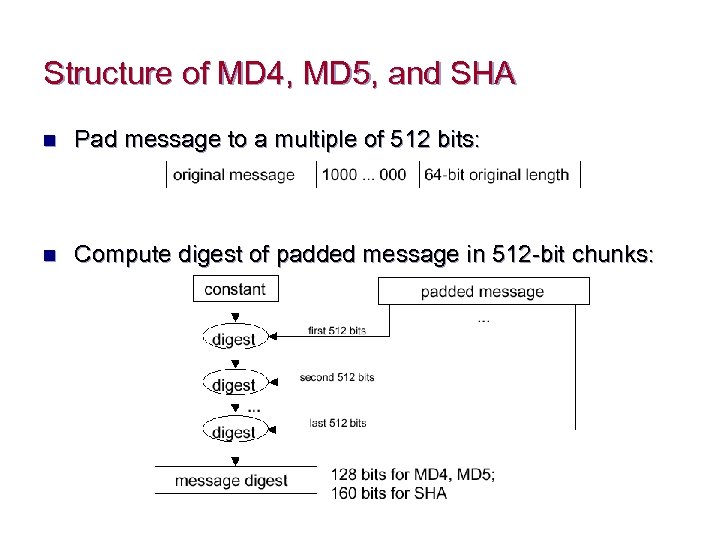
Structure of MD 4, MD 5, and SHA n Pad message to a multiple of 512 bits: n Compute digest of padded message in 512 -bit chunks:

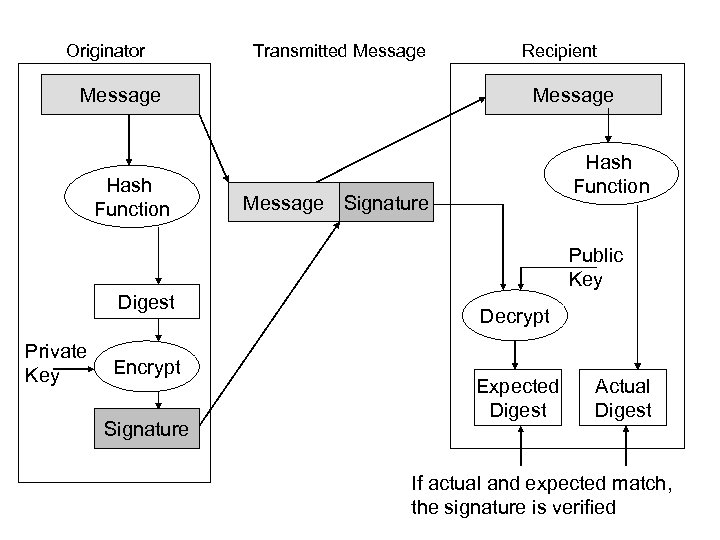
Cryptographic Services Allow n Digital Signatures ¨ n Message Digests ¨ n secure delivery of secret keys Certificates (Digital IDs) ¨ n short bit string hash of message Digital Envelopes ¨ n sign messages to validate source and integrity of the contents used to authenticate: users, web sites, public keys of public/private pair, and information in general Secure Channels ¨ encryption can be used to create secure channels over private or public networks

Digital Signatures n Digital Signature ¨ ¨ ¨ Encrypt sender’s identity string with sender’s private key Concatenate the encrypted text and the identity string together Encrypt this message with receiver’s public key to create message Receiver decrypts the encrypted text with their private key the cypher text portion of the message is decrypted with sender’s public key The decrypted text can be compared with the normal text to checks its integrity
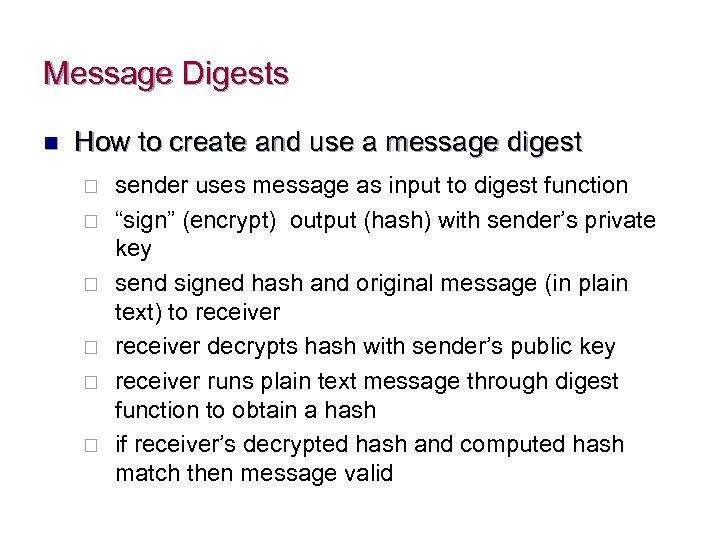
Message Digests n How to create and use a message digest ¨ ¨ ¨ sender uses message as input to digest function “sign” (encrypt) output (hash) with sender’s private key send signed hash and original message (in plain text) to receiver decrypts hash with sender’s public key receiver runs plain text message through digest function to obtain a hash if receiver’s decrypted hash and computed hash match then message valid
Originator Transmitted Message Hash Function Recipient Message Hash Function Message Signature Public Key Digest Private Key Encrypt Signature Decrypt Expected Digest Actual Digest If actual and expected match, the signature is verified
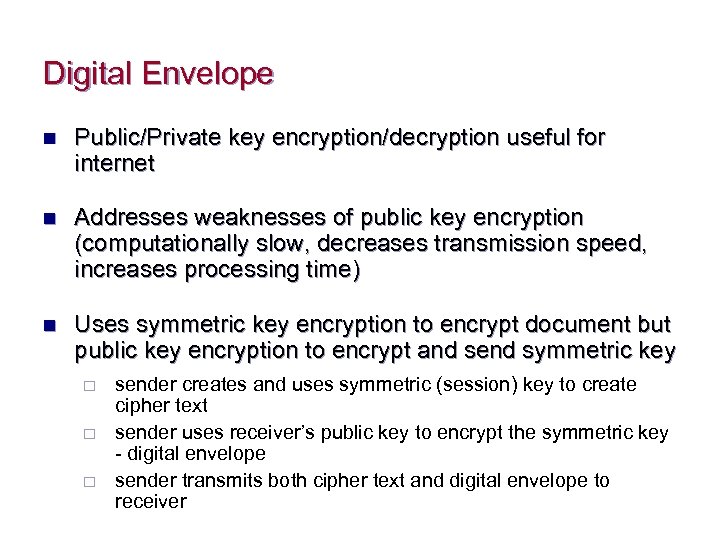
Digital Envelope n Public/Private key encryption/decryption useful for internet n Addresses weaknesses of public key encryption (computationally slow, decreases transmission speed, increases processing time) n Uses symmetric key encryption to encrypt document but public key encryption to encrypt and send symmetric key ¨ ¨ ¨ sender creates and uses symmetric (session) key to create cipher text sender uses receiver’s public key to encrypt the symmetric key - digital envelope sender transmits both cipher text and digital envelope to receiver

Understand Key Management n Key management is one of the most critical aspects of an encryption system n It includes creating strong keys, distributing them securely, certifying them, protecting while in use, and revoking them when they are compromised or expired n Keys must be transported securely to ensure the integrity of the keys n If keys are transmitted, they must be checked on arrival to ensure they have not been manipulated (usually done manually or by digital signatures) n Certificate Authorities (CAs) ensure the integrity of the keys and prevent an attacker from introducing their own keys

Digital Certificates n Certificate Authorities (CAs) ensure the integrity of the keys and prevent an attacker from introducing their own keys n Public keys require integrity protection (provided by certification), but they do not require confidentiality protection. However, all copies of the private key of a public key system must be protected at all times n Certification Authorities (CA) ¨ ¨ used to distribute the public key of a public/private pair guarantees the validity of the public key Ø ¨ Some Cases Ø Ø n does this by verifying the credentials of the entity associated with the public key Veri. Sign - http: //www. verisign. com Entrust - http: //www. entrust. com Public key pairs are generally certified for one or two years ¨ Session keys may only exist for a given session and may be deleted after the session

… Digital Certificates n Process to create Digital Certificate ¨ ¨ User generates public/private pair User creates and sends a certificate request his choice of CA contains: identifying information and user’s public key Ø ¨ ¨ ¨ Like Server, company, location, state, country and also the documents proving identity CA confirms the accuracy of the information submitted CA creates a certificate containing user’s public key and information CA creates message digest from certificate and signs it with CA’s private key This a signed certificate The certificate is sent to the subscriber and also a copy of it may be submitted to the certificate repository, such as a directory service for publication

… Digital Certificates n Using a Digital Certificate ¨ ¨ before sending a secure message sender request a signed certificate from receiver sender decrypts signed certificate with CA’s known public key to obtain message digest of info and public key provided to CA by receiver sender creates a message digest of public key and info provided by the receiver for sender’s use sender compare the message digests if they match then receiver is validated

Digital Certificate Verification n Do I trust the CA? (Is it in my list of trust root certification authorities? ) n Is the certificate genuine? ¨ ¨ Look up the CA’s public key; use it to decrypt the signature Compute the certificate’s hash; compare with decrypted sig n Is the holder genuine? This requires a challenge n If the holder is genuine, he must know the private key corresponding to the pubic key in the certificate n Having the certificate is not enough. (They are exchanged over the Internet all the time) n Send him a nonce (random 128 -bit number)
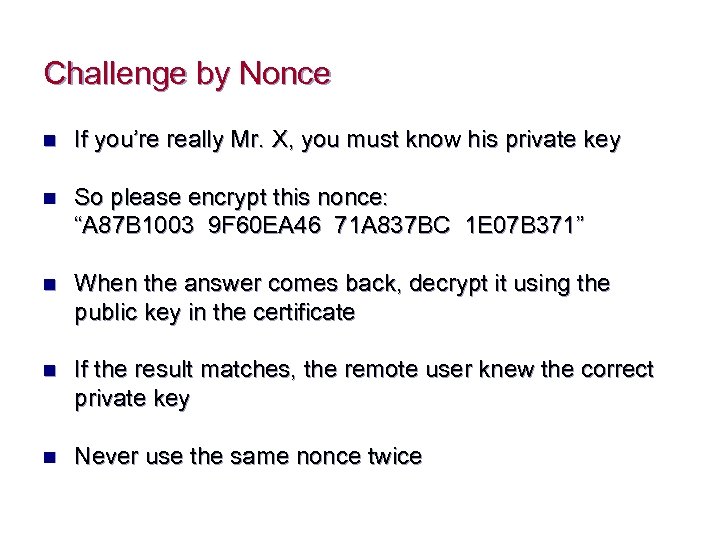
Challenge by Nonce n If you’re really Mr. X, you must know his private key n So please encrypt this nonce: “A 87 B 1003 9 F 60 EA 46 71 A 837 BC 1 E 07 B 371” n When the answer comes back, decrypt it using the public key in the certificate n If the result matches, the remote user knew the correct private key n Never use the same nonce twice
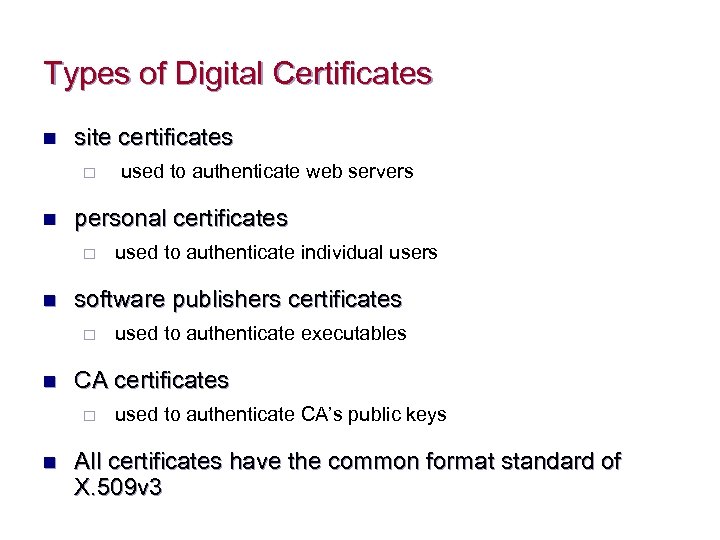
Types of Digital Certificates n site certificates ¨ n personal certificates ¨ n used to authenticate executables CA certificates ¨ n used to authenticate individual users software publishers certificates ¨ n used to authenticate web servers used to authenticate CA’s public keys All certificates have the common format standard of X. 509 v 3

Digital Certificate Contents n Name of holder n Public key of holder n Name of trusted third party (certificate authority) n DIGITAL SIGNATURE OF CERTIFICATE AUTHORITY n Data on which hash and public-key algorithms have been used n Other business or personal information
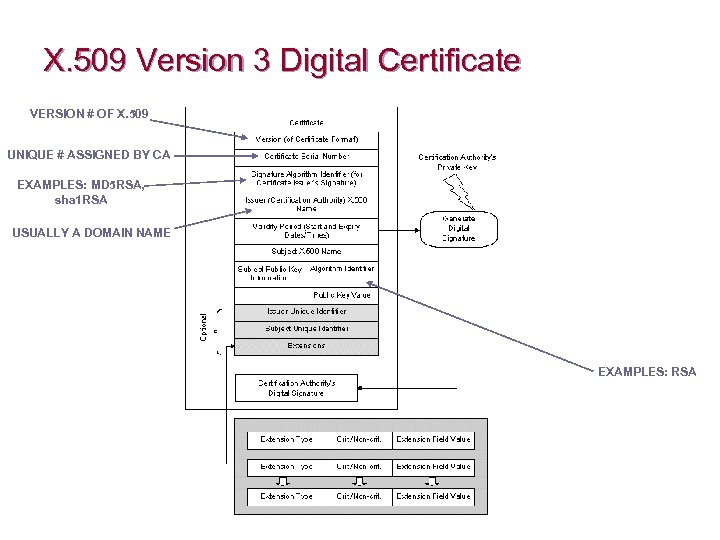
X. 509 Version 3 Digital Certificate VERSION # OF X. 509 UNIQUE # ASSIGNED BY CA EXAMPLES: MD 5 RSA, sha 1 RSA USUALLY A DOMAIN NAME EXAMPLES: RSA

Public Key Infrastructure (PKI) n Digital certificates alone are not enough to establish security ¨ Need control over certificate issuance and management n PKI: refers to the CAs and digital certificate procedures that are accepted by all parties n Functions of a PKI ¨ Generate public/private key pairs ¨ Identify and authenticate key subscribers ¨ Bind public keys to subscriber by digital certificate ¨ Issue, maintain, administer, revoke, suspend, reinstate, and renew digital certificates ¨ Create and manage a public key repository

Securing Channels of Communication n Secure Sockets Layer (SSL): Most common form of securing channels of communication ¨ n S-HTTP: Alternative method ¨ n used to establish a secure negotiated session (clientserver session in which URL of requested document, along with contents, is encrypted) provides a secure message-oriented communications protocol designed for use in conjunction with HTTP Virtual Private Networks (VPNs) ¨ Allow remote users to securely access internal networks via the Internet, using Tunneling Protocol
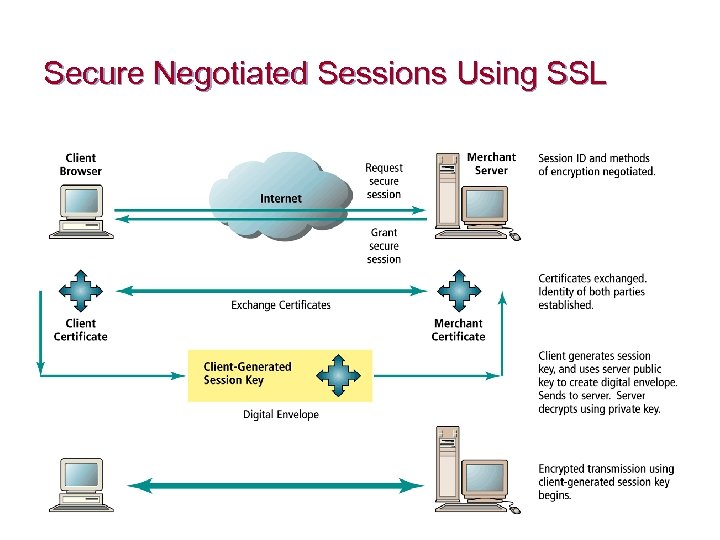
Secure Negotiated Sessions Using SSL

Internet Tunnels n virtual network circuit across the Internet between specified remote sites ¨ n uses an encrypting router that automatically encrypts all traffic that traverses the links of the virtual circuit Tunneling Protocols ¨ ¨ ¨ PPTP by Microsoft - http: //www. microsoft. com Layer 2 Forwarding (L 2 F) by Cisco http: //www. cisco. com L 2 TP (combines PPTP and L 2 F) http: //www. ietf. com

Secure Sockets Layer n SSL History ¨ ¨ ¨ Competitor to S-HTTP an extension of HTTP General purpose encryption system using symmetric encryption S-HTTP only encrypts Web protocols Three versions v 1. 0, v 2. 0 and v 3. 0 Ø Ø SSL v 3. 0 implemented in Netscape 3. 0 and Internet Explorer 3. 0 and higher SSL v 3. 0 supports Diffie-Hellman anonymous key exchange and Fortezza smart card
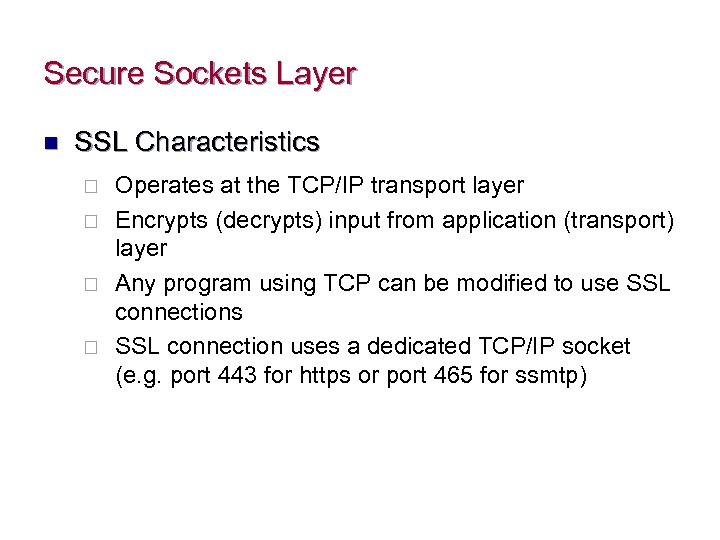
Secure Sockets Layer n SSL Characteristics ¨ ¨ Operates at the TCP/IP transport layer Encrypts (decrypts) input from application (transport) layer Any program using TCP can be modified to use SSL connections SSL connection uses a dedicated TCP/IP socket (e. g. port 443 for https or port 465 for ssmtp)
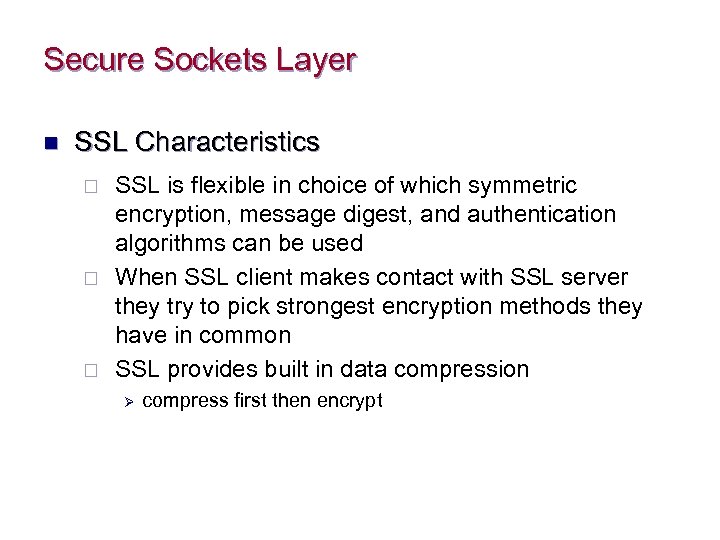
Secure Sockets Layer n SSL Characteristics ¨ ¨ ¨ SSL is flexible in choice of which symmetric encryption, message digest, and authentication algorithms can be used When SSL client makes contact with SSL server they try to pick strongest encryption methods they have in common SSL provides built in data compression Ø compress first then encrypt
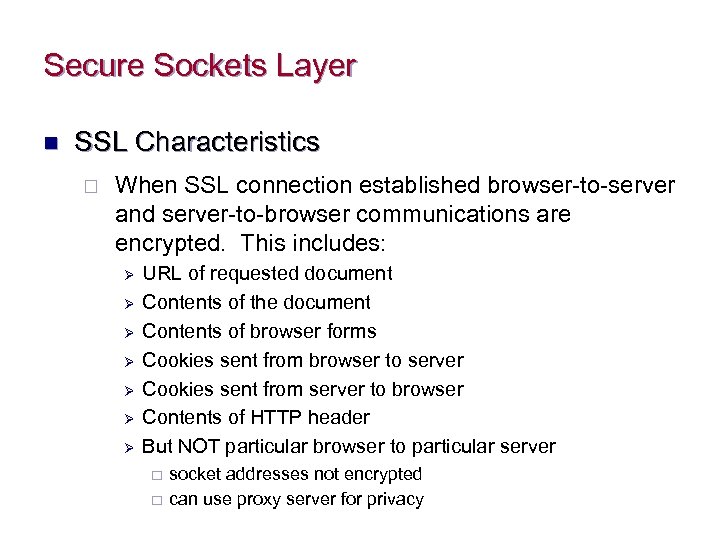
Secure Sockets Layer n SSL Characteristics ¨ When SSL connection established browser-to-server and server-to-browser communications are encrypted. This includes: Ø Ø Ø Ø URL of requested document Contents of the document Contents of browser forms Cookies sent from browser to server Cookies sent from server to browser Contents of HTTP header But NOT particular browser to particular server ¨ ¨ socket addresses not encrypted can use proxy server for privacy
Secure Sockets Layer n Establishing an SSL Connection ¨ ¨ The client (browser) opens a connection to server port Browser sends “client hello” message. Client hello message contains: Ø Ø ¨ version of SSL browser uses ciphers and data compression methods it supports The Server responds with a “server hello” message. Server hello message contains Ø Ø session id the chosen versions for ciphers and data compression methods
Secure Sockets Layer n Establishing an SSL Connection (con’t. ) ¨ The server sends its certificate Ø ¨ ¨ Optionally the server may request client’s certificate If requested, client will send its certificate of authentication Ø ¨ used to authenticate server to client if client has no certificate then connection failure Client sends a “Client. Key. Exchange” message Ø Ø symmetric session key chosen digital envelope is created using server’s public key and contains the symmetric session key
Secure Sockets Layer n Establishing an SSL Connection (con’t. ) ¨ ¨ ¨ Optionally, if client authentication is used the client will send a certificate verify message Server and client send “Change. Cipher. Spec” message indicating they are ready to begin encrypted transmission Client and server send “Finished” messages to each other Ø Ø These are a message digest of their entire conversation up to this point If the digests match then messages were received without interference
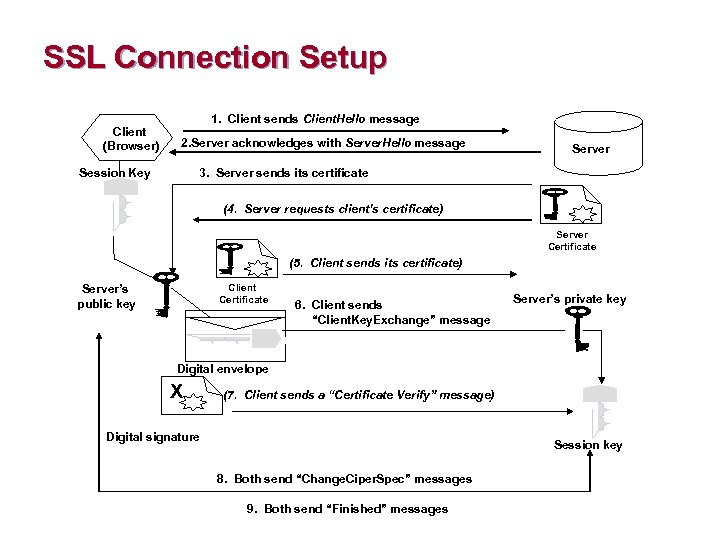
SSL Connection Setup Client (Browser) 1. Client sends Client. Hello message 2. Server acknowledges with Server. Hello message . Session Key Server 3. Server sends its certificate (4. Server requests client’s certificate) Server Certificate (5. Client sends its certificate) Client Certificate Server’s public key 6. Client sends “Client. Key. Exchange” message Server’s private key . Digital envelope X (7. Client sends a “Certificate Verify” message) Digital signature . Session key 8. Both send “Change. Ciper. Spec” messages 9. Both send “Finished” messages
a481315d12fe34e445a221b77a3a1a78.ppt