f53e1b63e7f671a629197ae4c1a1c534.ppt
- Количество слайдов: 30
 563. 3. 2 Do. S Detection and Defense Computer Security II CS 463/ECE 424 University of Illinois
563. 3. 2 Do. S Detection and Defense Computer Security II CS 463/ECE 424 University of Illinois
 Why is DDo. S Defense hard? • Simplicity – Plug-and-play attack tools • Traffic variety (similarity) – Attack traffic is as good as legitimate traffic • IP spoofing • High-volume traffic – Traffic profiling hard, requires per-packet processing • Short time span • Numerous agent machines • Weak spot in Internet topology – Highly connected and well-provisioned spots relay traffic for rest of the internet. [Mirkovic. DDR 04] 2
Why is DDo. S Defense hard? • Simplicity – Plug-and-play attack tools • Traffic variety (similarity) – Attack traffic is as good as legitimate traffic • IP spoofing • High-volume traffic – Traffic profiling hard, requires per-packet processing • Short time span • Numerous agent machines • Weak spot in Internet topology – Highly connected and well-provisioned spots relay traffic for rest of the internet. [Mirkovic. DDR 04] 2
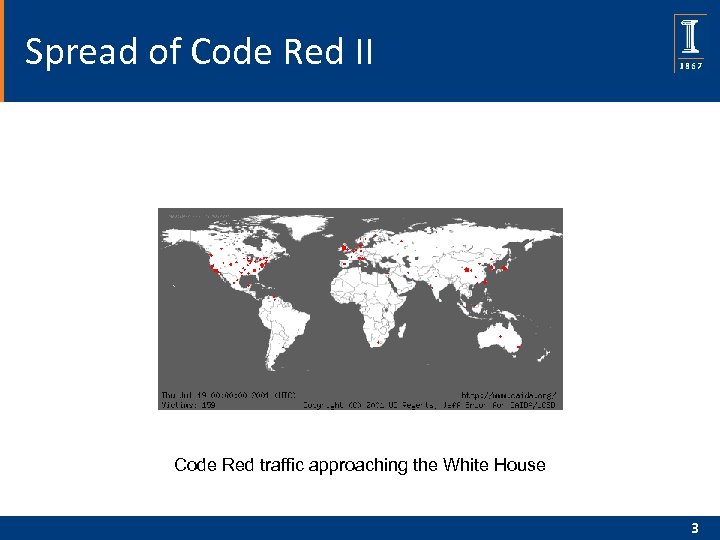 Spread of Code Red II Code Red traffic approaching the White House 3
Spread of Code Red II Code Red traffic approaching the White House 3
 Detecting Do. S Part 1 of 2 • How common are Do. S attacks and what is their nature? • Idea: conduct a survey of potential victims. Problem: how does a victim know it is was under attack? • Can an ISP recognize an attack using data gathered by its routers? 4
Detecting Do. S Part 1 of 2 • How common are Do. S attacks and what is their nature? • Idea: conduct a survey of potential victims. Problem: how does a victim know it is was under attack? • Can an ISP recognize an attack using data gathered by its routers? 4
![In-Network Monitoring [Sekar. DSMZ 06] 5 In-Network Monitoring [Sekar. DSMZ 06] 5](https://present5.com/presentation/f53e1b63e7f671a629197ae4c1a1c534/image-5.jpg) In-Network Monitoring [Sekar. DSMZ 06] 5
In-Network Monitoring [Sekar. DSMZ 06] 5
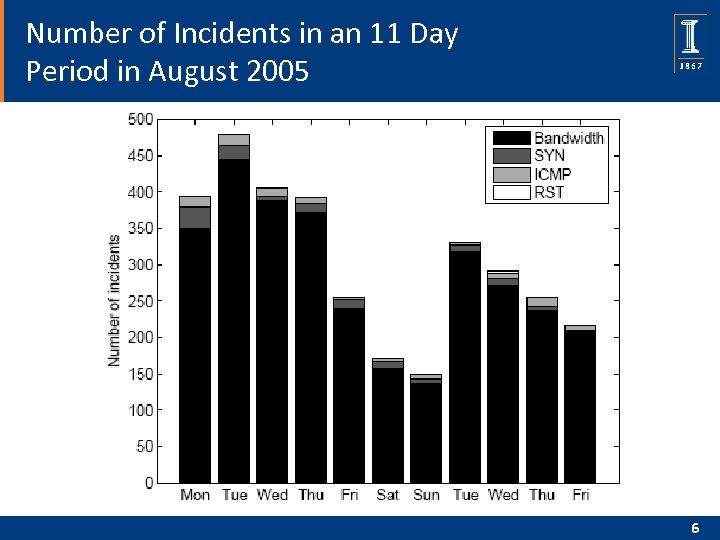 Number of Incidents in an 11 Day Period in August 2005 6
Number of Incidents in an 11 Day Period in August 2005 6
 Detecting Do. S Part 2 of 2 • Another idea: detect bad behavior that is a symptom of Do. S without cooperation of ISP. Examples: – Detect flows that violate TCP congestion control rules. – Detect spoofing. 7
Detecting Do. S Part 2 of 2 • Another idea: detect bad behavior that is a symptom of Do. S without cooperation of ISP. Examples: – Detect flows that violate TCP congestion control rules. – Detect spoofing. 7
![Backscatter Analysis [Moore. SBVS 06] 8 Backscatter Analysis [Moore. SBVS 06] 8](https://present5.com/presentation/f53e1b63e7f671a629197ae4c1a1c534/image-8.jpg) Backscatter Analysis [Moore. SBVS 06] 8
Backscatter Analysis [Moore. SBVS 06] 8
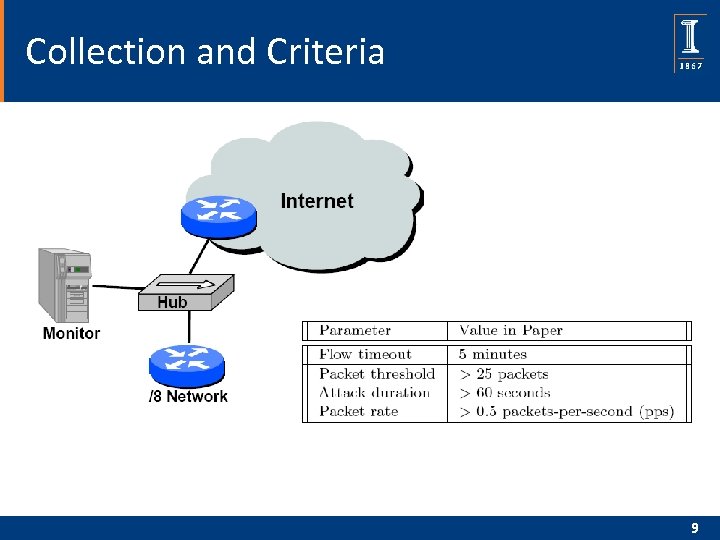 Collection and Criteria 9
Collection and Criteria 9
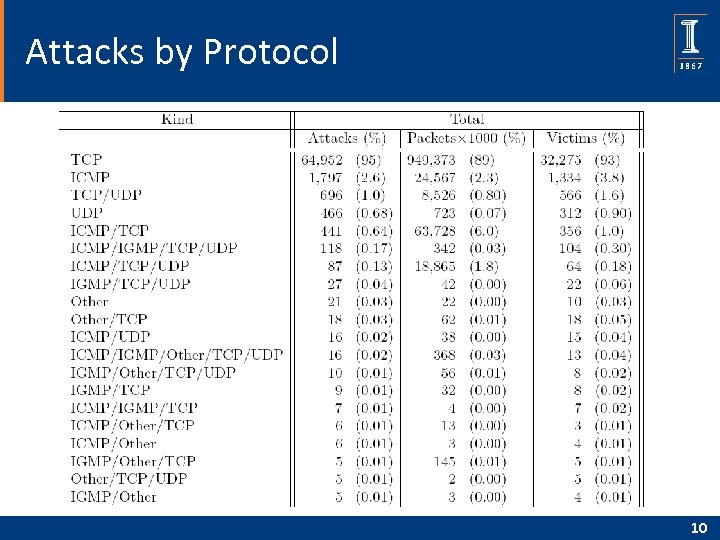 Attacks by Protocol 10
Attacks by Protocol 10
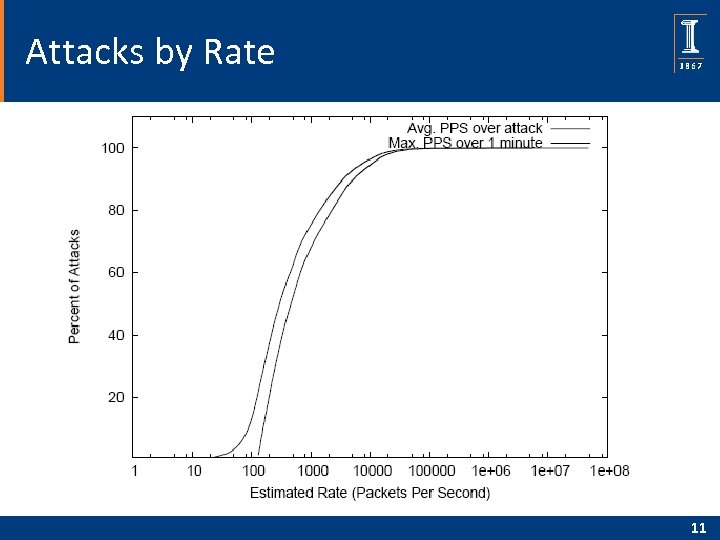 Attacks by Rate 11
Attacks by Rate 11
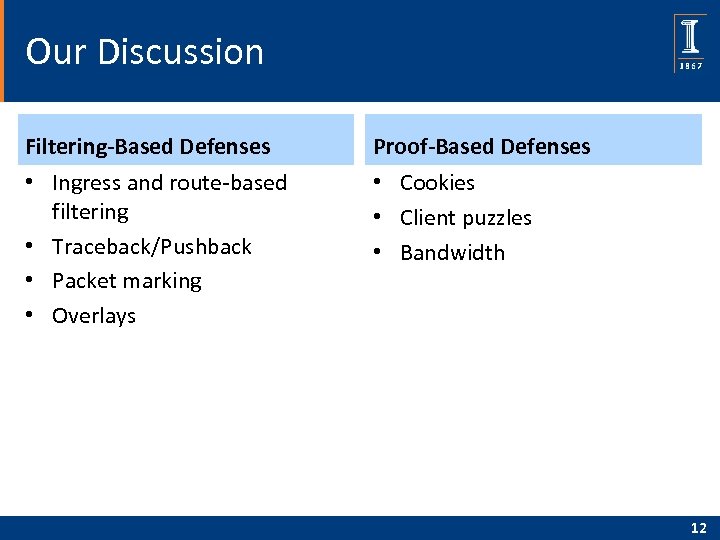 Our Discussion Filtering-Based Defenses Proof-Based Defenses • Ingress and route-based filtering • Traceback/Pushback • Packet marking • Overlays • Cookies • Client puzzles • Bandwidth 12
Our Discussion Filtering-Based Defenses Proof-Based Defenses • Ingress and route-based filtering • Traceback/Pushback • Packet marking • Overlays • Cookies • Client puzzles • Bandwidth 12
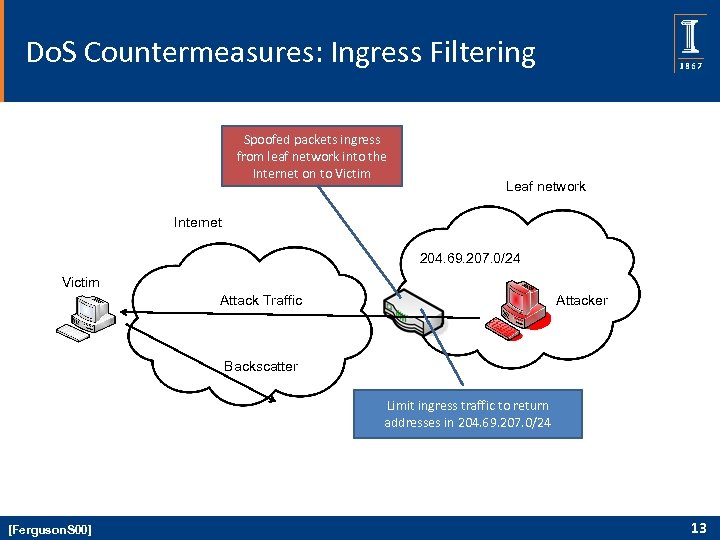 Do. S Countermeasures: Ingress Filtering Spoofed packets ingress from leaf network into the Internet on to Victim Leaf network Internet 204. 69. 207. 0/24 Victim Attack Traffic Attacker Backscatter Limit ingress traffic to return addresses in 204. 69. 207. 0/24 [Ferguson. S 00] 13
Do. S Countermeasures: Ingress Filtering Spoofed packets ingress from leaf network into the Internet on to Victim Leaf network Internet 204. 69. 207. 0/24 Victim Attack Traffic Attacker Backscatter Limit ingress traffic to return addresses in 204. 69. 207. 0/24 [Ferguson. S 00] 13
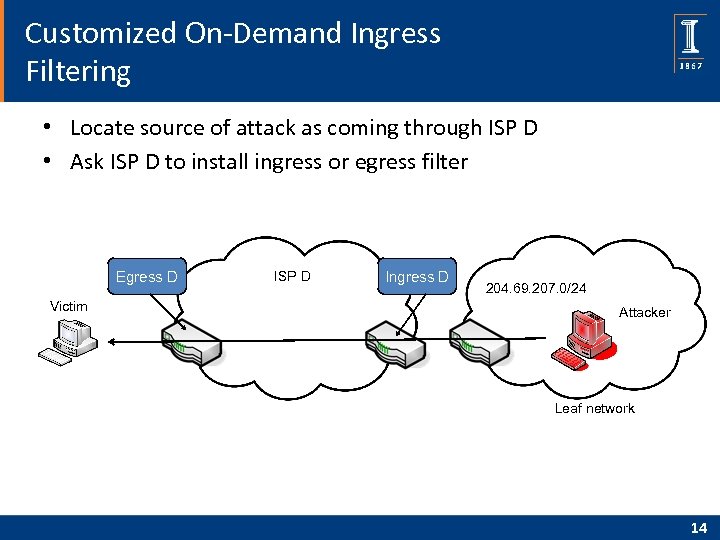 Customized On-Demand Ingress Filtering • Locate source of attack as coming through ISP D • Ask ISP D to install ingress or egress filter Egress D Victim ISP D Ingress D 204. 69. 207. 0/24 Attacker Leaf network 14
Customized On-Demand Ingress Filtering • Locate source of attack as coming through ISP D • Ask ISP D to install ingress or egress filter Egress D Victim ISP D Ingress D 204. 69. 207. 0/24 Attacker Leaf network 14
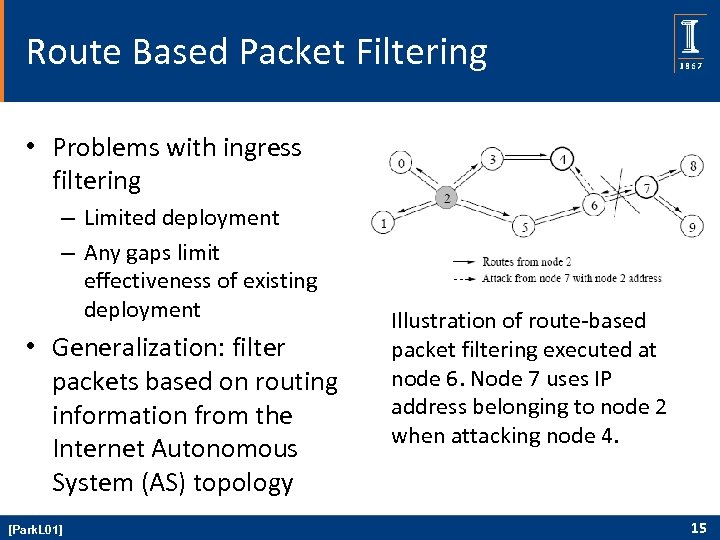 Route Based Packet Filtering • Problems with ingress filtering – Limited deployment – Any gaps limit effectiveness of existing deployment • Generalization: filter packets based on routing information from the Internet Autonomous System (AS) topology [Park. L 01] Illustration of route-based packet filtering executed at node 6. Node 7 uses IP address belonging to node 2 when attacking node 4. 15
Route Based Packet Filtering • Problems with ingress filtering – Limited deployment – Any gaps limit effectiveness of existing deployment • Generalization: filter packets based on routing information from the Internet Autonomous System (AS) topology [Park. L 01] Illustration of route-based packet filtering executed at node 6. Node 7 uses IP address belonging to node 2 when attacking node 4. 15
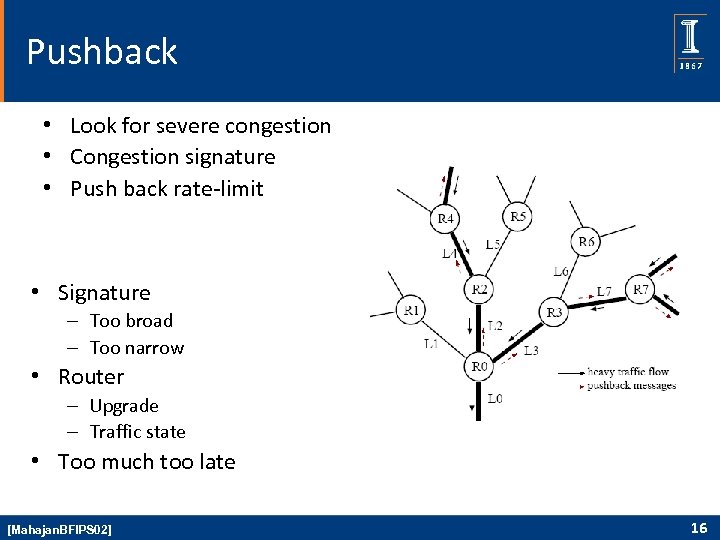 Pushback • Look for severe congestion • Congestion signature • Push back rate-limit • Signature – Too broad – Too narrow • Router – Upgrade – Traffic state • Too much too late [Mahajan. BFIPS 02] 16
Pushback • Look for severe congestion • Congestion signature • Push back rate-limit • Signature – Too broad – Too narrow • Router – Upgrade – Traffic state • Too much too late [Mahajan. BFIPS 02] 16
![Probabilistic Packet Marking to Traceback [Gao. A 05] 17 Probabilistic Packet Marking to Traceback [Gao. A 05] 17](https://present5.com/presentation/f53e1b63e7f671a629197ae4c1a1c534/image-17.jpg) Probabilistic Packet Marking to Traceback [Gao. A 05] 17
Probabilistic Packet Marking to Traceback [Gao. A 05] 17
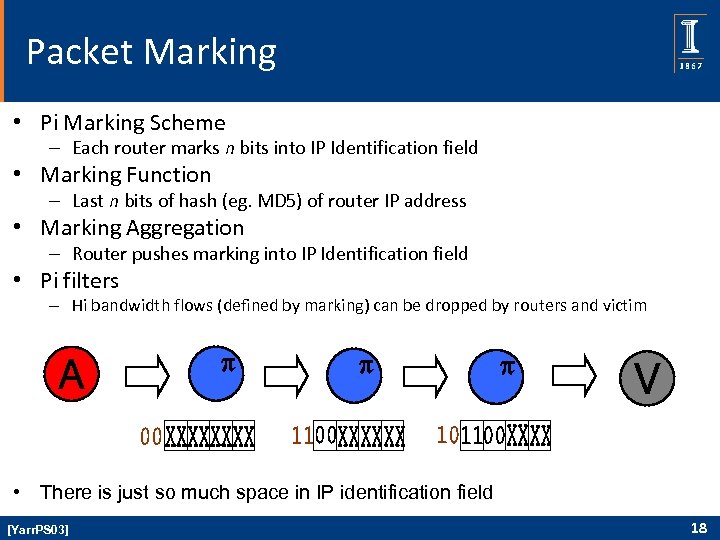 Packet Marking • Pi Marking Scheme – Each router marks n bits into IP Identification field • Marking Function – Last n bits of hash (eg. MD 5) of router IP address • Marking Aggregation – Router pushes marking into IP Identification field • Pi filters – Hi bandwidth flows (defined by marking) can be dropped by routers and victim • There is just so much space in IP identification field [Yarr. PS 03] 18
Packet Marking • Pi Marking Scheme – Each router marks n bits into IP Identification field • Marking Function – Last n bits of hash (eg. MD 5) of router IP address • Marking Aggregation – Router pushes marking into IP Identification field • Pi filters – Hi bandwidth flows (defined by marking) can be dropped by routers and victim • There is just so much space in IP identification field [Yarr. PS 03] 18
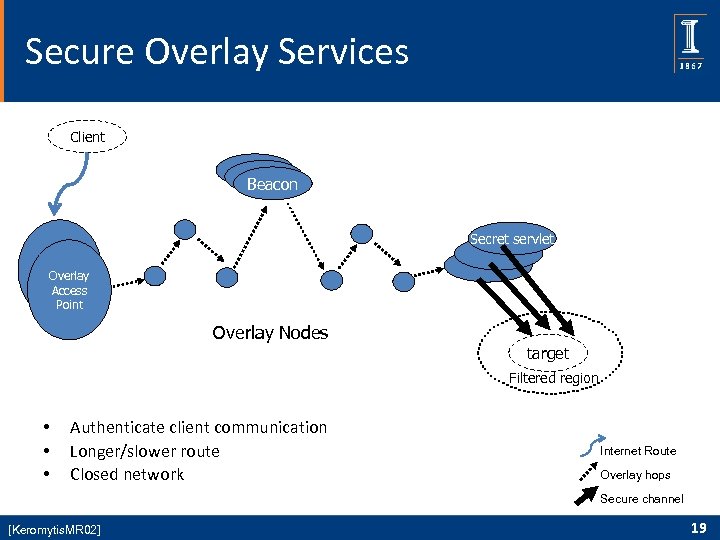 Secure Overlay Services Client Beacon Secret servlet Overlay Access Point Overlay Nodes target Filtered region • • • Authenticate client communication Longer/slower route Closed network Internet Route Overlay hops Secure channel [Keromytis. MR 02] 19
Secure Overlay Services Client Beacon Secret servlet Overlay Access Point Overlay Nodes target Filtered region • • • Authenticate client communication Longer/slower route Closed network Internet Route Overlay hops Secure channel [Keromytis. MR 02] 19
 DDo. S Defense Challenges • Distributed response required – Cooperation between many points • Economic and social factor – Source deploys filter to protect destination – Legislative measures • Lack of detailed attack information – Frequency of attack types, attack parameters, increasing attack scale – Backscatter, Internet Telescope • Lack of defense benchmark – How should the performance be measured? – NSF benchmarking effort • Difficulty of large scale testing – Test bed mimicking Internet (e. g. Planet. Lab and DETER) [Mirkovic. R 04] 20
DDo. S Defense Challenges • Distributed response required – Cooperation between many points • Economic and social factor – Source deploys filter to protect destination – Legislative measures • Lack of detailed attack information – Frequency of attack types, attack parameters, increasing attack scale – Backscatter, Internet Telescope • Lack of defense benchmark – How should the performance be measured? – NSF benchmarking effort • Difficulty of large scale testing – Test bed mimicking Internet (e. g. Planet. Lab and DETER) [Mirkovic. R 04] 20
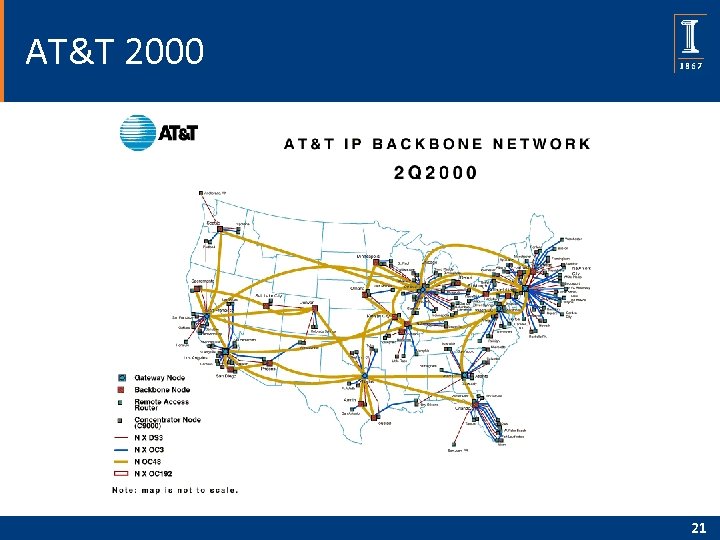 AT&T 2000 21
AT&T 2000 21
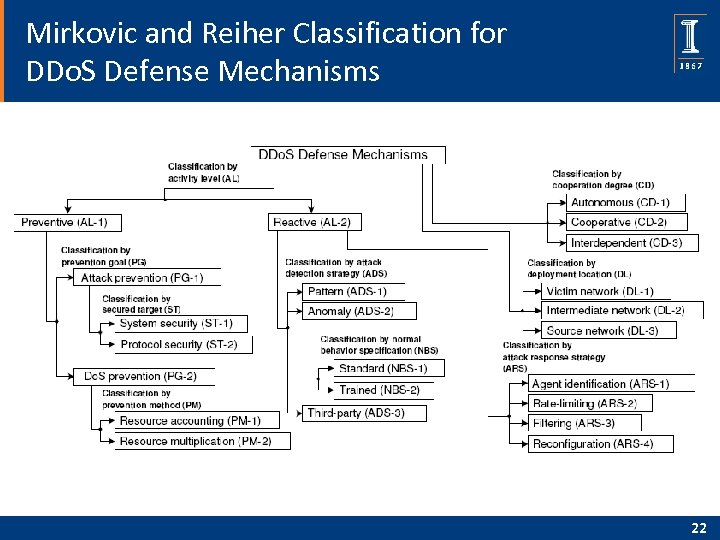 Mirkovic and Reiher Classification for DDo. S Defense Mechanisms 22
Mirkovic and Reiher Classification for DDo. S Defense Mechanisms 22
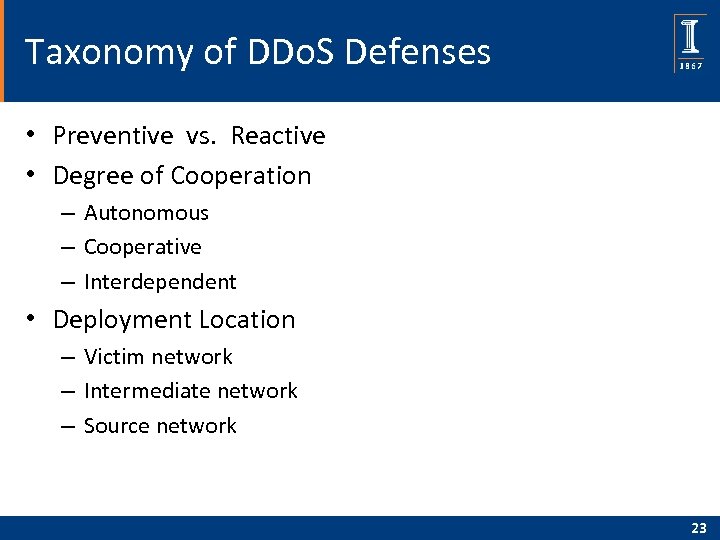 Taxonomy of DDo. S Defenses • Preventive vs. Reactive • Degree of Cooperation – Autonomous – Cooperative – Interdependent • Deployment Location – Victim network – Intermediate network – Source network 23
Taxonomy of DDo. S Defenses • Preventive vs. Reactive • Degree of Cooperation – Autonomous – Cooperative – Interdependent • Deployment Location – Victim network – Intermediate network – Source network 23
 Reactive Strategies Detection Response 1. Pattern – Signatures of known attacks stored 2. Anomaly – Model of normal system behavior a. Standard – Detect half-open TCP b. Trained – 1. 2. 3. 4. Agent Identification Rate-limiting Filtering Reconfiguration – Change the topology of victim or the network to add more resources or isolate attack machines. Traffic dynamics, expected system performance 3. Third Party – Traceback 24
Reactive Strategies Detection Response 1. Pattern – Signatures of known attacks stored 2. Anomaly – Model of normal system behavior a. Standard – Detect half-open TCP b. Trained – 1. 2. 3. 4. Agent Identification Rate-limiting Filtering Reconfiguration – Change the topology of victim or the network to add more resources or isolate attack machines. Traffic dynamics, expected system performance 3. Third Party – Traceback 24
 Degree of Cooperation • Autonomous – independent defense at the point of deployment • Cooperative – perform better in joint operation • Interdependent – cannot operate autonomously 25
Degree of Cooperation • Autonomous – independent defense at the point of deployment • Cooperative – perform better in joint operation • Interdependent – cannot operate autonomously 25
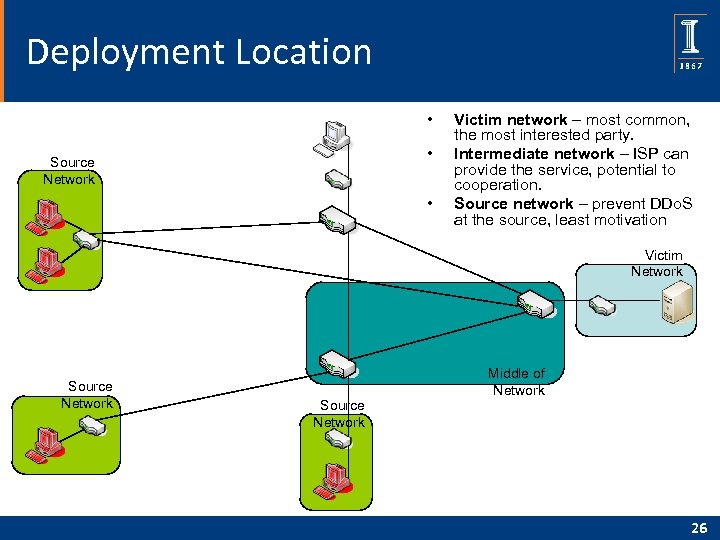 Deployment Location • • Source Network • Victim network – most common, the most interested party. Intermediate network – ISP can provide the service, potential to cooperation. Source network – prevent DDo. S at the source, least motivation Victim Network Source Network Middle of Network 26
Deployment Location • • Source Network • Victim network – most common, the most interested party. Intermediate network – ISP can provide the service, potential to cooperation. Source network – prevent DDo. S at the source, least motivation Victim Network Source Network Middle of Network 26
 Other factors • • Stateless vs. Stateful Internet architecture Router modification Application modification 27
Other factors • • Stateless vs. Stateful Internet architecture Router modification Application modification 27
![Reading Part 1 of 2 • [Sekar. DSMZ 06] LADS: Large-scale Automated DDo. S Reading Part 1 of 2 • [Sekar. DSMZ 06] LADS: Large-scale Automated DDo. S](https://present5.com/presentation/f53e1b63e7f671a629197ae4c1a1c534/image-28.jpg) Reading Part 1 of 2 • [Sekar. DSMZ 06] LADS: Large-scale Automated DDo. S detection System, Vyas Sekar, Nick Duffield, Oliver Spatscheck, Jacobus van der Merwe, and Hui Zhang. USENIX ATC 2006. • [Moore. SBVS 06] Inferring Internet Denial-of-service activity, David Moore, Colleen Shannon, Douglas J. Brown, Geoffrey M. Voelker, and Stefan Savage. ACM Transactions on Computer Systems, 24(2), 2006. • [Ferguson. S 00] Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing, P. Ferguson and D. Senie. IETF RFC 2827, 2000. • [Park. L 01] On the effectiveness of route-based packet filtering for distributed Do. S attack prevention in power-law internets, Kihong Park and Heejo Lee. SIGCOMM 2001. • [Yaar. PS 03 s] Pi: A Path Identification Mechanism to Defend against DDo. S Attacks, Abraham Yaar, Adrian Perrig, and Dawn Song, IEEE Security and Privacy, 2003. 28
Reading Part 1 of 2 • [Sekar. DSMZ 06] LADS: Large-scale Automated DDo. S detection System, Vyas Sekar, Nick Duffield, Oliver Spatscheck, Jacobus van der Merwe, and Hui Zhang. USENIX ATC 2006. • [Moore. SBVS 06] Inferring Internet Denial-of-service activity, David Moore, Colleen Shannon, Douglas J. Brown, Geoffrey M. Voelker, and Stefan Savage. ACM Transactions on Computer Systems, 24(2), 2006. • [Ferguson. S 00] Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing, P. Ferguson and D. Senie. IETF RFC 2827, 2000. • [Park. L 01] On the effectiveness of route-based packet filtering for distributed Do. S attack prevention in power-law internets, Kihong Park and Heejo Lee. SIGCOMM 2001. • [Yaar. PS 03 s] Pi: A Path Identification Mechanism to Defend against DDo. S Attacks, Abraham Yaar, Adrian Perrig, and Dawn Song, IEEE Security and Privacy, 2003. 28
![Reading Part 2 of 2 • [Mirkovic. DDR 04] Internet Denial of Service Attack Reading Part 2 of 2 • [Mirkovic. DDR 04] Internet Denial of Service Attack](https://present5.com/presentation/f53e1b63e7f671a629197ae4c1a1c534/image-29.jpg) Reading Part 2 of 2 • [Mirkovic. DDR 04] Internet Denial of Service Attack and Defense Mechanisms, Jelena Mirkovic, Sven Dietrich, David Dittrich, and Peter Reiher. Pearson 2004. • [Mirkovic. R 04] A Taxonomy of DDo. S Attacks and DDo. S Defense Mechanisms, Jelena Mirkovic and Peter Reiher. Computer Communications Review, Vol. 34, No. 2, April 2004. • [Gao. A 05] Tracing Cyber attacks from the practical perspective, Zhiqiang Gao and Nirwan Ansari. IEEE Communications Magazine, May 2005. • [Keromytis. MR 02] SOS: Secure Overlay Services (2002), Angelos D. Keromytis, Vishal Misra, Dan Rubenstein. ACM SIGCOMM 2002. 29
Reading Part 2 of 2 • [Mirkovic. DDR 04] Internet Denial of Service Attack and Defense Mechanisms, Jelena Mirkovic, Sven Dietrich, David Dittrich, and Peter Reiher. Pearson 2004. • [Mirkovic. R 04] A Taxonomy of DDo. S Attacks and DDo. S Defense Mechanisms, Jelena Mirkovic and Peter Reiher. Computer Communications Review, Vol. 34, No. 2, April 2004. • [Gao. A 05] Tracing Cyber attacks from the practical perspective, Zhiqiang Gao and Nirwan Ansari. IEEE Communications Magazine, May 2005. • [Keromytis. MR 02] SOS: Secure Overlay Services (2002), Angelos D. Keromytis, Vishal Misra, Dan Rubenstein. ACM SIGCOMM 2002. 29
 Discussion • What should be the qualities of a “good” detection technique? • What are the pros and cons of monitoring flows to see if they are “TCP-like” as a way to prevent Do. S? 30
Discussion • What should be the qualities of a “good” detection technique? • What are the pros and cons of monitoring flows to see if they are “TCP-like” as a way to prevent Do. S? 30


