de9bd33cf5b45014779a6c68a9a8e4e5.ppt
- Количество слайдов: 7
 56 th IETF San Francisco CA, March 16 -21, 2003 “EAP support in smartcards” Draft-urien-EAP-smartcard-01. txt My name is Pascal Urien, ENST Pascal. Urien@enst. fr Slide 1/7 03/17/03
56 th IETF San Francisco CA, March 16 -21, 2003 “EAP support in smartcards” Draft-urien-EAP-smartcard-01. txt My name is Pascal Urien, ENST Pascal. Urien@enst. fr Slide 1/7 03/17/03
 Draft Objectives 1/2 n Standardization initiative for EAP support in smartcard. q Agreement between major smartcard manufacturers. Under discussion in the wlan smartcard consortium (www. wlansmartcard. org) supported by nineteen founding members. q Definition of an “universal” ISO 7816 interface, e. g. supporting most of EAP authentication protocols. Height services are defined in this version. n Three logical interfaces. q Network interface. l Smartcard directly processes EAP messages (requests, notifications). l EAP profiles definition. A set of rules (if needed) for supporting a particular authentication protocol (messages maximum size, …). q Operating system interface. l Identity management. Multiple triplets (EAP-ID, EAP-Type, cryptographic keys) are stored in the smartcard; a triplet is required by each network. l User profile, typically an LDAP record stored in the smartcard (under discussion). q Management interface. Slide 2/7 03/17/03 l Identities & profiles download and update. Management could be done via dedicated EAP protocols (under discussion).
Draft Objectives 1/2 n Standardization initiative for EAP support in smartcard. q Agreement between major smartcard manufacturers. Under discussion in the wlan smartcard consortium (www. wlansmartcard. org) supported by nineteen founding members. q Definition of an “universal” ISO 7816 interface, e. g. supporting most of EAP authentication protocols. Height services are defined in this version. n Three logical interfaces. q Network interface. l Smartcard directly processes EAP messages (requests, notifications). l EAP profiles definition. A set of rules (if needed) for supporting a particular authentication protocol (messages maximum size, …). q Operating system interface. l Identity management. Multiple triplets (EAP-ID, EAP-Type, cryptographic keys) are stored in the smartcard; a triplet is required by each network. l User profile, typically an LDAP record stored in the smartcard (under discussion). q Management interface. Slide 2/7 03/17/03 l Identities & profiles download and update. Management could be done via dedicated EAP protocols (under discussion).
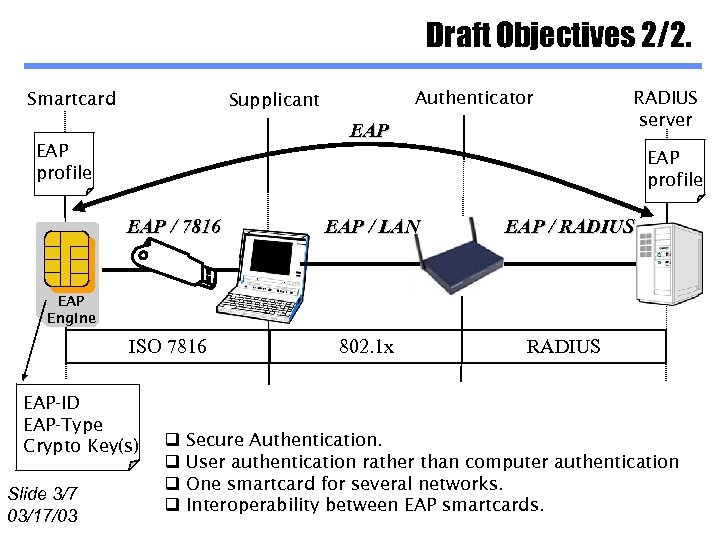 Draft Objectives 2/2. Smartcard Authenticator Supplicant EAP profile RADIUS server EAP profile EAP / 7816 EAP / LAN EAP / RADIUS EAP Engine ISO 7816 EAP-ID EAP-Type Crypto Key(s) Slide 3/7 03/17/03 q q 802. 1 x RADIUS Secure Authentication. User authentication rather than computer authentication One smartcard for several networks. Interoperability between EAP smartcards.
Draft Objectives 2/2. Smartcard Authenticator Supplicant EAP profile RADIUS server EAP profile EAP / 7816 EAP / LAN EAP / RADIUS EAP Engine ISO 7816 EAP-ID EAP-Type Crypto Key(s) Slide 3/7 03/17/03 q q 802. 1 x RADIUS Secure Authentication. User authentication rather than computer authentication One smartcard for several networks. Interoperability between EAP smartcards.
 Smartcard Facilities. n Tamper resistant device, highly tested (credit card, GSM card, PKI card…) n Low cost. n Multiple form factors (ISO 7816 – credit card format, SIM GSM 11. 11, USB…). n Sufficient cryptographic performances (RSA 2048 bits calculation in 500 ms). n Can be issued for millions users (half a billion – 600 millions of smartcard produced in 2001). n Can compute multiple EAP protocols. n Can be used in various networks (memory size around 128 kb, one Mb with the FLASH technology) Slide 4/7 03/17/03
Smartcard Facilities. n Tamper resistant device, highly tested (credit card, GSM card, PKI card…) n Low cost. n Multiple form factors (ISO 7816 – credit card format, SIM GSM 11. 11, USB…). n Sufficient cryptographic performances (RSA 2048 bits calculation in 500 ms). n Can be issued for millions users (half a billion – 600 millions of smartcard produced in 2001). n Can compute multiple EAP protocols. n Can be used in various networks (memory size around 128 kb, one Mb with the FLASH technology) Slide 4/7 03/17/03
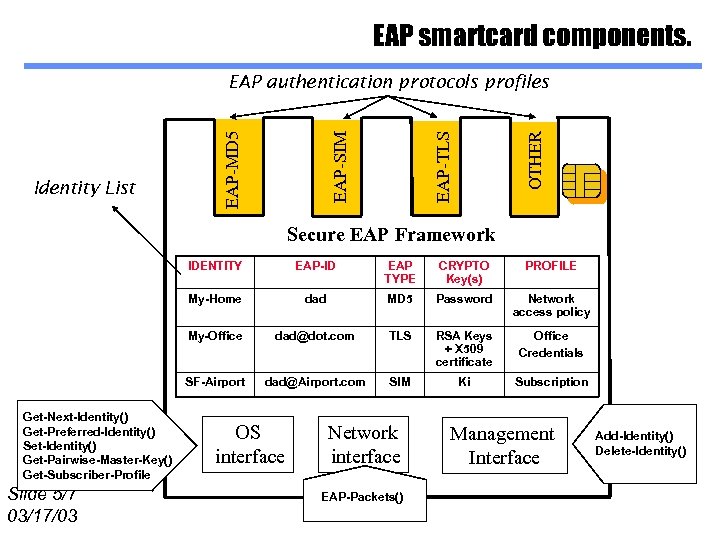 EAP smartcard components. OTHER EAP-TLS EAP-MD 5 Identity List EAP-SIM EAP authentication protocols profiles Secure EAP Framework IDENTITY CRYPTO Key(s) PROFILE dad MD 5 Password Network access policy My-Office dad@dot. com TLS RSA Keys + X 509 certificate Office Credentials SF-Airport Slide 5/7 03/17/03 EAP TYPE My-Home Get-Next-Identity() Get-Preferred-Identity() Set-Identity() Get-Pairwise-Master-Key() Get-Subscriber-Profile EAP-ID dad@Airport. com SIM Ki Subscription OS interface Network interface EAP-Packets() Management Interface Add-Identity() Delete-Identity()
EAP smartcard components. OTHER EAP-TLS EAP-MD 5 Identity List EAP-SIM EAP authentication protocols profiles Secure EAP Framework IDENTITY CRYPTO Key(s) PROFILE dad MD 5 Password Network access policy My-Office dad@dot. com TLS RSA Keys + X 509 certificate Office Credentials SF-Airport Slide 5/7 03/17/03 EAP TYPE My-Home Get-Next-Identity() Get-Preferred-Identity() Set-Identity() Get-Pairwise-Master-Key() Get-Subscriber-Profile EAP-ID dad@Airport. com SIM Ki Subscription OS interface Network interface EAP-Packets() Management Interface Add-Identity() Delete-Identity()
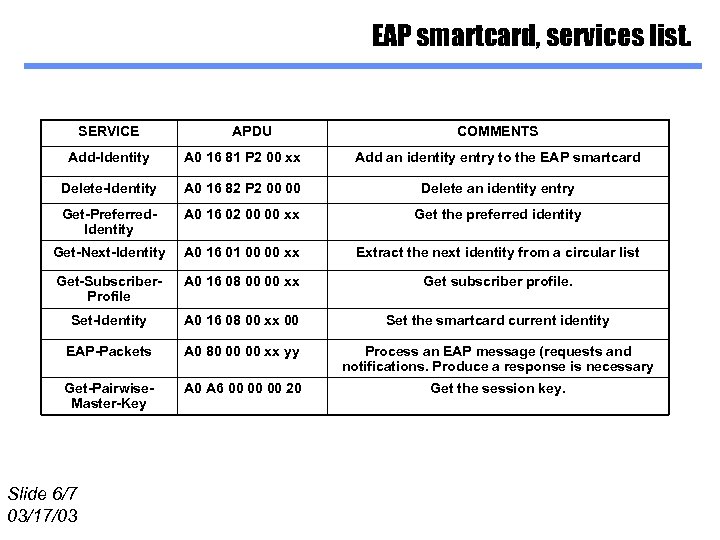 EAP smartcard, services list. SERVICE APDU COMMENTS Add-Identity A 0 16 81 P 2 00 xx Add an identity entry to the EAP smartcard Delete-Identity A 0 16 82 P 2 00 00 Delete an identity entry Get-Preferred. Identity A 0 16 02 00 00 xx Get the preferred identity Get-Next-Identity A 0 16 01 00 00 xx Extract the next identity from a circular list Get-Subscriber. Profile A 0 16 08 00 00 xx Get subscriber profile. Set-Identity A 0 16 08 00 xx 00 Set the smartcard current identity EAP-Packets A 0 80 00 00 xx yy Process an EAP message (requests and notifications. Produce a response is necessary Get-Pairwise. Master-Key A 0 A 6 00 00 00 20 Get the session key. Slide 6/7 03/17/03
EAP smartcard, services list. SERVICE APDU COMMENTS Add-Identity A 0 16 81 P 2 00 xx Add an identity entry to the EAP smartcard Delete-Identity A 0 16 82 P 2 00 00 Delete an identity entry Get-Preferred. Identity A 0 16 02 00 00 xx Get the preferred identity Get-Next-Identity A 0 16 01 00 00 xx Extract the next identity from a circular list Get-Subscriber. Profile A 0 16 08 00 00 xx Get subscriber profile. Set-Identity A 0 16 08 00 xx 00 Set the smartcard current identity EAP-Packets A 0 80 00 00 xx yy Process an EAP message (requests and notifications. Produce a response is necessary Get-Pairwise. Master-Key A 0 A 6 00 00 00 20 Get the session key. Slide 6/7 03/17/03
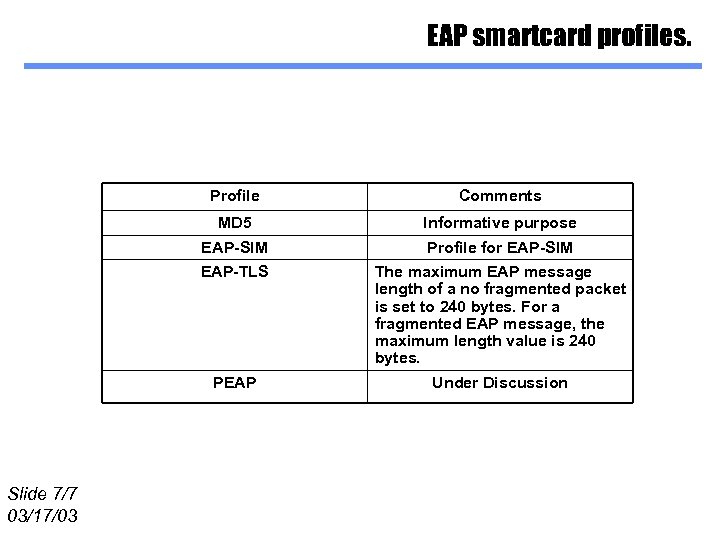 EAP smartcard profiles. Profile MD 5 Informative purpose EAP-SIM Profile for EAP-SIM EAP-TLS The maximum EAP message length of a no fragmented packet is set to 240 bytes. For a fragmented EAP message, the maximum length value is 240 bytes. PEAP Slide 7/7 03/17/03 Comments Under Discussion
EAP smartcard profiles. Profile MD 5 Informative purpose EAP-SIM Profile for EAP-SIM EAP-TLS The maximum EAP message length of a no fragmented packet is set to 240 bytes. For a fragmented EAP message, the maximum length value is 240 bytes. PEAP Slide 7/7 03/17/03 Comments Under Discussion


