e703addae8978e24508cc934917f7b55.ppt
- Количество слайдов: 100
 463. 6 Digital Rights Management Computer Security II CS 463/ECE 424 University of Illinois
463. 6 Digital Rights Management Computer Security II CS 463/ECE 424 University of Illinois
 Overview • Discussion in three parts – Software Reverse Engineering (SRE) – Digital Rights Management (DRM) Enforcement – Rights Expression Languages (RELs) 2
Overview • Discussion in three parts – Software Reverse Engineering (SRE) – Digital Rights Management (DRM) Enforcement – Rights Expression Languages (RELs) 2
 463. 6. 1 Software Reverse Engineering Based on slides by Mark Stamp.
463. 6. 1 Software Reverse Engineering Based on slides by Mark Stamp.
 Reverse Engineering Defined • Reverse engineering (RE) is the process of discovering the technological principles of a device, object or system through analysis of its structure, function and operation. – Used in maintenance – Used to make a new device or program that does the same thing without copying anything from the original – Used to alter the original for a specific purpose 4
Reverse Engineering Defined • Reverse engineering (RE) is the process of discovering the technological principles of a device, object or system through analysis of its structure, function and operation. – Used in maintenance – Used to make a new device or program that does the same thing without copying anything from the original – Used to alter the original for a specific purpose 4
 Software Reverse Engineering (SRE) • Software Reverse Engineering – Also known as Reverse Code Engineering (RCE) – Or simply “reversing” • Can be used for good. . . – Understand malware – Understand legacy code • …or not-so-good – Remove usage restrictions from software – Find and exploit flaws in software – Cheat at games, etc. 5
Software Reverse Engineering (SRE) • Software Reverse Engineering – Also known as Reverse Code Engineering (RCE) – Or simply “reversing” • Can be used for good. . . – Understand malware – Understand legacy code • …or not-so-good – Remove usage restrictions from software – Find and exploit flaws in software – Cheat at games, etc. 5
 Assumptions • We assume that – Reverse engineer is an attacker – Attacker only has exe (no source code) • Attacker might want to – Understand the software – Modify the software • Case studies below based on Windows 6
Assumptions • We assume that – Reverse engineer is an attacker – Attacker only has exe (no source code) • Attacker might want to – Understand the software – Modify the software • Case studies below based on Windows 6
 Types of Tools Used • Disassembler – Converts exe to assembly as best it can – Cannot always disassemble correctly – In general, it is not possible to assemble disassembly into working exe • Debugger – Must step thru code to completely understand it – Labor intensive lack of automated tools • Hex Editor – To patch (make changes to) exe file 7
Types of Tools Used • Disassembler – Converts exe to assembly as best it can – Cannot always disassemble correctly – In general, it is not possible to assemble disassembly into working exe • Debugger – Must step thru code to completely understand it – Labor intensive lack of automated tools • Hex Editor – To patch (make changes to) exe file 7
 Examples of Tools • IDA Pro is the top-rated disassembler – Cost is a few hundred dollars – Converts binary to assembly (as best it can) • Soft. ICE is “alpha and omega” of debuggers – Cost is in the $1000’s – Kernel mode debugger – Can debug anything, even the OS • Olly. Dbg is a high quality shareware debugger – Includes a good disassembler • Hex editor to view/modify bits of exe – Ultra. Edit is good freeware – HIEW useful for patching exe • Regmon, Filemon freeware 8
Examples of Tools • IDA Pro is the top-rated disassembler – Cost is a few hundred dollars – Converts binary to assembly (as best it can) • Soft. ICE is “alpha and omega” of debuggers – Cost is in the $1000’s – Kernel mode debugger – Can debug anything, even the OS • Olly. Dbg is a high quality shareware debugger – Includes a good disassembler • Hex editor to view/modify bits of exe – Ultra. Edit is good freeware – HIEW useful for patching exe • Regmon, Filemon freeware 8
 Debugger • Disassembler gives static results – Good overview of program logic – But need to “mentally execute” program – Difficult to jump to specific place in the code • Debugger is dynamic – Can set break points – Can treat complex code as “black box” – Not all code disassembles correctly • Disassembler and debugger both required for any serious SRE task 9
Debugger • Disassembler gives static results – Good overview of program logic – But need to “mentally execute” program – Difficult to jump to specific place in the code • Debugger is dynamic – Can set break points – Can treat complex code as “black box” – Not all code disassembles correctly • Disassembler and debugger both required for any serious SRE task 9
 SRE Necessary Skills • Working knowledge of target assembly code • Experience with the tools – IDA Pro sophisticated and complex – Soft. ICE large two-volume users manual • Knowledge of applicable executable formats (e. g. Windows Portable Executable (PE) file format) • Boundless patience and optimism • SRE is tedious and labor-intensive process! 10
SRE Necessary Skills • Working knowledge of target assembly code • Experience with the tools – IDA Pro sophisticated and complex – Soft. ICE large two-volume users manual • Knowledge of applicable executable formats (e. g. Windows Portable Executable (PE) file format) • Boundless patience and optimism • SRE is tedious and labor-intensive process! 10
 SRE Example • Consider simple example • This example only requires disassembler (IDA Pro) and hex editor – Trudy disassembles to understand code – Trudy also wants to patch the code • For most real-world code, also need a debugger (Soft. ICE or Olly. Dbg) 11
SRE Example • Consider simple example • This example only requires disassembler (IDA Pro) and hex editor – Trudy disassembles to understand code – Trudy also wants to patch the code • For most real-world code, also need a debugger (Soft. ICE or Olly. Dbg) 11
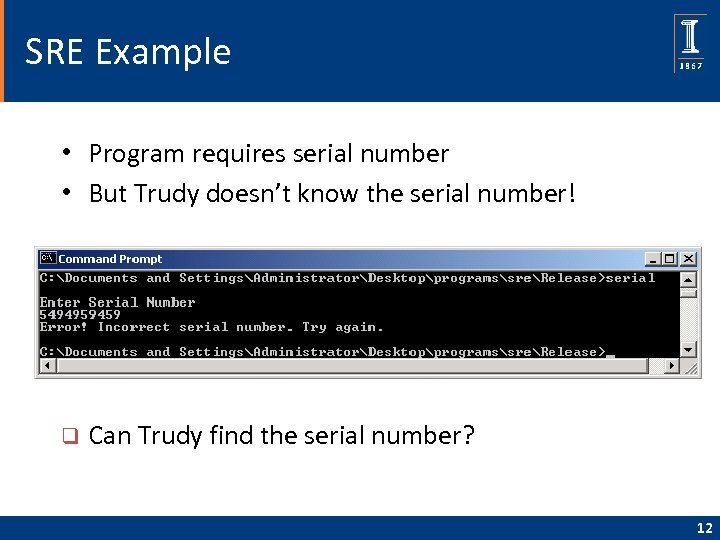 SRE Example • Program requires serial number • But Trudy doesn’t know the serial number! q Can Trudy find the serial number? 12
SRE Example • Program requires serial number • But Trudy doesn’t know the serial number! q Can Trudy find the serial number? 12
 SRE Example • IDA Pro disassembly q Looks like serial number is S 123 N 456 13
SRE Example • IDA Pro disassembly q Looks like serial number is S 123 N 456 13
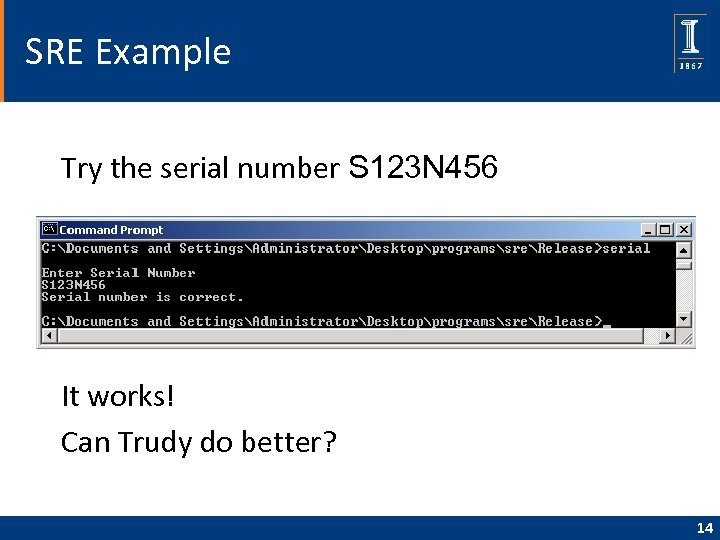 SRE Example Try the serial number S 123 N 456 It works! Can Trudy do better? 14
SRE Example Try the serial number S 123 N 456 It works! Can Trudy do better? 14
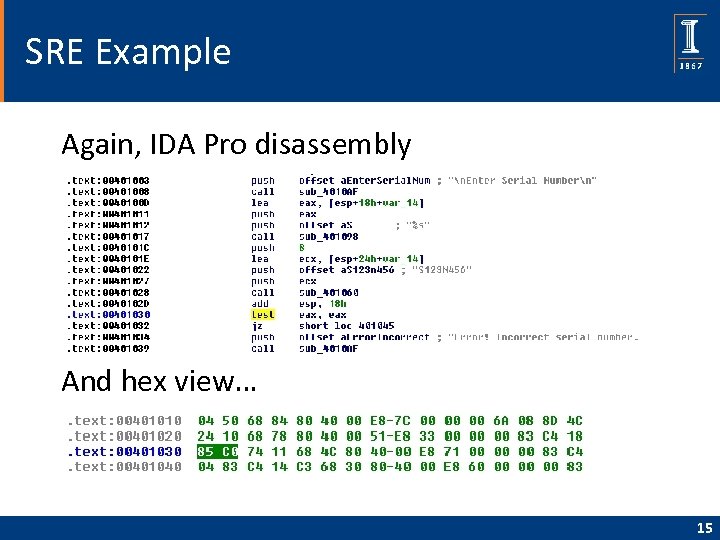 SRE Example Again, IDA Pro disassembly And hex view… 15
SRE Example Again, IDA Pro disassembly And hex view… 15
 SRE Example q test eax, eax gives AND of eax with itself o Result is 0 only if eax is 0 o If test returns 0, then jz is true Trudy wants jz to always be true! q Can Trudy patch exe so that jz always true? q 16
SRE Example q test eax, eax gives AND of eax with itself o Result is 0 only if eax is 0 o If test returns 0, then jz is true Trudy wants jz to always be true! q Can Trudy patch exe so that jz always true? q 16
 SRE Example q Can Trudy patch exe so that jz always true? xor Assembly test eax, eax xor eax, eax jz always true!!! Hex 85 C 0 … 33 C 0 … 17
SRE Example q Can Trudy patch exe so that jz always true? xor Assembly test eax, eax xor eax, eax jz always true!!! Hex 85 C 0 … 33 C 0 … 17
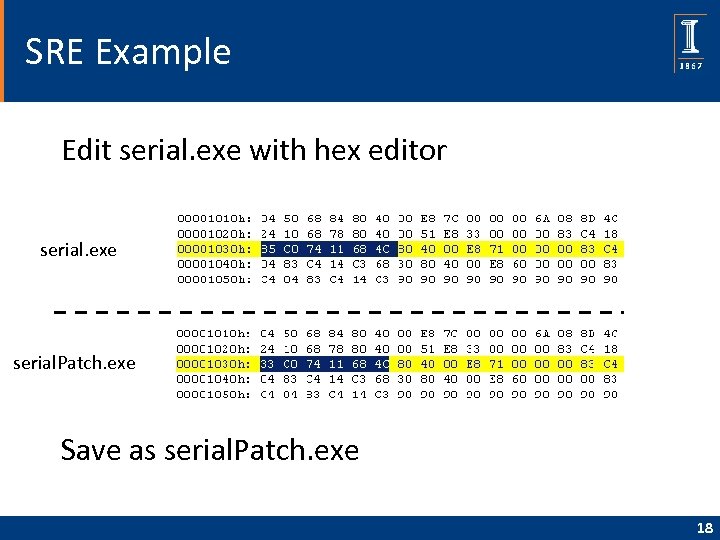 SRE Example Edit serial. exe with hex editor serial. exe serial. Patch. exe Save as serial. Patch. exe 18
SRE Example Edit serial. exe with hex editor serial. exe serial. Patch. exe Save as serial. Patch. exe 18
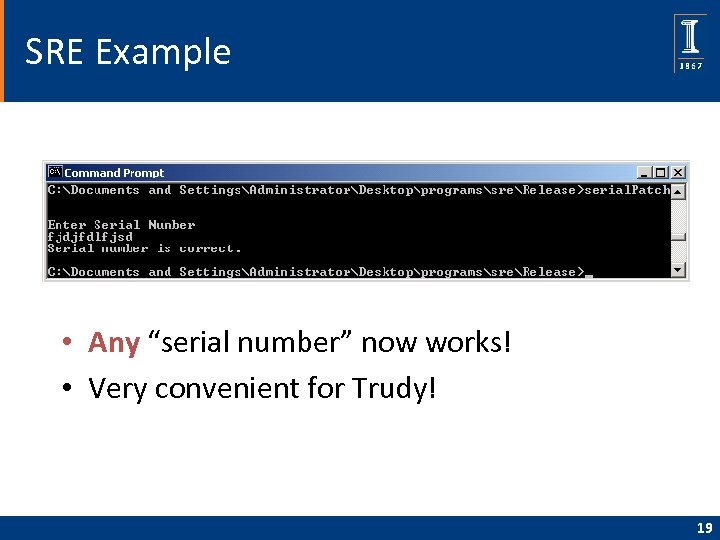 SRE Example • Any “serial number” now works! • Very convenient for Trudy! 19
SRE Example • Any “serial number” now works! • Very convenient for Trudy! 19
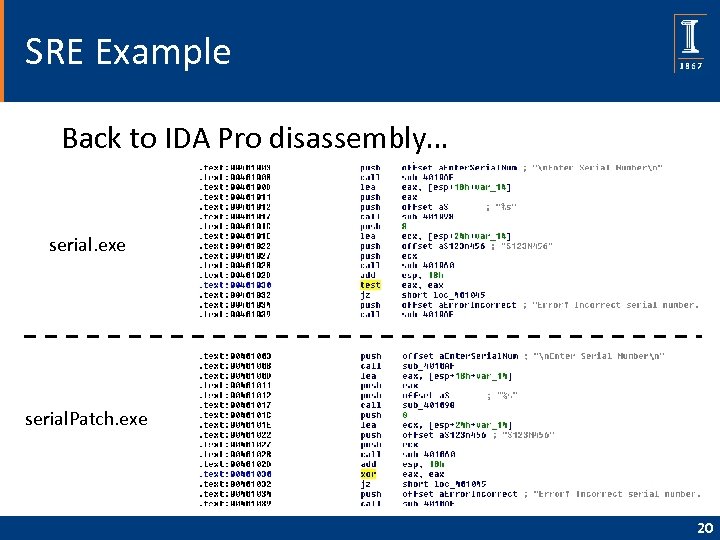 SRE Example Back to IDA Pro disassembly… serial. exe serial. Patch. exe 20
SRE Example Back to IDA Pro disassembly… serial. exe serial. Patch. exe 20
 Mitigation • It is impossible to completely prevent SRE on an open system • But it is possible to make such attacks more difficult • Anti-disassembly techniques can confuse static view of code • Anti-debugging techniques can confuse dynamic view of code • Tamper-resistance can be implemented by allowing code to check itself to detect tampering • Code obfuscation can make code more difficult to understand 21
Mitigation • It is impossible to completely prevent SRE on an open system • But it is possible to make such attacks more difficult • Anti-disassembly techniques can confuse static view of code • Anti-debugging techniques can confuse dynamic view of code • Tamper-resistance can be implemented by allowing code to check itself to detect tampering • Code obfuscation can make code more difficult to understand 21
 Anti-Disassembly • Anti-disassembly methods include – – Encrypted object code False disassembly Self-modifying code Many others • Encryption prevents disassembly – But still need code to decrypt the code! – Same problem as with polymorphic viruses 22
Anti-Disassembly • Anti-disassembly methods include – – Encrypted object code False disassembly Self-modifying code Many others • Encryption prevents disassembly – But still need code to decrypt the code! – Same problem as with polymorphic viruses 22
 Anti-Disassembly Example Suppose actual code instructions are inst 1 jmp junk inst 3 inst 4 … What the disassembler sees inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … This is example of “false disassembly” Clever attacker will figure it out! 23
Anti-Disassembly Example Suppose actual code instructions are inst 1 jmp junk inst 3 inst 4 … What the disassembler sees inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … This is example of “false disassembly” Clever attacker will figure it out! 23
 Anti-Debugging • Monitor for – Use of debug registers – Inserted breakpoints • Debuggers don’t handle threads well – Interacting threads may confuse debugger • Many other debugger-unfriendly tricks • Undetectable debugger possible in principle – Hardware-based debugging (Hard. ICE) is possible 24
Anti-Debugging • Monitor for – Use of debug registers – Inserted breakpoints • Debuggers don’t handle threads well – Interacting threads may confuse debugger • Many other debugger-unfriendly tricks • Undetectable debugger possible in principle – Hardware-based debugging (Hard. ICE) is possible 24
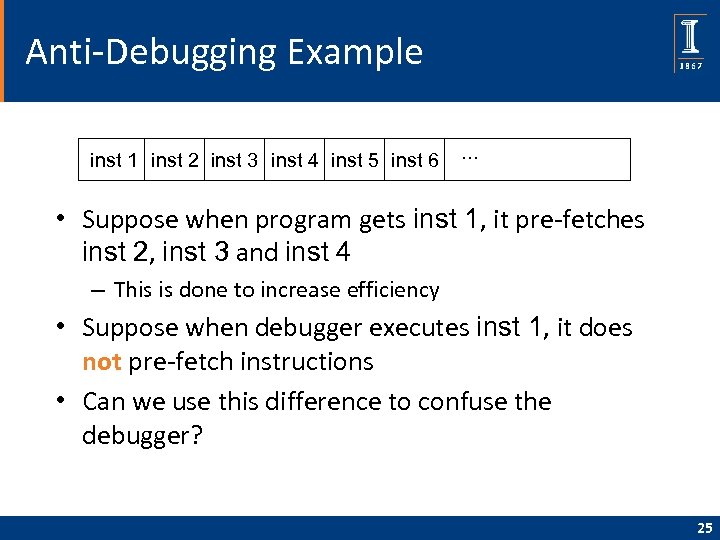 Anti-Debugging Example inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … • Suppose when program gets inst 1, it pre-fetches inst 2, inst 3 and inst 4 – This is done to increase efficiency • Suppose when debugger executes inst 1, it does not pre-fetch instructions • Can we use this difference to confuse the debugger? 25
Anti-Debugging Example inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … • Suppose when program gets inst 1, it pre-fetches inst 2, inst 3 and inst 4 – This is done to increase efficiency • Suppose when debugger executes inst 1, it does not pre-fetch instructions • Can we use this difference to confuse the debugger? 25
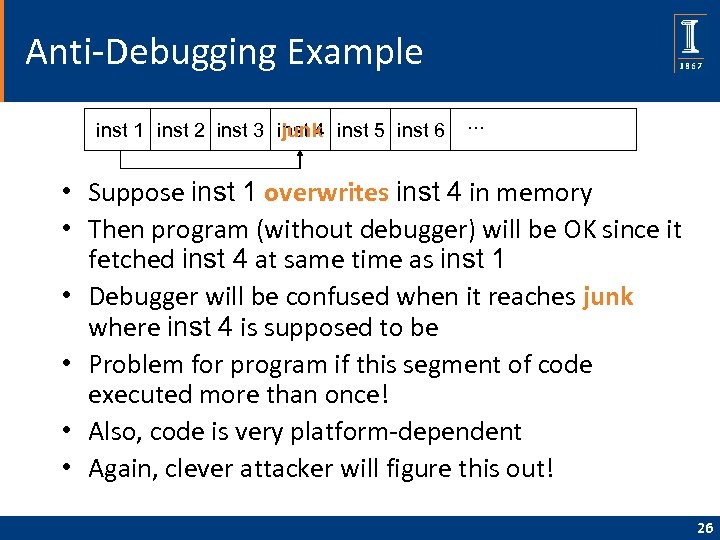 Anti-Debugging Example junk inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … • Suppose inst 1 overwrites inst 4 in memory • Then program (without debugger) will be OK since it fetched inst 4 at same time as inst 1 • Debugger will be confused when it reaches junk where inst 4 is supposed to be • Problem for program if this segment of code executed more than once! • Also, code is very platform-dependent • Again, clever attacker will figure this out! 26
Anti-Debugging Example junk inst 1 inst 2 inst 3 inst 4 inst 5 inst 6 … • Suppose inst 1 overwrites inst 4 in memory • Then program (without debugger) will be OK since it fetched inst 4 at same time as inst 1 • Debugger will be confused when it reaches junk where inst 4 is supposed to be • Problem for program if this segment of code executed more than once! • Also, code is very platform-dependent • Again, clever attacker will figure this out! 26
 Tamper Resistance Goal is to make patching more difficult Code can hash parts of itself If tampering occurs, hash check fails Can get good coverage of code with small performance penalty • But don’t want all checks to look similar • • – Or else easy for attacker to remove checks • This approach sometimes called “guards” 27
Tamper Resistance Goal is to make patching more difficult Code can hash parts of itself If tampering occurs, hash check fails Can get good coverage of code with small performance penalty • But don’t want all checks to look similar • • – Or else easy for attacker to remove checks • This approach sometimes called “guards” 27
 Code Obfuscation • • Goal is to make code hard to understand Opposite of good software engineering! Simple example: spaghetti code Much research into more robust obfuscation – Example: opaque predicate int x, y : if((x y) > (x x 2 x y+y y)){…} – The if() conditional is always false • Attacker will waste time analyzing dead code 28
Code Obfuscation • • Goal is to make code hard to understand Opposite of good software engineering! Simple example: spaghetti code Much research into more robust obfuscation – Example: opaque predicate int x, y : if((x y) > (x x 2 x y+y y)){…} – The if() conditional is always false • Attacker will waste time analyzing dead code 28
 Code Obfuscation • Code obfuscation sometimes promoted as a powerful security technique • Diffie and Hellman’s original ideas for public key crypto were based on similar ideas! • Theoreticians have framed and proved impossibility results for obfuscation • Obfuscation might still have practical uses! – Even if it can never be as strong as crypto 29
Code Obfuscation • Code obfuscation sometimes promoted as a powerful security technique • Diffie and Hellman’s original ideas for public key crypto were based on similar ideas! • Theoreticians have framed and proved impossibility results for obfuscation • Obfuscation might still have practical uses! – Even if it can never be as strong as crypto 29
 Authentication Example • Software used to determine authentication • Ultimately, authentication is 1 -bit decision – Regardless of method used (pwd, biometric, …) • Somewhere in authentication software, a single bit determines success/failure • If attacker can find this bit, he can force authentication to always succeed • Obfuscation makes it more difficult for attacker to find this all-important bit 30
Authentication Example • Software used to determine authentication • Ultimately, authentication is 1 -bit decision – Regardless of method used (pwd, biometric, …) • Somewhere in authentication software, a single bit determines success/failure • If attacker can find this bit, he can force authentication to always succeed • Obfuscation makes it more difficult for attacker to find this all-important bit 30
 Obfuscation • Obfuscation forces attacker to analyze larger amounts of code • Method could be combined with – Anti-disassembly techniques – Anti-debugging techniques – Code tamper-checking • All of these increase work (and pain) for attacker • But a persistent attacker will ultimately win 31
Obfuscation • Obfuscation forces attacker to analyze larger amounts of code • Method could be combined with – Anti-disassembly techniques – Anti-debugging techniques – Code tamper-checking • All of these increase work (and pain) for attacker • But a persistent attacker will ultimately win 31
 Software Cloning • Suppose we write a piece of software • We then distribute an identical copy (or clone) to each customer • If an attack is found on one copy, the same attack works on all copies • This approach has no resistance to “break once, break everywhere” (BOBE) • This is the usual situation in software development 32
Software Cloning • Suppose we write a piece of software • We then distribute an identical copy (or clone) to each customer • If an attack is found on one copy, the same attack works on all copies • This approach has no resistance to “break once, break everywhere” (BOBE) • This is the usual situation in software development 32
 Metamorphic Software • • Metamorphism is used in malware Can metamorphism also be used for good? Suppose we write a piece of software Each copy we distribute is different – This is an example of metamorphic software • Two levels of metamorphism are possible – All instances are functionally distinct (only possible in certain applications) – All instances are functionally identical but differ internally (always possible) • We consider the latter case 33
Metamorphic Software • • Metamorphism is used in malware Can metamorphism also be used for good? Suppose we write a piece of software Each copy we distribute is different – This is an example of metamorphic software • Two levels of metamorphism are possible – All instances are functionally distinct (only possible in certain applications) – All instances are functionally identical but differ internally (always possible) • We consider the latter case 33
 Metamorphic Software • If we distribute N copies of cloned software – One successful attack breaks all N • If we distribute N metamorphic copies, where each of N instances is functionally identical, but they differ internally… – An attack on one instance does not necessarily work against other instances – In the best case, N times as much work is required to break all N instances 34
Metamorphic Software • If we distribute N copies of cloned software – One successful attack breaks all N • If we distribute N metamorphic copies, where each of N instances is functionally identical, but they differ internally… – An attack on one instance does not necessarily work against other instances – In the best case, N times as much work is required to break all N instances 34
 Metamorphic Software • • We cannot prevent SRE attacks The best we can hope for is BOBE resistance Metamorphism can improve BOBE resistance Consider the analogy to genetic diversity – If all plants in a field are genetically identical, one disease can kill all of the plants – If the plants in a field are genetically diverse, one disease can only kill some of the plants 35
Metamorphic Software • • We cannot prevent SRE attacks The best we can hope for is BOBE resistance Metamorphism can improve BOBE resistance Consider the analogy to genetic diversity – If all plants in a field are genetically identical, one disease can kill all of the plants – If the plants in a field are genetically diverse, one disease can only kill some of the plants 35
 Cloning vs Metamorphism • Suppose our software has a buffer overflow • Cloned software – Same buffer overflow attack will work against all cloned copies of the software • Metamorphic software – Unique instances all are functionally the same, but they differ in internal structure – Buffer overflow likely exists in all instances – But a specific buffer overflow attack will only work against some instances – Buffer overflow attacks are delicate! 36
Cloning vs Metamorphism • Suppose our software has a buffer overflow • Cloned software – Same buffer overflow attack will work against all cloned copies of the software • Metamorphic software – Unique instances all are functionally the same, but they differ in internal structure – Buffer overflow likely exists in all instances – But a specific buffer overflow attack will only work against some instances – Buffer overflow attacks are delicate! 36
 Metamorphic Software • Metamorphic software is intriguing concept • But raises concerns regarding – Software development – Software upgrades, etc. • Metamorphism does not prevent SRE, but could make it infeasible on a large scale • Metamorphism might be a practical tool for increasing BOBE resistance • Metamorphism currently used in malware • But metamorphism not just for evil! 37
Metamorphic Software • Metamorphic software is intriguing concept • But raises concerns regarding – Software development – Software upgrades, etc. • Metamorphism does not prevent SRE, but could make it infeasible on a large scale • Metamorphism might be a practical tool for increasing BOBE resistance • Metamorphism currently used in malware • But metamorphism not just for evil! 37
![Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. •](https://present5.com/presentation/e703addae8978e24508cc934917f7b55/image-38.jpg) Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • [Wo. W EULA] World of Warcraft End User License Agreement. Blizzard 2009. http: //www. worldofwarcraft. com/legal/eula. html • [Hoqland. M 08] Exploiting Online Games: Cheating Massively Distributed Systems, Greg Mc. Graw and Gary Mc. Graw. Addison Wesley Software Security Series 2008. 38
Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • [Wo. W EULA] World of Warcraft End User License Agreement. Blizzard 2009. http: //www. worldofwarcraft. com/legal/eula. html • [Hoqland. M 08] Exploiting Online Games: Cheating Massively Distributed Systems, Greg Mc. Graw and Gary Mc. Graw. Addison Wesley Software Security Series 2008. 38
 Discussion • What are the limits for preventing a user of your software from studying it and using or interacting with it in a way you did not intend? – Illustration with the World of Warcraft (Wo. W) End User License Agreement (EULA). 39
Discussion • What are the limits for preventing a user of your software from studying it and using or interacting with it in a way you did not intend? – Illustration with the World of Warcraft (Wo. W) End User License Agreement (EULA). 39
 No Reverse Engineering • You agree that you will not, under any circumstances: – in whole or in part, copy, photocopy, reproduce, translate, reverse engineer, derive source code from, modify, disassemble, decompile, or create derivative works based on the Game … 40
No Reverse Engineering • You agree that you will not, under any circumstances: – in whole or in part, copy, photocopy, reproduce, translate, reverse engineer, derive source code from, modify, disassemble, decompile, or create derivative works based on the Game … 40
 No Monitoring (By You) • You agree that you will not, under any circumstances: – use any unauthorized third-party software that intercepts, "mines", or otherwise collects information from or through the Game or the Service, including without limitation any software that reads areas of RAM used by the Game to store information about a character or the game environment; provided, however, that Blizzard may, at its sole and absolute discretion, allow the use of certain third party user interfaces; … 41
No Monitoring (By You) • You agree that you will not, under any circumstances: – use any unauthorized third-party software that intercepts, "mines", or otherwise collects information from or through the Game or the Service, including without limitation any software that reads areas of RAM used by the Game to store information about a character or the game environment; provided, however, that Blizzard may, at its sole and absolute discretion, allow the use of certain third party user interfaces; … 41
 Locked Software • The media on which the Game Client is distributed may contain additional software and/or content for which you do not have a license (the "Locked Software"), and you agree that Blizzard may install the Locked Software onto your hard drive during the Game Client installation process. You also agree that you will not access, use, distribute, copy, display, reverse engineer, derive source code from, modify, disassemble, decompile any Locked Software, or create any derivative works based on the Locked Software 42
Locked Software • The media on which the Game Client is distributed may contain additional software and/or content for which you do not have a license (the "Locked Software"), and you agree that Blizzard may install the Locked Software onto your hard drive during the Game Client installation process. You also agree that you will not access, use, distribute, copy, display, reverse engineer, derive source code from, modify, disassemble, decompile any Locked Software, or create any derivative works based on the Locked Software 42
 Monitoring (By Them) • WHEN RUNNING, THE GAME MAY MONITOR YOUR COMPUTER'S RANDOM ACCESS MEMORY (RAM) FOR UNAUTHORIZED THIRD PARTY PROGRAMS RUNNING CONCURRENTLY WITH THE GAME. AN "UNAUTHORIZED THIRD PARTY PROGRAM" AS USED HEREIN SHALL BE DEFINED AS ANY THIRD PARTY SOFTWARE PROHIBITED BY SECTION 2. IN THE EVENT THAT THE GAME DETECTS AN UNAUTHORIZED THIRD PARTY PROGRAM, THE GAME MAY (a) COMMUNICATE INFORMATION BACK TO BLIZZARD, INCLUDING WITHOUT LIMITATION YOUR ACCOUNT NAME, DETAILS ABOUT THE UNAUTHORIZED THIRD PARTY PROGRAM DETECTED, AND THE TIME AND DATE; AND/OR (b) EXERCISE ANY OR ALL OF ITS RIGHTS UNDER THIS AGREEMENT, WITH OR WITHOUT PRIOR NOTICE TO THE USER. 43
Monitoring (By Them) • WHEN RUNNING, THE GAME MAY MONITOR YOUR COMPUTER'S RANDOM ACCESS MEMORY (RAM) FOR UNAUTHORIZED THIRD PARTY PROGRAMS RUNNING CONCURRENTLY WITH THE GAME. AN "UNAUTHORIZED THIRD PARTY PROGRAM" AS USED HEREIN SHALL BE DEFINED AS ANY THIRD PARTY SOFTWARE PROHIBITED BY SECTION 2. IN THE EVENT THAT THE GAME DETECTS AN UNAUTHORIZED THIRD PARTY PROGRAM, THE GAME MAY (a) COMMUNICATE INFORMATION BACK TO BLIZZARD, INCLUDING WITHOUT LIMITATION YOUR ACCOUNT NAME, DETAILS ABOUT THE UNAUTHORIZED THIRD PARTY PROGRAM DETECTED, AND THE TIME AND DATE; AND/OR (b) EXERCISE ANY OR ALL OF ITS RIGHTS UNDER THIS AGREEMENT, WITH OR WITHOUT PRIOR NOTICE TO THE USER. 43
 463. 6. 2 Digital Rights Management Enforcement Based on slides by Mark Stamp.
463. 6. 2 Digital Rights Management Enforcement Based on slides by Mark Stamp.
 What is DRM? • “Remote control” problem – Distribute digital content – Retain some control on its use, after delivery • Digital book example – – Digital book sold online could have huge market But might only sell 1 copy! Trivial to make perfect digital copies A fundamental change from pre-digital era • Similar comments for digital music, video, etc. 45
What is DRM? • “Remote control” problem – Distribute digital content – Retain some control on its use, after delivery • Digital book example – – Digital book sold online could have huge market But might only sell 1 copy! Trivial to make perfect digital copies A fundamental change from pre-digital era • Similar comments for digital music, video, etc. 45
 Persistent Protection • “Persistent protection” is the fundamental problem in DRM – How to enforce restrictions on use of content after delivery? • Examples of such restrictions – – No copying Limited number of reads/plays Time limits No forwarding, etc. 46
Persistent Protection • “Persistent protection” is the fundamental problem in DRM – How to enforce restrictions on use of content after delivery? • Examples of such restrictions – – No copying Limited number of reads/plays Time limits No forwarding, etc. 46
 What Can be Done? • The honor system? – Example: Stephen King’s, The Plant • Give up? – Internet sales? Regulatory compliance? etc. • Lame software-based DRM? – The standard DRM system today • Better software-based DRM? – Media. Snap case study. • Tamper-resistant hardware? – Later discussion: remote attestation. 47
What Can be Done? • The honor system? – Example: Stephen King’s, The Plant • Give up? – Internet sales? Regulatory compliance? etc. • Lame software-based DRM? – The standard DRM system today • Better software-based DRM? – Media. Snap case study. • Tamper-resistant hardware? – Later discussion: remote attestation. 47
 Is Crypto the Answer? • Attacker’s goal is to recover the key • In standard crypto scenario, attacker has – Ciphertext, some plaintext, side-channel info, etc. • In DRM scenario, attacker has – Everything in the box (at least) • Crypto was not designed for this problem! 48
Is Crypto the Answer? • Attacker’s goal is to recover the key • In standard crypto scenario, attacker has – Ciphertext, some plaintext, side-channel info, etc. • In DRM scenario, attacker has – Everything in the box (at least) • Crypto was not designed for this problem! 48
 Is Crypto the Answer? • But crypto is necessary – To securely deliver the bits – To prevent trivial attacks • Then attacker will not try to directly attack crypto • Attacker will try to find keys in software – DRM is “hide and seek” with keys in software! 49
Is Crypto the Answer? • But crypto is necessary – To securely deliver the bits – To prevent trivial attacks • Then attacker will not try to directly attack crypto • Attacker will try to find keys in software – DRM is “hide and seek” with keys in software! 49
 DRM Limitations • The analog hole – When content is rendered, it can be captured in analog form – DRM cannot prevent such an attack • Human nature matters – Absolute DRM security is impossible – Want something that “works” in practice – What works depends on context • DRM is not strictly a technical problem! 50
DRM Limitations • The analog hole – When content is rendered, it can be captured in analog form – DRM cannot prevent such an attack • Human nature matters – Absolute DRM security is impossible – Want something that “works” in practice – What works depends on context • DRM is not strictly a technical problem! 50
 Software-based DRM • Strong software-based DRM is impossible – We can’t really hide a secret in software – We cannot prevent SRE – User with full admin privilege can eventually break any anti. SRE protection 51
Software-based DRM • Strong software-based DRM is impossible – We can’t really hide a secret in software – We cannot prevent SRE – User with full admin privilege can eventually break any anti. SRE protection 51
 DRM for PDF Documents • Based on design of Media. Snap, Inc. , a small Silicon Valley startup company • Developed a DRM system – Designed to protect PDF documents • Two parts to the system – Server Secure Document Server (SDS) – Client PDF Reader “plugin” software 52
DRM for PDF Documents • Based on design of Media. Snap, Inc. , a small Silicon Valley startup company • Developed a DRM system – Designed to protect PDF documents • Two parts to the system – Server Secure Document Server (SDS) – Client PDF Reader “plugin” software 52
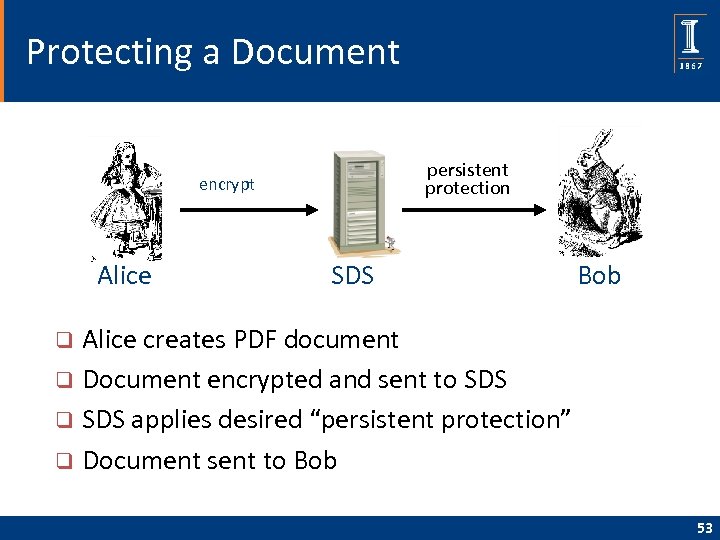 Protecting a Document persistent protection encrypt Alice SDS Bob Alice creates PDF document q Document encrypted and sent to SDS q SDS applies desired “persistent protection” q Document sent to Bob q 53
Protecting a Document persistent protection encrypt Alice SDS Bob Alice creates PDF document q Document encrypted and sent to SDS q SDS applies desired “persistent protection” q Document sent to Bob q 53
 Accessing a Document Request key Alice SDS Bob authenticates to SDS q Bob requests key from SDS q Bob can then access document, but only thru special DRM software q 54
Accessing a Document Request key Alice SDS Bob authenticates to SDS q Bob requests key from SDS q Bob can then access document, but only thru special DRM software q 54
 Security Issues • Server side (SDS) – Protect keys, authentication data, etc. – Apply persistent protection • Client side (PDF plugin) – Protect keys, authenticate user, etc. – Enforce persistent protection • Remaining discussion concerns client 55
Security Issues • Server side (SDS) – Protect keys, authentication data, etc. – Apply persistent protection • Client side (PDF plugin) – Protect keys, authenticate user, etc. – Enforce persistent protection • Remaining discussion concerns client 55
 Security Overview Tamper-resistance Obfuscation A tamper-resistant outer layer q Software obfuscation applied within q 56
Security Overview Tamper-resistance Obfuscation A tamper-resistant outer layer q Software obfuscation applied within q 56
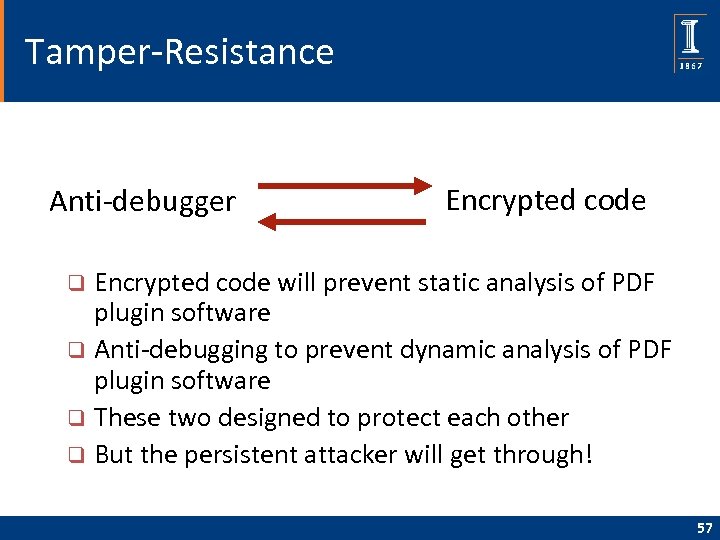 Tamper-Resistance Anti-debugger Encrypted code will prevent static analysis of PDF plugin software q Anti-debugging to prevent dynamic analysis of PDF plugin software q These two designed to protect each other q But the persistent attacker will get through! q 57
Tamper-Resistance Anti-debugger Encrypted code will prevent static analysis of PDF plugin software q Anti-debugging to prevent dynamic analysis of PDF plugin software q These two designed to protect each other q But the persistent attacker will get through! q 57
 Obfuscation • Obfuscation can be used for – – – Key management Authentication Caching (keys and authentication info) Encryption and “scrambling” Key parts (data and/or code) Multiple keys/key parts • Obfuscation can only slow the attacker • The persistent attacker still wins! 58
Obfuscation • Obfuscation can be used for – – – Key management Authentication Caching (keys and authentication info) Encryption and “scrambling” Key parts (data and/or code) Multiple keys/key parts • Obfuscation can only slow the attacker • The persistent attacker still wins! 58
 Other Security Features • Code tamper checking (hashing) – To validate all code executing on system • Anti-screen capture – To prevent obvious attack on digital documents • Watermarking – In theory, can trace stolen content – In practice, of limited value • Metamorphism (or individualization) – For BOBE-resistance 59
Other Security Features • Code tamper checking (hashing) – To validate all code executing on system • Anti-screen capture – To prevent obvious attack on digital documents • Watermarking – In theory, can trace stolen content – In practice, of limited value • Metamorphism (or individualization) – For BOBE-resistance 59
 Not Implemented in Media. Snap • More general code obfuscation • Making the code more fragile – Code that hash checks itself – Tampering should cause code to break • OS cannot be trusted – How to protect against “bad” OS? – Not an easy problem! 60
Not Implemented in Media. Snap • More general code obfuscation • Making the code more fragile – Code that hash checks itself – Tampering should cause code to break • OS cannot be trusted – How to protect against “bad” OS? – Not an easy problem! 60
 DRM Failures • One system defeated by a felt-tip pen • One defeated my holding down shift key • Secure Digital Music Initiative (SDMI) completely broken before it was finished • Adobe e. Books • Microsoft MS-DRM (version 2) • Many, many others! 61
DRM Failures • One system defeated by a felt-tip pen • One defeated my holding down shift key • Secure Digital Music Initiative (SDMI) completely broken before it was finished • Adobe e. Books • Microsoft MS-DRM (version 2) • Many, many others! 61
 Kryptonite Lock Hacked with Ball Point Pen 62
Kryptonite Lock Hacked with Ball Point Pen 62
![SDMI Case Study [Craver. WLSSWDF 01] 63 SDMI Case Study [Craver. WLSSWDF 01] 63](https://present5.com/presentation/e703addae8978e24508cc934917f7b55/image-63.jpg) SDMI Case Study [Craver. WLSSWDF 01] 63
SDMI Case Study [Craver. WLSSWDF 01] 63
![Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. •](https://present5.com/presentation/e703addae8978e24508cc934917f7b55/image-64.jpg) Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • [Craver. WLSSWDF 01] Reading Between the Lines: Lessons from the SDMI Challenge, Scott A. Craver, Min Wu, Bede Liu, Adam Stubblefield, Ben Swartzlander, Dan S. Wallach, Drew Dean, and Edward W. Felten. Usenix 2001. 64
Reading • [Stamp 06] Information Security Principles and Practice, Mark Stamp. Wiley 2006. • [Craver. WLSSWDF 01] Reading Between the Lines: Lessons from the SDMI Challenge, Scott A. Craver, Min Wu, Bede Liu, Adam Stubblefield, Ben Swartzlander, Dan S. Wallach, Drew Dean, and Edward W. Felten. Usenix 2001. 64
 Discussion • Speculate on “enterprise” uses of DRM: can an enterprise use DRM to help control, say, it’s employee’s use of sensitive documents? • Which do you think would be better overall, a world with widespread strong DRM or one with little or no DRM protection? 65
Discussion • Speculate on “enterprise” uses of DRM: can an enterprise use DRM to help control, say, it’s employee’s use of sensitive documents? • Which do you think would be better overall, a world with widespread strong DRM or one with little or no DRM protection? 65
 463. 6. 3 Rights Expression Languages (RELs)
463. 6. 3 Rights Expression Languages (RELs)
 Goals of a Rights Expression Language (REL) • Express copyright • Express contract or license agreements • Control access or use of digital good 67
Goals of a Rights Expression Language (REL) • Express copyright • Express contract or license agreements • Control access or use of digital good 67
 Historical Origins (Xr. ML Thread) • 1994 Xerox PARC patent by Mark Stefik • 1998 Xerox Rights Management group develops DPRL (version 2. 0 translates LISP to XML) • 2000 Content. Guard (spin off of PARC and Microsoft) develops Xr. ML • 2002 Oasis Xr. ML group disbands • 2003 MPEG-21 Part 5, Rights Expression Language (ISO/IEC 21000 -5) • 2003 Open e. Book Forum uses MPEG-21 as REL [Coyle 04] [Stefik 98] 68
Historical Origins (Xr. ML Thread) • 1994 Xerox PARC patent by Mark Stefik • 1998 Xerox Rights Management group develops DPRL (version 2. 0 translates LISP to XML) • 2000 Content. Guard (spin off of PARC and Microsoft) develops Xr. ML • 2002 Oasis Xr. ML group disbands • 2003 MPEG-21 Part 5, Rights Expression Language (ISO/IEC 21000 -5) • 2003 Open e. Book Forum uses MPEG-21 as REL [Coyle 04] [Stefik 98] 68
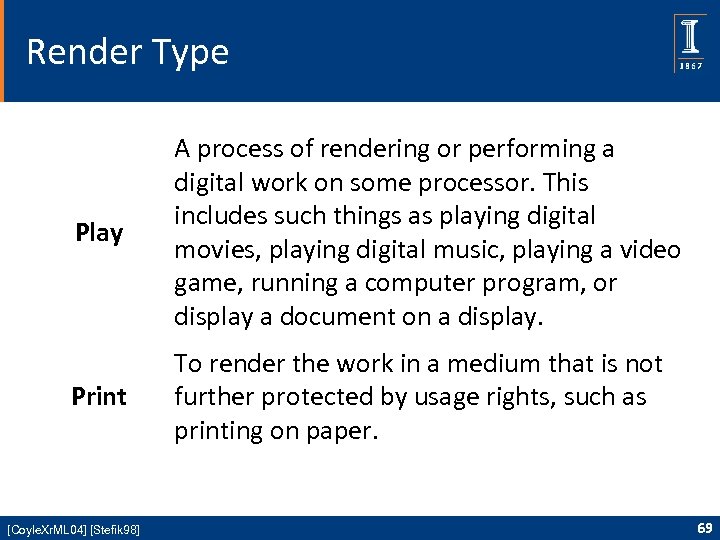 Render Type Play A process of rendering or performing a digital work on some processor. This includes such things as playing digital movies, playing digital music, playing a video game, running a computer program, or display a document on a display. Print To render the work in a medium that is not further protected by usage rights, such as printing on paper. [Coyle. Xr. ML 04] [Stefik 98] 69
Render Type Play A process of rendering or performing a digital work on some processor. This includes such things as playing digital movies, playing digital music, playing a video game, running a computer program, or display a document on a display. Print To render the work in a medium that is not further protected by usage rights, such as printing on paper. [Coyle. Xr. ML 04] [Stefik 98] 69
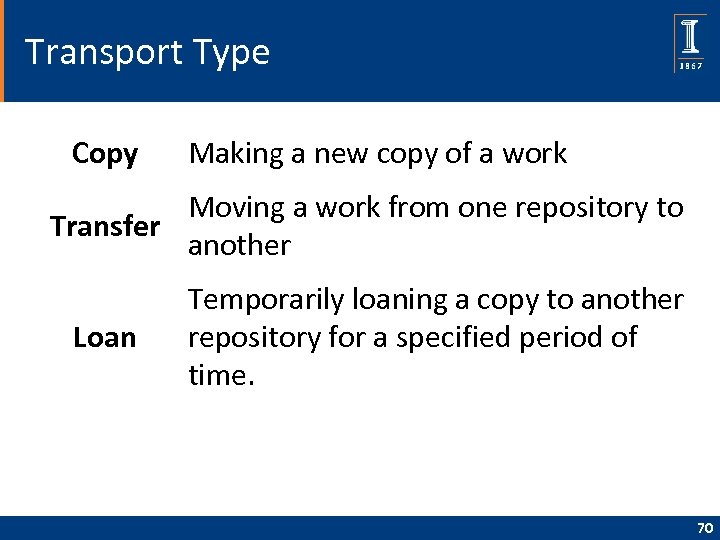 Transport Type Copy Making a new copy of a work Moving a work from one repository to Transfer another Loan Temporarily loaning a copy to another repository for a specified period of time. 70
Transport Type Copy Making a new copy of a work Moving a work from one repository to Transfer another Loan Temporarily loaning a copy to another repository for a specified period of time. 70
 File Management Backup To make a backup copy of a digital work as protection against media failure. Restore To restore a backup copy of a digital work. Delete To delete or erase a copy of a digital work. Folder To create and name folders, and to move files and folders between folders Directory To hide a folder or its contents 71
File Management Backup To make a backup copy of a digital work as protection against media failure. Restore To restore a backup copy of a digital work. Delete To delete or erase a copy of a digital work. Folder To create and name folders, and to move files and folders between folders Directory To hide a folder or its contents 71
 Derivative Works To remove a portion of a work, for Extract the purposes of creating a new work. Embed To include a work in an existing work. Edit To alter a digital work by copying, selecting and modifying portions of an existing digital work 72
Derivative Works To remove a portion of a work, for Extract the purposes of creating a new work. Embed To include a work in an existing work. Edit To alter a digital work by copying, selecting and modifying portions of an existing digital work 72
 Controls Copy count . . . limit as to the number of "copies" of the work which may be exercised simultaneously for the right. Restrictable / unrestrictable . . . a condition to specify the effect of usage rights and fees of parents on the exercise of the right. Time . . . provides for specification of time conditions on the exercise of a right. . The terms "time" and "date" are used synonymously to refer to a moment in time. Further divided into start, end, and intervals. Security class Access specifications can specify a required security class for a repository to exercise a right or a required authorization test that must be satisfied. The billing for use is fundamental to a commercial distribution system. Usage Fees and Allows for per use or metered; can be a fee from the user, or an Incentives incentive paid to the user. 73
Controls Copy count . . . limit as to the number of "copies" of the work which may be exercised simultaneously for the right. Restrictable / unrestrictable . . . a condition to specify the effect of usage rights and fees of parents on the exercise of the right. Time . . . provides for specification of time conditions on the exercise of a right. . The terms "time" and "date" are used synonymously to refer to a moment in time. Further divided into start, end, and intervals. Security class Access specifications can specify a required security class for a repository to exercise a right or a required authorization test that must be satisfied. The billing for use is fundamental to a commercial distribution system. Usage Fees and Allows for per use or metered; can be a fee from the user, or an Incentives incentive paid to the user. 73
 Four Examples of RELs • • Creative. Commons METSRights Open Digital Rights Language (ODRL) MPEG-21 Part 5 74
Four Examples of RELs • • Creative. Commons METSRights Open Digital Rights Language (ODRL) MPEG-21 Part 5 74
 Creative Commons • Developed in 2002 to express rights for web materials such as HTML documents, RSS feeds, and digital audio files • License is machine readable but there is no machine-actionable control, relies on trust and legal enforcement • Broadly based on open licensing scheme of in GNU General Public License 75
Creative Commons • Developed in 2002 to express rights for web materials such as HTML documents, RSS feeds, and digital audio files • License is machine readable but there is no machine-actionable control, relies on trust and legal enforcement • Broadly based on open licensing scheme of in GNU General Public License 75
 METSRights • METS community consists of library institutions providing digital materials for use in education and research. • Need to identify ownership and contractual requirements for re-use and re-purposing • XML schema developed but is not machine actionable • Targeted to library professionals who decide how resources can be used in their institutions 76
METSRights • METS community consists of library institutions providing digital materials for use in education and research. • Need to identify ownership and contractual requirements for re-use and re-purposing • XML schema developed but is not machine actionable • Targeted to library professionals who decide how resources can be used in their institutions 76
 ODRL • Designed as an open standard for expressing general machine-readable licenses • XML representation is meant to be machineactionable • Available for free use 77
ODRL • Designed as an open standard for expressing general machine-readable licenses • XML representation is meant to be machineactionable • Available for free use 77
 MPEG-21 Part 5 • Developed by Moving Picture Experts Group (MPEG) • MPEG-21 is a framework for multi-media content • Part 5 concerns an Intellectual Property Management and Protection (IPMP) framework and defines the MPEG REL (based on Xr. ML) • Accepted as ISO 21000 • Intended to be unambiguously machineactionable 78
MPEG-21 Part 5 • Developed by Moving Picture Experts Group (MPEG) • MPEG-21 is a framework for multi-media content • Part 5 concerns an Intellectual Property Management and Protection (IPMP) framework and defines the MPEG REL (based on Xr. ML) • Accepted as ISO 21000 • Intended to be unambiguously machineactionable 78
 Example • Foo University has a site license for itself and its sister institution, Fubar U. • Foo U is the main licensee, but the site license includes on-campus access for students and faculty at Fubar U and allows standard journal article copying for inter-library loan from Foo U to Fubar U. 79
Example • Foo University has a site license for itself and its sister institution, Fubar U. • Foo U is the main licensee, but the site license includes on-campus access for students and faculty at Fubar U and allows standard journal article copying for inter-library loan from Foo U to Fubar U. 79
 Professors (Foo U) Professors have: a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) c. right to make 30 downloadable digital copies of any documents for classroom use by students authenticated to be in the class (20 of these per year per professor). 80
Professors (Foo U) Professors have: a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) c. right to make 30 downloadable digital copies of any documents for classroom use by students authenticated to be in the class (20 of these per year per professor). 80
 Students in both universities and professors of Fubar have: a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) 81
Students in both universities and professors of Fubar have: a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) 81
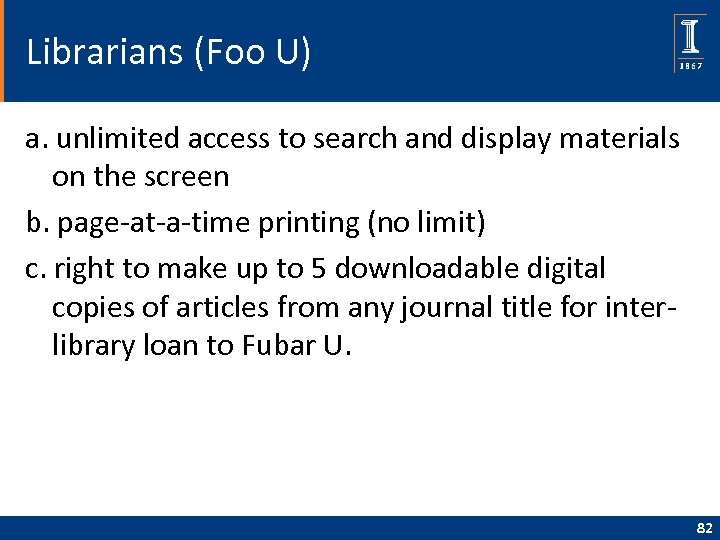 Librarians (Foo U) a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) c. right to make up to 5 downloadable digital copies of articles from any journal title for interlibrary loan to Fubar U. 82
Librarians (Foo U) a. unlimited access to search and display materials on the screen b. page-at-a-time printing (no limit) c. right to make up to 5 downloadable digital copies of articles from any journal title for interlibrary loan to Fubar U. 82
 Librarians (Fubar U) May grant rights to use these 5 copies, to students and professors of Fubar U. These usage rights are as follows: i. Maximum 1 other digital copy (to move it form one machine to another) ii. Maximum the equivalent of 2 print copies (you know, the dog ate it) iii. Time limit = end of semester c 4. No lending, no giving away, no selling 83
Librarians (Fubar U) May grant rights to use these 5 copies, to students and professors of Fubar U. These usage rights are as follows: i. Maximum 1 other digital copy (to move it form one machine to another) ii. Maximum the equivalent of 2 print copies (you know, the dog ate it) iii. Time limit = end of semester c 4. No lending, no giving away, no selling 83
 Agreement Frame 84
Agreement Frame 84
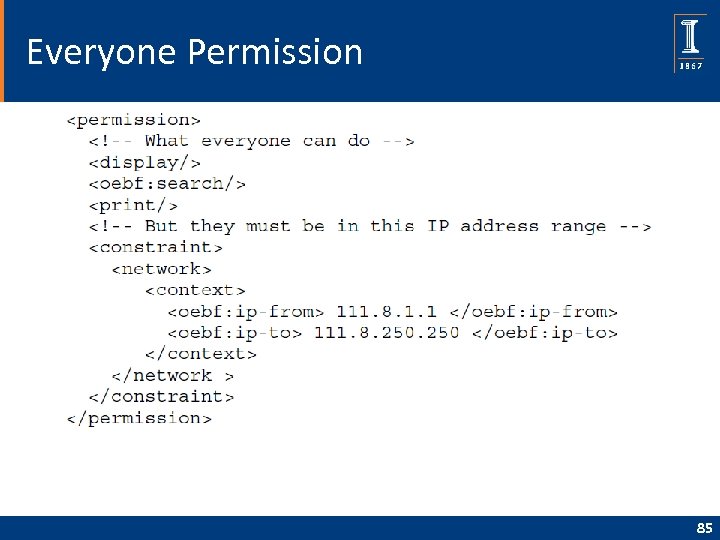 Everyone Permission 85
Everyone Permission 85
 Professors (Foo. U) Part 1 of 2 86
Professors (Foo. U) Part 1 of 2 86
 Professors (Foo. U) Part 2 of 2 87
Professors (Foo. U) Part 2 of 2 87
![Reading • [Coyle 04] Rights Expression Languages, Karen Coyle. A Report for the Library Reading • [Coyle 04] Rights Expression Languages, Karen Coyle. A Report for the Library](https://present5.com/presentation/e703addae8978e24508cc934917f7b55/image-88.jpg) Reading • [Coyle 04] Rights Expression Languages, Karen Coyle. A Report for the Library of Congress, February 2004. • [Stefik 07] “DRM Inside” DRM and the Future of Digital Media, Mark Stefik. Digital Rights Strategies 2007. • [Gunter. MS 04] A Formal Privacy System and its Application to Location Based Services, Carl A. Gunter, Michael J. May, Stuart Stubblebine. PET 2004. 88
Reading • [Coyle 04] Rights Expression Languages, Karen Coyle. A Report for the Library of Congress, February 2004. • [Stefik 07] “DRM Inside” DRM and the Future of Digital Media, Mark Stefik. Digital Rights Strategies 2007. • [Gunter. MS 04] A Formal Privacy System and its Application to Location Based Services, Carl A. Gunter, Michael J. May, Stuart Stubblebine. PET 2004. 88
 Discussion Preliminaries • “DRM Inside” • Personal DRM (PDRM) 89
Discussion Preliminaries • “DRM Inside” • Personal DRM (PDRM) 89
 Freedom From Advertisements • DRM could offer consumers the freedom to enjoy content without the distraction of advertisements. • This freedom would be available only in media and media systems that have DRM inside. [Stefik 07] 90
Freedom From Advertisements • DRM could offer consumers the freedom to enjoy content without the distraction of advertisements. • This freedom would be available only in media and media systems that have DRM inside. [Stefik 07] 90
 Enabling Social Networks to Drive Discovery • Digital media systems do not come close to the potential for supporting the discovery of music or other information. • There is a vast, untapped opportunity to use social networks to drive distribution, discovery and sales of interesting content. 91
Enabling Social Networks to Drive Discovery • Digital media systems do not come close to the potential for supporting the discovery of music or other information. • There is a vast, untapped opportunity to use social networks to drive distribution, discovery and sales of interesting content. 91
 Symbiotic Music Systems • With digital music and more modern lifestyles, we have more devices – at work, in our cars, and in our homes. • It would be more appropriate for our devices to act together as a single system. 92
Symbiotic Music Systems • With digital music and more modern lifestyles, we have more devices – at work, in our cars, and in our homes. • It would be more appropriate for our devices to act together as a single system. 92
 Personal Digital Rights Management (PDRM) • Turn Digital Rights Management on its head – Those who the data is about can manage how it is used • Users manage permissions on their data through rules and enforcements mechanisms – Use existing languages and software for DRM • If DRM can be used to specify that a movie can be watched only a specific number of times, PDRM can be used to specify that personal information can only be used in a certain way a particular number of times [Gunter. MS 04] 93
Personal Digital Rights Management (PDRM) • Turn Digital Rights Management on its head – Those who the data is about can manage how it is used • Users manage permissions on their data through rules and enforcements mechanisms – Use existing languages and software for DRM • If DRM can be used to specify that a movie can be watched only a specific number of times, PDRM can be used to specify that personal information can only be used in a certain way a particular number of times [Gunter. MS 04] 93
 Ad. Loc Architecture • Ad. Loc system allows for permission-based advertising based on geo-location information • Allows PDA users to discover their geo-location and send it to a central database where it can be accessed only with a digital license • Architectural elements – – Geo. Location Service (GLS) Geo. Information Service (GIS) Ad. Loc PDA Application Ad. Loc Merchant Application 94
Ad. Loc Architecture • Ad. Loc system allows for permission-based advertising based on geo-location information • Allows PDA users to discover their geo-location and send it to a central database where it can be accessed only with a digital license • Architectural elements – – Geo. Location Service (GLS) Geo. Information Service (GIS) Ad. Loc PDA Application Ad. Loc Merchant Application 94
 Discovering Location Private Data Holder Subject 95
Discovering Location Private Data Holder Subject 95
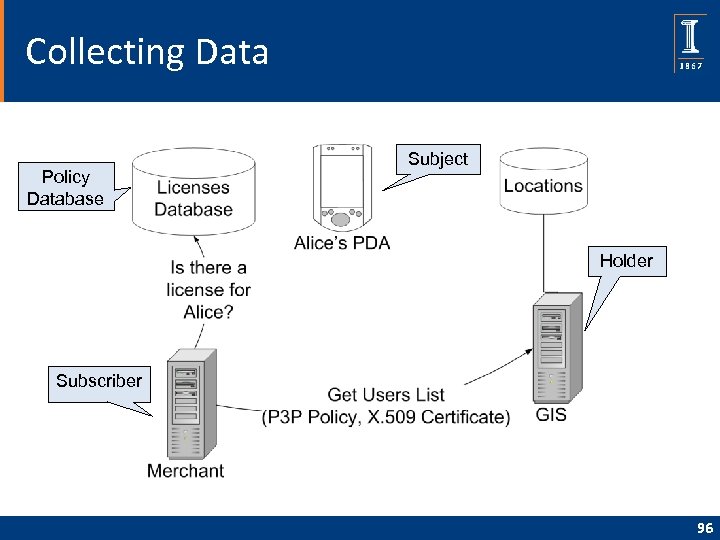 Collecting Data Policy Database Subject Holder Subscriber 96
Collecting Data Policy Database Subject Holder Subscriber 96
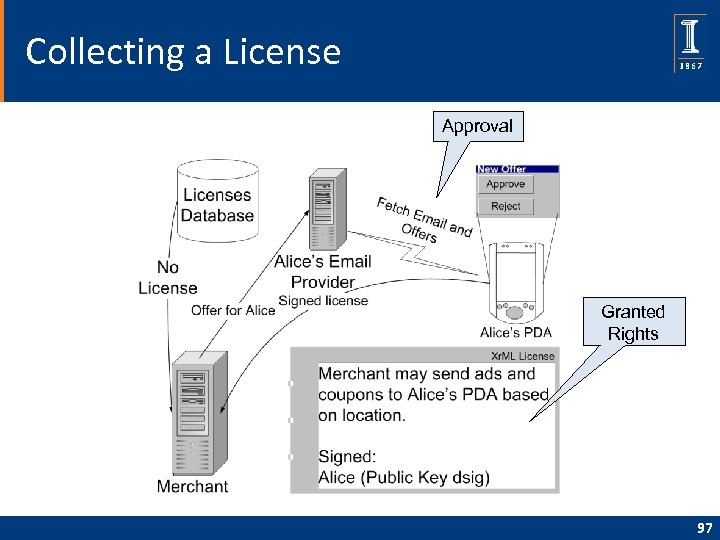 Collecting a License Approval Granted Rights 97
Collecting a License Approval Granted Rights 97
 Action – Sending an Ad Action as approved by license 98
Action – Sending an Ad Action as approved by license 98
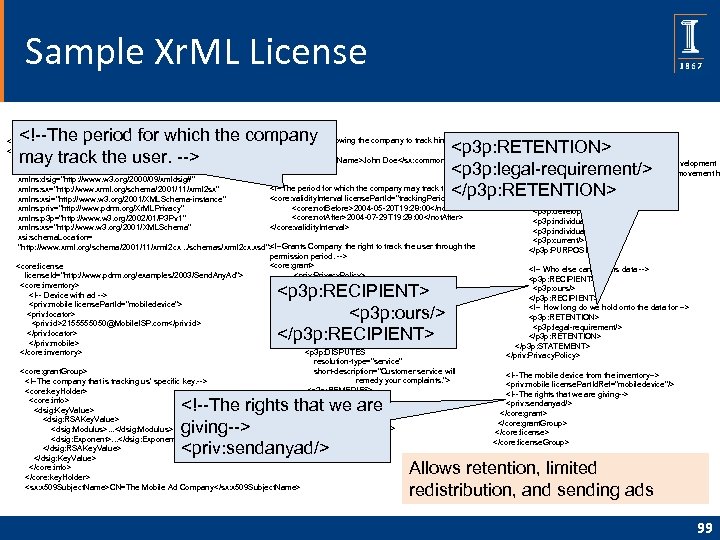 Sample Xr. ML License
Sample Xr. ML License
resolution-type="service" short-description="Customer service will
We collect your location information
for developmenth purposes and for tracking your individual movement
 Discussion Questions • What are the benefits a consumer might find in DRM? – Can we use it to eliminate advertisements? – Is it a good fit with social networking? • What are the limits of trust for DRM, is there anybody we can trust? • Is there hope for DRM-like enforcement of the use of personal information? 10
Discussion Questions • What are the benefits a consumer might find in DRM? – Can we use it to eliminate advertisements? – Is it a good fit with social networking? • What are the limits of trust for DRM, is there anybody we can trust? • Is there hope for DRM-like enforcement of the use of personal information? 10


