52903923b669183db38cb3e71d1061b0.ppt
- Количество слайдов: 51

463. 4 Botnets Computer Security II CS 463/ECE 424 University of Illinois

Overview • Discussion in two parts – Motives and analysis techniques – Architectures and strategies 2

463. 5. 1 Motives and Analysis Techniques for Botnets
What are Botnets? • A botnet is a collection of compromised machines (bots) remotely controlled by an attacker • They are used for various forms of illegal activity • Why the need for compromised machines? – Save money on provisioning – Obscure controlling party by the use of stepping stones • Why the need for multiple compromised machines? – Defending against multiple machines is harder: DDo. S and dynamic blacklisting 4

Underground Cyber-Markets • An “underground” market is one that operates outside of government regulation, often dealing in illegal goods or services • Examples: drugs, prostitution • The underground cyber-markets are ones where underground commerce is carried out over the Internet 5
![What’s the Supply and Demand? [Franklin. PPS 07] 6 What’s the Supply and Demand? [Franklin. PPS 07] 6](https://present5.com/presentation/52903923b669183db38cb3e71d1061b0/image-6.jpg)
What’s the Supply and Demand? [Franklin. PPS 07] 6
Internet Relay Chat (IRC) Channels • IETF protocol for message exchange • IRC client connects to a server identifying itself with a nickname (“nick”) and joins a channel • Client can broadcast on the channel or deliver messages privately on the channel • Channel manager may supplementary services to users 7
IRC Roles for Botnets • Connect buyers and sellers • Control botnet • Broadcast nature of IRC aids untraceable communication 8

Targeted Applications • Extortion – Cryptoviral extortion – Do. S • Fraud (viz. identity theft) – Bank accounts – Credit cards • SPAM – Direct advertising – Fraud 9

Roles of Participants Buyers: seek to make money off scams Carders: provide credit card data Cashiers: provide ways to convert these to cash Droppers: enable pick-ups of merchandise purchased with credit cards Rippers: take payment without providing service Operators: channel owners who provide integrity services like “verified status” 10

Buyer <buyer a> need fresh US Fullz Msg Me Fast If U have Am Payin E-gold. <buyer b> i buy uk cc's. . prv me only serios ppl 4 good dill. <buyer c> Looking to buy HSBC debit with pins and CC's. . . 11

Carder <carder a> selling US (Visa, Master) $2, UK (Barclay) $3. e-gold only <carder b> selling us, uk fresh fulls (master & visa) $10. I accept paypal or e-gold <carder c> Am Selling US, UK Mastercard, Visa, and American Express Fulls, Fresh and 100% valid, WIth DOB, SSN, DL. 12

Cashier <cashier a> i Cash Out Wells fargo, Boa, Nation Wide, Chase, Wachovi. A, Wa. Mu, Citibank, Halifax Msg me. <cashier b> I Cashout Skimmed Dumps + Pins 30/70 % Split i Take 30% You Take 70%. <cashier c> can cashout cvv's via WU terminal agent. 500 -700 $ per cvv's pvt me for more info. 13

Dropper <drop a> i drop in usa i can pick any name. <user b> F@!k drops man, I ship to my friends house, no fee. <user c> u will lose ur friends soon! ^^ <user d> I guess some friends are expendable! 14
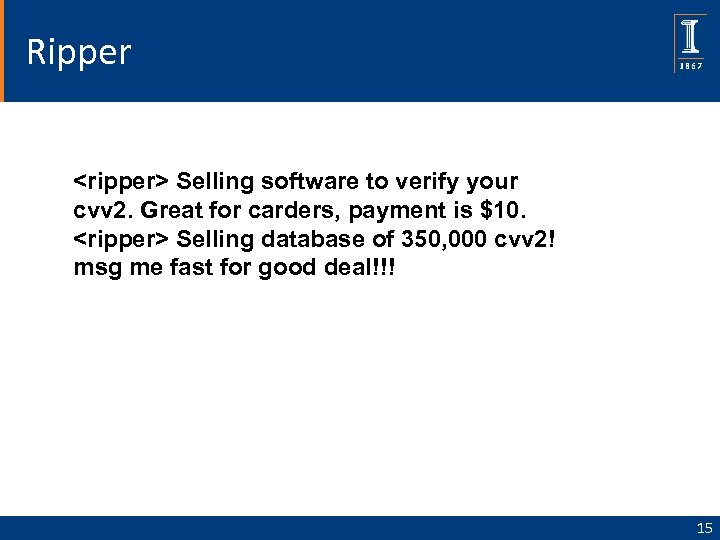
Ripper <ripper> Selling software to verify your cvv 2. Great for carders, payment is $10. <ripper> Selling database of 350, 000 cvv 2! msg me fast for good deal!!! 15
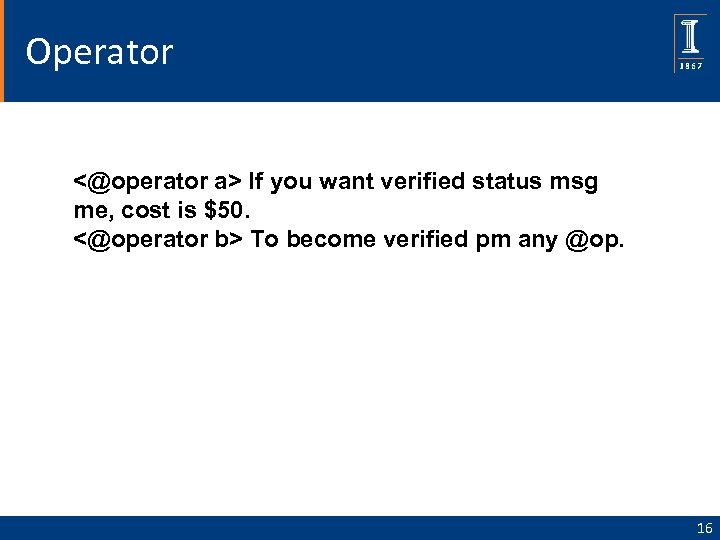
Operator <@operator a> If you want verified status msg me, cost is $50. <@operator b> To become verified pm any @op. 16
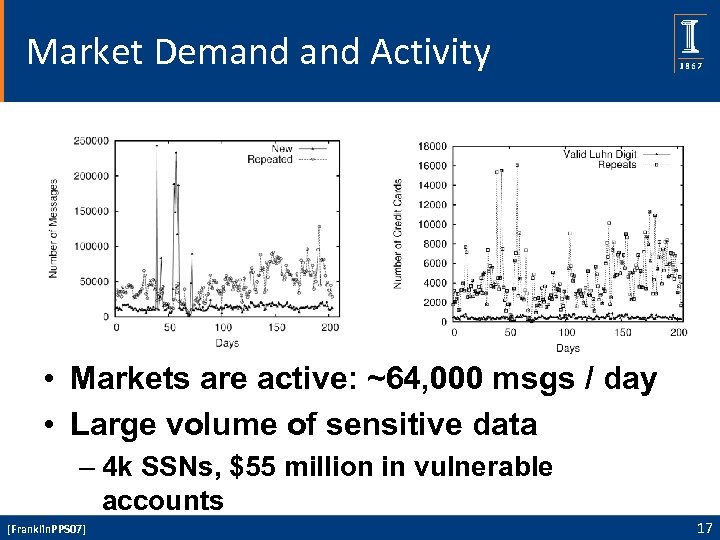
Market Demand Activity • Markets are active: ~64, 000 msgs / day • Large volume of sensitive data – 4 k SSNs, $55 million in vulnerable accounts [Franklin. PPS 07] 17
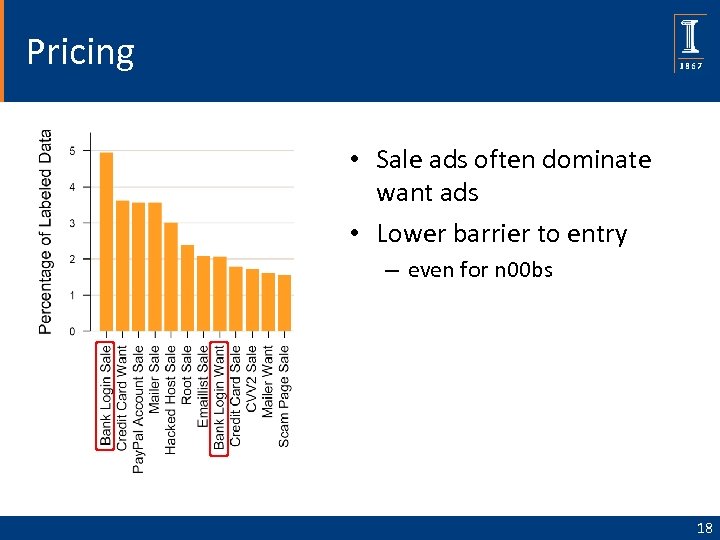
Pricing • Sale ads often dominate want ads • Lower barrier to entry – even for n 00 bs 18
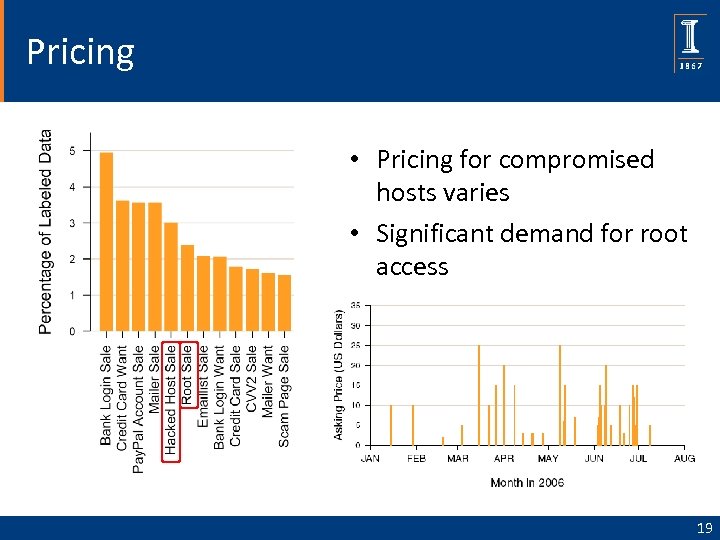
Pricing • Pricing for compromised hosts varies • Significant demand for root access 19
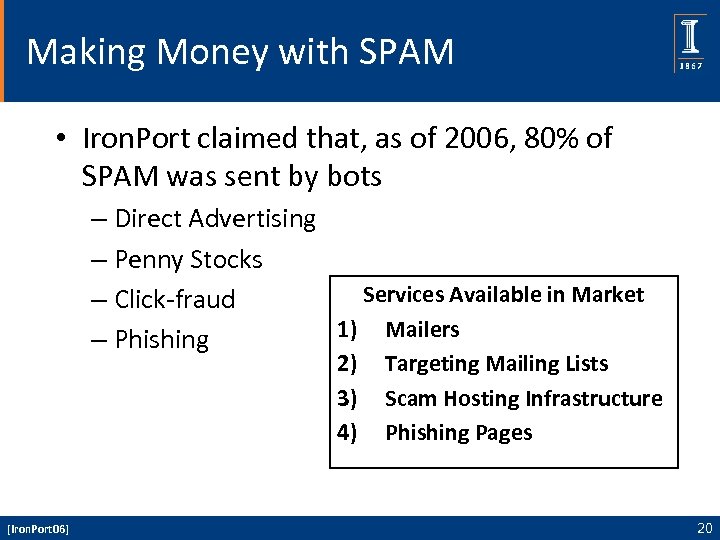
Making Money with SPAM • Iron. Port claimed that, as of 2006, 80% of SPAM was sent by bots – Direct Advertising – Penny Stocks Services Available in Market – Click-fraud 1) Mailers – Phishing 2) 3) 4) [Iron. Port 06] Targeting Mailing Lists Scam Hosting Infrastructure Phishing Pages 20

How Do I Get My (Stolen) Money? • E-gold (Nevis, Lesser Antilles) was fined $3. 7 million for “conspiracy to engage in money laundering” and the “operation of an unlicensed money transmitting business”. • Western Union requires in country initiation and transfers over $1 K require Passport, SSN, Drivers License # • Drops provide an out-of-band approach • Colorful strategies: touts, gambling, Lindens, etc. 21
Analyzing Bots • Examine source code • Attract compromise with a honeypot – Honeynet project • Observe public communications and collect statistics – By manual analysis – Using attribute searches – Using machine learning • Compromise a bot and observe its activities 22
![Reading List • [Franklin. PPS 07] An Inquiry into the Nature and Causes of Reading List • [Franklin. PPS 07] An Inquiry into the Nature and Causes of](https://present5.com/presentation/52903923b669183db38cb3e71d1061b0/image-23.jpg)
Reading List • [Franklin. PPS 07] An Inquiry into the Nature and Causes of the Wealth of Internet Miscreants, CCS 2007. • [Thomas. A 07] Kurt Thomas and David Albrecht, Cashing Out: Exploring Underground Economies, Manuscript 2007. 23 23

Discussion • Assuming an IRC channel, speculate on strategies for reducing the effectiveness of the underground cyber-market. • How far can/should a honeynet go to gather information about malware? 24

463. 5. 2 Botnet Architectures and Strategies
Botnet Recruitment/Propagation • Bot code is installed on compromised machines using many different techniques – Scan for victims with vulnerabilities • Horizontal scans across an address range • Vertical scans across a range of ports – Look for backdoors or vulnerable software • Bagel and My. Doom worms left backdoors that allow arbitrary code to be executed on the machine – Hide bot code in legitimate files placed in open file shares and on peer-to-peer networks – Send spam email with attachments infected with bot code 26
Botnet Maintenance/Control • After a computer has been compromised, the bot has several goals – Fortify the system against other malicious attacks – Disable anti-virus software – Harvest sensitive information • The attacker issues commands to the bots – Download updates to the bot code – Download patches to prevent other botnets from capturing the machine – Participate in the botnet “work”: send spam and phishing emails, contribute to DDo. S attack, etc. 27
![IRC Botnet in a DDo. S Attack [Cooke. JM 05] 28 IRC Botnet in a DDo. S Attack [Cooke. JM 05] 28](https://present5.com/presentation/52903923b669183db38cb3e71d1061b0/image-28.jpg)
IRC Botnet in a DDo. S Attack [Cooke. JM 05] 28

Case Study: Agobot • • Architecture, Botnet control mechanisms, Host control mechanisms, Propagation mechanisms, Target exploits and attack mechanisms, Malware delivery mechanisms, Obfuscation methods, and Deception strategies. [Barford. Y 07] 29

Architecture • • Source code was released publically around 2002. IRC-based command control Do. S attack library Limited polymorphic obfuscations Harvests Paypal passwords, AOL keys, etc. Defends compromised system Anti-disassembly mechanisms Built with good SE practices 30
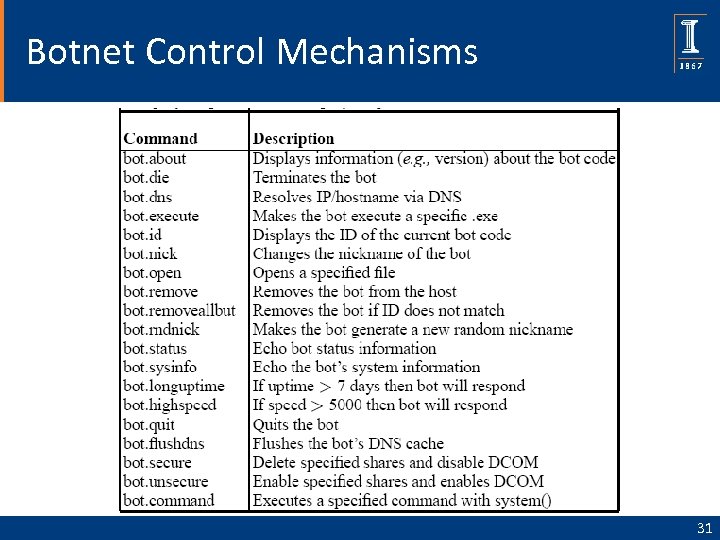
Botnet Control Mechanisms 31
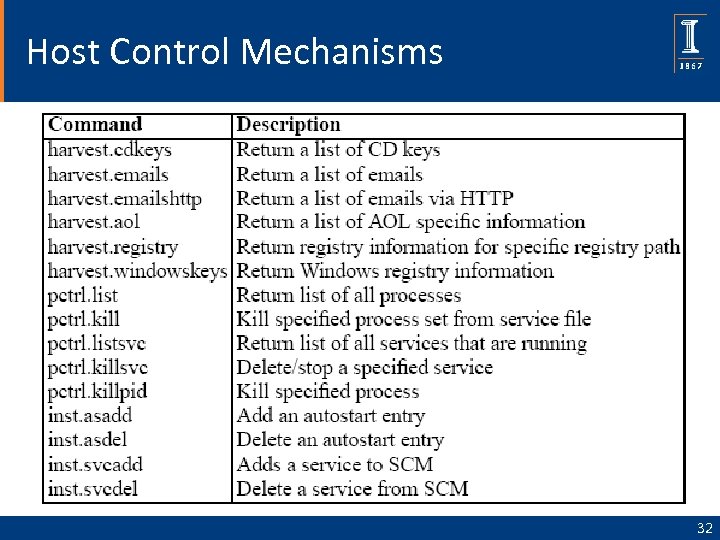
Host Control Mechanisms 32
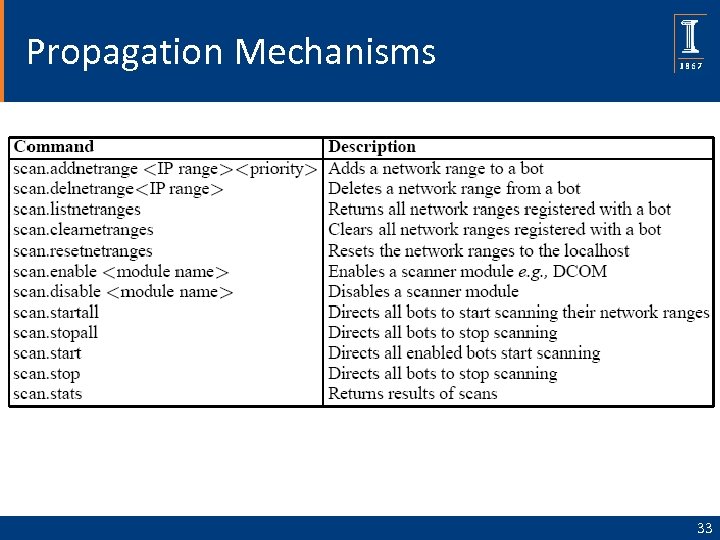
Propagation Mechanisms 33
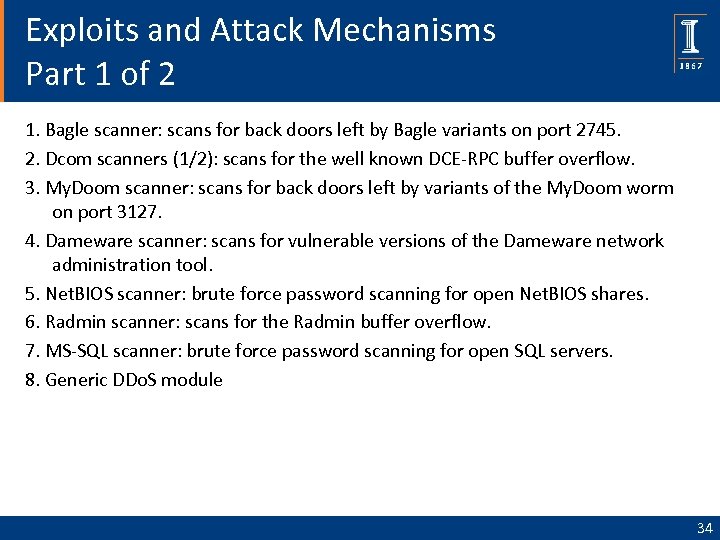
Exploits and Attack Mechanisms Part 1 of 2 1. Bagle scanner: scans for back doors left by Bagle variants on port 2745. 2. Dcom scanners (1/2): scans for the well known DCE-RPC buffer overflow. 3. My. Doom scanner: scans for back doors left by variants of the My. Doom worm on port 3127. 4. Dameware scanner: scans for vulnerable versions of the Dameware network administration tool. 5. Net. BIOS scanner: brute force password scanning for open Net. BIOS shares. 6. Radmin scanner: scans for the Radmin buffer overflow. 7. MS-SQL scanner: brute force password scanning for open SQL servers. 8. Generic DDo. S module 34
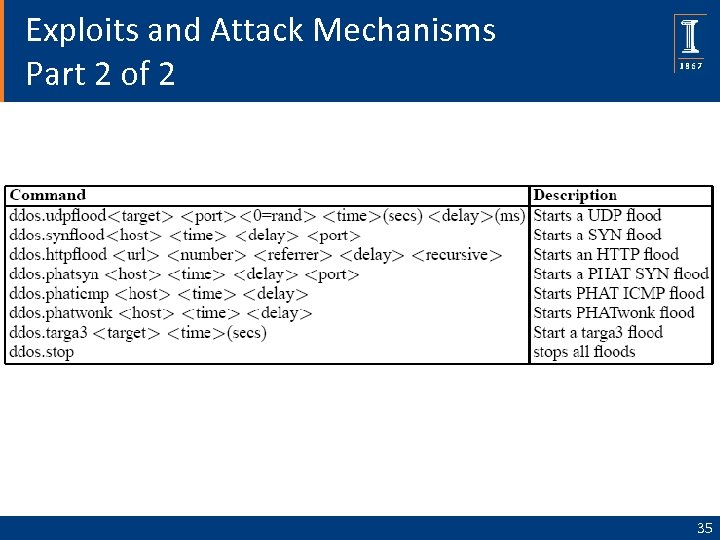
Exploits and Attack Mechanisms Part 2 of 2 35
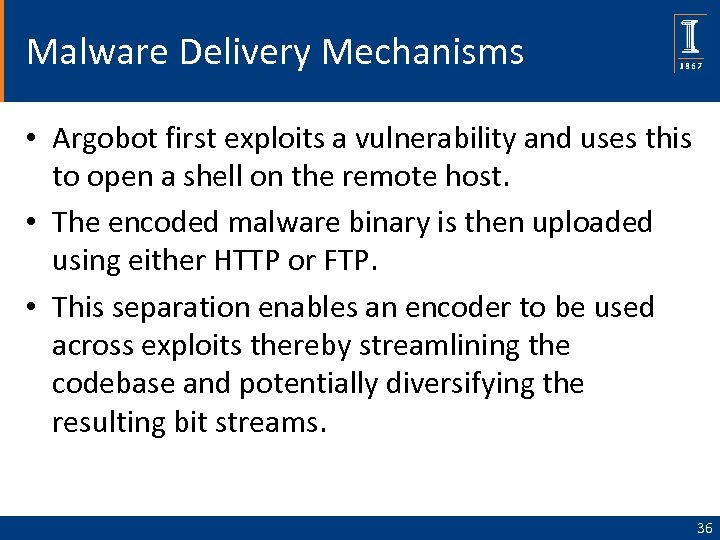
Malware Delivery Mechanisms • Argobot first exploits a vulnerability and uses this to open a shell on the remote host. • The encoded malware binary is then uploaded using either HTTP or FTP. • This separation enables an encoder to be used across exploits thereby streamlining the codebase and potentially diversifying the resulting bit streams. 36
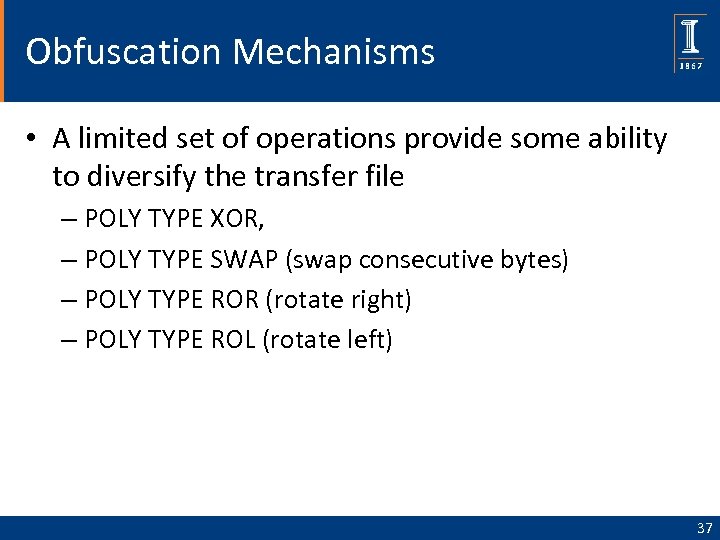
Obfuscation Mechanisms • A limited set of operations provide some ability to diversify the transfer file – POLY TYPE XOR, – POLY TYPE SWAP (swap consecutive bytes) – POLY TYPE ROR (rotate right) – POLY TYPE ROL (rotate left) 37
Deception Mechanisms Part 1 of 2 • Deception refers to the mechanisms used to evade detection once a bot is installed on a target host. • These mechanisms are also referred to as rootkits. 38
Deception Mechanisms Part 2 of 2 • In Agobot the following defenses are included: – Testing for debuggers such as Olly. Debug, Soft. Ice and procdump, – Testing for VMWare, – Killing anti-virus processes, and – Altering DNS entries of anti-virus software companies to point to localhost. 39

Beyond Agobot Evolving Botnet Structure • Original command-control mechanism – Internet Relay Chat (IRC) channels – Centralized control structure • Improved command-control mechanism – Peer-to-peer (P 2 P) networks – Decentralized control structure – More difficult to dismantle than IRC botnets 40
P 2 P Botnets • While IRC bots simply connect to their IRC server, P 2 P bots must follow a series of steps to connect with their P 2 P network • The initial P 2 P bot code contains a list of possible peers and code that attempts to connect the bot with the P 2 P network • After the bot joins the network, the peer list is updated • Then the bot searches the network and downloads the secondary injection code (code that instructs the bot to send spam or perform other malicious activities) 41
Case Study: Storm Worm • First major botnet to employ peer-to-peer command-andcontrol structure • Appeared in 2006, gained prominence in January 2007 • MS estimated 500, 000 bots as of September 2007 • Recruits new bots using a variety of attack vectors – Email messages with executable attachments – Email messages with links to infected sites – E-card spam • Uses computing power of compromised machines – Sends and relays SPAM – Hosts the exploits and binaries – Conducts DDo. S attacks on anti-spam websites and security researchers probing the botnet 42

Social Engineering with Email Headers • • “ 230 dead as storm batters Europe, ” “A killer at 11, he’s free at 21 and kill again!, ” “British Muslims Genocide, ” “Naked teens attack home director, ” “Re: Your text, ” “Russian missile shot down USA satellite, ” “US Secretary of State Condoleezza Rice has kicked German Chancellor Angela Merkel. ” 43
![Effectiveness of Storm [Smith 08] 44 Effectiveness of Storm [Smith 08] 44](https://present5.com/presentation/52903923b669183db38cb3e71d1061b0/image-44.jpg)
Effectiveness of Storm [Smith 08] 44
Storm Worm Botnet Infection Process 1. Victim downloads and runs Trojan executable file n Kernel mode driver component wincom 32. sys n Initialization file component peers. ini n Malware inserts itself into services. exe process 2. Malware connects with peers on P 2 P network n Uses initial list of 146 peers to connect to P 2 P network n Updates peer list with close peers n Searches for encrypted URL of payload 3. Malware downloads full payload n Decrypts URL of payload n Downloads code that sends spam, participates in DDo. S attacks, etc. 4. Malware executes code under the control of the botnet n Bots can periodically search the P 2 P network for code updates 45
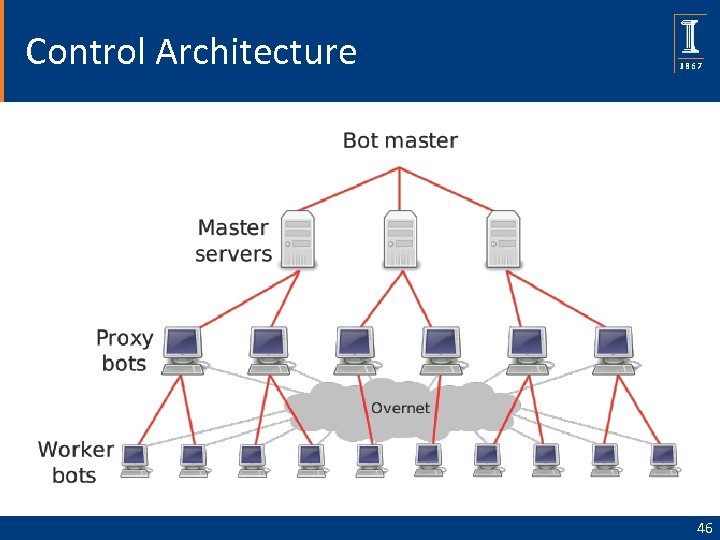
Control Architecture 46
Overnet Protocol • Overnet is a P 2 P protocol based on the Kademlia algorithm • It was created from file sharing community e. Donkey 2000 • Overnet and e. Donkey 2000 had an estimated total of 645, 000 users as of 2006 • Both were shut down by legal actions of RIAA in 2006 47
Distributed Hash Tables (DHT) • Kademlia, and hence also Overnet and Storm, are DHT protocols • DHT network manages a collection of nodes that store (key, value) pairs • DHT can support large scale storage in a robust decentralized system • Key concepts – Key space partitioning – Overlay network 48
Storm Worm Botnet Anti-malware Response • Botnet variations make signature-based detection difficult – New email subject lines and file attachment names – Re-encoded malware binary twice per hour • Anti-malware Response – Microsoft Malicious Software Removal Tool patch issued in September 2007 • Correlated with 20% drop in size of the Storm Worm botnet • Shows that aggressive removal of bots from botnet can make a significant impact on the size of the botnet 49
![Reading List • [Cooke. JM 05] The Zombie Roundup: Understanding, Detecting, and Disrupting Botnets, Reading List • [Cooke. JM 05] The Zombie Roundup: Understanding, Detecting, and Disrupting Botnets,](https://present5.com/presentation/52903923b669183db38cb3e71d1061b0/image-50.jpg)
Reading List • [Cooke. JM 05] The Zombie Roundup: Understanding, Detecting, and Disrupting Botnets, Evan Cooke, Farnam Jahanian, and Danny Mc. Pherson. Steps to Reducing Unwanted Traffic on the Internet Workshop, SRUTI 2005. • [Barford. Y 07] An Inside Look at Botnets, Paul Barford and Vinod Yegneswaran. Advances in Computer Security, Springer 2007. • [Smith 08] A Storm (Worm) Is Brewing, Brad Smith. IEEE Computer, vol. 41, no. 2, pp. 20 -22, Feb. 2008. 50
Discussion • Botnets seem like a major challenge today. How long do you think they will continue as a problem? • Storm represents a cross-over between the file sharing community and the underground cybermarket (viz. SPAM). Conjecture on similar synergies that might emerge in the future. 51
52903923b669183db38cb3e71d1061b0.ppt