8da84da85655b7a50c43975a35354742.ppt
- Количество слайдов: 13

2010. Március 30. IBM Tivoli security portfólió Vörös Ákos – Tivoli Sales Representative Gyenese Péter – Sales Representative © 2010 IBM Corporation
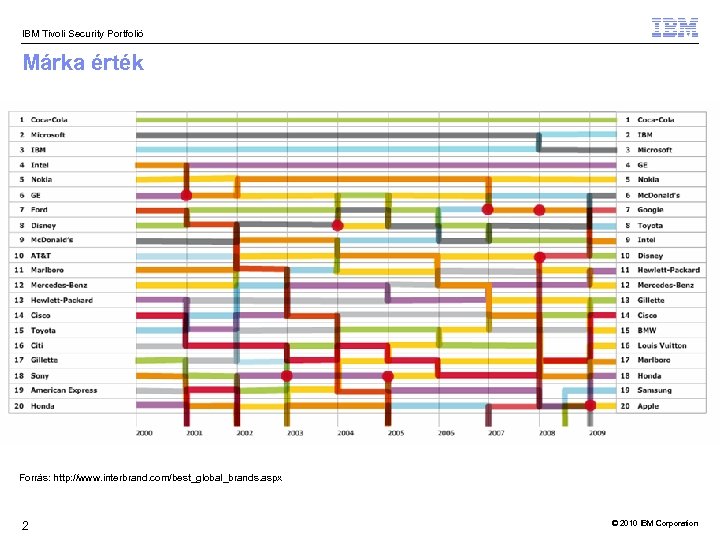
IBM Tivoli Security Portfolió Márka érték Forrás: http: //www. interbrand. com/best_global_brands. aspx 2 © 2010 IBM Corporation
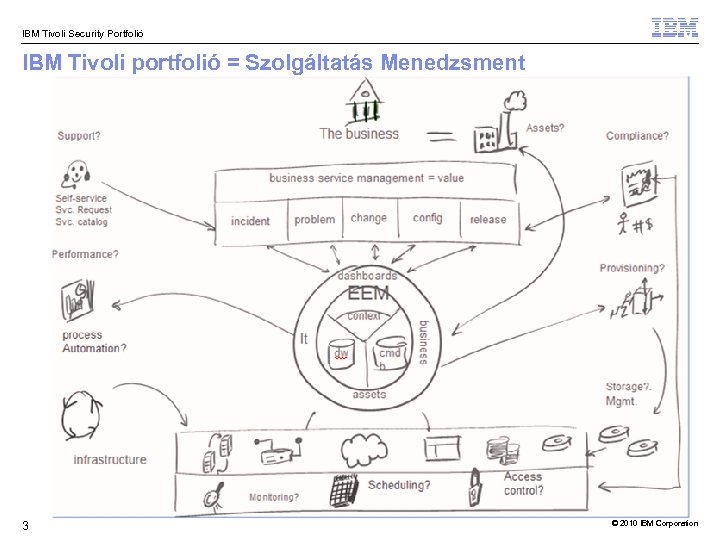
IBM Tivoli Security Portfolió IBM Tivoli portfolió = Szolgáltatás Menedzsment 3 © 2010 IBM Corporation
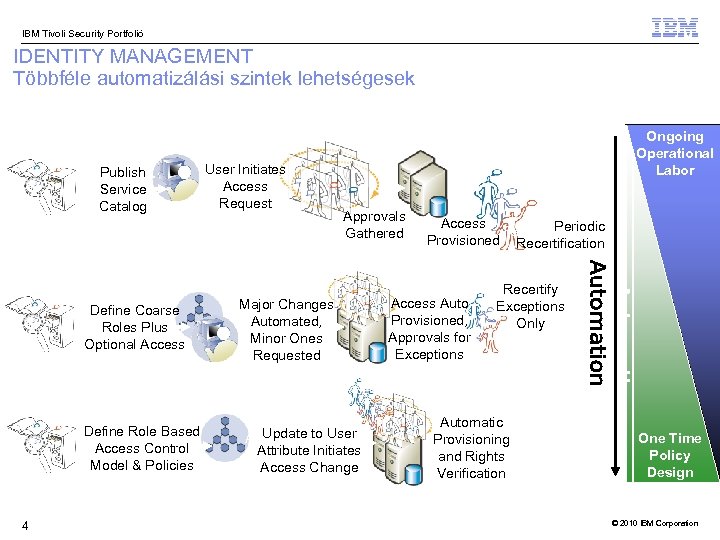
IBM Tivoli Security Portfolió IDENTITY MANAGEMENT Többféle automatizálási szintek lehetségesek Investments Publish Service Catalog User Initiates Access Request Define Coarse Roles Plus Optional Access Define Role Based Define Control Access. Role Based Access Control Model & Policies 4 Ongoing Operational Labor Approvals Access Periodic Approvals Gathered Access Periodic Gathered Provisioned Recertification Major Changes Automated, Minor Ones Requested Update to User Attribute Initiates Access Change Access Auto Provisioned, Approvals for Approvals Exceptions for Exceptions Recertify Exceptions Only Automatic Provisioning and Rights Verification One Time Policy Design © 2010 IBM Corporation
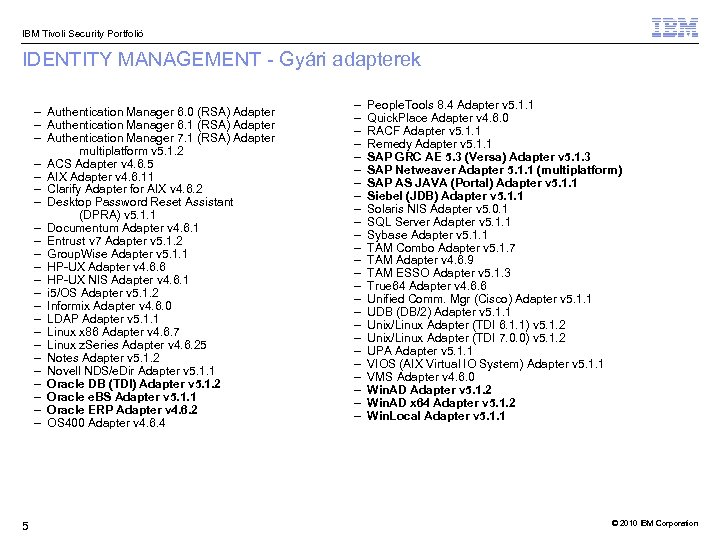
IBM Tivoli Security Portfolió IDENTITY MANAGEMENT - Gyári adapterek – Authentication Manager 6. 0 (RSA) Adapter – Authentication Manager 6. 1 (RSA) Adapter – Authentication Manager 7. 1 (RSA) Adapter multiplatform v 5. 1. 2 – ACS Adapter v 4. 6. 5 – AIX Adapter v 4. 6. 11 – Clarify Adapter for AIX v 4. 6. 2 – Desktop Password Reset Assistant (DPRA) v 5. 1. 1 – Documentum Adapter v 4. 6. 1 – Entrust v 7 Adapter v 5. 1. 2 – Group. Wise Adapter v 5. 1. 1 – HP-UX Adapter v 4. 6. 6 – HP-UX NIS Adapter v 4. 6. 1 – i 5/OS Adapter v 5. 1. 2 – Informix Adapter v 4. 6. 0 – LDAP Adapter v 5. 1. 1 – Linux x 86 Adapter v 4. 6. 7 – Linux z. Series Adapter v 4. 6. 25 – Notes Adapter v 5. 1. 2 – Novell NDS/e. Dir Adapter v 5. 1. 1 – Oracle DB (TDI) Adapter v 5. 1. 2 – Oracle e. BS Adapter v 5. 1. 1 – Oracle ERP Adapter v 4. 6. 2 – OS 400 Adapter v 4. 6. 4 5 – – – – – – – People. Tools 8. 4 Adapter v 5. 1. 1 Quick. Place Adapter v 4. 6. 0 RACF Adapter v 5. 1. 1 Remedy Adapter v 5. 1. 1 SAP GRC AE 5. 3 (Versa) Adapter v 5. 1. 3 SAP Netweaver Adapter 5. 1. 1 (multiplatform) SAP AS JAVA (Portal) Adapter v 5. 1. 1 Siebel (JDB) Adapter v 5. 1. 1 Solaris NIS Adapter v 5. 0. 1 SQL Server Adapter v 5. 1. 1 Sybase Adapter v 5. 1. 1 TAM Combo Adapter v 5. 1. 7 TAM Adapter v 4. 6. 9 TAM ESSO Adapter v 5. 1. 3 True 64 Adapter v 4. 6. 6 Unified Comm. Mgr (Cisco) Adapter v 5. 1. 1 UDB (DB/2) Adapter v 5. 1. 1 Unix/Linux Adapter (TDI 6. 1. 1) v 5. 1. 2 Unix/Linux Adapter (TDI 7. 0. 0) v 5. 1. 2 UPA Adapter v 5. 1. 1 VIOS (AIX Virtual IO System) Adapter v 5. 1. 1 VMS Adapter v 4. 6. 0 Win. AD Adapter v 5. 1. 2 Win. AD x 64 Adapter v 5. 1. 2 Win. Local Adapter v 5. 1. 1 © 2010 IBM Corporation
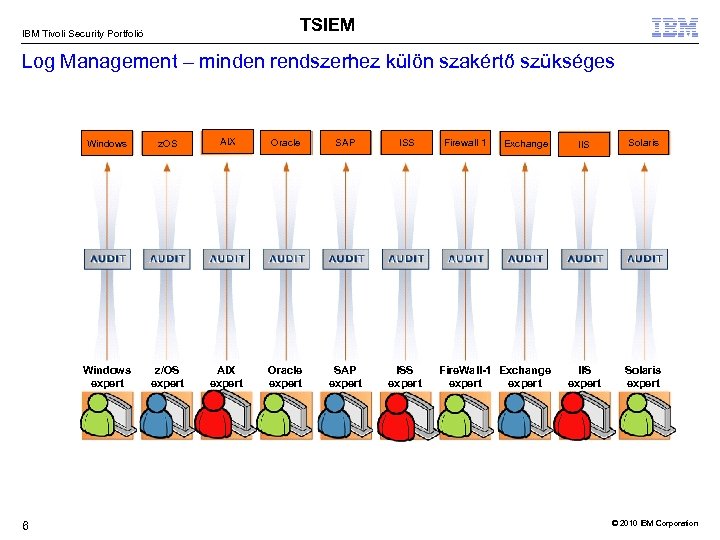
TSIEM IBM Tivoli Security Portfolió Log Management – minden rendszerhez külön szakértő szükséges Windows AIX Oracle SAP ISS Windows expert 6 z. OS z/OS expert AIX expert Oracle expert SAP expert ISS expert Firewall 1 Exchange Fire. Wall-1 Exchange expert IIS Solaris IIS expert Solaris expert © 2010 IBM Corporation
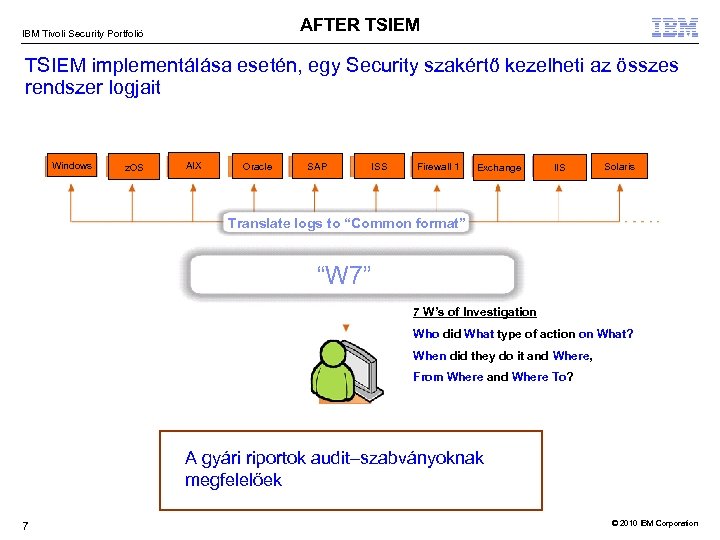
AFTER TSIEM IBM Tivoli Security Portfolió TSIEM implementálása esetén, egy Security szakértő kezelheti az összes rendszer logjait Windows z. OS AIX Oracle SAP ISS Firewall 1 Exchange IIS Solaris Translate logs to “Common format” “W 7” 7 W’s of Investigation Who did What type of action on What? When did they do it and Where, From Where and Where To? View this data via a graphical enterprise compliance dashboard A gyári riportok audit–szabványoknak megfelelőek 7 © 2010 IBM Corporation

IBM Tivoli Security Portfolió IBM-ISS X-Force Biztonsági Kutatás és Fejlesztés § Több mint 250 dedikált biztonsági mérnök § Élvonalbeli kutatói program § Lehetséges és észlelt fenyegetések publikálása a médiában § Fenyegetések korai felismerése § Folyamatos X-Press információk a Proventia technológiához 8 © 2010 IBM Corporation
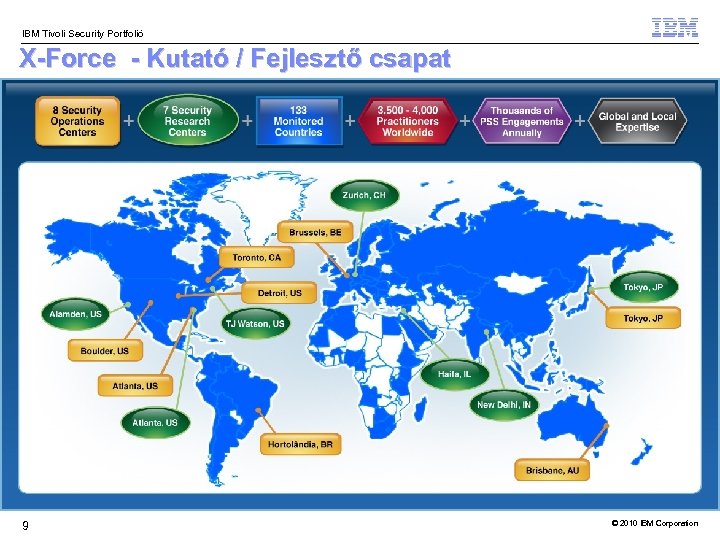
IBM Tivoli Security Portfolió X-Force - Kutató / Fejlesztő csapat 9 © 2010 IBM Corporation
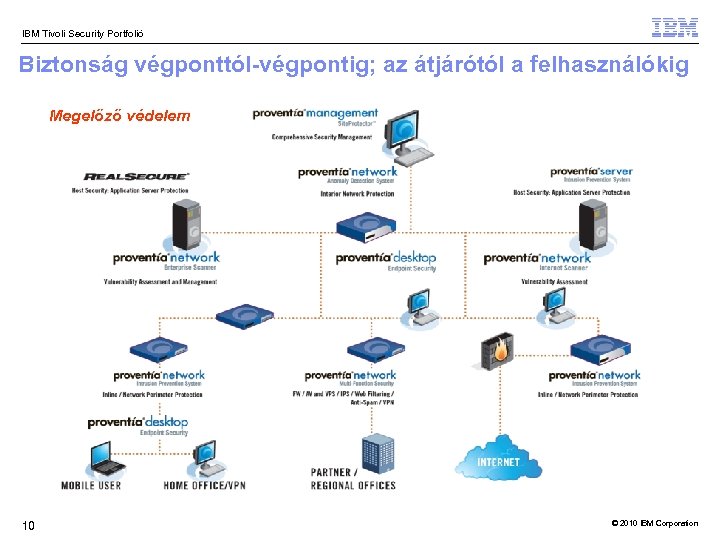
IBM Tivoli Security Portfolió Biztonság végponttól-végpontig; az átjárótól a felhasználókig Megelőző védelem 10 © 2010 IBM Corporation
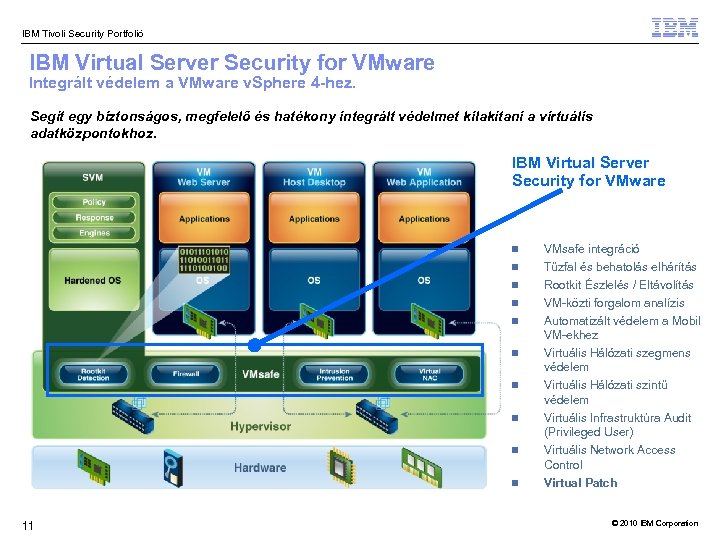
IBM Tivoli Security Portfolió IBM Virtual Server Security for VMware Integrált védelem a VMware v. Sphere 4 -hez. Segít egy biztonságos, megfelelő és hatékony integrált védelmet kilakítani a virtuális adatközpontokhoz. IBM Virtual Server Security for VMware VMsafe integráció Tűzfal és behatolás elhárítás Rootkit Észlelés / Eltávolítás VM-közti forgalom analízis Automatizált védelem a Mobil VM-ekhez Virtuális Hálózati szegmens védelem Virtuális Infrastruktúra Audit (Privileged User) Virtuális Network Access Control 11 Virtuális Hálózati szintű védelem Virtual Patch © 2010 IBM Corporation

IBM Tivoli Security Portfolió Köszönöm a figyelmet 12 © 2010 IBM Corporation
IBM Tivoli Security Portfolió Trademarks and notes IBM Corporation 2009 § IBM, the IBM logo, ibm. com, AIX, IBM Internet Security Systems, Proventia, Real Secure, Site. Protector, X-Force and Virtual Patch are trademarks or registered trademarks of International Business Machines Corporation in the United States, other countries, or both. If these and other IBM trademarked terms are marked on their first occurrence in this information with the appropriate symbol (® or ™), these symbols indicate US registered or common law trademarks owned by IBM at the time this information was published. Such trademarks may also be registered or common law trademarks in other countries. A current list of IBM trademarks is available on the Web at “Copyright and trademark information” at www. ibm. com/legal/copytrade. shtml § VMware, the VMware "boxes" logo and design, Virtual SMP and VMotion are registered trademarks or trademarks (the "Marks") of VMware, Inc. in the United States and/or other jurisdictions. § References in this publication to IBM products or services do not imply that IBM intends to make them available in all countries in which IBM operates. § The customer is responsible for ensuring compliance with legal requirements. It is the customer’s sole responsibility to obtain advice of competent legal counsel as to the identification and interpretation of any relevant laws and regulatory requirements that may affect the customer’s business and any actions the reader may have to take to comply with such laws. IBM does not provide legal advice or represent or warrant that its services or products will ensure that the customer is in compliance with any law or regulation. 13 © 2010 IBM Corporation
8da84da85655b7a50c43975a35354742.ppt