c5857831a6a91cf627447c44e16954fc.ppt
- Количество слайдов: 19
 2 G/3 G Authentication with SIM cards: usage & roaming basics for the Internet challenged Michael Haberler Internet Foundation Austria
2 G/3 G Authentication with SIM cards: usage & roaming basics for the Internet challenged Michael Haberler Internet Foundation Austria
 outline • a SIM card mini-tutorial • features, protocol flow, usage, production, addressing • UMTS authentication and key agreement • principles and protocol flow • the universal integrated circuit card (UICC) • USIM app • how 2 G, 3 G roaming works • „over the air“ (OTA) loading of UICC apps • example: X. 509 certificate download • (U)SIM‘s and Internet access authentication – how SIMs and RADIUS roaming works • (U)SIM‘s and SIP authentication – what the SIP server does • How the parameter logistics works • a bonus business model thrown in • summary
outline • a SIM card mini-tutorial • features, protocol flow, usage, production, addressing • UMTS authentication and key agreement • principles and protocol flow • the universal integrated circuit card (UICC) • USIM app • how 2 G, 3 G roaming works • „over the air“ (OTA) loading of UICC apps • example: X. 509 certificate download • (U)SIM‘s and Internet access authentication – how SIMs and RADIUS roaming works • (U)SIM‘s and SIP authentication – what the SIP server does • How the parameter logistics works • a bonus business model thrown in • summary
 what‘s a 2 G SIM card • crypto smart card as per ISO 7816 • access protected by a PIN code(s) („card holder verification“) • fixed storage of subscriber identity – IMSI (international mobile subscriber identity) – „GSM MAC address“ – E. 164 number to IMSI mapping at the operator only • safe storage for shared secret - accessible only through CHAP operation – not broken as of today except for most stupid CHAP algorithm known • CHAP algorithm in hardware – operator chooses algorithm • tree structured filesystem – stream, record, cyclic record files – can be readonly, read/write or none at all (for the key) – some permission hierarchy
what‘s a 2 G SIM card • crypto smart card as per ISO 7816 • access protected by a PIN code(s) („card holder verification“) • fixed storage of subscriber identity – IMSI (international mobile subscriber identity) – „GSM MAC address“ – E. 164 number to IMSI mapping at the operator only • safe storage for shared secret - accessible only through CHAP operation – not broken as of today except for most stupid CHAP algorithm known • CHAP algorithm in hardware – operator chooses algorithm • tree structured filesystem – stream, record, cyclic record files – can be readonly, read/write or none at all (for the key) – some permission hierarchy
 how are SIM cards produced • unprogrammed chips are „personalized“ and „closed“ (parameters written & sealed) • mass product - $5 -$7 apiece at 1000+ – GEMplus, Giesecke & Devrient. . • everybody can have SIM‘s made – even Mom&Pop ISP • not everybody may – roam with other cellular operators – use the GSM algorithm „A 3/A 8“ – you wouldnt want it anyway – must be member of GSM association for that • having your own algorithm in a chip mask is a circa $50 K+ affair • for testing & development unprogrammed castrated chips used (XOR algorithm for CHAP. . . )
how are SIM cards produced • unprogrammed chips are „personalized“ and „closed“ (parameters written & sealed) • mass product - $5 -$7 apiece at 1000+ – GEMplus, Giesecke & Devrient. . • everybody can have SIM‘s made – even Mom&Pop ISP • not everybody may – roam with other cellular operators – use the GSM algorithm „A 3/A 8“ – you wouldnt want it anyway – must be member of GSM association for that • having your own algorithm in a chip mask is a circa $50 K+ affair • for testing & development unprogrammed castrated chips used (XOR algorithm for CHAP. . . )
 how are (U)SIM cards accessed • 2 G, 3 G use – builtin reader in the mobile handset • for Internet use: – maybe builtin in PDA, PC (e. g. DELL) – external USB token – 20$ apiece – re-use a mobile SIM card via Bluetooth SIG SIM Access Profile (only if roaming against 2 G/3 G operator) • read 3 G „(U)SIM Security Reuse by Peripheral Decices on local interfaces“ – contains some threat analysis
how are (U)SIM cards accessed • 2 G, 3 G use – builtin reader in the mobile handset • for Internet use: – maybe builtin in PDA, PC (e. g. DELL) – external USB token – 20$ apiece – re-use a mobile SIM card via Bluetooth SIG SIM Access Profile (only if roaming against 2 G/3 G operator) • read 3 G „(U)SIM Security Reuse by Peripheral Decices on local interfaces“ – contains some threat analysis
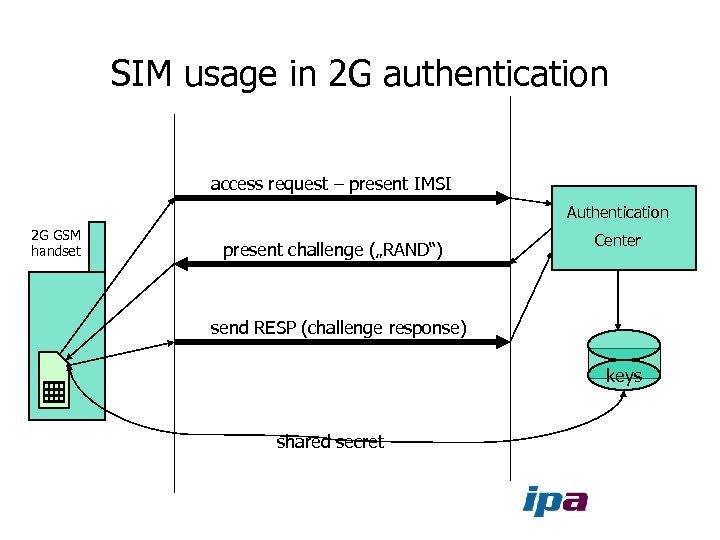 SIM usage in 2 G authentication access request – present IMSI Authentication 2 G GSM handset present challenge („RAND“) Center send RESP (challenge response) keys shared secret
SIM usage in 2 G authentication access request – present IMSI Authentication 2 G GSM handset present challenge („RAND“) Center send RESP (challenge response) keys shared secret
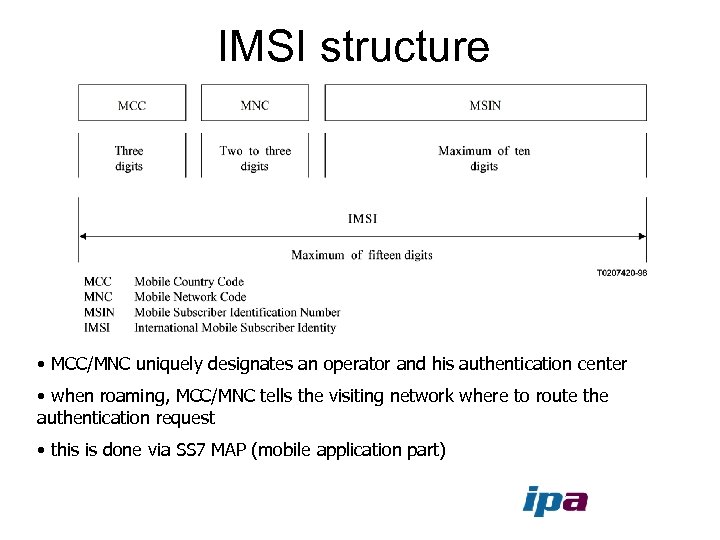 IMSI structure • MCC/MNC uniquely designates an operator and his authentication center • when roaming, MCC/MNC tells the visiting network where to route the authentication request • this is done via SS 7 MAP (mobile application part)
IMSI structure • MCC/MNC uniquely designates an operator and his authentication center • when roaming, MCC/MNC tells the visiting network where to route the authentication request • this is done via SS 7 MAP (mobile application part)
 what is „OTA“ (over the air) loading? • SIM cards are writable by mobile equipment – if authenticated to network – if instructed by operator „over the air“ – if file/directory is writable • example: ISIM X. 509 certificate „bootstrap“ – AKA authenticated: • let user visit PKI portal • download certificates through HTTP/Digest mechanism • certificates are stored in record structured files, as ar CA certifcates • „The Air“ can also be an IP connection • download of executable applets possible – SIM Toolkit, USAT (USIM Application toolkit) – bytecode instructions sent encrypted by 3 DES, stored on card • regularly used in 2 G networks today – for functionality upgrades & parameter download
what is „OTA“ (over the air) loading? • SIM cards are writable by mobile equipment – if authenticated to network – if instructed by operator „over the air“ – if file/directory is writable • example: ISIM X. 509 certificate „bootstrap“ – AKA authenticated: • let user visit PKI portal • download certificates through HTTP/Digest mechanism • certificates are stored in record structured files, as ar CA certifcates • „The Air“ can also be an IP connection • download of executable applets possible – SIM Toolkit, USAT (USIM Application toolkit) – bytecode instructions sent encrypted by 3 DES, stored on card • regularly used in 2 G networks today – for functionality upgrades & parameter download
 UMTS authentication and key agreement (AKA) • • • substantially improved over 2 G SIM protection against replay, MITM attacks sports also network-to-user authentication more complex algorithm compatibility functions 2 G network/3 G card, 3 G network/2 G card
UMTS authentication and key agreement (AKA) • • • substantially improved over 2 G SIM protection against replay, MITM attacks sports also network-to-user authentication more complex algorithm compatibility functions 2 G network/3 G card, 3 G network/2 G card
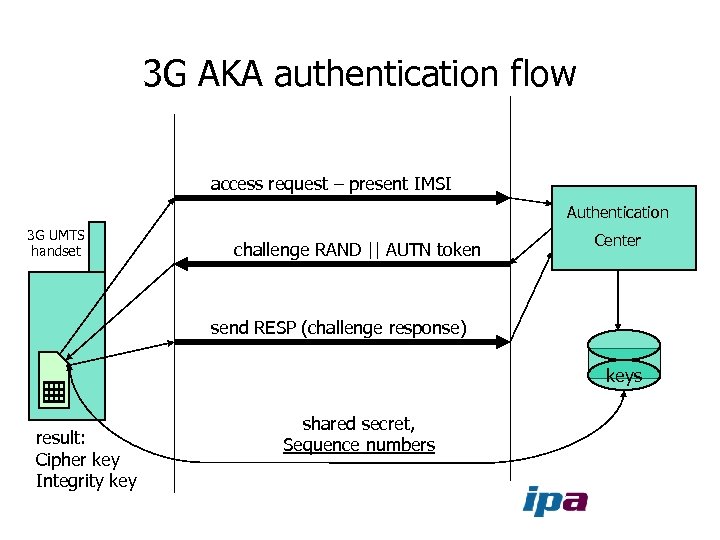 3 G AKA authentication flow access request – present IMSI Authentication 3 G UMTS handset challenge RAND || AUTN token Center send RESP (challenge response) keys result: Cipher key Integrity key shared secret, Sequence numbers
3 G AKA authentication flow access request – present IMSI Authentication 3 G UMTS handset challenge RAND || AUTN token Center send RESP (challenge response) keys result: Cipher key Integrity key shared secret, Sequence numbers
 what‘s the universal integrated circuit card (UICC) about • generic support mechanism for multiple applications on one card • 2 G, 3 G authentication become „applications“ selected as needed – USIM application implements AKA – 2 G SIM app implements 2 G CHAP – additional apps possible (ISIM, PKI certificate storage etc) – ISIM is pretty close to SIP client needs!! • mobile equipment chooses application
what‘s the universal integrated circuit card (UICC) about • generic support mechanism for multiple applications on one card • 2 G, 3 G authentication become „applications“ selected as needed – USIM application implements AKA – 2 G SIM app implements 2 G CHAP – additional apps possible (ISIM, PKI certificate storage etc) – ISIM is pretty close to SIP client needs!! • mobile equipment chooses application
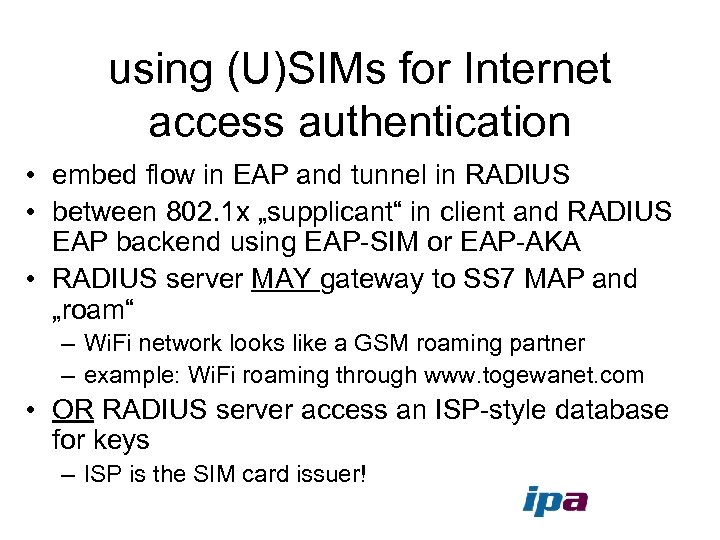 using (U)SIMs for Internet access authentication • embed flow in EAP and tunnel in RADIUS • between 802. 1 x „supplicant“ in client and RADIUS EAP backend using EAP-SIM or EAP-AKA • RADIUS server MAY gateway to SS 7 MAP and „roam“ – Wi. Fi network looks like a GSM roaming partner – example: Wi. Fi roaming through www. togewanet. com • OR RADIUS server access an ISP-style database for keys – ISP is the SIM card issuer!
using (U)SIMs for Internet access authentication • embed flow in EAP and tunnel in RADIUS • between 802. 1 x „supplicant“ in client and RADIUS EAP backend using EAP-SIM or EAP-AKA • RADIUS server MAY gateway to SS 7 MAP and „roam“ – Wi. Fi network looks like a GSM roaming partner – example: Wi. Fi roaming through www. togewanet. com • OR RADIUS server access an ISP-style database for keys – ISP is the SIM card issuer!
 using (U)SIM for SIP authentication • • • speak HTTP/AKA (RFC 3310) between SIP UA and proxy translates into EAP-AKA-in-RADIUS RFC specified only for AKA (3 G auth) no mapping of EAP-SIM onto HTTP/SIM for 2 G auth bad – almost all networks today use 2 G auth – which breaks SIP authentication through GSM/UMTS operators • we need to address this and spec HTTP/SIM
using (U)SIM for SIP authentication • • • speak HTTP/AKA (RFC 3310) between SIP UA and proxy translates into EAP-AKA-in-RADIUS RFC specified only for AKA (3 G auth) no mapping of EAP-SIM onto HTTP/SIM for 2 G auth bad – almost all networks today use 2 G auth – which breaks SIP authentication through GSM/UMTS operators • we need to address this and spec HTTP/SIM
 how 2 G roaming works • mobile equipment presents IMSI • visited network looks at MCC, MNC part of IMSI – if no roaming agreement, drop him – otherwise send access request thru SS 7 MAP to home network – the home network verifies IMSI and sends a „triplet“: (challenge, expected response, cipher key) authentication vector – visited network presents challenge, reads response – if (response == expected response), service user • the triplet is essentially an access ticket – note no replay detection – these fellows seem to trust each other
how 2 G roaming works • mobile equipment presents IMSI • visited network looks at MCC, MNC part of IMSI – if no roaming agreement, drop him – otherwise send access request thru SS 7 MAP to home network – the home network verifies IMSI and sends a „triplet“: (challenge, expected response, cipher key) authentication vector – visited network presents challenge, reads response – if (response == expected response), service user • the triplet is essentially an access ticket – note no replay detection – these fellows seem to trust each other
 how 3 G roaming works • not much different from 3 G, just more parameters needed for AKA • „triplets“ become „quintets“
how 3 G roaming works • not much different from 3 G, just more parameters needed for AKA • „triplets“ become „quintets“
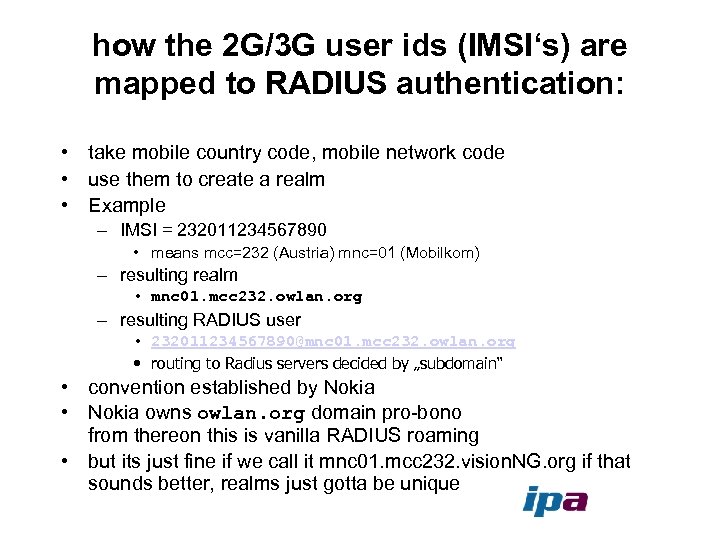 how the 2 G/3 G user ids (IMSI‘s) are mapped to RADIUS authentication: • take mobile country code, mobile network code • use them to create a realm • Example – IMSI = 232011234567890 • means mcc=232 (Austria) mnc=01 (Mobilkom) – resulting realm • mnc 01. mcc 232. owlan. org – resulting RADIUS user • 232011234567890@mnc 01. mcc 232. owlan. org • routing to Radius servers decided by „subdomain“ • convention established by Nokia • Nokia owns owlan. org domain pro-bono from thereon this is vanilla RADIUS roaming • but its just fine if we call it mnc 01. mcc 232. vision. NG. org if that sounds better, realms just gotta be unique
how the 2 G/3 G user ids (IMSI‘s) are mapped to RADIUS authentication: • take mobile country code, mobile network code • use them to create a realm • Example – IMSI = 232011234567890 • means mcc=232 (Austria) mnc=01 (Mobilkom) – resulting realm • mnc 01. mcc 232. owlan. org – resulting RADIUS user • 232011234567890@mnc 01. mcc 232. owlan. org • routing to Radius servers decided by „subdomain“ • convention established by Nokia • Nokia owns owlan. org domain pro-bono from thereon this is vanilla RADIUS roaming • but its just fine if we call it mnc 01. mcc 232. vision. NG. org if that sounds better, realms just gotta be unique
 how does 2 G/3 G address logistics work • if you are a service provider and have E. 164 ranges, get a MNC from your MCC administrator (FCC, regulator. . . ) • the E. 164 range might also be, for example, from vision. NG (+87810 ff) MCC = 901 • this doesnt mean you‘re part of 2 G/3 G roaming yet – contracts & regulatory prerequisites needed • but the addressing is all set to go!!
how does 2 G/3 G address logistics work • if you are a service provider and have E. 164 ranges, get a MNC from your MCC administrator (FCC, regulator. . . ) • the E. 164 range might also be, for example, from vision. NG (+87810 ff) MCC = 901 • this doesnt mean you‘re part of 2 G/3 G roaming yet – contracts & regulatory prerequisites needed • but the addressing is all set to go!!
 a bonus business model thrown in: • combine a SIP-based i. TSP with a Mobile Virtual Network Operator (MVNO) – an MVNO has authentication, billing, customers, numbers, but the radio network is outsourced from somewhere else • issue (U)SIM cards which work both in a 2/3 G handset AND as Wi. Fi/SIP auth tokens – note the same card authenticates both uses! • leave choice to user how to connect – Internet or cellular – using the same E. 164 number
a bonus business model thrown in: • combine a SIP-based i. TSP with a Mobile Virtual Network Operator (MVNO) – an MVNO has authentication, billing, customers, numbers, but the radio network is outsourced from somewhere else • issue (U)SIM cards which work both in a 2/3 G handset AND as Wi. Fi/SIP auth tokens – note the same card authenticates both uses! • leave choice to user how to connect – Internet or cellular – using the same E. 164 number
 Summary • 2 G/3 G has a strong/very strong authentication architecture • it is almost copy & paste for i. TSP use at Wi. Fi access, Wi. Fi roaming acces, SIP and other levels (TBD!) • it can serve to solve the X. 509 certificate distribution problem • operator model (2 G/3 G home network, ISP home network) has no impact on Internet-side terminals • numbering & addressing resources are compatible and available (maybe not obviously so) • the Internet could become the biggest (U)SIM authenticated mobile network ever to roam with 2 G/3 G land
Summary • 2 G/3 G has a strong/very strong authentication architecture • it is almost copy & paste for i. TSP use at Wi. Fi access, Wi. Fi roaming acces, SIP and other levels (TBD!) • it can serve to solve the X. 509 certificate distribution problem • operator model (2 G/3 G home network, ISP home network) has no impact on Internet-side terminals • numbering & addressing resources are compatible and available (maybe not obviously so) • the Internet could become the biggest (U)SIM authenticated mobile network ever to roam with 2 G/3 G land


