c5a6d6e20e3c352b688d583299ca47be.ppt
- Количество слайдов: 47
 2. Conventional networks 2. 4 GSM Prof. JP Hubaux 1
2. Conventional networks 2. 4 GSM Prof. JP Hubaux 1
 GSM: Global System for Mobile communications g Objectives g Principles i. Unique standard for European digital cellular networks i. International roaming i. Signal quality i. Voice and data services i. Standardization of the air and the network interfaces i. Security i. Strong integration with the telephone network (PSTN) i. Interfaces inspired by the Integrated Services Digital Network (ISDN) i. Hence, supervision by means of Signaling System 7 (SS 7) 2
GSM: Global System for Mobile communications g Objectives g Principles i. Unique standard for European digital cellular networks i. International roaming i. Signal quality i. Voice and data services i. Standardization of the air and the network interfaces i. Security i. Strong integration with the telephone network (PSTN) i. Interfaces inspired by the Integrated Services Digital Network (ISDN) i. Hence, supervision by means of Signaling System 7 (SS 7) 2
 Signaling System Number 7 l l l Enhanced services requested by users require bidirectional signaling capabilities, flexibility of call setup and remote database access With SS 7, a signaling channel conveys, by means of labeled messages, signaling information relating to call processing and to network management SS 7 is the most important signaling system in the world: it supervises the PSTN, the cellular networks (GSM), and the Intelligent Network 3
Signaling System Number 7 l l l Enhanced services requested by users require bidirectional signaling capabilities, flexibility of call setup and remote database access With SS 7, a signaling channel conveys, by means of labeled messages, signaling information relating to call processing and to network management SS 7 is the most important signaling system in the world: it supervises the PSTN, the cellular networks (GSM), and the Intelligent Network 3
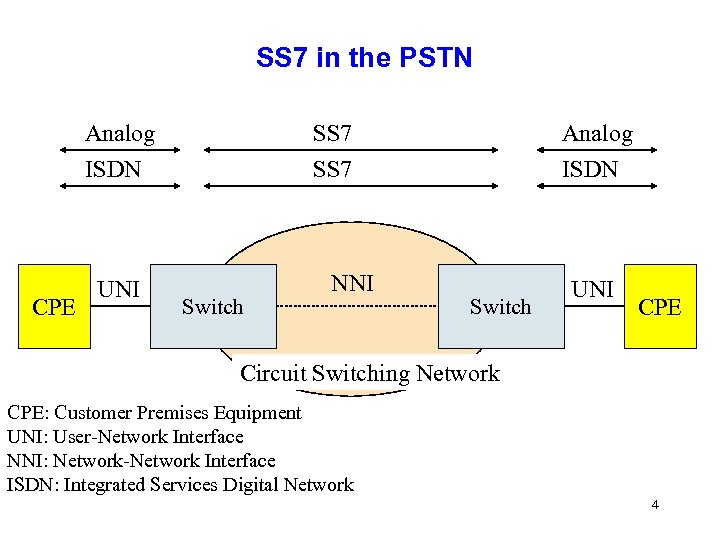 SS 7 in the PSTN Analog ISDN CPE SS 7 ISDN UNI Switch NNI Switch UNI CPE Circuit Switching Network CPE: Customer Premises Equipment UNI: User-Network Interface NNI: Network-Network Interface ISDN: Integrated Services Digital Network 4
SS 7 in the PSTN Analog ISDN CPE SS 7 ISDN UNI Switch NNI Switch UNI CPE Circuit Switching Network CPE: Customer Premises Equipment UNI: User-Network Interface NNI: Network-Network Interface ISDN: Integrated Services Digital Network 4
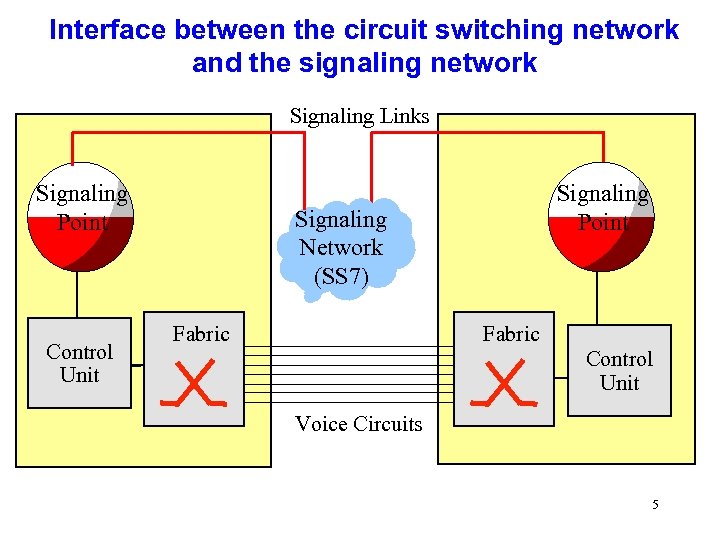 Interface between the circuit switching network and the signaling network Signaling Links Signaling Point Control Unit Signaling Point Signaling Network (SS 7) Fabric Control Unit Voice Circuits 5
Interface between the circuit switching network and the signaling network Signaling Links Signaling Point Control Unit Signaling Point Signaling Network (SS 7) Fabric Control Unit Voice Circuits 5
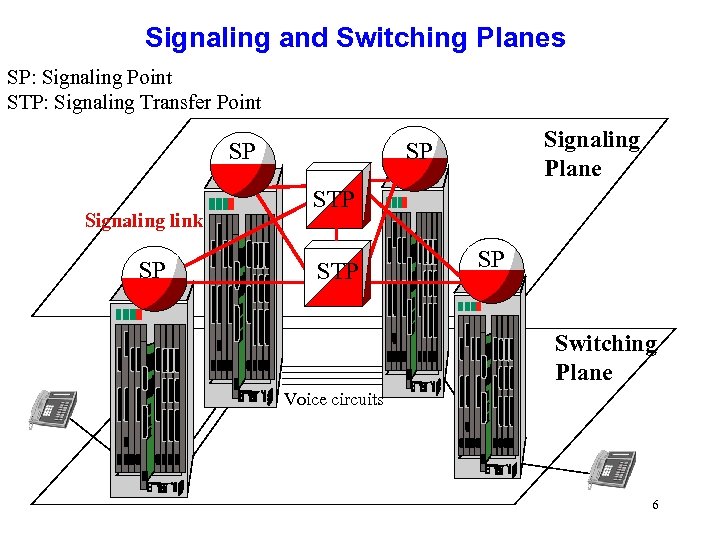 Signaling and Switching Planes SP: Signaling Point STP: Signaling Transfer Point SP Signaling link SP Signaling Plane SP STP SP Switching Plane Voice circuits 6
Signaling and Switching Planes SP: Signaling Point STP: Signaling Transfer Point SP Signaling link SP Signaling Plane SP STP SP Switching Plane Voice circuits 6
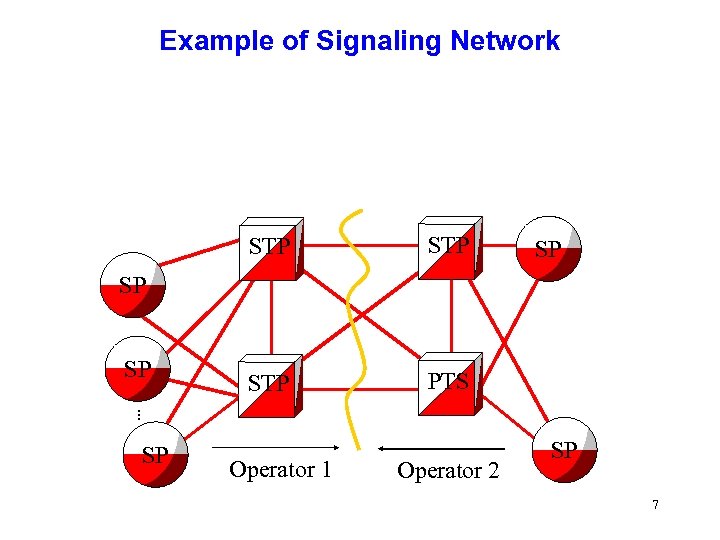 Example of Signaling Network STP STP PTS SP SP SP. . . SP Operator 1 Operator 2 SP 7
Example of Signaling Network STP STP PTS SP SP SP. . . SP Operator 1 Operator 2 SP 7
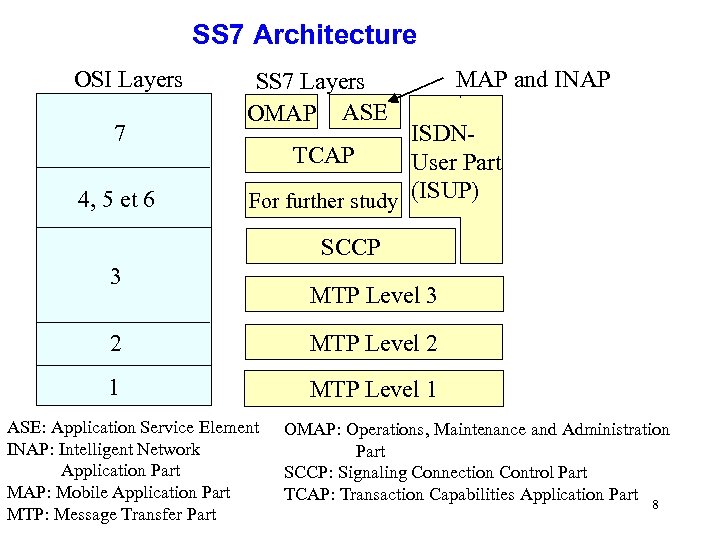 SS 7 Architecture OSI Layers 7 4, 5 et 6 SS 7 Layers OMAP ASE MAP and INAP ISDNTCAP User Part For further study (ISUP) SCCP 3 MTP Level 3 2 MTP Level 2 1 MTP Level 1 ASE: Application Service Element INAP: Intelligent Network Application Part MAP: Mobile Application Part MTP: Message Transfer Part OMAP: Operations, Maintenance and Administration Part SCCP: Signaling Connection Control Part TCAP: Transaction Capabilities Application Part 8
SS 7 Architecture OSI Layers 7 4, 5 et 6 SS 7 Layers OMAP ASE MAP and INAP ISDNTCAP User Part For further study (ISUP) SCCP 3 MTP Level 3 2 MTP Level 2 1 MTP Level 1 ASE: Application Service Element INAP: Intelligent Network Application Part MAP: Mobile Application Part MTP: Message Transfer Part OMAP: Operations, Maintenance and Administration Part SCCP: Signaling Connection Control Part TCAP: Transaction Capabilities Application Part 8
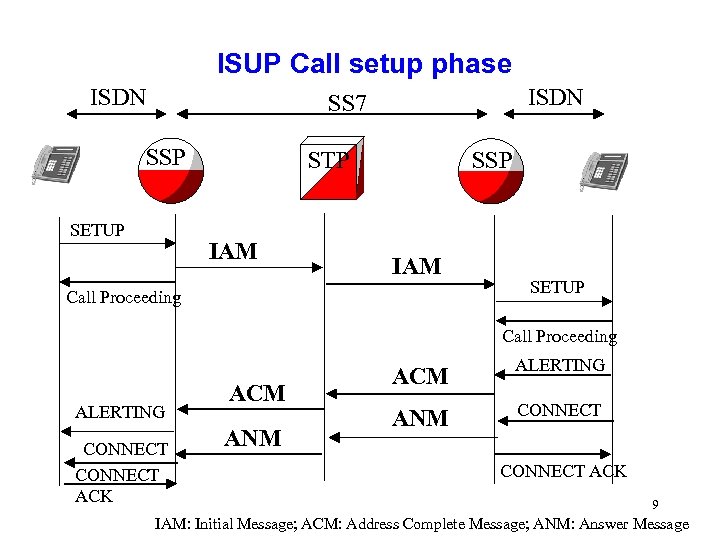 ISUP Call setup phase ISDN SS 7 SSP SETUP SSP STP IAM Call Proceeding SETUP Call Proceeding ALERTING CONNECT ACK ACM ANM ACM ALERTING ANM CONNECT ACK 9 IAM: Initial Message; ACM: Address Complete Message; ANM: Answer Message
ISUP Call setup phase ISDN SS 7 SSP SETUP SSP STP IAM Call Proceeding SETUP Call Proceeding ALERTING CONNECT ACK ACM ANM ACM ALERTING ANM CONNECT ACK 9 IAM: Initial Message; ACM: Address Complete Message; ANM: Answer Message
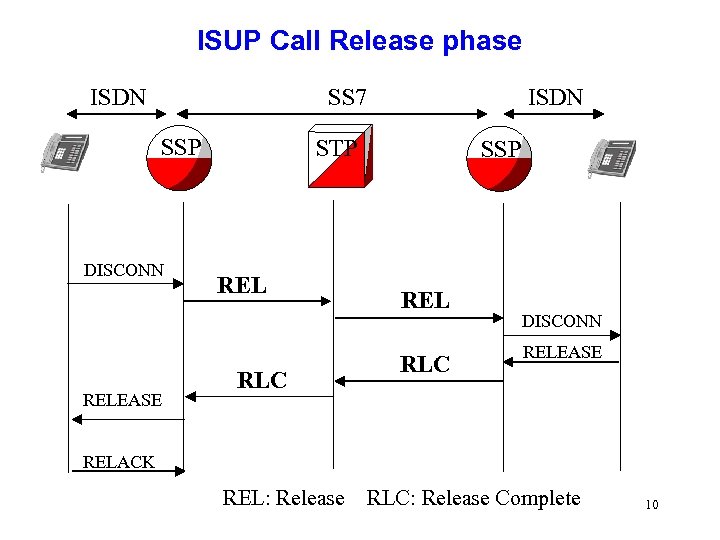 ISUP Call Release phase ISDN SS 7 SSP DISCONN RELEASE ISDN STP REL RLC SSP REL RLC DISCONN RELEASE RELACK REL: Release RLC: Release Complete 10
ISUP Call Release phase ISDN SS 7 SSP DISCONN RELEASE ISDN STP REL RLC SSP REL RLC DISCONN RELEASE RELACK REL: Release RLC: Release Complete 10
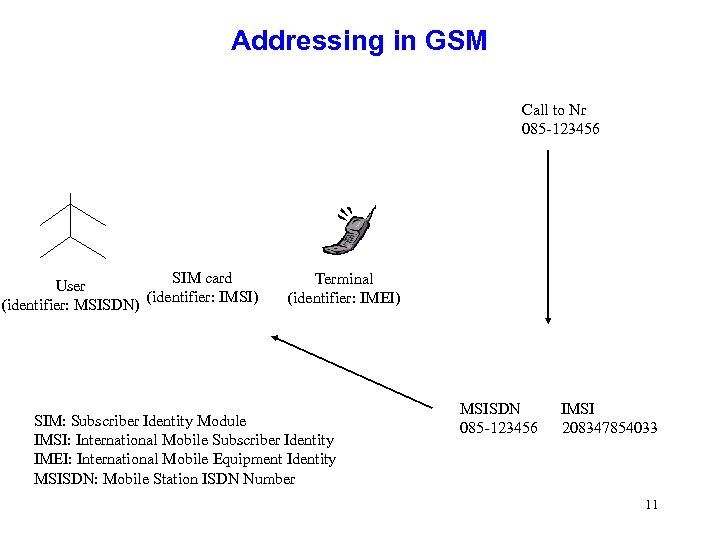 Addressing in GSM Call to Nr 085 -123456 SIM card User (identifier: IMSI) (identifier: MSISDN) Terminal (identifier: IMEI) SIM: Subscriber Identity Module IMSI: International Mobile Subscriber Identity IMEI: International Mobile Equipment Identity MSISDN: Mobile Station ISDN Number MSISDN IMSI 085 -123456 208347854033 11
Addressing in GSM Call to Nr 085 -123456 SIM card User (identifier: IMSI) (identifier: MSISDN) Terminal (identifier: IMEI) SIM: Subscriber Identity Module IMSI: International Mobile Subscriber Identity IMEI: International Mobile Equipment Identity MSISDN: Mobile Station ISDN Number MSISDN IMSI 085 -123456 208347854033 11
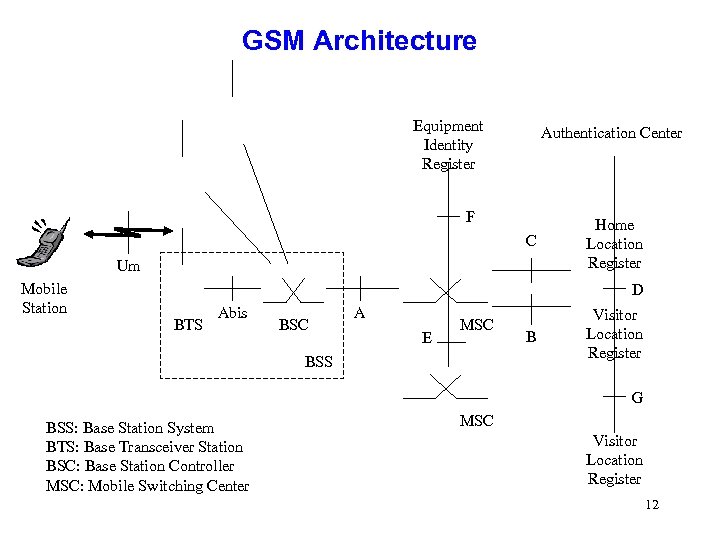 GSM Architecture Equipment Identity Register Authentication Center F C Um Mobile Station Home Location Register D BTS Abis BSC A E MSC BSS B Visitor Location Register G BSS: Base Station System BTS: Base Transceiver Station BSC: Base Station Controller MSC: Mobile Switching Center MSC Visitor Location Register 12
GSM Architecture Equipment Identity Register Authentication Center F C Um Mobile Station Home Location Register D BTS Abis BSC A E MSC BSS B Visitor Location Register G BSS: Base Station System BTS: Base Transceiver Station BSC: Base Station Controller MSC: Mobile Switching Center MSC Visitor Location Register 12
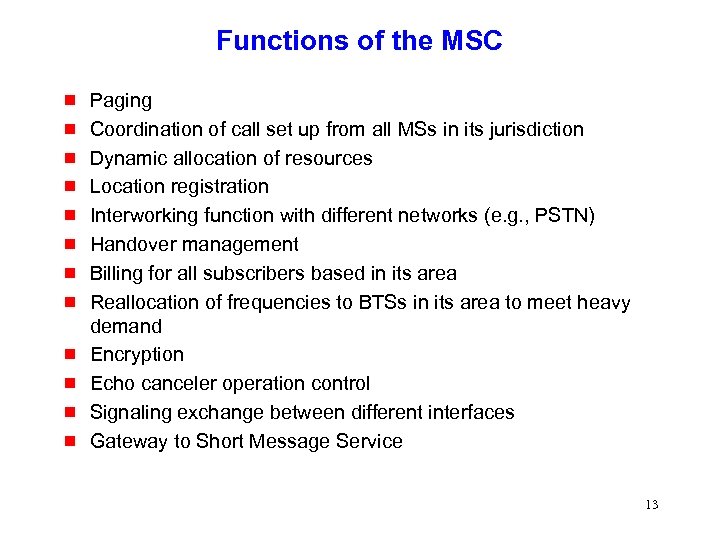 Functions of the MSC g g g Paging Coordination of call set up from all MSs in its jurisdiction Dynamic allocation of resources Location registration Interworking function with different networks (e. g. , PSTN) Handover management Billing for all subscribers based in its area Reallocation of frequencies to BTSs in its area to meet heavy demand Encryption Echo canceler operation control Signaling exchange between different interfaces Gateway to Short Message Service 13
Functions of the MSC g g g Paging Coordination of call set up from all MSs in its jurisdiction Dynamic allocation of resources Location registration Interworking function with different networks (e. g. , PSTN) Handover management Billing for all subscribers based in its area Reallocation of frequencies to BTSs in its area to meet heavy demand Encryption Echo canceler operation control Signaling exchange between different interfaces Gateway to Short Message Service 13
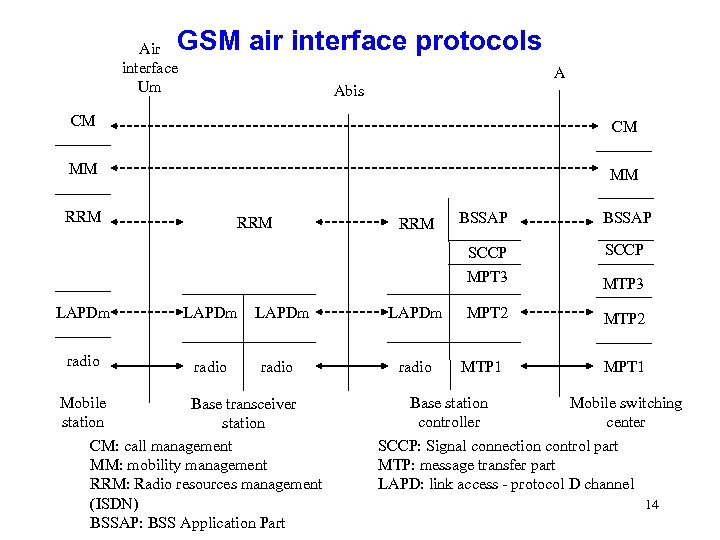 GSM air interface protocols Air interface Um A Abis CM CM MM MM RRM LAPDm radio Mobile Base transceiver station CM: call management MM: mobility management RRM: Radio resources management (ISDN) BSSAP: BSS Application Part RRM LAPDm radio BSSAP SCCP MPT 3 RRM SCCP MTP 3 MPT 2 MTP 1 MPT 1 Base station Mobile switching controller center SCCP: Signal connection control part MTP: message transfer part LAPD: link access - protocol D channel 14
GSM air interface protocols Air interface Um A Abis CM CM MM MM RRM LAPDm radio Mobile Base transceiver station CM: call management MM: mobility management RRM: Radio resources management (ISDN) BSSAP: BSS Application Part RRM LAPDm radio BSSAP SCCP MPT 3 RRM SCCP MTP 3 MPT 2 MTP 1 MPT 1 Base station Mobile switching controller center SCCP: Signal connection control part MTP: message transfer part LAPD: link access - protocol D channel 14
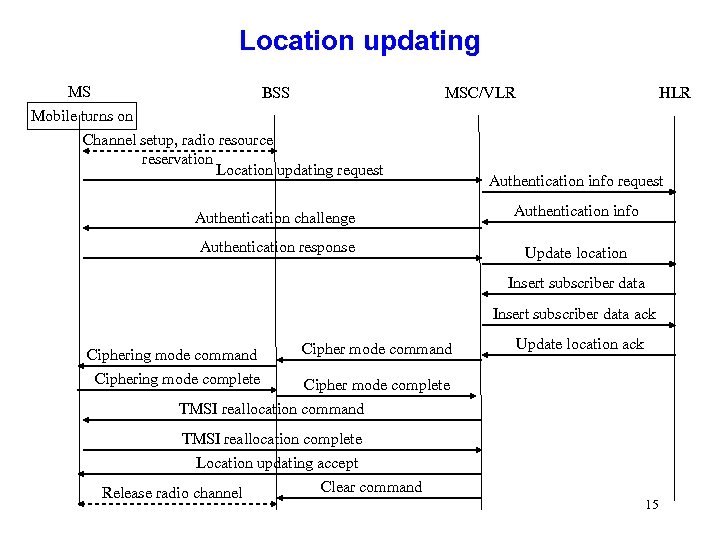 Location updating MS Mobile turns on BSS MSC/VLR Channel setup, radio resource reservation Location updating request HLR Authentication info request Authentication challenge Authentication info Authentication response Update location Insert subscriber data ack Ciphering mode command Ciphering mode complete Cipher mode command Update location ack Cipher mode complete TMSI reallocation command TMSI reallocation complete Location updating accept Clear command Release radio channel 15
Location updating MS Mobile turns on BSS MSC/VLR Channel setup, radio resource reservation Location updating request HLR Authentication info request Authentication challenge Authentication info Authentication response Update location Insert subscriber data ack Ciphering mode command Ciphering mode complete Cipher mode command Update location ack Cipher mode complete TMSI reallocation command TMSI reallocation complete Location updating accept Clear command Release radio channel 15
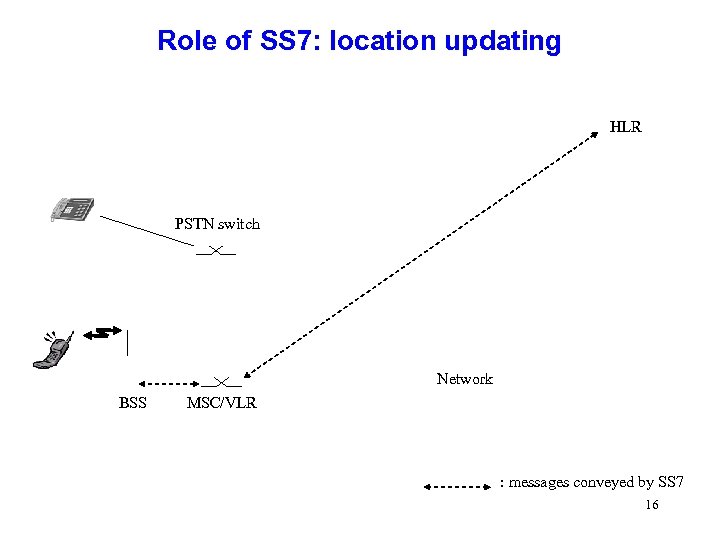 Role of SS 7: location updating HLR PSTN switch Network BSS MSC/VLR : messages conveyed by SS 7 16
Role of SS 7: location updating HLR PSTN switch Network BSS MSC/VLR : messages conveyed by SS 7 16
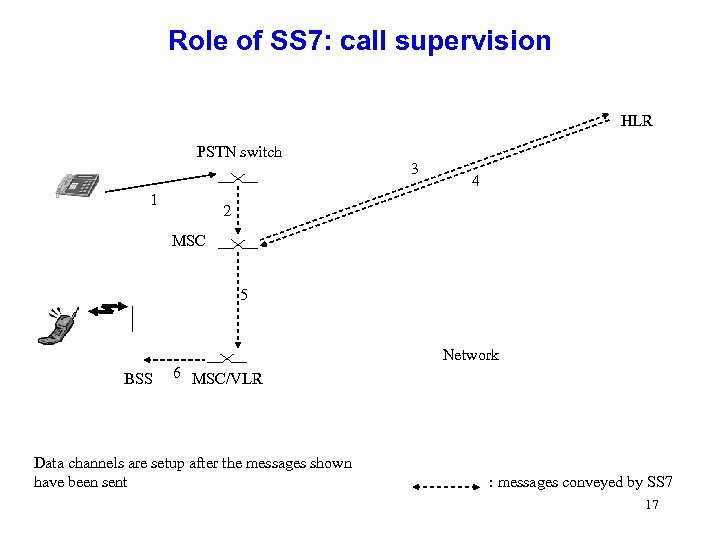 Role of SS 7: call supervision HLR PSTN switch 1 3 4 2 MSC 5 Network BSS 6 MSC/VLR Data channels are setup after the messages shown have been sent : messages conveyed by SS 7 17
Role of SS 7: call supervision HLR PSTN switch 1 3 4 2 MSC 5 Network BSS 6 MSC/VLR Data channels are setup after the messages shown have been sent : messages conveyed by SS 7 17
 Billing Principles in GSM g g Basic principle: the calling party pays Exception: the calling party does not pay for extra charges induced by initiatives of the callee: iroaming icall forwarding 18
Billing Principles in GSM g g Basic principle: the calling party pays Exception: the calling party does not pay for extra charges induced by initiatives of the callee: iroaming icall forwarding 18
 Data services of GSM g Short Message Service (SMS) g General Packet Radio Service (GPRS) g High Speed Circuit-Switched Data (HSCSD) i. Similar to advanced paging systems i. Makes use of the control channel i. Aimed at interfacing the Internet (e. g. , for Web browsing) i. Rates up to 170 kb/s 19
Data services of GSM g Short Message Service (SMS) g General Packet Radio Service (GPRS) g High Speed Circuit-Switched Data (HSCSD) i. Similar to advanced paging systems i. Makes use of the control channel i. Aimed at interfacing the Internet (e. g. , for Web browsing) i. Rates up to 170 kb/s 19
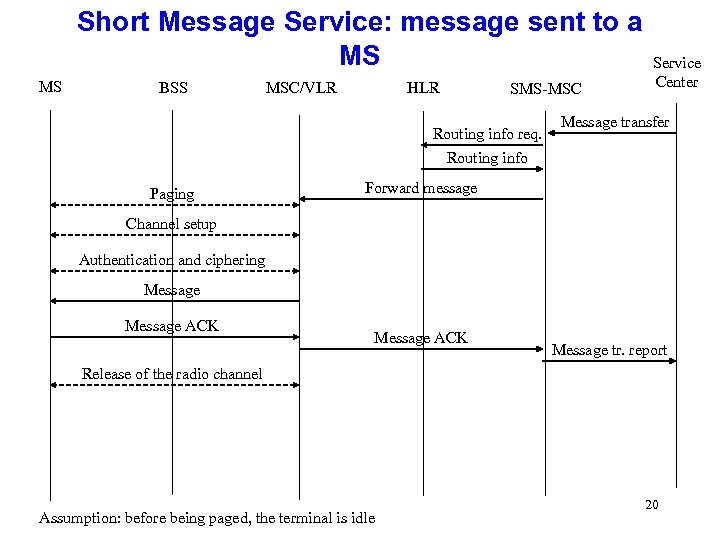 Short Message Service: message sent to a MS MS BSS MSC/VLR HLR SMS-MSC Routing info req. Service Center Message transfer Routing info Paging Forward message Channel setup Authentication and ciphering Message ACK Message tr. report Release of the radio channel Assumption: before being paged, the terminal is idle 20
Short Message Service: message sent to a MS MS BSS MSC/VLR HLR SMS-MSC Routing info req. Service Center Message transfer Routing info Paging Forward message Channel setup Authentication and ciphering Message ACK Message tr. report Release of the radio channel Assumption: before being paged, the terminal is idle 20
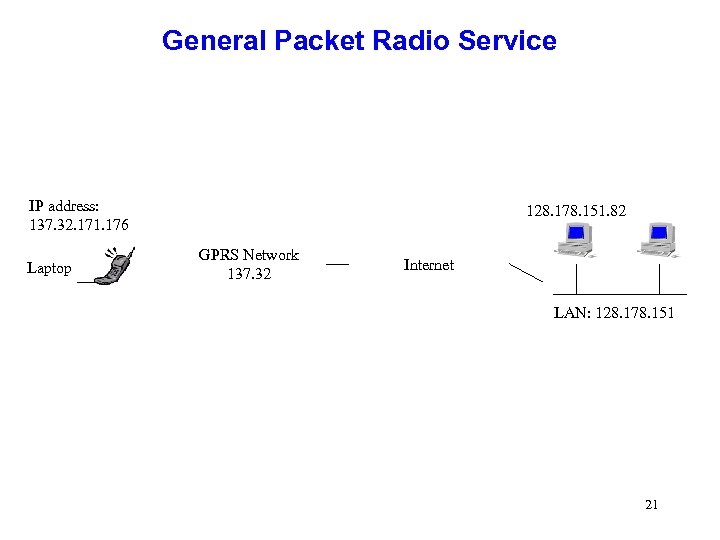 General Packet Radio Service IP address: 137. 32. 171. 176 Laptop 128. 178. 151. 82 GPRS Network 137. 32 Internet LAN: 128. 178. 151 21
General Packet Radio Service IP address: 137. 32. 171. 176 Laptop 128. 178. 151. 82 GPRS Network 137. 32 Internet LAN: 128. 178. 151 21
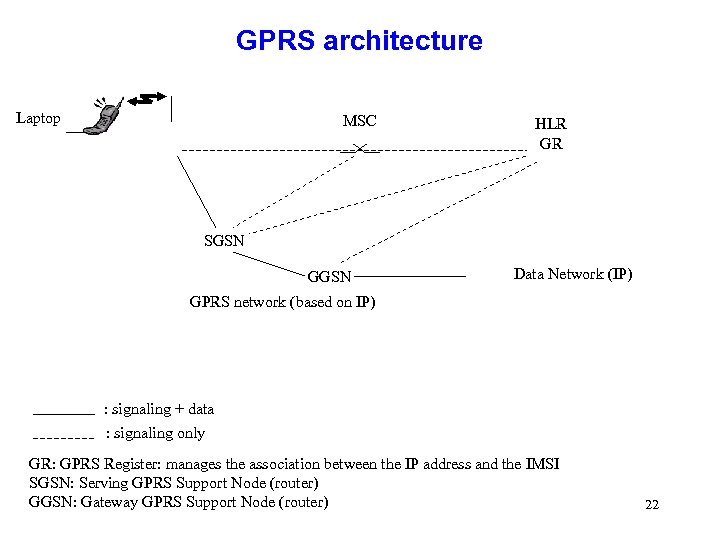 GPRS architecture Laptop MSC HLR GR SGSN GGSN Data Network (IP) GPRS network (based on IP) : signaling + data : signaling only GR: GPRS Register: manages the association between the IP address and the IMSI SGSN: Serving GPRS Support Node (router) GGSN: Gateway GPRS Support Node (router) 22
GPRS architecture Laptop MSC HLR GR SGSN GGSN Data Network (IP) GPRS network (based on IP) : signaling + data : signaling only GR: GPRS Register: manages the association between the IP address and the IMSI SGSN: Serving GPRS Support Node (router) GGSN: Gateway GPRS Support Node (router) 22
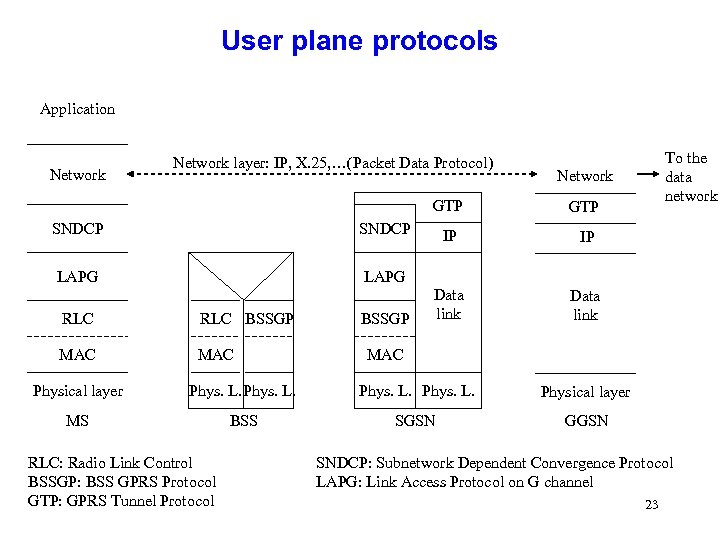 User plane protocols Application Network layer: IP, X. 25, …(Packet Data Protocol) Network GTP SNDCP GTP IP IP Data link SNDCP LAPG To the data network LAPG RLC BSSGP MAC Physical layer Phys. L. Physical layer MS BSS SGSN GGSN RLC: Radio Link Control BSSGP: BSS GPRS Protocol GTP: GPRS Tunnel Protocol SNDCP: Subnetwork Dependent Convergence Protocol LAPG: Link Access Protocol on G channel 23
User plane protocols Application Network layer: IP, X. 25, …(Packet Data Protocol) Network GTP SNDCP GTP IP IP Data link SNDCP LAPG To the data network LAPG RLC BSSGP MAC Physical layer Phys. L. Physical layer MS BSS SGSN GGSN RLC: Radio Link Control BSSGP: BSS GPRS Protocol GTP: GPRS Tunnel Protocol SNDCP: Subnetwork Dependent Convergence Protocol LAPG: Link Access Protocol on G channel 23
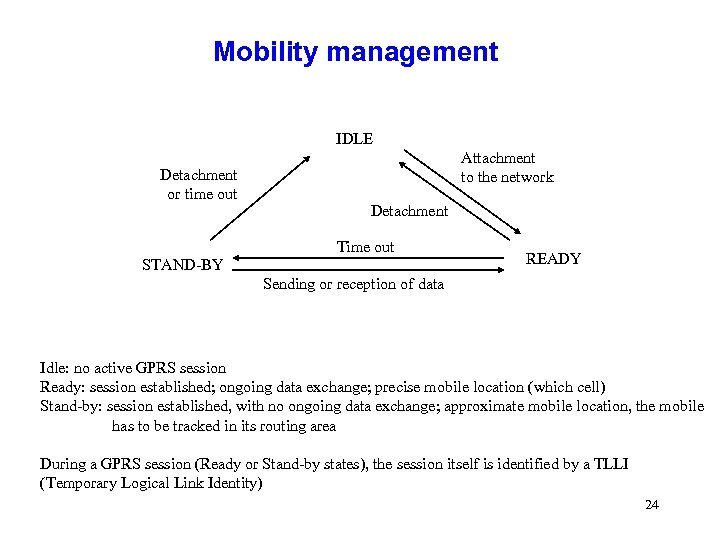 Mobility management IDLE Detachment or time out Attachment to the network Detachment Time out STAND-BY READY Sending or reception of data Idle: no active GPRS session Ready: session established; ongoing data exchange; precise mobile location (which cell) Stand-by: session established, with no ongoing data exchange; approximate mobile location, the mobile has to be tracked in its routing area During a GPRS session (Ready or Stand-by states), the session itself is identified by a TLLI (Temporary Logical Link Identity) 24
Mobility management IDLE Detachment or time out Attachment to the network Detachment Time out STAND-BY READY Sending or reception of data Idle: no active GPRS session Ready: session established; ongoing data exchange; precise mobile location (which cell) Stand-by: session established, with no ongoing data exchange; approximate mobile location, the mobile has to be tracked in its routing area During a GPRS session (Ready or Stand-by states), the session itself is identified by a TLLI (Temporary Logical Link Identity) 24
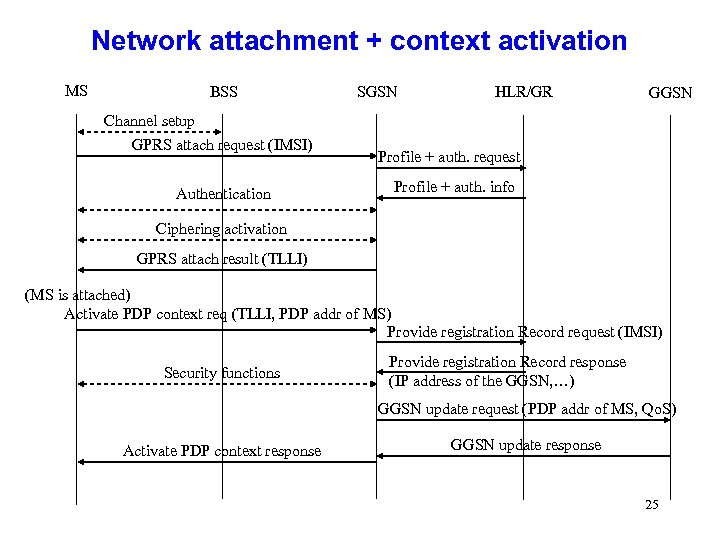 Network attachment + context activation MS BSS SGSN HLR/GR GGSN Channel setup GPRS attach request (IMSI) Authentication Profile + auth. request Profile + auth. info Ciphering activation GPRS attach result (TLLI) (MS is attached) Activate PDP context req (TLLI, PDP addr of MS) Provide registration Record request (IMSI) Security functions Provide registration Record response (IP address of the GGSN, …) GGSN update request (PDP addr of MS, Qo. S) Activate PDP context response GGSN update response 25
Network attachment + context activation MS BSS SGSN HLR/GR GGSN Channel setup GPRS attach request (IMSI) Authentication Profile + auth. request Profile + auth. info Ciphering activation GPRS attach result (TLLI) (MS is attached) Activate PDP context req (TLLI, PDP addr of MS) Provide registration Record request (IMSI) Security functions Provide registration Record response (IP address of the GGSN, …) GGSN update request (PDP addr of MS, Qo. S) Activate PDP context response GGSN update response 25
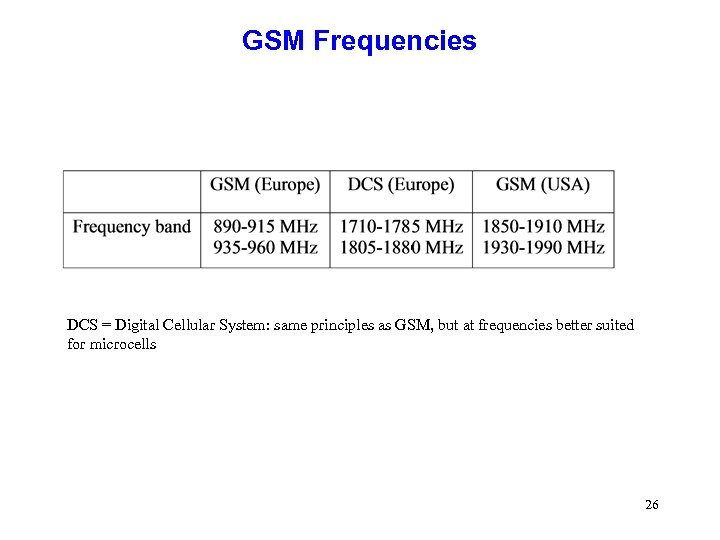 GSM Frequencies DCS = Digital Cellular System: same principles as GSM, but at frequencies better suited for microcells 26
GSM Frequencies DCS = Digital Cellular System: same principles as GSM, but at frequencies better suited for microcells 26
 GSM Security: The SIM card (Subscriber Identity Module) g g Must be tamper-resistant Protected by a PIN code (checked locally by the SIM) Is removable from the terminal Contains all data specific to the end user which have to reside in the Mobile Station: i. IMSI: International Mobile Subscriber Identity (permanent user’s identity) i. PIN i. TMSI (Temporary Mobile Subscriber Identity) i. Ki : User’s secret key i. Kc : Ciphering key i. List of the last call attempts i. List of preferred operators i. Supplementary service data (abbreviated dialing, last short messages received, . . . ) 27
GSM Security: The SIM card (Subscriber Identity Module) g g Must be tamper-resistant Protected by a PIN code (checked locally by the SIM) Is removable from the terminal Contains all data specific to the end user which have to reside in the Mobile Station: i. IMSI: International Mobile Subscriber Identity (permanent user’s identity) i. PIN i. TMSI (Temporary Mobile Subscriber Identity) i. Ki : User’s secret key i. Kc : Ciphering key i. List of the last call attempts i. List of preferred operators i. Supplementary service data (abbreviated dialing, last short messages received, . . . ) 27
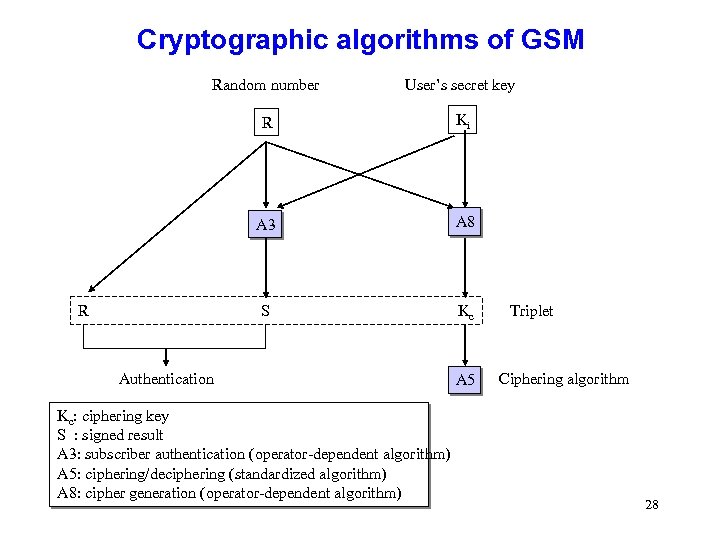 Cryptographic algorithms of GSM Random number User’s secret key R Ki A 3 A 8 R S Kc Authentication Kc: ciphering key S : signed result A 3: subscriber authentication (operator-dependent algorithm) A 5: ciphering/deciphering (standardized algorithm) A 8: cipher generation (operator-dependent algorithm) A 5 Triplet Ciphering algorithm 28
Cryptographic algorithms of GSM Random number User’s secret key R Ki A 3 A 8 R S Kc Authentication Kc: ciphering key S : signed result A 3: subscriber authentication (operator-dependent algorithm) A 5: ciphering/deciphering (standardized algorithm) A 8: cipher generation (operator-dependent algorithm) A 5 Triplet Ciphering algorithm 28
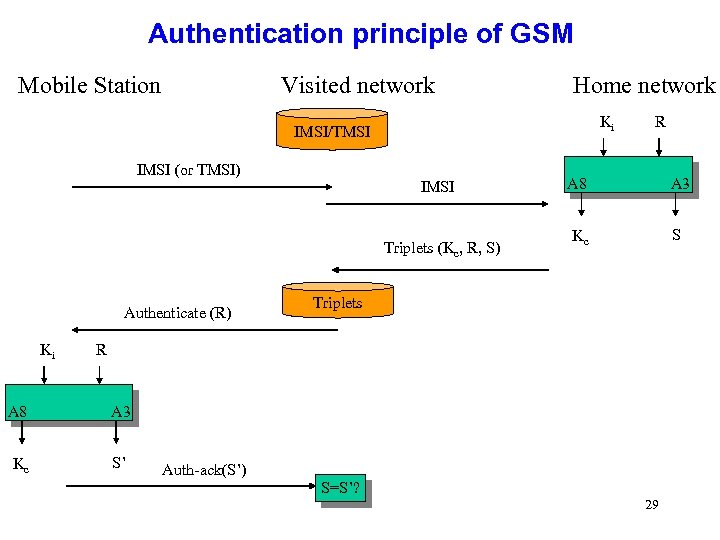 Authentication principle of GSM Mobile Station Visited network Home network Ki IMSI/TMSI IMSI (or TMSI) IMSI Triplets (Kc, R, S) Authenticate (R) Ki R A 8 A 3 S Kc Triplets R A 8 A 3 Kc S’ Auth-ack(S’) S=S’? 29
Authentication principle of GSM Mobile Station Visited network Home network Ki IMSI/TMSI IMSI (or TMSI) IMSI Triplets (Kc, R, S) Authenticate (R) Ki R A 8 A 3 S Kc Triplets R A 8 A 3 Kc S’ Auth-ack(S’) S=S’? 29
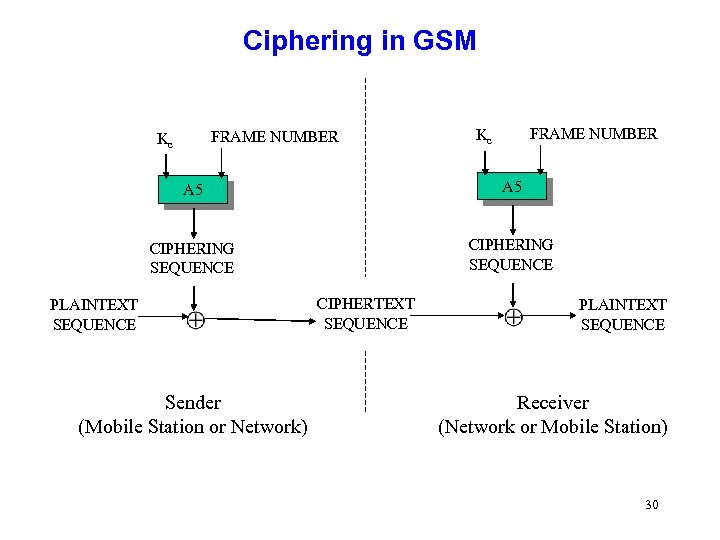 Ciphering in GSM FRAME NUMBER Kc A 5 CIPHERING SEQUENCE PLAINTEXT SEQUENCE Sender (Mobile Station or Network) CIPHERTEXT SEQUENCE PLAINTEXT SEQUENCE Receiver (Network or Mobile Station) 30
Ciphering in GSM FRAME NUMBER Kc A 5 CIPHERING SEQUENCE PLAINTEXT SEQUENCE Sender (Mobile Station or Network) CIPHERTEXT SEQUENCE PLAINTEXT SEQUENCE Receiver (Network or Mobile Station) 30
 Conclusion on GSM security g g Focused on the protection of the air interface No protection on the wired part of the network (neither for privacy nor for confidentiality) The visited network has access to all data (except the secret key of the end user) Generally robust, but a few successful attacks have been reported: ifaked base stations icloning of the SIM card 31
Conclusion on GSM security g g Focused on the protection of the air interface No protection on the wired part of the network (neither for privacy nor for confidentiality) The visited network has access to all data (except the secret key of the end user) Generally robust, but a few successful attacks have been reported: ifaked base stations icloning of the SIM card 31
 GSM today g g The common digital cellular technique deployed throughout Europe Probably the leading cellular technology worldwide Hundreds of millions of subscribers in more than 100 countries 7000+ pages of standards. . . 32
GSM today g g The common digital cellular technique deployed throughout Europe Probably the leading cellular technology worldwide Hundreds of millions of subscribers in more than 100 countries 7000+ pages of standards. . . 32
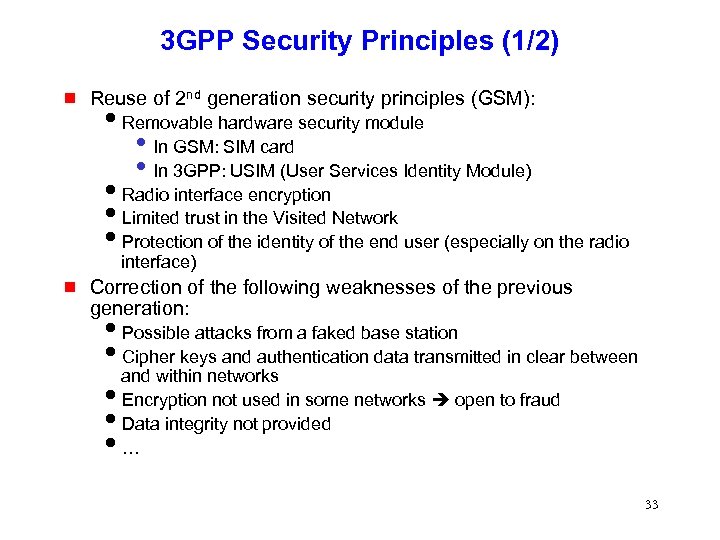 3 GPP Security Principles (1/2) g Reuse of 2 nd generation security principles (GSM): i. Removable hardware security module • In GSM: SIM card • In 3 GPP: USIM (User Services Identity Module) i. Radio interface encryption i. Limited trust in the Visited Network i. Protection of the identity of the end user (especially on the radio interface) g Correction of the following weaknesses of the previous generation: i. Possible attacks from a faked base station i. Cipher keys and authentication data transmitted in clear between and within networks i. Encryption not used in some networks open to fraud i. Data integrity not provided i… 33
3 GPP Security Principles (1/2) g Reuse of 2 nd generation security principles (GSM): i. Removable hardware security module • In GSM: SIM card • In 3 GPP: USIM (User Services Identity Module) i. Radio interface encryption i. Limited trust in the Visited Network i. Protection of the identity of the end user (especially on the radio interface) g Correction of the following weaknesses of the previous generation: i. Possible attacks from a faked base station i. Cipher keys and authentication data transmitted in clear between and within networks i. Encryption not used in some networks open to fraud i. Data integrity not provided i… 33
 3 GPP Security Principles (2/2) g New security features i. New kind of service providers (content providers, HLR only service providers, …) i. Increased control for the user over their service profile i. Enhanced resistance to active attacks i. Increased importance of non-voice services i… 34
3 GPP Security Principles (2/2) g New security features i. New kind of service providers (content providers, HLR only service providers, …) i. Increased control for the user over their service profile i. Enhanced resistance to active attacks i. Increased importance of non-voice services i… 34
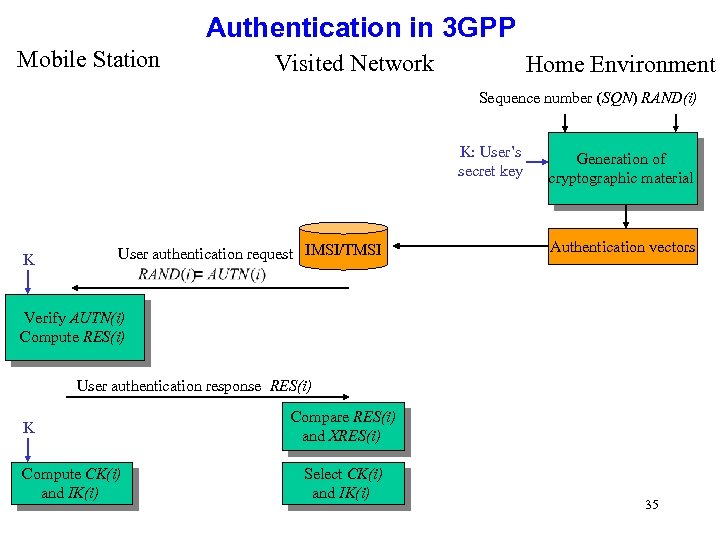 Authentication in 3 GPP Mobile Station Visited Network Home Environment Sequence number (SQN) RAND(i) K: User’s secret key K User authentication request IMSI/TMSI Generation of cryptographic material Authentication vectors Verify AUTN(i) Compute RES(i) User authentication response RES(i) K Compute CK(i) and IK(i) Compare RES(i) and XRES(i) Select CK(i) and IK(i) 35
Authentication in 3 GPP Mobile Station Visited Network Home Environment Sequence number (SQN) RAND(i) K: User’s secret key K User authentication request IMSI/TMSI Generation of cryptographic material Authentication vectors Verify AUTN(i) Compute RES(i) User authentication response RES(i) K Compute CK(i) and IK(i) Compare RES(i) and XRES(i) Select CK(i) and IK(i) 35
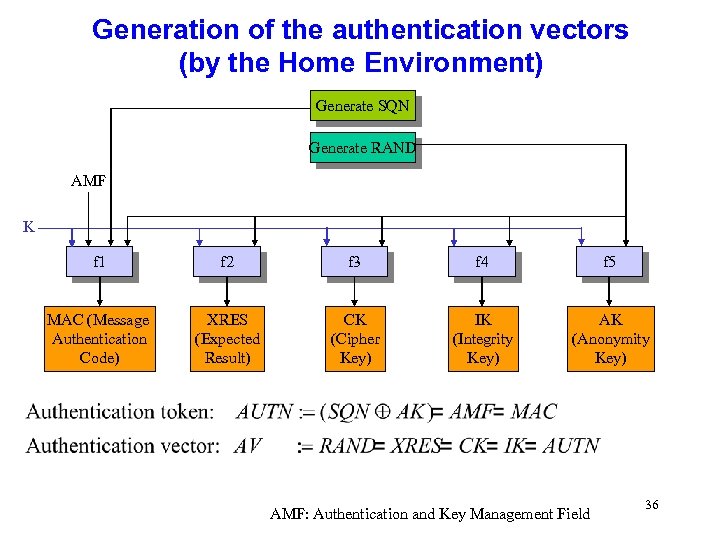 Generation of the authentication vectors (by the Home Environment) Generate SQN Generate RAND AMF K f 1 f 2 f 3 f 4 f 5 MAC (Message Authentication Code) XRES (Expected Result) CK (Cipher Key) IK (Integrity Key) AK (Anonymity Key) AMF: Authentication and Key Management Field 36
Generation of the authentication vectors (by the Home Environment) Generate SQN Generate RAND AMF K f 1 f 2 f 3 f 4 f 5 MAC (Message Authentication Code) XRES (Expected Result) CK (Cipher Key) IK (Integrity Key) AK (Anonymity Key) AMF: Authentication and Key Management Field 36
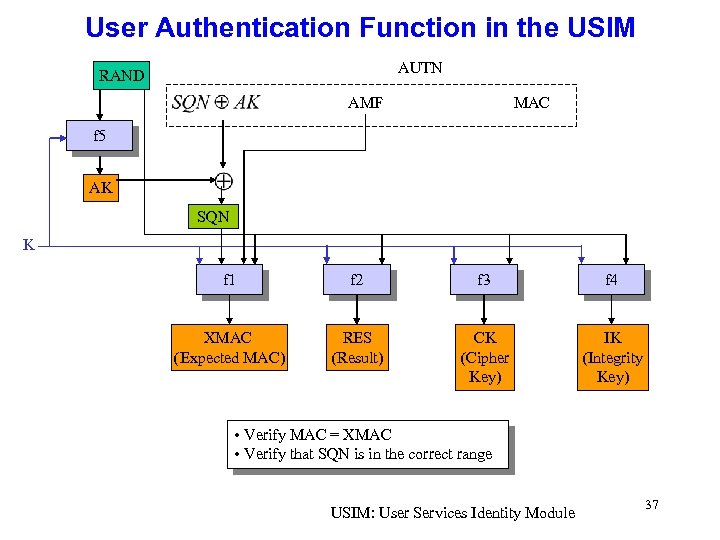 User Authentication Function in the USIM AUTN RAND AMF MAC f 5 AK SQN K f 1 f 2 f 3 f 4 XMAC (Expected MAC) RES (Result) CK (Cipher Key) IK (Integrity Key) • Verify MAC = XMAC • Verify that SQN is in the correct range USIM: User Services Identity Module 37
User Authentication Function in the USIM AUTN RAND AMF MAC f 5 AK SQN K f 1 f 2 f 3 f 4 XMAC (Expected MAC) RES (Result) CK (Cipher Key) IK (Integrity Key) • Verify MAC = XMAC • Verify that SQN is in the correct range USIM: User Services Identity Module 37
 More about the authentication and key generation function g g g In addition to f 1, f 2, f 3, f 4 and f 5, two more functions are defined: f 1* and f 5*, used in case the authentication procedure gets desynchronized (detected by the range of SQN). f 1, f 1*, f 2, f 3, f 4, f 5 and f 5* are operator-specific However, 3 GPP provides a detailed example of algorithm set, called MILENAGE is based on the Rijndael block cipher In MILENAGE, the generation of all seven functions f 1…f 5* is based on the Rijndael algorithm 38
More about the authentication and key generation function g g g In addition to f 1, f 2, f 3, f 4 and f 5, two more functions are defined: f 1* and f 5*, used in case the authentication procedure gets desynchronized (detected by the range of SQN). f 1, f 1*, f 2, f 3, f 4, f 5 and f 5* are operator-specific However, 3 GPP provides a detailed example of algorithm set, called MILENAGE is based on the Rijndael block cipher In MILENAGE, the generation of all seven functions f 1…f 5* is based on the Rijndael algorithm 38
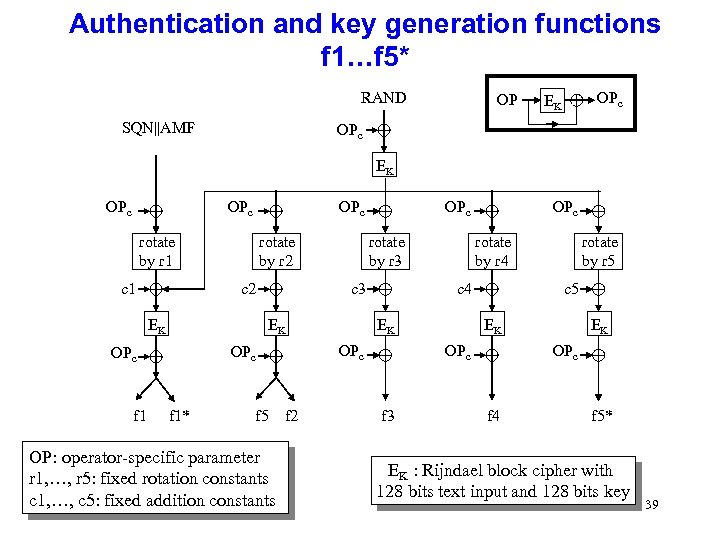 Authentication and key generation functions f 1…f 5* RAND SQN||AMF OP OPc EK OPc OPc rotate by r 1 c 1 rotate by r 2 c 2 EK f 1 rotate by r 3 c 3 EK OPc f 1* OPc f 5 f 2 OP: operator-specific parameter r 1, …, r 5: fixed rotation constants c 1, …, c 5: fixed addition constants OPc rotate by r 4 c 4 EK OPc c 5 EK OPc f 3 rotate by r 5 EK OPc f 4 f 5* EK : Rijndael block cipher with 128 bits text input and 128 bits key 39
Authentication and key generation functions f 1…f 5* RAND SQN||AMF OP OPc EK OPc OPc rotate by r 1 c 1 rotate by r 2 c 2 EK f 1 rotate by r 3 c 3 EK OPc f 1* OPc f 5 f 2 OP: operator-specific parameter r 1, …, r 5: fixed rotation constants c 1, …, c 5: fixed addition constants OPc rotate by r 4 c 4 EK OPc c 5 EK OPc f 3 rotate by r 5 EK OPc f 4 f 5* EK : Rijndael block cipher with 128 bits text input and 128 bits key 39
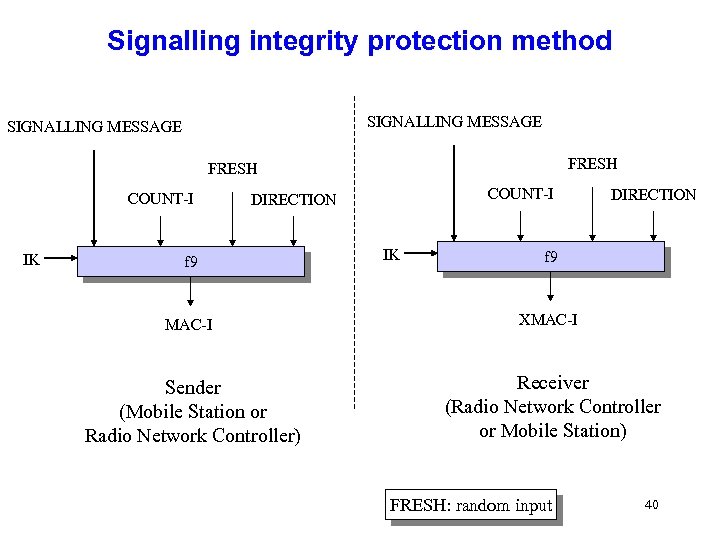 Signalling integrity protection method SIGNALLING MESSAGE FRESH COUNT-I IK COUNT-I DIRECTION f 9 IK DIRECTION f 9 MAC-I XMAC-I Sender (Mobile Station or Radio Network Controller) Receiver (Radio Network Controller or Mobile Station) FRESH: random input 40
Signalling integrity protection method SIGNALLING MESSAGE FRESH COUNT-I IK COUNT-I DIRECTION f 9 IK DIRECTION f 9 MAC-I XMAC-I Sender (Mobile Station or Radio Network Controller) Receiver (Radio Network Controller or Mobile Station) FRESH: random input 40
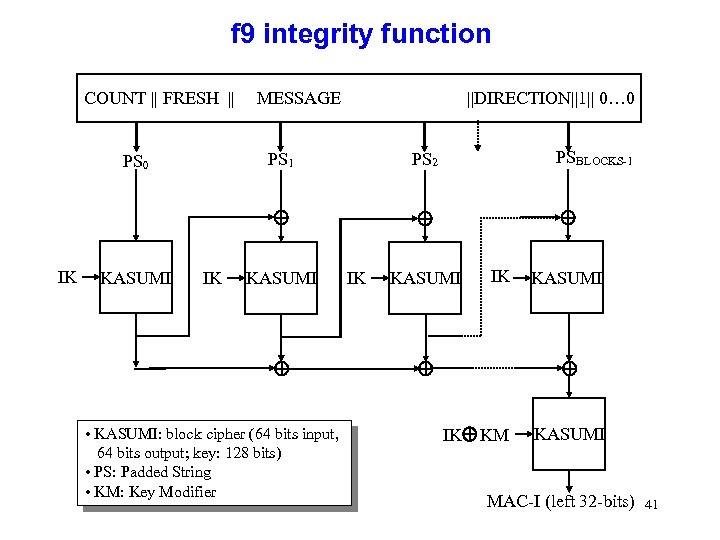 f 9 integrity function COUNT || FRESH || MESSAGE ||DIRECTION||1|| 0… 0 IK KASUMI • KASUMI: block cipher (64 bits input, 64 bits output; key: 128 bits) • PS: Padded String • KM: Key Modifier PSBLOCKS-1 PS 2 PS 1 PS 0 IK IK KASUMI IK KM KASUMI MAC-I (left 32 -bits) 41
f 9 integrity function COUNT || FRESH || MESSAGE ||DIRECTION||1|| 0… 0 IK KASUMI • KASUMI: block cipher (64 bits input, 64 bits output; key: 128 bits) • PS: Padded String • KM: Key Modifier PSBLOCKS-1 PS 2 PS 1 PS 0 IK IK KASUMI IK KM KASUMI MAC-I (left 32 -bits) 41
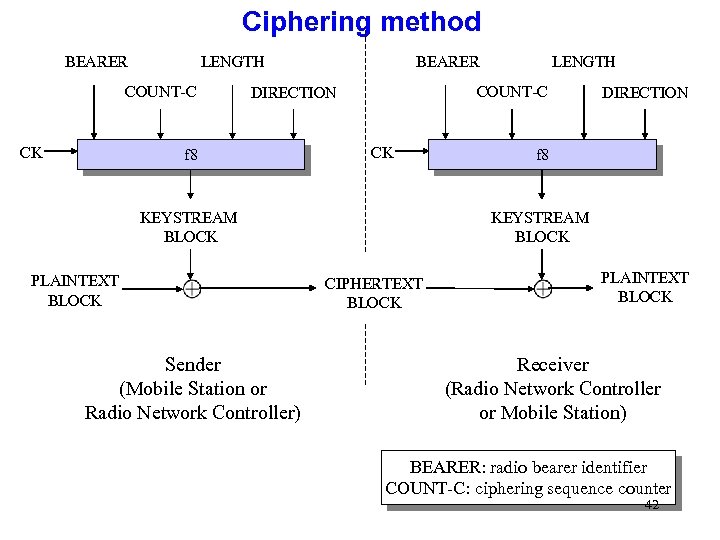 Ciphering method LENGTH BEARER COUNT-C CK COUNT-C DIRECTION f 8 CK KEYSTREAM BLOCK PLAINTEXT BLOCK Sender (Mobile Station or Radio Network Controller) LENGTH BEARER DIRECTION f 8 KEYSTREAM BLOCK CIPHERTEXT BLOCK PLAINTEXT BLOCK Receiver (Radio Network Controller or Mobile Station) BEARER: radio bearer identifier COUNT-C: ciphering sequence counter 42
Ciphering method LENGTH BEARER COUNT-C CK COUNT-C DIRECTION f 8 CK KEYSTREAM BLOCK PLAINTEXT BLOCK Sender (Mobile Station or Radio Network Controller) LENGTH BEARER DIRECTION f 8 KEYSTREAM BLOCK CIPHERTEXT BLOCK PLAINTEXT BLOCK Receiver (Radio Network Controller or Mobile Station) BEARER: radio bearer identifier COUNT-C: ciphering sequence counter 42
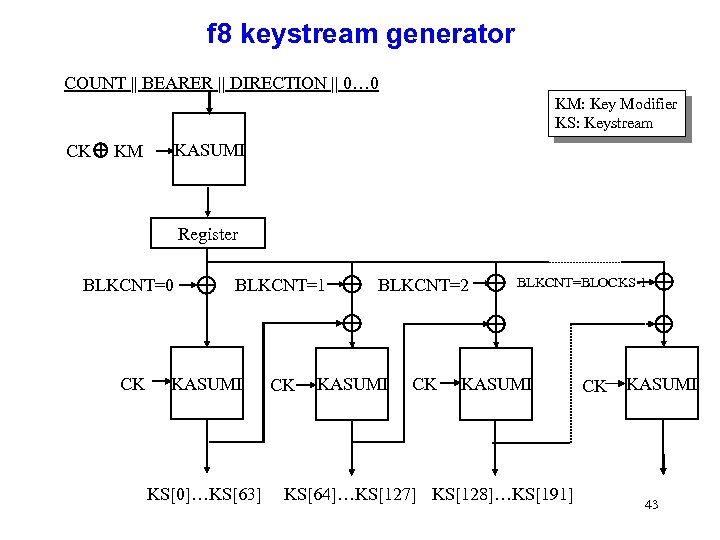 f 8 keystream generator COUNT || BEARER || DIRECTION || 0… 0 KM: Key Modifier KS: Keystream CK KM KASUMI Register BLKCNT=0 CK BLKCNT=1 KASUMI KS[0]…KS[63] CK BLKCNT=2 KASUMI CK BLKCNT=BLOCKS-1 KASUMI KS[64]…KS[127] KS[128]…KS[191] CK KASUMI 43
f 8 keystream generator COUNT || BEARER || DIRECTION || 0… 0 KM: Key Modifier KS: Keystream CK KM KASUMI Register BLKCNT=0 CK BLKCNT=1 KASUMI KS[0]…KS[63] CK BLKCNT=2 KASUMI CK BLKCNT=BLOCKS-1 KASUMI KS[64]…KS[127] KS[128]…KS[191] CK KASUMI 43
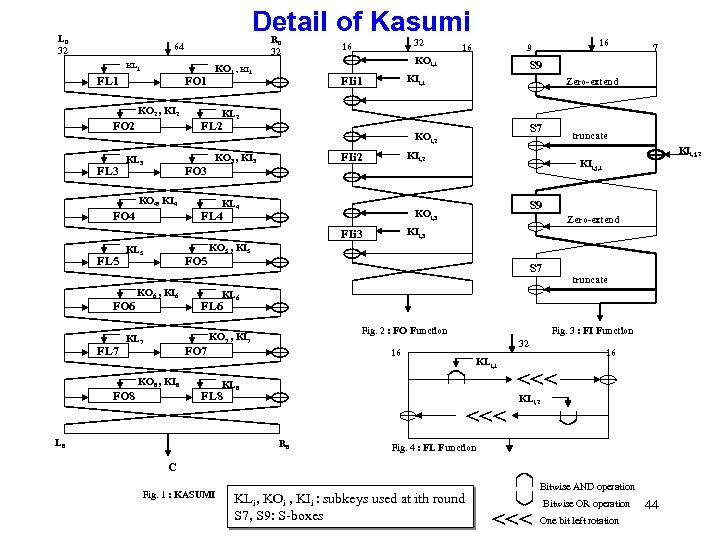 Detail of Kasumi L 0 32 R 0 32 64 KL 1 FO 1 KO 1 , KI 1 KO 2 , KI 2 FO 2 FL 3 32 16 FO 3 KL 4 FO 5 S 7 truncate KIi, j, 2 KIi, 2 FIi 2 KO 3 , KI 3 KIi, j, 1 S 9 KOi, 3 FL 4 KL 5 Zero-extend KOi, 2 Zero-extend KIi, 3 FIi 3 FL 5 S 9 KIi, 1 FIi 1 7 KL 2 KO 4, KI 4 FO 4 16 9 KOi, 1 FL 2 KL 3 16 KO 5 , KI 5 S 7 truncate FO 6 FL 7 KO 6 , KI 6 KL 7 KL 6 FO 7 KO 8 , KI 8 FO 8 Fig. 2 : FO Function KO 7 , KI 7 16 Fig. 3 : FI Function 32 KLi, 1 KL 8 FL 8 <<< L 8 R 8 16 <<< KLi, 2 Fig. 4 : FL Function C Fig. 1 : KASUMI KLi, KOi , KIi : subkeys used at ith round S 7, S 9: S-boxes Bitwise AND operation <<< Bitwise OR operation One bit left rotation 44
Detail of Kasumi L 0 32 R 0 32 64 KL 1 FO 1 KO 1 , KI 1 KO 2 , KI 2 FO 2 FL 3 32 16 FO 3 KL 4 FO 5 S 7 truncate KIi, j, 2 KIi, 2 FIi 2 KO 3 , KI 3 KIi, j, 1 S 9 KOi, 3 FL 4 KL 5 Zero-extend KOi, 2 Zero-extend KIi, 3 FIi 3 FL 5 S 9 KIi, 1 FIi 1 7 KL 2 KO 4, KI 4 FO 4 16 9 KOi, 1 FL 2 KL 3 16 KO 5 , KI 5 S 7 truncate FO 6 FL 7 KO 6 , KI 6 KL 7 KL 6 FO 7 KO 8 , KI 8 FO 8 Fig. 2 : FO Function KO 7 , KI 7 16 Fig. 3 : FI Function 32 KLi, 1 KL 8 FL 8 <<< L 8 R 8 16 <<< KLi, 2 Fig. 4 : FL Function C Fig. 1 : KASUMI KLi, KOi , KIi : subkeys used at ith round S 7, S 9: S-boxes Bitwise AND operation <<< Bitwise OR operation One bit left rotation 44
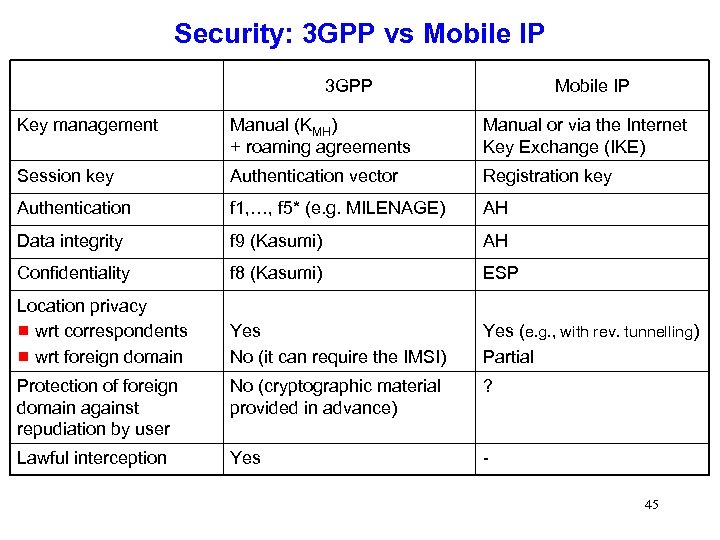 Security: 3 GPP vs Mobile IP 3 GPP Mobile IP Key management Manual (KMH) + roaming agreements Manual or via the Internet Key Exchange (IKE) Session key Authentication vector Registration key Authentication f 1, …, f 5* (e. g. MILENAGE) AH Data integrity f 9 (Kasumi) AH Confidentiality f 8 (Kasumi) ESP Location privacy g wrt correspondents g wrt foreign domain Yes No (it can require the IMSI) Yes (e. g. , with rev. tunnelling) Partial Protection of foreign domain against repudiation by user No (cryptographic material provided in advance) ? Lawful interception Yes 45
Security: 3 GPP vs Mobile IP 3 GPP Mobile IP Key management Manual (KMH) + roaming agreements Manual or via the Internet Key Exchange (IKE) Session key Authentication vector Registration key Authentication f 1, …, f 5* (e. g. MILENAGE) AH Data integrity f 9 (Kasumi) AH Confidentiality f 8 (Kasumi) ESP Location privacy g wrt correspondents g wrt foreign domain Yes No (it can require the IMSI) Yes (e. g. , with rev. tunnelling) Partial Protection of foreign domain against repudiation by user No (cryptographic material provided in advance) ? Lawful interception Yes 45
 Conclusion on 3 GPP security g Some improvement with respect to 2 nd generation g Quite conservative solution No real size experience so far Privacy/anonymity of the user not completely protected 2 nd/3 rd generation interoperation will be complicated and might open security breaches g g g i. Cryptographic algorithms are published i. Integrity of the signalling messages is protected 46
Conclusion on 3 GPP security g Some improvement with respect to 2 nd generation g Quite conservative solution No real size experience so far Privacy/anonymity of the user not completely protected 2 nd/3 rd generation interoperation will be complicated and might open security breaches g g g i. Cryptographic algorithms are published i. Integrity of the signalling messages is protected 46
 References On Signalling System 7 i. Travis Russel, Signaling System #7, Second Edition, Mc. Graw-Hill Telecommunications, 1998. i. Uyless Black, ISDN and SS 7, Prentice Hall, 1997 i. Abdi Modaressi and Ronald A. Skoog, Signaling System N° 7: A tutorial, IEEE Communications Magazine, July 1990, pp 19 -35. g On GSM i. D. Goodman: Wireless Personal Communications Systems Addison-Wesley, 1997 i. S. Redl et al. : GSM and Personal Communication Handbook Artech House Publ, 1998 i. A. Mehrotra: GSM System Engineering Artech House Publ, 1997 g On GPRS i. R. Kalden et al. : Wireless Interned Access Based on GPRS IEEE Personal Communication Magazine, April 2000 g On 3 GPP i 3 rd Generation Partnership Project: http: //www. 3 gpp. org 47
References On Signalling System 7 i. Travis Russel, Signaling System #7, Second Edition, Mc. Graw-Hill Telecommunications, 1998. i. Uyless Black, ISDN and SS 7, Prentice Hall, 1997 i. Abdi Modaressi and Ronald A. Skoog, Signaling System N° 7: A tutorial, IEEE Communications Magazine, July 1990, pp 19 -35. g On GSM i. D. Goodman: Wireless Personal Communications Systems Addison-Wesley, 1997 i. S. Redl et al. : GSM and Personal Communication Handbook Artech House Publ, 1998 i. A. Mehrotra: GSM System Engineering Artech House Publ, 1997 g On GPRS i. R. Kalden et al. : Wireless Interned Access Based on GPRS IEEE Personal Communication Magazine, April 2000 g On 3 GPP i 3 rd Generation Partnership Project: http: //www. 3 gpp. org 47


