6e536b58505d8ae67e78b117cb9cb10e.ppt
- Количество слайдов: 38
 18739 A: Foundations of Security and Privacy Course Review Anupam Datta CMU Fall 2007 -08
18739 A: Foundations of Security and Privacy Course Review Anupam Datta CMU Fall 2007 -08
 Goals of course o Provide an overview of foundational work in security and privacy n n Self-contained introduction + State-of-the-art research o Fundamental questions n What does being secure mean? p Model n of system + attacker Is a given system secure? p Sound analysis methods
Goals of course o Provide an overview of foundational work in security and privacy n n Self-contained introduction + State-of-the-art research o Fundamental questions n What does being secure mean? p Model n of system + attacker Is a given system secure? p Sound analysis methods
 Goals of course (2) o Cover 4 central research areas n n Security Protocols Distributed Access Control Privacy Language-based Security An experiment – existing courses typically focus on one area
Goals of course (2) o Cover 4 central research areas n n Security Protocols Distributed Access Control Privacy Language-based Security An experiment – existing courses typically focus on one area
 Goals of course (3) o Introduction to general analysis methods n Model-checking n Logics n Process calculi n Logic programming n Type systems o Application to practical security mechanisms n Industrial security protocols n Grey system for distributed access control n Specification and enforcement of privacy laws such as HIPAA in LPU n Cyclone (Safe C) and Jif (Java + information flow)
Goals of course (3) o Introduction to general analysis methods n Model-checking n Logics n Process calculi n Logic programming n Type systems o Application to practical security mechanisms n Industrial security protocols n Grey system for distributed access control n Specification and enforcement of privacy laws such as HIPAA in LPU n Cyclone (Safe C) and Jif (Java + information flow)
 Goals of course (4) o Provide breadth in area n Lectures and homeworks o Provide some depth in area n n Course project Largely successful!
Goals of course (4) o Provide breadth in area n Lectures and homeworks o Provide some depth in area n n Course project Largely successful!
 Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
 Security Protocol Analysis o The Problem: Is a given network protocol secure? o First define: n Model of protocol n Model of attacker n Security properties p Secrecy, confidentiality p Authentication, integrity p Denial of service
Security Protocol Analysis o The Problem: Is a given network protocol secure? o First define: n Model of protocol n Model of attacker n Security properties p Secrecy, confidentiality p Authentication, integrity p Denial of service
 Methods o Bug finding n n Automated model-checking techniques Finite number of sessions o Security proofs n n n Absence of bugs Unbounded number of sessions Many approaches p Paulson’s Inductive Method, Protocol Composition Logic, Applied Pi Calculus
Methods o Bug finding n n Automated model-checking techniques Finite number of sessions o Security proofs n n n Absence of bugs Unbounded number of sessions Many approaches p Paulson’s Inductive Method, Protocol Composition Logic, Applied Pi Calculus
 Modeling Cryptography o Symbolic Model n “Perfect crypto”: No attacker can break, e. g. can decrypt encrypted message iff has decryption key n Proof technique: Induction o Complexity-theoretic Model n Primitives secure with high probability against probabilistic polynomial time attackers n Proof technique: Reduction o Recent work combining methods
Modeling Cryptography o Symbolic Model n “Perfect crypto”: No attacker can break, e. g. can decrypt encrypted message iff has decryption key n Proof technique: Induction o Complexity-theoretic Model n Primitives secure with high probability against probabilistic polynomial time attackers n Proof technique: Reduction o Recent work combining methods
 Specifying security o Trace-based n Every execution satisfies desired security property n Model-checking, inductive method, PCL o Equivalence-based n Real protocol indistinguishable from “ideal” protocol n Applied pi calculus (observational equivalence), cryptography (pseudorandomness, …)
Specifying security o Trace-based n Every execution satisfies desired security property n Model-checking, inductive method, PCL o Equivalence-based n Real protocol indistinguishable from “ideal” protocol n Applied pi calculus (observational equivalence), cryptography (pseudorandomness, …)
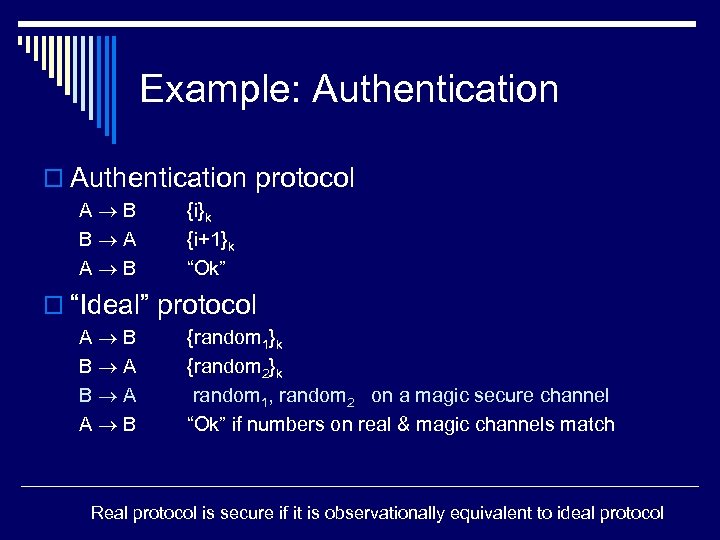 Example: Authentication o Authentication protocol A B B A A B {i}k {i+1}k “Ok” o “Ideal” protocol A B B A A B {random 1}k {random 2}k random 1, random 2 on a magic secure channel “Ok” if numbers on real & magic channels match Real protocol is secure if it is observationally equivalent to ideal protocol
Example: Authentication o Authentication protocol A B B A A B {i}k {i+1}k “Ok” o “Ideal” protocol A B B A A B {random 1}k {random 2}k random 1, random 2 on a magic secure channel “Ok” if numbers on real & magic channels match Real protocol is secure if it is observationally equivalent to ideal protocol
 Course Projects o Rivest’s 3 Ballot Voting Protocol o Ryan’s Pret-a-Voter Protocol o Verified by Visa o Tor Anonymity Protocol
Course Projects o Rivest’s 3 Ballot Voting Protocol o Ryan’s Pret-a-Voter Protocol o Verified by Visa o Tor Anonymity Protocol
 Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
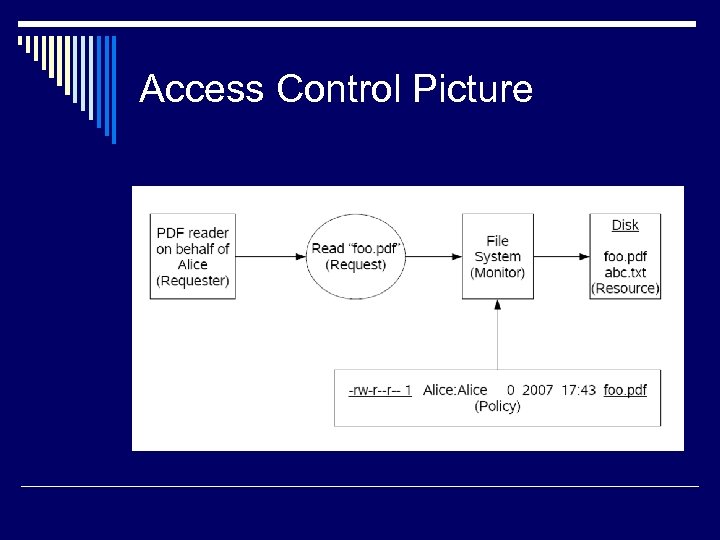 Access Control Picture
Access Control Picture
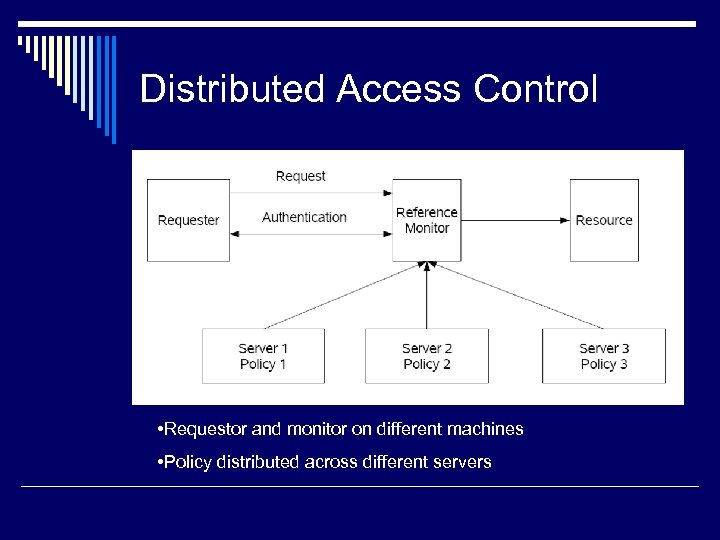 Distributed Access Control • Requestor and monitor on different machines • Policy distributed across different servers
Distributed Access Control • Requestor and monitor on different machines • Policy distributed across different servers
 We covered o Access control logics n n n Lampson et al “speaks-for” logic Proof Carrying Authorization (PCA) and the Grey System Constructive Authorization Logic o Trust Management n RT – Role-based Trust Management
We covered o Access control logics n n n Lampson et al “speaks-for” logic Proof Carrying Authorization (PCA) and the Grey System Constructive Authorization Logic o Trust Management n RT – Role-based Trust Management
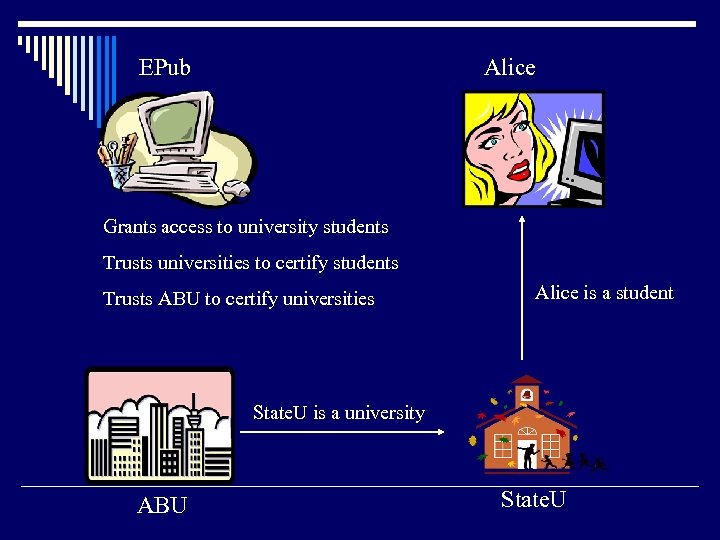 EPub Alice Grants access to university students Trusts universities to certify students Trusts ABU to certify universities Alice is a student State. U is a university ABU State. U
EPub Alice Grants access to university students Trusts universities to certify students Trusts ABU to certify universities Alice is a student State. U is a university ABU State. U
 Main issues o How to represent policies n Naming, delegation n Syntax of logic/language (Lampson+, PCA, Constructive Logic, RT) o How to reason by combining policies n Proof system for logics n Algorithms for RT (decision procedures for Datalog) o How to collect relevant credentials n Distributed proof-search using heuristics in Grey n Provably correct credential chain discovery in RT
Main issues o How to represent policies n Naming, delegation n Syntax of logic/language (Lampson+, PCA, Constructive Logic, RT) o How to reason by combining policies n Proof system for logics n Algorithms for RT (decision procedures for Datalog) o How to collect relevant credentials n Distributed proof-search using heuristics in Grey n Provably correct credential chain discovery in RT
 Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
![Privacy Research Space What is Privacy? [Philosophy, Law, Public Policy] Formal Model, Policy Language, Privacy Research Space What is Privacy? [Philosophy, Law, Public Policy] Formal Model, Policy Language,](https://present5.com/presentation/6e536b58505d8ae67e78b117cb9cb10e/image-20.jpg) Privacy Research Space What is Privacy? [Philosophy, Law, Public Policy] Formal Model, Policy Language, Compliance-check Algorithms [Programming Languages, Logic] Implementation-level Compliance [Software Engg, Formal Methods] Data Privacy [Databases, Cryptography]
Privacy Research Space What is Privacy? [Philosophy, Law, Public Policy] Formal Model, Policy Language, Compliance-check Algorithms [Programming Languages, Logic] Implementation-level Compliance [Software Engg, Formal Methods] Data Privacy [Databases, Cryptography]
 Privacy o Scenarios: n Enterprises collect personal information – email and postal addresses – in many cases through web sites n Organizations such as hospitals and financial institutions hold sensitive personal information o Fundamental questions: n Policy: Under what conditions is the collected information used and distributed? n Enforcement: Do organizational processes actually enforce the stated policy? o Privacy Laws: n HIPAA, GLBA, COPPA
Privacy o Scenarios: n Enterprises collect personal information – email and postal addresses – in many cases through web sites n Organizations such as hospitals and financial institutions hold sensitive personal information o Fundamental questions: n Policy: Under what conditions is the collected information used and distributed? n Enforcement: Do organizational processes actually enforce the stated policy? o Privacy Laws: n HIPAA, GLBA, COPPA
 Privacy Policy Languages o P 3 P n Privacy policy specification for web sites. o E-P 3 P/EPAL n Enterprise privacy policy specification and enforcement o Contextual Integrity and LPU n Philosophical theory of privacy n Formalization in temporal logic (specification and enforcement) n Expressing privacy laws, e. g. HIPAA, GLBA, COPPA
Privacy Policy Languages o P 3 P n Privacy policy specification for web sites. o E-P 3 P/EPAL n Enterprise privacy policy specification and enforcement o Contextual Integrity and LPU n Philosophical theory of privacy n Formalization in temporal logic (specification and enforcement) n Expressing privacy laws, e. g. HIPAA, GLBA, COPPA
![Contextual Integrity [N 2004] o Philosophical framework for privacy o Central concept: Context n Contextual Integrity [N 2004] o Philosophical framework for privacy o Central concept: Context n](https://present5.com/presentation/6e536b58505d8ae67e78b117cb9cb10e/image-23.jpg) Contextual Integrity [N 2004] o Philosophical framework for privacy o Central concept: Context n Examples: Healthcare, banking, education o What is a context? n Set of interacting agents in roles p Roles in healthcare: doctor, patient, … n Norms of transmission p Doctors should share patient health information as per the HIPAA rules n Purpose p Improve health
Contextual Integrity [N 2004] o Philosophical framework for privacy o Central concept: Context n Examples: Healthcare, banking, education o What is a context? n Set of interacting agents in roles p Roles in healthcare: doctor, patient, … n Norms of transmission p Doctors should share patient health information as per the HIPAA rules n Purpose p Improve health
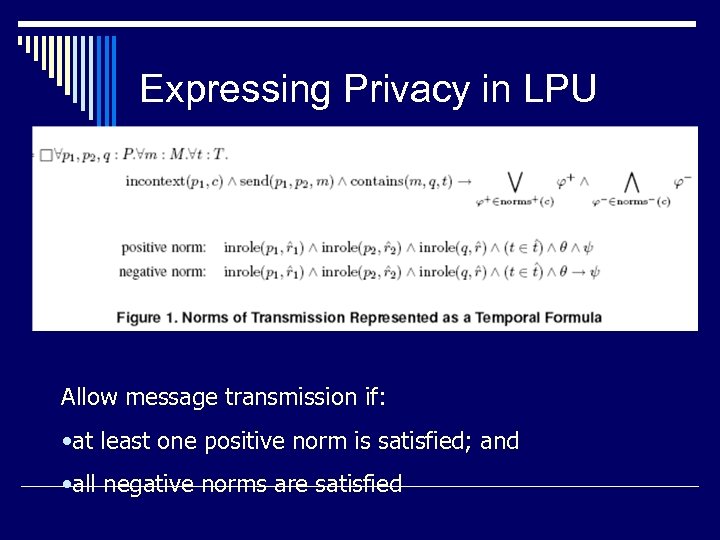 Expressing Privacy in LPU Allow message transmission if: • at least one positive norm is satisfied; and • all negative norms are satisfied
Expressing Privacy in LPU Allow message transmission if: • at least one positive norm is satisfied; and • all negative norms are satisfied
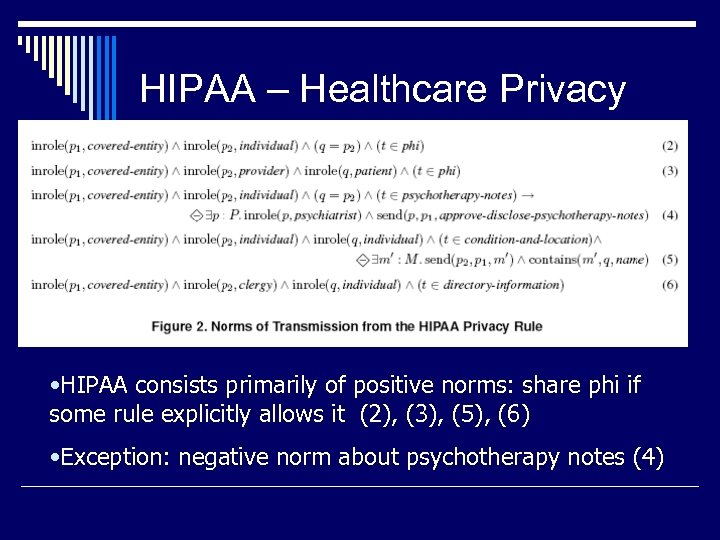 HIPAA – Healthcare Privacy • HIPAA consists primarily of positive norms: share phi if some rule explicitly allows it (2), (3), (5), (6) • Exception: negative norm about psychotherapy notes (4)
HIPAA – Healthcare Privacy • HIPAA consists primarily of positive norms: share phi if some rule explicitly allows it (2), (3), (5), (6) • Exception: negative norm about psychotherapy notes (4)
 COPPA – Children Online Privacy • COPPA consists primarily of negative norms • children can share their protected info only if parents consent (7) (condition) • (8) (obligation – future requirements)
COPPA – Children Online Privacy • COPPA consists primarily of negative norms • children can share their protected info only if parents consent (7) (condition) • (8) (obligation – future requirements)
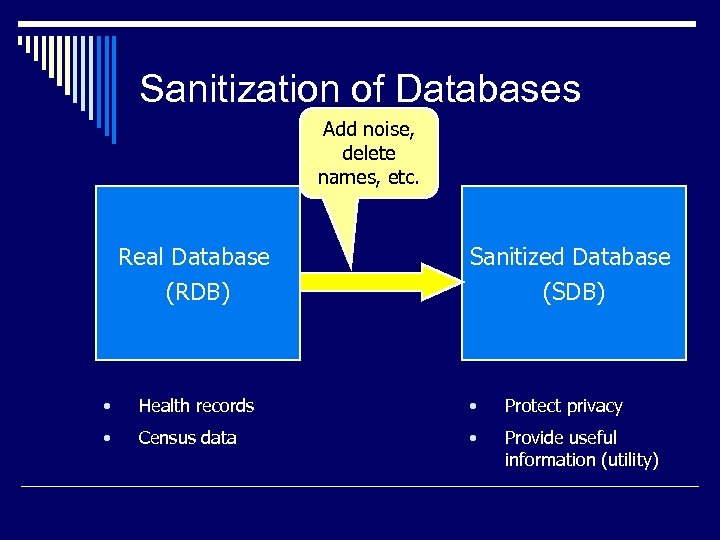 Sanitization of Databases Add noise, delete names, etc. Real Database (RDB) Sanitized Database (SDB) • Health records • Protect privacy • Census data • Provide useful information (utility)
Sanitization of Databases Add noise, delete names, etc. Real Database (RDB) Sanitized Database (SDB) • Health records • Protect privacy • Census data • Provide useful information (utility)
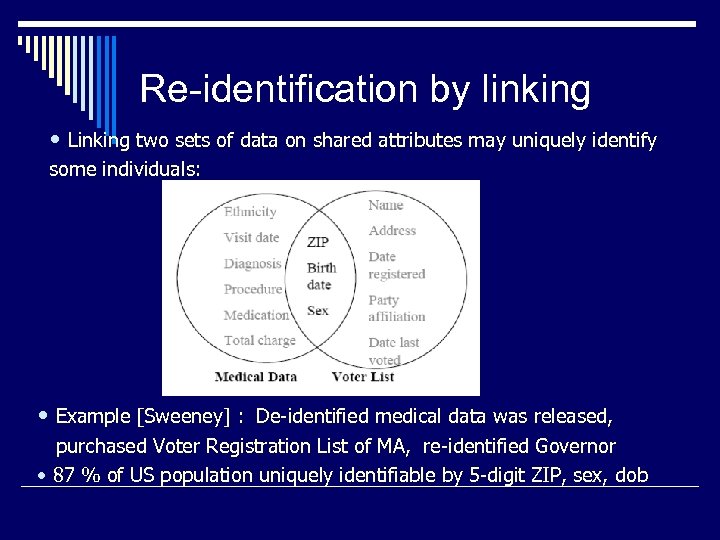 Re-identification by linking • Linking two sets of data on shared attributes may uniquely identify some individuals: • Example [Sweeney] : De-identified medical data was released, purchased Voter Registration List of MA, re-identified Governor • 87 % of US population uniquely identifiable by 5 -digit ZIP, sex, dob
Re-identification by linking • Linking two sets of data on shared attributes may uniquely identify some individuals: • Example [Sweeney] : De-identified medical data was released, purchased Voter Registration List of MA, re-identified Governor • 87 % of US population uniquely identifiable by 5 -digit ZIP, sex, dob
 K-anonymity (1) o Quasi-identifier: Set of attributes (e. g. ZIP, sex, dob) that can be linked with external data to uniquely identify individuals in the population o Make every record in the table indistinguishable from at least k-1 other records with respect to quasiidentifiers o Linking on quasi-identifiers yields at least k records for each possible value of the quasi-identifier
K-anonymity (1) o Quasi-identifier: Set of attributes (e. g. ZIP, sex, dob) that can be linked with external data to uniquely identify individuals in the population o Make every record in the table indistinguishable from at least k-1 other records with respect to quasiidentifiers o Linking on quasi-identifiers yields at least k records for each possible value of the quasi-identifier
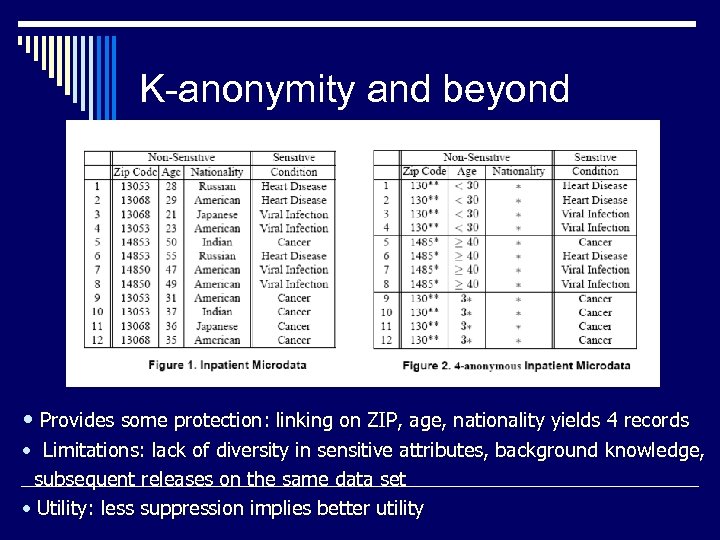 K-anonymity and beyond • Provides some protection: linking on ZIP, age, nationality yields 4 records • Limitations: lack of diversity in sensitive attributes, background knowledge, subsequent releases on the same data set • Utility: less suppression implies better utility
K-anonymity and beyond • Provides some protection: linking on ZIP, age, nationality yields 4 records • Limitations: lack of diversity in sensitive attributes, background knowledge, subsequent releases on the same data set • Utility: less suppression implies better utility
 Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
Four broad topics 1. Security Protocols 2. Distributed Access Control 3. Privacy 4. Language-based Security
 Type Systems for Security o Focus on the use of type systems to improve software security o Two representative projects n n Cyclone: Memory safe dialect of C, i. e. no buffer overflow attacks, format string vulnerabilities etc (or Ccured) Jif: Enforcing information flow security properties (non-interference and variants)
Type Systems for Security o Focus on the use of type systems to improve software security o Two representative projects n n Cyclone: Memory safe dialect of C, i. e. no buffer overflow attacks, format string vulnerabilities etc (or Ccured) Jif: Enforcing information flow security properties (non-interference and variants)
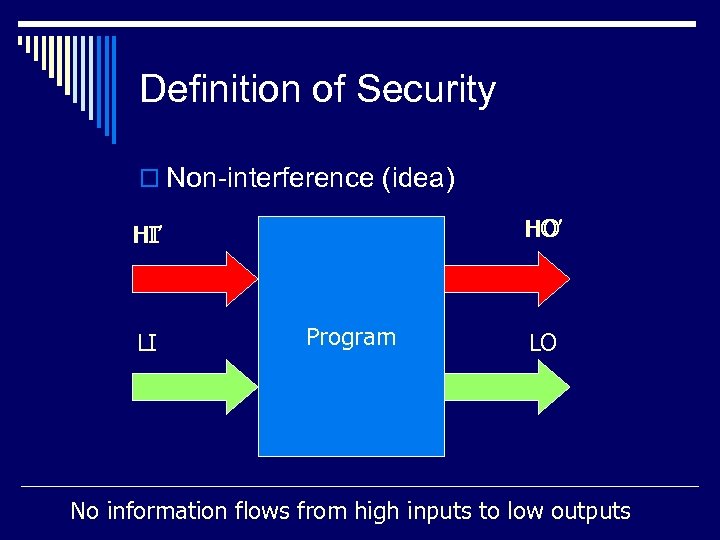 Definition of Security o Non-interference (idea) HO’ HO HI’ HI LI Program LO No information flows from high inputs to low outputs
Definition of Security o Non-interference (idea) HO’ HO HI’ HI LI Program LO No information flows from high inputs to low outputs
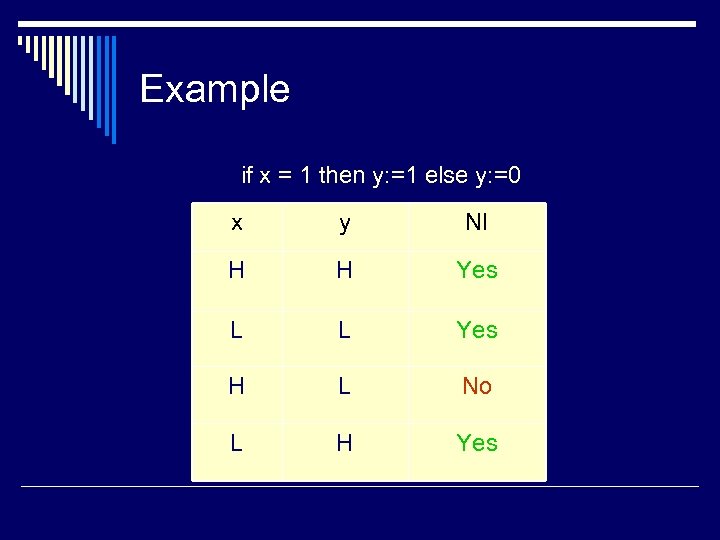 Example if x = 1 then y: =1 else y: =0 x y NI H H Yes L L Yes H L No L H Yes
Example if x = 1 then y: =1 else y: =0 x y NI H H Yes L L Yes H L No L H Yes
 Language definition o Syntax o Type system (static semantics) o Operational semantics (dynamic semantics) o Type safety (soundness) theorem
Language definition o Syntax o Type system (static semantics) o Operational semantics (dynamic semantics) o Type safety (soundness) theorem
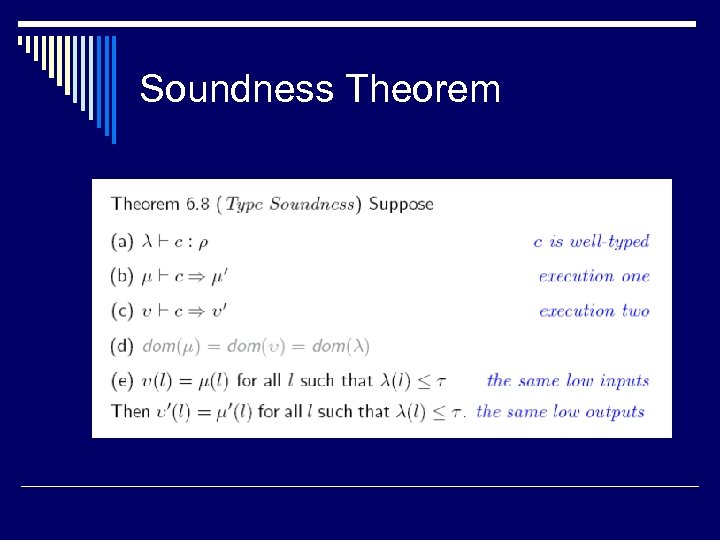 Soundness Theorem
Soundness Theorem
 What next? o Security courses@CMU n 18730 – Introduction to Computer Security p n 18731 – Network Security p n Complementary course on software security 18733 – Applied Cryptography p n Not much overlap, except network security protocols 18732 - Secure Software Systems p n Some overlap in topics; presentation focuses more on attacks and mechanisms, not security models and analysis Complementary course; details of crypto that we treated as black boxes (offered next semester) 15 -819 - Languages and Logics for Security p Reading seminar focused primarily on language-based security
What next? o Security courses@CMU n 18730 – Introduction to Computer Security p n 18731 – Network Security p n Complementary course on software security 18733 – Applied Cryptography p n Not much overlap, except network security protocols 18732 - Secure Software Systems p n Some overlap in topics; presentation focuses more on attacks and mechanisms, not security models and analysis Complementary course; details of crypto that we treated as black boxes (offered next semester) 15 -819 - Languages and Logics for Security p Reading seminar focused primarily on language-based security
 The End
The End


