34ed4a2fc531b1d24abab27e46552c68.ppt
- Количество слайдов: 61
 17 -803/17 -400 Electronic Voting Session 10: Internet Voting Michael I. Shamos, Ph. D. , J. D. Institute for Software Research International Carnegie Mellon University
17 -803/17 -400 Electronic Voting Session 10: Internet Voting Michael I. Shamos, Ph. D. , J. D. Institute for Software Research International Carnegie Mellon University
 Outline • • Internet voting issues SENSUS (Lorrie Cranor) Project SERVE Canton of Geneva, Switzerland 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Outline • • Internet voting issues SENSUS (Lorrie Cranor) Project SERVE Canton of Geneva, Switzerland 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Internet Voting • Where? – – Polling place Kiosks Home Anywhere 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Internet Voting • Where? – – Polling place Kiosks Home Anywhere 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Internet Voting Benefits • Convenience – Accessibility in all weather, all ages – Vote anywhere, maybe even from cellphone – Availability of candidate information • Maybe lower operating cost (maybe not) – if regular polling places are eliminated 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Internet Voting Benefits • Convenience – Accessibility in all weather, all ages – Vote anywhere, maybe even from cellphone – Availability of candidate information • Maybe lower operating cost (maybe not) – if regular polling places are eliminated 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Internet Voting Risks • Digital divide – People without Internet access – People without computer skills • Security, trust • Casual environment • Open to the world 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Internet Voting Risks • Digital divide – People without Internet access – People without computer skills • Security, trust • Casual environment • Open to the world 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Internet Voting Security Risks • • Bugs Backdoors to manipulation Malicious code COTS (Commercial Off-the-Shelf Software), e. g. Windows, may contain exploits • Insider attacks – Compromising results – Compromising privacy • Client attacks – Operator (for Internet cafes) – Worms, viruses, Active. X, spyware 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Internet Voting Security Risks • • Bugs Backdoors to manipulation Malicious code COTS (Commercial Off-the-Shelf Software), e. g. Windows, may contain exploits • Insider attacks – Compromising results – Compromising privacy • Client attacks – Operator (for Internet cafes) – Worms, viruses, Active. X, spyware 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Internet Voting Security Risks • Denial of Service – DDOS attacks on server – Selective disenfranchisement • Spoof websites – Fake “official” site – captures voting credentials, issues fake acknowledgement, then casts real vote differently • Promotion of coercion – Automated credential-selling – Installation of watcher software 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Internet Voting Security Risks • Denial of Service – DDOS attacks on server – Selective disenfranchisement • Spoof websites – Fake “official” site – captures voting credentials, issues fake acknowledgement, then casts real vote differently • Promotion of coercion – Automated credential-selling – Installation of watcher software 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
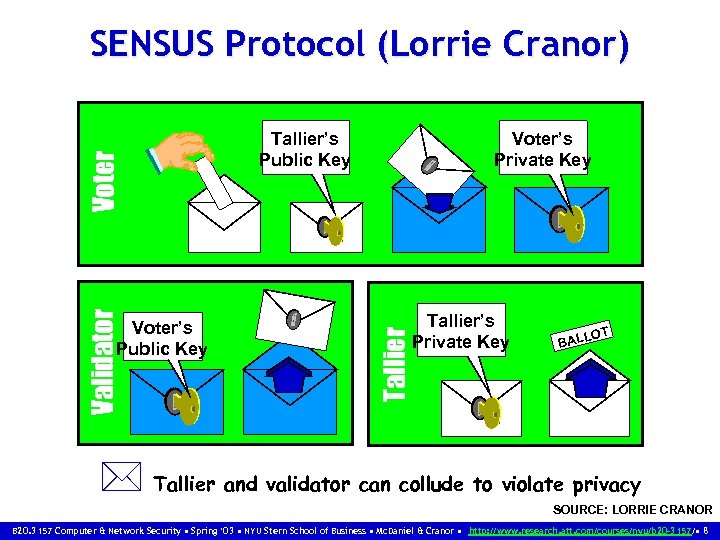 Voter’s Private Key Tallier Voter’s Public Key OT Validator Tallier’s Public Key LL BA Voter SENSUS Protocol (Lorrie Cranor) Tallier’s Private Key T O BALL * Tallier and validator can collude to violate privacy SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 8
Voter’s Private Key Tallier Voter’s Public Key OT Validator Tallier’s Public Key LL BA Voter SENSUS Protocol (Lorrie Cranor) Tallier’s Private Key T O BALL * Tallier and validator can collude to violate privacy SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 8
 Blind Signatures (Chaum) n Sometimes useful to have people sign things without seeing what they are signing « notarizing confidential documents « preserving anonymity n Alice wants to have Bob sign message M. (In cryptography, a message is just a number. ) n Alice multiplies M by a number -- the blinding factor n Alice sends the blinded message to Bob. He can’t read it -- it’s blinded. n Bob signs with his private key, sends it back to Alice. n Alice divides out the blinding factor. She now has M signed by Bob. B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 9
Blind Signatures (Chaum) n Sometimes useful to have people sign things without seeing what they are signing « notarizing confidential documents « preserving anonymity n Alice wants to have Bob sign message M. (In cryptography, a message is just a number. ) n Alice multiplies M by a number -- the blinding factor n Alice sends the blinded message to Bob. He can’t read it -- it’s blinded. n Bob signs with his private key, sends it back to Alice. n Alice divides out the blinding factor. She now has M signed by Bob. B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 9
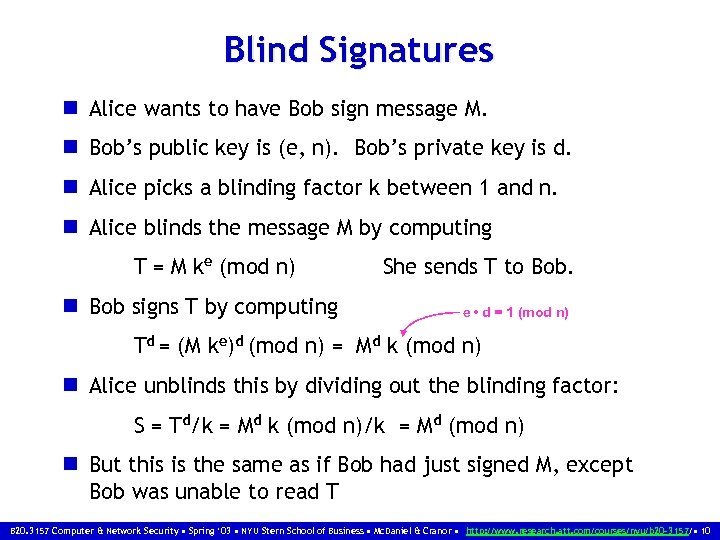 Blind Signatures n Alice wants to have Bob sign message M. n Bob’s public key is (e, n). Bob’s private key is d. n Alice picks a blinding factor k between 1 and n. n Alice blinds the message M by computing T = M ke (mod n) n Bob signs T by computing She sends T to Bob. e • d = 1 (mod n) Td = (M ke)d (mod n) = Md k (mod n) n Alice unblinds this by dividing out the blinding factor: S = Td/k = Md k (mod n)/k = Md (mod n) n But this is the same as if Bob had just signed M, except Bob was unable to read T B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 10
Blind Signatures n Alice wants to have Bob sign message M. n Bob’s public key is (e, n). Bob’s private key is d. n Alice picks a blinding factor k between 1 and n. n Alice blinds the message M by computing T = M ke (mod n) n Bob signs T by computing She sends T to Bob. e • d = 1 (mod n) Td = (M ke)d (mod n) = Md k (mod n) n Alice unblinds this by dividing out the blinding factor: S = Td/k = Md k (mod n)/k = Md (mod n) n But this is the same as if Bob had just signed M, except Bob was unable to read T B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 10
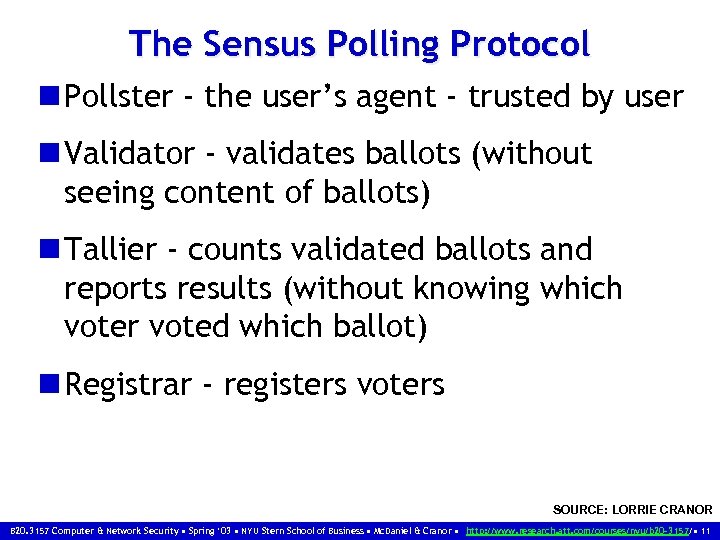 The Sensus Polling Protocol n Pollster - the user’s agent - trusted by user n Validator - validates ballots (without seeing content of ballots) n Tallier - counts validated ballots and reports results (without knowing which voter voted which ballot) n Registrar - registers voters SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 11
The Sensus Polling Protocol n Pollster - the user’s agent - trusted by user n Validator - validates ballots (without seeing content of ballots) n Tallier - counts validated ballots and reports results (without knowing which voter voted which ballot) n Registrar - registers voters SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 11
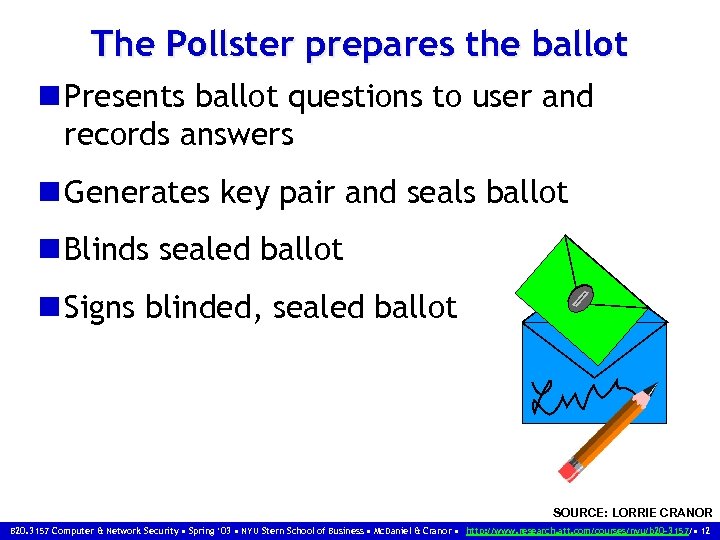 The Pollster prepares the ballot n Presents ballot questions to user and records answers n Generates key pair and seals ballot n Blinds sealed ballot n Signs blinded, sealed ballot SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 12
The Pollster prepares the ballot n Presents ballot questions to user and records answers n Generates key pair and seals ballot n Blinds sealed ballot n Signs blinded, sealed ballot SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 12
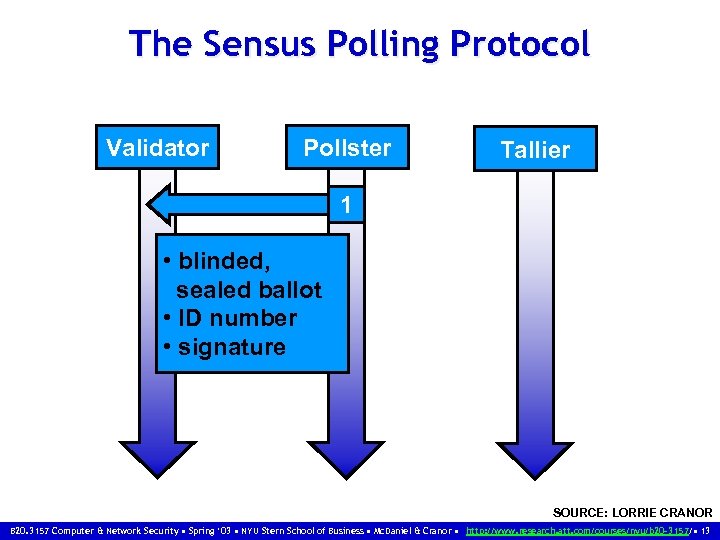 The Sensus Polling Protocol Validator Pollster Tallier 1 • blinded, sealed ballot • ID number • signature SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 13
The Sensus Polling Protocol Validator Pollster Tallier 1 • blinded, sealed ballot • ID number • signature SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 13
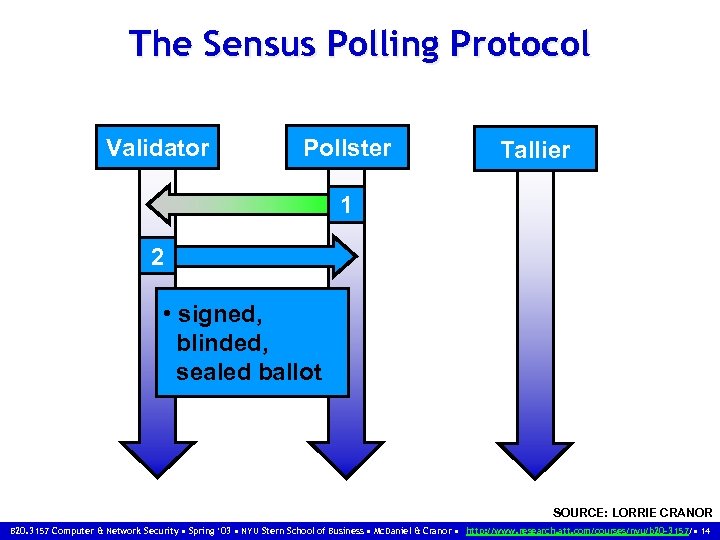 The Sensus Polling Protocol Validator Pollster Tallier 1 2 • signed, blinded, sealed ballot SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 14
The Sensus Polling Protocol Validator Pollster Tallier 1 2 • signed, blinded, sealed ballot SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 14
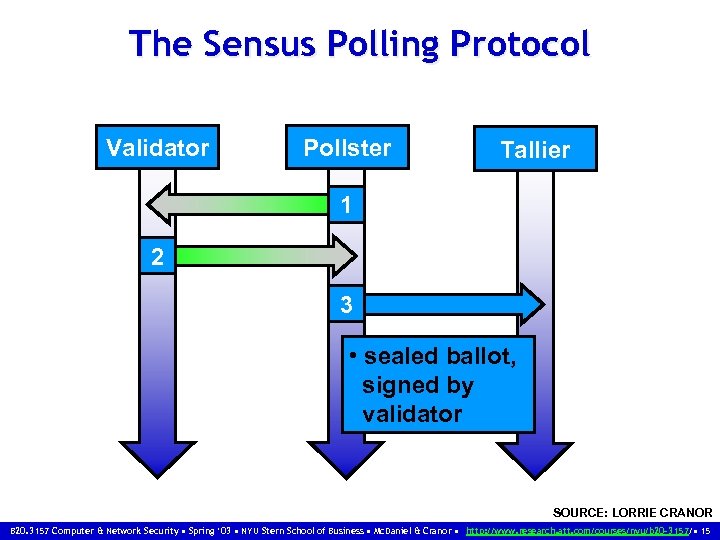 The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 • sealed ballot, signed by validator SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 15
The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 • sealed ballot, signed by validator SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 15
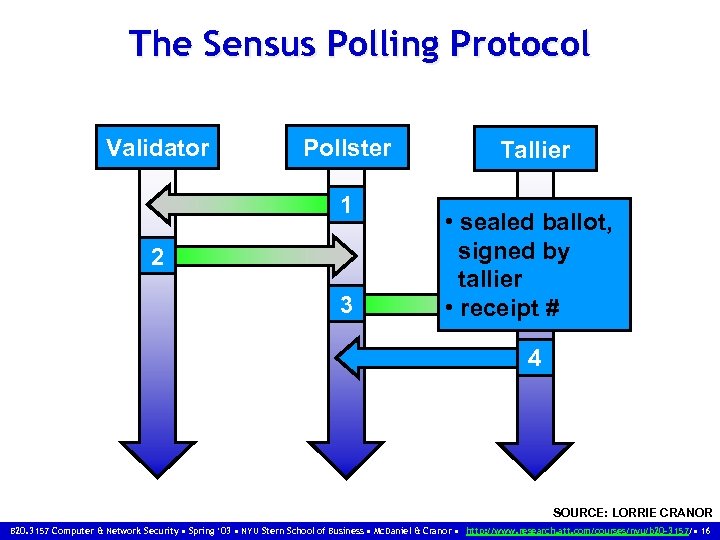 The Sensus Polling Protocol Validator Pollster 1 2 3 Tallier • sealed ballot, signed by tallier • receipt # 4 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 16
The Sensus Polling Protocol Validator Pollster 1 2 3 Tallier • sealed ballot, signed by tallier • receipt # 4 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 16
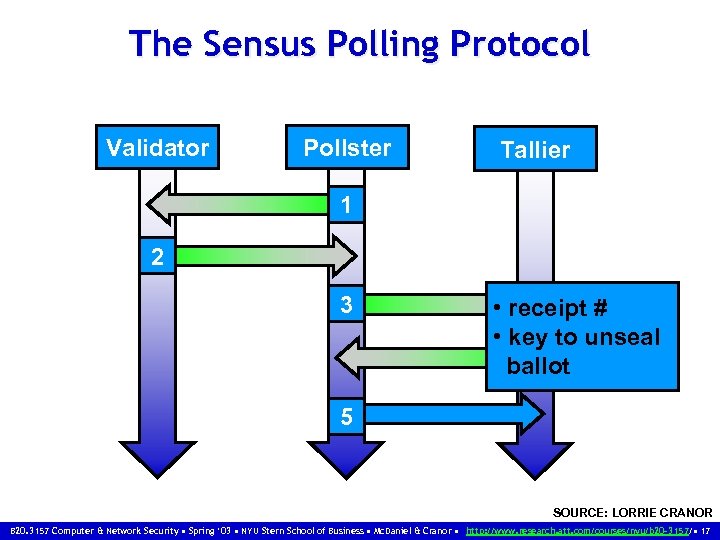 The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 • receipt # • key to unseal 4 ballot 5 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 17
The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 • receipt # • key to unseal 4 ballot 5 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 17
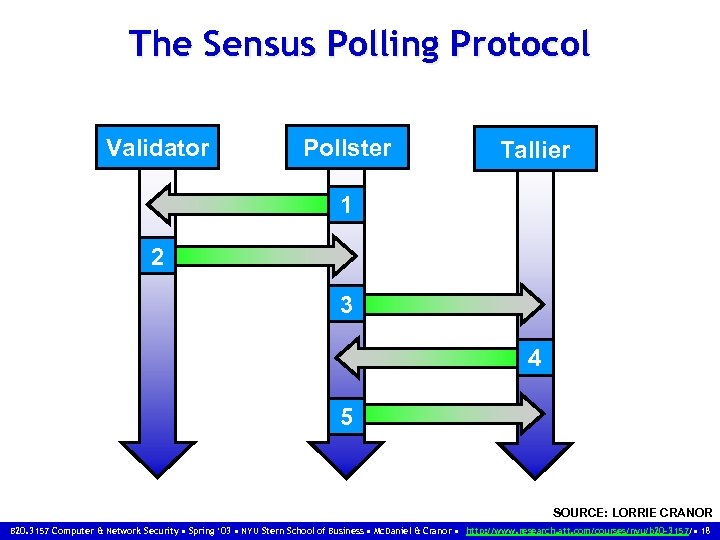 The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 4 5 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 18
The Sensus Polling Protocol Validator Pollster Tallier 1 2 3 4 5 SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 18
 Sensus assumptions n Communication occurs over an anonymous channel n Machines (along with secrets on them) are secure (including users’ machines!) n Messages are not likely to arrive at validator and tallier in the same order n Strong encryption n Election is not disrupted due to denial of service attacks, power outages, etc. Can we count on these assumptions to be true? SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 19
Sensus assumptions n Communication occurs over an anonymous channel n Machines (along with secrets on them) are secure (including users’ machines!) n Messages are not likely to arrive at validator and tallier in the same order n Strong encryption n Election is not disrupted due to denial of service attacks, power outages, etc. Can we count on these assumptions to be true? SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 19
 Even if these assumptions hold n If voters abstain, validator may submit ballots for them «These invalid ballots may be detected, but not corrected n Voters can prove how they voted (and sell their votes) n Only weak verifiability (voters can verify their votes but not third-party) SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 20
Even if these assumptions hold n If voters abstain, validator may submit ballots for them «These invalid ballots may be detected, but not corrected n Voters can prove how they voted (and sell their votes) n Only weak verifiability (voters can verify their votes but not third-party) SOURCE: LORRIE CRANOR B 20. 3157 Computer & Network Security • Spring ‘ 03 • NYU Stern School of Business • Mc. Daniel & Cranor • http: //www. research. att. com/courses/nyu/b 20 -3157/ • 20
 Project SERVE • About 5, 000 citizens are eligible to vote but cannot because – they are unable to comply with absentee voting requirements – they are physically unable to cast votes because of circumstances (military service) • This is almost 5% of voters • To address this, Congress passed UOCAVA, the Uniformed and Overseas Citizens Absentee Voting Act 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Project SERVE • About 5, 000 citizens are eligible to vote but cannot because – they are unable to comply with absentee voting requirements – they are physically unable to cast votes because of circumstances (military service) • This is almost 5% of voters • To address this, Congress passed UOCAVA, the Uniformed and Overseas Citizens Absentee Voting Act 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 UOCAVA 42 U. S. C. 1973 ff • Each State shall— • (1) permit absent uniformed services voters and overseas voters to use absentee registration procedures and to vote by absentee ballot in general, special, primary, and runoff elections for Federal office; • (2) accept and process … any otherwise valid voter registration application and absentee ballot application from an absent uniformed services voter or overseas voter, if … received … not less than 30 days before the election; • (3) permit overseas voters to use Federal write-in absentee ballots … in general elections for Federal office; and • (4) use the official post card form (prescribed under … this title) for simultaneous voter registration application and absentee ballot application. 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
UOCAVA 42 U. S. C. 1973 ff • Each State shall— • (1) permit absent uniformed services voters and overseas voters to use absentee registration procedures and to vote by absentee ballot in general, special, primary, and runoff elections for Federal office; • (2) accept and process … any otherwise valid voter registration application and absentee ballot application from an absent uniformed services voter or overseas voter, if … received … not less than 30 days before the election; • (3) permit overseas voters to use Federal write-in absentee ballots … in general elections for Federal office; and • (4) use the official post card form (prescribed under … this title) for simultaneous voter registration application and absentee ballot application. 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Congressional Mandate § 1604 FY 02 National Defense Authorization Act Ø Do. D to carry out an electronic voting demonstration project through Federal Voting Assistance Program (FVAP) • Absentee Uniformed Services voters • November 2002 or 2004 general election • Participation of sufficient numbers so results are statistically relevant • Coordinate with state election officials Ø Report to Congress (June 2005)
Congressional Mandate § 1604 FY 02 National Defense Authorization Act Ø Do. D to carry out an electronic voting demonstration project through Federal Voting Assistance Program (FVAP) • Absentee Uniformed Services voters • November 2002 or 2004 general election • Participation of sufficient numbers so results are statistically relevant • Coordinate with state election officials Ø Report to Congress (June 2005)
 Do. D Response Ø Include all absentee Uniformed Services and overseas citizens Ø Target of 100, 000 voters, cross-section of election jurisdictions Ø 7 states (out of 50), 51 counties (out of 3140) Ø Use electronic system beginning January 2004 for voter registration, voting in primaries and general election Ø Killed in February 2004 by Deputy Defense Secretary Wolfowitz after an essay by four computer scientists
Do. D Response Ø Include all absentee Uniformed Services and overseas citizens Ø Target of 100, 000 voters, cross-section of election jurisdictions Ø 7 states (out of 50), 51 counties (out of 3140) Ø Use electronic system beginning January 2004 for voter registration, voting in primaries and general election Ø Killed in February 2004 by Deputy Defense Secretary Wolfowitz after an essay by four computer scientists
 Evaluation Questions Ø Is remote Internet registration and voting an effective, affordable and secure method to improve absentee uniformed services and overseas citizens’ access to the polls? Ø What do we need to know to implement this type of system as an alternative to by-mail?
Evaluation Questions Ø Is remote Internet registration and voting an effective, affordable and secure method to improve absentee uniformed services and overseas citizens’ access to the polls? Ø What do we need to know to implement this type of system as an alternative to by-mail?
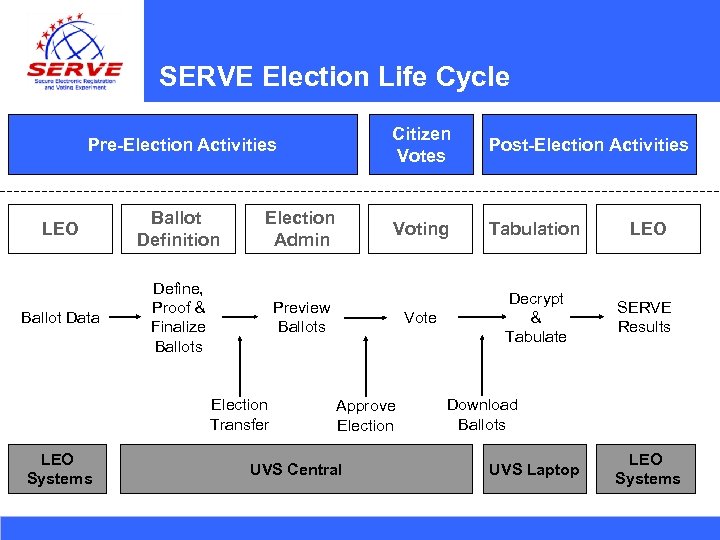 SERVE Election Life Cycle Pre-Election Activities Citizen Votes Post-Election Activities LEO Ballot Definition Election Admin Voting Tabulation LEO Ballot Data Define, Proof & Finalize Ballots Preview Ballots Vote Decrypt & Tabulate SERVE Results Election Transfer LEO Systems Approve Election UVS Central Download Ballots UVS Laptop LEO Systems
SERVE Election Life Cycle Pre-Election Activities Citizen Votes Post-Election Activities LEO Ballot Definition Election Admin Voting Tabulation LEO Ballot Data Define, Proof & Finalize Ballots Preview Ballots Vote Decrypt & Tabulate SERVE Results Election Transfer LEO Systems Approve Election UVS Central Download Ballots UVS Laptop LEO Systems
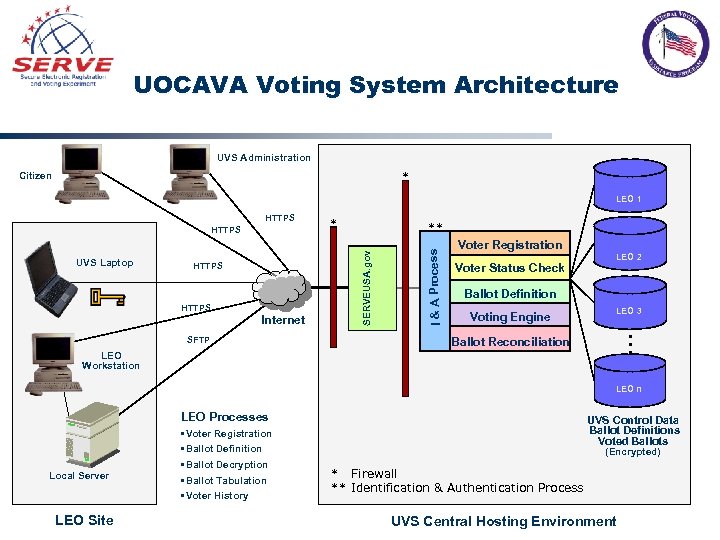 UOCAVA Voting System Architecture UVS Administration * Citizen LEO 1 HTTPS ** Web Server HTTPS Internet Voter Registration Voter Status Check LEO 2 Ballot Definition Voting Engine LEO 3 … SFTP I & A Process UVS Laptop * SERVEUSA. gov HTTPS Ballot Reconciliation LEO Workstation LEO n LEO Processes Local Server LEO Site • Voter Registration • Ballot Definition • Ballot Decryption • Ballot Tabulation • Voter History UVS Control Data Ballot Definitions Voted Ballots (Encrypted) * Firewall ** Identification & Authentication Process UVS Central Hosting Environment
UOCAVA Voting System Architecture UVS Administration * Citizen LEO 1 HTTPS ** Web Server HTTPS Internet Voter Registration Voter Status Check LEO 2 Ballot Definition Voting Engine LEO 3 … SFTP I & A Process UVS Laptop * SERVEUSA. gov HTTPS Ballot Reconciliation LEO Workstation LEO n LEO Processes Local Server LEO Site • Voter Registration • Ballot Definition • Ballot Decryption • Ballot Tabulation • Voter History UVS Control Data Ballot Definitions Voted Ballots (Encrypted) * Firewall ** Identification & Authentication Process UVS Central Hosting Environment
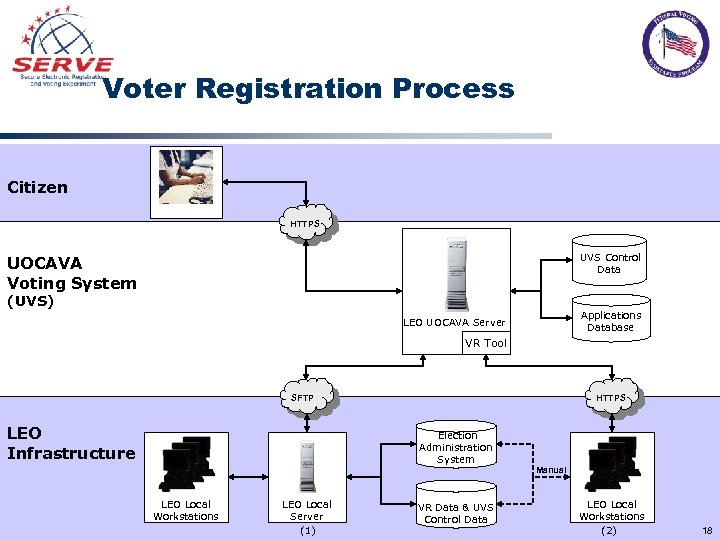 Voter Registration Process Citizen HTTPS UVS Control Data UOCAVA Voting System (UVS) Applications Database LEO UOCAVA Server VR Tool SFTP LEO Infrastructure HTTPS Election Administration System LEO Local Workstations LEO Local Server (1) VR Data & UVS Control Data Manual LEO Local Workstations (2) 18
Voter Registration Process Citizen HTTPS UVS Control Data UOCAVA Voting System (UVS) Applications Database LEO UOCAVA Server VR Tool SFTP LEO Infrastructure HTTPS Election Administration System LEO Local Workstations LEO Local Server (1) VR Data & UVS Control Data Manual LEO Local Workstations (2) 18
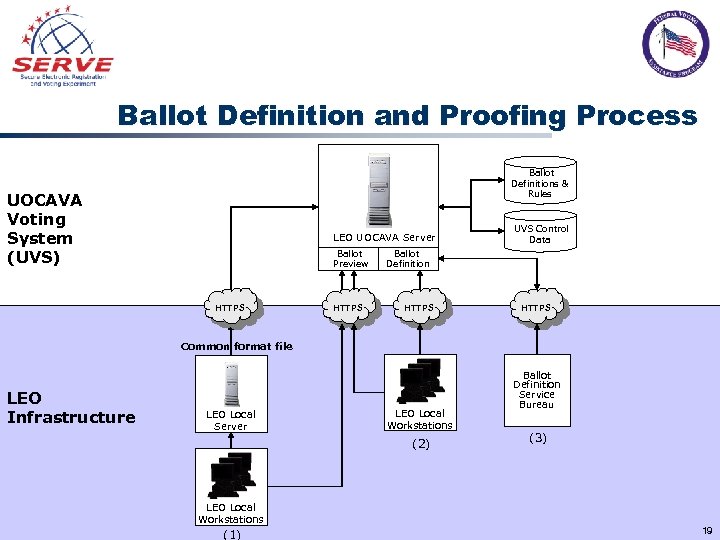 Ballot Definition and Proofing Process Ballot Definitions & Rules UOCAVA Voting System (UVS) LEO UOCAVA Server Ballot Preview HTTPS UVS Control Data Ballot Definition HTTPS Common format file LEO Infrastructure LEO Local Server LEO Local Workstations (2) Ballot Definition Service Bureau (3) LEO Local Workstations (1) 19
Ballot Definition and Proofing Process Ballot Definitions & Rules UOCAVA Voting System (UVS) LEO UOCAVA Server Ballot Preview HTTPS UVS Control Data Ballot Definition HTTPS Common format file LEO Infrastructure LEO Local Server LEO Local Workstations (2) Ballot Definition Service Bureau (3) LEO Local Workstations (1) 19
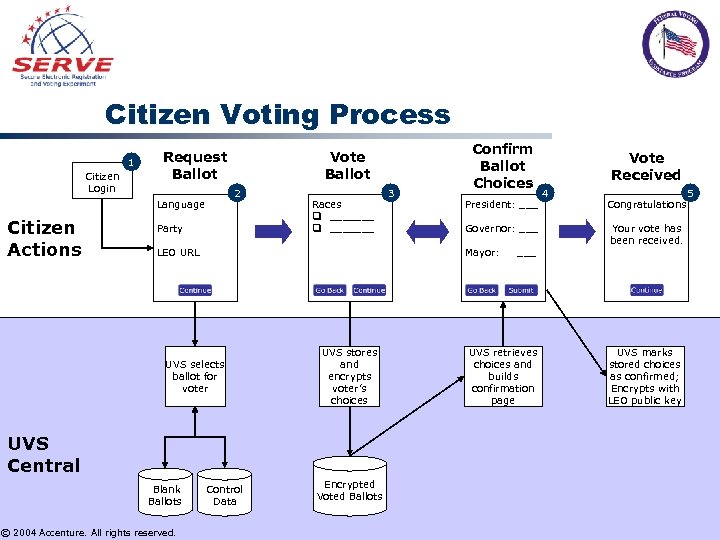 Citizen Voting Process 1 Citizen Login Request Ballot 2 Language Citizen Actions Vote Ballot Party Races q _______ LEO URL UVS stores and encrypts voter’s choices UVS Central © 2004 Accenture. All rights reserved. President: ___ Governor: ___ Mayor: UVS selects ballot for voter Blank Ballots 3 Confirm Ballot Choices Control Data Encrypted Voted Ballots ___ UVS retrieves choices and builds confirmation page Vote Received 4 Congratulations Your vote has been received. UVS marks stored choices as confirmed; Encrypts with LEO public key 5
Citizen Voting Process 1 Citizen Login Request Ballot 2 Language Citizen Actions Vote Ballot Party Races q _______ LEO URL UVS stores and encrypts voter’s choices UVS Central © 2004 Accenture. All rights reserved. President: ___ Governor: ___ Mayor: UVS selects ballot for voter Blank Ballots 3 Confirm Ballot Choices Control Data Encrypted Voted Ballots ___ UVS retrieves choices and builds confirmation page Vote Received 4 Congratulations Your vote has been received. UVS marks stored choices as confirmed; Encrypts with LEO public key 5
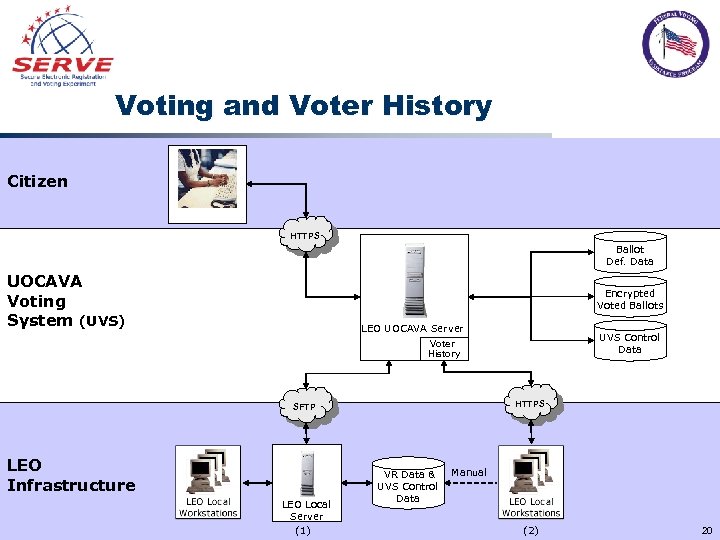 Voting and Voter History Citizen HTTPS Ballot Def. Data UOCAVA Voting System (UVS) Encrypted Voted Ballots LEO UOCAVA Server UVS Control Data Voter History HTTPS SFTP LEO Infrastructure LEO Local Server (1) VR Data & UVS Control Data Manual (2) 20
Voting and Voter History Citizen HTTPS Ballot Def. Data UOCAVA Voting System (UVS) Encrypted Voted Ballots LEO UOCAVA Server UVS Control Data Voter History HTTPS SFTP LEO Infrastructure LEO Local Server (1) VR Data & UVS Control Data Manual (2) 20
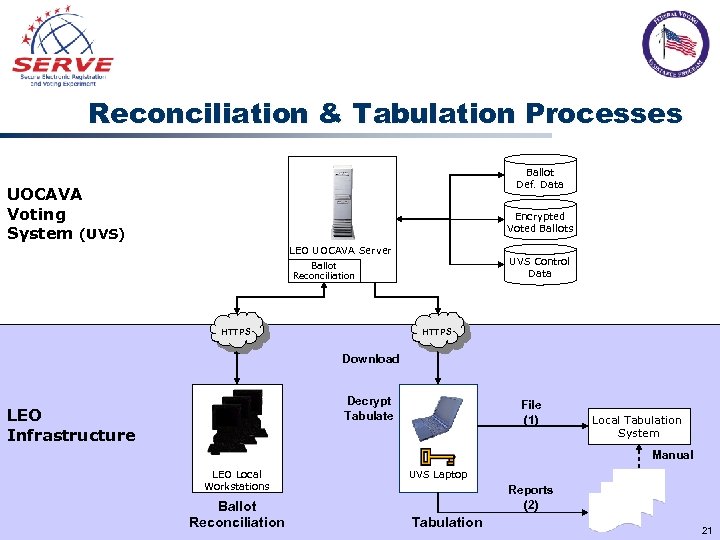 Reconciliation & Tabulation Processes Ballot Def. Data UOCAVA Voting System (UVS) Encrypted Voted Ballots LEO UOCAVA Server UVS Control Data Ballot Reconciliation HTTPS Download Decrypt Tabulate LEO Infrastructure File (1) Local Tabulation System Manual LEO Local Workstations Ballot Reconciliation UVS Laptop Reports (2) Tabulation 21
Reconciliation & Tabulation Processes Ballot Def. Data UOCAVA Voting System (UVS) Encrypted Voted Ballots LEO UOCAVA Server UVS Control Data Ballot Reconciliation HTTPS Download Decrypt Tabulate LEO Infrastructure File (1) Local Tabulation System Manual LEO Local Workstations Ballot Reconciliation UVS Laptop Reports (2) Tabulation 21
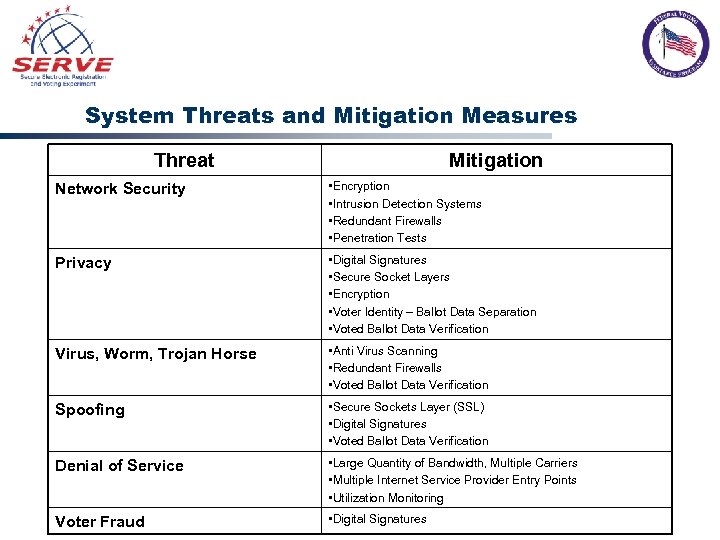 System Threats and Mitigation Measures Threat Mitigation Network Security • Encryption • Intrusion Detection Systems • Redundant Firewalls • Penetration Tests Privacy • Digital Signatures • Secure Socket Layers • Encryption • Voter Identity – Ballot Data Separation • Voted Ballot Data Verification Virus, Worm, Trojan Horse • Anti Virus Scanning • Redundant Firewalls • Voted Ballot Data Verification Spoofing • Secure Sockets Layer (SSL) • Digital Signatures • Voted Ballot Data Verification Denial of Service • Large Quantity of Bandwidth, Multiple Carriers • Multiple Internet Service Provider Entry Points • Utilization Monitoring Voter Fraud • Digital Signatures
System Threats and Mitigation Measures Threat Mitigation Network Security • Encryption • Intrusion Detection Systems • Redundant Firewalls • Penetration Tests Privacy • Digital Signatures • Secure Socket Layers • Encryption • Voter Identity – Ballot Data Separation • Voted Ballot Data Verification Virus, Worm, Trojan Horse • Anti Virus Scanning • Redundant Firewalls • Voted Ballot Data Verification Spoofing • Secure Sockets Layer (SSL) • Digital Signatures • Voted Ballot Data Verification Denial of Service • Large Quantity of Bandwidth, Multiple Carriers • Multiple Internet Service Provider Entry Points • Utilization Monitoring Voter Fraud • Digital Signatures
 UVS Security Features Ø Digital signatures for authentication of all users Ø Centralized servers host all processes except ballot decryption and tabulation Ø All voted ballot data encrypted Ø Applications and data completely enveloped by layers of physical security, disaster recovery, network and denial of service mitigations Ø External peer review and critique of security architecture
UVS Security Features Ø Digital signatures for authentication of all users Ø Centralized servers host all processes except ballot decryption and tabulation Ø All voted ballot data encrypted Ø Applications and data completely enveloped by layers of physical security, disaster recovery, network and denial of service mitigations Ø External peer review and critique of security architecture
 Personal Digital Signatures Ø Issued to all SERVE participants (citizens, LEOs, system administrators) Ø Medium assurance (X. 509 compliant) Ø Stored on server for portability Ø Citizen must remember password and challenge question Ø Provides audit trail of all participant transactions
Personal Digital Signatures Ø Issued to all SERVE participants (citizens, LEOs, system administrators) Ø Medium assurance (X. 509 compliant) Ø Stored on server for portability Ø Citizen must remember password and challenge question Ø Provides audit trail of all participant transactions
 Critique of SERVE • Jefferson, Rubin, Simons, Wagner were four of nine members of the SERVE Project Review Group. Their points: • DRE systems have been criticized • SERVE is Internet- and PC-based • Vulnerable to large-scale attacks by parties outside the reach of U. S. law • Impossible to estimate the probability of a successful attack • Vulnerabilities cannot be fixed by redesign of SERVE, but are fundamental to the Internet architecture • Even if SERVE worked flawlessly in a 2004 experiment would not mean it was safe • We recommend shutting down SERVE development immediately 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Critique of SERVE • Jefferson, Rubin, Simons, Wagner were four of nine members of the SERVE Project Review Group. Their points: • DRE systems have been criticized • SERVE is Internet- and PC-based • Vulnerable to large-scale attacks by parties outside the reach of U. S. law • Impossible to estimate the probability of a successful attack • Vulnerabilities cannot be fixed by redesign of SERVE, but are fundamental to the Internet architecture • Even if SERVE worked flawlessly in a 2004 experiment would not mean it was safe • We recommend shutting down SERVE development immediately 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
 Michel Chevallier Head of communication Geneva State Internet voting project Internet voting : Status, Perspectives and Issues ITU E-Government workshop Geneva 6 June 2003 Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 37
Michel Chevallier Head of communication Geneva State Internet voting project Internet voting : Status, Perspectives and Issues ITU E-Government workshop Geneva 6 June 2003 Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 37
 Geneva developed one of the first public Internet voting applications in the world. Held first ballot using the Internet in January 2003, in a suburban municipality nearby Geneva. Voters had three ways to casting ballot: postal voting, polling stations and the Internet. ~200, 000 registered voters in Geneva Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 38
Geneva developed one of the first public Internet voting applications in the world. Held first ballot using the Internet in January 2003, in a suburban municipality nearby Geneva. Voters had three ways to casting ballot: postal voting, polling stations and the Internet. ~200, 000 registered voters in Geneva Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 38
 Transition Stages in Internet Voting EVE ( «Evaluating Practices & Validating technologies in E-democracy» , www. eve. cnrs. fr/) showed Internet voting is mostly considered by countries that have already implemented changes in polling methods: placing electronic ballot boxes in polling stations, introducing postal voting, using the Internet as political campaign tool. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 39
Transition Stages in Internet Voting EVE ( «Evaluating Practices & Validating technologies in E-democracy» , www. eve. cnrs. fr/) showed Internet voting is mostly considered by countries that have already implemented changes in polling methods: placing electronic ballot boxes in polling stations, introducing postal voting, using the Internet as political campaign tool. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 39
 Role of Political System Political system plays a role in the decision to develop an Internet voting application. Not a coincidence that the two leading countries in Internet voting, UK and Switzerland, are decentralized States. Secrecy is not equally important everywhere. The more stringent the law on secrecy, the more difficult the implementation of Internet voting. UK and Switzerland have «soft» regulations. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 40
Role of Political System Political system plays a role in the decision to develop an Internet voting application. Not a coincidence that the two leading countries in Internet voting, UK and Switzerland, are decentralized States. Secrecy is not equally important everywhere. The more stringent the law on secrecy, the more difficult the implementation of Internet voting. UK and Switzerland have «soft» regulations. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 40
 Swiss Voters Want Versatilityto 6 times a Swiss citizens are vote 4 year Postal voting in 22 of 26 Swiss cantons In Geneva last year, 95% of the voters cast their vote by post. Nationwide, the percentage exceeds 50%. In Geneva, postal voting has increased the turnout by 20 percentage points over the last 8 years (from an average of 30%-35% to an average of 50%-55%). Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 41
Swiss Voters Want Versatilityto 6 times a Swiss citizens are vote 4 year Postal voting in 22 of 26 Swiss cantons In Geneva last year, 95% of the voters cast their vote by post. Nationwide, the percentage exceeds 50%. In Geneva, postal voting has increased the turnout by 20 percentage points over the last 8 years (from an average of 30%-35% to an average of 50%-55%). Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 41
 Consolidating a positive trend In a everchanging world, you must innovate to maintain your position. This is also true of public services. We were looking for a way of consolidating the success of postal voting and increasing ballot flexibility. We wanted to improve ballot access for citizens living abroad and disabled voters. We wanted to take better into account the habits of many citzens, who travel on week-ends and school holidays. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 42
Consolidating a positive trend In a everchanging world, you must innovate to maintain your position. This is also true of public services. We were looking for a way of consolidating the success of postal voting and increasing ballot flexibility. We wanted to improve ballot access for citizens living abroad and disabled voters. We wanted to take better into account the habits of many citzens, who travel on week-ends and school holidays. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 42
 Cost Is Internet voting cheaper? Ballot reading is automatic, no recounts are needed. Not necessarily ! Parameters influencing cost Will polling stations be eliminated ? Will smartcards be issued ? Should voters buy plug-in devices ? What is the cost of system maintenance ? How often will upgrades occur? Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 43
Cost Is Internet voting cheaper? Ballot reading is automatic, no recounts are needed. Not necessarily ! Parameters influencing cost Will polling stations be eliminated ? Will smartcards be issued ? Should voters buy plug-in devices ? What is the cost of system maintenance ? How often will upgrades occur? Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 43
 Conditions for a Democratic Ballot «Contracting parties undertake to hold free elections at reasonable intervals by secret ballot, under conditions which will ensure the free expression of the opinion of the people to rotocol 1 P (…)» (Art. 3 of ropean the Eu r man on on Hu Conventi hts) Rig Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 44
Conditions for a Democratic Ballot «Contracting parties undertake to hold free elections at reasonable intervals by secret ballot, under conditions which will ensure the free expression of the opinion of the people to rotocol 1 P (…)» (Art. 3 of ropean the Eu r man on on Hu Conventi hts) Rig Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 44
 11 Commandments of Internet Voting (1) The provisions of the European Convention on Human Rights and our own legal rules define a 11 points terms of reference for Internet voting : 1) Votes cannot be intercepted nor modified, 2) Votes cannot be known before the official ballot reading, 3) Only registered voters will be able to vote, 4) Each voter will have one and only one vote, 5) Vote secrecy is guaranteed. It NEVER will be possible to link a voter and his/her vote, Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 45
11 Commandments of Internet Voting (1) The provisions of the European Convention on Human Rights and our own legal rules define a 11 points terms of reference for Internet voting : 1) Votes cannot be intercepted nor modified, 2) Votes cannot be known before the official ballot reading, 3) Only registered voters will be able to vote, 4) Each voter will have one and only one vote, 5) Vote secrecy is guaranteed. It NEVER will be possible to link a voter and his/her vote, Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 45
 11 Commandments of Internet Voting (2) 6) The voting web site will resist any denial of service attack, 7) Voters will be protected against identity theft, 8) The number of cast votes will be equal to the number of received ballots, 9) It will be possible to prove that a given citizen has voted, 10) The system will not accept votes outside the ballot opening period, 11) The system will be auditable. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 46
11 Commandments of Internet Voting (2) 6) The voting web site will resist any denial of service attack, 7) Voters will be protected against identity theft, 8) The number of cast votes will be equal to the number of received ballots, 9) It will be possible to prove that a given citizen has voted, 10) The system will not accept votes outside the ballot opening period, 11) The system will be auditable. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 46
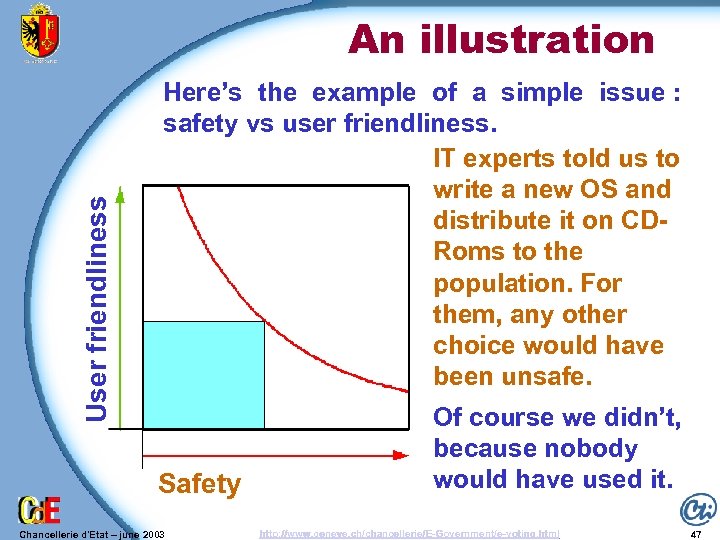 User friendliness An illustration Here’s the example of a simple issue : safety vs user friendliness. IT experts told us to write a new OS and distribute it on CDRoms to the population. For them, any other choice would have been unsafe. Safety Chancellerie d'Etat – june 2003 Of course we didn’t, because nobody would have used it. http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 47
User friendliness An illustration Here’s the example of a simple issue : safety vs user friendliness. IT experts told us to write a new OS and distribute it on CDRoms to the population. For them, any other choice would have been unsafe. Safety Chancellerie d'Etat – june 2003 Of course we didn’t, because nobody would have used it. http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 47
 An idea whose time has come In 2000, we felt that the public was receptive to Internet voting : Internet connectivity had been growing steadily for a few years, e. Commerce turnover grew significantly, Poll conducted in the whole country showed 66% of Internet users would like to be able to vote online, Parliament reversed a previous negative vote and asked for Internet voting to be studied, The Geneva electoral law allows e. Voting testing without prior local Parliament approval, Geneva’s voters register was the only one in Switzerland already digitized. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 48
An idea whose time has come In 2000, we felt that the public was receptive to Internet voting : Internet connectivity had been growing steadily for a few years, e. Commerce turnover grew significantly, Poll conducted in the whole country showed 66% of Internet users would like to be able to vote online, Parliament reversed a previous negative vote and asked for Internet voting to be studied, The Geneva electoral law allows e. Voting testing without prior local Parliament approval, Geneva’s voters register was the only one in Switzerland already digitized. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 48
 A proprietary solution In 2000, the State issued a tender to seek private partners to realize the e. Voting application. Hewlett-Packard and Wisekey (digital certificate) were choosen as partners. The tender underlined the legal requirements for ballots, proposed a structure for the system, imposed that the servers should be located in a secured environment, within the State premises, Imposed that the application’s code should be available for independent experts to check (proprietary solution owned by the State). (www. geneve. ch/chancellerie/E-Government/cahier_charges. html#3) Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 49
A proprietary solution In 2000, the State issued a tender to seek private partners to realize the e. Voting application. Hewlett-Packard and Wisekey (digital certificate) were choosen as partners. The tender underlined the legal requirements for ballots, proposed a structure for the system, imposed that the servers should be located in a secured environment, within the State premises, Imposed that the application’s code should be available for independent experts to check (proprietary solution owned by the State). (www. geneve. ch/chancellerie/E-Government/cahier_charges. html#3) Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 49
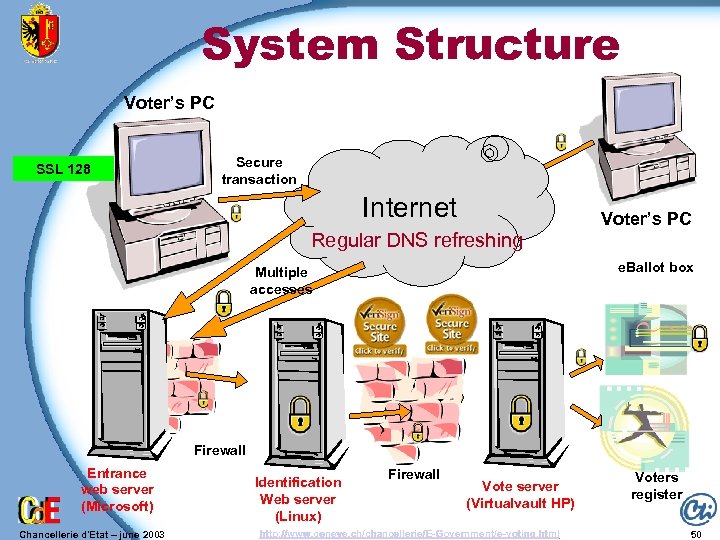 System Structure Voter’s PC SSL 128 Secure transaction Internet Regular DNS refreshing Voter’s PC e. Ballot box Multiple accesses Firewall Entrance web server (Microsoft) Chancellerie d'Etat – june 2003 Identification Web server (Linux) Firewall Vote server (Virtualvault HP) http: //www. geneve. ch/chancellerie/E-Government/e-voting. html Voters register 50
System Structure Voter’s PC SSL 128 Secure transaction Internet Regular DNS refreshing Voter’s PC e. Ballot box Multiple accesses Firewall Entrance web server (Microsoft) Chancellerie d'Etat – june 2003 Identification Web server (Linux) Firewall Vote server (Virtualvault HP) http: //www. geneve. ch/chancellerie/E-Government/e-voting. html Voters register 50
 No Man-in-the-Middle Attack Each voting card carries a personal code (besides the hidden identification one): 7425 in this example When the system confirms your vote, it displays the code underneath the vote Besides giving the voters the possibility to check the sites’ certificate fingerprint, we introduced a personal code on the e. Ballot. If you don’t see this code, you must stop the connection and call our helpdesk Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 51
No Man-in-the-Middle Attack Each voting card carries a personal code (besides the hidden identification one): 7425 in this example When the system confirms your vote, it displays the code underneath the vote Besides giving the voters the possibility to check the sites’ certificate fingerprint, we introduced a personal code on the e. Ballot. If you don’t see this code, you must stop the connection and call our helpdesk Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 51
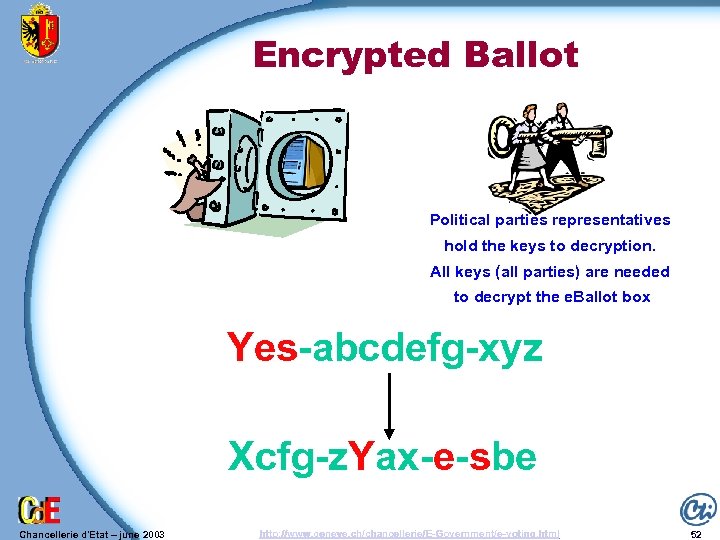 Encrypted Ballot Political parties representatives hold the keys to decryption. All keys (all parties) are needed to decrypt the e. Ballot box Yes-abcdefg-xyz Xcfg-z. Yax-e-sbe Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 52
Encrypted Ballot Political parties representatives hold the keys to decryption. All keys (all parties) are needed to decrypt the e. Ballot box Yes-abcdefg-xyz Xcfg-z. Yax-e-sbe Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 52
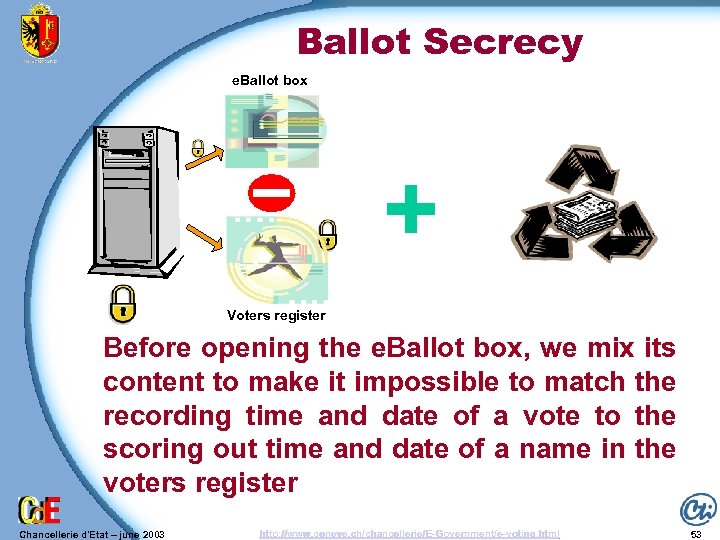 Ballot Secrecy e. Ballot box + Voters register Before opening the e. Ballot box, we mix its content to make it impossible to match the recording time and date of a vote to the scoring out time and date of a name in the voters register Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 53
Ballot Secrecy e. Ballot box + Voters register Before opening the e. Ballot box, we mix its content to make it impossible to match the recording time and date of a vote to the scoring out time and date of a name in the voters register Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 53
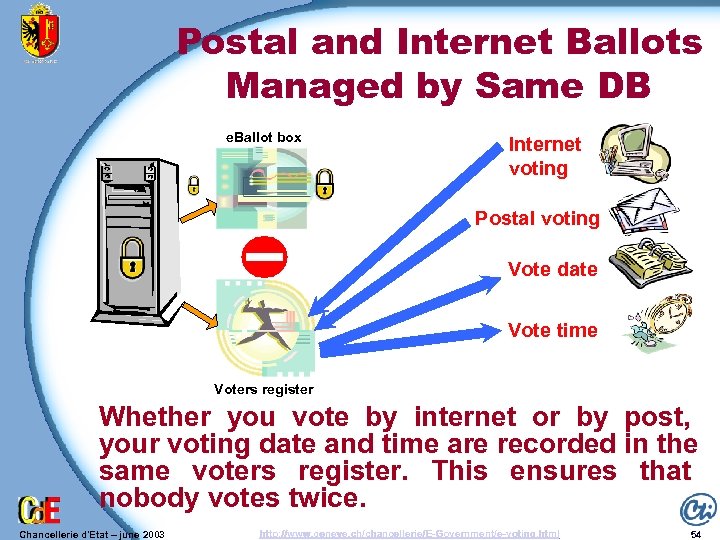 Postal and Internet Ballots Managed by Same DB e. Ballot box Internet voting Postal voting Vote date Vote time Voters register Whether you vote by internet or by post, your voting date and time are recorded in the same voters register. This ensures that nobody votes twice. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 54
Postal and Internet Ballots Managed by Same DB e. Ballot box Internet voting Postal voting Vote date Vote time Voters register Whether you vote by internet or by post, your voting date and time are recorded in the same voters register. This ensures that nobody votes twice. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 54
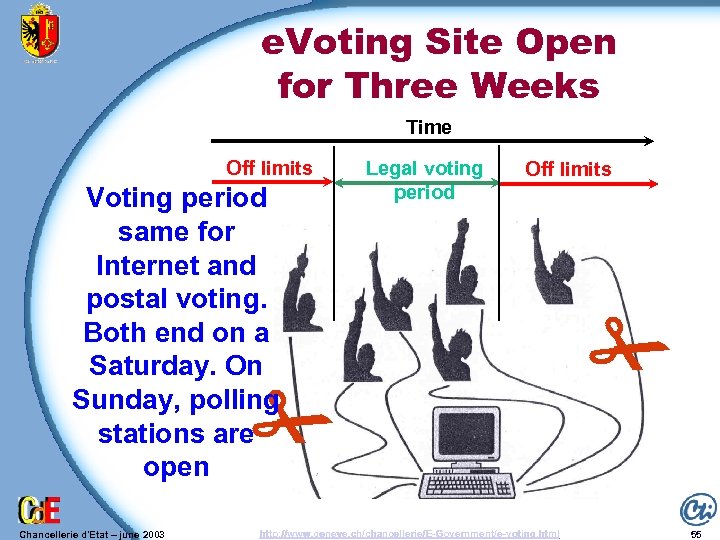 e. Voting Site Open for Three Weeks Time Off limits Voting period same for Internet and postal voting. Both end on a Saturday. On Sunday, polling stations are open Legal voting period Off limits Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 55
e. Voting Site Open for Three Weeks Time Off limits Voting period same for Internet and postal voting. Both end on a Saturday. On Sunday, polling stations are open Legal voting period Off limits Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 55
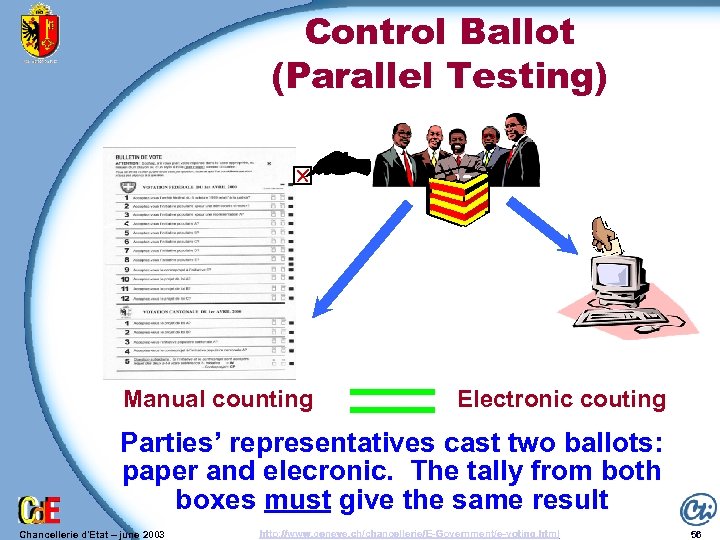 Control Ballot (Parallel Testing) Manual counting Electronic couting Parties’ representatives cast two ballots: paper and elecronic. The tally from both boxes must give the same result Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 56
Control Ballot (Parallel Testing) Manual counting Electronic couting Parties’ representatives cast two ballots: paper and elecronic. The tally from both boxes must give the same result Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 56
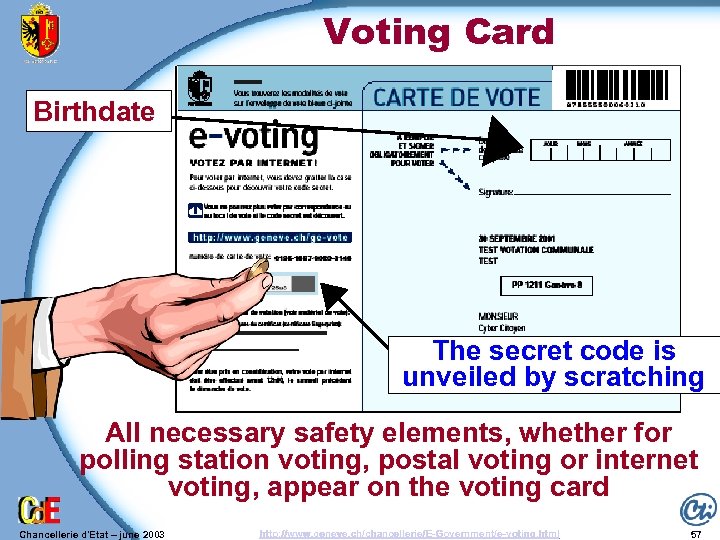 Voting Card Birthdate The secret code is unveiled by scratching All necessary safety elements, whether for polling station voting, postal voting or internet voting, appear on the voting card Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 57
Voting Card Birthdate The secret code is unveiled by scratching All necessary safety elements, whether for polling station voting, postal voting or internet voting, appear on the voting card Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 57
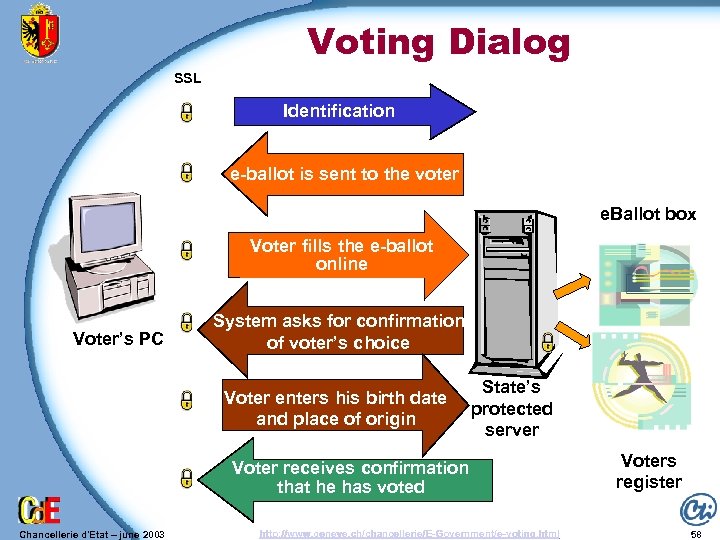 Voting Dialog SSL Identification e-ballot is sent to the voter e. Ballot box Voter fills the e-ballot online Voter’s PC System asks for confirmation of voter’s choice Voter enters his birth date and place of origin State’s protected server Voter receives confirmation Confirmation de that he has voted l’expression d’un vote Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html Voters register 58
Voting Dialog SSL Identification e-ballot is sent to the voter e. Ballot box Voter fills the e-ballot online Voter’s PC System asks for confirmation of voter’s choice Voter enters his birth date and place of origin State’s protected server Voter receives confirmation Confirmation de that he has voted l’expression d’un vote Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html Voters register 58
 Voting card This half contains the The other half is needed to identification features vote by post or at the for Internet voting polling station The Internet voting application is essentially a re-engineering of postal voting. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 59
Voting card This half contains the The other half is needed to identification features vote by post or at the for Internet voting polling station The Internet voting application is essentially a re-engineering of postal voting. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 59
 Swiss e. Ballot lessons % of votes cast on the Internet was far greater than expected : 43. 6% of the voters used the Internet and 49. 9% postal voting. The three ballot system gave the same outcome, but percentages differed. * There were more voters above 60 years old on the Internet (14%) than voters under 24 years (12%). 93% of e. Voters trust our system. The more they use Internet, the more they trust it. The younger they are, the less they trust it. * By the way : this is another issue to consider : do you give detailed or consolidated results. We give consolidated ones. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 60
Swiss e. Ballot lessons % of votes cast on the Internet was far greater than expected : 43. 6% of the voters used the Internet and 49. 9% postal voting. The three ballot system gave the same outcome, but percentages differed. * There were more voters above 60 years old on the Internet (14%) than voters under 24 years (12%). 93% of e. Voters trust our system. The more they use Internet, the more they trust it. The younger they are, the less they trust it. * By the way : this is another issue to consider : do you give detailed or consolidated results. We give consolidated ones. Chancellerie d'Etat – june 2003 http: //www. geneve. ch/chancellerie/E-Government/e-voting. html 60
 Q&A 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS
Q&A 17 -803/17 -400 ELECTRONIC VOTING FALL 2004 COPYRIGHT © 2004 MICHAEL I. SHAMOS


