af13dd8398a043bf2d071115ce056557.ppt
- Количество слайдов: 43
 15 -853: Algorithms in the Real World Cryptography 3 and 4 15 -853 1
15 -853: Algorithms in the Real World Cryptography 3 and 4 15 -853 1
 Cryptography Outline Introduction: terminology, cryptanalysis, security Primitives: one-way functions, trapdoors, … Protocols: digital signatures, key exchange, . . Private-Key Algorithms: Rijndael, DES Public-Key Algorithms: – Diffie-Hellman Key Exchange – RSA, El-Gamal, Blum-Goldwasser – Quantum Cryptography Case Studies: Kerberos, Digital Cash 15 -853 2
Cryptography Outline Introduction: terminology, cryptanalysis, security Primitives: one-way functions, trapdoors, … Protocols: digital signatures, key exchange, . . Private-Key Algorithms: Rijndael, DES Public-Key Algorithms: – Diffie-Hellman Key Exchange – RSA, El-Gamal, Blum-Goldwasser – Quantum Cryptography Case Studies: Kerberos, Digital Cash 15 -853 2
 Public Key Cryptosystems Introduced by Diffie and Hellman in 1976. Plaintext K 1 Encryption Ek(M) = C Cyphertext K 2 Public Key systems K 1 = public key K 2 = private key Digital signatures Decryption Dk(C) = M K 1 = private key K 2 = public key Original Plaintext Typically used as part of a more complicated protocol. 15 -853 3
Public Key Cryptosystems Introduced by Diffie and Hellman in 1976. Plaintext K 1 Encryption Ek(M) = C Cyphertext K 2 Public Key systems K 1 = public key K 2 = private key Digital signatures Decryption Dk(C) = M K 1 = private key K 2 = public key Original Plaintext Typically used as part of a more complicated protocol. 15 -853 3
 One-way trapdoor functions Both Public-Key and Digital signatures make use of one-way trapdoor functions. Public Key: – Encode: c = f(m) – Decode: m = f-1(c) using trapdoor Digital Signatures: – Sign: c = f-1(m) using trapdoor – Verify: m = f(c) 15 -853 4
One-way trapdoor functions Both Public-Key and Digital signatures make use of one-way trapdoor functions. Public Key: – Encode: c = f(m) – Decode: m = f-1(c) using trapdoor Digital Signatures: – Sign: c = f-1(m) using trapdoor – Verify: m = f(c) 15 -853 4
 Example of SSL (3. 0) SSL (Secure Socket Layer) is the standard for the web (https). Protocol (somewhat simplified): Bob -> amazon. com B->A: client hello: protocol version, acceptable ciphers A->B: server hello: cipher, session ID, |amazon. com|verisign hand. B->A: key exchange, {masterkey}amazon’s public key A->B: server finish: ([amazon, prev-messages, masterkey])key 1 shake B->A: client finish: ([bob, prev-messages, masterkey])key 2 A->B: server message: (message 1, [message 1])key 1 data B->A: client message: (message 2, [message 2])key 2 |h|issuer = Certificate = Issuer,
Example of SSL (3. 0) SSL (Secure Socket Layer) is the standard for the web (https). Protocol (somewhat simplified): Bob -> amazon. com B->A: client hello: protocol version, acceptable ciphers A->B: server hello: cipher, session ID, |amazon. com|verisign hand. B->A: key exchange, {masterkey}amazon’s public key A->B: server finish: ([amazon, prev-messages, masterkey])key 1 shake B->A: client finish: ([bob, prev-messages, masterkey])key 2 A->B: server message: (message 1, [message 1])key 1 data B->A: client message: (message 2, [message 2])key 2 |h|issuer = Certificate = Issuer,
 Public Key History Some – – – algorithms Diffie-Hellman, 1976, key-exchange based on discrete logs Merkle-Hellman, 1978, based on “knapsack problem” Mc. Eliece, 1978, based on algebraic coding theory RSA, 1978, based on factoring Rabin, 1979, security can be reduced to factoring El. Gamal, 1985, based on discrete logs Blum-Goldwasser, 1985, based on quadratic residues Elliptic curves, 1985, discrete logs over Elliptic curves Chor-Rivest, 1988, based on knapsack problem NTRU, 1996, based on Lattices XTR, 2000, based on discrete logs of a particular field 15 -853 6
Public Key History Some – – – algorithms Diffie-Hellman, 1976, key-exchange based on discrete logs Merkle-Hellman, 1978, based on “knapsack problem” Mc. Eliece, 1978, based on algebraic coding theory RSA, 1978, based on factoring Rabin, 1979, security can be reduced to factoring El. Gamal, 1985, based on discrete logs Blum-Goldwasser, 1985, based on quadratic residues Elliptic curves, 1985, discrete logs over Elliptic curves Chor-Rivest, 1988, based on knapsack problem NTRU, 1996, based on Lattices XTR, 2000, based on discrete logs of a particular field 15 -853 6
 Diffie-Hellman Key Exchange A group (G, *) and a primitive element (generator) g is made public. – Alice picks a, and sends ga to Bob – Bob picks b and sends gb to Alice – The shared key is gab Note this is easy for Alice or Bob to compute, but assuming discrete logs are hard is hard for anyone else to compute. Can someone see a problem with this protocol? 15 -853 7
Diffie-Hellman Key Exchange A group (G, *) and a primitive element (generator) g is made public. – Alice picks a, and sends ga to Bob – Bob picks b and sends gb to Alice – The shared key is gab Note this is easy for Alice or Bob to compute, but assuming discrete logs are hard is hard for anyone else to compute. Can someone see a problem with this protocol? 15 -853 7
 Person-in-the-middle attack ga Alice gc Mallory gd Bob gb Key 1 = gad Key 1 = gcb Mallory gets to listen to everything. 15 -853 8
Person-in-the-middle attack ga Alice gc Mallory gd Bob gb Key 1 = gad Key 1 = gcb Mallory gets to listen to everything. 15 -853 8
 Merkle-Hellman Gets “security” from the Subset Sum (also called knapsack) which is NP-hard to solve in general. Subset Sum (Knapsack): Given a sequence W = {w 0, w 1, …, wn-1}, wi Z of weights and a sum S, calculate a boolean vector B, such that: Even deciding if there is a solution is NP-hard. 15 -853 9
Merkle-Hellman Gets “security” from the Subset Sum (also called knapsack) which is NP-hard to solve in general. Subset Sum (Knapsack): Given a sequence W = {w 0, w 1, …, wn-1}, wi Z of weights and a sum S, calculate a boolean vector B, such that: Even deciding if there is a solution is NP-hard. 15 -853 9
 Merkle-Hellman W is superincreasing if: It is easy to solve the subset-sum problem for superincreasing W in O(n) time. Main idea of Merkle-Hellman: – Hide the easy case by multiplying each wi by a constant a modulo a prime p – Knowing a and p allows you to retrieve the superincreasing sequence 15 -853 10
Merkle-Hellman W is superincreasing if: It is easy to solve the subset-sum problem for superincreasing W in O(n) time. Main idea of Merkle-Hellman: – Hide the easy case by multiplying each wi by a constant a modulo a prime p – Knowing a and p allows you to retrieve the superincreasing sequence 15 -853 10
 Merkle-Hellman What we need • w 1, L, wn superincreasing integers • p > åi=1 n wi and prime • a, 1 a < p • w’i = a wi mod p Public Key: w’i Private Key: wi, p, a, Encode: y = E(m) = åi=1 n mi w’i Decode: z = a-1 y mod p = a-1 åi=1 n mi w’i mod p = a-1 åi=1 n miaiwi mod p = åi=1 n mi wi Solve subset sum prob: (w 1, L, wn, z) obtaining m 1, L mn 15 -853 11
Merkle-Hellman What we need • w 1, L, wn superincreasing integers • p > åi=1 n wi and prime • a, 1 a < p • w’i = a wi mod p Public Key: w’i Private Key: wi, p, a, Encode: y = E(m) = åi=1 n mi w’i Decode: z = a-1 y mod p = a-1 åi=1 n mi w’i mod p = a-1 åi=1 n miaiwi mod p = åi=1 n mi wi Solve subset sum prob: (w 1, L, wn, z) obtaining m 1, L mn 15 -853 11
 Merkle Hellman: Problem Was broken by Shamir in 1984. Shamir showed how to use integer programming to solve the particular class of Subset Sum problems in polynomial time. Lesson: don’t leave your trapdoor loose. 15 -853 12
Merkle Hellman: Problem Was broken by Shamir in 1984. Shamir showed how to use integer programming to solve the particular class of Subset Sum problems in polynomial time. Lesson: don’t leave your trapdoor loose. 15 -853 12
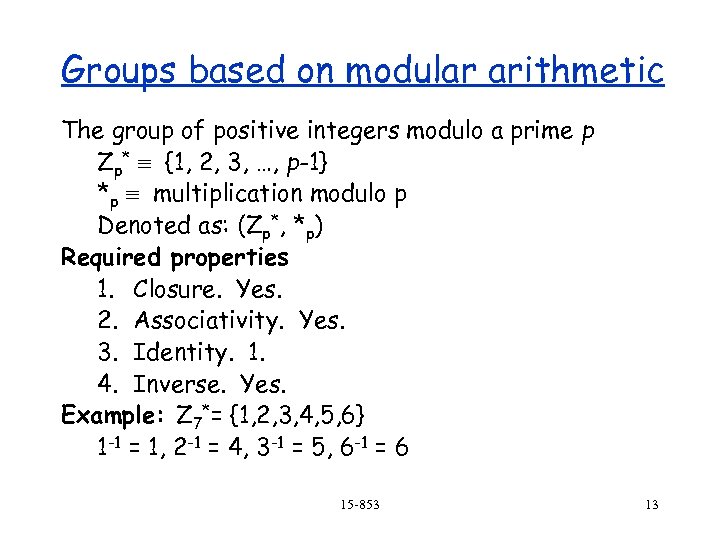 Groups based on modular arithmetic The group of positive integers modulo a prime p Zp* {1, 2, 3, …, p-1} *p multiplication modulo p Denoted as: (Zp*, *p) Required properties 1. Closure. Yes. 2. Associativity. Yes. 3. Identity. 1. 4. Inverse. Yes. Example: Z 7*= {1, 2, 3, 4, 5, 6} 1 -1 = 1, 2 -1 = 4, 3 -1 = 5, 6 -1 = 6 15 -853 13
Groups based on modular arithmetic The group of positive integers modulo a prime p Zp* {1, 2, 3, …, p-1} *p multiplication modulo p Denoted as: (Zp*, *p) Required properties 1. Closure. Yes. 2. Associativity. Yes. 3. Identity. 1. 4. Inverse. Yes. Example: Z 7*= {1, 2, 3, 4, 5, 6} 1 -1 = 1, 2 -1 = 4, 3 -1 = 5, 6 -1 = 6 15 -853 13
 Other properties |Zp*| = (p-1) By Fermat’s little theorem: a(p-1) = 1 (mod p) Example of Z 7* Generators x 1 2 3 4 5 6 x 2 1 4 2 2 4 1 x 3 1 1 6 6 x 4 1 2 4 4 2 1 x 5 1 4 5 2 3 6 x 6 1 1 1 For all p the group is cyclic. 15 -853 14
Other properties |Zp*| = (p-1) By Fermat’s little theorem: a(p-1) = 1 (mod p) Example of Z 7* Generators x 1 2 3 4 5 6 x 2 1 4 2 2 4 1 x 3 1 1 6 6 x 4 1 2 4 4 2 1 x 5 1 4 5 2 3 6 x 6 1 1 1 For all p the group is cyclic. 15 -853 14
 What if n is not a prime? The group of positive integers modulo a non-prime n Zn {1, 2, 3, …, n-1}, n not prime *p multiplication modulo n Required properties? 1. Closure. ? 2. Associativity. ? 3. Identity. ? 4. Inverse. ? How do we fix this? 15 -853 15
What if n is not a prime? The group of positive integers modulo a non-prime n Zn {1, 2, 3, …, n-1}, n not prime *p multiplication modulo n Required properties? 1. Closure. ? 2. Associativity. ? 3. Identity. ? 4. Inverse. ? How do we fix this? 15 -853 15
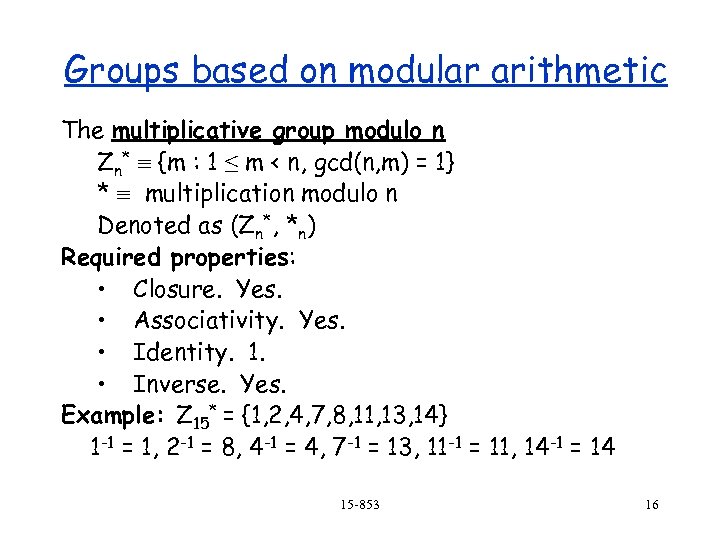 Groups based on modular arithmetic The multiplicative group modulo n Zn* {m : 1 ≤ m < n, gcd(n, m) = 1} * multiplication modulo n Denoted as (Zn*, *n) Required properties: • Closure. Yes. • Associativity. Yes. • Identity. 1. • Inverse. Yes. Example: Z 15* = {1, 2, 4, 7, 8, 11, 13, 14} 1 -1 = 1, 2 -1 = 8, 4 -1 = 4, 7 -1 = 13, 11 -1 = 11, 14 -1 = 14 15 -853 16
Groups based on modular arithmetic The multiplicative group modulo n Zn* {m : 1 ≤ m < n, gcd(n, m) = 1} * multiplication modulo n Denoted as (Zn*, *n) Required properties: • Closure. Yes. • Associativity. Yes. • Identity. 1. • Inverse. Yes. Example: Z 15* = {1, 2, 4, 7, 8, 11, 13, 14} 1 -1 = 1, 2 -1 = 8, 4 -1 = 4, 7 -1 = 13, 11 -1 = 11, 14 -1 = 14 15 -853 16
 The Euler Phi Function If n is a product of two primes p and q, then Euler’s Theorem: Or for n = pq Law of exponentiation: This will be very important in RSA! 15 -853 17
The Euler Phi Function If n is a product of two primes p and q, then Euler’s Theorem: Or for n = pq Law of exponentiation: This will be very important in RSA! 15 -853 17
 Generators Example of Z 10*: {1, 3, 7, 9} x x 3 x 4 1 Generators x 2 1 1 1 3 9 7 1 7 9 3 1 9 1 15 -853 18
Generators Example of Z 10*: {1, 3, 7, 9} x x 3 x 4 1 Generators x 2 1 1 1 3 9 7 1 7 9 3 1 9 1 15 -853 18
 Operations we will need Multiplication: a*b (mod n) – Can be done in O(log 2 n) bit operations, or better Power: ak (mod n) – The power method O(log n) steps, O(log 3 n) bit ops fun pow(a, k) = if (k = 0) then 1 else if (k mod 2 = 1) then a * (pow(a, k/2))2 else (pow(a, k/2))2 Inverse: a-1 (mod n) – Euclid’s algorithm O(log n) steps, O(log 3 n) bit ops 15 -853 19
Operations we will need Multiplication: a*b (mod n) – Can be done in O(log 2 n) bit operations, or better Power: ak (mod n) – The power method O(log n) steps, O(log 3 n) bit ops fun pow(a, k) = if (k = 0) then 1 else if (k mod 2 = 1) then a * (pow(a, k/2))2 else (pow(a, k/2))2 Inverse: a-1 (mod n) – Euclid’s algorithm O(log n) steps, O(log 3 n) bit ops 15 -853 19
 Euclid’s Algorithm: gcd(a, b) = gcd(b, a mod b) gcd(a, 0) = a “Extended” Euclid’s algorithm: – Find x and y such that ax + by = gcd(a, b) – Can be calculated as a side-effect of Euclid’s algorithm. – Note that x and y can be zero or negative. This allows us to find a-1 mod n, for a Zn* In particular return x in ax + ny = 1. 15 -853 20
Euclid’s Algorithm: gcd(a, b) = gcd(b, a mod b) gcd(a, 0) = a “Extended” Euclid’s algorithm: – Find x and y such that ax + by = gcd(a, b) – Can be calculated as a side-effect of Euclid’s algorithm. – Note that x and y can be zero or negative. This allows us to find a-1 mod n, for a Zn* In particular return x in ax + ny = 1. 15 -853 20
 Euclid’s Algorithm fun euclid(a, b) = if (b = 0) then a else euclid(b, a mod b) gcd y fun ext_euclid(a, b) = if (b = 0) then (a, 1, 0) x else let (d, x, y) = ext_euclid(b, a mod b) in (d, y, x – (a/b) y) integer quotient end The code is in the form of an inductive proof. Exercise: prove the inductive step 15 -853 21
Euclid’s Algorithm fun euclid(a, b) = if (b = 0) then a else euclid(b, a mod b) gcd y fun ext_euclid(a, b) = if (b = 0) then (a, 1, 0) x else let (d, x, y) = ext_euclid(b, a mod b) in (d, y, x – (a/b) y) integer quotient end The code is in the form of an inductive proof. Exercise: prove the inductive step 15 -853 21
 RSA Invented by Rivest, Shamir and Adleman in 1978 Based on difficulty of factoring. Used to hide the size of a group Zn* since: . Factoring has not been reduced to RSA – an algorithm that generates m from c does not give an efficient algorithm for factoring On the other hand, factoring has been reduced to finding the private-key. – there is an efficient algorithm for factoring given one that can find the private key. 15 -853 22
RSA Invented by Rivest, Shamir and Adleman in 1978 Based on difficulty of factoring. Used to hide the size of a group Zn* since: . Factoring has not been reduced to RSA – an algorithm that generates m from c does not give an efficient algorithm for factoring On the other hand, factoring has been reduced to finding the private-key. – there is an efficient algorithm for factoring given one that can find the private key. 15 -853 22
 RSA Public-key Cryptosystem What we need: • p and q, primes of approximately the same size • n = pq (n) = (p-1)(q-1) • e Z (n)* • d = e-1 mod (n) Public Key: (e, n) Private Key: d Encode: m Zn E(m) = me mod n Decode: D(c) = cd mod n 15 -853 23
RSA Public-key Cryptosystem What we need: • p and q, primes of approximately the same size • n = pq (n) = (p-1)(q-1) • e Z (n)* • d = e-1 mod (n) Public Key: (e, n) Private Key: d Encode: m Zn E(m) = me mod n Decode: D(c) = cd mod n 15 -853 23
 RSA continued Why it works: D(c) = cd mod n = med mod n = m 1 + k(p-1)(q-1) mod n = m 1 + k (n) mod n = m(m (n))k mod n =m Why is this argument not quite sound? What if m Zn* then m (n) 1 mod n Answer 1: Still works – prove mk (n)+1 = m mod n via Chinese Remainder Theorem Answer 2: jackpot – if you find an m Zn* then GCD(m, n) is a factor of n 15 -853 24
RSA continued Why it works: D(c) = cd mod n = med mod n = m 1 + k(p-1)(q-1) mod n = m 1 + k (n) mod n = m(m (n))k mod n =m Why is this argument not quite sound? What if m Zn* then m (n) 1 mod n Answer 1: Still works – prove mk (n)+1 = m mod n via Chinese Remainder Theorem Answer 2: jackpot – if you find an m Zn* then GCD(m, n) is a factor of n 15 -853 24
 Proof for m Zn* Case Assume w. l. o. g. that q divides m but p does not: Let x = m 1 + k(p-1)(q-1) = m*(m(p-1))k(q-1) (1) x p m (by Euler’s Theorem) (2) x q 0 (since q | m) The Chinese Remainder Theorem states that for any two solutions x 1 and x 2 to equations (1) and (2), x 1 n x 2. Notice that for both x 1 = m 1 + k(p-1)(q-1) and x 2 = m the equations are satisfied. Hence x 1 n x 2 n m. 15 -853 25
Proof for m Zn* Case Assume w. l. o. g. that q divides m but p does not: Let x = m 1 + k(p-1)(q-1) = m*(m(p-1))k(q-1) (1) x p m (by Euler’s Theorem) (2) x q 0 (since q | m) The Chinese Remainder Theorem states that for any two solutions x 1 and x 2 to equations (1) and (2), x 1 n x 2. Notice that for both x 1 = m 1 + k(p-1)(q-1) and x 2 = m the equations are satisfied. Hence x 1 n x 2 n m. 15 -853 25
 RSA computations To generate the keys, we need to – Find two primes p and q. Generate candidates and use primality testing to filter them. – Find e-1 mod (p-1)(q-1). Use Euclid’s algorithm. Takes time log 2(n) To encode and decode – Take me or cd. Use the power method. Takes time log(e) log 2(n) and log(d) log 2(n). In practice e is selected to be small so that encoding is fast. 15 -853 26
RSA computations To generate the keys, we need to – Find two primes p and q. Generate candidates and use primality testing to filter them. – Find e-1 mod (p-1)(q-1). Use Euclid’s algorithm. Takes time log 2(n) To encode and decode – Take me or cd. Use the power method. Takes time log(e) log 2(n) and log(d) log 2(n). In practice e is selected to be small so that encoding is fast. 15 -853 26
 Security of RSA Warning: – Do not use this or any other algorithm naively! Possible security holes: – Need to use “safe” primes p and q. In particular p 1 and q-1 should have large prime factors. – p and q should not have the same number of digits. Can use a middle attack starting at sqrt(n). – e cannot be too small – Don’t use same n for different e’s. – You should always “pad” 15 -853 27
Security of RSA Warning: – Do not use this or any other algorithm naively! Possible security holes: – Need to use “safe” primes p and q. In particular p 1 and q-1 should have large prime factors. – p and q should not have the same number of digits. Can use a middle attack starting at sqrt(n). – e cannot be too small – Don’t use same n for different e’s. – You should always “pad” 15 -853 27
 Algorithm to factor n given d and e Given (n), easy to factor n (two equations, two unknowns): (p-1)(q-1) = (n) pq = n Given d and e, don’t have (n), but since ed = 1 mod (n), have ed-1 = k (n), for some unknown k. Almost as good. 15 -853 28
Algorithm to factor n given d and e Given (n), easy to factor n (two equations, two unknowns): (p-1)(q-1) = (n) pq = n Given d and e, don’t have (n), but since ed = 1 mod (n), have ed-1 = k (n), for some unknown k. Almost as good. 15 -853 28
 Algorithm to factor n given d and e Suggested by Miller’s primality testing paper (1976): Las. Vegas algorithm Function Try. Factor(e, d, n) Probability of pass 1. write ed – 1 as 2 sr, r odd is >. 5. 2. choose w at random < n Will return p or q 3. v = wr mod n if it passes. 4. if v = 1 then return(fail) Try until you pass. 5. while v 1 mod n 6. v 0 = v 7. v = v 2 mod n 8. if v 0 = n - 1 then return(fail) 9. return(pass, GCD(v 0 - 1, n)) 15 -853 Let ’(n) = LCM(p-1, q-1) Let m = #2(k (n)/ ’(n)/2) (#2 is largest power of 2) w ’(n)/2 - 1 shares a factor with n w ’(n)/2 = w k (n)/2 m mod n 29
Algorithm to factor n given d and e Suggested by Miller’s primality testing paper (1976): Las. Vegas algorithm Function Try. Factor(e, d, n) Probability of pass 1. write ed – 1 as 2 sr, r odd is >. 5. 2. choose w at random < n Will return p or q 3. v = wr mod n if it passes. 4. if v = 1 then return(fail) Try until you pass. 5. while v 1 mod n 6. v 0 = v 7. v = v 2 mod n 8. if v 0 = n - 1 then return(fail) 9. return(pass, GCD(v 0 - 1, n)) 15 -853 Let ’(n) = LCM(p-1, q-1) Let m = #2(k (n)/ ’(n)/2) (#2 is largest power of 2) w ’(n)/2 - 1 shares a factor with n w ’(n)/2 = w k (n)/2 m mod n 29
 RSA Performance: (600 Mhz PIII) (from: ssh toolkit): Algorithm Bits/key Mbits/sec 1024 . 35 sec/key 2048 2. 83 sec/key 1024 1786/sec 3. 5 2048 672/sec 1. 2 1024 74/sec . 074 2048 12/sec . 024 El. Gamal Enc. 1024 31/sec . 031 El. Gamal Dec. 1024 61/sec . 061 RSA Keygen RSA Encrypt RSA Decrypt DES-cbc 56 95 twofish-cbc 128 140 Rijndael 128 180 15 -853 30
RSA Performance: (600 Mhz PIII) (from: ssh toolkit): Algorithm Bits/key Mbits/sec 1024 . 35 sec/key 2048 2. 83 sec/key 1024 1786/sec 3. 5 2048 672/sec 1. 2 1024 74/sec . 074 2048 12/sec . 024 El. Gamal Enc. 1024 31/sec . 031 El. Gamal Dec. 1024 61/sec . 061 RSA Keygen RSA Encrypt RSA Decrypt DES-cbc 56 95 twofish-cbc 128 140 Rijndael 128 180 15 -853 30
 RSA in the “Real World” Part of many standards: PKCS, ITU X. 509, ANSI X 9. 31, IEEE P 1363 Used by: SSL, PEM, PGP, Entrust, … The standards specify many details on the implementation, e. g. – e should be selected to be small, but not too small – “multi prime” versions make use of n = pqr… this makes it cheaper to decode especially in parallel (uses Chinese remainder theorem). 15 -853 31
RSA in the “Real World” Part of many standards: PKCS, ITU X. 509, ANSI X 9. 31, IEEE P 1363 Used by: SSL, PEM, PGP, Entrust, … The standards specify many details on the implementation, e. g. – e should be selected to be small, but not too small – “multi prime” versions make use of n = pqr… this makes it cheaper to decode especially in parallel (uses Chinese remainder theorem). 15 -853 31
 Factoring in the Real World Quadratic Sieve (QS): – log n bits in input, superpolynomial time – Used in 1994 to factor a 129 digit (428 -bit) number. 1600 Machines, 8 months. Number field Sieve (NFS): – Used in 1999 to factor 155 digit (512 -bit) number. 35 CPU years. At least 4 x faster than QS – Used in 2003 -2005 to factor 200 digits (663 bits) 75 CPU years ($20 K prize) 15 -853 32
Factoring in the Real World Quadratic Sieve (QS): – log n bits in input, superpolynomial time – Used in 1994 to factor a 129 digit (428 -bit) number. 1600 Machines, 8 months. Number field Sieve (NFS): – Used in 1999 to factor 155 digit (512 -bit) number. 35 CPU years. At least 4 x faster than QS – Used in 2003 -2005 to factor 200 digits (663 bits) 75 CPU years ($20 K prize) 15 -853 32
 Discrete Logarithms If g is a generator of Zn*, then for all y there is a unique x (mod (n)) such that – y = gx mod n This is called the discrete logarithm of y and we use the notation – x = logg(y) In general finding the discrete logarithm is conjectured to be hard…as hard as factoring. 15 -853 33
Discrete Logarithms If g is a generator of Zn*, then for all y there is a unique x (mod (n)) such that – y = gx mod n This is called the discrete logarithm of y and we use the notation – x = logg(y) In general finding the discrete logarithm is conjectured to be hard…as hard as factoring. 15 -853 33
 El. Gamal Based on the difficulty of the discrete log problem. Invented in 1985 Digital signature and Key-exchange variants – Digital signature is AES standard – Public Key used by TRW (avoided RSA patent) Works over various groups – Zp, – Multiplicative group GF(pn), – Elliptic Curves 15 -853 34
El. Gamal Based on the difficulty of the discrete log problem. Invented in 1985 Digital signature and Key-exchange variants – Digital signature is AES standard – Public Key used by TRW (avoided RSA patent) Works over various groups – Zp, – Multiplicative group GF(pn), – Elliptic Curves 15 -853 34
 El. Gamal Public-key Cryptosystem (G, *) is a group • a generator for G • a Z|G| • = a G is selected so that it is hard to solve the discrete log problem. Public Key: ( , ) and some description of G Private Key: a Encode: Pick random k Z|G| E(m) = (y 1, y 2) = ( k, m * k) Decode: D(y) = y 2 * (y 1 a)-1 = (m * k) * ( ka)-1 = m * k * ( k)-1 =m You need to know a to easily decode y! 15 -853 35
El. Gamal Public-key Cryptosystem (G, *) is a group • a generator for G • a Z|G| • = a G is selected so that it is hard to solve the discrete log problem. Public Key: ( , ) and some description of G Private Key: a Encode: Pick random k Z|G| E(m) = (y 1, y 2) = ( k, m * k) Decode: D(y) = y 2 * (y 1 a)-1 = (m * k) * ( ka)-1 = m * k * ( k)-1 =m You need to know a to easily decode y! 15 -853 35
 El. Gamal: Example G • • • = Z 11* =2 a =8 = 28 (mod 11) = 3 Public Key: (2, 3), Z 11* Private Key: a = 8 Encode: 7 Pick random k = 4 E(m) = (24, 7 * 34) = (5, 6) Decode: (5, 6) D(y) = 6 * (58)-1 = 6 * 4 -1 = 6 * 3 (mod 11) =7 15 -853 36
El. Gamal: Example G • • • = Z 11* =2 a =8 = 28 (mod 11) = 3 Public Key: (2, 3), Z 11* Private Key: a = 8 Encode: 7 Pick random k = 4 E(m) = (24, 7 * 34) = (5, 6) Decode: (5, 6) D(y) = 6 * (58)-1 = 6 * 4 -1 = 6 * 3 (mod 11) =7 15 -853 36
 Probabilistic Encryption For RSA one message goes to one cipher word. This means we might gain information by running Epublic(M). Probabilistic encryption maps every M to many C randomly. Cryptanalysists can’t tell whether C = Epublic(M). El. Gamal is an example (based on the random k), but it doubles the size of message. 15 -853 37
Probabilistic Encryption For RSA one message goes to one cipher word. This means we might gain information by running Epublic(M). Probabilistic encryption maps every M to many C randomly. Cryptanalysists can’t tell whether C = Epublic(M). El. Gamal is an example (based on the random k), but it doubles the size of message. 15 -853 37
 BBS “secure” random bits BBS (Blum, Blum and Shub, 1984) – Based on difficulty of factoring, or finding square roots modulo n = pq. Fixed • p and q are primes such that p = q = 3 (mod 4) • n = pq (is called a Blum integer) For a particular bit seq. • Seed: random x relatively prime to n. • Initial state: x 0 = x 2 • ith state: xi = (xi-1)2 • ith bit: lsb of xi Note that: Therefore knowing p and q allows us to find x 0 from xi 15 -853 38
BBS “secure” random bits BBS (Blum, Blum and Shub, 1984) – Based on difficulty of factoring, or finding square roots modulo n = pq. Fixed • p and q are primes such that p = q = 3 (mod 4) • n = pq (is called a Blum integer) For a particular bit seq. • Seed: random x relatively prime to n. • Initial state: x 0 = x 2 • ith state: xi = (xi-1)2 • ith bit: lsb of xi Note that: Therefore knowing p and q allows us to find x 0 from xi 15 -853 38
 Blum-Goldwasser: A stream cypher Public key: n (= pq) Encrypt: Private key: p or q mi (0 i l) Random x xor bi x 2 mod n ci (0 i l) lsb xi BBS ci (l i l + log n) = xl Decrypt: Using p and q, find Use this to regenerate the bi and hence mi 15 -853 39
Blum-Goldwasser: A stream cypher Public key: n (= pq) Encrypt: Private key: p or q mi (0 i l) Random x xor bi x 2 mod n ci (0 i l) lsb xi BBS ci (l i l + log n) = xl Decrypt: Using p and q, find Use this to regenerate the bi and hence mi 15 -853 39
 Quantum Cryptography In quantum mechanics, there is no way to take a measurement without potentially changing the state. E. g. – Measuring position, spreads out the momentum – Measuring spin horizontally, “spreads out” the spin probability vertically Related to Heisenberg’s uncertainty principal 15 -853 40
Quantum Cryptography In quantum mechanics, there is no way to take a measurement without potentially changing the state. E. g. – Measuring position, spreads out the momentum – Measuring spin horizontally, “spreads out” the spin probability vertically Related to Heisenberg’s uncertainty principal 15 -853 40
 Using photon polarization = = ? (equal probability) or or measure diagonal ? (equal probability) measure square destroys state 15 -853 41
Using photon polarization = = ? (equal probability) or or measure diagonal ? (equal probability) measure square destroys state 15 -853 41
 Quantum Key Exchange 1. Alice sends bob photon stream randomly polarized in one of 4 polarizations: 2. Bob measures photons in random orientations e. g. : x++xxx+x (orientations used) | - / / - (measured polarizations) and tells Alice in the open what orientations he used, but not what he measured. 3. Alice tells Bob in the open which are correct 4. Bob and Alice keep the correct values Susceptible to a man-in-the-middle attack 15 -853 42
Quantum Key Exchange 1. Alice sends bob photon stream randomly polarized in one of 4 polarizations: 2. Bob measures photons in random orientations e. g. : x++xxx+x (orientations used) | - / / - (measured polarizations) and tells Alice in the open what orientations he used, but not what he measured. 3. Alice tells Bob in the open which are correct 4. Bob and Alice keep the correct values Susceptible to a man-in-the-middle attack 15 -853 42
 In the “real world” Not yet used in practice, but experiments have verified that it works. IBM has working system over 30 cm at 10 bits/sec. More recently, up to 10 km of fiber. 15 -853 43
In the “real world” Not yet used in practice, but experiments have verified that it works. IBM has working system over 30 cm at 10 bits/sec. More recently, up to 10 km of fiber. 15 -853 43


