a12422e128adcf2d5ab055785d20f907.ppt
- Количество слайдов: 64
 15 -441 Computer Networking Lecture 18 – TCP over Wireless 1
15 -441 Computer Networking Lecture 18 – TCP over Wireless 1
![Readings • [R. 2] Hari Balakrishnan, Srinivasan Seshan, and Randy H. Katz, Readings • [R. 2] Hari Balakrishnan, Srinivasan Seshan, and Randy H. Katz,](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-2.jpg) Readings • [R. 2] Hari Balakrishnan, Srinivasan Seshan, and Randy H. Katz, "Improving Reliable Transport and Handoff Performance in Cellular Wireless Networks. " ACM Wireless Networks, Volume 1, Number 4. December 1995. Pages 469 -481. • [R. 3] Ajay Bakre and B. R. Badrinath, "I-TCP: Indirect TCP for Mobile Hosts, " Proceedings of the 15 th International Conference on Distributed Computing Systems (ICDCS '95), May 30 - June 2, 1995, Vancouver, British Columbia. Pages 136 -143. • [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G. Holland N. Vaidya, Wireless Networks 8, 2002 4 -3 -06 Lecture 18: Wireless TCP 2
Readings • [R. 2] Hari Balakrishnan, Srinivasan Seshan, and Randy H. Katz, "Improving Reliable Transport and Handoff Performance in Cellular Wireless Networks. " ACM Wireless Networks, Volume 1, Number 4. December 1995. Pages 469 -481. • [R. 3] Ajay Bakre and B. R. Badrinath, "I-TCP: Indirect TCP for Mobile Hosts, " Proceedings of the 15 th International Conference on Distributed Computing Systems (ICDCS '95), May 30 - June 2, 1995, Vancouver, British Columbia. Pages 136 -143. • [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G. Holland N. Vaidya, Wireless Networks 8, 2002 4 -3 -06 Lecture 18: Wireless TCP 2
![Optional Readings • [R. 1] Ramon Caceres and Liviu Iftode, Optional Readings • [R. 1] Ramon Caceres and Liviu Iftode,](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-3.jpg) Optional Readings • [R. 1] Ramon Caceres and Liviu Iftode, "Improving the Performance of Reliable Transport Protocols in Mobile Computing Environments. " IEEE JSAC, Volume 13, Number 5. June 1995. • [R. 4] H. Balakrishnan, Venkat Padmanabhan, Srinivasan Seshan, and Randy H. Katz, A Comparison of Mechanisms for Improving TCP Performance over Wireless Links, IEEE/ACM Transactions on Networking, December 1997. • [R. 5] David Eckhardt and Peter Steenkiste, "An Internet-style Approach to Wireless Link Errors", Journal of Wireless Communications and Mobile Computing, Wiley, special issue on "Reliably Transport Protocols for Mobile Computing", Volume 2, Number 1, February 2002. • [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan, Vaidyanathan Anantharaman, Hung-Yun Hsieh, Raghupathy Sivakumar, Mobi. Hoc'03. • [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A Receiver-Centric Transport Protocol for Mobile Hosts with Heterogeneous Wireless Interfaces. Mobi. Com 2003. 4 -3 -06 Lecture 18: Wireless TCP 3
Optional Readings • [R. 1] Ramon Caceres and Liviu Iftode, "Improving the Performance of Reliable Transport Protocols in Mobile Computing Environments. " IEEE JSAC, Volume 13, Number 5. June 1995. • [R. 4] H. Balakrishnan, Venkat Padmanabhan, Srinivasan Seshan, and Randy H. Katz, A Comparison of Mechanisms for Improving TCP Performance over Wireless Links, IEEE/ACM Transactions on Networking, December 1997. • [R. 5] David Eckhardt and Peter Steenkiste, "An Internet-style Approach to Wireless Link Errors", Journal of Wireless Communications and Mobile Computing, Wiley, special issue on "Reliably Transport Protocols for Mobile Computing", Volume 2, Number 1, February 2002. • [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan, Vaidyanathan Anantharaman, Hung-Yun Hsieh, Raghupathy Sivakumar, Mobi. Hoc'03. • [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A Receiver-Centric Transport Protocol for Mobile Hosts with Heterogeneous Wireless Interfaces. Mobi. Com 2003. 4 -3 -06 Lecture 18: Wireless TCP 3
![TCP Problems Over Noisy Links • First reported in [R. 1] • Wireless links TCP Problems Over Noisy Links • First reported in [R. 1] • Wireless links](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-4.jpg) TCP Problems Over Noisy Links • First reported in [R. 1] • Wireless links are inherently error-prone • • Fades, interference, attenuation Errors often happen in bursts • TCP cannot distinguish between corruption and congestion • TCP unnecessarily reduces window, resulting in low throughput and high latency • Burst losses often result in timeouts • Sender retransmission is the only option • Inefficient use of bandwidth 4 -3 -06 Lecture 18: Wireless TCP 4
TCP Problems Over Noisy Links • First reported in [R. 1] • Wireless links are inherently error-prone • • Fades, interference, attenuation Errors often happen in bursts • TCP cannot distinguish between corruption and congestion • TCP unnecessarily reduces window, resulting in low throughput and high latency • Burst losses often result in timeouts • Sender retransmission is the only option • Inefficient use of bandwidth 4 -3 -06 Lecture 18: Wireless TCP 4
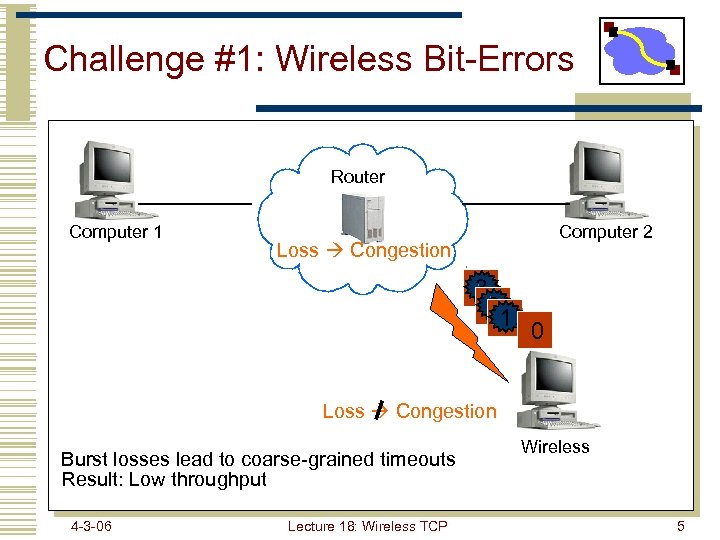 Challenge #1: Wireless Bit-Errors Router Computer 1 Computer 2 Loss Congestion 3 2 22 1 0 Loss Congestion Burst losses lead to coarse-grained timeouts Result: Low throughput 4 -3 -06 Lecture 18: Wireless TCP Wireless 5
Challenge #1: Wireless Bit-Errors Router Computer 1 Computer 2 Loss Congestion 3 2 22 1 0 Loss Congestion Burst losses lead to coarse-grained timeouts Result: Low throughput 4 -3 -06 Lecture 18: Wireless TCP Wireless 5
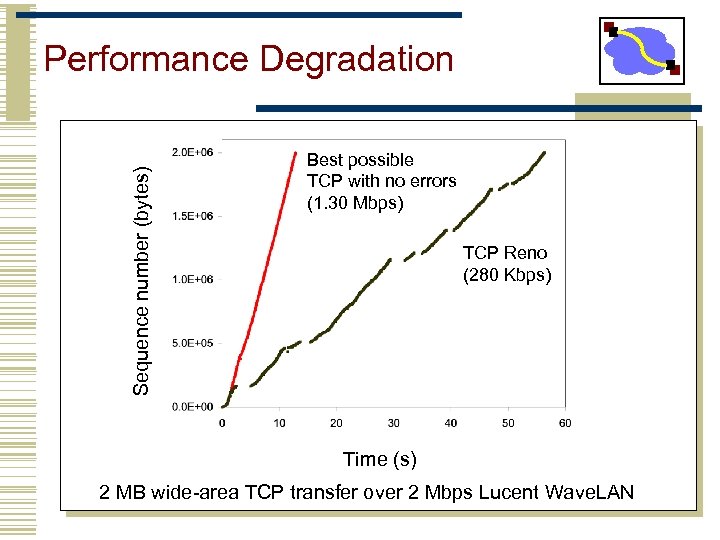 Sequence number (bytes) Performance Degradation Best possible TCP with no errors (1. 30 Mbps) TCP Reno (280 Kbps) Time (s) 2 MB wide-area TCP transfer over 2 Mbps Lucent Wave. LAN
Sequence number (bytes) Performance Degradation Best possible TCP with no errors (1. 30 Mbps) TCP Reno (280 Kbps) Time (s) 2 MB wide-area TCP transfer over 2 Mbps Lucent Wave. LAN
 Constraints & Requirements • Incremental deployment • • Solution should not require modifications to fixed hosts If possible, avoid modifying mobile hosts • Probably more data to mobile than from mobile • Attempt to solve this first 4 -3 -06 Lecture 18: Wireless TCP 7
Constraints & Requirements • Incremental deployment • • Solution should not require modifications to fixed hosts If possible, avoid modifying mobile hosts • Probably more data to mobile than from mobile • Attempt to solve this first 4 -3 -06 Lecture 18: Wireless TCP 7
 Proposed Solutions • End-to-end protocols • Selective ACKs, Explicit loss notification • Split-connection protocols • Separate connections for wired path and wireless hop • Reliable link-layer protocols • • Error-correcting codes Local retransmission 4 -3 -06 Lecture 18: Wireless TCP 8
Proposed Solutions • End-to-end protocols • Selective ACKs, Explicit loss notification • Split-connection protocols • Separate connections for wired path and wireless hop • Reliable link-layer protocols • • Error-correcting codes Local retransmission 4 -3 -06 Lecture 18: Wireless TCP 8
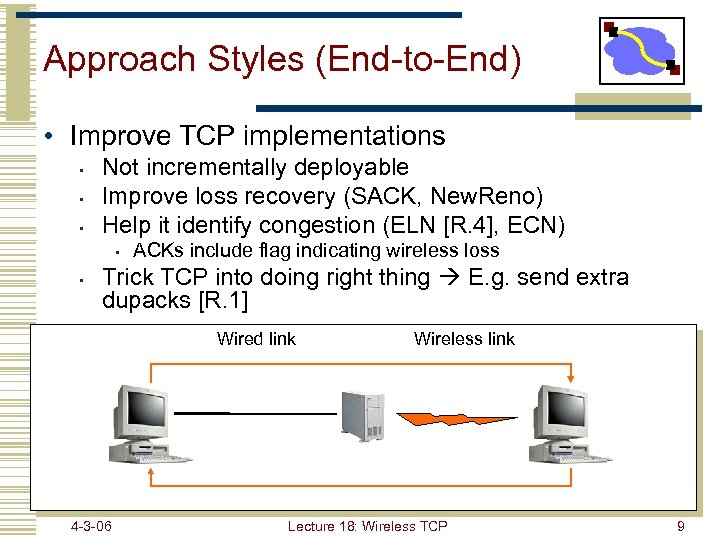 Approach Styles (End-to-End) • Improve TCP implementations • • • Not incrementally deployable Improve loss recovery (SACK, New. Reno) Help it identify congestion (ELN [R. 4], ECN) • • ACKs include flag indicating wireless loss Trick TCP into doing right thing E. g. send extra dupacks [R. 1] Wired link 4 -3 -06 Wireless link Lecture 18: Wireless TCP 9
Approach Styles (End-to-End) • Improve TCP implementations • • • Not incrementally deployable Improve loss recovery (SACK, New. Reno) Help it identify congestion (ELN [R. 4], ECN) • • ACKs include flag indicating wireless loss Trick TCP into doing right thing E. g. send extra dupacks [R. 1] Wired link 4 -3 -06 Wireless link Lecture 18: Wireless TCP 9
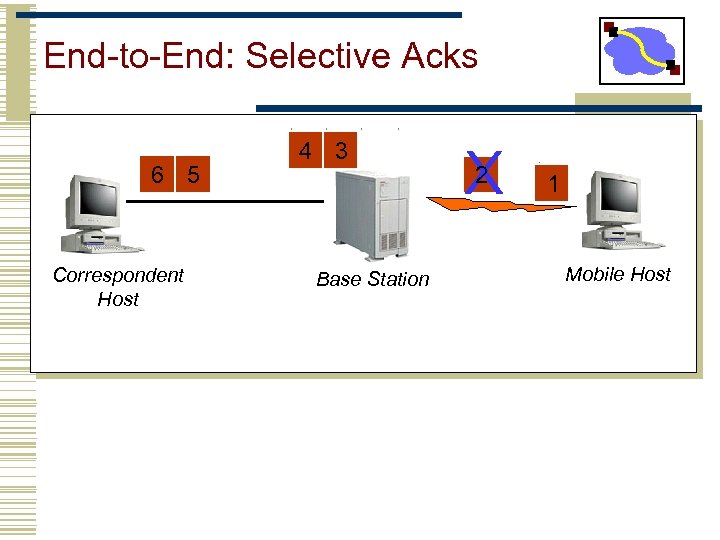 End-to-End: Selective Acks 6 5 Correspondent Host 4 3 Base Station X 2 1 Mobile Host
End-to-End: Selective Acks 6 5 Correspondent Host 4 3 Base Station X 2 1 Mobile Host
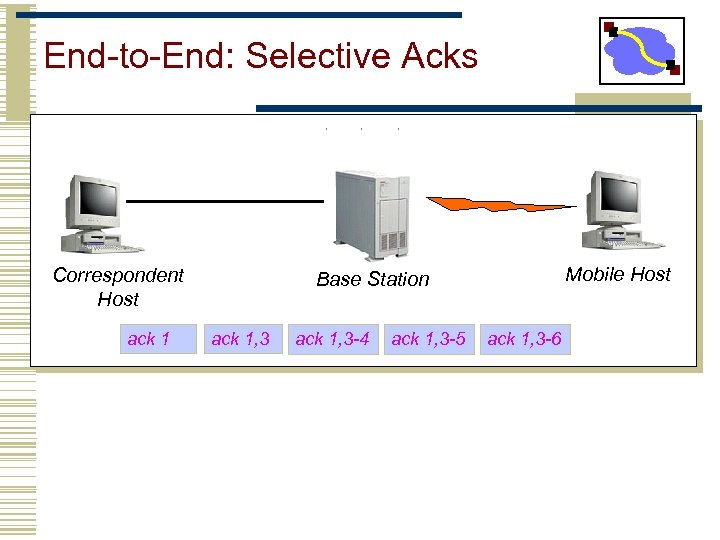 End-to-End: Selective Acks Correspondent Host ack 1 Mobile Host Base Station ack 1, 3 -4 ack 1, 3 -5 ack 1, 3 -6
End-to-End: Selective Acks Correspondent Host ack 1 Mobile Host Base Station ack 1, 3 -4 ack 1, 3 -5 ack 1, 3 -6
![Approach Styles (Split Connection) • Split connections [R. 3] • • Wireless connection need Approach Styles (Split Connection) • Split connections [R. 3] • • Wireless connection need](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-12.jpg) Approach Styles (Split Connection) • Split connections [R. 3] • • Wireless connection need not be TCP Hard state at base station • • • Complicates mobility Vulnerable to failures Violates end-to-end semantics Wired link 4 -3 -06 Wireless link Lecture 18: Wireless TCP 12
Approach Styles (Split Connection) • Split connections [R. 3] • • Wireless connection need not be TCP Hard state at base station • • • Complicates mobility Vulnerable to failures Violates end-to-end semantics Wired link 4 -3 -06 Wireless link Lecture 18: Wireless TCP 12
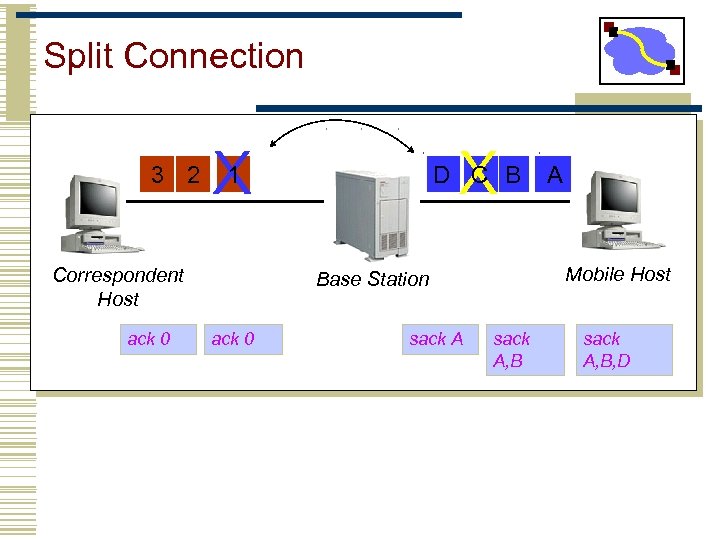 Split Connection 3 2 X Correspondent Host ack 0 X 1 D C B Mobile Host Base Station ack 0 sack A A sack A, B, D
Split Connection 3 2 X Correspondent Host ack 0 X 1 D C B Mobile Host Base Station ack 0 sack A A sack A, B, D
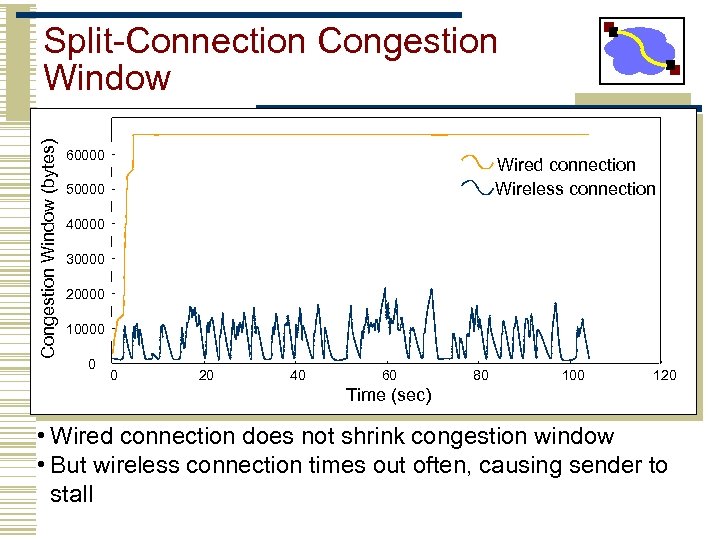 Congestion Window (bytes) Split-Connection Congestion Window 60000 Wired connection Wireless connection 50000 40000 30000 20000 10000 0 0 20 40 60 80 100 120 Time (sec) • Wired connection does not shrink congestion window • But wireless connection times out often, causing sender to stall
Congestion Window (bytes) Split-Connection Congestion Window 60000 Wired connection Wireless connection 50000 40000 30000 20000 10000 0 0 20 40 60 80 100 120 Time (sec) • Wired connection does not shrink congestion window • But wireless connection times out often, causing sender to stall
 Approach Styles (Link Layer) • More aggressive local rexmit than TCP • Bandwidth not wasted on wired links • Adverse interactions with transport layer • • • Timer interactions Interactions with fast retransmissions Large end-to-end round-trip time variation • FEC does not work well with burst losses Wired link Wireless link ARQ/FEC 4 -3 -06 Lecture 18: Wireless TCP 15
Approach Styles (Link Layer) • More aggressive local rexmit than TCP • Bandwidth not wasted on wired links • Adverse interactions with transport layer • • • Timer interactions Interactions with fast retransmissions Large end-to-end round-trip time variation • FEC does not work well with burst losses Wired link Wireless link ARQ/FEC 4 -3 -06 Lecture 18: Wireless TCP 15
![Hybrid Approach: Snoop Protocol • Described in [R. 2] • Transport-aware link protocol • Hybrid Approach: Snoop Protocol • Described in [R. 2] • Transport-aware link protocol •](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-16.jpg) Hybrid Approach: Snoop Protocol • Described in [R. 2] • Transport-aware link protocol • Modify base station • • To cache un-acked TCP packets … And perform local retransmissions • Key ideas • • No transport level code in base station When node moves to different base station, state eventually recreated there 4 -3 -06 Lecture 18: Wireless TCP 16
Hybrid Approach: Snoop Protocol • Described in [R. 2] • Transport-aware link protocol • Modify base station • • To cache un-acked TCP packets … And perform local retransmissions • Key ideas • • No transport level code in base station When node moves to different base station, state eventually recreated there 4 -3 -06 Lecture 18: Wireless TCP 16
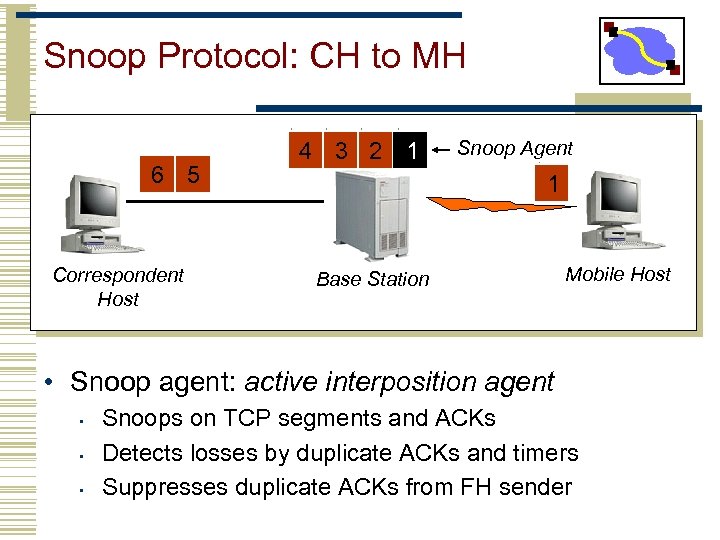 Snoop Protocol: CH to MH 6 5 Correspondent Host 4 3 2 1 Snoop Agent 1 Base Station Mobile Host • Snoop agent: active interposition agent • • • Snoops on TCP segments and ACKs Detects losses by duplicate ACKs and timers Suppresses duplicate ACKs from FH sender
Snoop Protocol: CH to MH 6 5 Correspondent Host 4 3 2 1 Snoop Agent 1 Base Station Mobile Host • Snoop agent: active interposition agent • • • Snoops on TCP segments and ACKs Detects losses by duplicate ACKs and timers Suppresses duplicate ACKs from FH sender
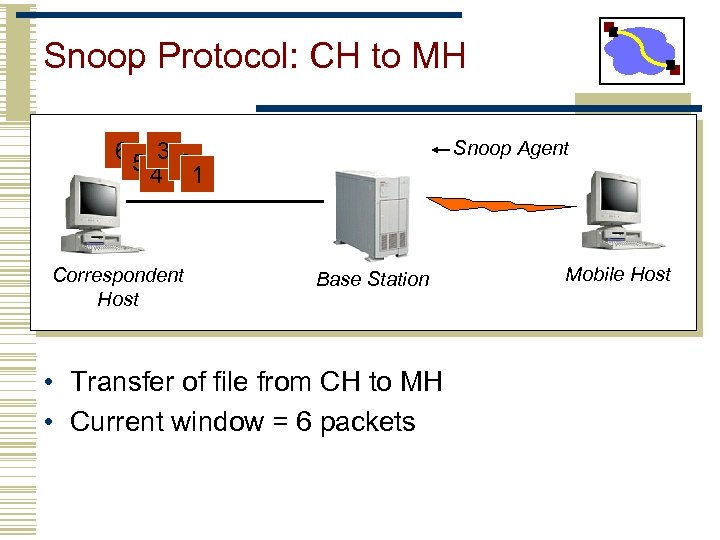 Snoop Protocol: CH to MH Snoop Agent 65 3 2 4 1 Correspondent Host Base Station • Transfer of file from CH to MH • Current window = 6 packets Mobile Host
Snoop Protocol: CH to MH Snoop Agent 65 3 2 4 1 Correspondent Host Base Station • Transfer of file from CH to MH • Current window = 6 packets Mobile Host
 Snoop Protocol: CH to MH 6 5 Snoop Agent 4 3 2 Correspondent Host • Transfer begins 1 Base Station Mobile Host
Snoop Protocol: CH to MH 6 5 Snoop Agent 4 3 2 Correspondent Host • Transfer begins 1 Base Station Mobile Host
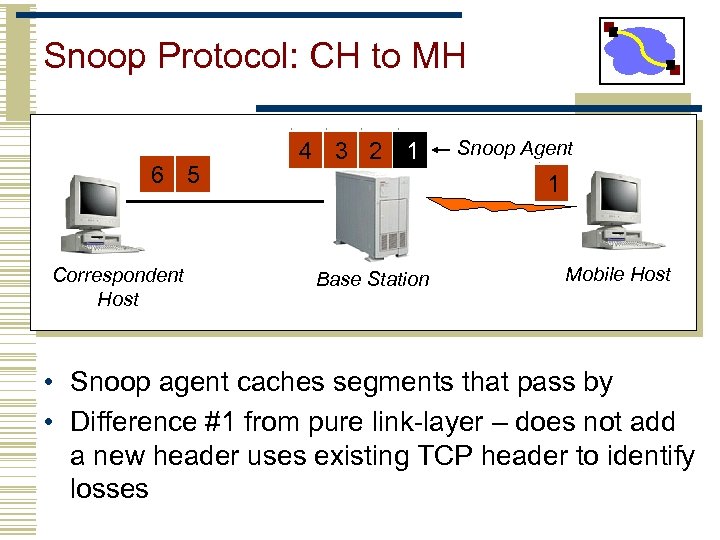 Snoop Protocol: CH to MH 6 5 Correspondent Host 4 3 2 1 Snoop Agent 1 Base Station Mobile Host • Snoop agent caches segments that pass by • Difference #1 from pure link-layer – does not add a new header uses existing TCP header to identify losses
Snoop Protocol: CH to MH 6 5 Correspondent Host 4 3 2 1 Snoop Agent 1 Base Station Mobile Host • Snoop agent caches segments that pass by • Difference #1 from pure link-layer – does not add a new header uses existing TCP header to identify losses
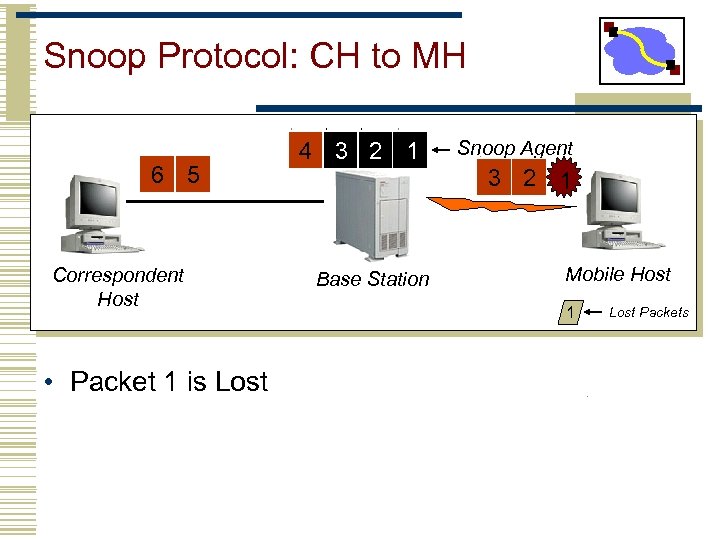 Snoop Protocol: CH to MH 6 5 Correspondent Host • Packet 1 is Lost 4 3 2 1 Snoop Agent 3 2 1 Base Station Mobile Host 1 Lost Packets
Snoop Protocol: CH to MH 6 5 Correspondent Host • Packet 1 is Lost 4 3 2 1 Snoop Agent 3 2 1 Base Station Mobile Host 1 Lost Packets
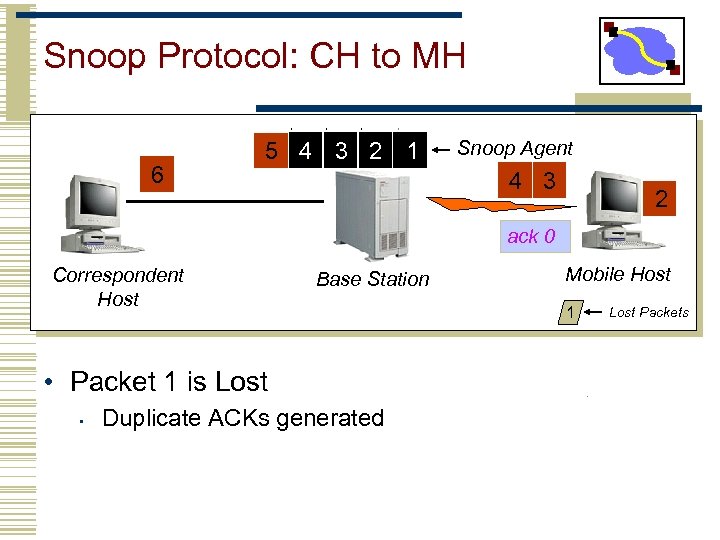 Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 4 3 2 ack 0 Correspondent Host Base Station • Packet 1 is Lost • Duplicate ACKs generated Mobile Host 1 Lost Packets
Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 4 3 2 ack 0 Correspondent Host Base Station • Packet 1 is Lost • Duplicate ACKs generated Mobile Host 1 Lost Packets
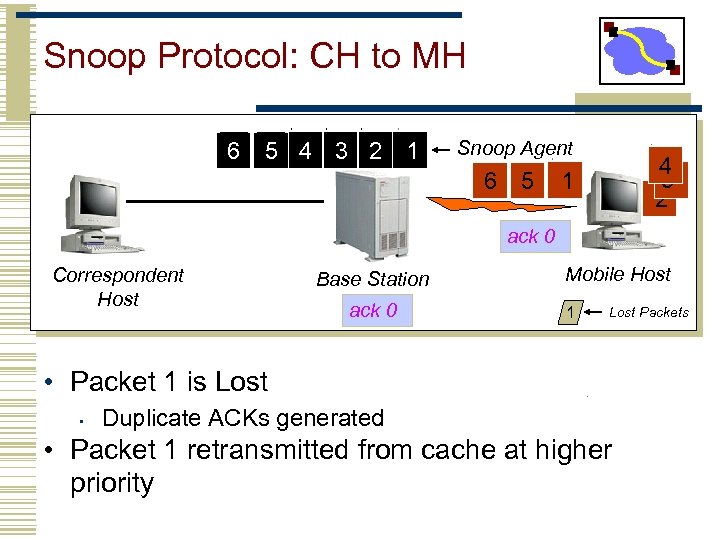 Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 6 5 4 3 2 1 ack 0 Correspondent Host Base Station ack 0 Mobile Host 1 Lost Packets • Packet 1 is Lost • Duplicate ACKs generated • Packet 1 retransmitted from cache at higher priority
Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 6 5 4 3 2 1 ack 0 Correspondent Host Base Station ack 0 Mobile Host 1 Lost Packets • Packet 1 is Lost • Duplicate ACKs generated • Packet 1 retransmitted from cache at higher priority
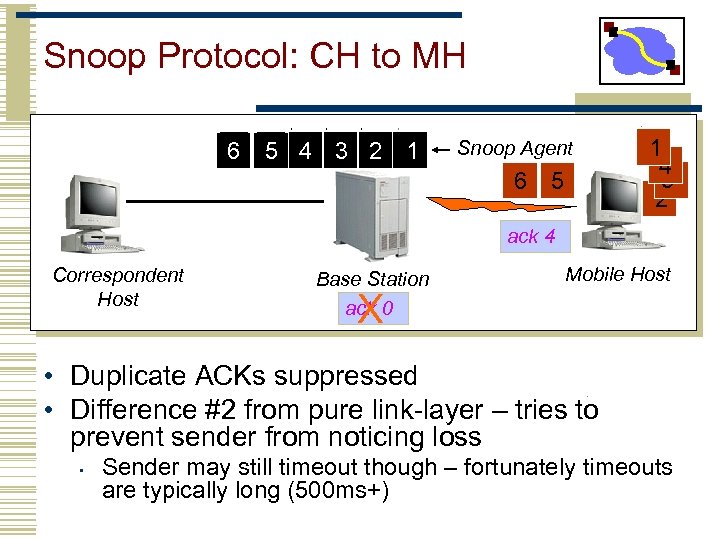 Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 6 5 1 4 3 2 ack 4 Correspondent Host Base Station ack 0 Mobile Host X • Duplicate ACKs suppressed • Difference #2 from pure link-layer – tries to prevent sender from noticing loss • Sender may still timeout though – fortunately timeouts are typically long (500 ms+)
Snoop Protocol: CH to MH 6 5 4 3 2 1 Snoop Agent 6 5 1 4 3 2 ack 4 Correspondent Host Base Station ack 0 Mobile Host X • Duplicate ACKs suppressed • Difference #2 from pure link-layer – tries to prevent sender from noticing loss • Sender may still timeout though – fortunately timeouts are typically long (500 ms+)
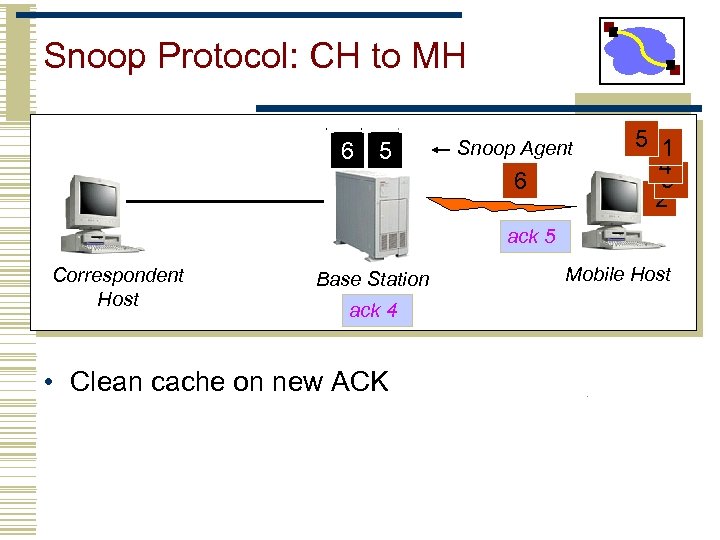 Snoop Protocol: CH to MH 6 5 Snoop Agent 6 5 1 4 3 2 ack 5 Correspondent Host Base Station ack 4 • Clean cache on new ACK Mobile Host
Snoop Protocol: CH to MH 6 5 Snoop Agent 6 5 1 4 3 2 ack 5 Correspondent Host Base Station ack 4 • Clean cache on new ACK Mobile Host
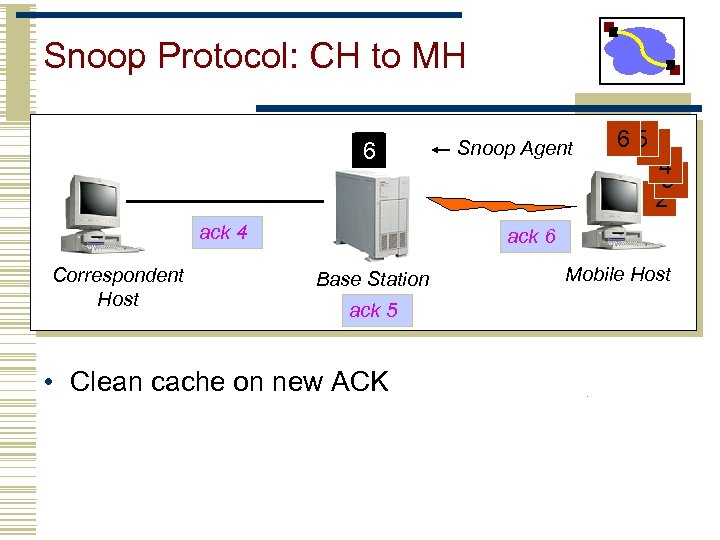 Snoop Protocol: CH to MH 6 ack 4 Correspondent Host Snoop Agent 6 51 4 3 2 ack 6 Base Station ack 5 • Clean cache on new ACK Mobile Host
Snoop Protocol: CH to MH 6 ack 4 Correspondent Host Snoop Agent 6 51 4 3 2 ack 6 Base Station ack 5 • Clean cache on new ACK Mobile Host
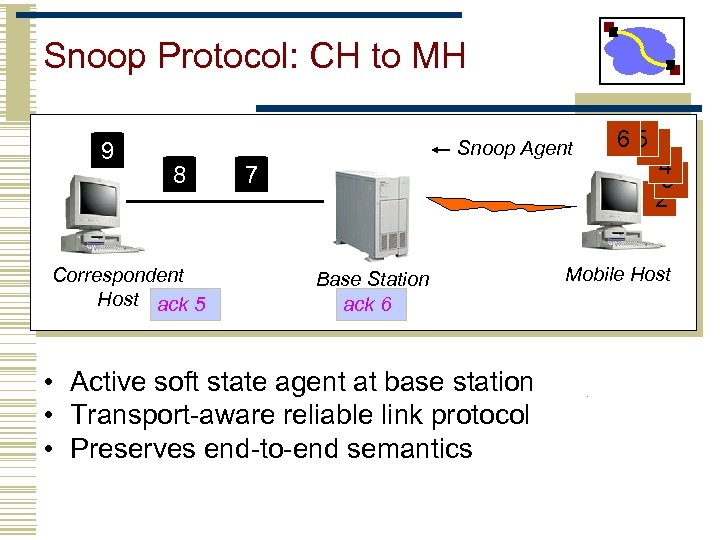 Snoop Protocol: CH to MH 9 Snoop Agent 8 Correspondent Host ack 5 7 Base Station ack 6 • Active soft state agent at base station • Transport-aware reliable link protocol • Preserves end-to-end semantics 6 51 4 3 2 Mobile Host
Snoop Protocol: CH to MH 9 Snoop Agent 8 Correspondent Host ack 5 7 Base Station ack 6 • Active soft state agent at base station • Transport-aware reliable link protocol • Preserves end-to-end semantics 6 51 4 3 2 Mobile Host
 Other Issues • What about mobility? • What about mobile-to-fixed communication? 4 -3 -06 Lecture 18: Wireless TCP 28
Other Issues • What about mobility? • What about mobile-to-fixed communication? 4 -3 -06 Lecture 18: Wireless TCP 28
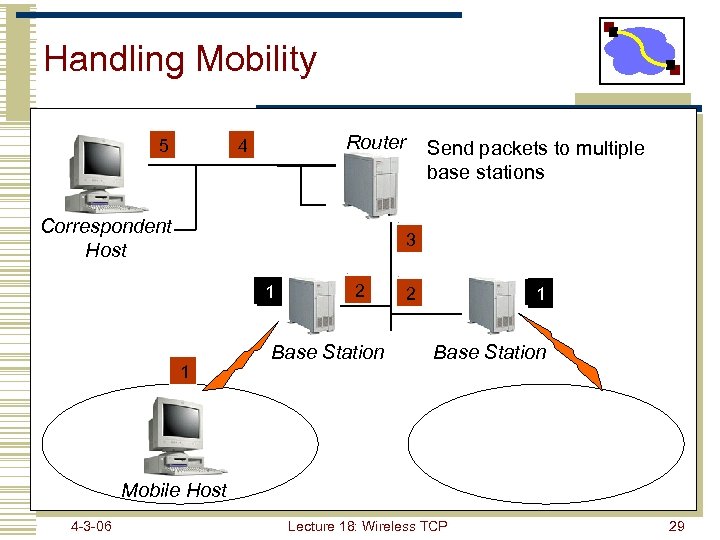 Handling Mobility 5 Router 4 Correspondent Host Send packets to multiple base stations 3 1 1 2 Base Station 2 1 Base Station Mobile Host 4 -3 -06 Lecture 18: Wireless TCP 29
Handling Mobility 5 Router 4 Correspondent Host Send packets to multiple base stations 3 1 1 2 Base Station 2 1 Base Station Mobile Host 4 -3 -06 Lecture 18: Wireless TCP 29
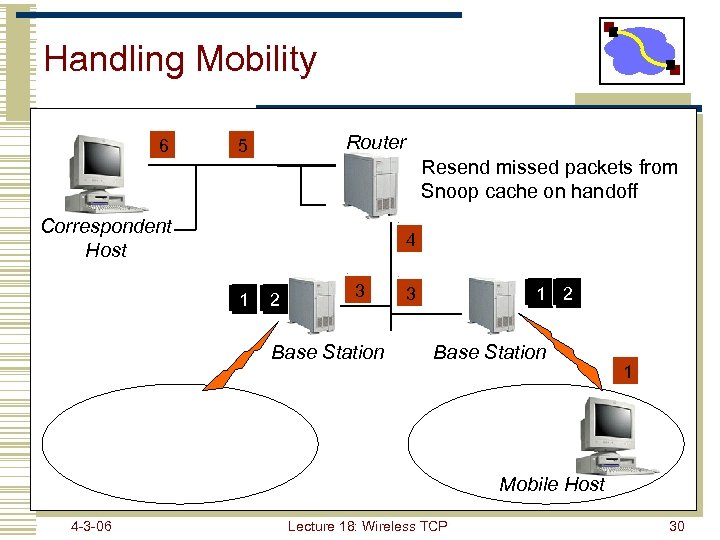 Handling Mobility 6 Router 5 Resend missed packets from Snoop cache on handoff Correspondent Host 4 1 2 3 Base Station 3 1 2 Base Station 1 Mobile Host 4 -3 -06 Lecture 18: Wireless TCP 30
Handling Mobility 6 Router 5 Resend missed packets from Snoop cache on handoff Correspondent Host 4 1 2 3 Base Station 3 1 2 Base Station 1 Mobile Host 4 -3 -06 Lecture 18: Wireless TCP 30
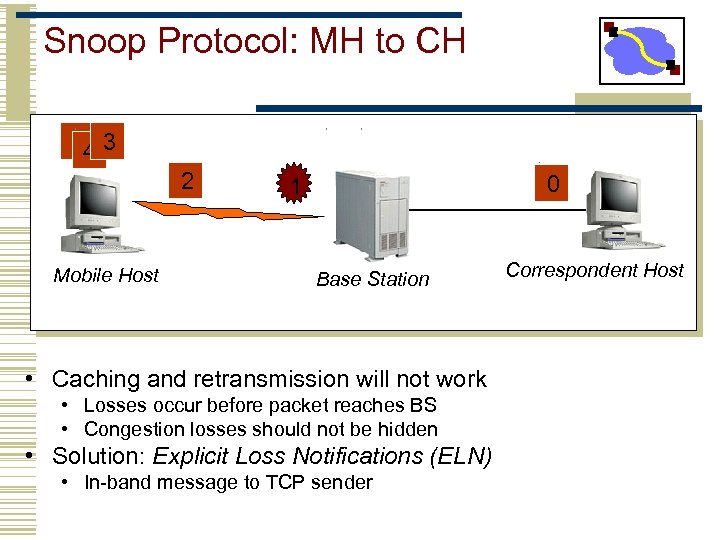 Snoop Protocol: MH to CH 65 3 4 2 Mobile Host 0 1 Base Station • Caching and retransmission will not work • Losses occur before packet reaches BS • Congestion losses should not be hidden • Solution: Explicit Loss Notifications (ELN) • In-band message to TCP sender Correspondent Host
Snoop Protocol: MH to CH 65 3 4 2 Mobile Host 0 1 Base Station • Caching and retransmission will not work • Losses occur before packet reaches BS • Congestion losses should not be hidden • Solution: Explicit Loss Notifications (ELN) • In-band message to TCP sender Correspondent Host
 Snoop Protocol: MH to CH 65 21 3 4 0 Mobile Host Base Station • MH begins transfer to CH Correspondent Host
Snoop Protocol: MH to CH 65 21 3 4 0 Mobile Host Base Station • MH begins transfer to CH Correspondent Host
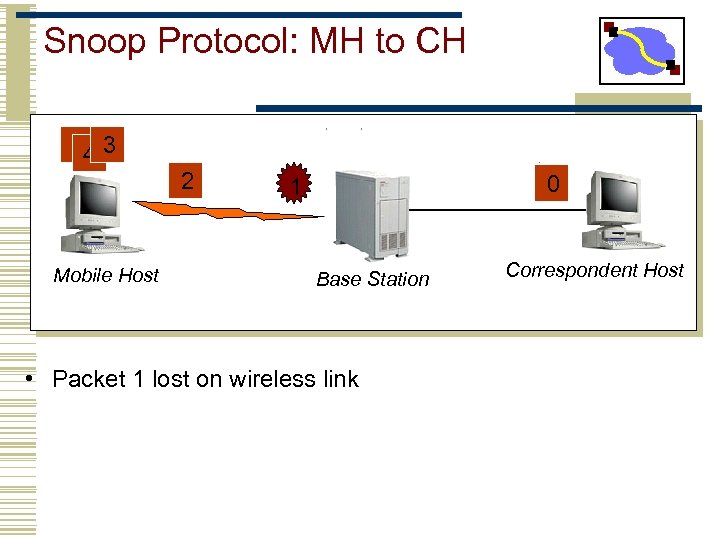 Snoop Protocol: MH to CH 65 3 4 Mobile Host 2 0 1 Base Station • Packet 1 lost on wireless link Correspondent Host
Snoop Protocol: MH to CH 65 3 4 Mobile Host 2 0 1 Base Station • Packet 1 lost on wireless link Correspondent Host
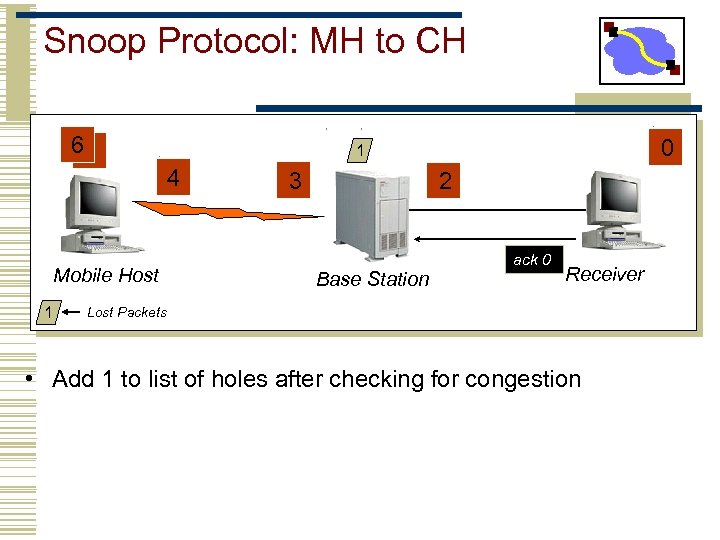 Snoop Protocol: MH to CH 65 4 Mobile Host 1 0 1 3 2 Base Station ack 0 Receiver Lost Packets • Add 1 to list of holes after checking for congestion
Snoop Protocol: MH to CH 65 4 Mobile Host 1 0 1 3 2 Base Station ack 0 Receiver Lost Packets • Add 1 to list of holes after checking for congestion
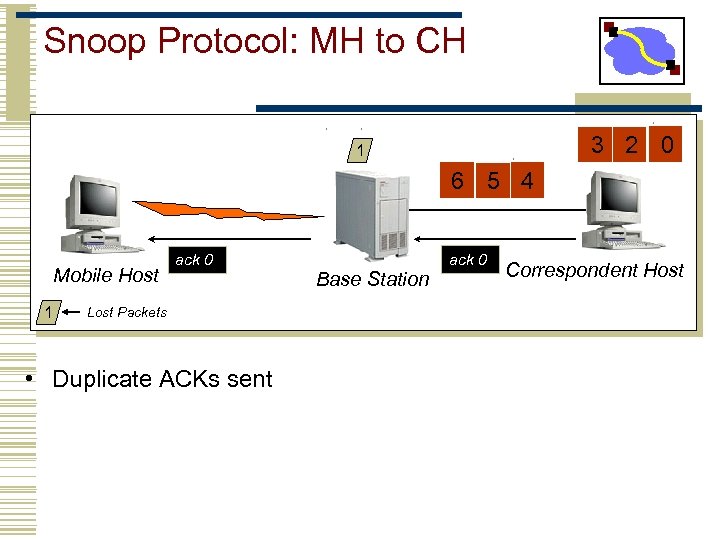 Snoop Protocol: MH to CH 3 2 0 1 6 5 4 Mobile Host 1 ack 0 Lost Packets • Duplicate ACKs sent Base Station ack 0 Correspondent Host
Snoop Protocol: MH to CH 3 2 0 1 6 5 4 Mobile Host 1 ack 0 Lost Packets • Duplicate ACKs sent Base Station ack 0 Correspondent Host
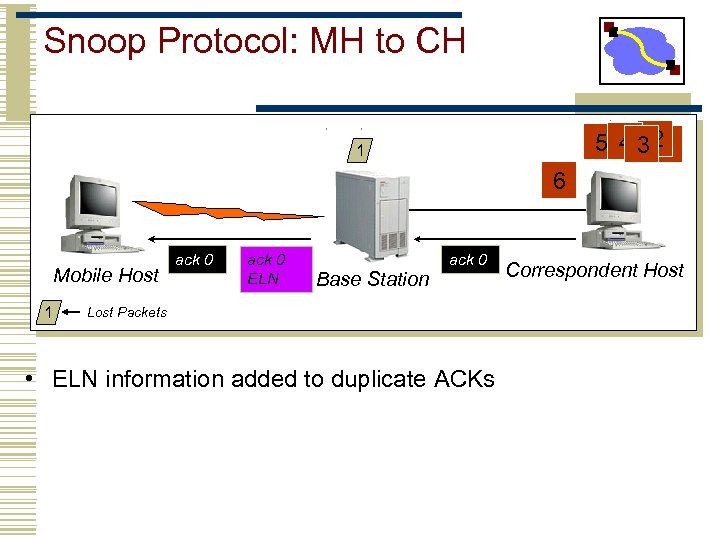 Snoop Protocol: MH to CH 5 4 320 1 6 Mobile Host 1 ack 0 ELN Base Station ack 0 Lost Packets • ELN information added to duplicate ACKs Correspondent Host
Snoop Protocol: MH to CH 5 4 320 1 6 Mobile Host 1 ack 0 ELN Base Station ack 0 Lost Packets • ELN information added to duplicate ACKs Correspondent Host
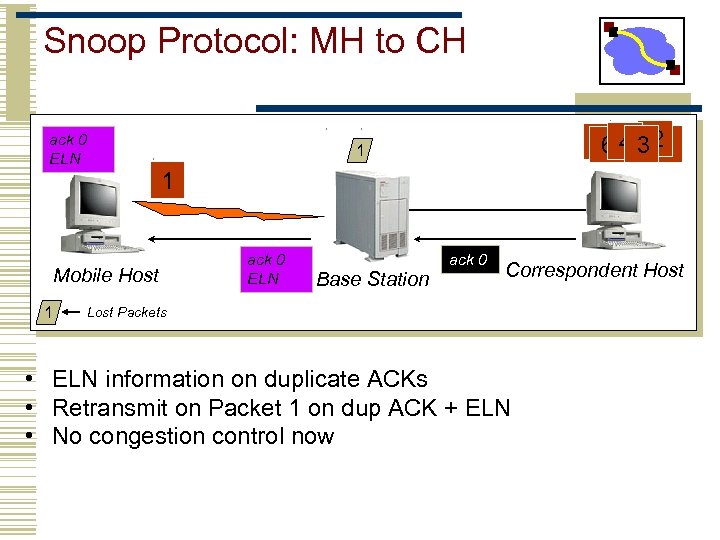 Snoop Protocol: MH to CH ack 0 ELN 1 Mobile Host 1 5 4 320 6 1 ack 0 ELN Base Station ack 0 Correspondent Host Lost Packets • ELN information on duplicate ACKs • Retransmit on Packet 1 on dup ACK + ELN • No congestion control now
Snoop Protocol: MH to CH ack 0 ELN 1 Mobile Host 1 5 4 320 6 1 ack 0 ELN Base Station ack 0 Correspondent Host Lost Packets • ELN information on duplicate ACKs • Retransmit on Packet 1 on dup ACK + ELN • No congestion control now
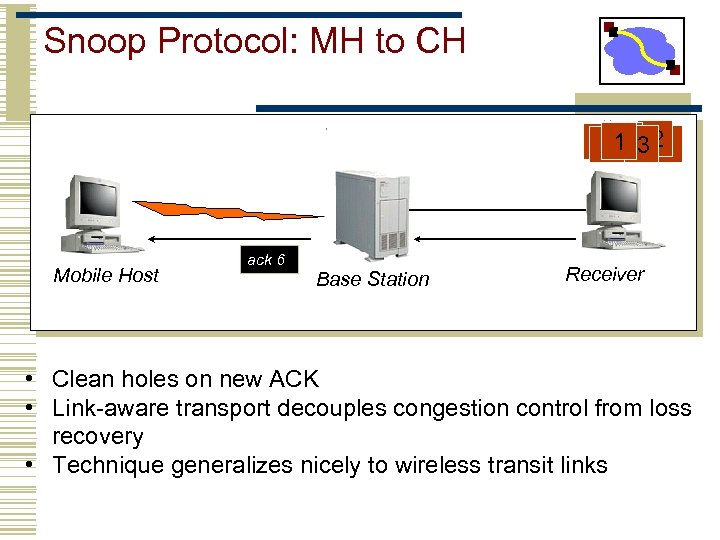 Snoop Protocol: MH to CH 5 1 320 64 Mobile Host ack 6 Base Station Receiver • Clean holes on new ACK • Link-aware transport decouples congestion control from loss recovery • Technique generalizes nicely to wireless transit links
Snoop Protocol: MH to CH 5 1 320 64 Mobile Host ack 6 Base Station Receiver • Clean holes on new ACK • Link-aware transport decouples congestion control from loss recovery • Technique generalizes nicely to wireless transit links
 Discussion • Why does Snoop perform well? • Hides out-of-order delivery from sender • 4 -3 -06 Current reliable MACs do single packet at a time reliability no out-of-order delivery [R. 5] Lecture 18: Wireless TCP 41
Discussion • Why does Snoop perform well? • Hides out-of-order delivery from sender • 4 -3 -06 Current reliable MACs do single packet at a time reliability no out-of-order delivery [R. 5] Lecture 18: Wireless TCP 41
![• [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G. • [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G.](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-40.jpg) • [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G. Holland N. Vaidya, Wireless Networks 8, 2002 4 -3 -06 Lecture 18: Wireless TCP 42
• [R. 6] Analysis of TCP Performance over Mobile Ad Hoc Networks, G. Holland N. Vaidya, Wireless Networks 8, 2002 4 -3 -06 Lecture 18: Wireless TCP 42
 TCP ELFN (Explicit Link Failure Notification ) • Analysis of TCP performance in static, linear, multi hop wireless network • Analysis of TCP in MANETs using expected throughput and measured throughput • Suggestion of TCP ELFN • Simulation results 4 -3 -06 Lecture 18: Wireless TCP 43
TCP ELFN (Explicit Link Failure Notification ) • Analysis of TCP performance in static, linear, multi hop wireless network • Analysis of TCP in MANETs using expected throughput and measured throughput • Suggestion of TCP ELFN • Simulation results 4 -3 -06 Lecture 18: Wireless TCP 43
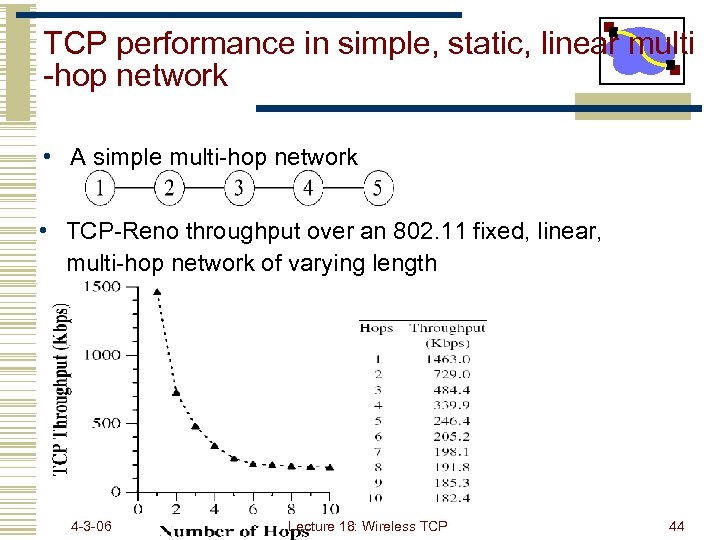 TCP performance in simple, static, linear multi -hop network • A simple multi-hop network • TCP-Reno throughput over an 802. 11 fixed, linear, multi-hop network of varying length 4 -3 -06 Lecture 18: Wireless TCP 44
TCP performance in simple, static, linear multi -hop network • A simple multi-hop network • TCP-Reno throughput over an 802. 11 fixed, linear, multi-hop network of varying length 4 -3 -06 Lecture 18: Wireless TCP 44
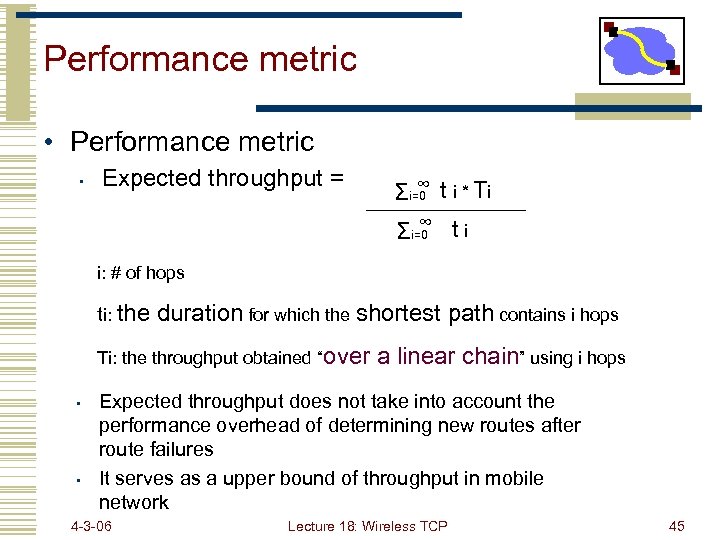 Performance metric • Expected throughput = ∞ Σi=0 t i * Ti ∞ Σi=0 t i i: # of hops ti: the duration for which the shortest path contains i hops Ti: the throughput obtained “over • • a linear chain” using i hops Expected throughput does not take into account the performance overhead of determining new routes after route failures It serves as a upper bound of throughput in mobile network 4 -3 -06 Lecture 18: Wireless TCP 45
Performance metric • Expected throughput = ∞ Σi=0 t i * Ti ∞ Σi=0 t i i: # of hops ti: the duration for which the shortest path contains i hops Ti: the throughput obtained “over • • a linear chain” using i hops Expected throughput does not take into account the performance overhead of determining new routes after route failures It serves as a upper bound of throughput in mobile network 4 -3 -06 Lecture 18: Wireless TCP 45
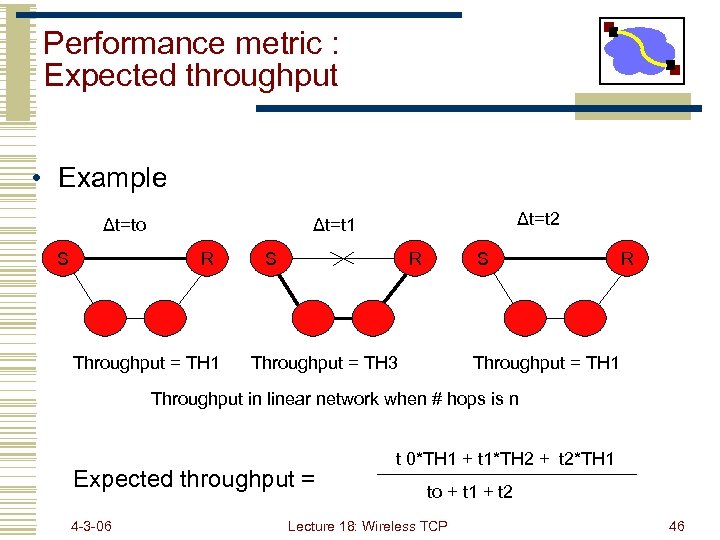 Performance metric : Expected throughput • Example Δt=to S Δt=t 2 Δt=t 1 R Throughput = TH 1 S R S Throughput = TH 3 R Throughput = TH 1 Throughput in linear network when # hops is n Expected throughput = 4 -3 -06 t 0*TH 1 + t 1*TH 2 + t 2*TH 1 to + t 1 + t 2 Lecture 18: Wireless TCP 46
Performance metric : Expected throughput • Example Δt=to S Δt=t 2 Δt=t 1 R Throughput = TH 1 S R S Throughput = TH 3 R Throughput = TH 1 Throughput in linear network when # hops is n Expected throughput = 4 -3 -06 t 0*TH 1 + t 1*TH 2 + t 2*TH 1 to + t 1 + t 2 Lecture 18: Wireless TCP 46
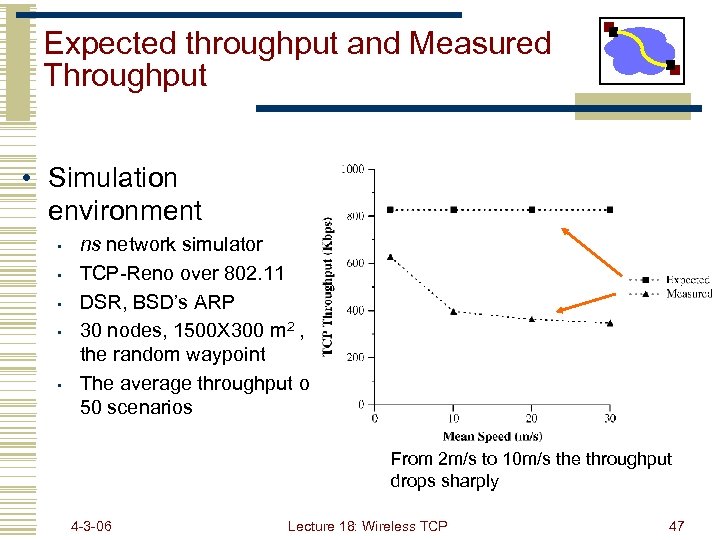 Expected throughput and Measured Throughput • Simulation environment • • • ns network simulator TCP-Reno over 802. 11 DSR, BSD’s ARP 30 nodes, 1500 X 300 m 2 , the random waypoint The average throughput of 50 scenarios From 2 m/s to 10 m/s the throughput drops sharply 4 -3 -06 Lecture 18: Wireless TCP 47
Expected throughput and Measured Throughput • Simulation environment • • • ns network simulator TCP-Reno over 802. 11 DSR, BSD’s ARP 30 nodes, 1500 X 300 m 2 , the random waypoint The average throughput of 50 scenarios From 2 m/s to 10 m/s the throughput drops sharply 4 -3 -06 Lecture 18: Wireless TCP 47
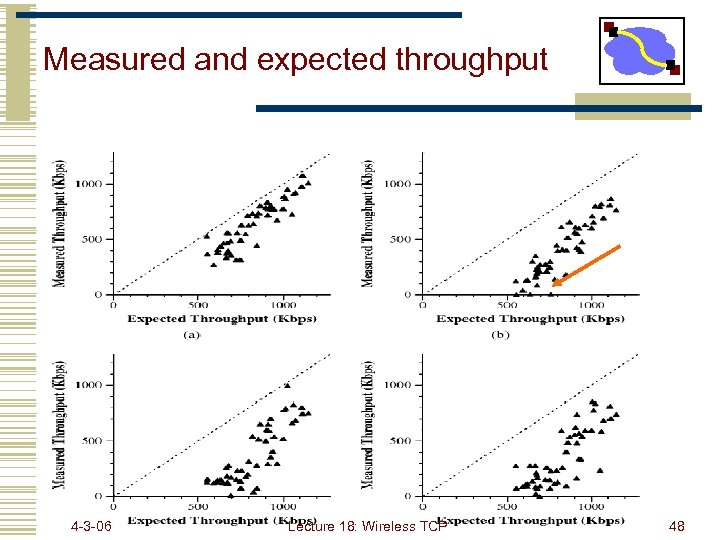 Measured and expected throughput 4 -3 -06 Lecture 18: Wireless TCP 48
Measured and expected throughput 4 -3 -06 Lecture 18: Wireless TCP 48
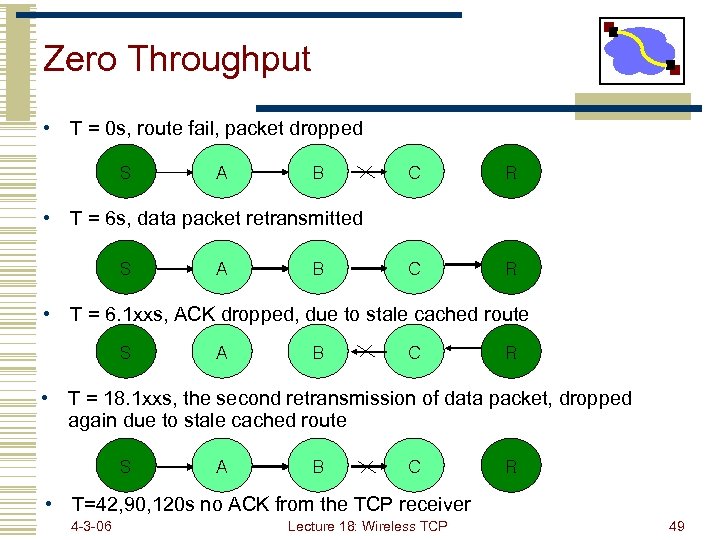 Zero Throughput • T = 0 s, route fail, packet dropped S A B C R • T = 6 s, data packet retransmitted S A B • T = 6. 1 xxs, ACK dropped, due to stale cached route S A B C R • T = 18. 1 xxs, the second retransmission of data packet, dropped again due to stale cached route S A B C R • T=42, 90, 120 s no ACK from the TCP receiver 4 -3 -06 Lecture 18: Wireless TCP 49
Zero Throughput • T = 0 s, route fail, packet dropped S A B C R • T = 6 s, data packet retransmitted S A B • T = 6. 1 xxs, ACK dropped, due to stale cached route S A B C R • T = 18. 1 xxs, the second retransmission of data packet, dropped again due to stale cached route S A B C R • T=42, 90, 120 s no ACK from the TCP receiver 4 -3 -06 Lecture 18: Wireless TCP 49
 Some facts • In previous example, only for 6 s of 120 s the network is partitioned • DSR’s stale cached route can degrade TCP throughput significantly • DSR does not retransmit dropped packet when it receives Route Error Msg, and the TCP sender or receiver does not know about the packet loss • The TCP sender waits for occurring time out • Unnecessary RTO back-off of the TCP sender makes problems even worse 4 -3 -06 Lecture 18: Wireless TCP 50
Some facts • In previous example, only for 6 s of 120 s the network is partitioned • DSR’s stale cached route can degrade TCP throughput significantly • DSR does not retransmit dropped packet when it receives Route Error Msg, and the TCP sender or receiver does not know about the packet loss • The TCP sender waits for occurring time out • Unnecessary RTO back-off of the TCP sender makes problems even worse 4 -3 -06 Lecture 18: Wireless TCP 50
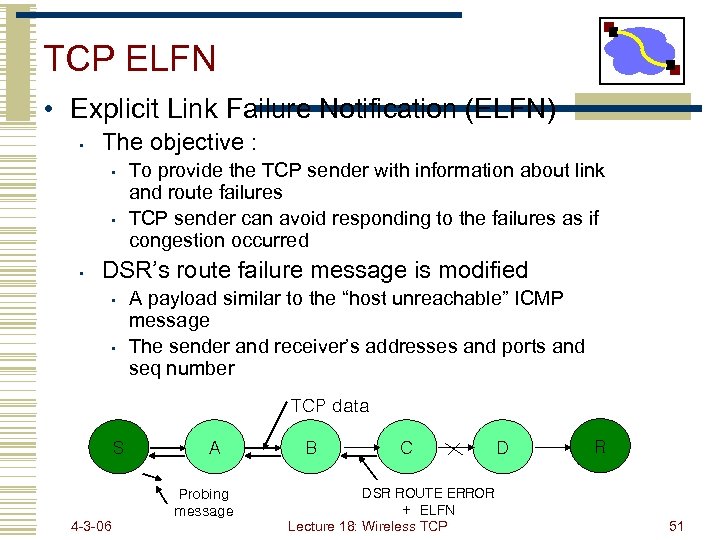 TCP ELFN • Explicit Link Failure Notification (ELFN) • The objective : • • • To provide the TCP sender with information about link and route failures TCP sender can avoid responding to the failures as if congestion occurred DSR’s route failure message is modified • • A payload similar to the “host unreachable” ICMP message The sender and receiver’s addresses and ports and seq number TCP data S A Probing message 4 -3 -06 B C DSR ROUTE ERROR + ELFN Lecture 18: Wireless TCP D R 51
TCP ELFN • Explicit Link Failure Notification (ELFN) • The objective : • • • To provide the TCP sender with information about link and route failures TCP sender can avoid responding to the failures as if congestion occurred DSR’s route failure message is modified • • A payload similar to the “host unreachable” ICMP message The sender and receiver’s addresses and ports and seq number TCP data S A Probing message 4 -3 -06 B C DSR ROUTE ERROR + ELFN Lecture 18: Wireless TCP D R 51
 TCP ELFN • Sender reaction • When a TCP sender receives an ELFN, • • While on standby, • • It disables its retransmission timers and enters a “stanby” mode A packet is sent at periodic intervals to probe the network to see if a route has been established If an acknowledgment is received, • 4 -3 -06 Then it leaves standby mode Lecture 18: Wireless TCP 52
TCP ELFN • Sender reaction • When a TCP sender receives an ELFN, • • While on standby, • • It disables its retransmission timers and enters a “stanby” mode A packet is sent at periodic intervals to probe the network to see if a route has been established If an acknowledgment is received, • 4 -3 -06 Then it leaves standby mode Lecture 18: Wireless TCP 52
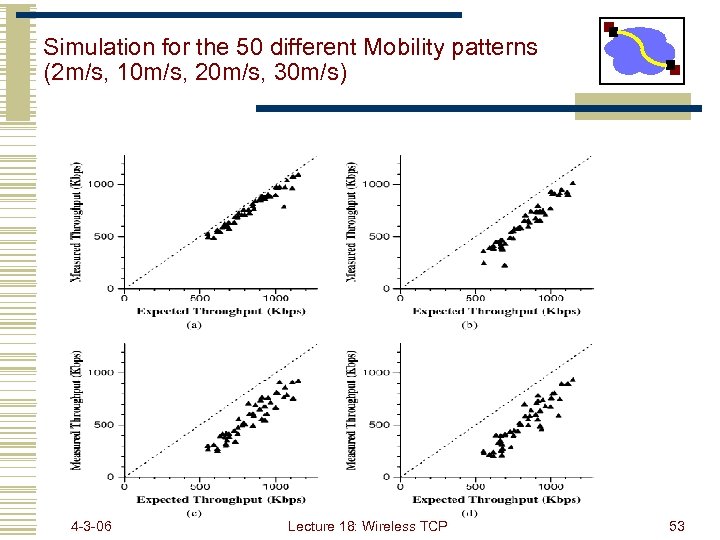 Simulation for the 50 different Mobility patterns (2 m/s, 10 m/s, 20 m/s, 30 m/s) 4 -3 -06 Lecture 18: Wireless TCP 53
Simulation for the 50 different Mobility patterns (2 m/s, 10 m/s, 20 m/s, 30 m/s) 4 -3 -06 Lecture 18: Wireless TCP 53
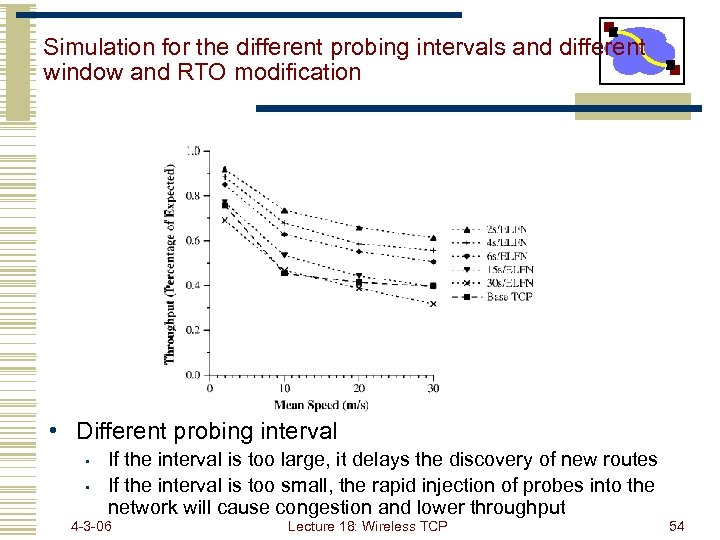 Simulation for the different probing intervals and different window and RTO modification • Different probing interval • • If the interval is too large, it delays the discovery of new routes If the interval is too small, the rapid injection of probes into the network will cause congestion and lower throughput 4 -3 -06 Lecture 18: Wireless TCP 54
Simulation for the different probing intervals and different window and RTO modification • Different probing interval • • If the interval is too large, it delays the discovery of new routes If the interval is too small, the rapid injection of probes into the network will cause congestion and lower throughput 4 -3 -06 Lecture 18: Wireless TCP 54
![• [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan, • [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan,](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-53.jpg) • [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan, Vaidyanathan Anantharaman, Hung-Yun Hsieh, Raghupathy Sivakumar, Mobi. Hoc'03. 4 -3 -06 Lecture 18: Wireless TCP 55
• [R. 7] ATP: A Reliable Transport Protocol for Ad-hoc Networks, Karthikeyan Sundaresan, Vaidyanathan Anantharaman, Hung-Yun Hsieh, Raghupathy Sivakumar, Mobi. Hoc'03. 4 -3 -06 Lecture 18: Wireless TCP 55
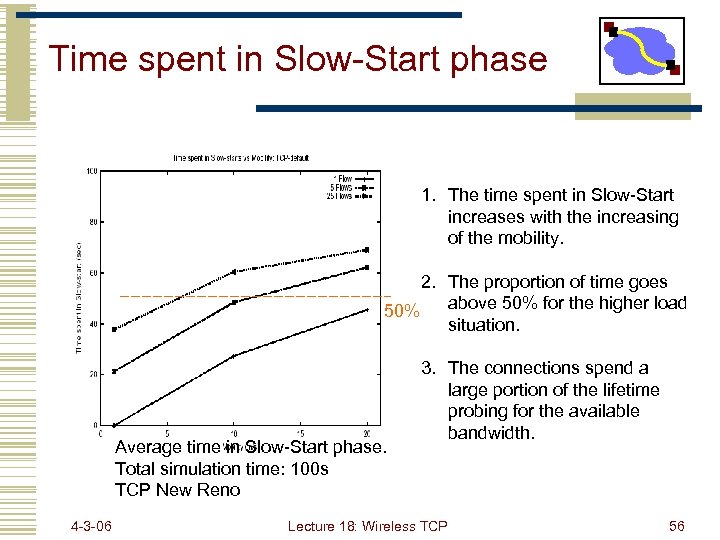 Time spent in Slow-Start phase 1. The time spent in Slow-Start increases with the increasing of the mobility. 2. The proportion of time goes above 50% for the higher load 50% situation. Average time in Slow-Start phase. Total simulation time: 100 s TCP New Reno 4 -3 -06 3. The connections spend a large portion of the lifetime probing for the available bandwidth. Lecture 18: Wireless TCP 56
Time spent in Slow-Start phase 1. The time spent in Slow-Start increases with the increasing of the mobility. 2. The proportion of time goes above 50% for the higher load 50% situation. Average time in Slow-Start phase. Total simulation time: 100 s TCP New Reno 4 -3 -06 3. The connections spend a large portion of the lifetime probing for the available bandwidth. Lecture 18: Wireless TCP 56
 Key design elements of ATP • Cross layer coordination • Rate based transmissions • This is the core of ATP • Decoupled congestion control and reliability 4 -3 -06 Lecture 18: Wireless TCP 57
Key design elements of ATP • Cross layer coordination • Rate based transmissions • This is the core of ATP • Decoupled congestion control and reliability 4 -3 -06 Lecture 18: Wireless TCP 57
 Layer Coordination Similar to TCP-ELFN • Utilize explicit feedback from intermediate nodes. • ATP uses layer coordination for • • 4 -3 -06 Path failure notification Initiating a sending-rate estimation for the new route Lecture 18: Wireless TCP 58
Layer Coordination Similar to TCP-ELFN • Utilize explicit feedback from intermediate nodes. • ATP uses layer coordination for • • 4 -3 -06 Path failure notification Initiating a sending-rate estimation for the new route Lecture 18: Wireless TCP 58
 Rate based transmissions • What is rate based transmission • Transmit fixed size of data in each time interval. • • GSM example, 260 bits from speech codec in every 20 ms Use timer to clock the new data, not the sending window • Avoids drawbacks due to burstiness • The need for self-clocking by the arrival of ACKs is eliminated • Allows decoupling of congestion control mechanism from the reliability mechanism • Timer granularity in low bandwidth MANETS large enough to be realized without significant overheads 4 -3 -06 Lecture 18: Wireless TCP 59
Rate based transmissions • What is rate based transmission • Transmit fixed size of data in each time interval. • • GSM example, 260 bits from speech codec in every 20 ms Use timer to clock the new data, not the sending window • Avoids drawbacks due to burstiness • The need for self-clocking by the arrival of ACKs is eliminated • Allows decoupling of congestion control mechanism from the reliability mechanism • Timer granularity in low bandwidth MANETS large enough to be realized without significant overheads 4 -3 -06 Lecture 18: Wireless TCP 59
 Decoupling of Congestion Control & Reliability • For congestion control: • • • Intermediate nodes provide the feedback of available rate. The feedback is piggybacked on forward path and sent back from receiver to sender. The sender adjusts the sending rate accordingly. • For reliability: • 4 -3 -06 The receiver uses SACK to report any new holes in the data stream. Lecture 18: Wireless TCP 60
Decoupling of Congestion Control & Reliability • For congestion control: • • • Intermediate nodes provide the feedback of available rate. The feedback is piggybacked on forward path and sent back from receiver to sender. The sender adjusts the sending rate accordingly. • For reliability: • 4 -3 -06 The receiver uses SACK to report any new holes in the data stream. Lecture 18: Wireless TCP 60
![• [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A • [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A](https://present5.com/presentation/a12422e128adcf2d5ab055785d20f907/image-59.jpg) • [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A Receiver-Centric Transport Protocol for Mobile Hosts with Heterogeneous Wireless Interfaces. Mobi. Com 2003. 4 -3 -06 Lecture 18: Wireless TCP 61
• [R. 8] Hung-Yun Hsieh, Kyu-Han Kim, Yujie Zhu, and Raghupathy Sivakumar. A Receiver-Centric Transport Protocol for Mobile Hosts with Heterogeneous Wireless Interfaces. Mobi. Com 2003. 4 -3 -06 Lecture 18: Wireless TCP 61
 Core Thesis Behind Proposal • The wireless last link is crucial • Receiver has accurate knowledge of channel conditions • Receiver has knowledge of all its interfaces • Receiver can handle functionality without making changes at the sender 4 -3 -06 Lecture 18: Wireless TCP 62
Core Thesis Behind Proposal • The wireless last link is crucial • Receiver has accurate knowledge of channel conditions • Receiver has knowledge of all its interfaces • Receiver can handle functionality without making changes at the sender 4 -3 -06 Lecture 18: Wireless TCP 62
 Loss recovery • React to non-congestion related losses • Sender-centric approach • • Sender needs feedback from receiver Difficult to provide all types of feedback • Receiver-centric approach • Avoids feedback overheads and latency 4 -3 -06 Lecture 18: Wireless TCP 63
Loss recovery • React to non-congestion related losses • Sender-centric approach • • Sender needs feedback from receiver Difficult to provide all types of feedback • Receiver-centric approach • Avoids feedback overheads and latency 4 -3 -06 Lecture 18: Wireless TCP 63
 Congestion Control • Discover the point of threshold of packet loss • Sender-centric • Server might need several congestion control schemes for the different types of connections • Receiver-centric • • Receiver responsible for congestions control Each receiver can implement its own congestion control 4 -3 -06 Lecture 18: Wireless TCP 64
Congestion Control • Discover the point of threshold of packet loss • Sender-centric • Server might need several congestion control schemes for the different types of connections • Receiver-centric • • Receiver responsible for congestions control Each receiver can implement its own congestion control 4 -3 -06 Lecture 18: Wireless TCP 64
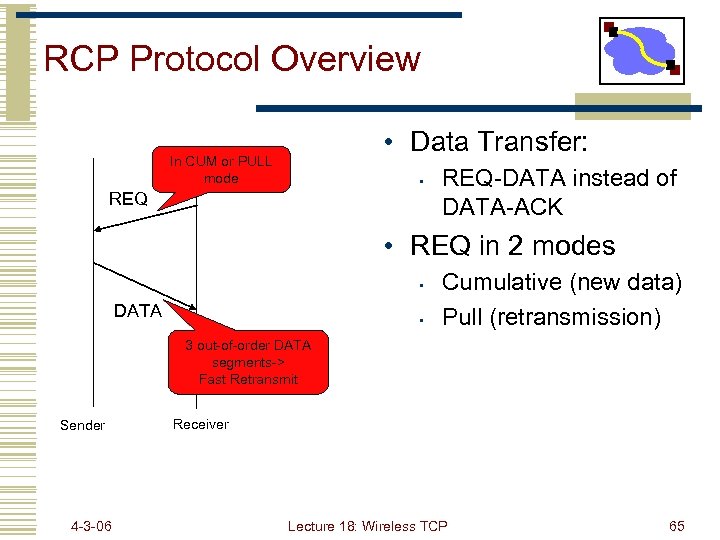 RCP Protocol Overview • Data Transfer: In CUM or PULL mode • REQ-DATA instead of DATA-ACK • REQ in 2 modes • DATA • Cumulative (new data) Pull (retransmission) 3 out-of-order DATA segments-> Fast Retransmit Sender 4 -3 -06 Receiver Lecture 18: Wireless TCP 65
RCP Protocol Overview • Data Transfer: In CUM or PULL mode • REQ-DATA instead of DATA-ACK • REQ in 2 modes • DATA • Cumulative (new data) Pull (retransmission) 3 out-of-order DATA segments-> Fast Retransmit Sender 4 -3 -06 Receiver Lecture 18: Wireless TCP 65
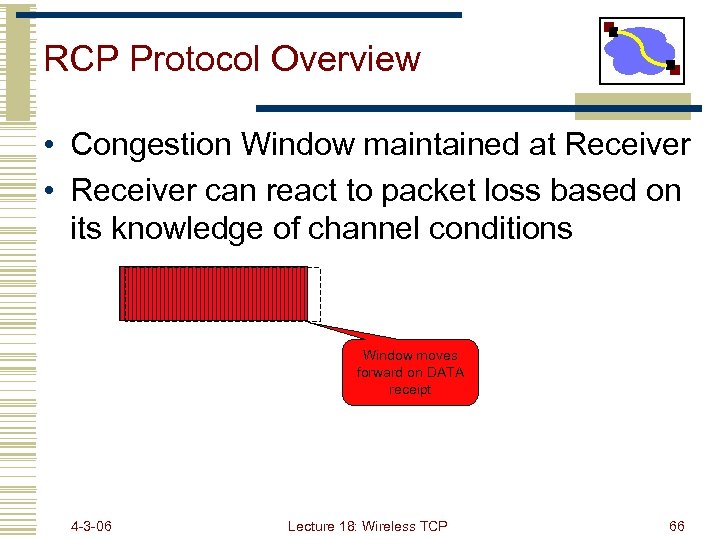 RCP Protocol Overview • Congestion Window maintained at Receiver • Receiver can react to packet loss based on its knowledge of channel conditions Window moves forward on DATA receipt 4 -3 -06 Lecture 18: Wireless TCP 66
RCP Protocol Overview • Congestion Window maintained at Receiver • Receiver can react to packet loss based on its knowledge of channel conditions Window moves forward on DATA receipt 4 -3 -06 Lecture 18: Wireless TCP 66


