6152a629074fa764d6605571e7cf5f8e.ppt
- Количество слайдов: 35
 15 -213 “The course that gives CMU its Zip!” Machine-Level Programming V: Advanced Topics Sept. 18, 2008 Topics n Linux Memory Layout Understanding Pointers n Buffer Overflow n Floating Point Code n class 08. ppt
15 -213 “The course that gives CMU its Zip!” Machine-Level Programming V: Advanced Topics Sept. 18, 2008 Topics n Linux Memory Layout Understanding Pointers n Buffer Overflow n Floating Point Code n class 08. ppt
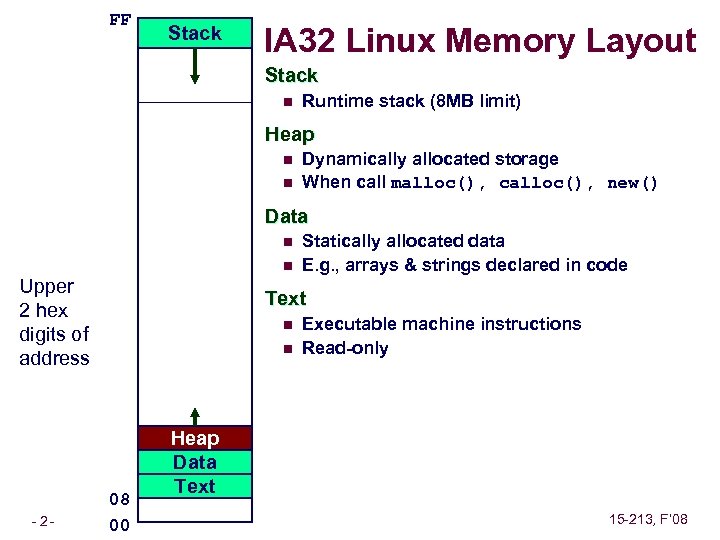 FF Stack IA 32 Linux Memory Layout Stack n Runtime stack (8 MB limit) Heap n n Dynamically allocated storage When call malloc(), calloc(), new() Data n n Upper 2 hex digits of address – 2– Statically allocated data E. g. , arrays & strings declared in code Text n n 08 00 Executable machine instructions Read-only Heap Data Text 15 -213, F’ 08
FF Stack IA 32 Linux Memory Layout Stack n Runtime stack (8 MB limit) Heap n n Dynamically allocated storage When call malloc(), calloc(), new() Data n n Upper 2 hex digits of address – 2– Statically allocated data E. g. , arrays & strings declared in code Text n n 08 00 Executable machine instructions Read-only Heap Data Text 15 -213, F’ 08
![Memory Allocation Example char big_array[1<<24]; /* 16 MB */ char huge_array[1<<28]; /* 256 MB Memory Allocation Example char big_array[1<<24]; /* 16 MB */ char huge_array[1<<28]; /* 256 MB](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-3.jpg) Memory Allocation Example char big_array[1<<24]; /* 16 MB */ char huge_array[1<<28]; /* 256 MB */ int beyond; char *p 1, *p 2, *p 3, *p 4; int useless() { int { p 1 p 2 p 3 p 4 /* } – 3– return 0; } main() = malloc(1 Some print <<28); /* << 8); /* statements 256 256. . . MB B */ */ */ 15 -213, F’ 08
Memory Allocation Example char big_array[1<<24]; /* 16 MB */ char huge_array[1<<28]; /* 256 MB */ int beyond; char *p 1, *p 2, *p 3, *p 4; int useless() { int { p 1 p 2 p 3 p 4 /* } – 3– return 0; } main() = malloc(1 Some print <<28); /* << 8); /* statements 256 256. . . MB B */ */ */ 15 -213, F’ 08
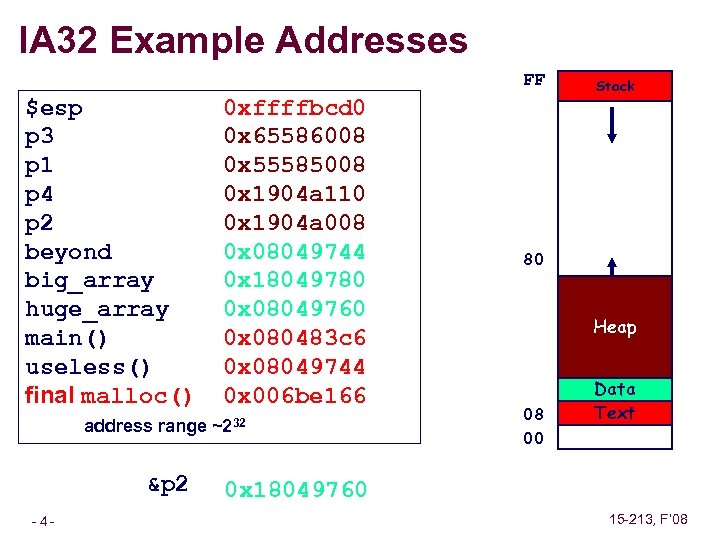 IA 32 Example Addresses FF $esp p 3 p 1 p 4 p 2 beyond big_array huge_array main() useless() final malloc() 0 xffffbcd 0 0 x 65586008 0 x 55585008 0 x 1904 a 110 0 x 1904 a 008 0 x 08049744 0 x 18049780 0 x 08049760 0 x 080483 c 6 0 x 08049744 0 x 006 be 166 address range ~232 &p 2 – 4– Stack 80 Heap 08 00 Data Text 0 x 18049760 15 -213, F’ 08
IA 32 Example Addresses FF $esp p 3 p 1 p 4 p 2 beyond big_array huge_array main() useless() final malloc() 0 xffffbcd 0 0 x 65586008 0 x 55585008 0 x 1904 a 110 0 x 1904 a 008 0 x 08049744 0 x 18049780 0 x 08049760 0 x 080483 c 6 0 x 08049744 0 x 006 be 166 address range ~232 &p 2 – 4– Stack 80 Heap 08 00 Data Text 0 x 18049760 15 -213, F’ 08
 x 86 -64 Example Addresses 7 F $rsp p 3 p 1 p 4 p 2 beyond big_array huge_array main() useless() final malloc() 0 x 7 ffffff 8 d 1 f 8 0 x 2 aaabaadd 010 0 x 2 aaaaaadc 010 0 x 000011501120 0 x 000011501010 0 x 000000500 a 44 0 x 000010500 a 80 0 x 000000500 a 50 0 x 000000400510 0 x 000000400500 0 x 00386 ae 6 a 170 address range ~247 Stack 30 Heap 08 00 Data Text &p 2 0 x 000010500 a 60 – 5– 15 -213, F’ 08
x 86 -64 Example Addresses 7 F $rsp p 3 p 1 p 4 p 2 beyond big_array huge_array main() useless() final malloc() 0 x 7 ffffff 8 d 1 f 8 0 x 2 aaabaadd 010 0 x 2 aaaaaadc 010 0 x 000011501120 0 x 000011501010 0 x 000000500 a 44 0 x 000010500 a 80 0 x 000000500 a 50 0 x 000000400510 0 x 000000400500 0 x 00386 ae 6 a 170 address range ~247 Stack 30 Heap 08 00 Data Text &p 2 0 x 000010500 a 60 – 5– 15 -213, F’ 08
![C operators Operators Associativity () [] ->. ! ~ ++ -- + - * C operators Operators Associativity () [] ->. ! ~ ++ -- + - *](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-6.jpg) C operators Operators Associativity () [] ->. ! ~ ++ -- + - * & (type) sizeof * / % + << >> < <= > >= == != & ^ | && || ? : = += -= *= /= %= &= ^= != <<= >>= , left to right to left to right left to right left to right to left right to left to right n n n – 6– -> has very high precedence () has very high precedence monadic * just below 15 -213, F’ 08
C operators Operators Associativity () [] ->. ! ~ ++ -- + - * & (type) sizeof * / % + << >> < <= > >= == != & ^ | && || ? : = += -= *= /= %= &= ^= != <<= >>= , left to right to left to right left to right left to right to left right to left to right n n n – 6– -> has very high precedence () has very high precedence monadic * just below 15 -213, F’ 08
![C pointer declarations int *p p is a pointer to int *p[13] p is C pointer declarations int *p p is a pointer to int *p[13] p is](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-7.jpg) C pointer declarations int *p p is a pointer to int *p[13] p is an array[13] of pointer to int *(p[13]) p is an array[13] of pointer to int **p p is a pointer to an int (*p)[13] p is a pointer to an array[13] of int *f() f is a function returning a pointer to int (*f)() f is a pointer to a function returning int (*(*f())[13])() f is a function returning ptr to an array[13] of pointers to functions returning int (*(*x[3])())[5] x is an array[3] of pointers to functions returning pointers to array[5] of ints 15 -213, F’ 08 – 7–
C pointer declarations int *p p is a pointer to int *p[13] p is an array[13] of pointer to int *(p[13]) p is an array[13] of pointer to int **p p is a pointer to an int (*p)[13] p is a pointer to an array[13] of int *f() f is a function returning a pointer to int (*f)() f is a pointer to a function returning int (*(*f())[13])() f is a function returning ptr to an array[13] of pointers to functions returning int (*(*x[3])())[5] x is an array[3] of pointers to functions returning pointers to array[5] of ints 15 -213, F’ 08 – 7–
![Avoiding Complex Declarations Use typedef to build up the declaration Instead of int (*(*x[3])())[5] Avoiding Complex Declarations Use typedef to build up the declaration Instead of int (*(*x[3])())[5]](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-8.jpg) Avoiding Complex Declarations Use typedef to build up the declaration Instead of int (*(*x[3])())[5] : typedef int fiveints[5]; typedef fiveints* p 5 i; typedef p 5 i (*f_of_p 5 is)(); f_of_p 5 is x[3]; x is an array of 3 elements, each of which is a pointer to a function returning an array of 5 ints. – 8– 15 -213, F’ 08
Avoiding Complex Declarations Use typedef to build up the declaration Instead of int (*(*x[3])())[5] : typedef int fiveints[5]; typedef fiveints* p 5 i; typedef p 5 i (*f_of_p 5 is)(); f_of_p 5 is x[3]; x is an array of 3 elements, each of which is a pointer to a function returning an array of 5 ints. – 8– 15 -213, F’ 08
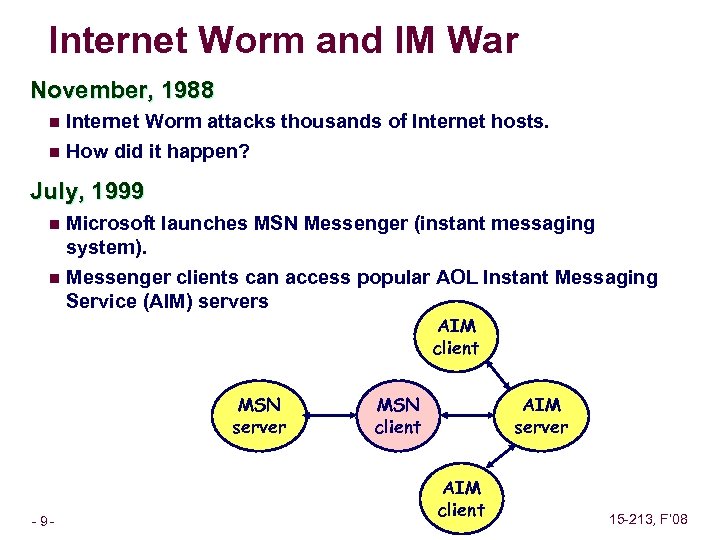 Internet Worm and IM War November, 1988 n Internet Worm attacks thousands of Internet hosts. n How did it happen? July, 1999 Microsoft launches MSN Messenger (instant messaging system). n Messenger clients can access popular AOL Instant Messaging Service (AIM) servers n AIM client MSN server – 9– MSN client AIM server AIM client 15 -213, F’ 08
Internet Worm and IM War November, 1988 n Internet Worm attacks thousands of Internet hosts. n How did it happen? July, 1999 Microsoft launches MSN Messenger (instant messaging system). n Messenger clients can access popular AOL Instant Messaging Service (AIM) servers n AIM client MSN server – 9– MSN client AIM server AIM client 15 -213, F’ 08
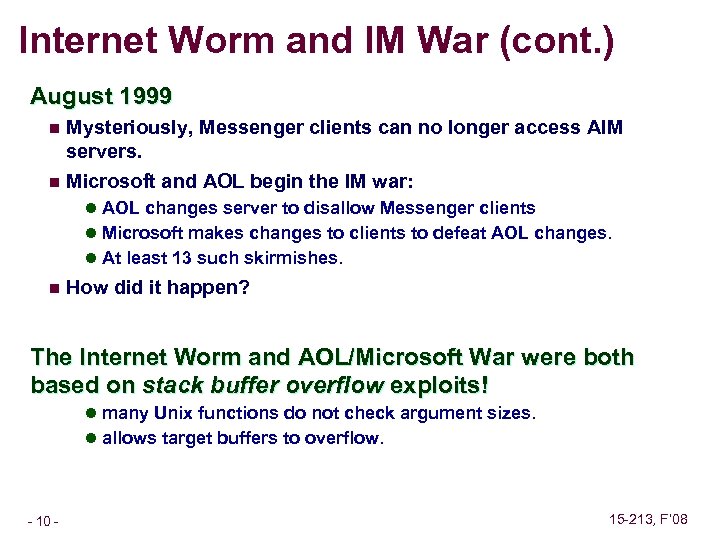 Internet Worm and IM War (cont. ) August 1999 Mysteriously, Messenger clients can no longer access AIM servers. n Microsoft and AOL begin the IM war: n l AOL changes server to disallow Messenger clients l Microsoft makes changes to clients to defeat AOL changes. l At least 13 such skirmishes. n How did it happen? The Internet Worm and AOL/Microsoft War were both based on stack buffer overflow exploits! l many Unix functions do not check argument sizes. l allows target buffers to overflow. – 10 – 15 -213, F’ 08
Internet Worm and IM War (cont. ) August 1999 Mysteriously, Messenger clients can no longer access AIM servers. n Microsoft and AOL begin the IM war: n l AOL changes server to disallow Messenger clients l Microsoft makes changes to clients to defeat AOL changes. l At least 13 such skirmishes. n How did it happen? The Internet Worm and AOL/Microsoft War were both based on stack buffer overflow exploits! l many Unix functions do not check argument sizes. l allows target buffers to overflow. – 10 – 15 -213, F’ 08
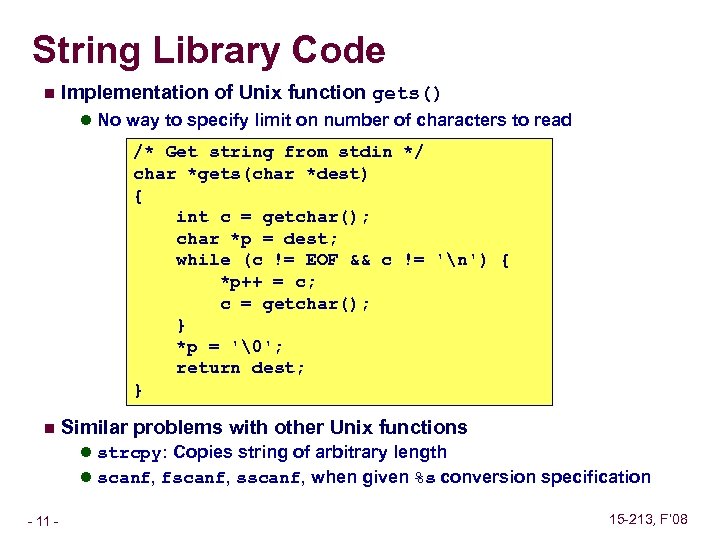 String Library Code n Implementation of Unix function gets() l No way to specify limit on number of characters to read /* Get string from stdin */ char *gets(char *dest) { int c = getchar(); char *p = dest; while (c != EOF && c != 'n') { *p++ = c; c = getchar(); } *p = '�'; return dest; } n Similar problems with other Unix functions l strcpy: Copies string of arbitrary length l scanf, fscanf, sscanf, when given %s conversion specification – 11 – 15 -213, F’ 08
String Library Code n Implementation of Unix function gets() l No way to specify limit on number of characters to read /* Get string from stdin */ char *gets(char *dest) { int c = getchar(); char *p = dest; while (c != EOF && c != 'n') { *p++ = c; c = getchar(); } *p = '�'; return dest; } n Similar problems with other Unix functions l strcpy: Copies string of arbitrary length l scanf, fscanf, sscanf, when given %s conversion specification – 11 – 15 -213, F’ 08
![Vulnerable Buffer Code /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); Vulnerable Buffer Code /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf);](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-12.jpg) Vulnerable Buffer Code /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } /* Way too small! */ int main() { printf("Type a string: "); echo(); return 0; } – 12 – 15 -213, F’ 08
Vulnerable Buffer Code /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } /* Way too small! */ int main() { printf("Type a string: "); echo(); return 0; } – 12 – 15 -213, F’ 08
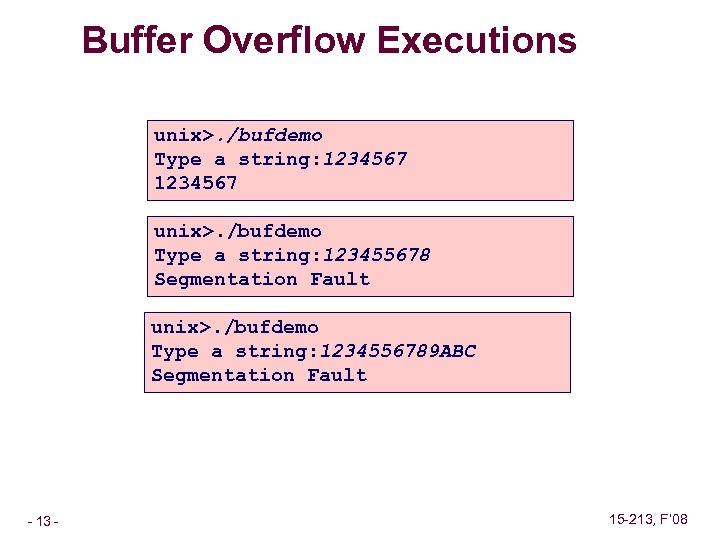 Buffer Overflow Executions unix>. /bufdemo Type a string: 1234567 unix>. /bufdemo Type a string: 123455678 Segmentation Fault unix>. /bufdemo Type a string: 1234556789 ABC Segmentation Fault – 13 – 15 -213, F’ 08
Buffer Overflow Executions unix>. /bufdemo Type a string: 1234567 unix>. /bufdemo Type a string: 123455678 Segmentation Fault unix>. /bufdemo Type a string: 1234556789 ABC Segmentation Fault – 13 – 15 -213, F’ 08
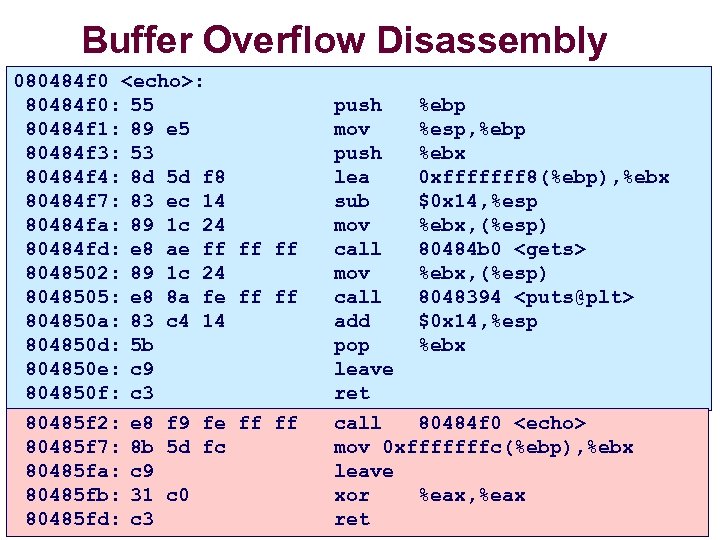 Buffer Overflow Disassembly 080484 f 0
Buffer Overflow Disassembly 080484 f 0
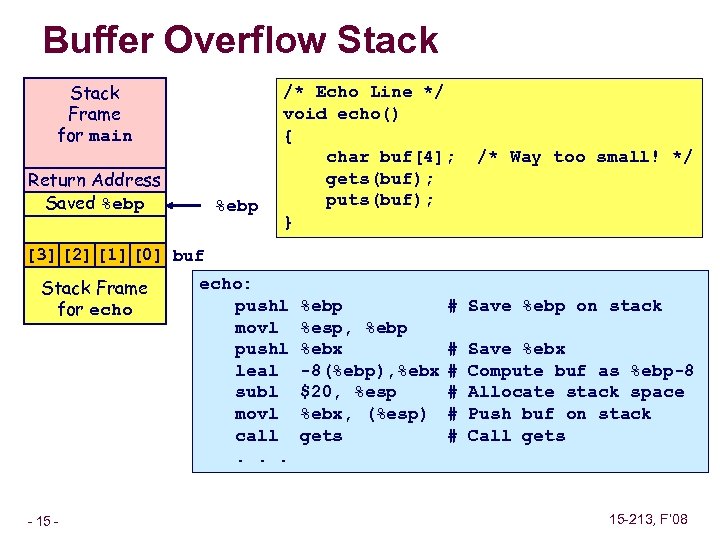 Buffer Overflow Stack Frame for main Return Address Saved %ebp /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } /* Way too small! */ [3] [2] [1] [0] buf Stack Frame for echo – 15 – echo: pushl movl pushl leal subl movl call. . . %ebp %esp, %ebp %ebx -8(%ebp), %ebx $20, %esp %ebx, (%esp) gets # Save %ebp on stack # # # Save %ebx Compute buf as %ebp-8 Allocate stack space Push buf on stack Call gets 15 -213, F’ 08
Buffer Overflow Stack Frame for main Return Address Saved %ebp /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } /* Way too small! */ [3] [2] [1] [0] buf Stack Frame for echo – 15 – echo: pushl movl pushl leal subl movl call. . . %ebp %esp, %ebp %ebx -8(%ebp), %ebx $20, %esp %ebx, (%esp) gets # Save %ebp on stack # # # Save %ebx Compute buf as %ebp-8 Allocate stack space Push buf on stack Call gets 15 -213, F’ 08
![Buffer Overflow Stack Example Stack Frame for main Return Address Saved %ebp [3] [2] Buffer Overflow Stack Example Stack Frame for main Return Address Saved %ebp [3] [2]](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-16.jpg) Buffer Overflow Stack Example Stack Frame for main Return Address Saved %ebp [3] [2] [1] [0] buf Stack Frame for echo – 16 – unix> gdb bufdemo (gdb) break echo Breakpoint 1 at 0 x 8048583 (gdb) run Breakpoint 1, 0 x 8048583 in echo () (gdb) print /x $ebp $1 = 0 xffffc 638 (gdb) print /x *(unsigned *)$ebp $2 = 0 xffffc 658 (gdb) print /x *((unsigned *)$ebp + 1) $3 = 0 x 80485 f 7 %ebp 0 xbfffc 658 Before call to gets 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo 80485 f 2: call 80484 f 0
Buffer Overflow Stack Example Stack Frame for main Return Address Saved %ebp [3] [2] [1] [0] buf Stack Frame for echo – 16 – unix> gdb bufdemo (gdb) break echo Breakpoint 1 at 0 x 8048583 (gdb) run Breakpoint 1, 0 x 8048583 in echo () (gdb) print /x $ebp $1 = 0 xffffc 638 (gdb) print /x *(unsigned *)$ebp $2 = 0 xffffc 658 (gdb) print /x *((unsigned *)$ebp + 1) $3 = 0 x 80485 f 7 %ebp 0 xbfffc 658 Before call to gets 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo 80485 f 2: call 80484 f 0
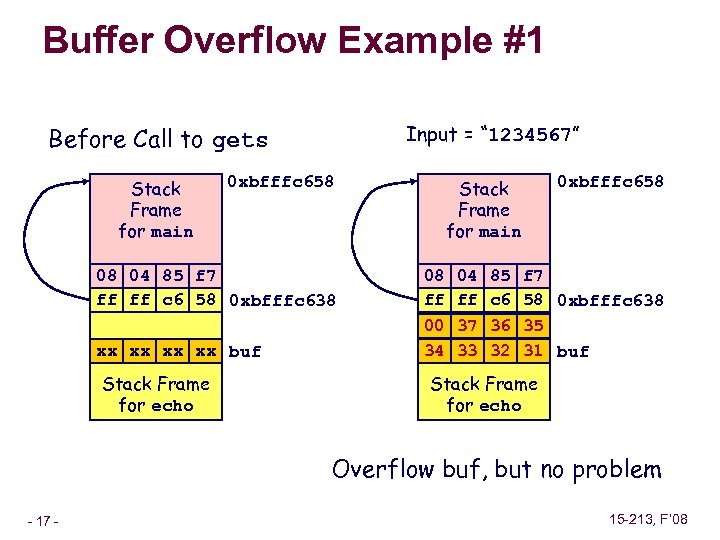 Buffer Overflow Example #1 Input = “ 1234567” Before Call to gets Stack Frame for main 0 xbfffc 658 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo Stack Frame for main 0 xbfffc 658 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp 00 37 36 35 34 33 32 31 buf Stack Frame for echo Overflow buf, but no problem – 17 – 15 -213, F’ 08
Buffer Overflow Example #1 Input = “ 1234567” Before Call to gets Stack Frame for main 0 xbfffc 658 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo Stack Frame for main 0 xbfffc 658 08 04 85 f 7 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp 00 37 36 35 34 33 32 31 buf Stack Frame for echo Overflow buf, but no problem – 17 – 15 -213, F’ 08
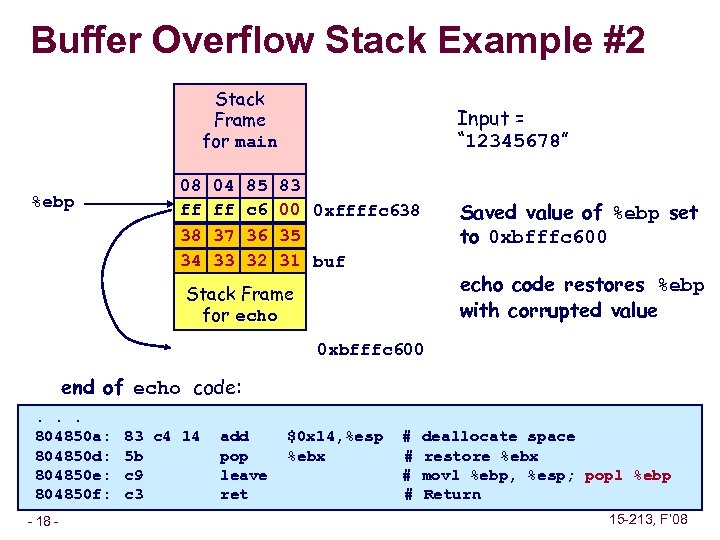 Buffer Overflow Stack Example #2 Stack Frame for main %ebp Input = “ 12345678” 08 04 85 83 Return Address Saved %ebp ff ff c 6 00 0 xffffc 638 38 37 36 35 34 33 32 31 buf Saved value of %ebp set to 0 xbfffc 600 echo code restores %ebp with corrupted value Stack Frame for echo 0 xbfffc 600 end of echo code: . . . 804850 a: 804850 d: 804850 e: 804850 f: – 18 – 83 c 4 14 5 b c 9 c 3 add pop leave ret $0 x 14, %esp %ebx # # deallocate space restore %ebx movl %ebp, %esp; popl %ebp Return 15 -213, F’ 08
Buffer Overflow Stack Example #2 Stack Frame for main %ebp Input = “ 12345678” 08 04 85 83 Return Address Saved %ebp ff ff c 6 00 0 xffffc 638 38 37 36 35 34 33 32 31 buf Saved value of %ebp set to 0 xbfffc 600 echo code restores %ebp with corrupted value Stack Frame for echo 0 xbfffc 600 end of echo code: . . . 804850 a: 804850 d: 804850 e: 804850 f: – 18 – 83 c 4 14 5 b c 9 c 3 add pop leave ret $0 x 14, %esp %ebx # # deallocate space restore %ebx movl %ebp, %esp; popl %ebp Return 15 -213, F’ 08
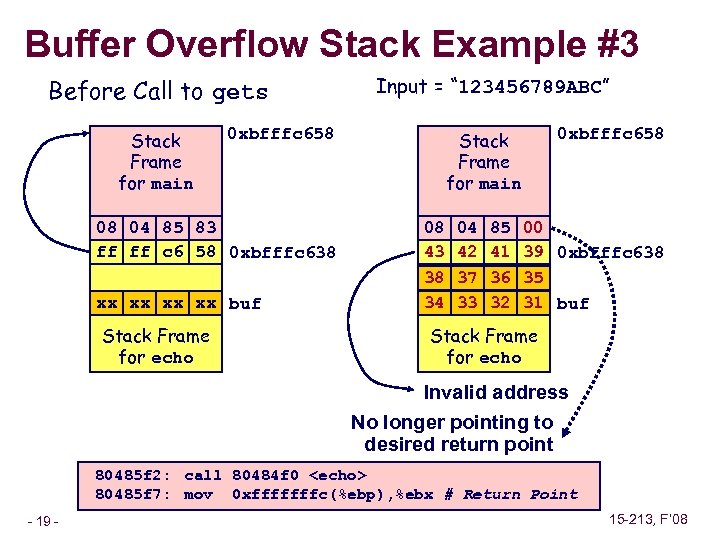 Buffer Overflow Stack Example #3 Before Call to gets Stack Frame for main 0 xbfffc 658 08 04 85 83 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo Input = “ 123456789 ABC” Stack Frame for main 0 xbfffc 658 08 04 85 00 Return Address 43 42 41 39 0 xbfffc 638 Saved %ebp 38 37 36 35 34 33 32 31 buf Stack Frame for echo Invalid address No longer pointing to desired return point 80485 f 2: call 80484 f 0
Buffer Overflow Stack Example #3 Before Call to gets Stack Frame for main 0 xbfffc 658 08 04 85 83 Return Address ff ff c 6 58 0 xbfffc 638 Saved %ebp xx xx buf Stack Frame for echo Input = “ 123456789 ABC” Stack Frame for main 0 xbfffc 658 08 04 85 00 Return Address 43 42 41 39 0 xbfffc 638 Saved %ebp 38 37 36 35 34 33 32 31 buf Stack Frame for echo Invalid address No longer pointing to desired return point 80485 f 2: call 80484 f 0
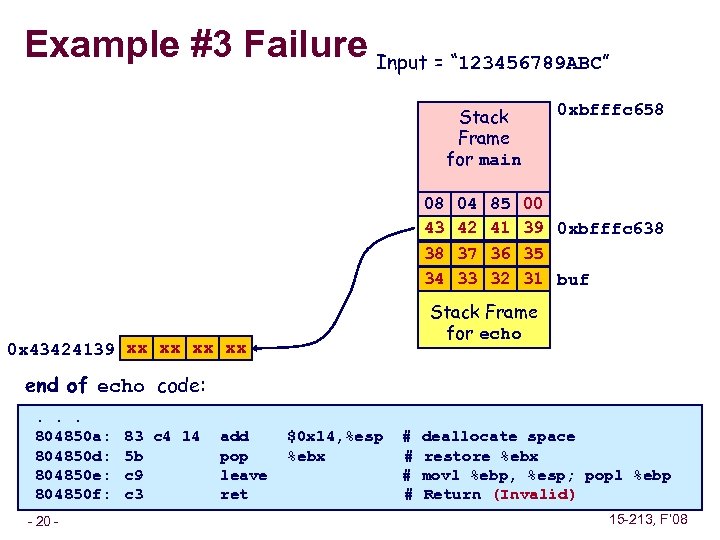 Example #3 Failure Input = “ 123456789 ABC” Stack Frame for main 0 xbfffc 658 08 04 85 00 Return Address 43 42 41 39 0 xbfffc 638 Saved %ebp 38 37 36 35 34 33 32 31 buf Stack Frame for echo 0 x 43424139 xx xx end of echo code: . . . 804850 a: 804850 d: 804850 e: 804850 f: – 20 – 83 c 4 14 5 b c 9 c 3 add pop leave ret $0 x 14, %esp %ebx # # deallocate space restore %ebx movl %ebp, %esp; popl %ebp Return (Invalid) 15 -213, F’ 08
Example #3 Failure Input = “ 123456789 ABC” Stack Frame for main 0 xbfffc 658 08 04 85 00 Return Address 43 42 41 39 0 xbfffc 638 Saved %ebp 38 37 36 35 34 33 32 31 buf Stack Frame for echo 0 x 43424139 xx xx end of echo code: . . . 804850 a: 804850 d: 804850 e: 804850 f: – 20 – 83 c 4 14 5 b c 9 c 3 add pop leave ret $0 x 14, %esp %ebx # # deallocate space restore %ebx movl %ebp, %esp; popl %ebp Return (Invalid) 15 -213, F’ 08
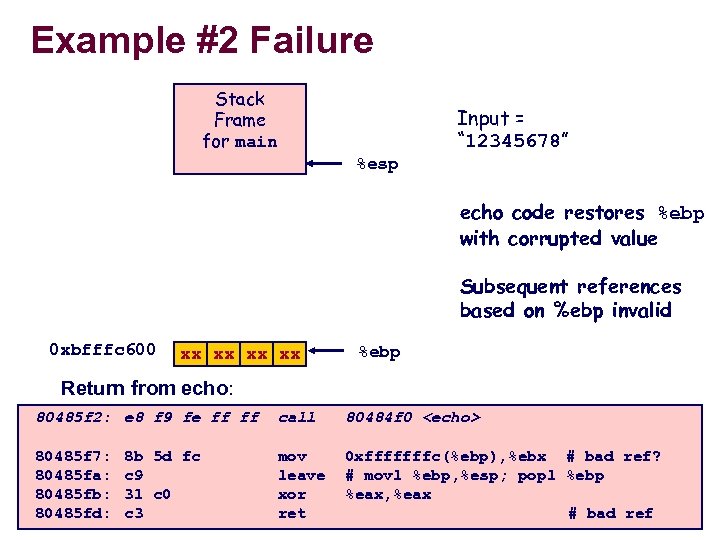 Example #2 Failure Stack Frame for main Input = “ 12345678” %esp echo code restores %ebp with corrupted value Subsequent references based on %ebp invalid 0 xbfffc 600 xx xx %ebp Return from echo: 80485 f 2: e 8 f 9 fe ff ff 80485 f 7: 80485 fa: 80485 fb: 80485 fd: – 21 – 8 b 5 d fc c 9 31 c 0 c 3 call 80484 f 0
Example #2 Failure Stack Frame for main Input = “ 12345678” %esp echo code restores %ebp with corrupted value Subsequent references based on %ebp invalid 0 xbfffc 600 xx xx %ebp Return from echo: 80485 f 2: e 8 f 9 fe ff ff 80485 f 7: 80485 fa: 80485 fb: 80485 fd: – 21 – 8 b 5 d fc c 9 31 c 0 c 3 call 80484 f 0
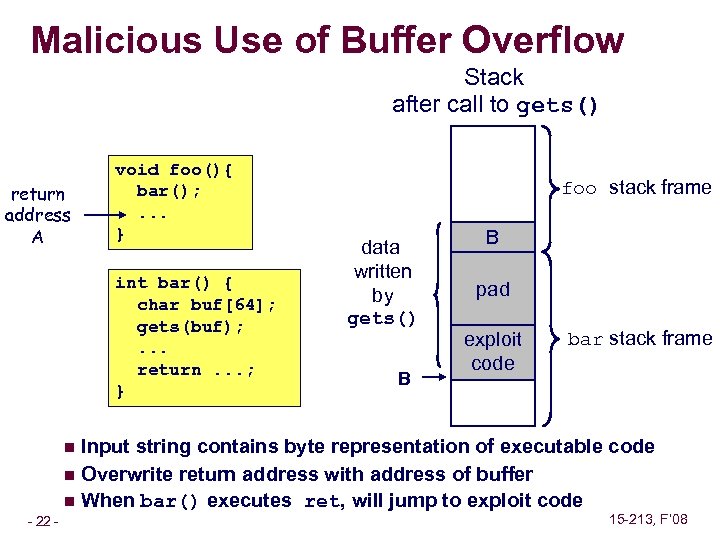 Malicious Use of Buffer Overflow Stack after call to gets() return address A void foo(){ bar(); . . . } int bar() { char buf[64]; gets(buf); . . . return. . . ; } foo stack frame data written by gets() B B pad exploit code bar stack frame Input string contains byte representation of executable code n Overwrite return address with address of buffer n When bar() executes ret, will jump to exploit code n – 22 – 15 -213, F’ 08
Malicious Use of Buffer Overflow Stack after call to gets() return address A void foo(){ bar(); . . . } int bar() { char buf[64]; gets(buf); . . . return. . . ; } foo stack frame data written by gets() B B pad exploit code bar stack frame Input string contains byte representation of executable code n Overwrite return address with address of buffer n When bar() executes ret, will jump to exploit code n – 22 – 15 -213, F’ 08
 Exploits Based on Buffer Overflows Buffer overflow bugs allow remote machines to execute arbitrary code on victim machines. Internet worm n Early versions of the finger server (fingerd) used gets() to read the argument sent by the client: l finger droh@cs. cmu. edu n Worm attacked fingerd server by sending phony argument: l finger “exploit-code padding new-return-address” l exploit code: executed a root shell on the victim machine with a direct TCP connection to the attacker. – 23 – 15 -213, F’ 08
Exploits Based on Buffer Overflows Buffer overflow bugs allow remote machines to execute arbitrary code on victim machines. Internet worm n Early versions of the finger server (fingerd) used gets() to read the argument sent by the client: l finger droh@cs. cmu. edu n Worm attacked fingerd server by sending phony argument: l finger “exploit-code padding new-return-address” l exploit code: executed a root shell on the victim machine with a direct TCP connection to the attacker. – 23 – 15 -213, F’ 08
 Exploits Based on Buffer Overflows Buffer overflow bugs allow remote machines to execute arbitrary code on victim machines. IM War AOL exploited existing buffer overflow bug in AIM clients n exploit code: returned 4 -byte signature (the bytes at some location in the AIM client) to server. n When Microsoft changed code to match signature, AOL changed signature location. n – 24 – 15 -213, F’ 08
Exploits Based on Buffer Overflows Buffer overflow bugs allow remote machines to execute arbitrary code on victim machines. IM War AOL exploited existing buffer overflow bug in AIM clients n exploit code: returned 4 -byte signature (the bytes at some location in the AIM client) to server. n When Microsoft changed code to match signature, AOL changed signature location. n – 24 – 15 -213, F’ 08
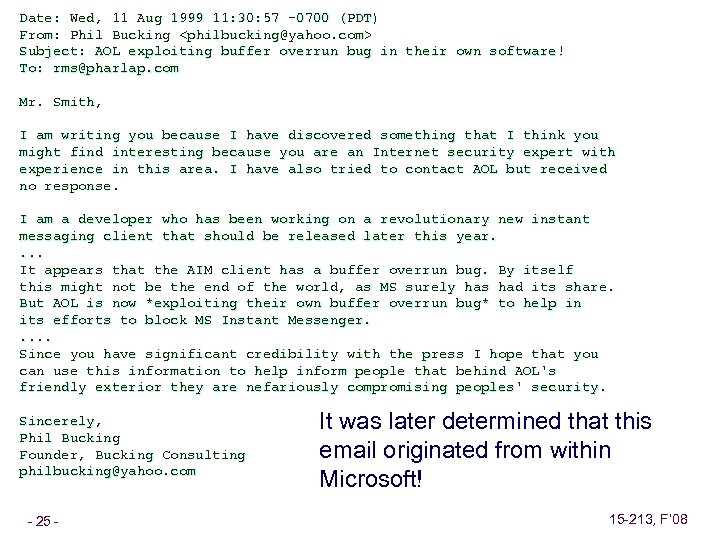 Date: Wed, 11 Aug 1999 11: 30: 57 -0700 (PDT) From: Phil Bucking
Date: Wed, 11 Aug 1999 11: 30: 57 -0700 (PDT) From: Phil Bucking
![Avoiding Overflow Vulnerability /* Echo Line */ void echo() { char buf[4]; /* Way Avoiding Overflow Vulnerability /* Echo Line */ void echo() { char buf[4]; /* Way](https://present5.com/presentation/6152a629074fa764d6605571e7cf5f8e/image-26.jpg) Avoiding Overflow Vulnerability /* Echo Line */ void echo() { char buf[4]; /* Way too small! */ fgets(buf, 4, stdin); puts(buf); } Use Library Routines that Limit String Lengths n fgets instead of gets n strncpy instead of strcpy n Don’t use scanf with %s conversion specification l Use fgets to read the string l Or use %ns where n is a suitable integer – 29 – 15 -213, F’ 08
Avoiding Overflow Vulnerability /* Echo Line */ void echo() { char buf[4]; /* Way too small! */ fgets(buf, 4, stdin); puts(buf); } Use Library Routines that Limit String Lengths n fgets instead of gets n strncpy instead of strcpy n Don’t use scanf with %s conversion specification l Use fgets to read the string l Or use %ns where n is a suitable integer – 29 – 15 -213, F’ 08
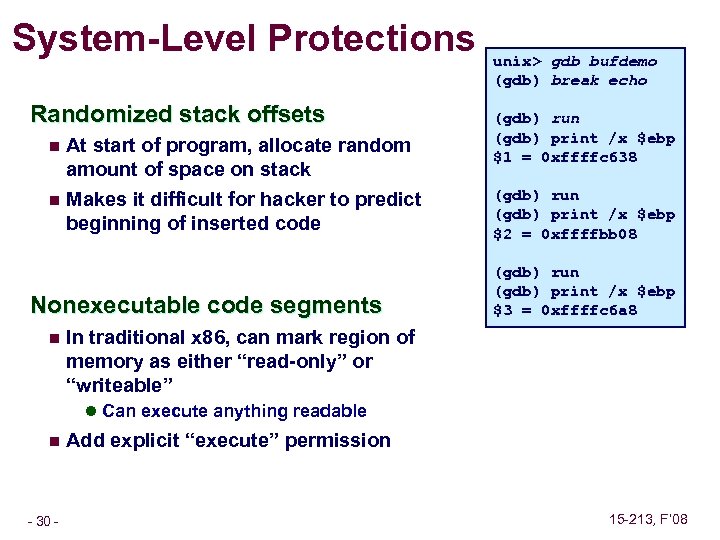 System-Level Protections Randomized stack offsets At start of program, allocate random amount of space on stack n Makes it difficult for hacker to predict beginning of inserted code n Nonexecutable code segments n unix> gdb bufdemo (gdb) break echo (gdb) run (gdb) print /x $ebp $1 = 0 xffffc 638 (gdb) run (gdb) print /x $ebp $2 = 0 xffffbb 08 (gdb) run (gdb) print /x $ebp $3 = 0 xffffc 6 a 8 In traditional x 86, can mark region of memory as either “read-only” or “writeable” l Can execute anything readable n – 30 – Add explicit “execute” permission 15 -213, F’ 08
System-Level Protections Randomized stack offsets At start of program, allocate random amount of space on stack n Makes it difficult for hacker to predict beginning of inserted code n Nonexecutable code segments n unix> gdb bufdemo (gdb) break echo (gdb) run (gdb) print /x $ebp $1 = 0 xffffc 638 (gdb) run (gdb) print /x $ebp $2 = 0 xffffbb 08 (gdb) run (gdb) print /x $ebp $3 = 0 xffffc 6 a 8 In traditional x 86, can mark region of memory as either “read-only” or “writeable” l Can execute anything readable n – 30 – Add explicit “execute” permission 15 -213, F’ 08
 IA 32 Floating Point History n Instruction decoder and sequencer 8086: first computer to implement IEEE FP l separate 8087 FPU (floating point unit) n 486: merged FPU and Integer Unit onto one chip Summary Hardware to add, multiply, and divide n Floating point data registers n Various control & status registers n Integer Unit FPU Floating Point Formats single precision (C float): 32 bits n double precision (C double): 64 bits n extended precision (C long double): 80 bits n – 31 – Memory 15 -213, F’ 08
IA 32 Floating Point History n Instruction decoder and sequencer 8086: first computer to implement IEEE FP l separate 8087 FPU (floating point unit) n 486: merged FPU and Integer Unit onto one chip Summary Hardware to add, multiply, and divide n Floating point data registers n Various control & status registers n Integer Unit FPU Floating Point Formats single precision (C float): 32 bits n double precision (C double): 64 bits n extended precision (C long double): 80 bits n – 31 – Memory 15 -213, F’ 08
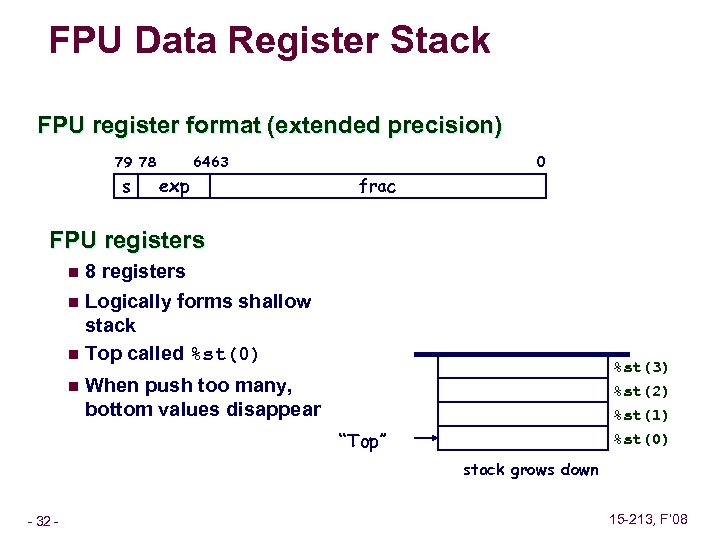 FPU Data Register Stack FPU register format (extended precision) 79 78 s 0 64 63 exp frac FPU registers n 8 registers Logically forms shallow stack n Top called %st(0) n n %st(3) %st(2) When push too many, bottom values disappear %st(1) %st(0) “Top” stack grows down – 32 – 15 -213, F’ 08
FPU Data Register Stack FPU register format (extended precision) 79 78 s 0 64 63 exp frac FPU registers n 8 registers Logically forms shallow stack n Top called %st(0) n n %st(3) %st(2) When push too many, bottom values disappear %st(1) %st(0) “Top” stack grows down – 32 – 15 -213, F’ 08
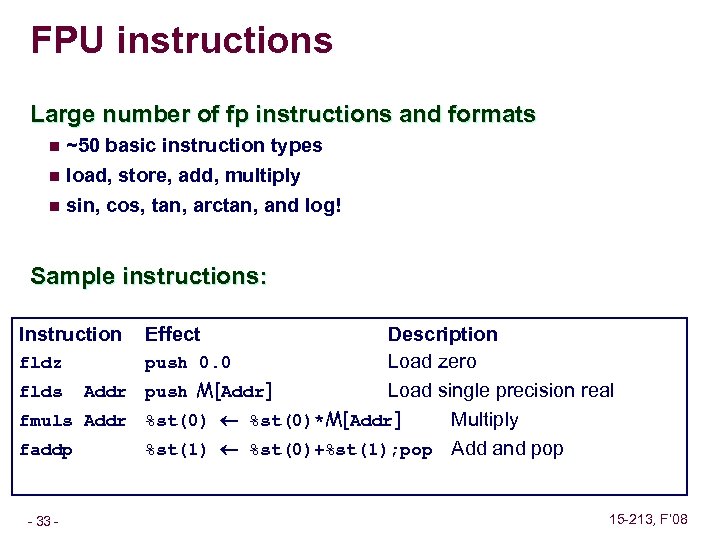 FPU instructions Large number of fp instructions and formats n ~50 basic instruction types load, store, add, multiply n sin, cos, tan, arctan, and log! n Sample instructions: Instruction Description fldz push 0. 0 Load zero flds Addr push M[Addr] Load single precision real fmuls Addr %st(0)*M[Addr] Multiply faddp %st(1) %st(0)+%st(1); pop Add and pop – 33 – Effect 15 -213, F’ 08
FPU instructions Large number of fp instructions and formats n ~50 basic instruction types load, store, add, multiply n sin, cos, tan, arctan, and log! n Sample instructions: Instruction Description fldz push 0. 0 Load zero flds Addr push M[Addr] Load single precision real fmuls Addr %st(0)*M[Addr] Multiply faddp %st(1) %st(0)+%st(1); pop Add and pop – 33 – Effect 15 -213, F’ 08
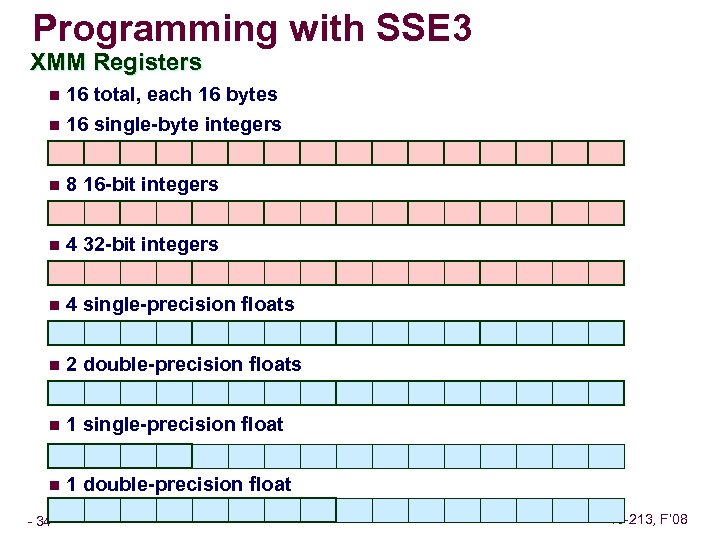 Programming with SSE 3 XMM Registers n 16 total, each 16 bytes n 16 single-byte integers n 8 16 -bit integers n 4 32 -bit integers n 4 single-precision floats n 2 double-precision floats n 1 single-precision float n 1 double-precision float – 34 – 15 -213, F’ 08
Programming with SSE 3 XMM Registers n 16 total, each 16 bytes n 16 single-byte integers n 8 16 -bit integers n 4 32 -bit integers n 4 single-precision floats n 2 double-precision floats n 1 single-precision float n 1 double-precision float – 34 – 15 -213, F’ 08
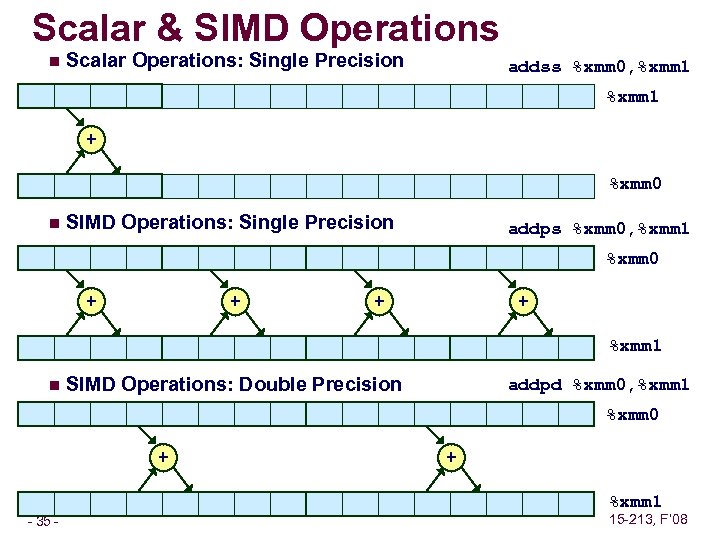 Scalar & SIMD Operations n Scalar Operations: Single Precision addss %xmm 0, %xmm 1 + %xmm 0 n SIMD Operations: Single Precision addps %xmm 0, %xmm 1 %xmm 0 + + %xmm 1 n SIMD Operations: Double Precision addpd %xmm 0, %xmm 1 %xmm 0 + + %xmm 1 – 35 – 15 -213, F’ 08
Scalar & SIMD Operations n Scalar Operations: Single Precision addss %xmm 0, %xmm 1 + %xmm 0 n SIMD Operations: Single Precision addps %xmm 0, %xmm 1 %xmm 0 + + %xmm 1 n SIMD Operations: Double Precision addpd %xmm 0, %xmm 1 %xmm 0 + + %xmm 1 – 35 – 15 -213, F’ 08
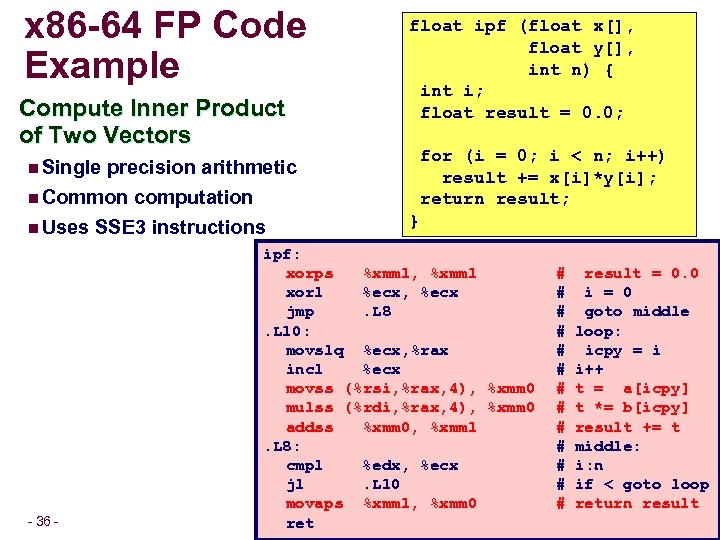 x 86 -64 FP Code Example Compute Inner Product of Two Vectors precision arithmetic n Common computation n Uses SSE 3 instructions float ipf (float x[], float y[], int n) { int i; float result = 0. 0; for (i = 0; i < n; i++) result += x[i]*y[i]; return result; n Single – 36 – } ipf: xorps %xmm 1, %xmm 1 xorl %ecx, %ecx jmp. L 8. L 10: movslq %ecx, %rax incl %ecx movss (%rsi, %rax, 4), %xmm 0 mulss (%rdi, %rax, 4), %xmm 0 addss %xmm 0, %xmm 1. L 8: cmpl %edx, %ecx jl. L 10 movaps %xmm 1, %xmm 0 ret # # # # result = 0. 0 i = 0 goto middle loop: icpy = i i++ t = a[icpy] t *= b[icpy] result += t middle: i: n if < goto loop return result 15 -213, F’ 08
x 86 -64 FP Code Example Compute Inner Product of Two Vectors precision arithmetic n Common computation n Uses SSE 3 instructions float ipf (float x[], float y[], int n) { int i; float result = 0. 0; for (i = 0; i < n; i++) result += x[i]*y[i]; return result; n Single – 36 – } ipf: xorps %xmm 1, %xmm 1 xorl %ecx, %ecx jmp. L 8. L 10: movslq %ecx, %rax incl %ecx movss (%rsi, %rax, 4), %xmm 0 mulss (%rdi, %rax, 4), %xmm 0 addss %xmm 0, %xmm 1. L 8: cmpl %edx, %ecx jl. L 10 movaps %xmm 1, %xmm 0 ret # # # # result = 0. 0 i = 0 goto middle loop: icpy = i i++ t = a[icpy] t *= b[icpy] result += t middle: i: n if < goto loop return result 15 -213, F’ 08
 Final Observations Memory Layout n OS/machine dependent (including kernel version) n Basic partitioning: stack/data/text/heap/shared-libs found in most machines Type Declarations in C n Notation obscure, but very systematic Working with Strange Code n Important to analyze nonstandard cases l E. g. , what happens when stack corrupted due to buffer overflow n Helps to step through with GDB Floating Point IA 32: Strange “shallow stack” architecture n x 86 -64: SSE 3 permits more conventional, register-based approach n – 37 – 15 -213, F’ 08
Final Observations Memory Layout n OS/machine dependent (including kernel version) n Basic partitioning: stack/data/text/heap/shared-libs found in most machines Type Declarations in C n Notation obscure, but very systematic Working with Strange Code n Important to analyze nonstandard cases l E. g. , what happens when stack corrupted due to buffer overflow n Helps to step through with GDB Floating Point IA 32: Strange “shallow stack” architecture n x 86 -64: SSE 3 permits more conventional, register-based approach n – 37 – 15 -213, F’ 08
 Final Observations (Cont. ) Assembly Language n Very different than programming in C Architecture specific (IA-32, X 86 -64, Sparc, PPC, MIPS, ARM, 370, …) n No types, no data structures, no safety, just bits&bytes n Rarely used to program n Needed to access the full capabilities of a machine n Important to understand for debugging and optimization n – 38 – 15 -213, F’ 08
Final Observations (Cont. ) Assembly Language n Very different than programming in C Architecture specific (IA-32, X 86 -64, Sparc, PPC, MIPS, ARM, 370, …) n No types, no data structures, no safety, just bits&bytes n Rarely used to program n Needed to access the full capabilities of a machine n Important to understand for debugging and optimization n – 38 – 15 -213, F’ 08


