cdfdadeeb68ac5c3a14be58b4160ab31.ppt
- Количество слайдов: 65
 11. FSAP and the Model Checking Approach to FT Extraction. An overview of the algorithms for fault tree generation available in FSAP. Algorithms based on model checking techniques. • • In this tutorial: focus on BDD-based routines. SAT-based routines exist as well. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 174
11. FSAP and the Model Checking Approach to FT Extraction. An overview of the algorithms for fault tree generation available in FSAP. Algorithms based on model checking techniques. • • In this tutorial: focus on BDD-based routines. SAT-based routines exist as well. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 174
 Model Checking Automated technique to verify a formal system model against a formal specification. • Systems typically modeled as state transition systems. • Specifications provided as temporal logic formulae. Model checking provides a formal guarantee that a specification is obeyed. (A counterexample trace is produced if the specification does not hold) • Exhaustive technique compared to testing and simulation. Major breakthrough with the introduction of symbolic model checking: • Idea: manipulate sets of states and transitions. • Efficient symbolic representations for the characteristic functions of such sets. In the rest of this chapter: model checking techniques applied to FT generation. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 175
Model Checking Automated technique to verify a formal system model against a formal specification. • Systems typically modeled as state transition systems. • Specifications provided as temporal logic formulae. Model checking provides a formal guarantee that a specification is obeyed. (A counterexample trace is produced if the specification does not hold) • Exhaustive technique compared to testing and simulation. Major breakthrough with the introduction of symbolic model checking: • Idea: manipulate sets of states and transitions. • Efficient symbolic representations for the characteristic functions of such sets. In the rest of this chapter: model checking techniques applied to FT generation. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 175
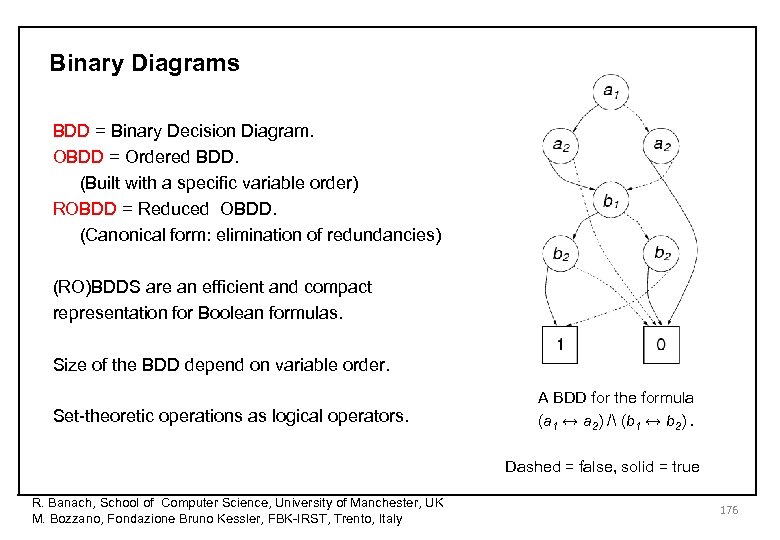 Binary Diagrams BDD = Binary Decision Diagram. OBDD = Ordered BDD. (Built with a specific variable order) ROBDD = Reduced OBDD. (Canonical form: elimination of redundancies) (RO)BDDS are an efficient and compact representation for Boolean formulas. Size of the BDD depend on variable order. Set-theoretic operations as logical operators. A BDD for the formula (a 1 ↔ a 2) / (b 1 ↔ b 2). Dashed = false, solid = true R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 176
Binary Diagrams BDD = Binary Decision Diagram. OBDD = Ordered BDD. (Built with a specific variable order) ROBDD = Reduced OBDD. (Canonical form: elimination of redundancies) (RO)BDDS are an efficient and compact representation for Boolean formulas. Size of the BDD depend on variable order. Set-theoretic operations as logical operators. A BDD for the formula (a 1 ↔ a 2) / (b 1 ↔ b 2). Dashed = false, solid = true R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 176
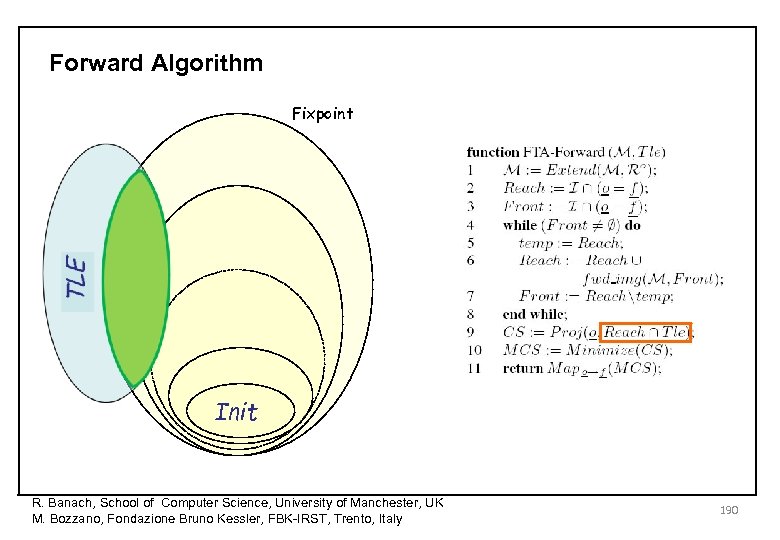
 BDD-based Algorithms for FTA Different algorithms available: • Forward (FWD). • Backward (BWD). Optimizations: • Dynamic cone of influence (DCOI). • Dynamic pruning (PRUN). R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 177
BDD-based Algorithms for FTA Different algorithms available: • Forward (FWD). • Backward (BWD). Optimizations: • Dynamic cone of influence (DCOI). • Dynamic pruning (PRUN). R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 177
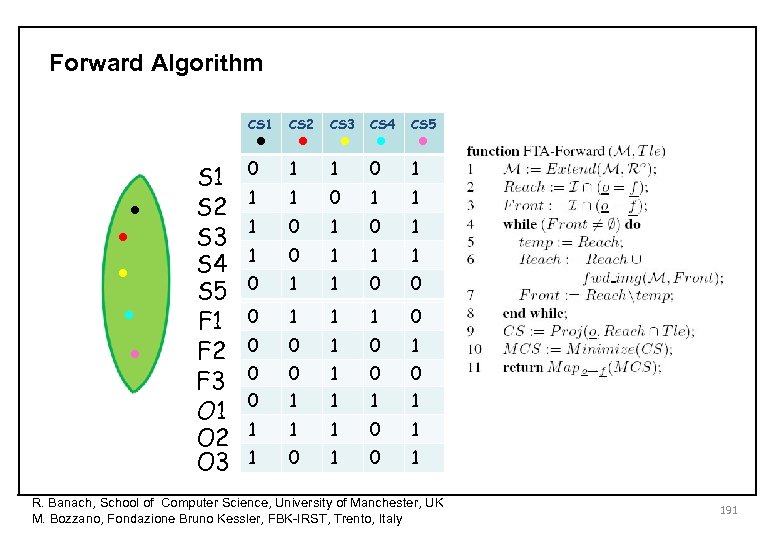
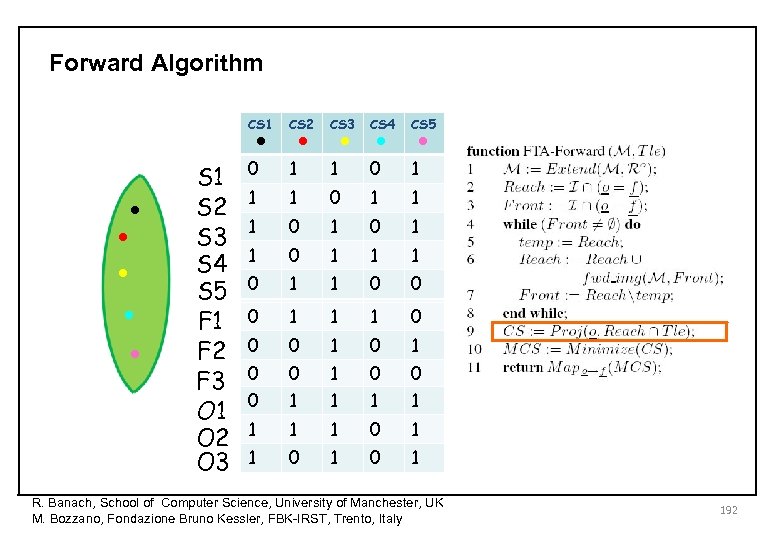
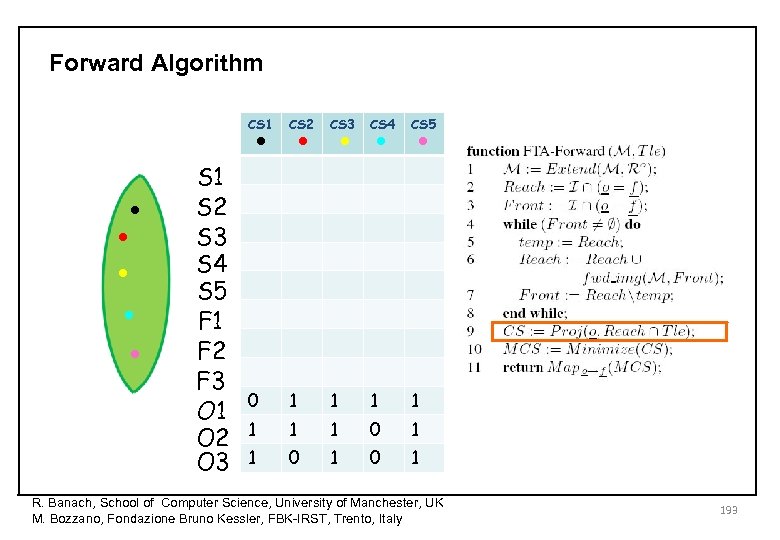
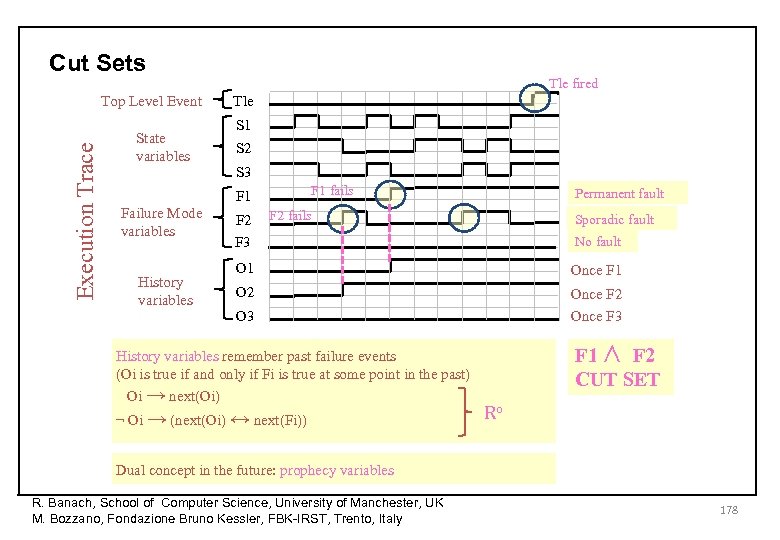 Cut Sets Execution Trace Top Level Event State variables Tle fired Tle S 1 S 2 S 3 F 1 fails F 1 Failure Mode variables History variables F 2 F 3 Permanent fault F 2 fails Sporadic fault No fault O 1 Once F 1 O 2 Once F 3 O 3 F 1 ∧ F 2 CUT SET History variables remember past failure events (Oi is true if and only if Fi is true at some point in the past) Oi → next(Oi) ¬ Oi → (next(Oi) ↔ next(Fi)) Ro Dual concept in the future: prophecy variables R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 178
Cut Sets Execution Trace Top Level Event State variables Tle fired Tle S 1 S 2 S 3 F 1 fails F 1 Failure Mode variables History variables F 2 F 3 Permanent fault F 2 fails Sporadic fault No fault O 1 Once F 1 O 2 Once F 3 O 3 F 1 ∧ F 2 CUT SET History variables remember past failure events (Oi is true if and only if Fi is true at some point in the past) Oi → next(Oi) ¬ Oi → (next(Oi) ↔ next(Fi)) Ro Dual concept in the future: prophecy variables R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 178
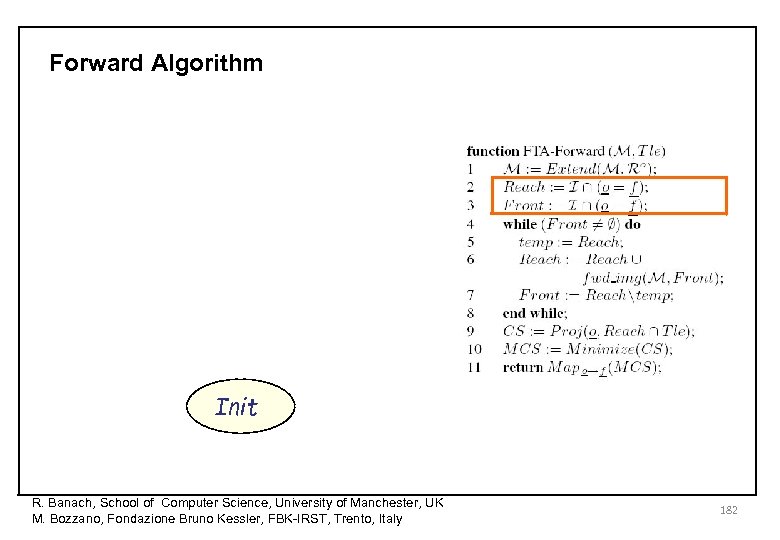
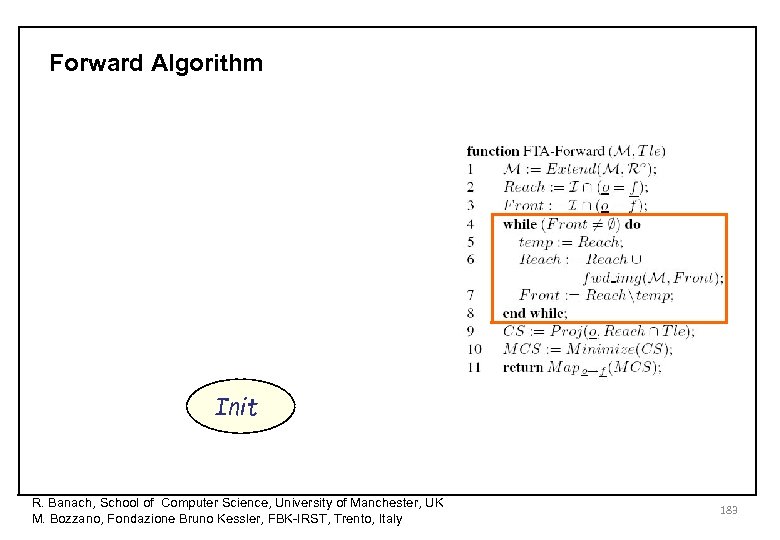
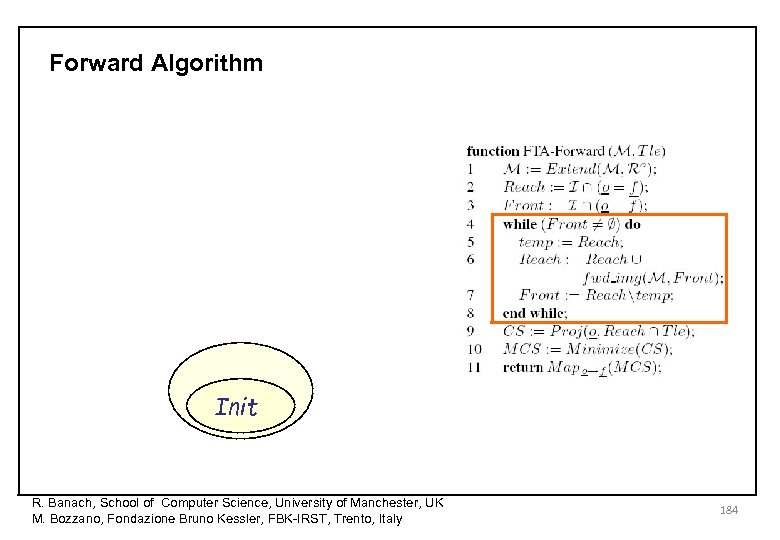
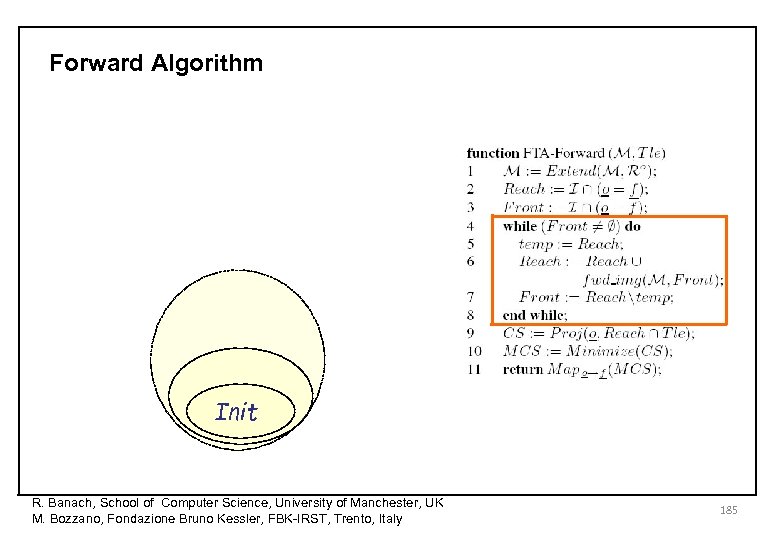
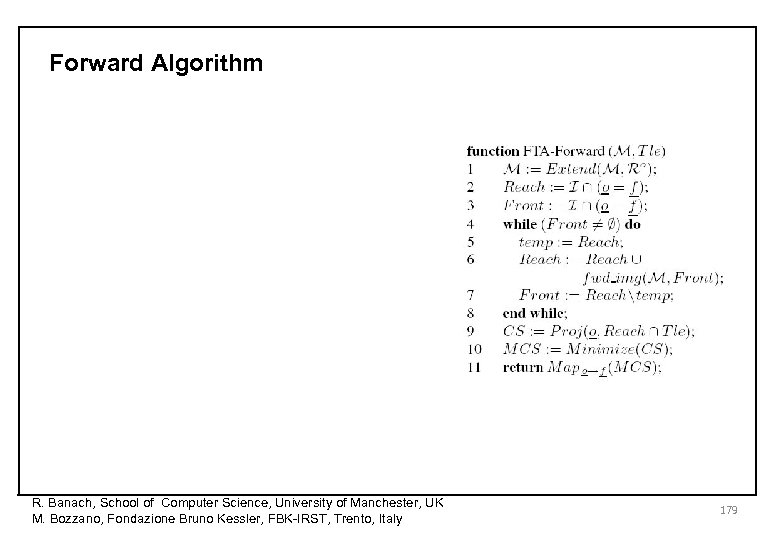 Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 179
Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 179
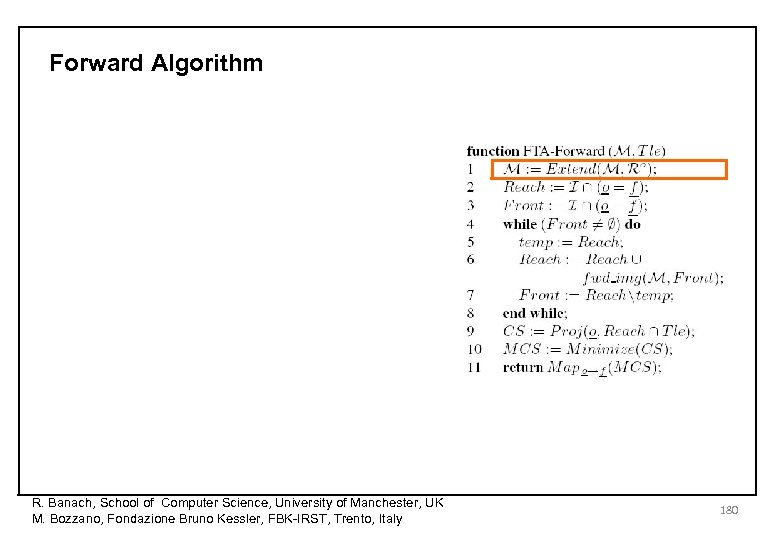 Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 180
Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 180
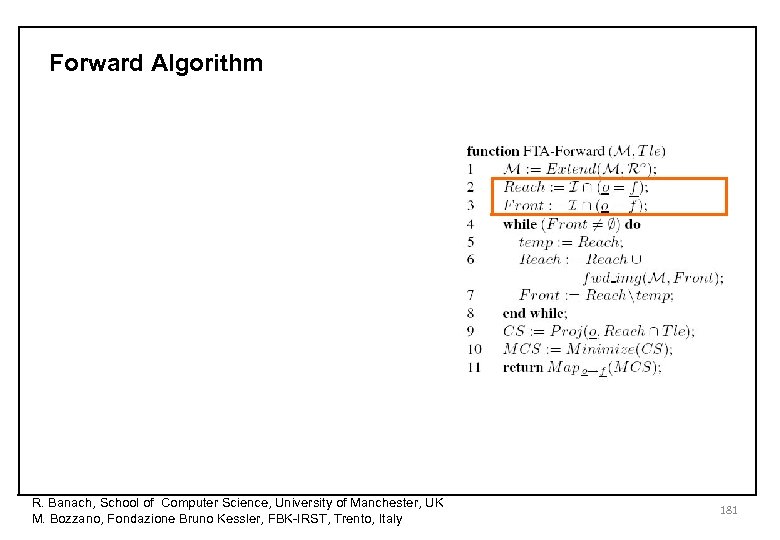 Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 181
Forward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 181
 Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 182
Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 182
 Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 183
Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 183
 Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 184
Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 184
 Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 185
Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 185
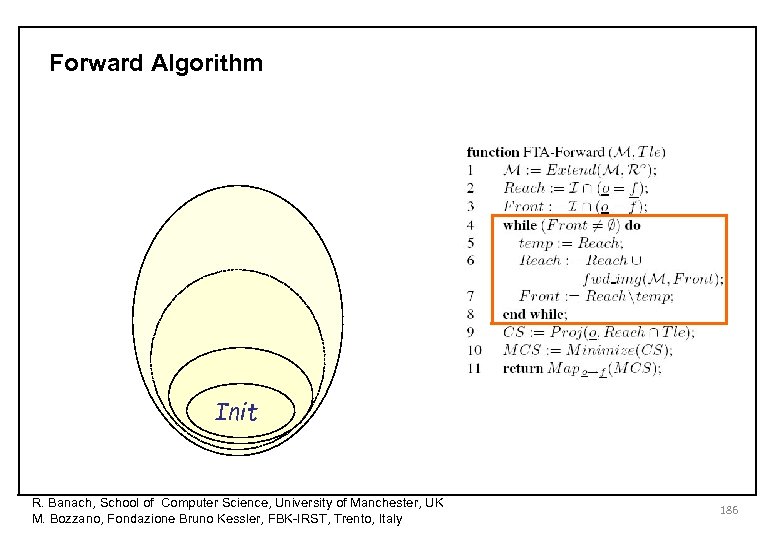 Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 186
Forward Algorithm Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 186
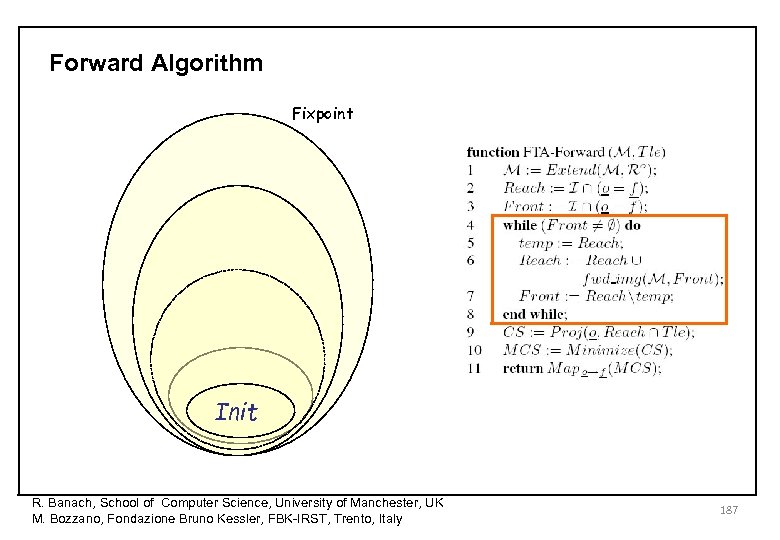 Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 187
Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 187
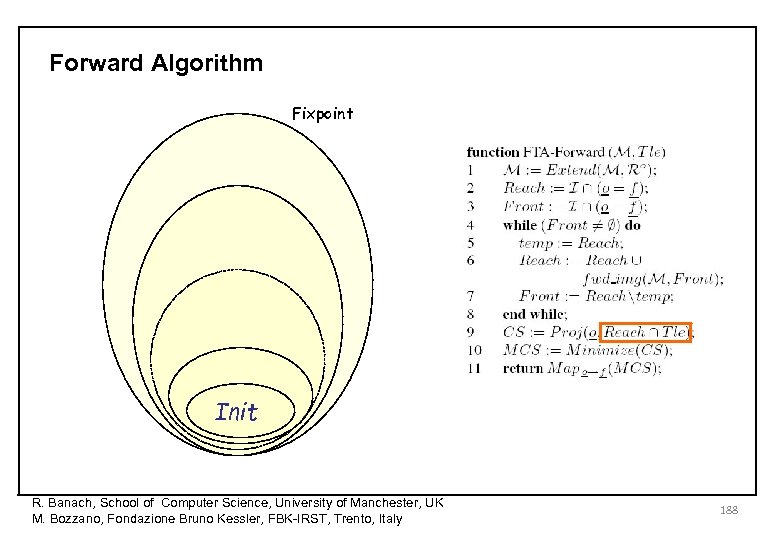 Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 188
Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 188
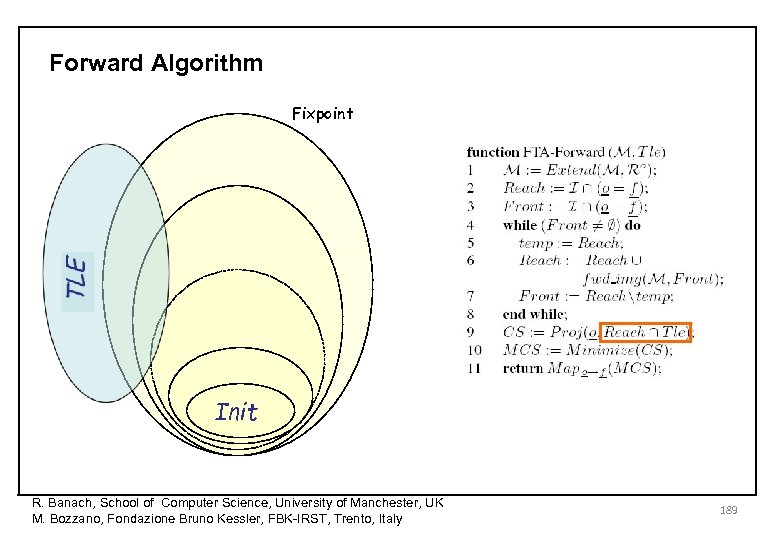 Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 189
Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 189
 Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 190
Forward Algorithm Fixpoint Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 190
 Forward Algorithm • 1 • 0 CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 1 1 0 1 0 1 1 0 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 191
Forward Algorithm • 1 • 0 CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 1 1 0 1 0 1 1 0 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 191
 Forward Algorithm • 1 • 0 CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 1 1 0 1 0 1 1 0 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 192
Forward Algorithm • 1 • 0 CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 1 1 0 1 0 1 1 0 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 192
 Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 0 1 1 1 1 0 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 193
Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 0 1 1 1 1 0 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 193
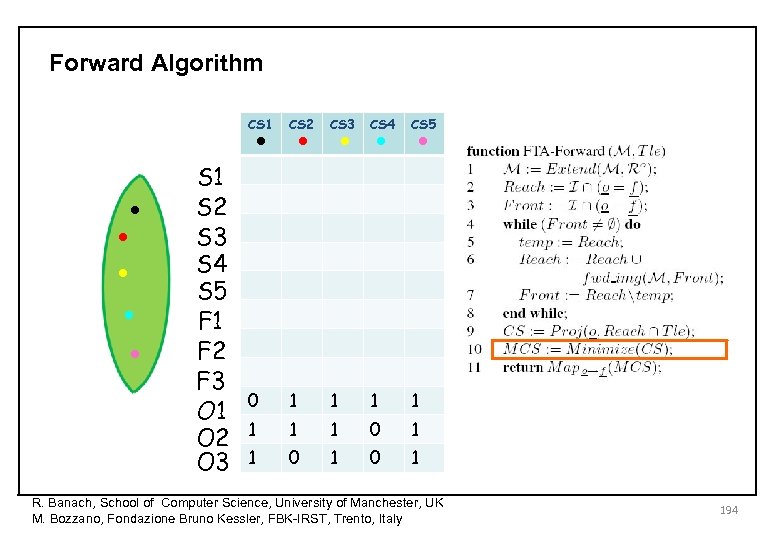 Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 0 1 1 1 1 0 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 194
Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 CS 5 0 1 1 1 1 0 1 0 1 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 194
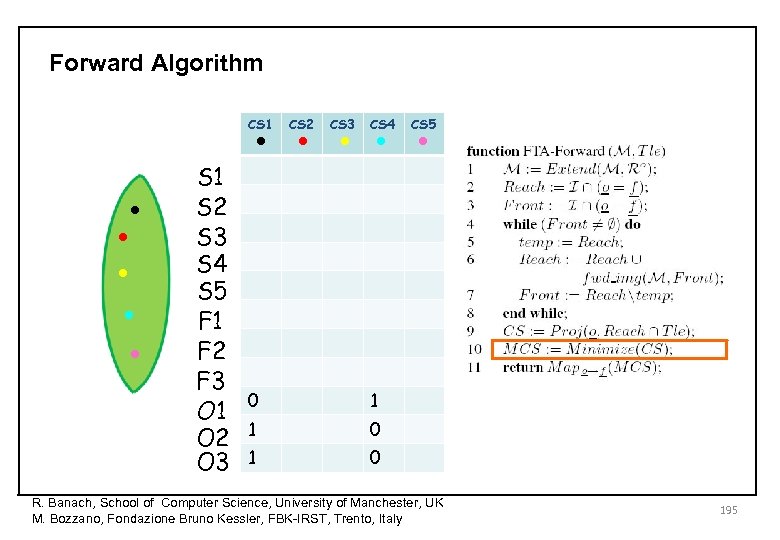 Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 0 1 1 0 1 CS 5 0 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 195
Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 0 1 1 0 1 CS 5 0 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 195
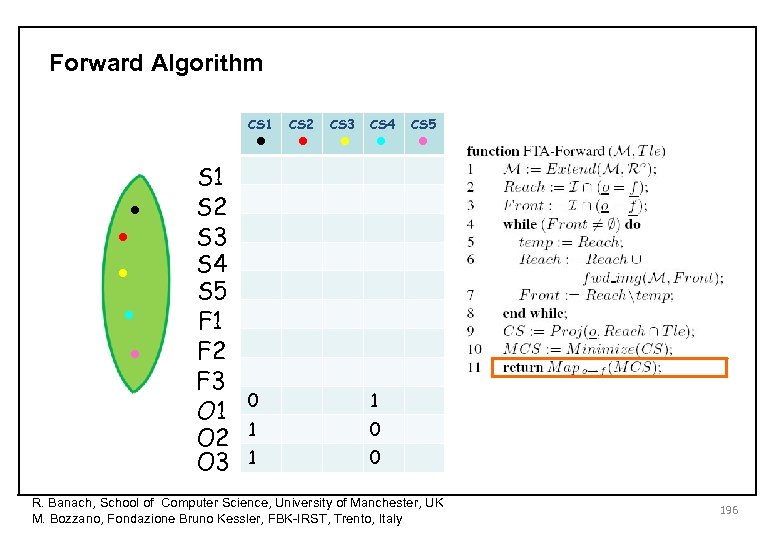 Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 0 1 1 0 1 CS 5 0 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 196
Forward Algorithm • • • CS 1 • • • S 1 S 2 S 3 S 4 S 5 F 1 F 2 F 3 O 1 O 2 O 3 CS 2 CS 3 CS 4 0 1 1 0 1 CS 5 0 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 196
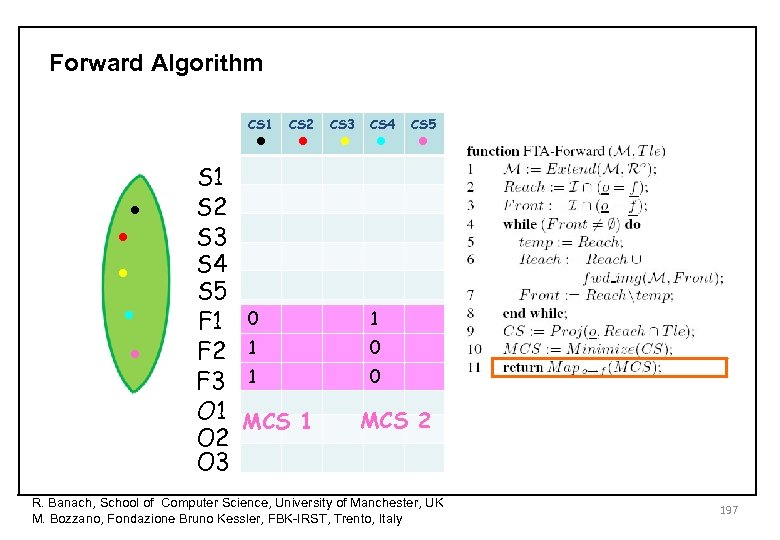 Forward Algorithm • • • CS 1 • • • CS 2 S 1 S 2 S 3 S 4 S 5 F 1 0 F 2 1 F 3 1 O 1 MCS 1 O 2 O 3 CS 4 CS 5 1 0 0 MCS 2 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 197
Forward Algorithm • • • CS 1 • • • CS 2 S 1 S 2 S 3 S 4 S 5 F 1 0 F 2 1 F 3 1 O 1 MCS 1 O 2 O 3 CS 4 CS 5 1 0 0 MCS 2 R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 197
 Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 198
Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 198
 Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 199
Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 199
 Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 200
Backward Algorithm R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 200
 Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 201
Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 201
 Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 202
Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 202
 Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 203
Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 203
 Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 204
Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 204
 Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 205
Backward Algorithm Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 205
 Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 206
Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 206
 Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 207
Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 207
 Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 208
Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 208
 Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 209
Backward Algorithm Tle Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 209
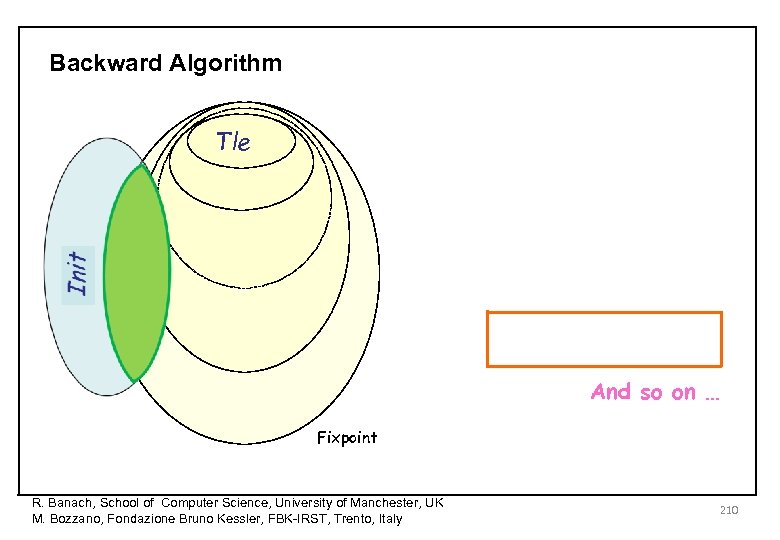 Backward Algorithm Tle And so on … Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 210
Backward Algorithm Tle And so on … Fixpoint R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 210
 Dynamic Cone of Influence Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 211
Dynamic Cone of Influence Tle R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 211
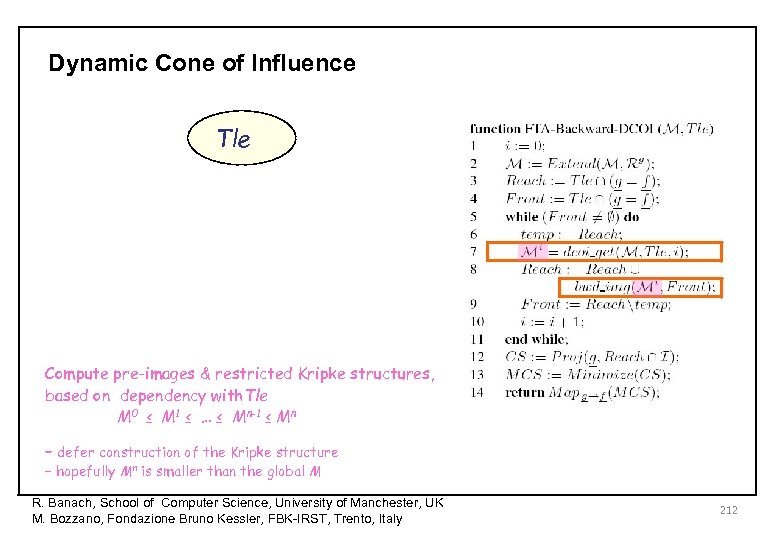 Dynamic Cone of Influence Tle Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 212
Dynamic Cone of Influence Tle Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 212
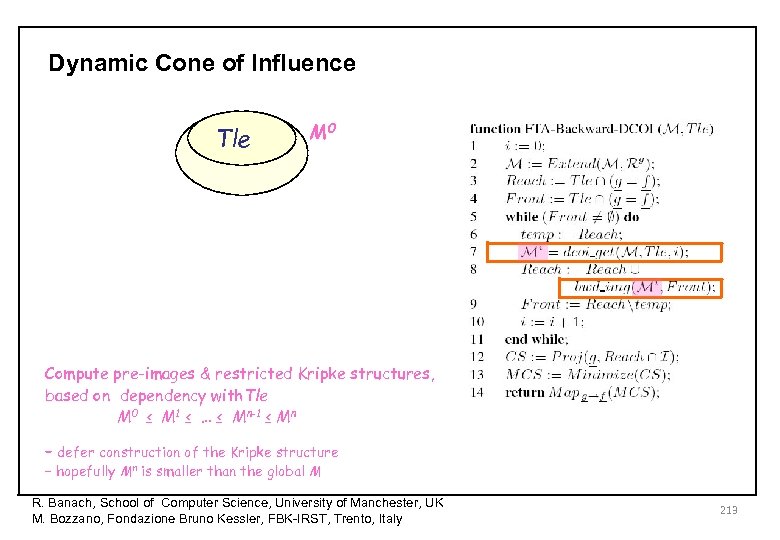 Dynamic Cone of Influence Tle M 0 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 213
Dynamic Cone of Influence Tle M 0 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 213
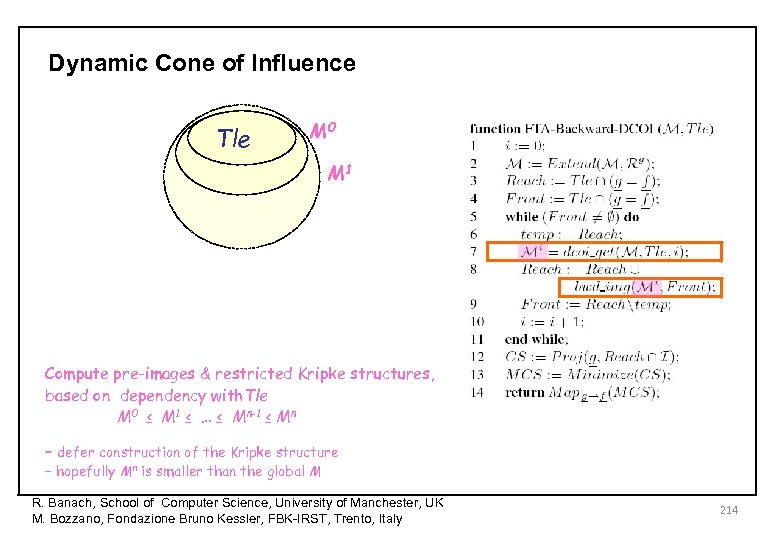 Dynamic Cone of Influence Tle M 0 M 1 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 214
Dynamic Cone of Influence Tle M 0 M 1 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 214
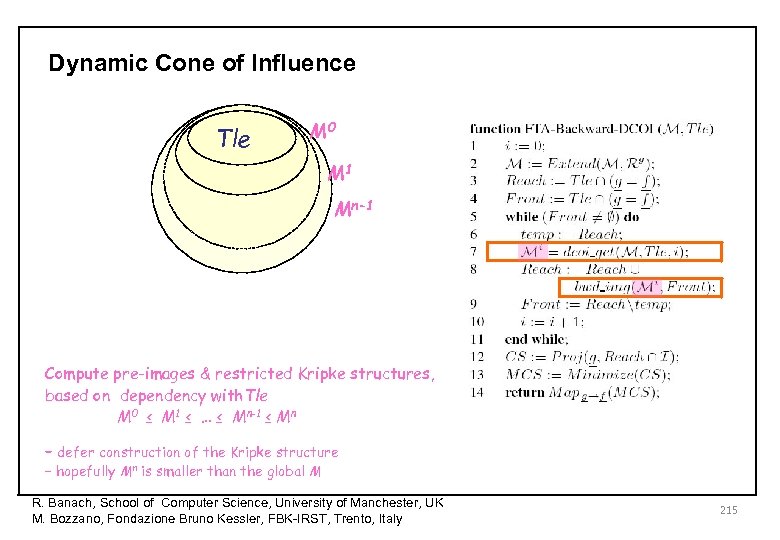 Dynamic Cone of Influence Tle M 0 M 1 Mn-1 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 215
Dynamic Cone of Influence Tle M 0 M 1 Mn-1 Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 215
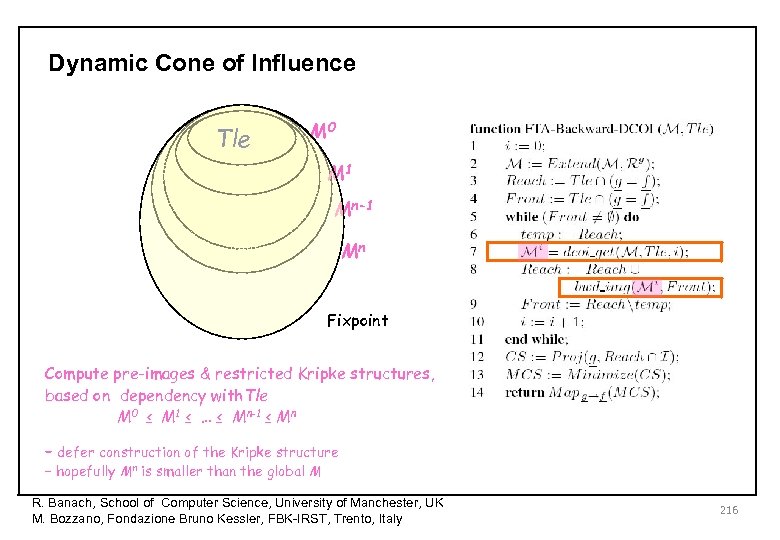 Dynamic Cone of Influence Tle M 0 M 1 Mn-1 Mn Fixpoint Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 216
Dynamic Cone of Influence Tle M 0 M 1 Mn-1 Mn Fixpoint Compute pre-images & restricted Kripke structures, based on dependency with. Tle M 0 ≤ M 1 ≤ … ≤ Mn-1 ≤ Mn – defer construction of the Kripke structure – hopefully Mn is smaller than the global M R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 216
 Dynamic Pruning Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 217
Dynamic Pruning Init R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 217
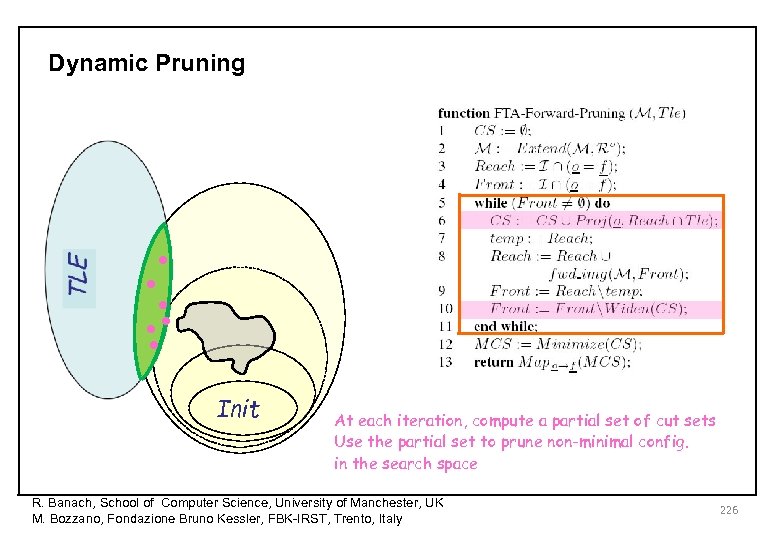
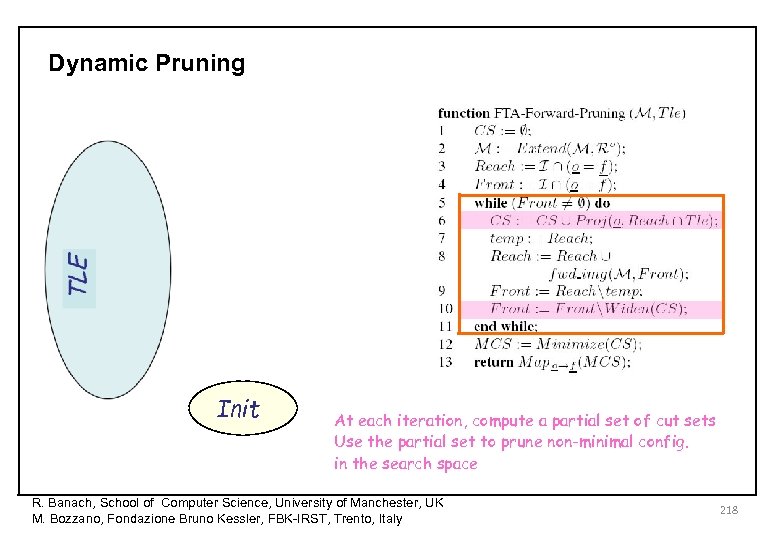 Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 218
Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 218
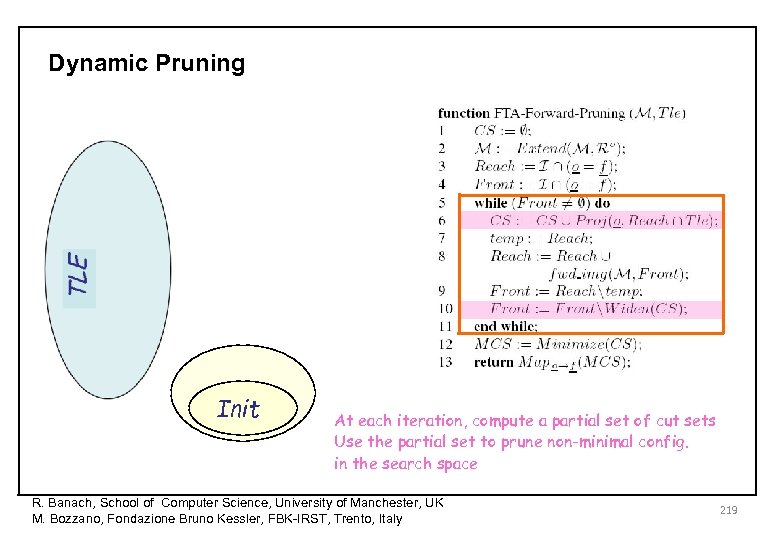 Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 219
Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 219
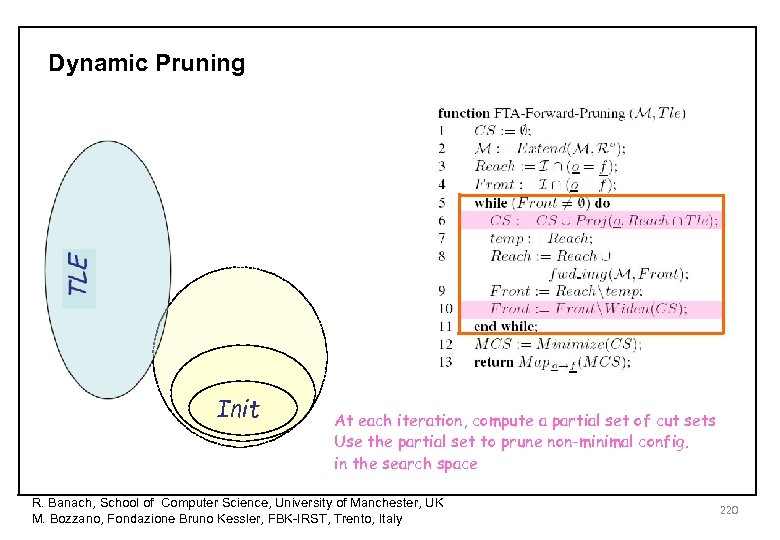 Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 220
Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 220
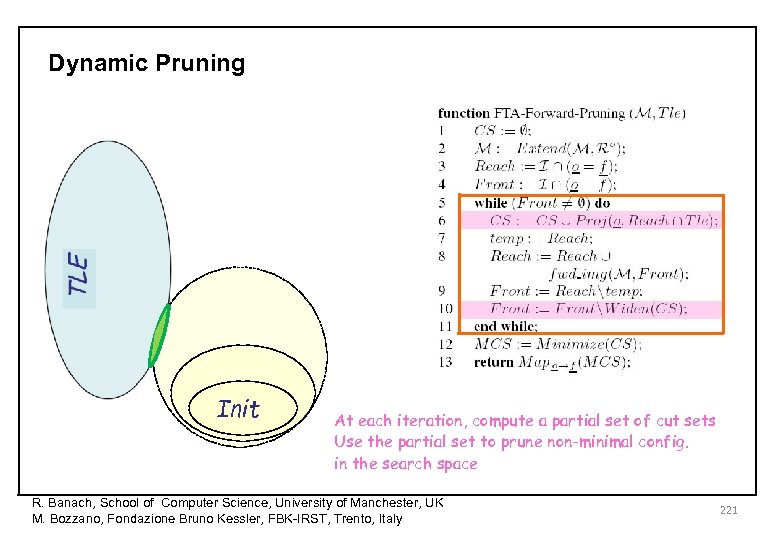 Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 221
Dynamic Pruning Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 221
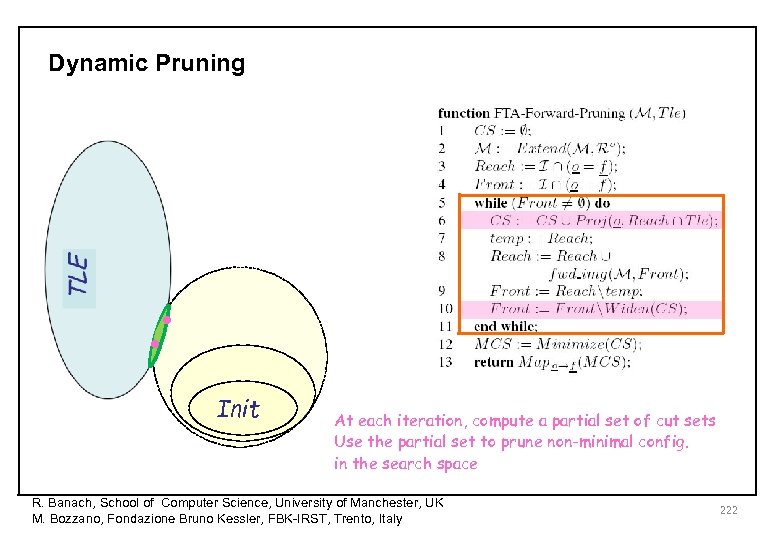 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 222
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 222
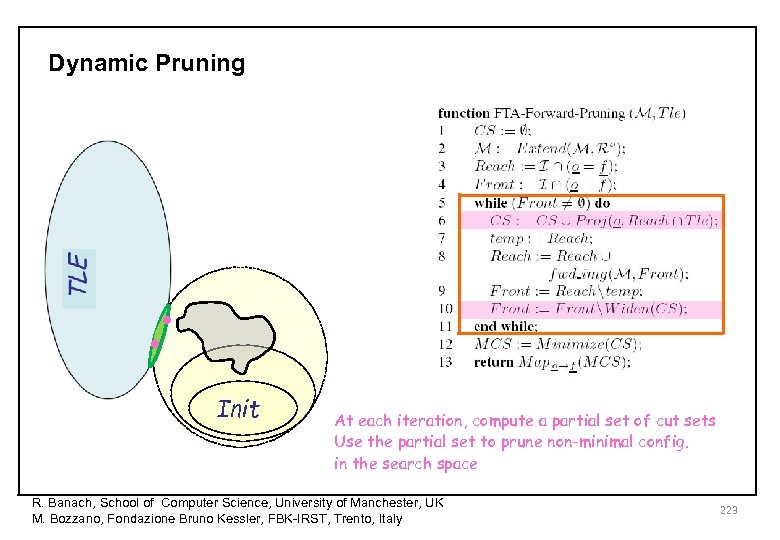 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 223
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 223
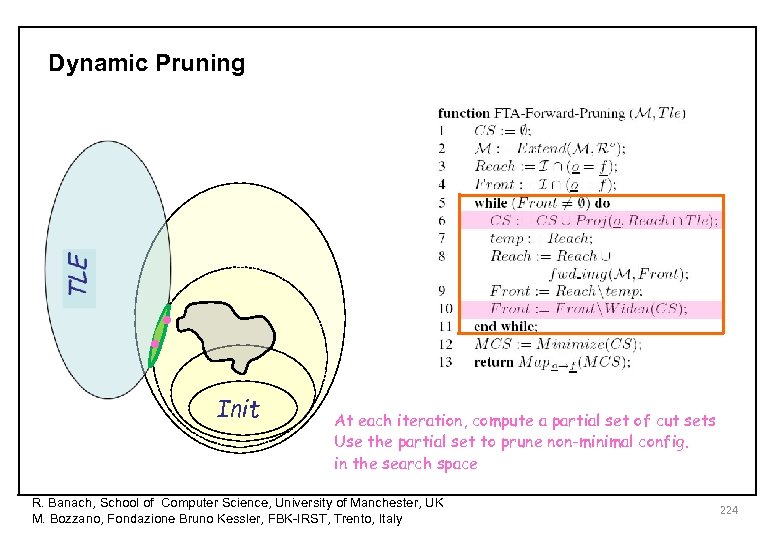 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 224
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 224
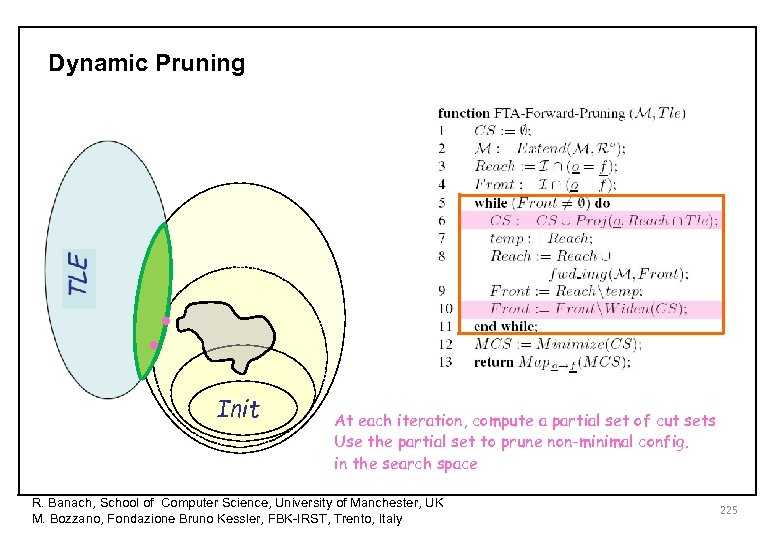 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 225
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 225
 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 226
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 226
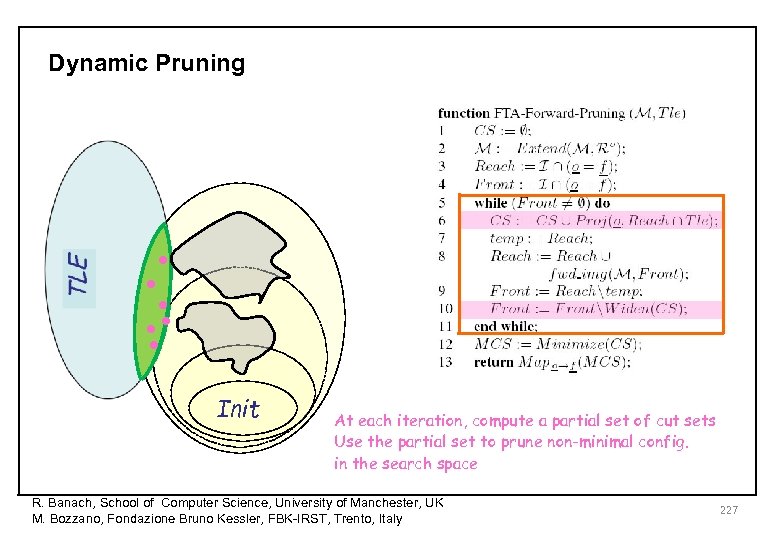 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 227
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 227
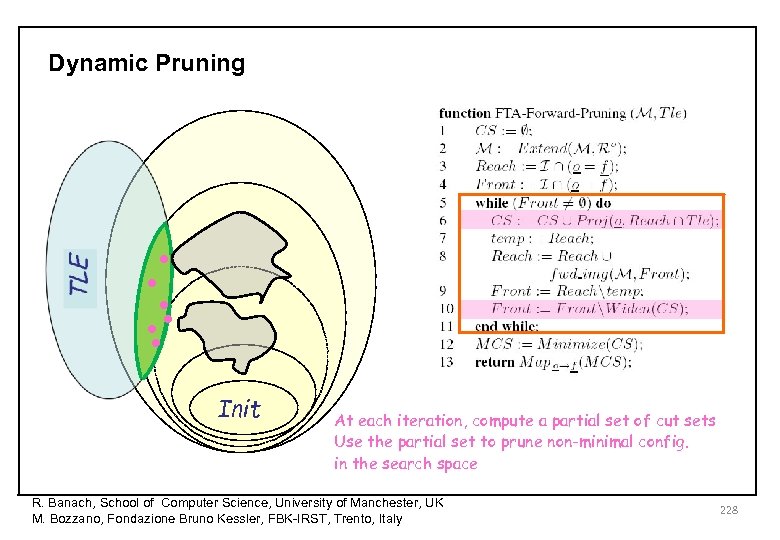 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 228
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 228
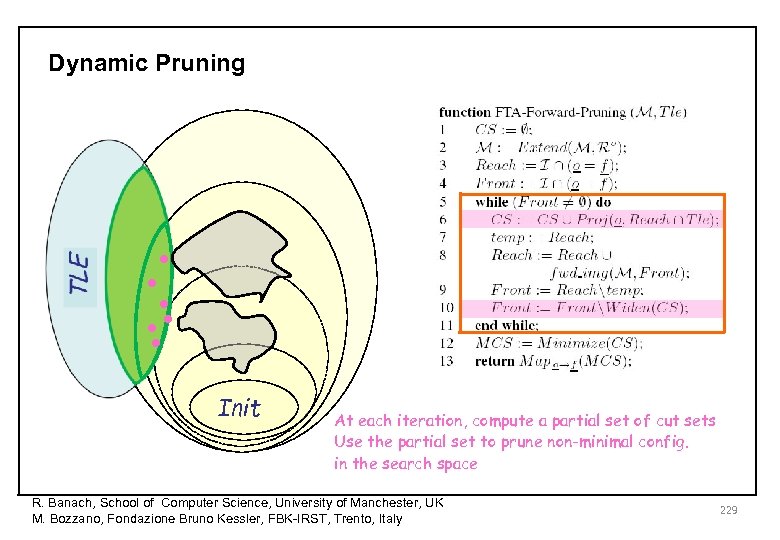 Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 229
Dynamic Pruning • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 229
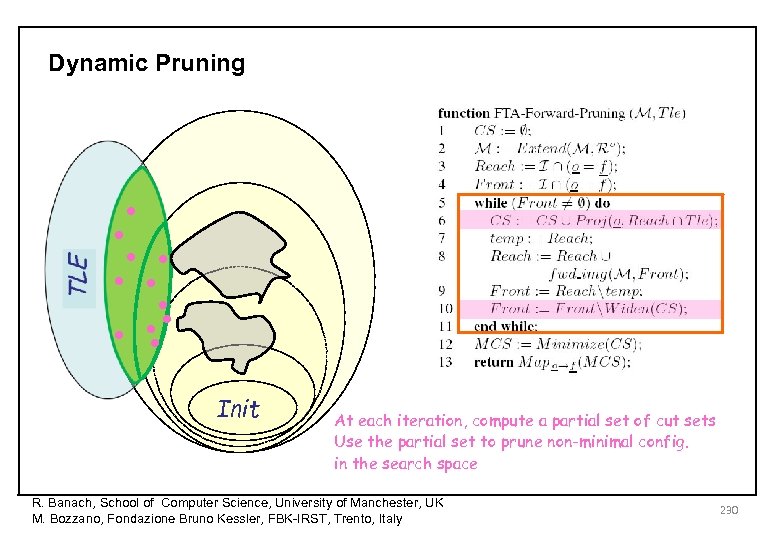 Dynamic Pruning • • • • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 230
Dynamic Pruning • • • • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 230
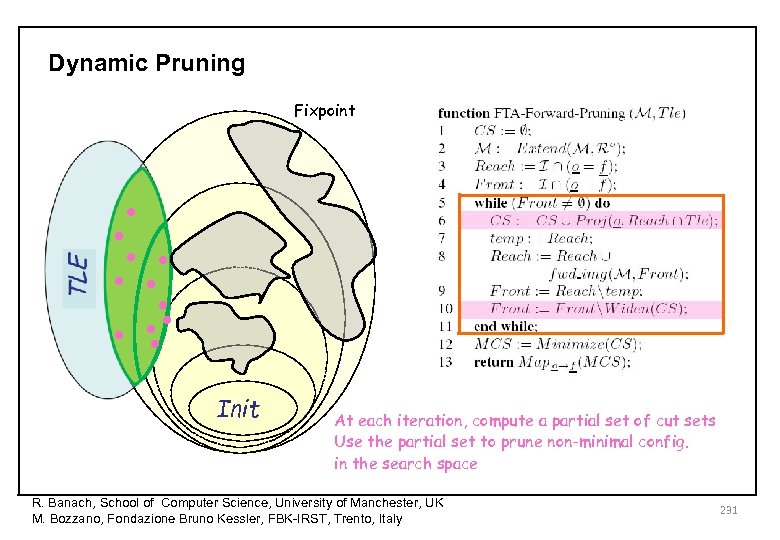 Dynamic Pruning Fixpoint • • • • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 231
Dynamic Pruning Fixpoint • • • • • Init At each iteration, compute a partial set of cut sets Use the partial set to prune non-minimal config. in the search space R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 231
 12. Retrenchment and Model Checking Compared. We compare: • The Retrenchment-based FT generation algorithm. • The BDD-based backward FT generation algorithm. (with Dynamic Cone of Influence and Dynamic Pruning) In the general case of feedback circuits with time delays. Strong similarities: • Most important: backward resolution, i. e. start from the TLE. But – several differences: • Related to: system decomposition, search strategy, etc. • Implementation-level but also theoretical differences. Discussion: how to reconcile retrenchment with model checking. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 232
12. Retrenchment and Model Checking Compared. We compare: • The Retrenchment-based FT generation algorithm. • The BDD-based backward FT generation algorithm. (with Dynamic Cone of Influence and Dynamic Pruning) In the general case of feedback circuits with time delays. Strong similarities: • Most important: backward resolution, i. e. start from the TLE. But – several differences: • Related to: system decomposition, search strategy, etc. • Implementation-level but also theoretical differences. Discussion: how to reconcile retrenchment with model checking. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 232
 System Decomposition Retrenchment-based: decomposition based on system structure. BDD-based: decomposition based on time delays. Consequences: • No difference if unit delays between every block. (e. g. , adders and fanouts in the circuit example). • In the purely combinational case – no delays: BDD-based flattens the system – monolithic transition relation. Reconciliation: • Not a huge difference: BDD-based could be instructed to take system structure into account, or use “hybrid” strategies. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 233
System Decomposition Retrenchment-based: decomposition based on system structure. BDD-based: decomposition based on time delays. Consequences: • No difference if unit delays between every block. (e. g. , adders and fanouts in the circuit example). • In the purely combinational case – no delays: BDD-based flattens the system – monolithic transition relation. Reconciliation: • Not a huge difference: BDD-based could be instructed to take system structure into account, or use “hybrid” strategies. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 233
 Search Strategy Retrenchment-based: non-deterministic, data dependency driven, search. • Depth-first search illustrated here, although simplified by the use of angelic non-determinism theoretically. BDD-based: breadth-first search. • Each step decomposing one layer of the composition. • Efficiency of breadth-first search relies on the BDD package. • Dynamic pruning introducing controlled depth-first aspects in the search. Reconciliation: • Not a huge difference: search strategy in BDD-based is flexible. • Possibly introducing further depth-first aspects in BDD-based, e. g. descend first in branches with a lower number of faults, and then prune. • Mostly an implementation detail. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 234
Search Strategy Retrenchment-based: non-deterministic, data dependency driven, search. • Depth-first search illustrated here, although simplified by the use of angelic non-determinism theoretically. BDD-based: breadth-first search. • Each step decomposing one layer of the composition. • Efficiency of breadth-first search relies on the BDD package. • Dynamic pruning introducing controlled depth-first aspects in the search. Reconciliation: • Not a huge difference: search strategy in BDD-based is flexible. • Possibly introducing further depth-first aspects in BDD-based, e. g. descend first in branches with a lower number of faults, and then prune. • Mostly an implementation detail. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 234
 Minimisation Rules Retrenchment-based: minimisation rules to prune the search tree on the fly. BDD-based: minimisation rules mimicked by the internals of the algorithm or by the BDD package. • Discarding non-needed subtrees → BDD package + DCOI reduction rules. • Discarding subtrees at input-insensitive faults → BDD package. • Discarding locally subsumed expressions → dynamic pruning. • Subsumption checking at the subsystem level → dynamic pruning. Reconciliation: • Not needed. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 235
Minimisation Rules Retrenchment-based: minimisation rules to prune the search tree on the fly. BDD-based: minimisation rules mimicked by the internals of the algorithm or by the BDD package. • Discarding non-needed subtrees → BDD package + DCOI reduction rules. • Discarding subtrees at input-insensitive faults → BDD package. • Discarding locally subsumed expressions → dynamic pruning. • Subsumption checking at the subsystem level → dynamic pruning. Reconciliation: • Not needed. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 235
 Timing and Feedback Retrenchment-based: deals with time delays explicitly. • Time information fully recorded. • Different definitions of minimality may be used to turn a RT into a FT. BDD-based: deals with time delays tacitly. • Time information is not recorded, temporal details abstracted away, same states with different time delays are identified. • Directly generates the fault trees representing the minimal cut sets. (where definition of minimality abstracts away from time) Reconciliation: • Soundness: we get the same results in both cases if we abstract away from time. • Possibly introducing handling of timing information in BDD-based – but in practice may have an impact on performance. Need to deal with sets of traces rather than sets of states, in a controlled way. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 236
Timing and Feedback Retrenchment-based: deals with time delays explicitly. • Time information fully recorded. • Different definitions of minimality may be used to turn a RT into a FT. BDD-based: deals with time delays tacitly. • Time information is not recorded, temporal details abstracted away, same states with different time delays are identified. • Directly generates the fault trees representing the minimal cut sets. (where definition of minimality abstracts away from time) Reconciliation: • Soundness: we get the same results in both cases if we abstract away from time. • Possibly introducing handling of timing information in BDD-based – but in practice may have an impact on performance. Need to deal with sets of traces rather than sets of states, in a controlled way. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 236
 Initial States and Cold-Start Failures Retrenchment-based: uses appropriate truncation of the detailed FT. • Minimisation performed independently of initialisation. BDD-based: truncation performed on-the-fly, reachability check built in. • Tight coupling of initialisation and minimisation. • Minimisation may interact with timing abstraction: • It may discard states that have been identified because of timing abstraction. • It may discard hot-running scenarios in favour of cold-start ones. • Focus on computation of MCSs, rather than fault trees. Reconciliation: • It is possible to rule out cold-start scenarios in BDD-based, if desired. • Possibly introducing further guidance in BDD-based to deal with hot-running and cold-start failures. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 237
Initial States and Cold-Start Failures Retrenchment-based: uses appropriate truncation of the detailed FT. • Minimisation performed independently of initialisation. BDD-based: truncation performed on-the-fly, reachability check built in. • Tight coupling of initialisation and minimisation. • Minimisation may interact with timing abstraction: • It may discard states that have been identified because of timing abstraction. • It may discard hot-running scenarios in favour of cold-start ones. • Focus on computation of MCSs, rather than fault trees. Reconciliation: • It is possible to rule out cold-start scenarios in BDD-based, if desired. • Possibly introducing further guidance in BDD-based to deal with hot-running and cold-start failures. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 237
 Conclusions Retrenchment-based: an idealised specification of a FT generation algorithm. Can move it closer to the BDD-based algorithm by carefully forgetting details. BDD-based: an implementation that does not completely conform to it. Can move it closer to the Retrenchment-based ‘ideal’ by including more details … but you have to watch performance in practice. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 238
Conclusions Retrenchment-based: an idealised specification of a FT generation algorithm. Can move it closer to the BDD-based algorithm by carefully forgetting details. BDD-based: an implementation that does not completely conform to it. Can move it closer to the Retrenchment-based ‘ideal’ by including more details … but you have to watch performance in practice. R. Banach, School of Computer Science, University of Manchester, UK M. Bozzano, Fondazione Bruno Kessler, FBK-IRST, Trento, Italy 238


