4238dc2f953d7f09c5219f7a0fe09c5e.ppt
- Количество слайдов: 24

10 th CACR Information Security Workshop Biometrics—The Foundation of Quick & Positive Authentication 8 May 2002 Dario Stipisic Senior Consultant 212 -809 -9491 DStipisic@biometricgroup. com
Biometrics: Definition Biometrics: the automated measurement of physiological or behavioral characteristics to determine or authenticate identity l Leading technologies in public sector l – AFIS (large-scale identification through fingerprints) – Finger-scan – Facial-scan l Other technologies – Iris-scan – Signature-scan – Hand-scan www. biometricgroup. com © Copyright 2002 International Biometric Group Page 2
Why Are Biometrics Used? l Security – Protect sensitive data – High degree of identity certainty in transactions – Create databases with singular identities l Accountability – Improve auditing / reporting / record keeping l Convenience – Reduce password-related problems – Simplified access to controlled areas www. biometricgroup. com © Copyright 2002 International Biometric Group Page 3

Questions… l Questions no longer asked: – Should we consider looking at biometrics? – Are biometrics a viable security solution? l Questions now asked: – Which biometric technology and which vendor can address specific security issues? – What is the business case behind a biometric implementation? • Decrease losses due to fraud • Increase employee accountability • Increase customer convenience www. biometricgroup. com © Copyright 2002 International Biometric Group Page 4
Behavioral and Physiological Biometrics l Behavioral - Voice, Signature, Keystroke – Easier to use, often less expensive, less accurate, more subject to day-to-day fluctuation – Appropriate for relatively low-security, low-risk applications where acquisition devices are already in place (camera, telephone, signature pad) l Physiological - Finger, Hand, Iris, Retina, Face – Higher accuracy, stable, require slightly more effort l Biometric usage is both behavioral and physiological – Finger-scan, for example, requires the appropriate “behavior” – placing finger on device correctly – Voice patterns are based, to some degree, on physiological characteristics www. biometricgroup. com © Copyright 2002 International Biometric Group Page 5
Biometrics Vs. Other Authentication Methods l Pros – Biometrics cannot be lost, shared, stolen, forgotten, or easily repudiated – Biometrics enable strong auditing and reporting capabilities – Can alter security requirements on a transactional basis – Only technology capable of identifying non-cooperative individuals l Cons – Biometrics do not provide 100% accuracy – Percentage of users cannot use some technologies – Characteristics can change over time www. biometricgroup. com © Copyright 2002 International Biometric Group Page 6
Typical Biometric Applications l Large-scale government identification – – – l Drivers license (IL, WV, GA, possibly CA, MD, MA) Voter registration (throughout Latin America) Public benefits (CA, NY, TX, South Africa, Philippines) National ID (Nigeria, Argentina, possibly China) Tens of millions of individuals enrolled Time and attendance, access control – Hand geometry, finger-scan – Hundreds of thousands of individuals enrolled l Network Security – Windows NT Login, Intranets – Tens of thousands of users enrolled www. biometricgroup. com © Copyright 2002 International Biometric Group Page 7
Identification vs. Verification: Am I who I claim to be? – Faster, more accurate, less expensive – The more common method for IT security – More accountability – Requires that users enter a unique username or present a card/token l Identification: Who am I? – Used to locate duplicate identities in databases – Used when entering a username/ID is not feasible – Privacy challenges l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 8
Biometric Templates Definition – Distinctive, encoded files derived and encoded from the unique features of a biometric sample l A basic element of biometric systems – Templates, not samples, are used in biometric matching – Created during enrollment and verification – Much smaller amount of data than sample (1/100 th, 1/1000 th) – Cannot reverse-engineer sample from template – Size facilitates encryption, storage on various tokens – Vendor templates are not interchangeable – Different templates are generated each time an individual provides a biometric sample l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 9
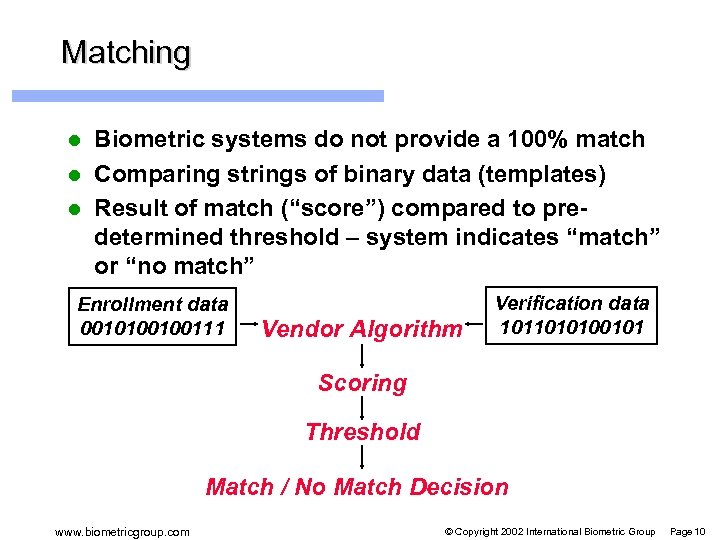
Matching Biometric systems do not provide a 100% match l Comparing strings of binary data (templates) l Result of match (“score”) compared to predetermined threshold – system indicates “match” or “no match” l Enrollment data 0010100100111 Vendor Algorithm Verification data 1011010100101 Scoring Threshold Match / No Match Decision www. biometricgroup. com © Copyright 2002 International Biometric Group Page 10
Real-World Accuracy Vendor claims (1/1000, 1/1000000) are not always based on experience in real-world deployments l System accuracy defined through three metrics – False match (imposter breaks in) – False non-match (correct user locked out) – Failure to enroll (user cannot register in system) l Comparative testing shows that some devices and technologies provide very high accuracy, others very low accuracy l Regardless of technology, some small percentage will be unable to enroll l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 11

Biometric Market Size 2001 Total Revenue: $524 m USD l Projected 2003 Revenue: $1. 05 b USD l Most revenues today from law enforcement / public sector identification l Revenues for IT-oriented technologies l – Finger-scan: $99. 37 m – Middleware: $24. 2 m – Less than $20 m: voice-scan, signature-scan, iris-scan Source: Biometric Market Report 2000 -2005 www. biometricgroup. com © Copyright 2002 International Biometric Group Page 12

Major Developments in the Marketplace l l l l Large-scale ID systems for travel, licensing being developed Finger-scan devices manufactured by Infineon, ST, Fujitsu, Sony, Motorola Compaq, Dell, Toshiba shipping biometric devices with PCs 1 m users of facial-scan for ATM check-cashing Microsoft, Intel to incorporate biometric functionality in future versions of OS Increased adoption of standards – file formats, encryption, APIs Convergence with smart card technology www. biometricgroup. com © Copyright 2002 International Biometric Group Page 13
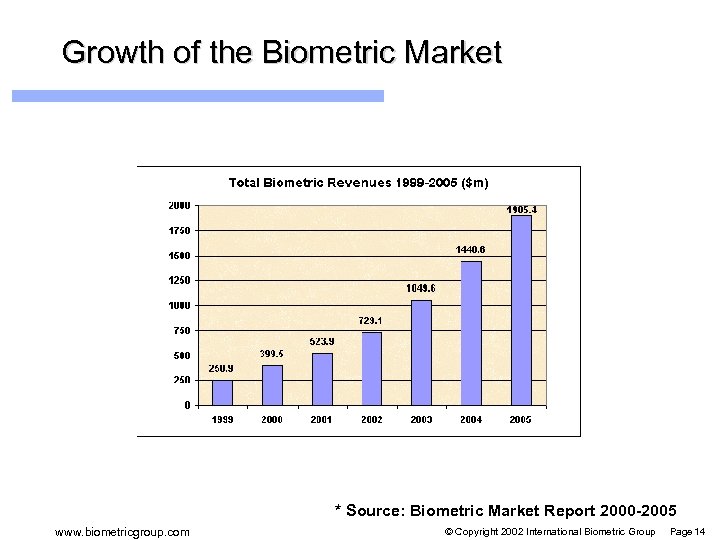
Growth of the Biometric Market * Source: Biometric Market Report 2000 -2005 www. biometricgroup. com © Copyright 2002 International Biometric Group Page 14
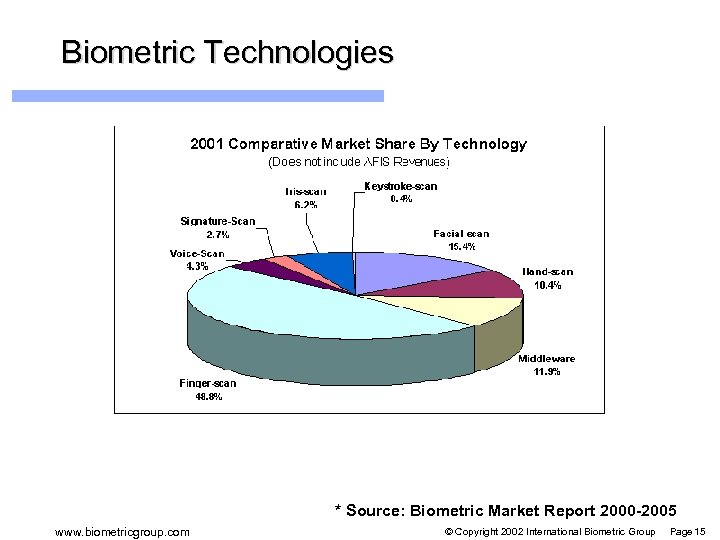
Biometric Technologies * Source: Biometric Market Report 2000 -2005 www. biometricgroup. com © Copyright 2002 International Biometric Group Page 15
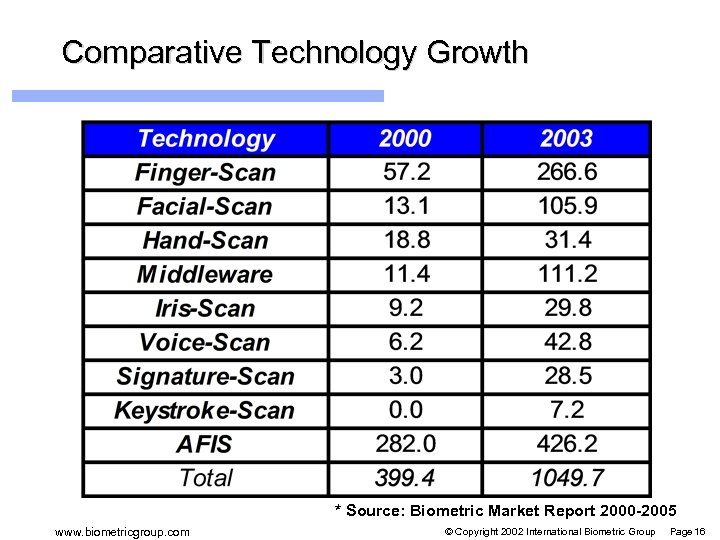
Comparative Technology Growth * Source: Biometric Market Report 2000 -2005 www. biometricgroup. com © Copyright 2002 International Biometric Group Page 16
Future Market Trends PC/Network security, e-commerce will drive growth – From less than 20% of total biometric revenue to over 40% by 2005 l Emergence of Retail – ATM - Point of Sale sector – From $10 m today to $131 m by 2005 l Biometric revenue models based on transactional authentication, not device sales l Larger firms will absorb or eliminate many/most of today’s biometric players l Source: Biometric Market Report 2000 -2005 www. biometricgroup. com © Copyright 2002 International Biometric Group Page 17
Privacy Protection, Privacy Erosion l Biometric Protection of Privacy – Limiting access to sensitive data – Individual control over personal information – Potential weapon against identity fraud / theft l Biometric Erosion of Privacy – If used for broader purposes than originally intended (linking disparate data, tracking behavior) – If captured without informed consent www. biometricgroup. com © Copyright 2002 International Biometric Group Page 18

Privacy Fears Informational Privacy – Function creep – Use as unique identifier – Associating unrelated data – Use by law enforcement agencies without oversight – Generally based on misuse of technology as opposed to intended uses l Personal Privacy – Inherent discomfort with or opposition to biometrics – Perception of invasiveness l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 19
Mitigating Factors l l l l Most biometrics incapable of identification Substantial amount of biometric data required for large-scale identification Very few shared public or private sector systems aside from law enforcement Core matching algorithms not cross-compatible Deployers can implement operational and designoriented protections against system abuse Technology not infallible or foolproof Legislation accompanies public sector deployment to protect against misuse Biometric usage has been closely monitored www. biometricgroup. com © Copyright 2002 International Biometric Group Page 20
IBG’s Bio. Privacy™ Initiative Analysis of biometric applications – Bio. Privacy Impact Framework Not all biometric deployments bear the same privacy risks: specific features of biometric deployments increase or decrease the likelihood of misuse l Analysis of core biometric technologies – Bio. Privacy Technology Risk Ratings Certain technologies are more prone to be misused than others and require extra precautions l Steps towards a privacy-sympathetic system – Bio. Privacy Best Practices Ensure that deployers adhere to privacy principles regarding consent, use limitation, storage limitation, and accountability l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 21
Bio. Privacy Impact Framework l l l l l Overt vs. Covert Opt-in vs. Mandatory Verification vs. Identification Fixed Duration vs. Indefinite Duration Private Sector vs. Public Sector Individual / Customer vs. Employee / Citizen User Ownership vs. Institutional Ownership Personal Storage vs. Template Database Behavioral vs. Physiological Templates vs. Identifiable Data www. biometricgroup. com © Copyright 2002 International Biometric Group Page 22
Technology Risk Rating Criteria Verification/Identification l Overt/Covert l Behavioral/Physiological l Give/Grab – Technologies in which the user "gives" biometric data are rated “lower-risk” – Technologies in which the system "grabs" user data without the user initiating a sequence are rated “higher-risk” l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 23

Bio. Privacy 25 Best Practices Implement as many Best Practices as possible without undermining the basic operations of the biometric system l Few deployers will be able to adhere to all Bio. Privacy Best Practices l Inability to comply with certain Best Practices is balanced by adherence to others l Four Categories – Scope and Capabilities – Data Protection – User Control Of Personal Data – Disclosure, Auditing and Accountability l www. biometricgroup. com © Copyright 2002 International Biometric Group Page 24
4238dc2f953d7f09c5219f7a0fe09c5e.ppt