ff46e6bdf968599502eb810518c7db19.ppt
- Количество слайдов: 41
 1
1
 Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the • Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 2
Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the • Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 2
 Ø The past three years, demonstrates that Vo. IP is here to stay. ü Security issues will become more apparent as the subscriber population increases. Ø IETF has made several improvements that provide protection for the Vo. IP signaling and media streams. ü Encrypt SIP signaling, SRTP (Secure Real Time Protocol) to protect the media stream. Ø One of the problems is that vendors maintain a slow adoption and implementation rate of these protocols. ü Some Vo. IP service providers confuse what security means in packet based communications. Ø Discussion the security mechanisms recommended by the SIP standard ü SIP Security based on S/MIME authentication and encryption of the session initiation. ü Protection of the media channels using the Secure Real-time Transport Protocol (SRTP). 3
Ø The past three years, demonstrates that Vo. IP is here to stay. ü Security issues will become more apparent as the subscriber population increases. Ø IETF has made several improvements that provide protection for the Vo. IP signaling and media streams. ü Encrypt SIP signaling, SRTP (Secure Real Time Protocol) to protect the media stream. Ø One of the problems is that vendors maintain a slow adoption and implementation rate of these protocols. ü Some Vo. IP service providers confuse what security means in packet based communications. Ø Discussion the security mechanisms recommended by the SIP standard ü SIP Security based on S/MIME authentication and encryption of the session initiation. ü Protection of the media channels using the Secure Real-time Transport Protocol (SRTP). 3
 Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the • Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 4
Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the • Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 4
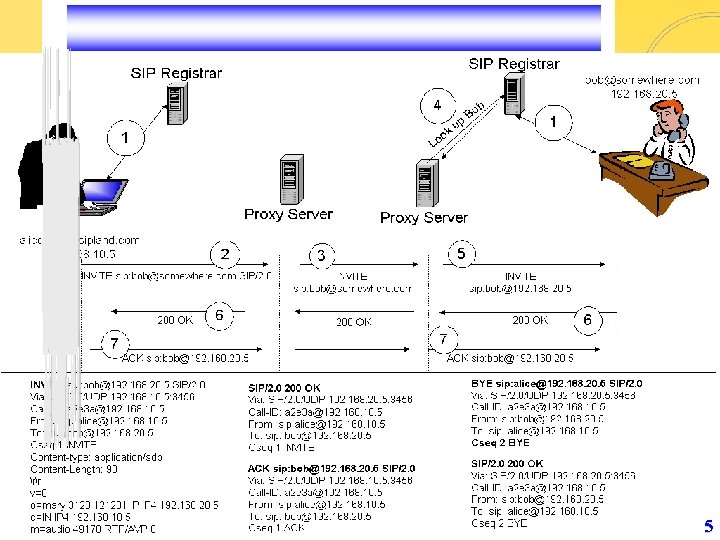 5
5
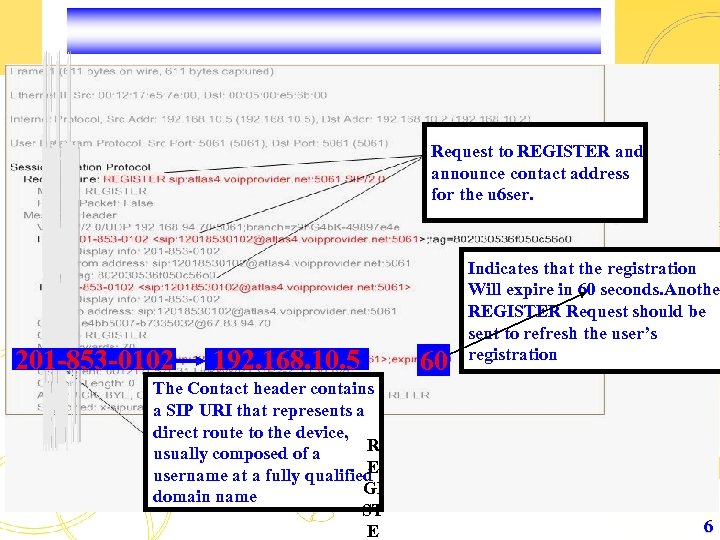 Request to REGISTER and announce contact address for the u 6 ser. 201 -853 -0102 192. 168. 10. 5 The Contact header contains a SIP URI that represents a direct route to the device, R usually composed of a E username at a fully qualified GI domain name ST E 60 Indicates that the registration Will expire in 60 seconds. Another REGISTER Request should be sent to refresh the user’s registration 6
Request to REGISTER and announce contact address for the u 6 ser. 201 -853 -0102 192. 168. 10. 5 The Contact header contains a SIP URI that represents a direct route to the device, R usually composed of a E username at a fully qualified GI domain name ST E 60 Indicates that the registration Will expire in 60 seconds. Another REGISTER Request should be sent to refresh the user’s registration 6
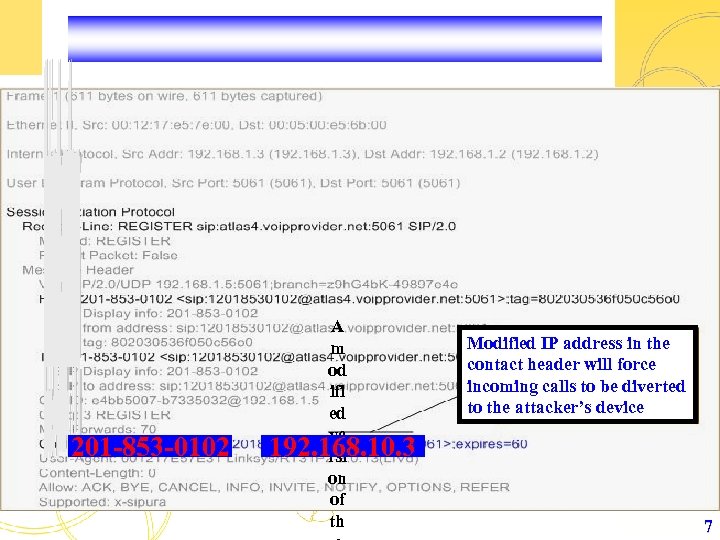 201 -853 -0102 A m od ifi ed ve 192. 168. 10. 3 rsi on of th Modified IP address in the contact header will force incoming calls to be diverted to the attacker’s device 7
201 -853 -0102 A m od ifi ed ve 192. 168. 10. 3 rsi on of th Modified IP address in the contact header will force incoming calls to be diverted to the attacker’s device 7
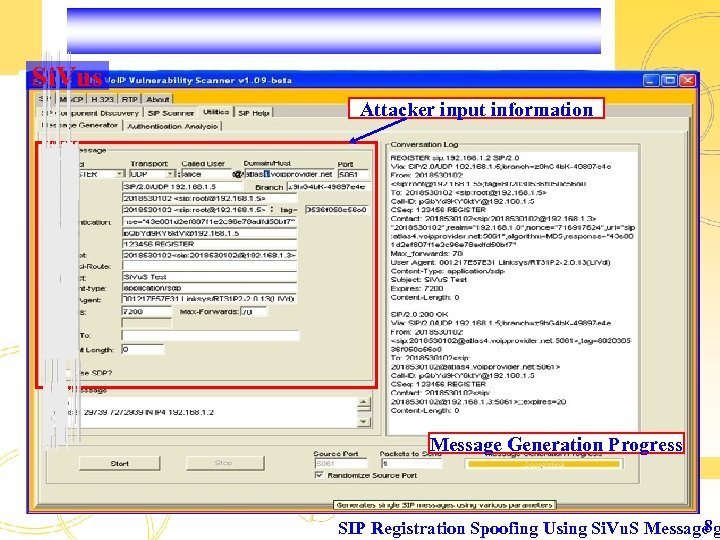 Si. Vus Attacker input information Message Generation Progress 8 SIP Registration Spoofing Using Si. Vu. S Message g
Si. Vus Attacker input information Message Generation Progress 8 SIP Registration Spoofing Using Si. Vu. S Message g
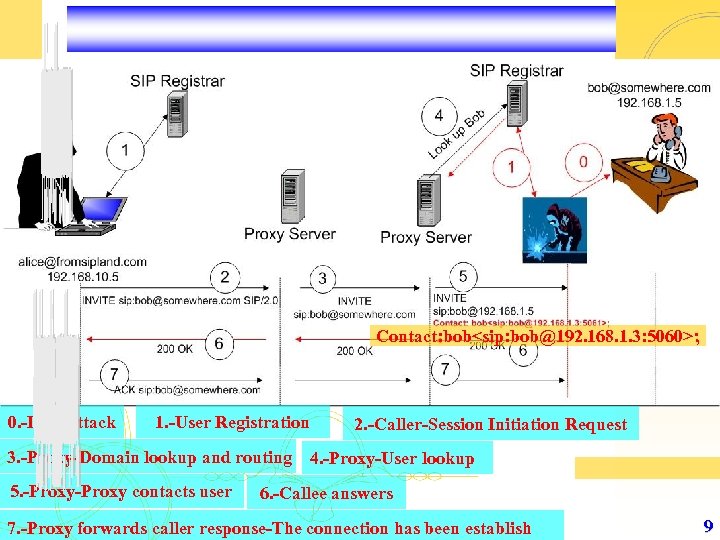 Contact: bob
Contact: bob
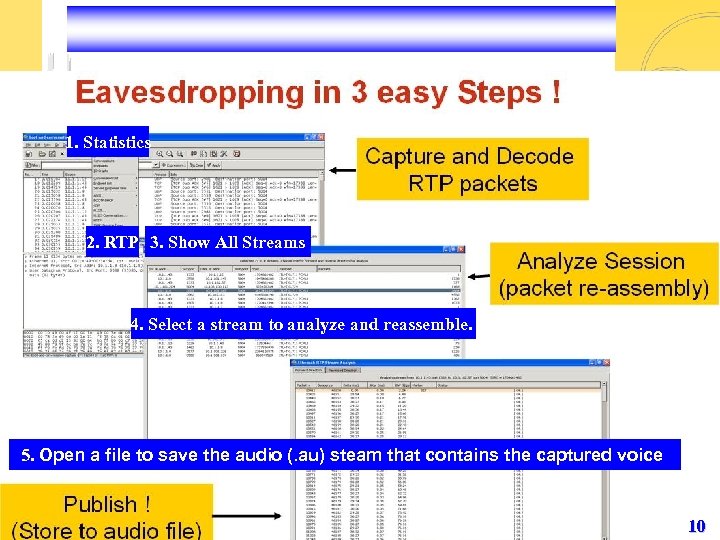 1. Statistics 2. RTP 3. Show All Streams 4. Select a stream to analyze and reassemble. 5. Open a file to save the audio (. au) steam that contains the captured voice 10
1. Statistics 2. RTP 3. Show All Streams 4. Select a stream to analyze and reassemble. 5. Open a file to save the audio (. au) steam that contains the captured voice 10
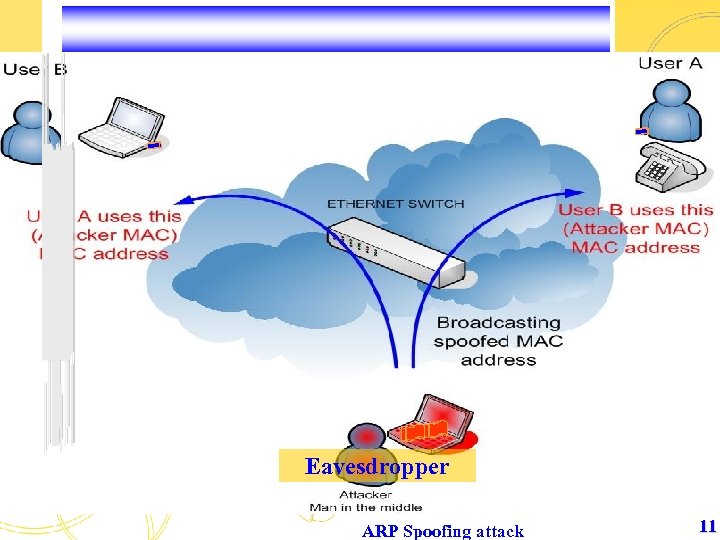 Eavesdropper ARP Spoofing attack 11
Eavesdropper ARP Spoofing attack 11
 Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Ø Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 13
Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Ø Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 13
 Ø S/MIME : Secure/Multipurpose Internet Mail Extension RFC 2633 – Information Digests:Integrity, SHA-1(Secure Hash Algorithm Version 1. 0) 160 Bits RFC 3174 – Digital Signature:Non-repudiation, DSS (Digital Signature Standard),Digital Signature RFC 2943 – Cleartext Encryption Algorithm:Secrecy or Privacy, AES (Advance Encryption Standard) RFC 3565 – Session Key Encryption:Secret Key Exchange , Diffie-Hellman RFC 2631 14
Ø S/MIME : Secure/Multipurpose Internet Mail Extension RFC 2633 – Information Digests:Integrity, SHA-1(Secure Hash Algorithm Version 1. 0) 160 Bits RFC 3174 – Digital Signature:Non-repudiation, DSS (Digital Signature Standard),Digital Signature RFC 2943 – Cleartext Encryption Algorithm:Secrecy or Privacy, AES (Advance Encryption Standard) RFC 3565 – Session Key Encryption:Secret Key Exchange , Diffie-Hellman RFC 2631 14
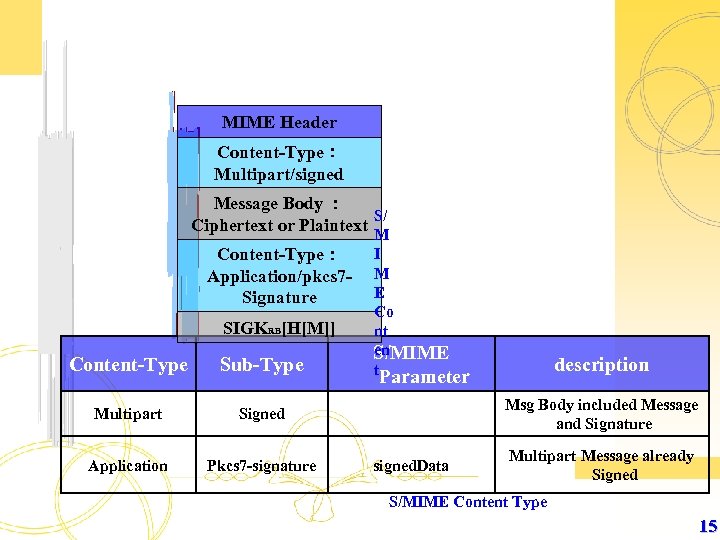 MIME Header Content-Type: Multipart/signed Message Body : S/ Ciphertext or Plaintext Content-Type: Application/pkcs 7 Signature SIGKRB[H[M]] Content-Type Sub-Type Multipart Signed Application Pkcs 7 -signature M I M E Co nt en S/MIME t. Parameter description Msg Body included Message and Signature signed. Data Multipart Message already Signed S/MIME Content Type 15
MIME Header Content-Type: Multipart/signed Message Body : S/ Ciphertext or Plaintext Content-Type: Application/pkcs 7 Signature SIGKRB[H[M]] Content-Type Sub-Type Multipart Signed Application Pkcs 7 -signature M I M E Co nt en S/MIME t. Parameter description Msg Body included Message and Signature signed. Data Multipart Message already Signed S/MIME Content Type 15
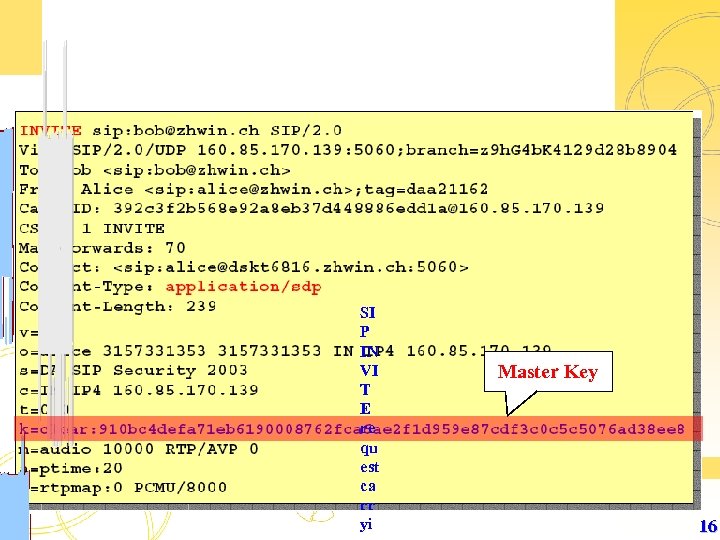 SI P IN VI T E re qu est ca rr yi Master Key 16
SI P IN VI T E re qu est ca rr yi Master Key 16
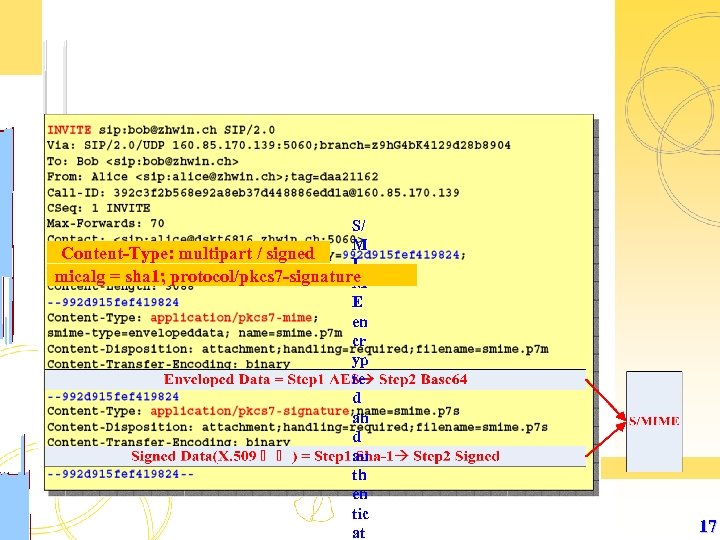 S/ M Content-Type: multipart / signed I micalg = sha 1; protocol/pkcs 7 -signature M E en cr yp te d an d au th en tic at 17
S/ M Content-Type: multipart / signed I micalg = sha 1; protocol/pkcs 7 -signature M E en cr yp te d an d au th en tic at 17
 Ø Session Key Exchange Algorithm Diffie-Hellman Key Exchange Ø SIP Message Encryption Algorithm AES : Block Cipher Ø Digital Signature (SIP Message Integrity) DSS : Integrity and Non-repudiation Ø Message Hash Algorithm SHA-1 : Message Digest 18
Ø Session Key Exchange Algorithm Diffie-Hellman Key Exchange Ø SIP Message Encryption Algorithm AES : Block Cipher Ø Digital Signature (SIP Message Integrity) DSS : Integrity and Non-repudiation Ø Message Hash Algorithm SHA-1 : Message Digest 18
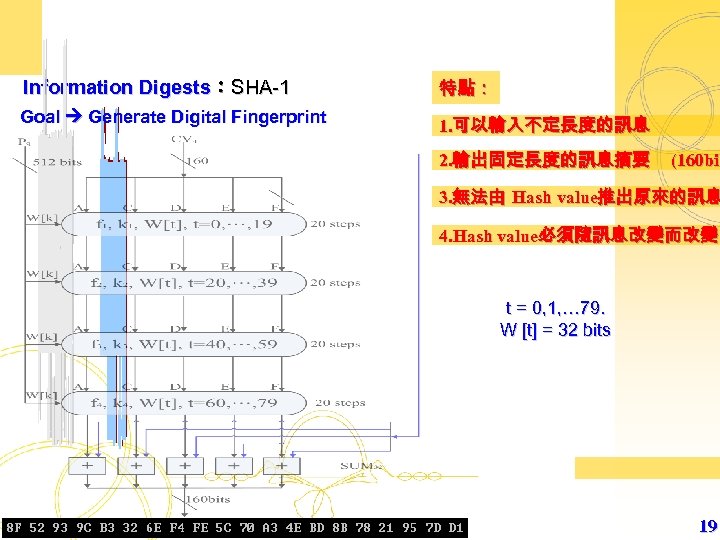 Information Digests:SHA-1 特點: Goal Generate Digital Fingerprint 1. 可以輸入不定長度的訊息 2. 輸出固定長度的訊息摘要 (160 bit 3. 無法由 Hash value推出原來的訊息 4. Hash value必須隨訊息改變而改變 t = 0, 1, … 79. W [t] = 32 bits 19
Information Digests:SHA-1 特點: Goal Generate Digital Fingerprint 1. 可以輸入不定長度的訊息 2. 輸出固定長度的訊息摘要 (160 bit 3. 無法由 Hash value推出原來的訊息 4. Hash value必須隨訊息改變而改變 t = 0, 1, … 79. W [t] = 32 bits 19
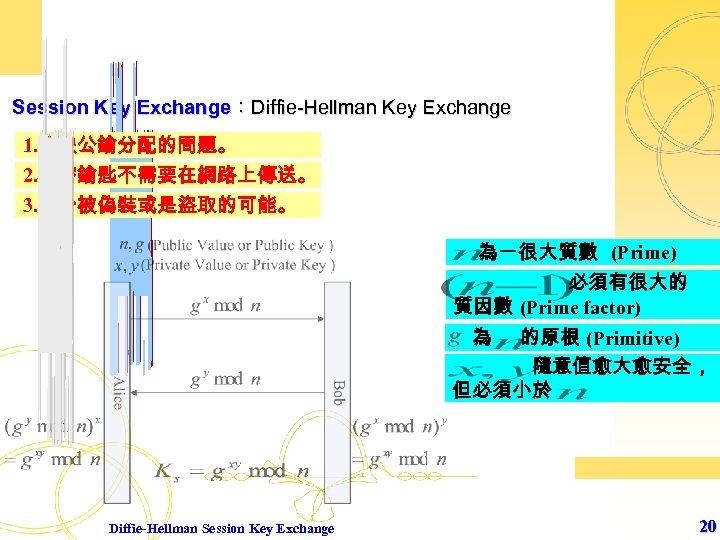 Session Key Exchange:Diffie-Hellman Key Exchange 1. 解決公鑰分配的問題。 2. 秘密鑰匙不需要在網路上傳送。 3. 減少被偽裝或是盜取的可能。 為一很大質數 (Prime) 必須有很大的 質因數 (Prime factor) 為 的原根 (Primitive) 隨意值愈大愈安全, 但必須小於 Diffie-Hellman Session Key Exchange 20
Session Key Exchange:Diffie-Hellman Key Exchange 1. 解決公鑰分配的問題。 2. 秘密鑰匙不需要在網路上傳送。 3. 減少被偽裝或是盜取的可能。 為一很大質數 (Prime) 必須有很大的 質因數 (Prime factor) 為 的原根 (Primitive) 隨意值愈大愈安全, 但必須小於 Diffie-Hellman Session Key Exchange 20
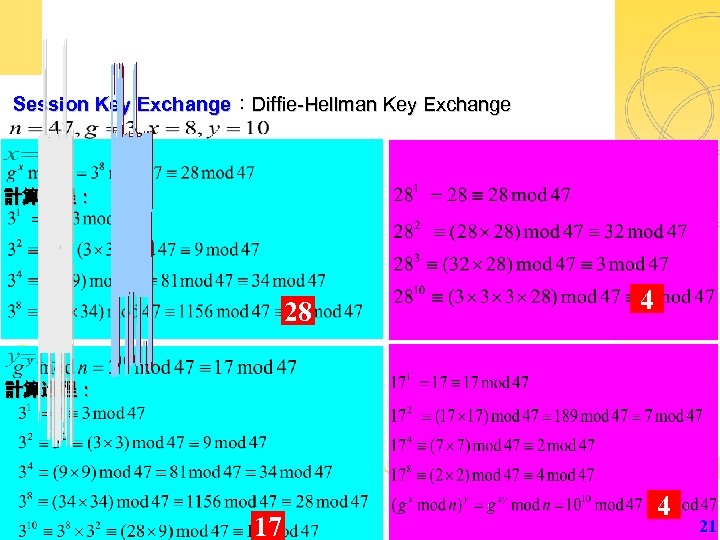 Session Key Exchange:Diffie-Hellman Key Exchange 計算過程: 28 4 計算過程: 17 4 21
Session Key Exchange:Diffie-Hellman Key Exchange 計算過程: 28 4 計算過程: 17 4 21
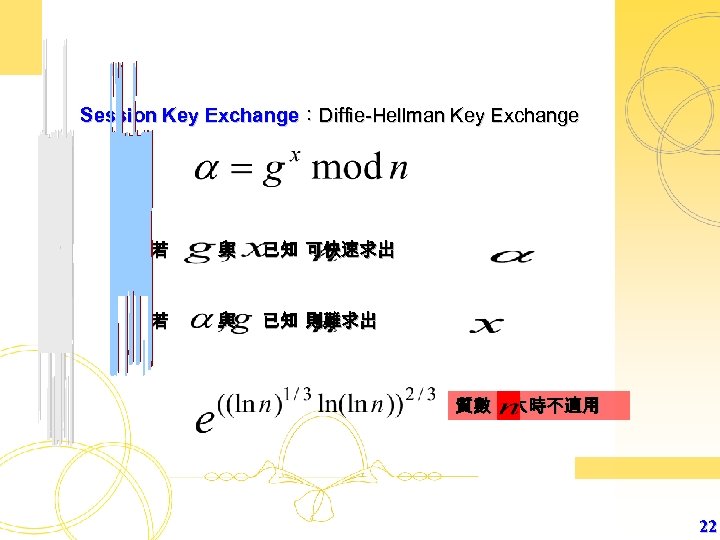 Session Key Exchange:Diffie-Hellman Key Exchange 若 與 已知 可快速求出 若 與 已知 則難求出 質數 大時不適用 22
Session Key Exchange:Diffie-Hellman Key Exchange 若 與 已知 可快速求出 若 與 已知 則難求出 質數 大時不適用 22
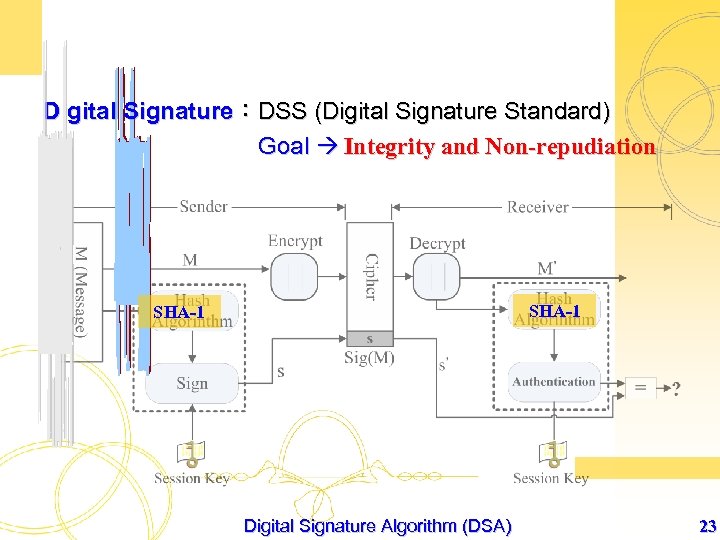 Digital Signature:DSS (Digital Signature Standard) Goal Integrity and Non-repudiation SHA-1 Digital Signature Algorithm (DSA) 23
Digital Signature:DSS (Digital Signature Standard) Goal Integrity and Non-repudiation SHA-1 Digital Signature Algorithm (DSA) 23
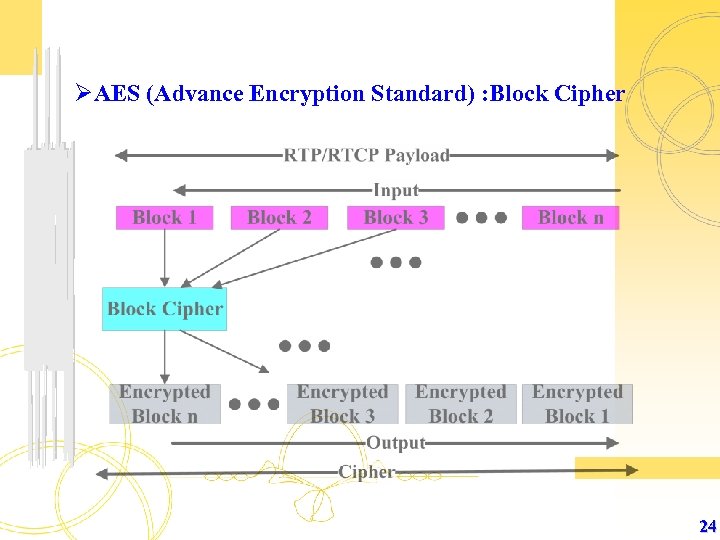 ØAES (Advance Encryption Standard) : Block Cipher 24
ØAES (Advance Encryption Standard) : Block Cipher 24
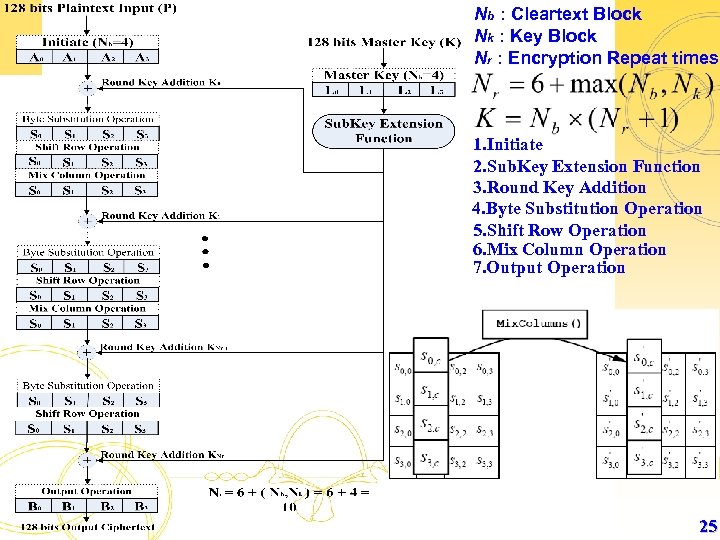 Nb : Cleartext Block Nk : Key Block Nr : Encryption Repeat times 1. Initiate 2. Sub. Key Extension Function 3. Round Key Addition 4. Byte Substitution Operation 5. Shift Row Operation 6. Mix Column Operation 7. Output Operation 25
Nb : Cleartext Block Nk : Key Block Nr : Encryption Repeat times 1. Initiate 2. Sub. Key Extension Function 3. Round Key Addition 4. Byte Substitution Operation 5. Shift Row Operation 6. Mix Column Operation 7. Output Operation 25
 Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Ø Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 26
Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Ø Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 26
 Ø Currently defined encryption transforms do not add any padding. Ø The size of the RTP payload is not increased by encryption. Ø The default tag length is 10 bytes but might be reduced if the. transmission channel does not allow such a large increase of the RTP packet size. 27
Ø Currently defined encryption transforms do not add any padding. Ø The size of the RTP payload is not increased by encryption. Ø The default tag length is 10 bytes but might be reduced if the. transmission channel does not allow such a large increase of the RTP packet size. 27
 28
28
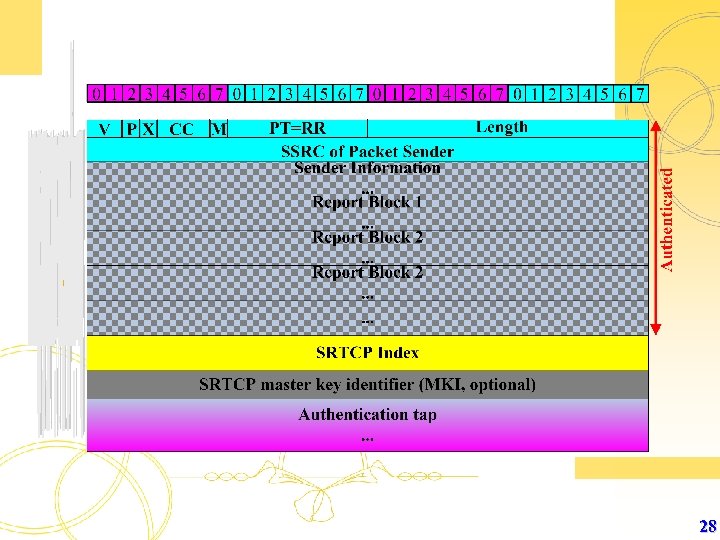
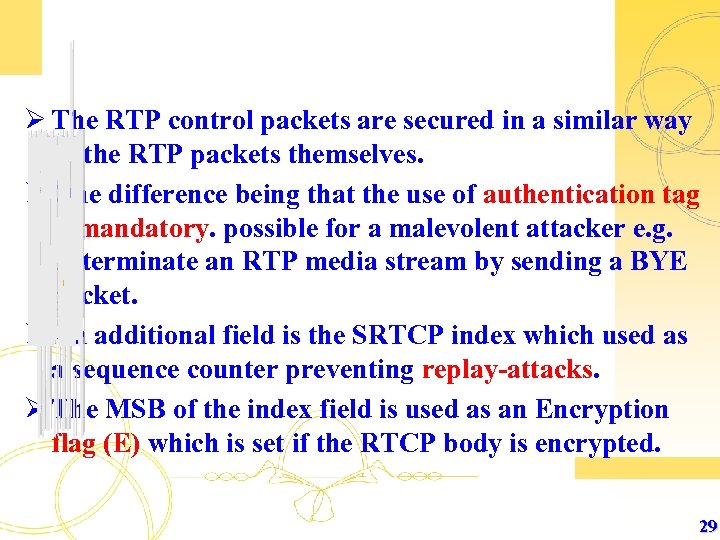 Ø The RTP control packets are secured in a similar way as the RTP packets themselves. Ø One difference being that the use of authentication tag is mandatory. possible for a malevolent attacker e. g. to terminate an RTP media stream by sending a BYE packet. Ø An additional field is the SRTCP index which used as a sequence counter preventing replay-attacks. Ø The MSB of the index field is used as an Encryption flag (E) which is set if the RTCP body is encrypted. 29
Ø The RTP control packets are secured in a similar way as the RTP packets themselves. Ø One difference being that the use of authentication tag is mandatory. possible for a malevolent attacker e. g. to terminate an RTP media stream by sending a BYE packet. Ø An additional field is the SRTCP index which used as a sequence counter preventing replay-attacks. Ø The MSB of the index field is used as an Encryption flag (E) which is set if the RTCP body is encrypted. 29
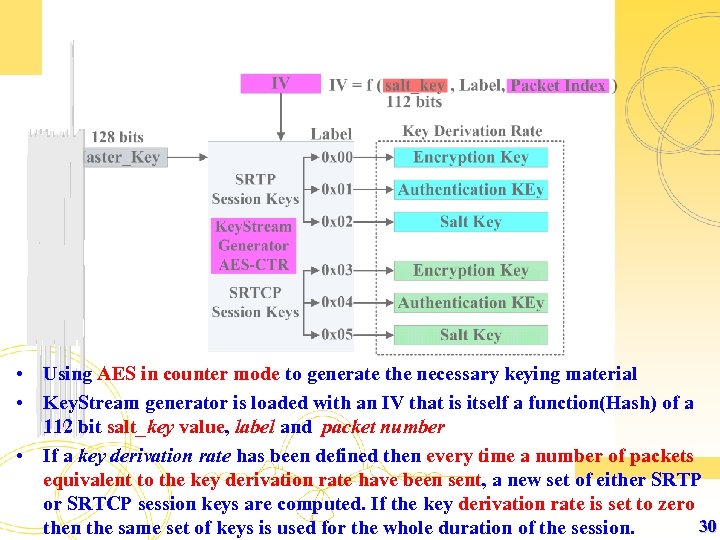 • Using AES in counter mode to generate the necessary keying material • Key. Stream generator is loaded with an IV that is itself a function(Hash) of a 112 bit salt_key value, label and packet number • If a key derivation rate has been defined then every time a number of packets equivalent to the key derivation rate have been sent, a new set of either SRTP or SRTCP session keys are computed. If the key derivation rate is set to zero 30 then the same set of keys is used for the whole duration of the session.
• Using AES in counter mode to generate the necessary keying material • Key. Stream generator is loaded with an IV that is itself a function(Hash) of a 112 bit salt_key value, label and packet number • If a key derivation rate has been defined then every time a number of packets equivalent to the key derivation rate have been sent, a new set of either SRTP or SRTCP session keys are computed. If the key derivation rate is set to zero 30 then the same set of keys is used for the whole duration of the session.
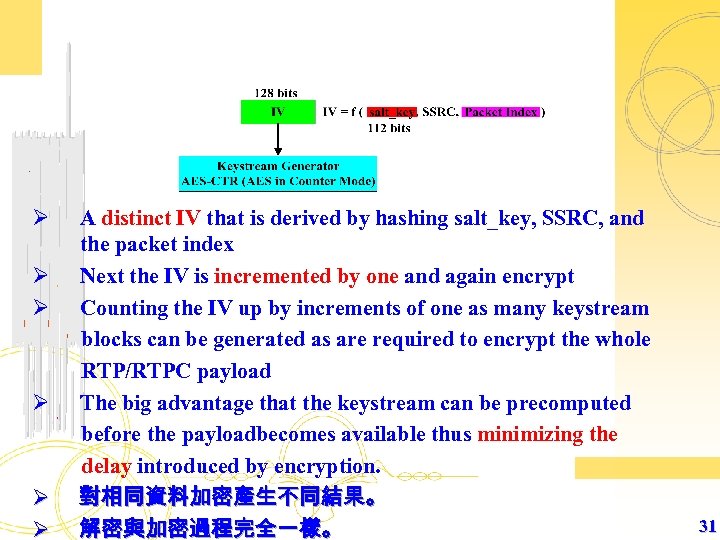 Ø A distinct IV that is derived by hashing salt_key, SSRC, and the packet index Ø Next the IV is incremented by one and again encrypt Ø Counting the IV up by increments of one as many keystream blocks can be generated as are required to encrypt the whole RTP/RTPC payload Ø The big advantage that the keystream can be precomputed before the payloadbecomes available thus minimizing the delay introduced by encryption. Ø 對相同資料加密產生不同結果。 Ø 解密與加密過程完全一樣。 31
Ø A distinct IV that is derived by hashing salt_key, SSRC, and the packet index Ø Next the IV is incremented by one and again encrypt Ø Counting the IV up by increments of one as many keystream blocks can be generated as are required to encrypt the whole RTP/RTPC payload Ø The big advantage that the keystream can be precomputed before the payloadbecomes available thus minimizing the delay introduced by encryption. Ø 對相同資料加密產生不同結果。 Ø 解密與加密過程完全一樣。 31
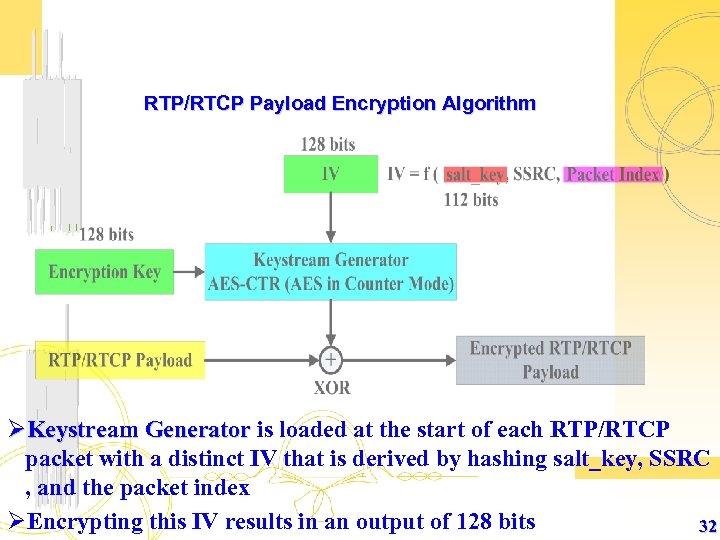 RTP/RTCP Payload Encryption Algorithm ØKeystream Generator is loaded at the start of each RTP/RTCP Generator packet with a distinct IV that is derived by hashing salt_key, SSRC , and the packet index ØEncrypting this IV results in an output of 128 bits 32
RTP/RTCP Payload Encryption Algorithm ØKeystream Generator is loaded at the start of each RTP/RTCP Generator packet with a distinct IV that is derived by hashing salt_key, SSRC , and the packet index ØEncrypting this IV results in an output of 128 bits 32
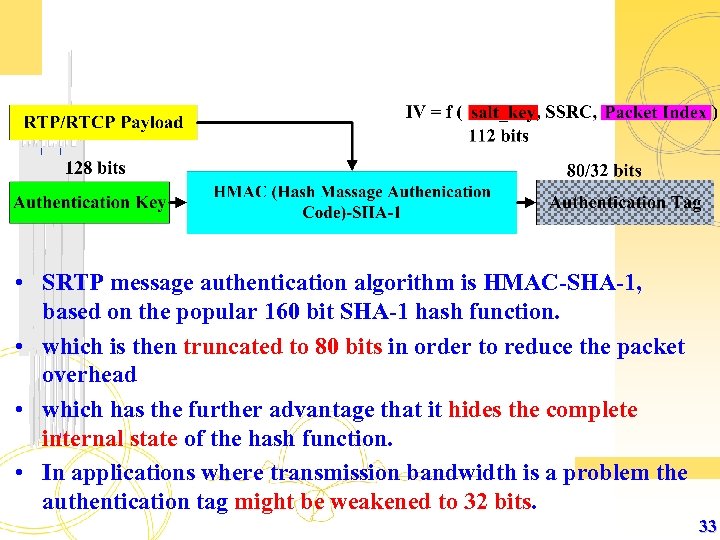 • SRTP message authentication algorithm is HMAC-SHA-1, based on the popular 160 bit SHA-1 hash function. • which is then truncated to 80 bits in order to reduce the packet overhead • which has the further advantage that it hides the complete internal state of the hash function. • In applications where transmission bandwidth is a problem the authentication tag might be weakened to 32 bits. 33
• SRTP message authentication algorithm is HMAC-SHA-1, based on the popular 160 bit SHA-1 hash function. • which is then truncated to 80 bits in order to reduce the packet overhead • which has the further advantage that it hides the complete internal state of the hash function. • In applications where transmission bandwidth is a problem the authentication tag might be weakened to 32 bits. 33
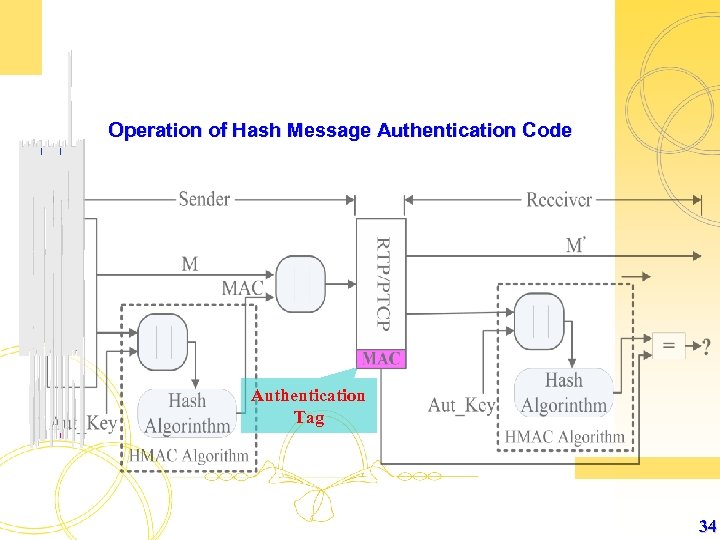 Operation of Hash Message Authentication Code Authentication Tag 34
Operation of Hash Message Authentication Code Authentication Tag 34
![HAMC Generate MAC (Message Authentication Code) HMACk[RTP/RTCP] = H[(Aut_Key XOR Opad)||H[(Auth_Key XOR ipad)||RTP/RTCP]] 35 HAMC Generate MAC (Message Authentication Code) HMACk[RTP/RTCP] = H[(Aut_Key XOR Opad)||H[(Auth_Key XOR ipad)||RTP/RTCP]] 35](https://present5.com/presentation/ff46e6bdf968599502eb810518c7db19/image-35.jpg) HAMC Generate MAC (Message Authentication Code) HMACk[RTP/RTCP] = H[(Aut_Key XOR Opad)||H[(Auth_Key XOR ipad)||RTP/RTCP]] 35
HAMC Generate MAC (Message Authentication Code) HMACk[RTP/RTCP] = H[(Aut_Key XOR Opad)||H[(Auth_Key XOR ipad)||RTP/RTCP]] 35
 Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 36
Ø Ø Ø Introduction Two attacks against Vo. IP Security Mechanisms Securing the SIP Session Management Using S/MIME Authentication Encryption of the Session Initiation Securing the Real-time Media Streams The Secure Real-Time Transport Protocol (SRTP) Conclusion Reference 36
 Ø Solutions for Securing the Real-time media streams üSecure RTP (SRTP), Uses master key which must be distributed by other means Ø Solutions for Securing the SIP Session Management üSecure MIME (S/MIME), for encryption the public key of the recipient user agent must be know Ø Diffie-Hellman Session Key Attachment Master Key in SIP Invite Message Sha-1 Generate Msg Digest DSS Generate Signature AES Encrypte Session Key Ø AES-CTR Generate All Key AES-CTR Encryption RTP/RTCP Payload HMAC-Sha-1 37
Ø Solutions for Securing the Real-time media streams üSecure RTP (SRTP), Uses master key which must be distributed by other means Ø Solutions for Securing the SIP Session Management üSecure MIME (S/MIME), for encryption the public key of the recipient user agent must be know Ø Diffie-Hellman Session Key Attachment Master Key in SIP Invite Message Sha-1 Generate Msg Digest DSS Generate Signature AES Encrypte Session Key Ø AES-CTR Generate All Key AES-CTR Encryption RTP/RTCP Payload HMAC-Sha-1 37
 粘添壽,吳順裕著,「資訊與網路安全技術」,2004年,旗標出版 社。 • 國科會電信國家型計畫,「安全網路電話中 SRTP的研究與金鑰 交換的設計」,馮輝副教授,國立台灣科技大學資訊 程系。 • Andreas Steffen, Daniel Kaufmann and Andreas Stricker, “SIP Security, ” DFN-Arbeitstagung über Kommunikationsnetze 2005: 397412 • Salsano, S. , Veltri, L. and Papalilo, D. . “SIP security issues: the SIP authentication procedure and its processing load, ” Network, IEEE Volume: 16 , Issue: 6 , pp. 38 - 44 Nov. -Dec. 2004 • M. Baugher, M. Naslund, E. Carrara, K. Norrman and D. Mc. Grew, “The Secure Real-time Transport Protocol (SRTP), ” Network Working Group , RFC 3711, March 2004. • J. Rosenberg, M. Handley, H. Schulzrinne, E. Schooler And J. Rosenberg, “SIP: Session Initiation Protocol, ” Internet Engineering Task Force, RFC 3261, June 2002. • http: //www. securityfocus. com/infocus/1862, Security. Focus • • Cain & Abel, http: //www. oxid. it/cain. html. 38
粘添壽,吳順裕著,「資訊與網路安全技術」,2004年,旗標出版 社。 • 國科會電信國家型計畫,「安全網路電話中 SRTP的研究與金鑰 交換的設計」,馮輝副教授,國立台灣科技大學資訊 程系。 • Andreas Steffen, Daniel Kaufmann and Andreas Stricker, “SIP Security, ” DFN-Arbeitstagung über Kommunikationsnetze 2005: 397412 • Salsano, S. , Veltri, L. and Papalilo, D. . “SIP security issues: the SIP authentication procedure and its processing load, ” Network, IEEE Volume: 16 , Issue: 6 , pp. 38 - 44 Nov. -Dec. 2004 • M. Baugher, M. Naslund, E. Carrara, K. Norrman and D. Mc. Grew, “The Secure Real-time Transport Protocol (SRTP), ” Network Working Group , RFC 3711, March 2004. • J. Rosenberg, M. Handley, H. Schulzrinne, E. Schooler And J. Rosenberg, “SIP: Session Initiation Protocol, ” Internet Engineering Task Force, RFC 3261, June 2002. • http: //www. securityfocus. com/infocus/1862, Security. Focus • • Cain & Abel, http: //www. oxid. it/cain. html. 38
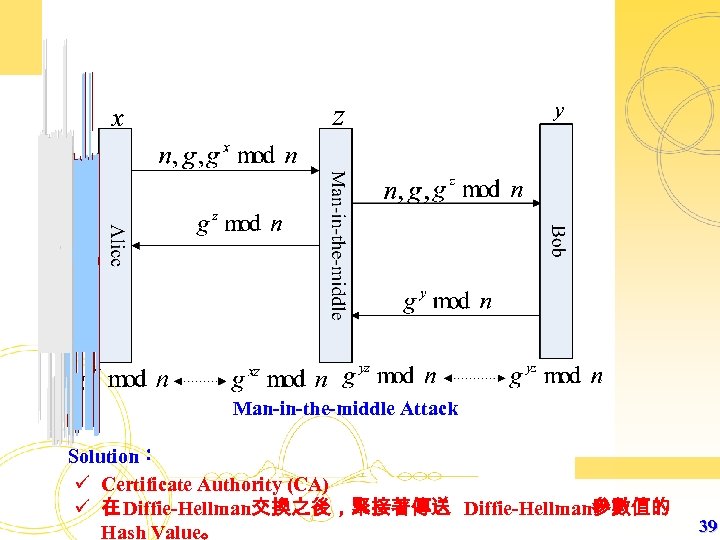 Man-in-the-middle Attack Solution: ü Certificate Authority (CA) ü 在 Diffie-Hellman交換之後,緊接著傳送 Diffie-Hellman參數值的 Hash Value。 39
Man-in-the-middle Attack Solution: ü Certificate Authority (CA) ü 在 Diffie-Hellman交換之後,緊接著傳送 Diffie-Hellman參數值的 Hash Value。 39
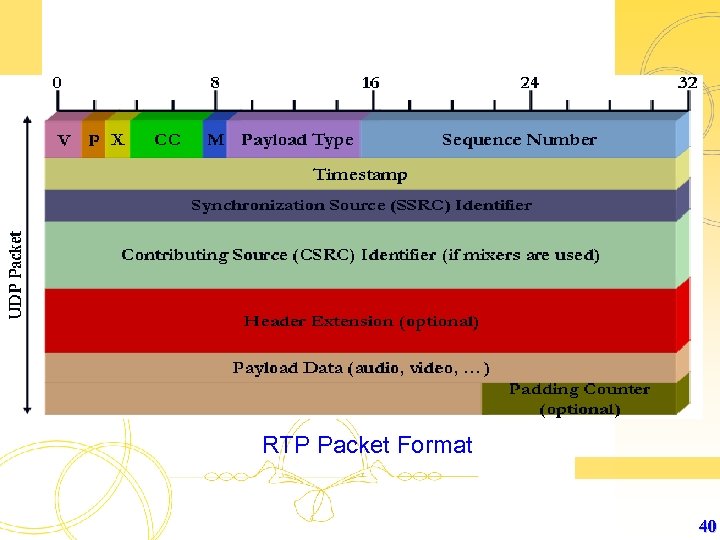 RTP Packet Format 40
RTP Packet Format 40
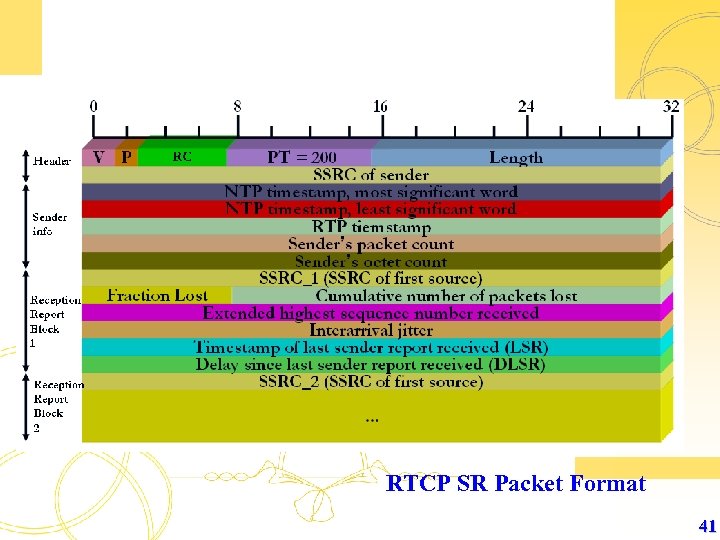 RTCP SR Packet Format 41
RTCP SR Packet Format 41


