fc792a22b7dcf10177f36cad468165c4.ppt
- Количество слайдов: 52
 1 Information Security Chapter 2: Cryptography Lecture #1 -Week 2 Dr. Khalid, Dr. Mohannad CIT 460 Information Security Dr. Khalid, Dr. Mohannad
1 Information Security Chapter 2: Cryptography Lecture #1 -Week 2 Dr. Khalid, Dr. Mohannad CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 2 Outline Basic Cryptographic Terms Historical Background Symmetric Crypto Primitives Asymmetric Crypto Primitives Modes of Operations CIT 460 Information Security Dr. Khalid, Dr. Mohannad
2 Outline Basic Cryptographic Terms Historical Background Symmetric Crypto Primitives Asymmetric Crypto Primitives Modes of Operations CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 3 Basic Terminology plaintext - the original message cipher text - the coded message cipher - algorithm for transforming plaintext to cipher text key - info used in cipher known only to sender/receiver encipher (encrypt) - converting plaintext to cipher text decipher (decrypt) - recovering cipher text from plaintext cryptography - study of encryption principles/methods cryptanalysis (code breaking) - the study of principles/ methods of deciphering cipher text without knowing key cryptology - the field of both cryptography and cryptanalysis CIT 460 Information Security Dr. Khalid, Dr. Mohannad
3 Basic Terminology plaintext - the original message cipher text - the coded message cipher - algorithm for transforming plaintext to cipher text key - info used in cipher known only to sender/receiver encipher (encrypt) - converting plaintext to cipher text decipher (decrypt) - recovering cipher text from plaintext cryptography - study of encryption principles/methods cryptanalysis (code breaking) - the study of principles/ methods of deciphering cipher text without knowing key cryptology - the field of both cryptography and cryptanalysis CIT 460 Information Security Dr. Khalid, Dr. Mohannad
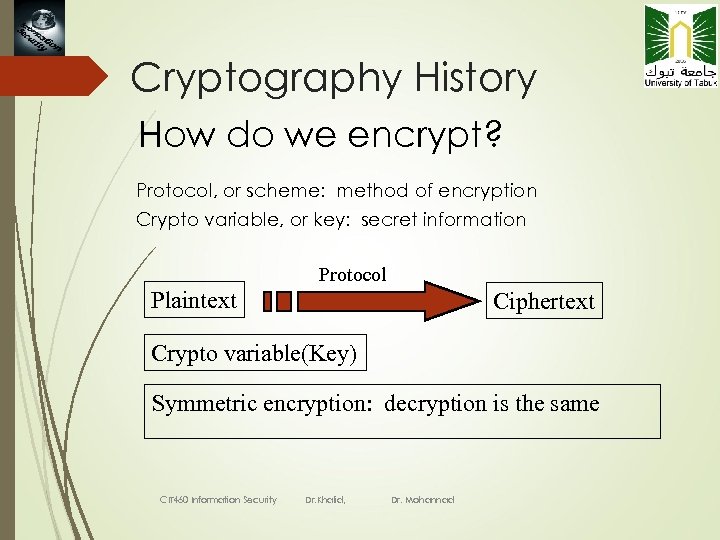 4 Cryptography History How do we encrypt? Protocol, or scheme: method of encryption Crypto variable, or key: secret information Protocol Plaintext Ciphertext Crypto variable(Key) Symmetric encryption: decryption is the same CIT 460 Information Security Dr. Khalid, Dr. Mohannad
4 Cryptography History How do we encrypt? Protocol, or scheme: method of encryption Crypto variable, or key: secret information Protocol Plaintext Ciphertext Crypto variable(Key) Symmetric encryption: decryption is the same CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 5 Transposition Ciphers now consider classical transposition or permutation ciphers these hide the message by rearranging the letter order without altering the actual letters used can recognise these since have the same frequency distribution as the original text CIT 460 Information Security Dr. Khalid, Dr. Mohannad
5 Transposition Ciphers now consider classical transposition or permutation ciphers these hide the message by rearranging the letter order without altering the actual letters used can recognise these since have the same frequency distribution as the original text CIT 460 Information Security Dr. Khalid, Dr. Mohannad
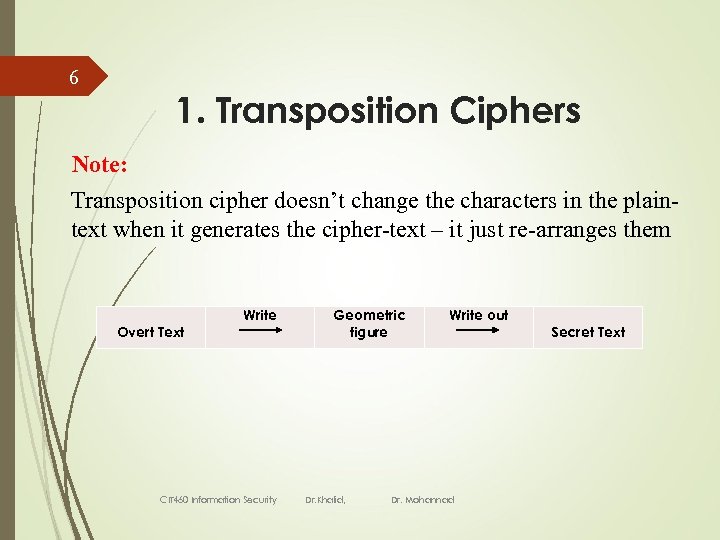 6 1. Transposition Ciphers Note: Transposition cipher doesn’t change the characters in the plaintext when it generates the cipher-text – it just re-arranges them Overt Text Write CIT 460 Information Security Geometric figure Dr. Khalid, Write out Dr. Mohannad Secret Text
6 1. Transposition Ciphers Note: Transposition cipher doesn’t change the characters in the plaintext when it generates the cipher-text – it just re-arranges them Overt Text Write CIT 460 Information Security Geometric figure Dr. Khalid, Write out Dr. Mohannad Secret Text
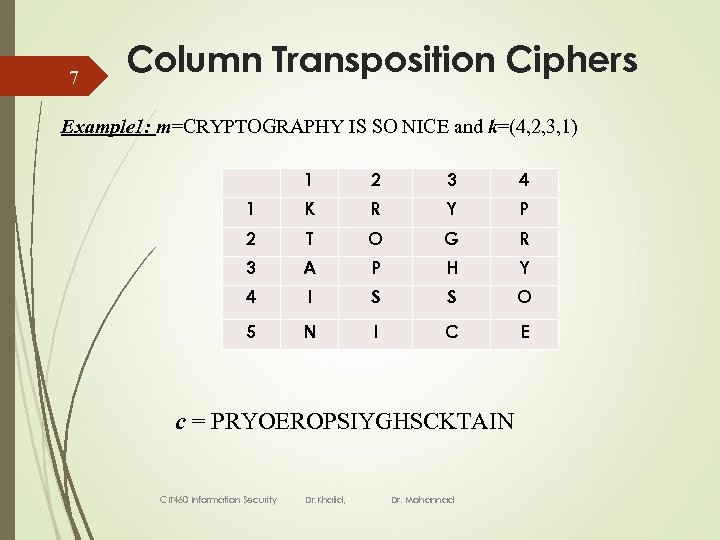 7 Column Transposition Ciphers Example 1: m=CRYPTOGRAPHY IS SO NICE and k=(4, 2, 3, 1) 1 2 3 4 1 K R Y P 2 T O G R 3 A P H Y 4 I S S O 5 N I C E c = PRYOEROPSIYGHSCKTAIN CIT 460 Information Security Dr. Khalid, Dr. Mohannad
7 Column Transposition Ciphers Example 1: m=CRYPTOGRAPHY IS SO NICE and k=(4, 2, 3, 1) 1 2 3 4 1 K R Y P 2 T O G R 3 A P H Y 4 I S S O 5 N I C E c = PRYOEROPSIYGHSCKTAIN CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 8 Algorithm of ciphering: Begin 1. Make a table with four columns and index them in turn from one. 2. Fill every cell in turn with one character for every cell 3. When we finish filling the cells from right to left in one row insert a new one 4. If not end of m go to point 2 5. If there is still any cell empty in the last row fill it with character X. 6. Read in turn by the index given order of the key, which will represent c. End. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
8 Algorithm of ciphering: Begin 1. Make a table with four columns and index them in turn from one. 2. Fill every cell in turn with one character for every cell 3. When we finish filling the cells from right to left in one row insert a new one 4. If not end of m go to point 2 5. If there is still any cell empty in the last row fill it with character X. 6. Read in turn by the index given order of the key, which will represent c. End. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
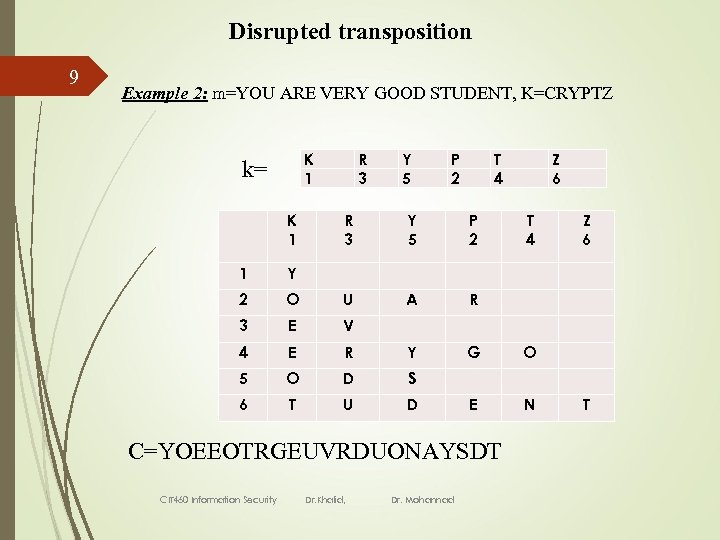 Disrupted transposition 9 Example 2: m=YOU ARE VERY GOOD STUDENT, K=CRYPTZ K 1 k= R 3 Y 5 P 2 T 4 Z 6 K 1 R 3 Y 5 P 2 T 4 Z 6 1 Y 2 O U A R 3 E V 4 E R Y G O 5 O D S 6 T U D E N T C=YOEEOTRGEUVRDUONAYSDT CIT 460 Information Security Dr. Khalid, Dr. Mohannad
Disrupted transposition 9 Example 2: m=YOU ARE VERY GOOD STUDENT, K=CRYPTZ K 1 k= R 3 Y 5 P 2 T 4 Z 6 K 1 R 3 Y 5 P 2 T 4 Z 6 1 Y 2 O U A R 3 E V 4 E R Y G O 5 O D S 6 T U D E N T C=YOEEOTRGEUVRDUONAYSDT CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 10 How to break transposition cipher The only way is trial and error CIT 460 Information Security Dr. Khalid, Dr. Mohannad
10 How to break transposition cipher The only way is trial and error CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 11 2. Substitution Ciphers It is a method of enryption by which units of plaintext are replaced with ciphertext, according to a regular system; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing an inverse substitution CIT 460 Information Security Dr. Khalid, Dr. Mohannad
11 2. Substitution Ciphers It is a method of enryption by which units of plaintext are replaced with ciphertext, according to a regular system; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing an inverse substitution CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 12 2. 1. Monoalphabatic Ciphers Every plaintext character in A is replaced (substituted) by another suitable character from the secret text B. We have to alphabets: a – plaintext, b – secret text and f is unique f : a→b Example 1: A B C D D A G E F G H I J K L CIT 460 Information Security Dr. Khalid, M N O P Q R Dr. Mohannad S T U V W X Y Z
12 2. 1. Monoalphabatic Ciphers Every plaintext character in A is replaced (substituted) by another suitable character from the secret text B. We have to alphabets: a – plaintext, b – secret text and f is unique f : a→b Example 1: A B C D D A G E F G H I J K L CIT 460 Information Security Dr. Khalid, M N O P Q R Dr. Mohannad S T U V W X Y Z
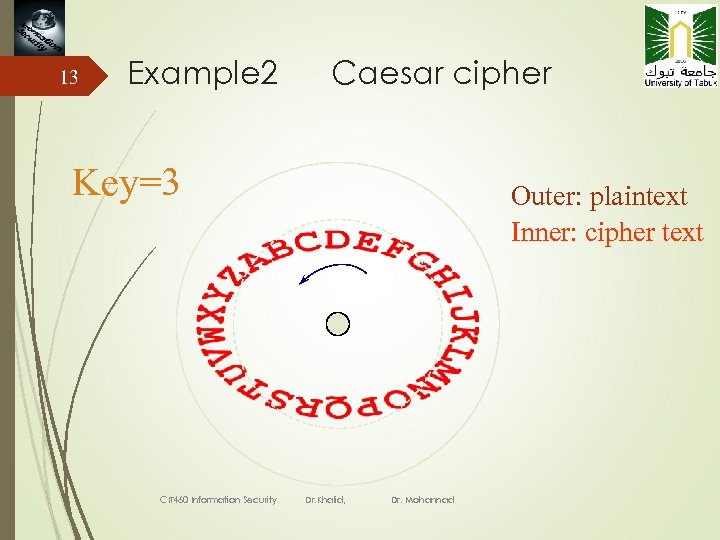 13 Example 2 Caesar cipher Key=3 CIT 460 Information Security Outer: plaintext Inner: cipher text Dr. Khalid, Dr. Mohannad
13 Example 2 Caesar cipher Key=3 CIT 460 Information Security Outer: plaintext Inner: cipher text Dr. Khalid, Dr. Mohannad
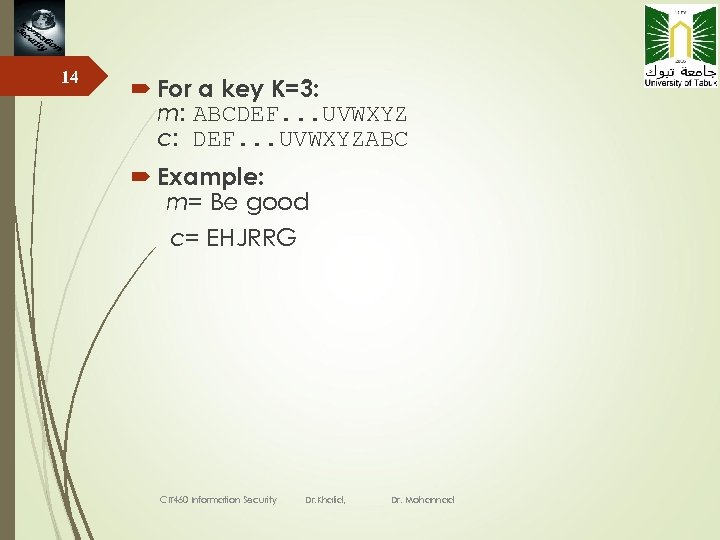 14 For a key K=3: m: ABCDEF. . . UVWXYZ c: DEF. . . UVWXYZABC Example: m= Be good c= EHJRRG CIT 460 Information Security Dr. Khalid, Dr. Mohannad
14 For a key K=3: m: ABCDEF. . . UVWXYZ c: DEF. . . UVWXYZABC Example: m= Be good c= EHJRRG CIT 460 Information Security Dr. Khalid, Dr. Mohannad
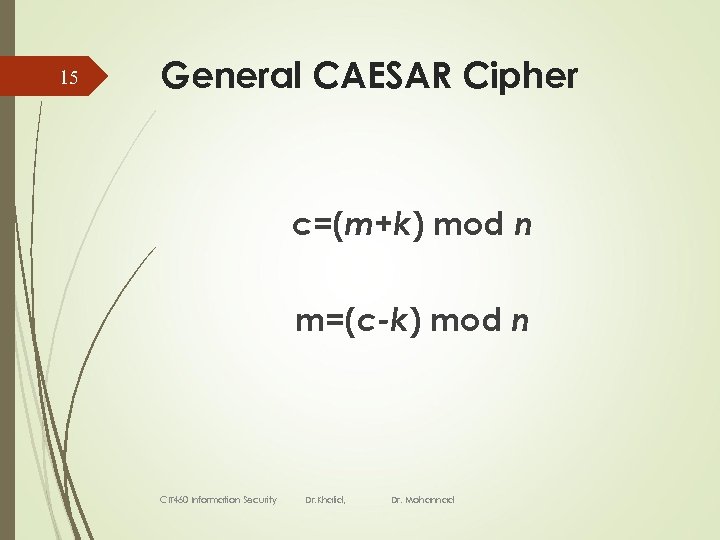 15 General CAESAR Cipher c=(m+k) mod n m=(c-k) mod n CIT 460 Information Security Dr. Khalid, Dr. Mohannad
15 General CAESAR Cipher c=(m+k) mod n m=(c-k) mod n CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 16 How could we break this? Cipher text only attack Caesar: Only 26 possibilities Analysis the occurrence frequency of the alphabet CIT 460 Information Security Dr. Khalid, Dr. Mohannad
16 How could we break this? Cipher text only attack Caesar: Only 26 possibilities Analysis the occurrence frequency of the alphabet CIT 460 Information Security Dr. Khalid, Dr. Mohannad
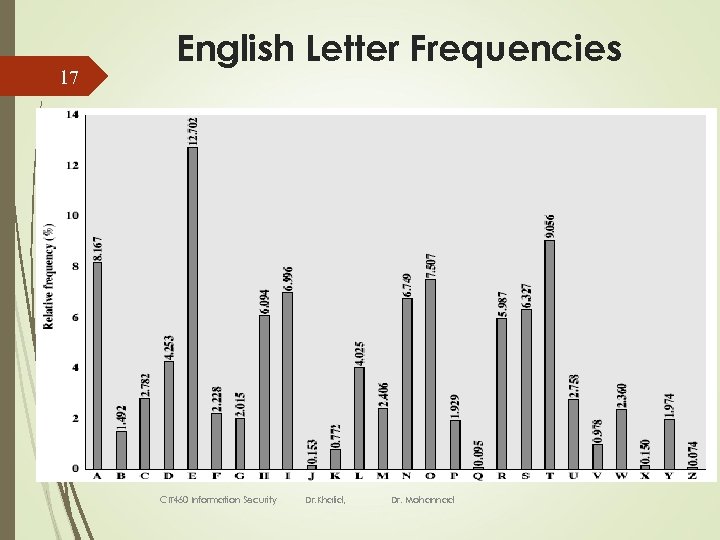 17 English Letter Frequencies CIT 460 Information Security Dr. Khalid, Dr. Mohannad
17 English Letter Frequencies CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 18 2. 1. Homophonic Ciphers Homofon: is a term, which means that it sounds the same like another. A A B C D I F G H ……. SB {$, %} I K L {W, &, 9} 8 7 A …… ……… CIT 460 Information Security f: a → SB Dr. Khalid, Dr. Mohannad
18 2. 1. Homophonic Ciphers Homofon: is a term, which means that it sounds the same like another. A A B C D I F G H ……. SB {$, %} I K L {W, &, 9} 8 7 A …… ……… CIT 460 Information Security f: a → SB Dr. Khalid, Dr. Mohannad
 19 Main characteristics • The letter, which occur much, we give it more number of characters in ciphering. • In this type of ciphers attack by analyzing the occurrence frequency of the alphabet is not a good solution. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
19 Main characteristics • The letter, which occur much, we give it more number of characters in ciphering. • In this type of ciphers attack by analyzing the occurrence frequency of the alphabet is not a good solution. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 20 2. 3. Polyalphabetical Ciphers In this kind of ciphering, every plaintext a is convert into many secret alphabets b 1, b 2, …. fi : a → B i Where i=1, 2, 3, … Special case of this kind of ciphers is Polyalphabetical cipher with period p: fi : a → Bi Where i=1, 2, 3, …, p p- is the period of cipher. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
20 2. 3. Polyalphabetical Ciphers In this kind of ciphering, every plaintext a is convert into many secret alphabets b 1, b 2, …. fi : a → B i Where i=1, 2, 3, … Special case of this kind of ciphers is Polyalphabetical cipher with period p: fi : a → Bi Where i=1, 2, 3, …, p p- is the period of cipher. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 21 Attention: When p=1 then we got monoalphabatic cipher. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
21 Attention: When p=1 then we got monoalphabatic cipher. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 22 Vigenere cipher c=(m+ki) mod n m=(c-ki) mod n A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 CIT 460 Information Security Dr. Khalid, Dr. Mohannad
22 Vigenere cipher c=(m+ki) mod n m=(c-ki) mod n A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 Example 1: 23 If we have n=26, and k=HOST, cipher the following “ I AM GOING HOME”: m= I A M G O I k= H O S N G H O M E T H O S T c= P O E Z V W F Z O C E Y CIT 460 Information Security Dr. Khalid, Dr. Mohannad
Example 1: 23 If we have n=26, and k=HOST, cipher the following “ I AM GOING HOME”: m= I A M G O I k= H O S N G H O M E T H O S T c= P O E Z V W F Z O C E Y CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 How to break Vigenere Cipher 24 Vigenere cipher is resistance against frequency attack Kasiski method: which give the period of the cipher, usually repeat oneself the period p or the multi of it. index of coincidence: it specifies the probability of occurring in the secret text at least two same letters CIT 460 Information Security Dr. Khalid, Dr. Mohannad
How to break Vigenere Cipher 24 Vigenere cipher is resistance against frequency attack Kasiski method: which give the period of the cipher, usually repeat oneself the period p or the multi of it. index of coincidence: it specifies the probability of occurring in the secret text at least two same letters CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 2. 4 Polylitters Ciphers 25 All the ciphers before convert only individual characters of the known alphabet. In polylitters ciphers we convert more than one character in same time. This kind of ciphering hides the litters occurrence frequency that makes crypto analyzing very hard. Playfair cipher and Hill cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad
2. 4 Polylitters Ciphers 25 All the ciphers before convert only individual characters of the known alphabet. In polylitters ciphers we convert more than one character in same time. This kind of ciphering hides the litters occurrence frequency that makes crypto analyzing very hard. Playfair cipher and Hill cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 26 Information Security Chapter 2: Cryptography Lecture #2 -Week 2 Dr. Khalid , Dr. Mohannad CIT 460 Information Security Dr. Khalid, Dr. Mohannad
26 Information Security Chapter 2: Cryptography Lecture #2 -Week 2 Dr. Khalid , Dr. Mohannad CIT 460 Information Security Dr. Khalid, Dr. Mohannad
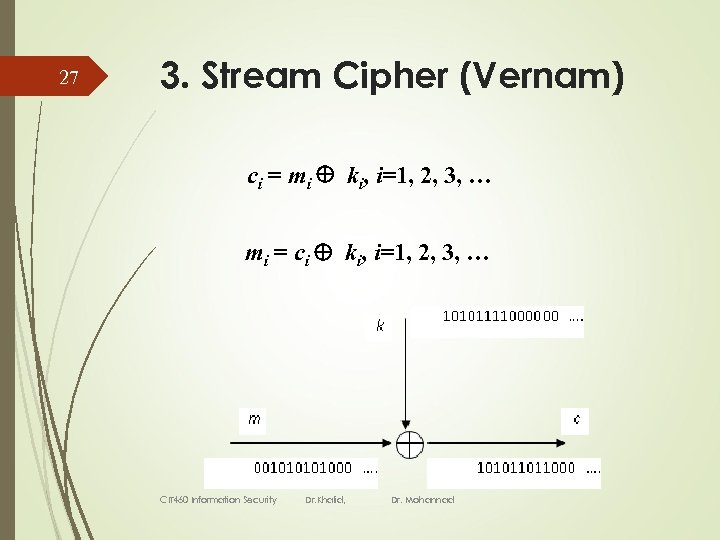 27 3. Stream Cipher (Vernam) ci = mi ki, i=1, 2, 3, … mi = ci ki, i=1, 2, 3, … CIT 460 Information Security Dr. Khalid, Dr. Mohannad
27 3. Stream Cipher (Vernam) ci = mi ki, i=1, 2, 3, … mi = ci ki, i=1, 2, 3, … CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 28 The perfect cryptosystem One-time pad: encrypt each letter with its own key Key length equal to message length Random key CIT 460 Information Security Dr. Khalid, Dr. Mohannad
28 The perfect cryptosystem One-time pad: encrypt each letter with its own key Key length equal to message length Random key CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 29 4. Product Ciphers A product cipher E is a composition of t functions (ciphers) F 1, … , Ft where each Fi may be a substitution or transposition And they use modular arithmetic. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
29 4. Product Ciphers A product cipher E is a composition of t functions (ciphers) F 1, … , Ft where each Fi may be a substitution or transposition And they use modular arithmetic. CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 30 Examples: Rotor machine ENIGMA DES, 3 DES AES Modern Symmetric Ciphers BLOWFISH FEAL IDEA RC 5 SAFER CIT 460 Information Security Dr. Khalid, Dr. Mohannad
30 Examples: Rotor machine ENIGMA DES, 3 DES AES Modern Symmetric Ciphers BLOWFISH FEAL IDEA RC 5 SAFER CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 31 Enigma Machine German cryptosystem in World War II Same idea: modify letters Scrambler disks implement permutation Rotate after each letter, so many different permutations used Additional permutation provided by plugboard CIT 460 Information Security Dr. Khalid, Dr. Mohannad
31 Enigma Machine German cryptosystem in World War II Same idea: modify letters Scrambler disks implement permutation Rotate after each letter, so many different permutations used Additional permutation provided by plugboard CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 32 Enigma Machine-WWII CIT 460 Information Security Dr. Khalid, Dr. Mohannad
32 Enigma Machine-WWII CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 33 Modern Symmetric Cryptography Assume the protocol is known to the enemy Only the key is secret Encryption, cryptanalysis use computers Operate on bits, rather than letters DES, AES Open standards; let everyone try to break it Closed design often fails (cell phones) Don’t try this in-house CIT 460 Information Security Dr. Khalid, Dr. Mohannad
33 Modern Symmetric Cryptography Assume the protocol is known to the enemy Only the key is secret Encryption, cryptanalysis use computers Operate on bits, rather than letters DES, AES Open standards; let everyone try to break it Closed design often fails (cell phones) Don’t try this in-house CIT 460 Information Security Dr. Khalid, Dr. Mohannad
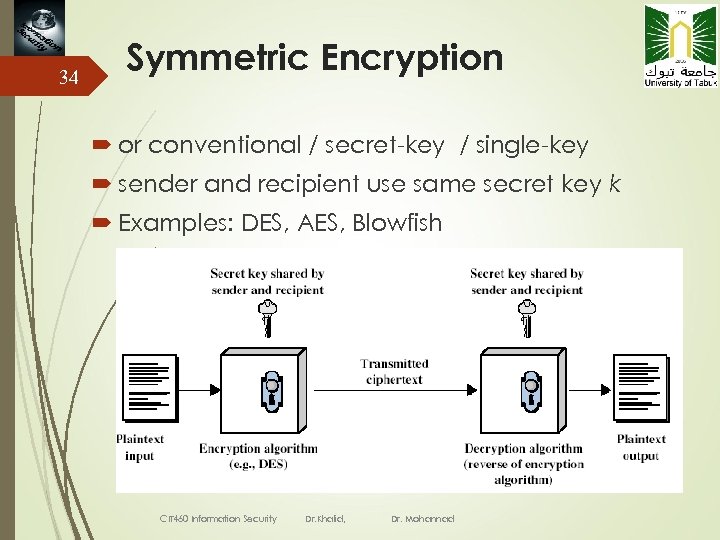 34 Symmetric Encryption or conventional / secret-key / single-key sender and recipient use same secret key k Examples: DES, AES, Blowfish CIT 460 Information Security Dr. Khalid, Dr. Mohannad
34 Symmetric Encryption or conventional / secret-key / single-key sender and recipient use same secret key k Examples: DES, AES, Blowfish CIT 460 Information Security Dr. Khalid, Dr. Mohannad
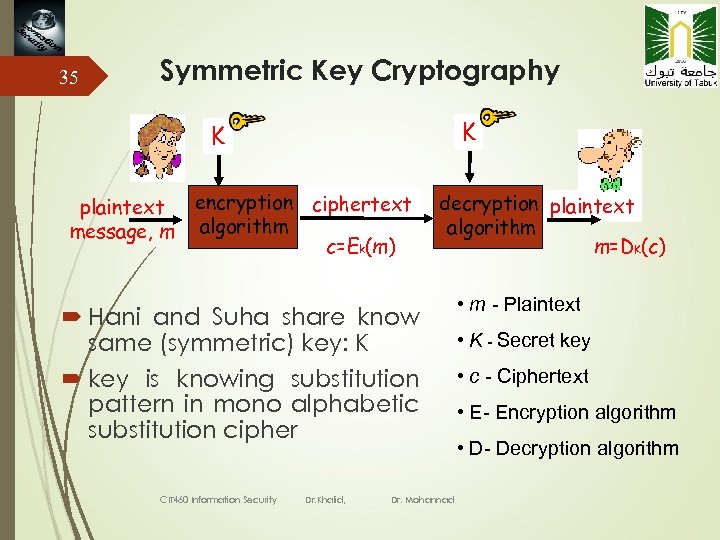 35 Symmetric Key Cryptography K K plaintext message, m encryption ciphertext algorithm c=Ek(m) decryption plaintext algorithm m=DK(c) Hani and Suha share know same (symmetric) key: K key is knowing substitution pattern in mono alphabetic substitution cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad • m - Plaintext • K - Secret key • c - Ciphertext • E- Encryption algorithm • D- Decryption algorithm
35 Symmetric Key Cryptography K K plaintext message, m encryption ciphertext algorithm c=Ek(m) decryption plaintext algorithm m=DK(c) Hani and Suha share know same (symmetric) key: K key is knowing substitution pattern in mono alphabetic substitution cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad • m - Plaintext • K - Secret key • c - Ciphertext • E- Encryption algorithm • D- Decryption algorithm
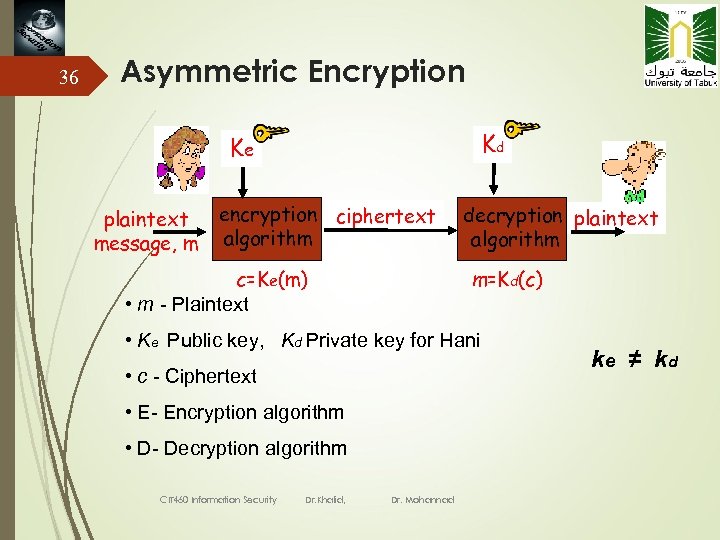 36 Asymmetric Encryption Kd Ke plaintext message, m encryption ciphertext algorithm c=Ke(m) • m - Plaintext decryption plaintext algorithm m=Kd(c) • Ke Public key, Kd Private key for Hani • c - Ciphertext • E- Encryption algorithm • D- Decryption algorithm CIT 460 Information Security Dr. Khalid, Dr. Mohannad ke ≠ kd
36 Asymmetric Encryption Kd Ke plaintext message, m encryption ciphertext algorithm c=Ke(m) • m - Plaintext decryption plaintext algorithm m=Kd(c) • Ke Public key, Kd Private key for Hani • c - Ciphertext • E- Encryption algorithm • D- Decryption algorithm CIT 460 Information Security Dr. Khalid, Dr. Mohannad ke ≠ kd
 37 Requirements two requirements for secure use of symmetric encryption: a strong encryption algorithm a secret key known only to sender / receiver Y = EK(X) X = DK(Y) assume encryption algorithm is known implies a secure channel to distribute key CIT 460 Information Security Dr. Khalid, Dr. Mohannad
37 Requirements two requirements for secure use of symmetric encryption: a strong encryption algorithm a secret key known only to sender / receiver Y = EK(X) X = DK(Y) assume encryption algorithm is known implies a secure channel to distribute key CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 38 Types of cryptanalysis Attacks ciphertext only know algorithm / ciphertext, statistical, can identify plaintext known plaintext know/suspect plaintext & ciphertext to attack cipher chosen plaintext select plaintext and obtain ciphertext to attack cipher chosen ciphertext select ciphertext and obtain plaintext to attack cipher chosen text select either plaintext or ciphertext to en/decrypt to attack cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad
38 Types of cryptanalysis Attacks ciphertext only know algorithm / ciphertext, statistical, can identify plaintext known plaintext know/suspect plaintext & ciphertext to attack cipher chosen plaintext select plaintext and obtain ciphertext to attack cipher chosen ciphertext select ciphertext and obtain plaintext to attack cipher chosen text select either plaintext or ciphertext to en/decrypt to attack cipher CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 39 Types of attacks Cipher text only attack the only data available is a target cipher text Known plaintext attack a target cipher text pairs of other cipher text and plaintext (say, previously broken or guessing) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
39 Types of attacks Cipher text only attack the only data available is a target cipher text Known plaintext attack a target cipher text pairs of other cipher text and plaintext (say, previously broken or guessing) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 40 Types of attacks Chosen plaintext attacks a target cipher text can feed encryption algorithm with plaintexts and obtain the matching cipher texts Chosen cipher text attack a target cipher text can feed decryption algorithm with cipher texts and obtain the matching plaintexts CIT 460 Information Security Dr. Khalid, Dr. Mohannad
40 Types of attacks Chosen plaintext attacks a target cipher text can feed encryption algorithm with plaintexts and obtain the matching cipher texts Chosen cipher text attack a target cipher text can feed decryption algorithm with cipher texts and obtain the matching plaintexts CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 41 Brute Force Search always possible to simply try every key most basic attack, proportional to key size assume either know / recognise plaintext CIT 460 Information Security Dr. Khalid, Dr. Mohannad
41 Brute Force Search always possible to simply try every key most basic attack, proportional to key size assume either know / recognise plaintext CIT 460 Information Security Dr. Khalid, Dr. Mohannad
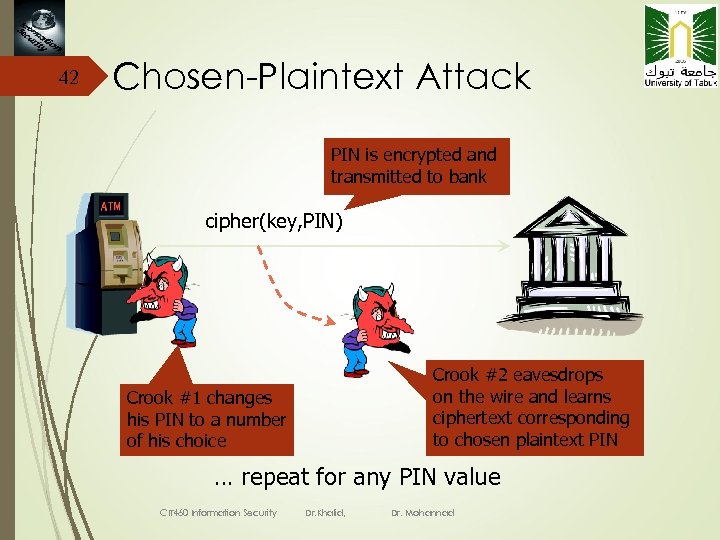 42 Chosen-Plaintext Attack PIN is encrypted and transmitted to bank cipher(key, PIN) Crook #2 eavesdrops on the wire and learns ciphertext corresponding to chosen plaintext PIN Crook #1 changes his PIN to a number of his choice … repeat for any PIN value CIT 460 Information Security Dr. Khalid, Dr. Mohannad
42 Chosen-Plaintext Attack PIN is encrypted and transmitted to bank cipher(key, PIN) Crook #2 eavesdrops on the wire and learns ciphertext corresponding to chosen plaintext PIN Crook #1 changes his PIN to a number of his choice … repeat for any PIN value CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 43 Information Security Chapter 2: Cryptography Lecture #3 -Week 2 Dr. Khalid , Dr. Mohannad CIT 460 Information Security Dr. Khalid M. O Nahar
43 Information Security Chapter 2: Cryptography Lecture #3 -Week 2 Dr. Khalid , Dr. Mohannad CIT 460 Information Security Dr. Khalid M. O Nahar
 44 Product Ciphers ciphers using substitutions or transpositions are not secure because of language characteristics hence consider using several ciphers in succession to make harder, but: two substitutions make a more complex substitution two transpositions make more complex transposition but a substitution followed by a transposition makes a new much harder cipher this is bridge from classical to modern ciphers CIT 460 Information Security Dr. Khalid, Dr. Mohannad
44 Product Ciphers ciphers using substitutions or transpositions are not secure because of language characteristics hence consider using several ciphers in succession to make harder, but: two substitutions make a more complex substitution two transpositions make more complex transposition but a substitution followed by a transposition makes a new much harder cipher this is bridge from classical to modern ciphers CIT 460 Information Security Dr. Khalid, Dr. Mohannad
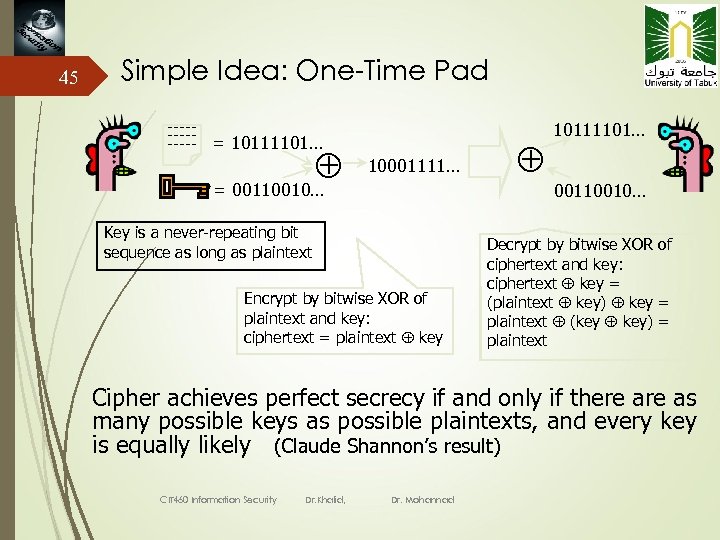 45 Simple Idea: One-Time Pad ------- = 10111101… 10001111… = 00110010… Key is a never-repeating bit sequence as long as plaintext Encrypt by bitwise XOR of plaintext and key: ciphertext = plaintext key 10111101… 00110010… Decrypt by bitwise XOR of ciphertext and key: ciphertext key = (plaintext key) key = plaintext (key key) = plaintext Cipher achieves perfect secrecy if and only if there as many possible keys as possible plaintexts, and every key is equally likely (Claude Shannon’s result) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
45 Simple Idea: One-Time Pad ------- = 10111101… 10001111… = 00110010… Key is a never-repeating bit sequence as long as plaintext Encrypt by bitwise XOR of plaintext and key: ciphertext = plaintext key 10111101… 00110010… Decrypt by bitwise XOR of ciphertext and key: ciphertext key = (plaintext key) key = plaintext (key key) = plaintext Cipher achieves perfect secrecy if and only if there as many possible keys as possible plaintexts, and every key is equally likely (Claude Shannon’s result) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 46 Advantages of One-Time Pad Easy to compute Encryption and decryption are the same operation Bitwise XOR is very cheap to compute As secure as possible Given a cipher text, all plaintexts are equally likely, regardless of attacker’s computational resources …as long as the key sequence is truly random True randomness is expensive to obtain in large quantities …as long as each key is same length as plaintext But how does the sender communicate the key to receiver? CIT 460 Information Security Dr. Khalid, Dr. Mohannad
46 Advantages of One-Time Pad Easy to compute Encryption and decryption are the same operation Bitwise XOR is very cheap to compute As secure as possible Given a cipher text, all plaintexts are equally likely, regardless of attacker’s computational resources …as long as the key sequence is truly random True randomness is expensive to obtain in large quantities …as long as each key is same length as plaintext But how does the sender communicate the key to receiver? CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 47 Problems with One-Time Pad Key must be as long as plaintext Impractical in most realistic scenarios Still used for diplomatic and intelligence traffic Does not guarantee integrity One-time pad only guarantees confidentiality Attacker cannot recover plaintext, but can easily change it to something else Insecure if keys are reused Attacker can obtain XOR of plaintexts CIT 460 Information Security Dr. Khalid, Dr. Mohannad
47 Problems with One-Time Pad Key must be as long as plaintext Impractical in most realistic scenarios Still used for diplomatic and intelligence traffic Does not guarantee integrity One-time pad only guarantees confidentiality Attacker cannot recover plaintext, but can easily change it to something else Insecure if keys are reused Attacker can obtain XOR of plaintexts CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 48 Modern Block Ciphers will now look at modern block ciphers one of the most widely used types of cryptographic algorithms provide secrecy and/or authentication services in particular will introduce DES (Data Encryption Standard) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
48 Modern Block Ciphers will now look at modern block ciphers one of the most widely used types of cryptographic algorithms provide secrecy and/or authentication services in particular will introduce DES (Data Encryption Standard) CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 49 Block vs Stream Ciphers block ciphers process messages into blocks, each of which is then en/decrypted like a substitution on very big characters 64 -bits or more stream ciphers process messages a bit or byte at a time when en/decrypting many current ciphers are block ciphers hence are focus of course CIT 460 Information Security Dr. Khalid, Dr. Mohannad
49 Block vs Stream Ciphers block ciphers process messages into blocks, each of which is then en/decrypted like a substitution on very big characters 64 -bits or more stream ciphers process messages a bit or byte at a time when en/decrypting many current ciphers are block ciphers hence are focus of course CIT 460 Information Security Dr. Khalid, Dr. Mohannad
 50 Block Ciphers Operates on a single chunk (“block”) of plaintext For example, 64 bits for DES Same key is reused for each block (can use short keys) Result should look like a random permutation As if plaintext bits were randomly shuffled Only computational guarantee of secrecy Not impossible to break, just very expensive If there is no efficient algorithm (unproven assumption!), then can only break by brute-force, try-every-possible-key search Time/cost of breaking the cipher exceeds the value and/or useful lifetime of protected information CIT 460 Information Security Dr. Khalid, Dr. Mohannad
50 Block Ciphers Operates on a single chunk (“block”) of plaintext For example, 64 bits for DES Same key is reused for each block (can use short keys) Result should look like a random permutation As if plaintext bits were randomly shuffled Only computational guarantee of secrecy Not impossible to break, just very expensive If there is no efficient algorithm (unproven assumption!), then can only break by brute-force, try-every-possible-key search Time/cost of breaking the cipher exceeds the value and/or useful lifetime of protected information CIT 460 Information Security Dr. Khalid, Dr. Mohannad
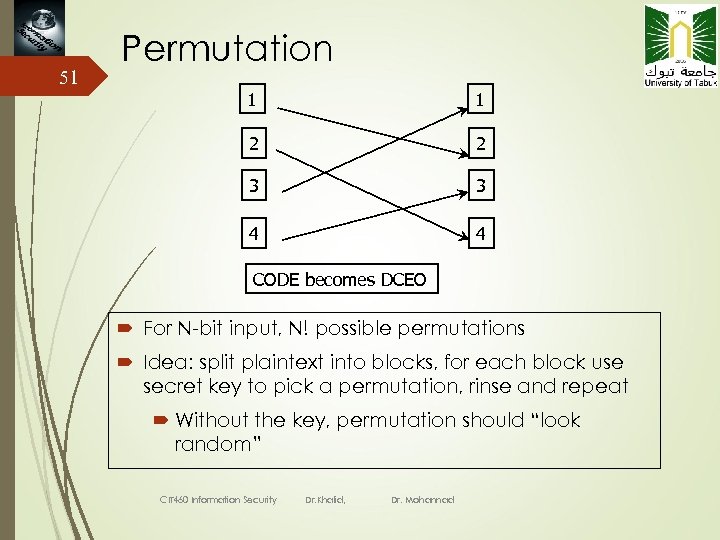 51 Permutation 1 1 2 2 3 3 4 4 CODE becomes DCEO For N-bit input, N! possible permutations Idea: split plaintext into blocks, for each block use secret key to pick a permutation, rinse and repeat Without the key, permutation should “look random” CIT 460 Information Security Dr. Khalid, Dr. Mohannad
51 Permutation 1 1 2 2 3 3 4 4 CODE becomes DCEO For N-bit input, N! possible permutations Idea: split plaintext into blocks, for each block use secret key to pick a permutation, rinse and repeat Without the key, permutation should “look random” CIT 460 Information Security Dr. Khalid, Dr. Mohannad
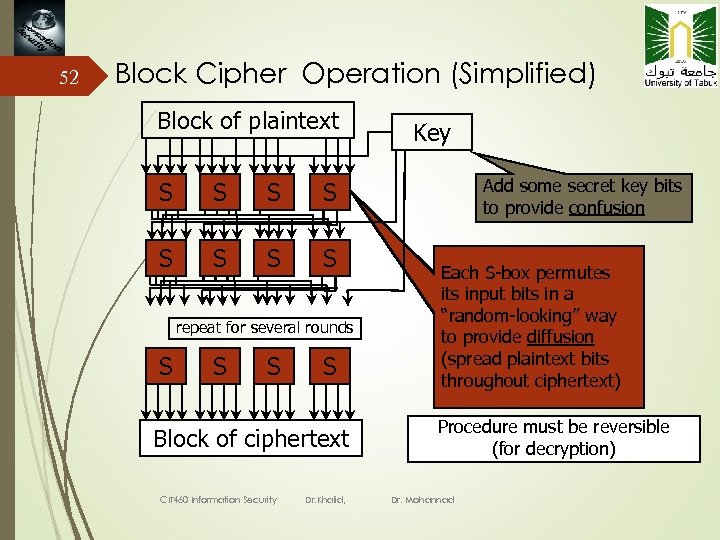 52 Block Cipher Operation (Simplified) Block of plaintext S S S Add some secret key bits to provide confusion S S Key repeat for several rounds S S Block of ciphertext CIT 460 Information Security Dr. Khalid, Each S-box permutes its input bits in a “random-looking” way to provide diffusion (spread plaintext bits throughout ciphertext) Procedure must be reversible (for decryption) Dr. Mohannad
52 Block Cipher Operation (Simplified) Block of plaintext S S S Add some secret key bits to provide confusion S S Key repeat for several rounds S S Block of ciphertext CIT 460 Information Security Dr. Khalid, Each S-box permutes its input bits in a “random-looking” way to provide diffusion (spread plaintext bits throughout ciphertext) Procedure must be reversible (for decryption) Dr. Mohannad


