b62479e83fafa050b6cf987c0ea267b3.ppt
- Количество слайдов: 82

1 F 5 Application Traffic Management Radovan Gibala Senior Solutions Architect r. gibala@f 5. com +420 731 137 223 2009
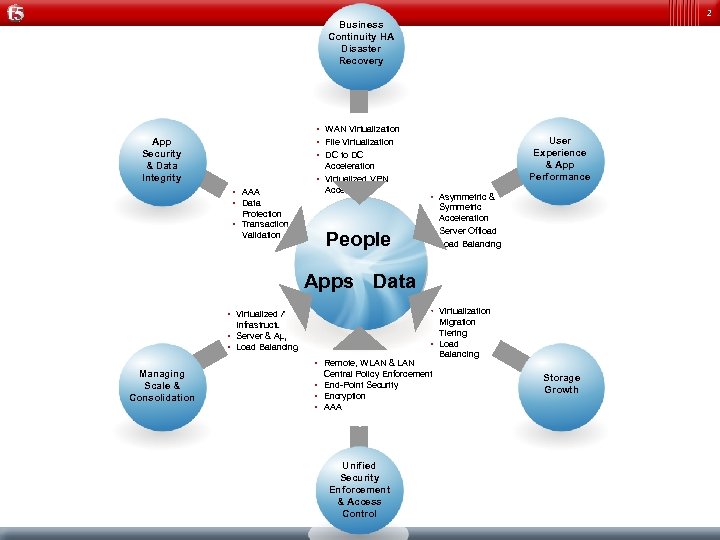
2 Business Continuity HA Disaster Recovery • WAN Virtualization • File Virtualization • DC to DC App Security & Data Integrity User Experience & App Performance Acceleration • Virtualized VPN Access • AAA • Data Protection • Transaction Validation People • Asymmetric & Symmetric Acceleration • Server Offload • Load Balancing Apps Data • Virtualized App & Infrastructure • Server & App Offload • Load Balancing Managing Scale & Consolidation • • • Remote, WLAN & LAN Central Policy Enforcement • End-Point Security • Encryption • AAA Unified Security Enforcement & Access Control Virtualization Migration Tiering Load Balancing Storage Growth
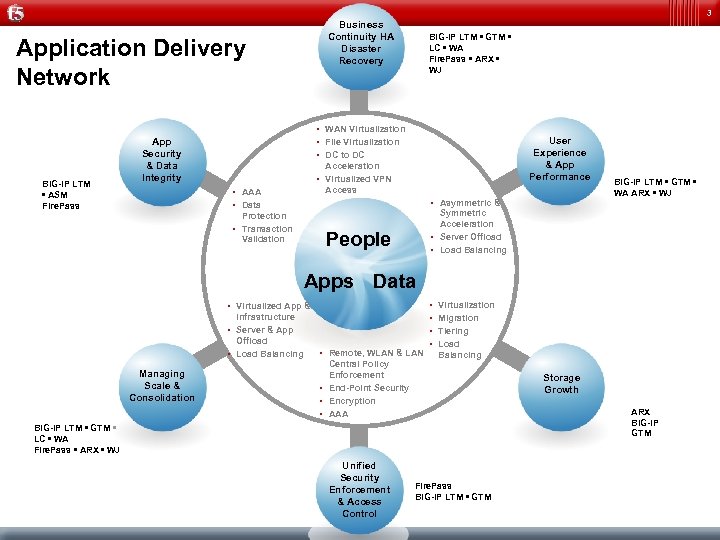
3 Business Continuity HA Disaster Recovery Application Delivery Network BIG-IP LTM • ASM Fire. Pass BIG-IP LTM • GTM • LC • WA Fire. Pass • ARX • WJ • WAN Virtualization • File Virtualization • DC to DC App Security & Data Integrity User Experience & App Performance Acceleration • Virtualized VPN Access • AAA • Data • Asymmetric & Protection • Transaction Validation BIG-IP LTM • GTM • WA ARX • WJ Symmetric Acceleration • Server Offload • Load Balancing People Apps Data • Virtualized App & Infrastructure • Server & App Offload • Load Balancing Managing Scale & Consolidation • Remote, WLAN & LAN Central Policy Enforcement • End-Point Security • Encryption • AAA • • Virtualization Migration Tiering Load Balancing Storage Growth ARX BIG-IP GTM BIG-IP LTM • GTM • LC • WA Fire. Pass • ARX • WJ Unified Security Enforcement & Access Control Fire. Pass BIG-IP LTM • GTM
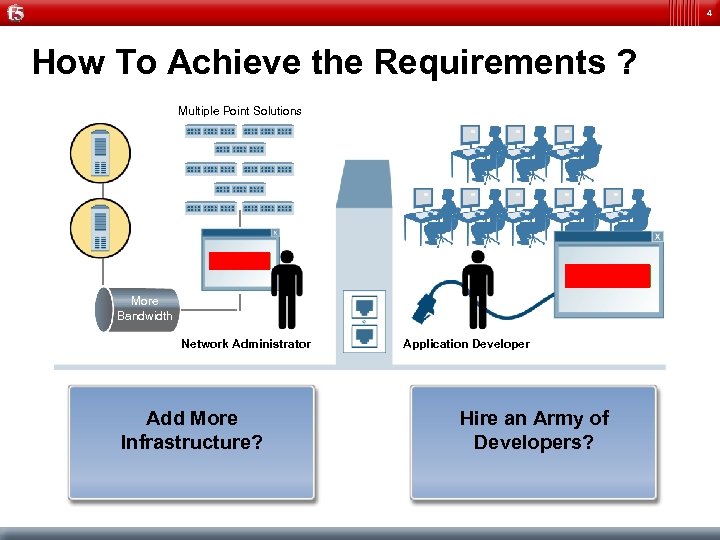
4 How To Achieve the Requirements ? Multiple Point Solutions Application More Bandwidth Network Administrator Add More Infrastructure? Application Developer Hire an Army of Developers?
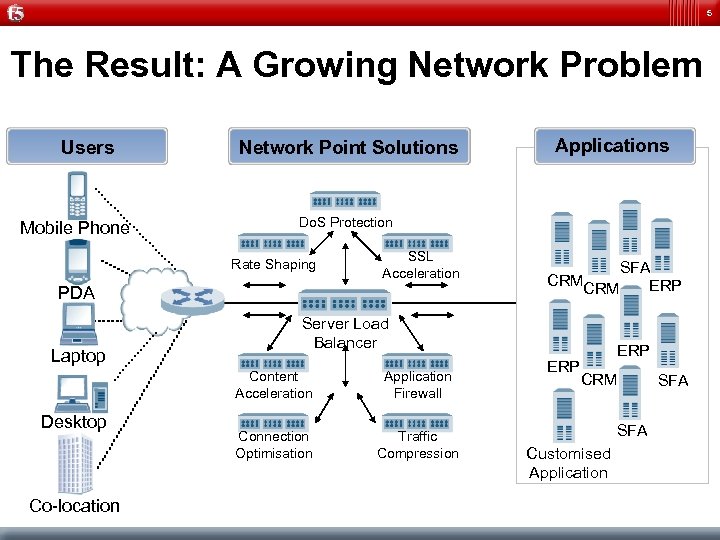
5 The Result: A Growing Network Problem Users Mobile Phone Network Point Solutions Do. S Protection Rate Shaping SSL Acceleration PDA Laptop Co-location SFA CRMCRM ERP Server Load Balancer Content Acceleration Desktop Applications Application Firewall Connection Optimisation Traffic Compression ERP CRM SFA Customised Application SFA
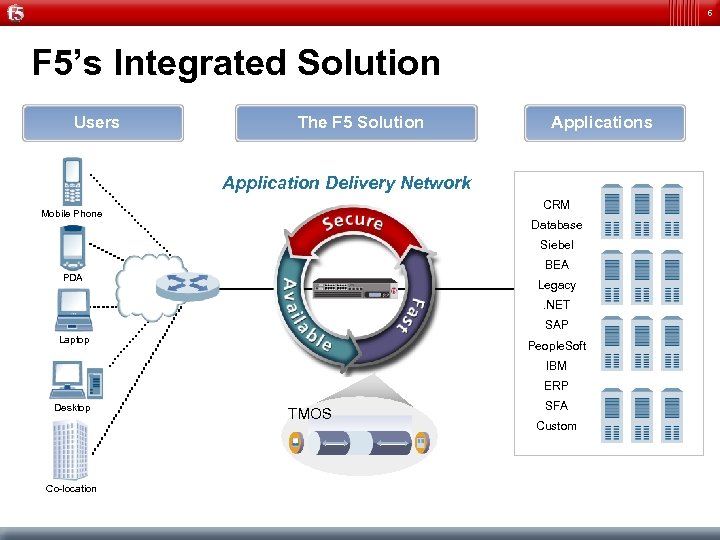
6 F 5’s Integrated Solution Users The F 5 Solution Applications Application Delivery Network CRM Mobile Phone Database Siebel BEA PDA Legacy. NET SAP Laptop People. Soft IBM ERP Desktop Co-location TMOS SFA Custom
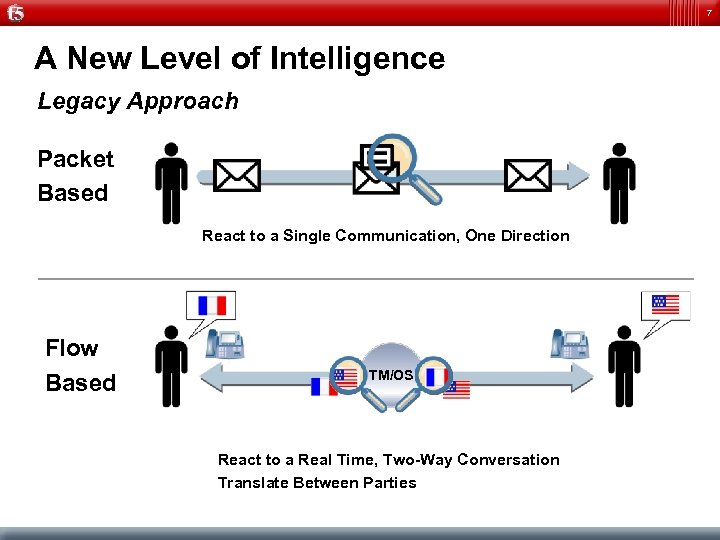
7 A New Level of Intelligence Legacy Approach Packet Based React to a Single Communication, One Direction Flow Based TM/OS React to a Real Time, Two-Way Conversation Translate Between Parties
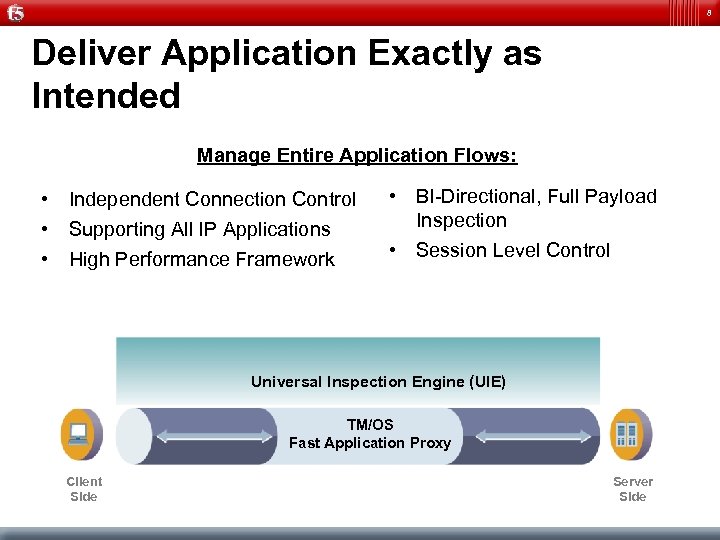
8 Deliver Application Exactly as Intended Manage Entire Application Flows: • Independent Connection Control • Supporting All IP Applications • High Performance Framework • BI-Directional, Full Payload Inspection • Session Level Control Universal Inspection Engine (UIE) TM/OS Fast Application Proxy Client Side Server Side
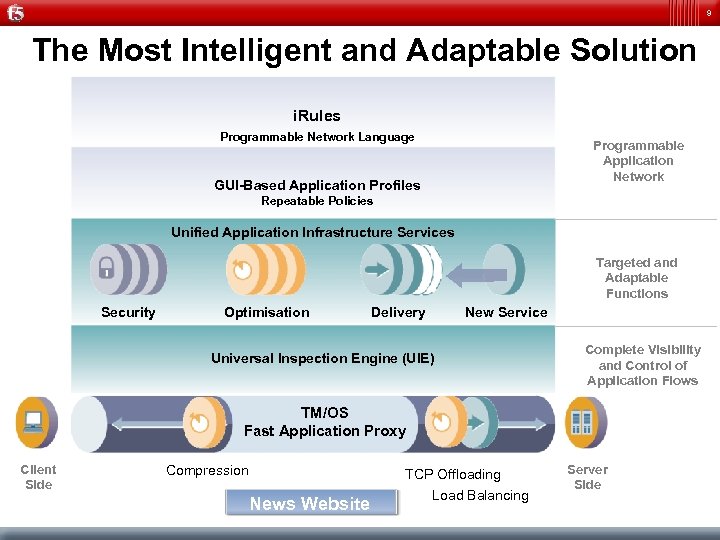
9 The Most Intelligent and Adaptable Solution i. Rules Programmable Network Language Programmable Application Network GUI-Based Application Profiles Repeatable Policies Unified Application Infrastructure Services Targeted and Adaptable Functions Security Optimisation Delivery New Service Universal Inspection Engine (UIE) Complete Visibility and Control of Application Flows TM/OS Fast Application Proxy Client Side Compression TCP Offloading News Website Load Balancing Server Side
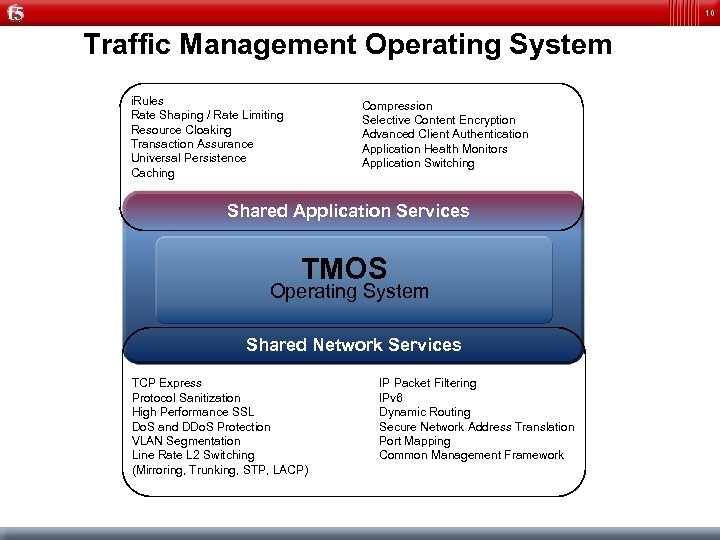
10 Traffic Management Operating System i. Rules Rate Shaping / Rate Limiting Resource Cloaking Transaction Assurance Universal Persistence Caching Compression Selective Content Encryption Advanced Client Authentication Application Health Monitors Application Switching Shared Application Services TMOS Operating System Shared Network Services TCP Express Protocol Sanitization High Performance SSL Do. S and DDo. S Protection VLAN Segmentation Line Rate L 2 Switching (Mirroring, Trunking, STP, LACP) IP Packet Filtering IPv 6 Dynamic Routing Secure Network Address Translation Port Mapping Common Management Framework
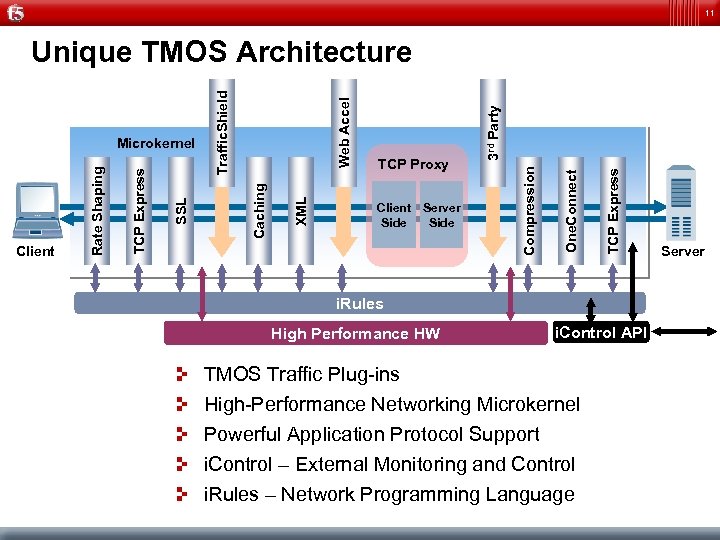
11 TCP Express Server Side One. Connect Client Side Compression TCP Proxy 3 rd Party Web Accel XML Caching SSL TCP Express Client Rate Shaping Microkernel Traffic. Shield Unique TMOS Architecture i. Rules High Performance HW i. Control API TMOS Traffic Plug-ins High-Performance Networking Microkernel Powerful Application Protocol Support i. Control – External Monitoring and Control i. Rules – Network Programming Language Server
12 BIG-IP
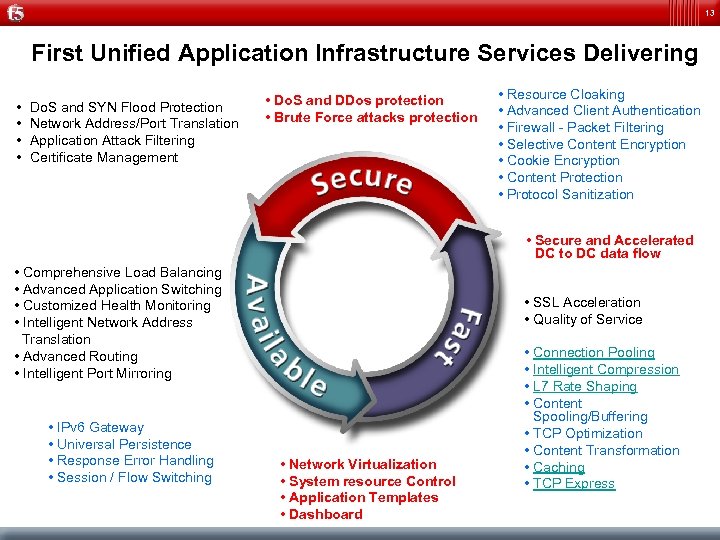
13 First Unified Application Infrastructure Services Delivering • • Do. S and SYN Flood Protection Network Address/Port Translation Application Attack Filtering Certificate Management • Do. S and DDos protection • Brute Force attacks protection • Resource Cloaking • Advanced Client Authentication • Firewall - Packet Filtering • Selective Content Encryption • Cookie Encryption • Content Protection • Protocol Sanitization • Secure and Accelerated DC to DC data flow • Comprehensive Load Balancing • Advanced Application Switching • Customized Health Monitoring • Intelligent Network Address Translation • Advanced Routing • Intelligent Port Mirroring • IPv 6 Gateway • Universal Persistence • Response Error Handling • Session / Flow Switching • SSL Acceleration • Quality of Service • Network Virtualization • System resource Control • Application Templates • Dashboard • Connection Pooling • Intelligent Compression • L 7 Rate Shaping • Content Spooling/Buffering • TCP Optimization • Content Transformation • Caching • TCP Express
14 Comprehensive Load Balancing Static – Round. Robin – Ratio Dynamic – – – Fastest Least. Connections Observed Predictive Dynamic Ratio Priority Groups

15 Feature Overview/BIG-IP Availability Checking • Check any back-end process using EAV • Will work for any IP based application • Stateful failover between devices Security • Firewall-like device to resist most attacks • All administration is encrypted • Integrated SSL/FIPS and secure NAT
16 Feature Overview/BIG-IP SSL and E-Commerce • Only product with integrated SSL • Single certificate simplifies administration • Lowers certificate costs • Client certificate checking (Authentication) Layer 7 Functionality • Can utilize all HTTP header/content or TCP content in traffic decisions • Can persist on anything • HTTP 1. 1 keep-alives dramatically improve performance
17 Feature Overview/BIG-IP Easy to Implement and Support • Can be deployed as either Layer 2 or 3 device • Simple and complete Graphical User Interface • Installation services by F 5 and/or partner Flexibility • BIG-IP works with any server or IP based service • i. Control enables integration with internal and/or 3 rd party applications
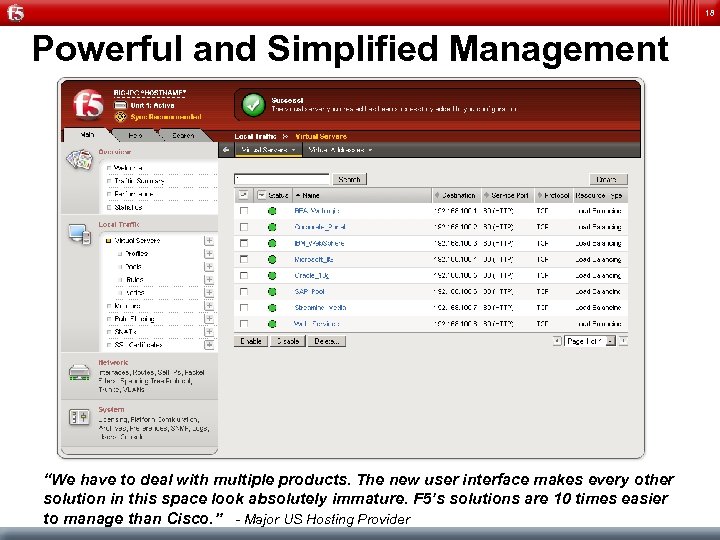
18 Powerful and Simplified Management “We have to deal with multiple products. The new user interface makes every other solution in this space look absolutely immature. F 5’s solutions are 10 times easier to manage than Cisco. ” - Major US Hosting Provider
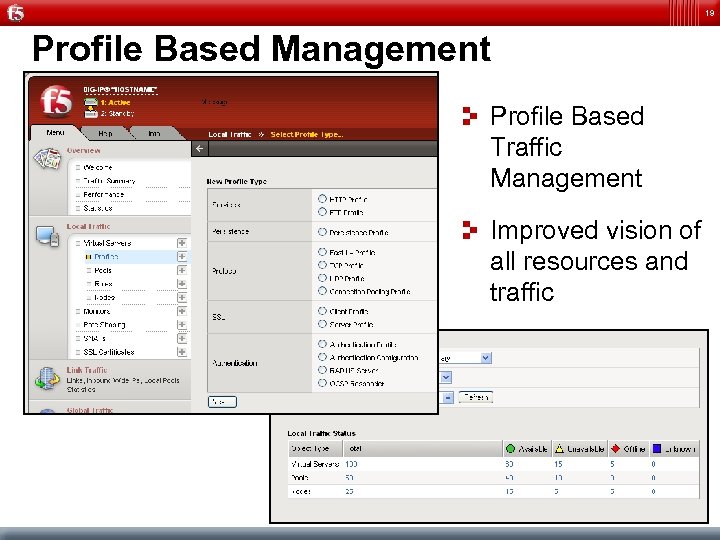
19 Profile Based Management Profile Based Traffic Management Improved vision of all resources and traffic Deliver Optimize Secure
20 Ensure Higher Availability - Superior System Design Processes Reporting and Control – Granular status, logging and configurable actions for component-level failures. Capable of warm restarts and upgrades. 3 -way HA Design – Robust Internal system checking and passthrough design.
21 Extensibility - IPv 6 Gateway
22 Network Virtualization Route Domains Consolidation with control Host multiple groups on one BIG-IP without conflicts Granular control to provide separate routing domains and overlapping IPs
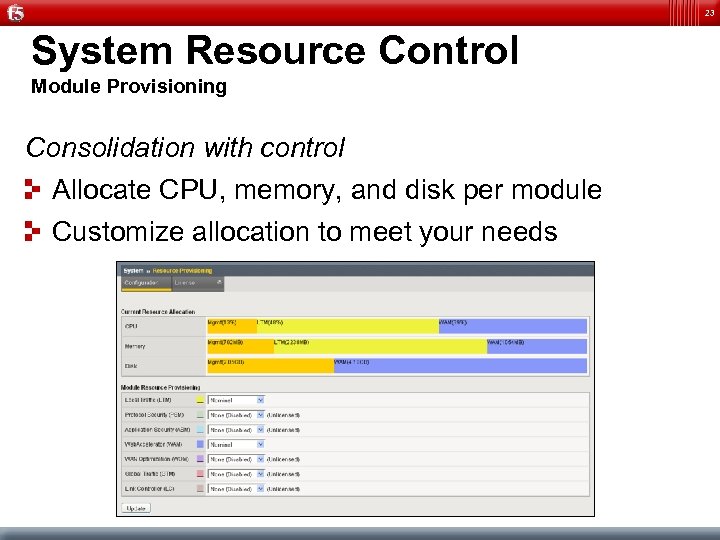
23 System Resource Control Module Provisioning Consolidation with control Allocate CPU, memory, and disk per module Customize allocation to meet your needs
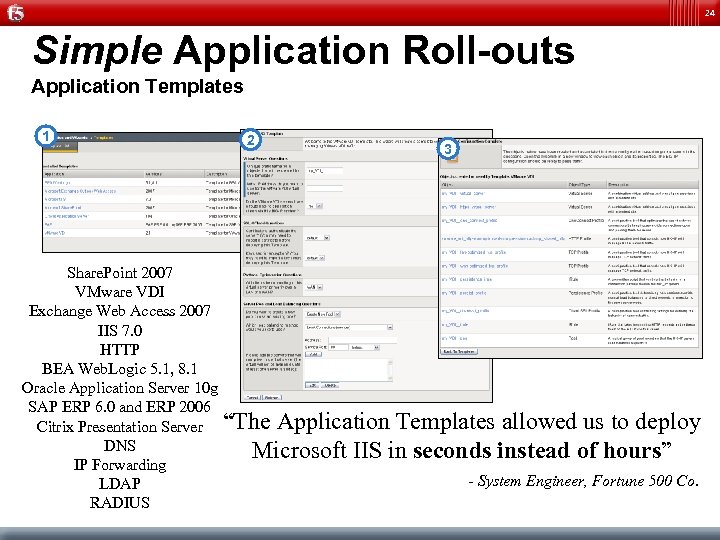
24 Simple Application Roll-outs Application Templates 1 Share. Point 2007 VMware VDI Exchange Web Access 2007 IIS 7. 0 HTTP BEA Web. Logic 5. 1, 8. 1 Oracle Application Server 10 g SAP ERP 6. 0 and ERP 2006 Citrix Presentation Server DNS IP Forwarding LDAP RADIUS 2 3 “The Application Templates allowed us to deploy Microsoft IIS in seconds instead of hours” - System Engineer, Fortune 500 Co.
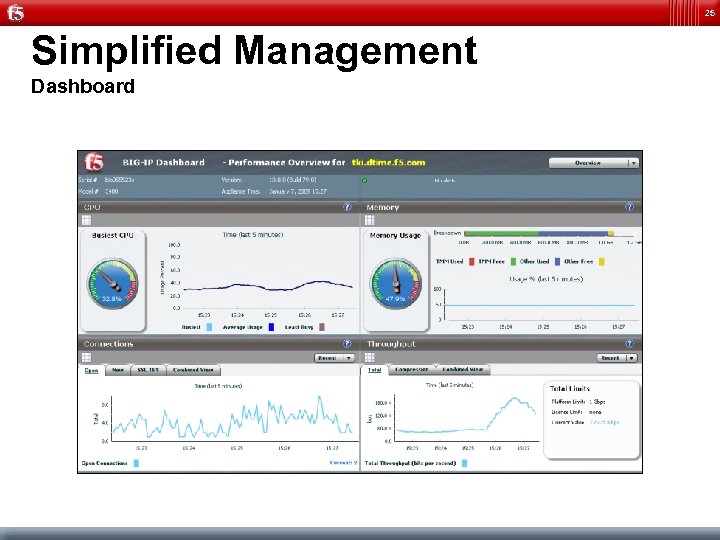
25 Simplified Management Dashboard
26 Secure and Accelerate DC to DC i. Sessions Secure and accelerate between data centers Integrated and free with BIG-IP LTM v 10 Symmetric Compression • Adaptive • Deflate • LZO SSL Encryption Note: Not available on the 1500 and 3400
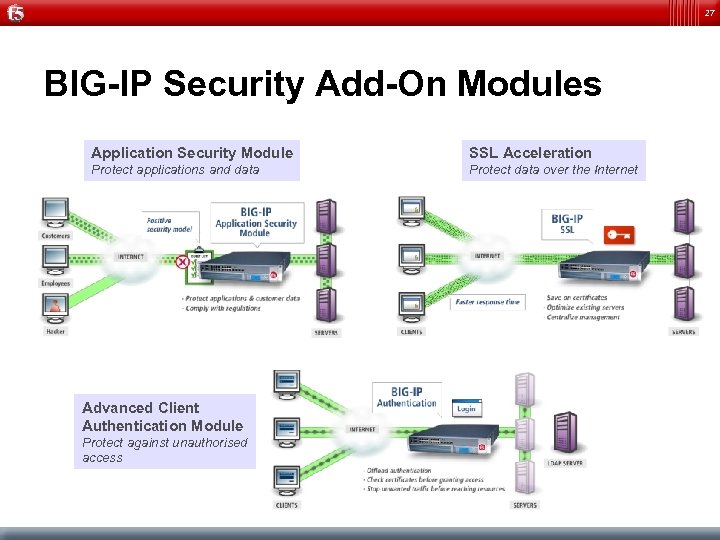
27 BIG-IP Security Add-On Modules Application Security Module SSL Acceleration Protect applications and data Protect data over the Internet Advanced Client Authentication Module Protect against unauthorised access
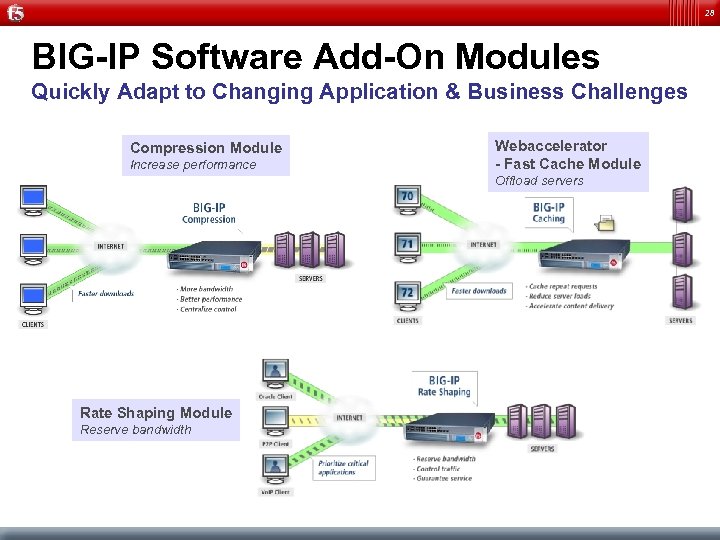
28 BIG-IP Software Add-On Modules Quickly Adapt to Changing Application & Business Challenges Compression Module Increase performance Webaccelerator - Fast Cache Module Offload servers Rate Shaping Module Reserve bandwidth
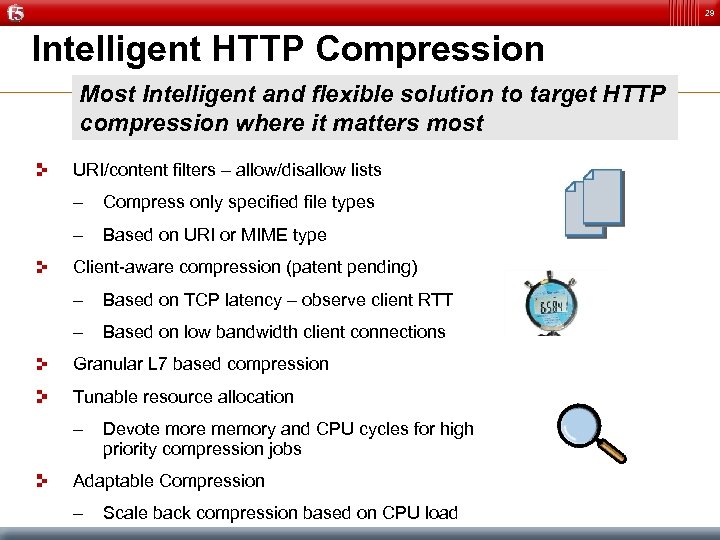
29 Intelligent HTTP Compression Most Intelligent and flexible solution to target HTTP compression where it matters most URI/content filters – allow/disallow lists – Compress only specified file types – Based on URI or MIME type Client-aware compression (patent pending) – Based on TCP latency – observe client RTT – Based on low bandwidth client connections Granular L 7 based compression Tunable resource allocation – Devote more memory and CPU cycles for high priority compression jobs Adaptable Compression – Scale back compression based on CPU load
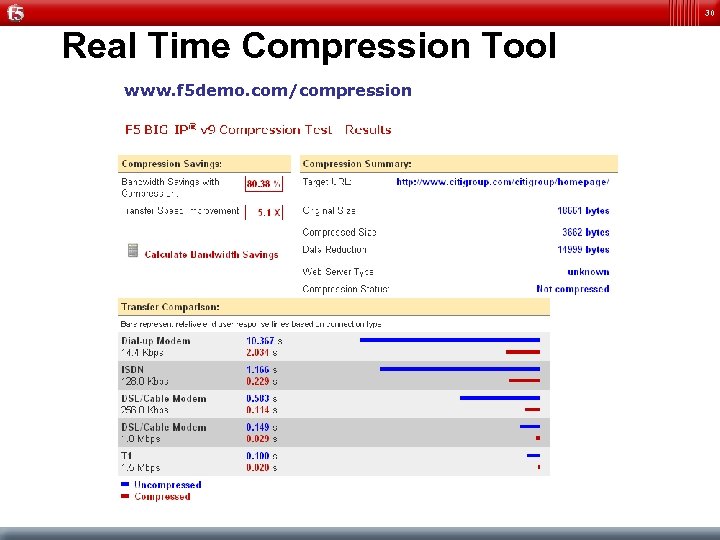
30 Real Time Compression Tool www. f 5 demo. com/compression

31 TCP Express Behaviors of a good TCP/IP implementation. – Proper congestion detection. – Good congestion recovery. – High bandwidth utilization. • • • Being too aggressive can cause individual connections to consume all of the network. Not being aggressive enough will leave unused bandwidth especially during a low number of connections. Always needs to adapt to changing congestion. – Increased windowing and buffering will often help compensate for latency and can also offload the application equipment more quickly. Most important tuning you can do in TCP typically has to do with window sizes and retransmission logic (aka congestion control behavior). On today’s networks, loss is almost always caused from congestion. – Most TCP stacks are not aggressive enough.
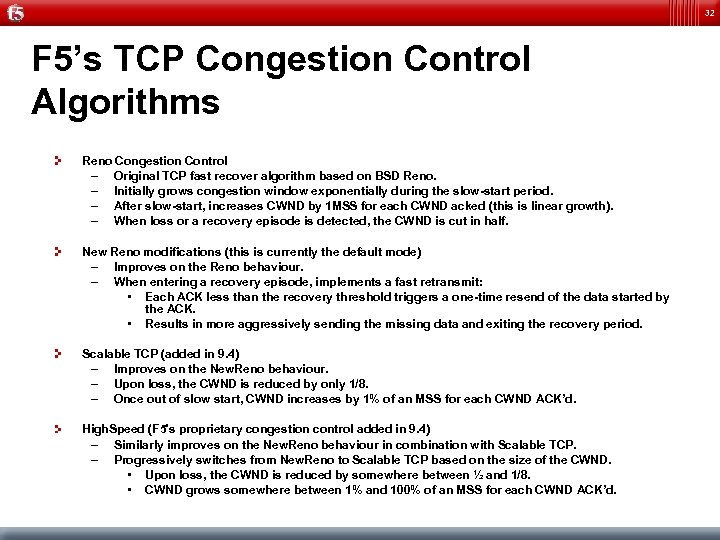
32 F 5’s TCP Congestion Control Algorithms Reno Congestion Control – Original TCP fast recover algorithm based on BSD Reno. – Initially grows congestion window exponentially during the slow-start period. – After slow-start, increases CWND by 1 MSS for each CWND acked (this is linear growth). – When loss or a recovery episode is detected, the CWND is cut in half. New Reno modifications (this is currently the default mode) – Improves on the Reno behaviour. – When entering a recovery episode, implements a fast retransmit: • Each ACK less than the recovery threshold triggers a one-time resend of the data started by the ACK. • Results in more aggressively sending the missing data and exiting the recovery period. Scalable TCP (added in 9. 4) – Improves on the New. Reno behaviour. – Upon loss, the CWND is reduced by only 1/8. – Once out of slow start, CWND increases by 1% of an MSS for each CWND ACK’d. High. Speed (F 5's proprietary congestion control added in 9. 4) – Similarly improves on the New. Reno behaviour in combination with Scalable TCP. – Progressively switches from New. Reno to Scalable TCP based on the size of the CWND. • Upon loss, the CWND is reduced by somewhere between ½ and 1/8. • CWND grows somewhere between 1% and 100% of an MSS for each CWND ACK’d.
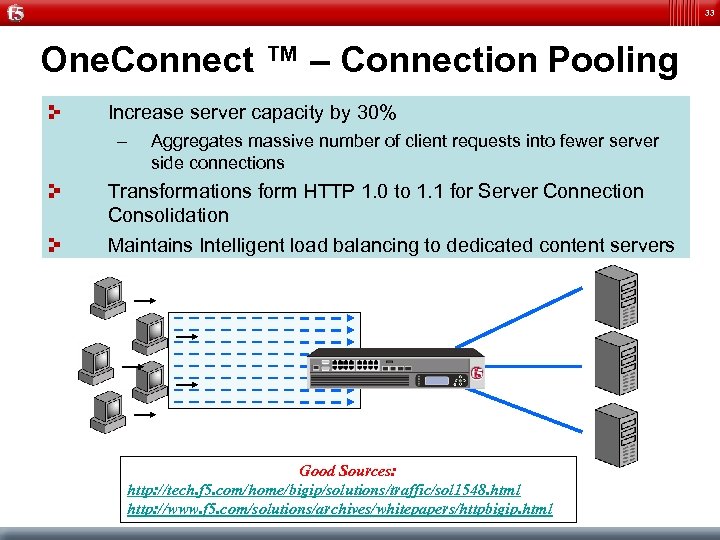
33 One. Connect ™ – Connection Pooling Increase server capacity by 30% – Aggregates massive number of client requests into fewer server side connections Transformations form HTTP 1. 0 to 1. 1 for Server Connection Consolidation Maintains Intelligent load balancing to dedicated content servers Good Sources: http: //tech. f 5. com/home/bigip/solutions/traffic/sol 1548. html http: //www. f 5. com/solutions/archives/whitepapers/httpbigip. html
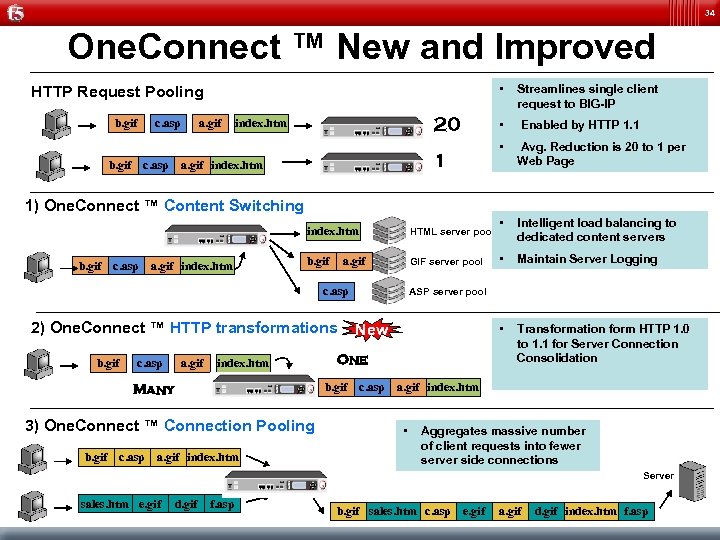
34 One. Connect ™ New and Improved • b. gif c. asp a. gif Avg. Reduction is 20 to 1 per Web Page • Intelligent load balancing to dedicated content servers • Maintain Server Logging • 1 b. gif c. asp a. gif index. htm Enabled by HTTP 1. 1 • 20 index. htm Streamlines single client request to BIG-IP • HTTP Request Pooling Transformation form HTTP 1. 0 to 1. 1 for Server Connection Consolidation 1) One. Connect ™ Content Switching index. htm b. gif c. asp a. gif index. htm HTML server pool b. gif GIF server pool a. gif c. asp ASP server pool 2) One. Connect ™ HTTP transformations New b. gif c. asp a. gif index. htm One b. gif c. asp a. gif index. htm Many 3) One. Connect ™ Connection Pooling b. gif c. asp a. gif index. htm • Aggregates massive number of client requests into fewer server side connections Server sales. htm e. gif d. gif f. asp b. gif sales. htm c. asp e. gif a. gif d. gif index. htm f. asp
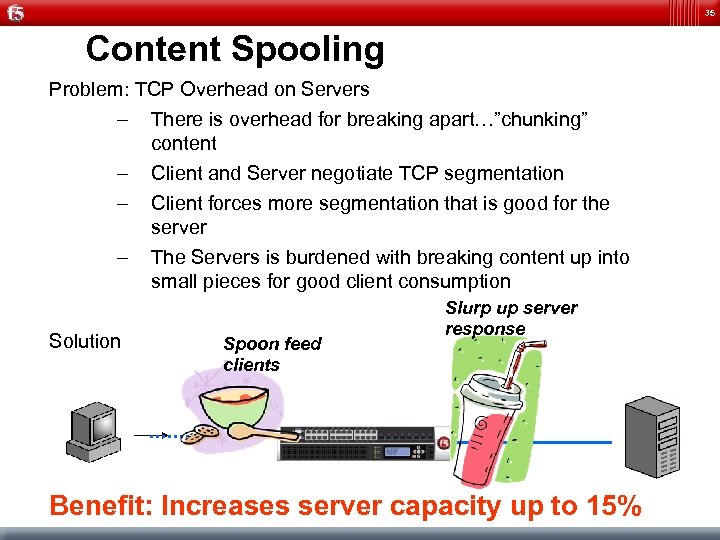
35 Content Spooling Problem: TCP Overhead on Servers – There is overhead for breaking apart…”chunking” content – Client and Server negotiate TCP segmentation – Client forces more segmentation that is good for the server – The Servers is burdened with breaking content up into small pieces for good client consumption Solution Spoon feed clients Slurp up server response Benefit: Increases server capacity up to 15%
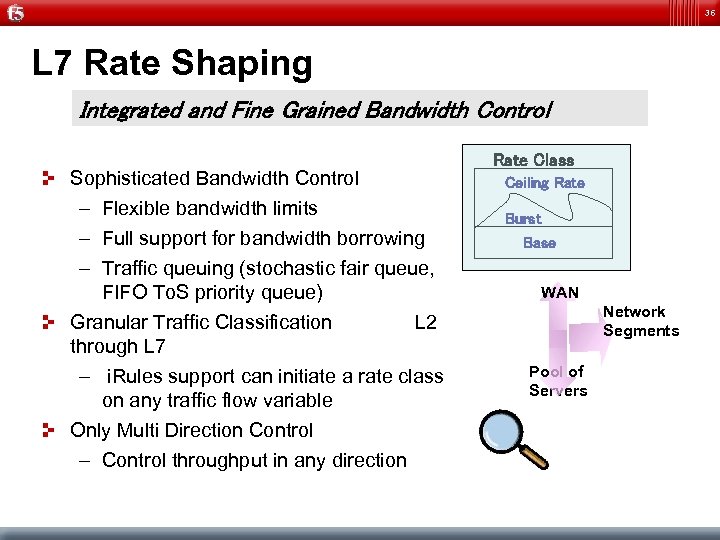
36 L 7 Rate Shaping Integrated and Fine Grained Bandwidth Control Sophisticated Bandwidth Control – Flexible bandwidth limits – Full support for bandwidth borrowing – Traffic queuing (stochastic fair queue, FIFO To. S priority queue) Granular Traffic Classification L 2 through L 7 – i. Rules support can initiate a rate class on any traffic flow variable Only Multi Direction Control – Control throughput in any direction Rate Class Ceiling Rate Burst Base WAN Network Segments Pool of Servers
37 Hardware
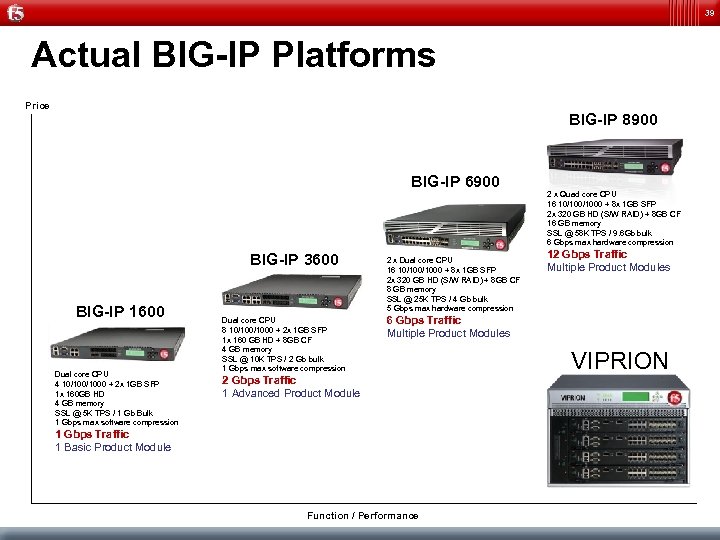
39 Actual BIG-IP Platforms Price BIG-IP 8900 BIG-IP 6900 BIG-IP 3600 BIG-IP 1600 Dual core CPU 4 10/1000 + 2 x 1 GB SFP 1 x 160 GB HD 4 GB memory SSL @ 5 K TPS / 1 Gb Bulk 1 Gbps max software compression Dual core CPU 8 10/1000 + 2 x 1 GB SFP 1 x 160 GB HD + 8 GB CF 4 GB memory SSL @ 10 K TPS / 2 Gb bulk 1 Gbps max software compression 2 x Dual core CPU 16 10/1000 + 8 x 1 GB SFP 2 x 320 GB HD (S/W RAID) + 8 GB CF 8 GB memory SSL @ 25 K TPS / 4 Gb bulk 5 Gbps max hardware compression 2 x Quad core CPU 16 10/1000 + 8 x 1 GB SFP 2 x 320 GB HD (S/W RAID) + 8 GB CF 16 GB memory SSL @ 58 K TPS / 9. 6 Gb bulk 6 Gbps max hardware compression 12 Gbps Traffic Multiple Product Modules 6 Gbps Traffic Multiple Product Modules 2 Gbps Traffic 1 Advanced Product Module 1 Gbps Traffic 1 Basic Product Module Function / Performance VIPRION
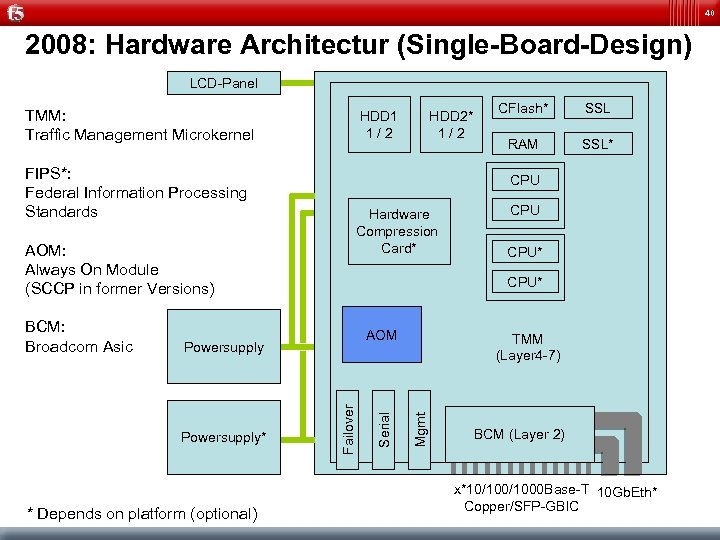
40 2008: Hardware Architectur (Single-Board-Design) LCD-Panel TMM: Traffic Management Microkernel HDD 1 1 / 2 FIPS*: Federal Information Processing Standards Hardware Compression Card* * Depends on platform (optional) SSL RAM SSL* CPU* TMM (Layer 4 -7) Mgmt Failover Serial AOM Powersupply* CFlash* CPU AOM: Always On Module (SCCP in former Versions) BCM: Broadcom Asic HDD 2* 1 / 2 BCM (Layer 2) x*10/1000 Base-T 10 Gb. Eth* Copper/SFP-GBIC
41 High-Performance Application Switches BIG-IP 8900 Consolidate with Purpose-built Hardware Designed specifically for application delivery Integrated platform for security, acceleration, availability BIG-IP 6900 Offload Application Servers High performance hardware SSL and compression offload Advanced connection management Reduce Operating Costs BIG-IP 1600 - 3600 Simplified management with USB, front panel management, remote boot, and more Increased uptime with hot swappable and redundant components

42 BIG-IP 1600 High performance meets high value High Performance – Dual-core CPU provides 1 Gb/s of L 7 throughput Reliable and Adaptable – Options for dual power and DC power – Front-to-back cooling Basic security and acceleration options – Protocol Security Module – 1 Gb/s compression and SSL throughput

43 BIG-IP 3600 Integrated ADC in a 1 U platform Advanced security and acceleration options – Web. Accelerator option – Application Security Module option High Performance – Dual-core CPU provides 2 Gb/s of L 7 throughput Reliable and Adaptable – Options for dual power and DC power – Front-to-back cooling

44 BIG-IP 6900 Consolidation and Integration High Performance for Consolidation – Dual CPU, Dual Core for 6 Gb/s of L 7 throughput – Hardware SSL and Compression offload Multi-module Integration – Run multiple modules and unify application delivery functions onto a single device Reliable and Adaptable – Dual power supplies and dual hard drives standard – Front-to-back cooling

45 BIG-IP 8900 The Foundation of a Unified ADN High Performance for Consolidation – Dual CPU, Quad Core for 12 Gb/s of L 7 throughput – Hardware SSL and compression offload 10 G Ports for Next-gen Data Centers – Two 10 G SFP ports in addition to 1 G copper and fiber connections Reliable and Adaptable – Dual power supplies and dual hard drives standard – Front-to-back cooling
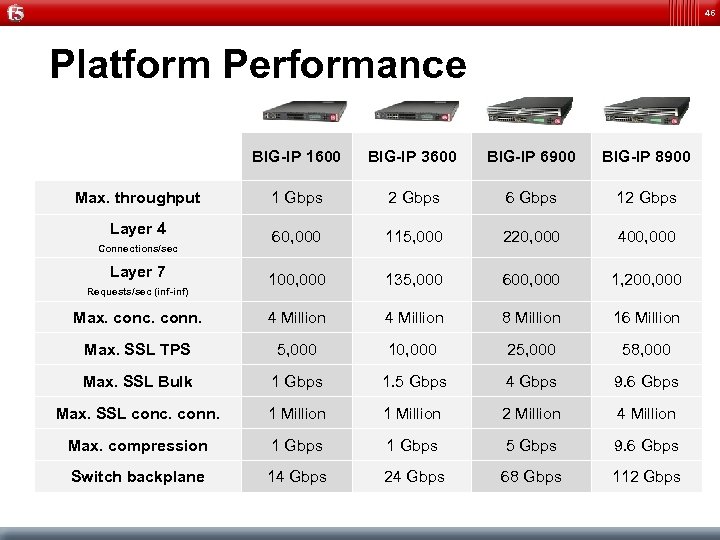
46 Platform Performance BIG-IP 1600 BIG-IP 3600 BIG-IP 6900 BIG-IP 8900 1 Gbps 2 Gbps 6 Gbps 12 Gbps 60, 000 115, 000 220, 000 400, 000 100, 000 135, 000 600, 000 1, 200, 000 Max. conc. conn. 4 Million 8 Million 16 Million Max. SSL TPS 5, 000 10, 000 25, 000 58, 000 Max. SSL Bulk 1 Gbps 1. 5 Gbps 4 Gbps 9. 6 Gbps Max. SSL conc. conn. 1 Million 2 Million 4 Million Max. compression 1 Gbps 5 Gbps 9. 6 Gbps Switch backplane 14 Gbps 24 Gbps 68 Gbps 112 Gbps Max. throughput Layer 4 Connections/sec Layer 7 Requests/sec (inf-inf)
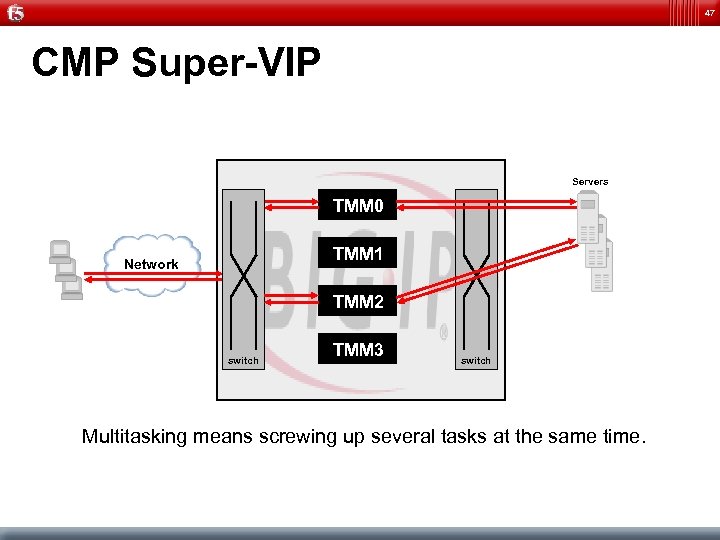
47 CMP Super-VIP Servers TMM 0 TMM 1 Network TMM 2 switch TMM 3 switch Multitasking means screwing up several tasks at the same time.

48 The World’s Only On Demand ADC
49 VIPRION – On Demand ADC Add application intelligence without adding management cost Market-leading performance Ultimate redundancy TMOS inside

50 Viprion Overview Unmatched Performance – Massive scalability – Processing architecture common with 8800 Intelligent clustering – Super. VIP (Virtuals can seamlessly span blades) – N+M redundancy for all features in cluster High Availability – Automatic failover within cluster – Chassis-to-chassis redundancy Full Modular Chassis – 4 blade slots w/1 blade type – Any blade can be chassis master Common central management console – Single point of Management – Same user interface as BIG-IP appliances
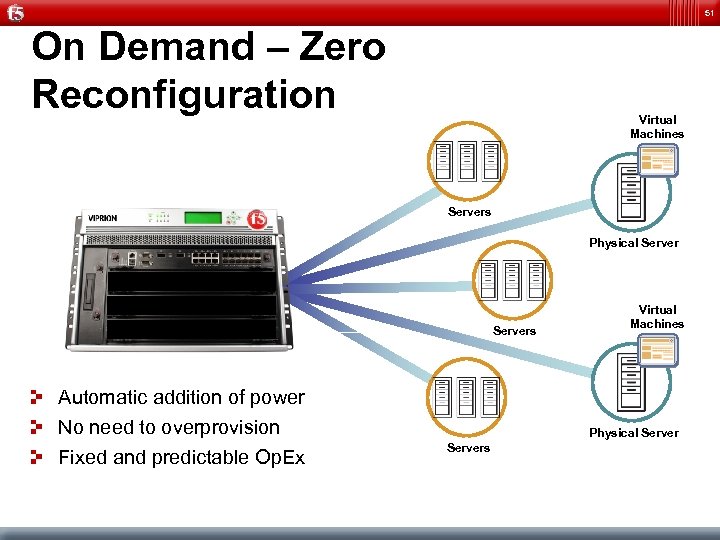
51 On Demand – Zero Reconfiguration Virtual Machines Servers Physical Servers Automatic addition of power No need to overprovision Fixed and predictable Op. Ex Virtual Machines Physical Servers

52 Ultimate Reliability Multi-Level Redundancy Internal blade to blade failover External chassis to chassis Hot swappable power supplies Hot swappable fan trays Hot swappable LCD display Passive, redundant backplane Integrated Lights Out mgmt
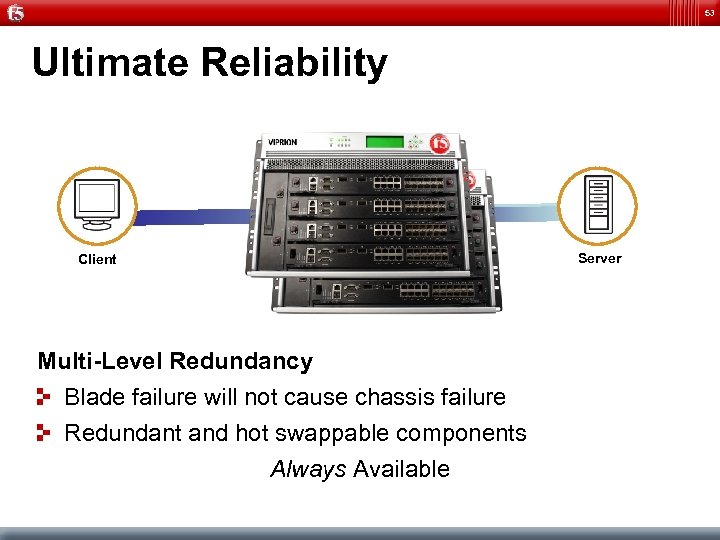
53 Ultimate Reliability Server Client Multi-Level Redundancy Blade failure will not cause chassis failure Redundant and hot swappable components Always Available
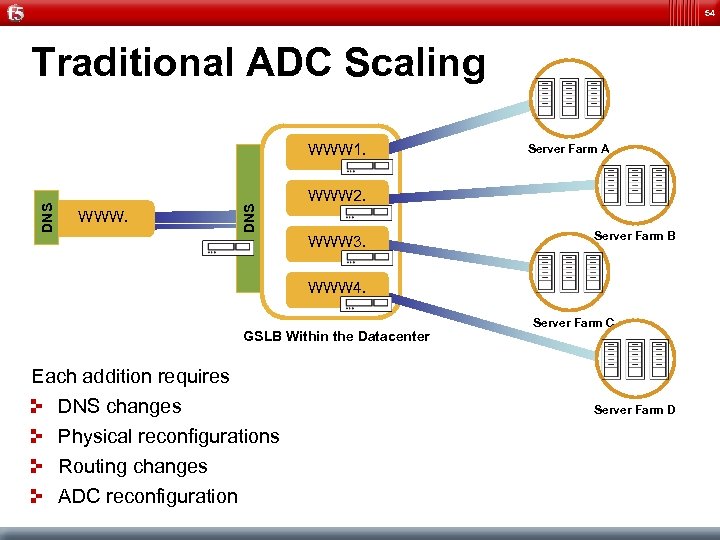
54 Traditional ADC Scaling WWW. DNS WWW 1. Server Farm A WWW 2. WWW 3. Server Farm B WWW 4. GSLB Within the Datacenter Each addition requires DNS changes Physical reconfigurations Routing changes ADC reconfiguration Server Farm C Server Farm D
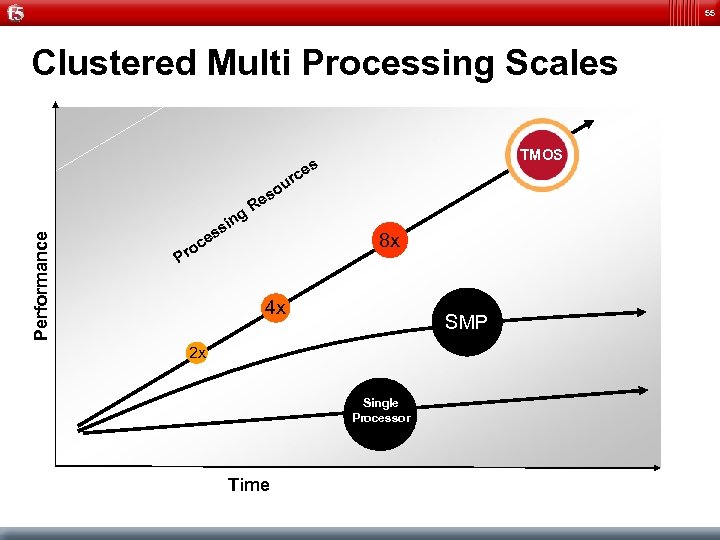
55 Clustered Multi Processing Scales TMOS es Performance rc R g u so e in c ro P s es 8 x 4 x SMP 2 x Single Processor Time
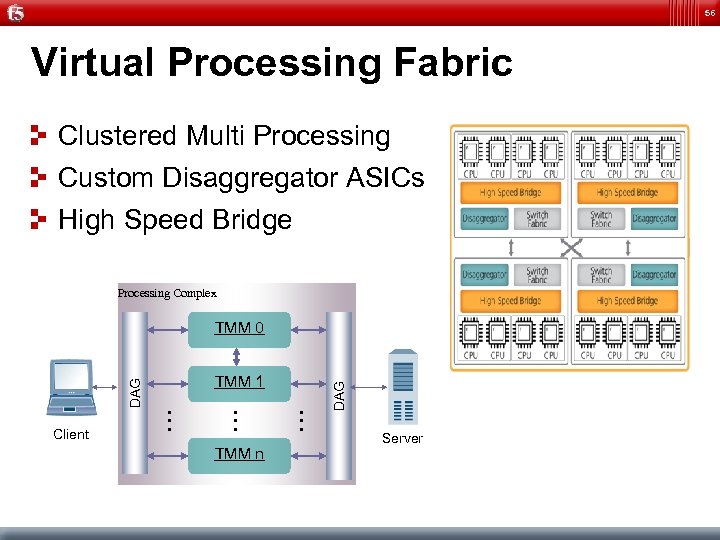
56 Virtual Processing Fabric Clustered Multi Processing Custom Disaggregator ASICs High Speed Bridge Processing Complex DAG TMM 1 TMM n … … … Client DAG TMM 0 Server

57 The Super. VIP WWW. Pool Virtualization: “Separating the physical characteristics of computing resources from the systems, applications or end users interacting with those resources”. With a Super. VIP, a single virtual server may be processed by all computing resources of the VIPRION.
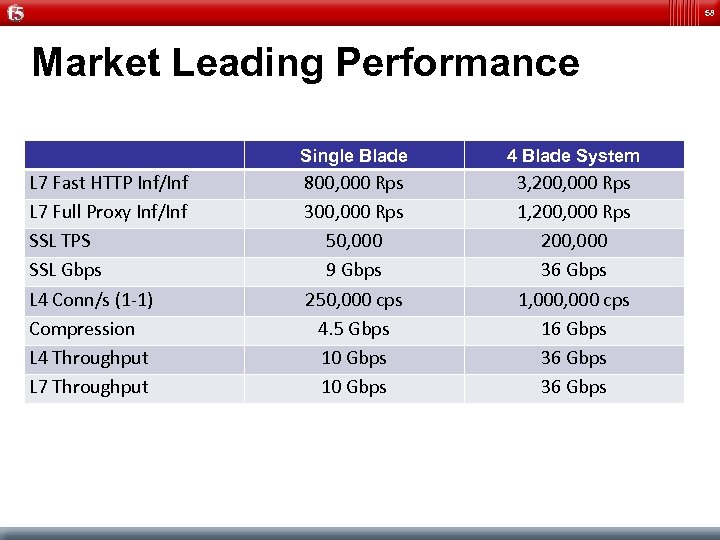
58 Market Leading Performance Single Blade L 7 Fast HTTP Inf/Inf L 7 Full Proxy Inf/Inf SSL TPS SSL Gbps L 4 Conn/s (1 -1) Compression L 4 Throughput L 7 Throughput 4 Blade System 800, 000 Rps 300, 000 Rps 50, 000 9 Gbps 250, 000 cps 4. 5 Gbps 10 Gbps 3, 200, 000 Rps 1, 200, 000 Rps 200, 000 36 Gbps 1, 000 cps 16 Gbps 36 Gbps
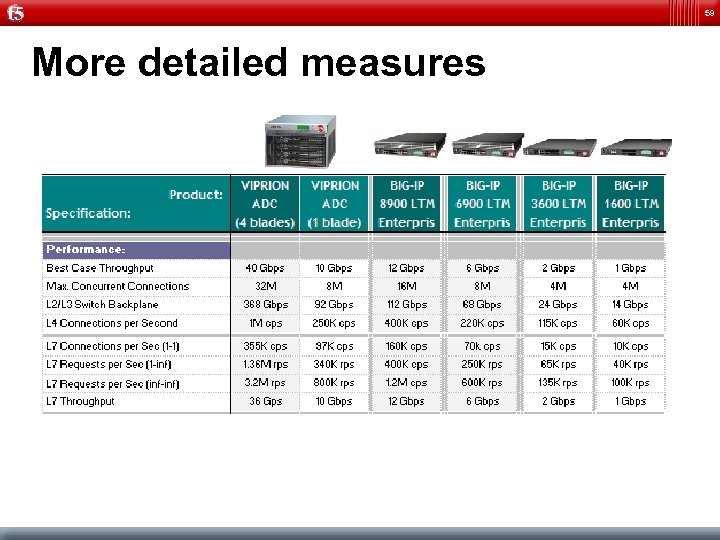
59 More detailed measures
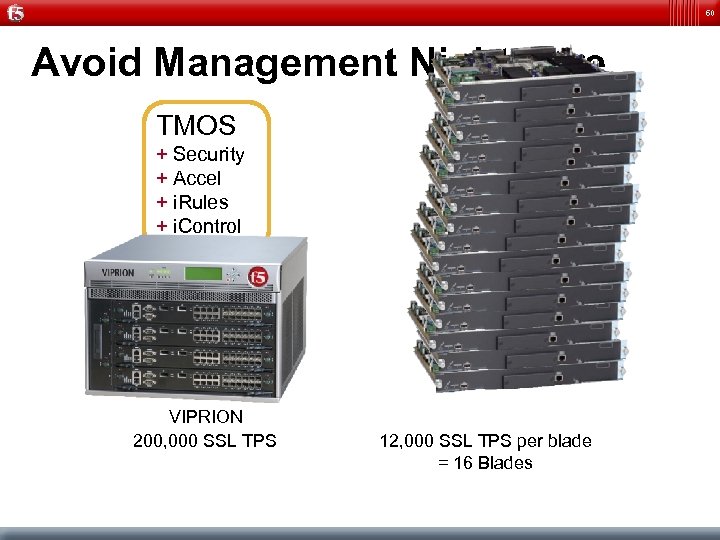
60 Avoid Management Nightmare TMOS + Security + Accel + i. Rules + i. Control VIPRION 200, 000 SSL TPS 12, 000 SSL TPS per blade = 16 Blades
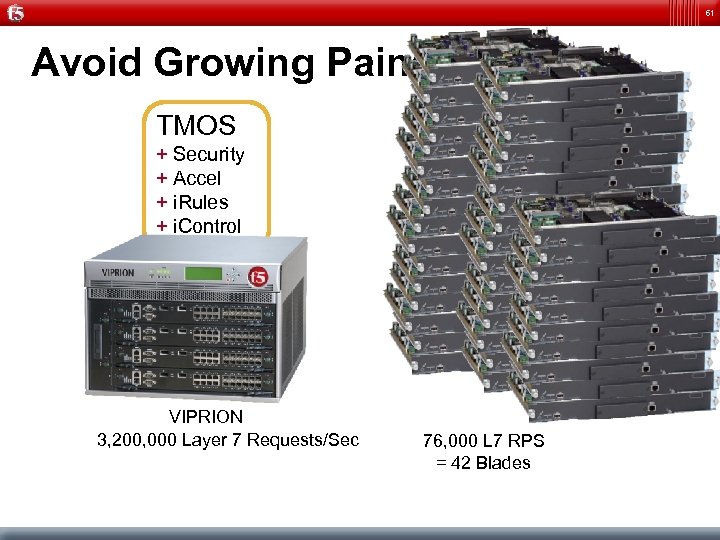
61 Avoid Growing Pains TMOS + Security + Accel + i. Rules + i. Control VIPRION 3, 200, 000 Layer 7 Requests/Sec 76, 000 L 7 RPS = 42 Blades
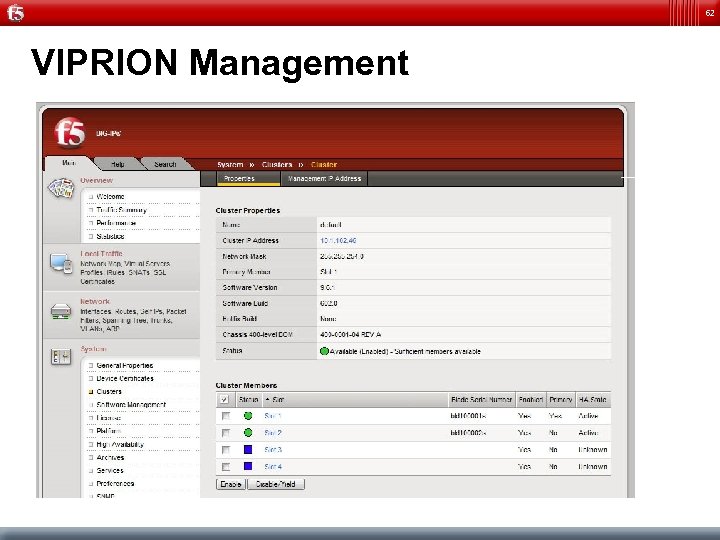
62 VIPRION Management
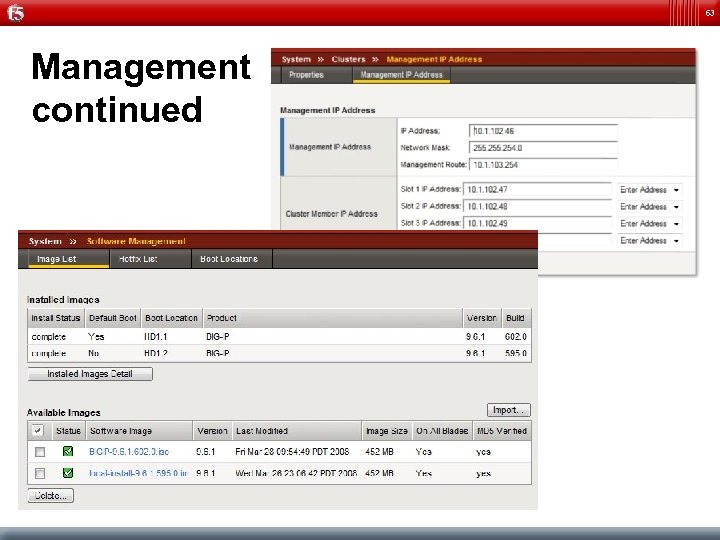
63 Management continued
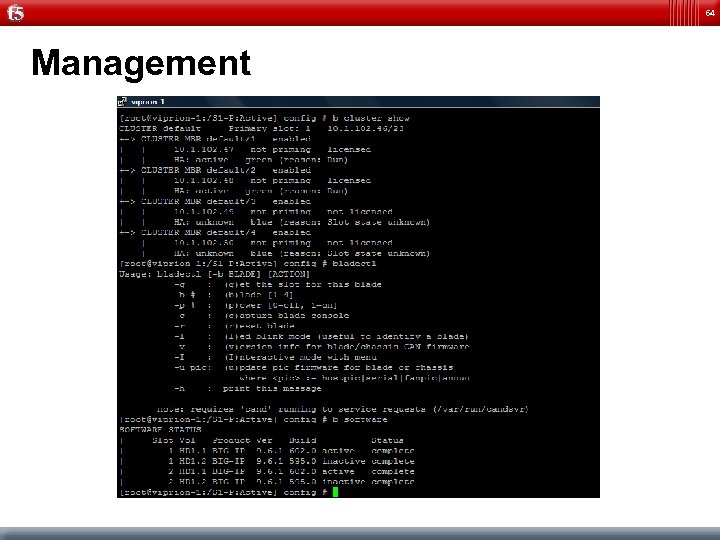
64 Management

65 i. Rules and i. Control

66 What are i. Rules? Programming language integrated into TMOS Traffic Management Operating System Based on industry standard TCL language Tool Command Language Provide ability to intercept, inspect, transform, direct and track inbound or outbound application traffic Core of the F 5 “secret sauce” and key differentiator
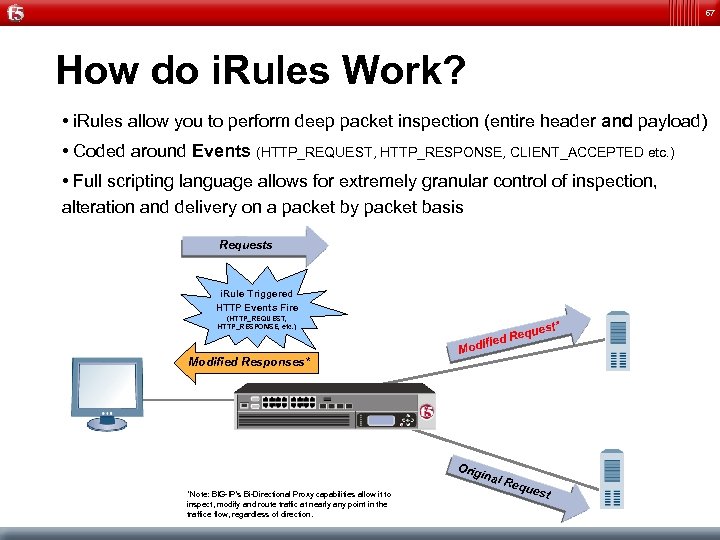
67 How do i. Rules Work? • i. Rules allow you to perform deep packet inspection (entire header and payload) • Coded around Events (HTTP_REQUEST, HTTP_RESPONSE, CLIENT_ACCEPTED etc. ) • Full scripting language allows for extremely granular control of inspection, alteration and delivery on a packet by packet basis Requests i. Rule Triggered HTTP Events Fire (HTTP_REQUEST, HTTP_RESPONSE, etc. ) Modified Responses* Mo Orig inal *Note: BIG-IP’s Bi-Directional Proxy capabilities allow it to inspect, modify and route traffic at nearly any point in the traffice flow, regardless of direction. t* ques Re dified Req ues t
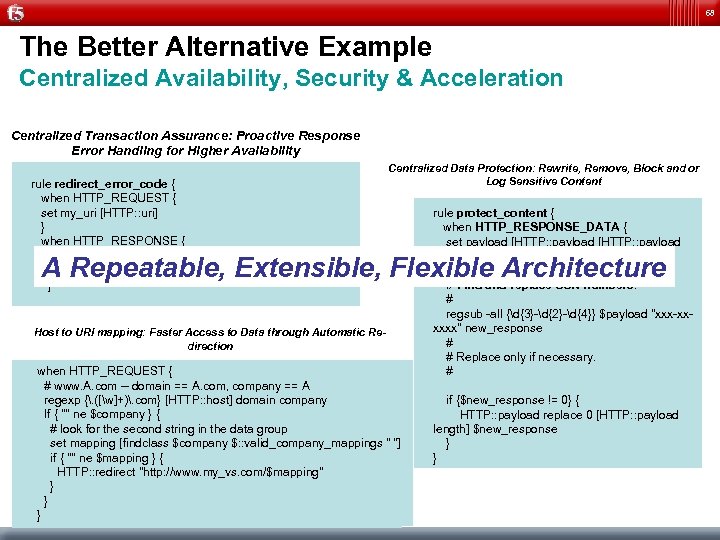
68 The Better Alternative Example Centralized Availability, Security & Acceleration Centralized Transaction Assurance: Proactive Response Error Handling for Higher Availability rule redirect_error_code { when HTTP_REQUEST { set my_uri [HTTP: : uri] } when HTTP_RESPONSE { if { [HTTP: : status] == 500 } { HTTP: : redirect http: //192. 168. 33. 131$my_uri } Centralized Data Protection: Rewrite, Remove, Block and or Log Sensitive Content rule protect_content { when HTTP_RESPONSE_DATA { set payload [HTTP: : payload length]] # # Find and replace SSN numbers. # regsub -all {d{3}-d{2}-d{4}} $payload "xxx-xxxxxx" new_response # # Replace only if necessary. # if {$new_response != 0} { HTTP: : payload replace 0 [HTTP: : payload length] $new_response } } A Repeatable, Extensible, Flexible Architecture Host to URI mapping: Faster Access to Data through Automatic Redirection when HTTP_REQUEST { # www. A. com -- domain == A. com, company == A regexp {. ([w]+). com} [HTTP: : host] domain company If { "" ne $company } { # look for the second string in the data group set mapping [findclass $company $: : valid_company_mappings " "] if { "" ne $mapping } { HTTP: : redirect "http: //www. my_vs. com/$mapping" } } }
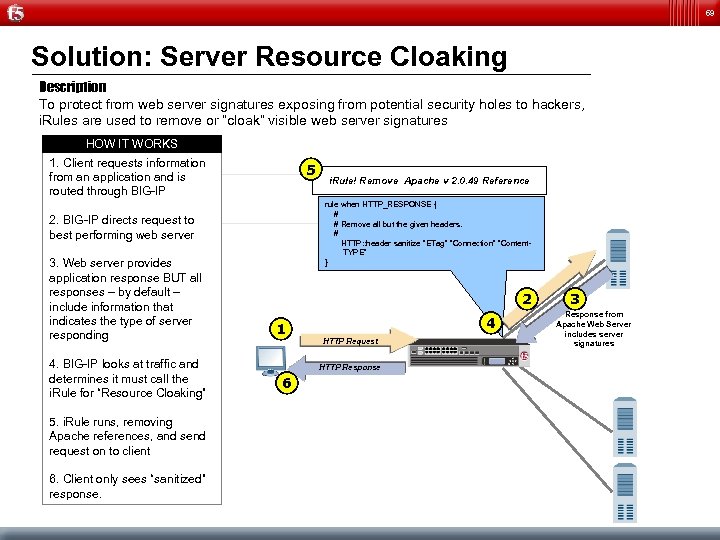
69 Solution: Server Resource Cloaking Description To protect from web server signatures exposing from potential security holes to hackers, i. Rules are used to remove or “cloak” visible web server signatures HOW IT WORKS 1. Client requests information from an application and is routed through BIG-IP 5 rule when HTTP_RESPONSE { # # Remove all but the given headers. # HTTP: : header sanitize “ETag” “Connection” “Content. TYPE” } 2. BIG-IP directs request to best performing web server 3. Web server provides application response BUT all responses – by default – include information that indicates the type of server responding 4. BIG-IP looks at traffic and determines it must call the i. Rule for “Resource Cloaking” 5. i. Rule runs, removing Apache references, and send request on to client 6. Client only sees “sanitized” response. i. Rule! Remove Apache v 2. 0. 49 Reference 2 1 4 HTTP Request HTTP Response 6 3 Response from Apache Web Server includes server signatures
70 What can an i. Rule do? Read, transform, replace header or payload information (HTTP, TCP, SIP, etc. ) Work with any protocol, such as SIP, RTSP, XML, others, whether with native (HTTP: : cookie) or generic (TCP: : payload) commands Make adjustments to TCP behavior, such as MSS, checking the RTT, deep payload inspection Authentication assistance, offload, inspection and more for LDAP, RADIUS, etc. Caching, compression, profile selection, rate shaping and much, much more
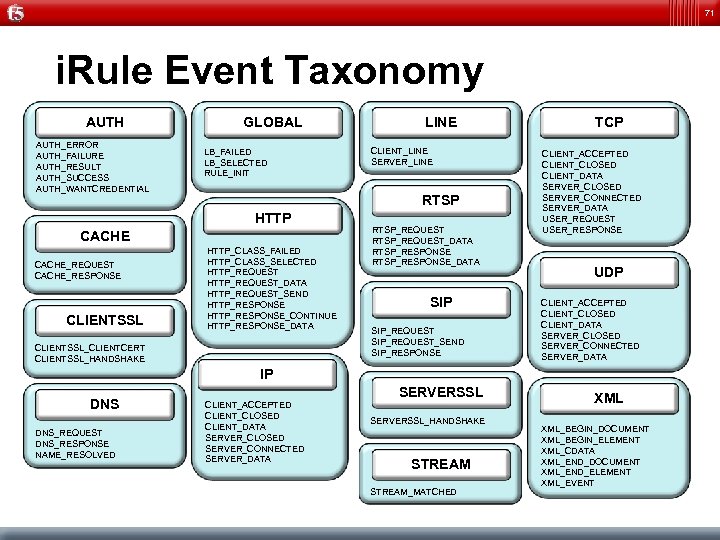
71 i. Rule Event Taxonomy AUTH_ERROR AUTH_FAILURE AUTH_RESULT AUTH_SUCCESS AUTH_WANTCREDENTIAL CACHE_REQUEST CACHE_RESPONSE CLIENTSSL GLOBAL LB_FAILED LB_SELECTED RULE_INIT HTTP_CLASS_FAILED HTTP_CLASS_SELECTED HTTP_REQUEST_DATA HTTP_REQUEST_SEND HTTP_RESPONSE_CONTINUE HTTP_RESPONSE_DATA CLIENTSSL_CLIENTCERT CLIENTSSL_HANDSHAKE IP IP DNS DNS_REQUEST DNS_RESPONSE NAME_RESOLVED CLIENT_ACCEPTED CLIENT_CLOSED CLIENT_DATA SERVER_CLOSED SERVER_CONNECTED SERVER_DATA LINE CLIENT_LINE SERVER_LINE RTSP_REQUEST_DATA RTSP_RESPONSE_DATA SIP SIP_REQUEST_SEND SIP_RESPONSE SERVERSSL_HANDSHAKE STREAM_MATCHED TCP CLIENT_ACCEPTED CLIENT_CLOSED CLIENT_DATA SERVER_CLOSED SERVER_CONNECTED SERVER_DATA USER_REQUEST USER_RESPONSE UDP CLIENT_ACCEPTED CLIENT_CLOSED CLIENT_DATA SERVER_CLOSED SERVER_CONNECTED SERVER_DATA XML XML_BEGIN_DOCUMENT XML_BEGIN_ELEMENT XML_CDATA XML_END_DOCUMENT XML_END_ELEMENT XML_EVENT
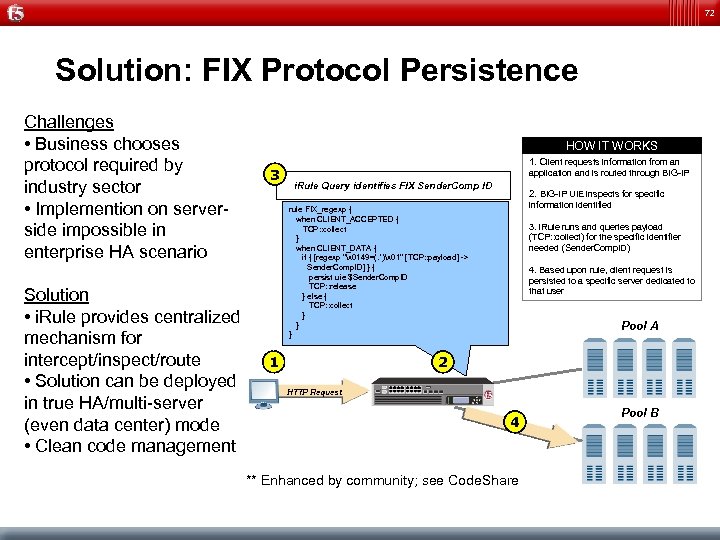
72 Solution: FIX Protocol Persistence Challenges • Business chooses protocol required by industry sector • Implemention on serverside impossible in enterprise HA scenario HOW IT WORKS 3 Solution • i. Rule provides centralized mechanism for intercept/inspect/route • Solution can be deployed in true HA/multi-server (even data center) mode • Clean code management 1. Client requests information from an application and is routed through BIG-IP i. Rule Query identifies FIX Sender. Comp ID 2. BIG-IP UIE inspects for specific information identified rule FIX_regexp { when CLIENT_ACCEPTED { TCP: : collect } when CLIENT_DATA { if { [regexp "x 0149=(. *)x 01" [TCP: : payload] -> Sender. Comp. ID] } { persist uie $Sender. Comp. ID TCP: : release } else { TCP: : collect } } } 1 3. i. Rule runs and queries payload (TCP: : collect) for the specific identifier needed (Sender. Comp. ID) 4. Based upon rule, client request is persisted to a specific server dedicated to that user Pool A 2 HTTP Request 4 ** Enhanced by community; see Code. Share Pool B

73 What makes i. Rules so unique? Full-fledged scripts, executed against traffic on the network, at wire-speed Powerful logical operations combined with deep packet inspection The ability to route, re-direct, retry, or block traffic Community support, tools and innovation
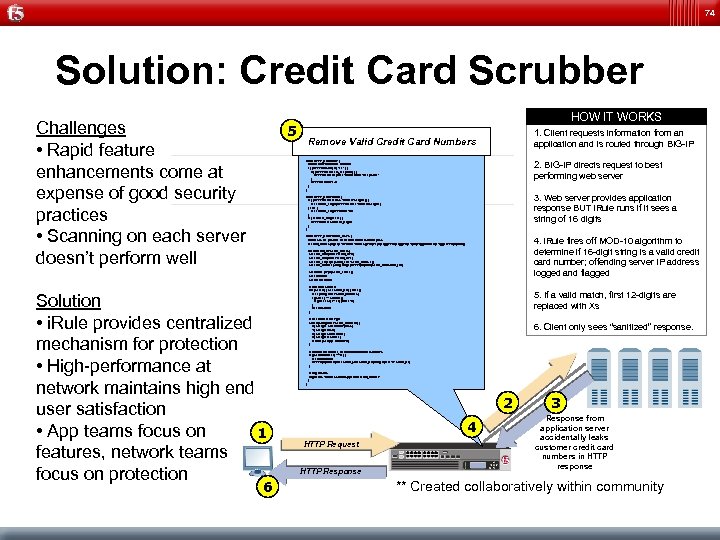
74 Solution: Credit Card Scrubber Challenges • Rapid feature enhancements come at expense of good security practices • Scanning on each server doesn’t perform well 5 HOW IT WORKS 1. Client requests information from an Remove Valid Credit Card Numbers application and is routed through BIG-IP when HTTP_REQUEST { # Don't allow data to be chunked if { [HTTP: : version] eq "1. 1" } { if { [ HTTP: : header is_keepalive] } { HTTP: : header replace "Connection" "Keep-Alive" } HTTP: : version "1. 0" } } 2. BIG-IP directs request to best performing web server 3. Web server provides application response BUT i. Rule runs if it sees a string of 16 digits when HTTP_RESPONSE { if { [HTTP: : header exists "Content-Length"] } { set content_length [HTTP: : header "Content-Length"] } else { set content_length 4294967295 } if { $content_length > 0 } { HTTP: : collect $content_length } } when HTTP_RESPONSE_DATA { # Find ALL the possible credit card numbers in one pass set card_indices [regexp -all -inline -indices {(? : 3[4 -7]d{13})|(? : 4d{15})|(? : 5[1 -5]d{14})|(? : 6011d{12})} [ TTP: : payload]] H 4. i. Rule fires off MOD-10 algorithm to determine if 16 -digit string is a valid credit card number; offending server IP address logged and flagged foreach card_idx $card_indices { set card_start [lindex $card_idx 0] set card_end [lindex $card_idx 1] set card_len [expr {$card_end - $card_start + 1}] set card_number [string range [HTTP: : payload] $card_start $card_end] set double [expr {$card_len & 1}] set chksum 0 set is. Card invalid Solution • i. Rule provides centralized mechanism for protection • High-performance at network maintains high end user satisfaction • App teams focus on 1 features, network teams focus on protection 6 # Calculate MOD 10 for { set i 0 } { $i < $ card_len } { incr i } { set c [string index $card_number $i] if {($i & 1) == $double} { if {[ incr c $c] >= 10} {incr c -9} } incr chksum $c } 5. If a valid match, first 12 -digits are replaced with Xs # Determine Card Type switch [string index $card_number 0] { 3 { set type American. Express } 4 { set type Visa } 5 { set type Master. Card } 6 { set type Discover } default { set type Unknown } } # If valid card number, then mask out numbers with X's if { ($chksum % 10) == 0 } { set is. Card valid HTTP: : payload replace $card_start $card_len [string repeat "X" $card_len] } # Log Results log local 0. "Found $is. Card $type CC# $card_number" } } 6. Client only sees “sanitized” response. 2 4 HTTP Request HTTP Response 3 Response from application server accidentally leaks customer credit card numbers in HTTP response ** Created collaboratively within community
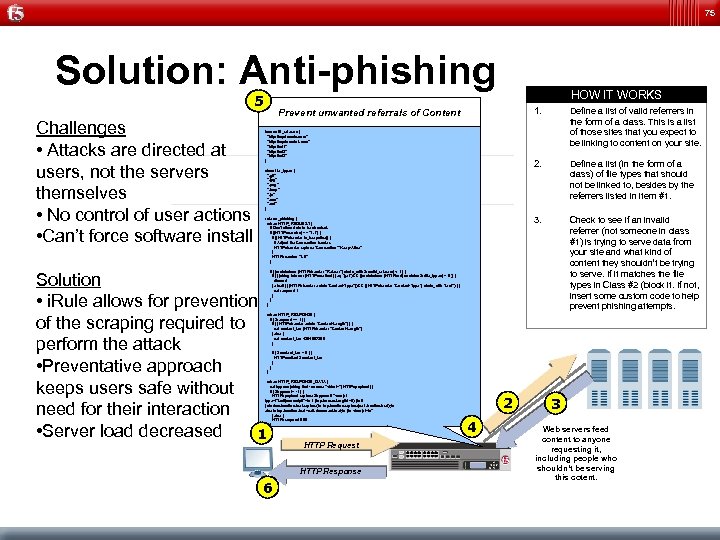
75 Solution: Anti-phishing 5 Challenges • Attacks are directed at users, not the servers themselves • No control of user actions • Can’t force software install HOW IT WORKS 1. class file_types { ". gif" ". jpg" ". png" ". bmp" ". js" ". css" ". xsl" } rule no_phishing { when HTTP_REQUEST { # Don't allow data to be chunked. if {[HTTP: : version] == "1. 1"} { if {[HTTP: : header is_keepalive]} { # Adjust the Connection header. HTTP: : header replace "Connection" "Keep-Alive" } HTTP: : version "1. 0" } Define a list (in the form of a class) of file types that should not be linked to, besides by the referrers listed in item #1. 3. lass valid_referers { "http: //mydomain. com" "http: //mydomain 1. com" "http: //url 1" "http: //url 2" "http: //url 3" } Define a list of valid referrers in the form of a class. This is a list of those sites that you expect to be linking to content on your site. 2. Prevent unwanted referrals of Content Check to see if an invalid referrer (not someone in class #1) is trying to serve data from your site and what kind of content they shouldn’t be trying to serve. If it matches the file types in Class #2 (block it. If not, insert some custom code to help prevent phishing attempts. if { [matchclass [HTTP: : header "Referer"] starts_with $: : valid_referers] < 1 } { if { ([string tolower [HTTP: : method] ] eq "get") && ([matchclass [HTTP: : uri] contains $: : file_types] > 0 )} { discard } elseif { ([HTTP: : header exists "Content-Type"]) && ([HTTP: : header "Content-Type"] starts_with "text" ) } { set respond 1 } } } Solution • i. Rule allows for prevention of the scraping required to perform the attack • Preventative approach keeps users safe without need for their interaction • Server load decreased 1 when HTTP_RESPONSE { if { $respond == 1 } { if { [HTTP: : header exists "Content-Length"] } { set content_len [HTTP: : header "Content-Length"] } else { set content_len 4294967295 } if { $content_len > 0 } { HTTP: : collect $content_len } } } when HTTP_RESPONSE_DATA { set bypass [string first - nocase "<html>" [HTTP: : payload] ] if { $bypass != -1 } { HTTP: : payload replace $bypass 0 "<script type="text/javascript">n if (top. frames. length!=0) {n if (window. location. href. replace)n top. location. replace(self. location. href); n elsen top. location. href=self. document. href; n }n </script>n" } else { HTTP: : respond 500 } } } HTTP Request HTTP Response 6 2 4 3 Web servers feed content to anyone requesting it, including people who shouldn’t be serving this cotent.
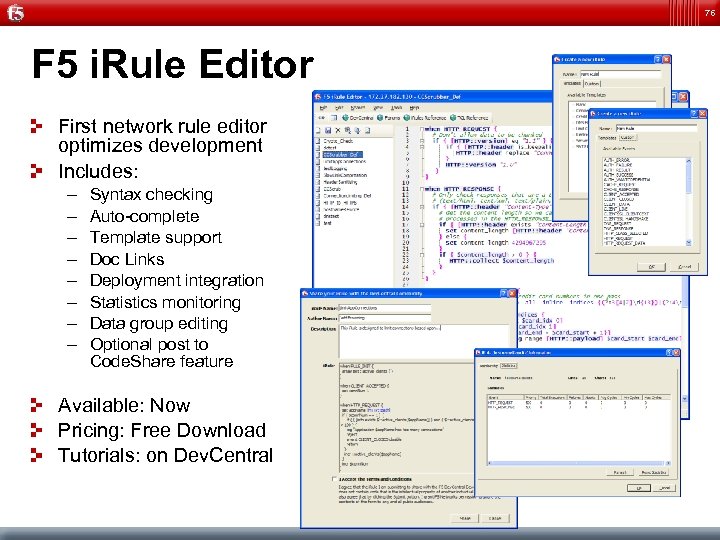
76 F 5 i. Rule Editor First network rule editor optimizes development Includes: – – – – Syntax checking Auto-complete Template support Doc Links Deployment integration Statistics monitoring Data group editing Optional post to Code. Share feature Available: Now Pricing: Free Download Tutorials: on Dev. Central
77 Introducing i. Control v 9 Open API (SOAP/XML) allows applications to automatically interact with the network Integration with development tools from Microsoft, BEA, and Oracle Online community F 5 Dev. Central – Developer assistance on F 5 Dev. Central via developer forums (http: //devcentral. f 5. com) – i. Rules forum and code examples
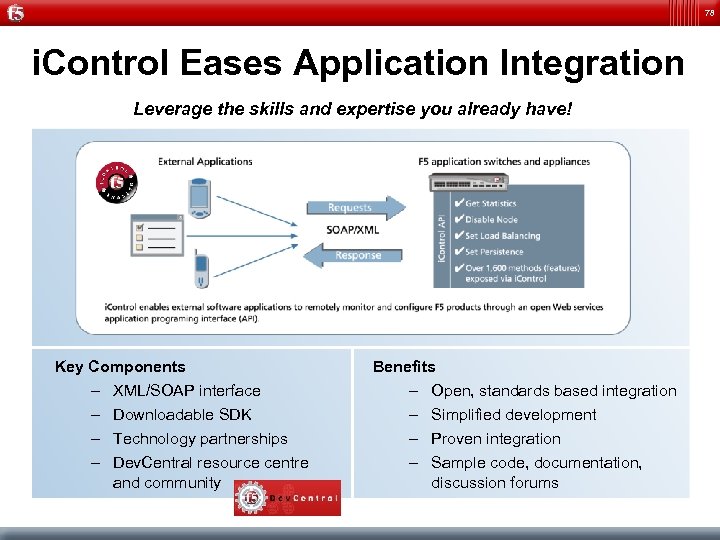
78 i. Control Eases Application Integration Leverage the skills and expertise you already have! Key Components – XML/SOAP interface – Downloadable SDK – Technology partnerships – Dev. Central resource centre and community Benefits – Open, standards based integration – Simplified development – Proven integration – Sample code, documentation, discussion forums
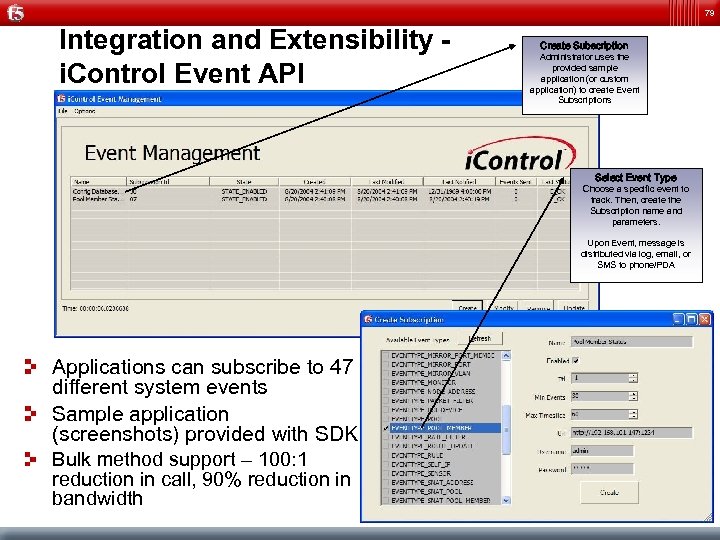
79 Integration and Extensibility - i. Control Event API Create Subscription Administrator uses the provided sample application (or custom application) to create Event Subscriptions Select Event Type Choose a specific event to track. Then, create the Subscription name and parameters. Upon Event, message is distributed via log, email, or SMS to phone/PDA Applications can subscribe to 47 different system events Sample application (screenshots) provided with SDK Bulk method support – 100: 1 reduction in call, 90% reduction in bandwidth
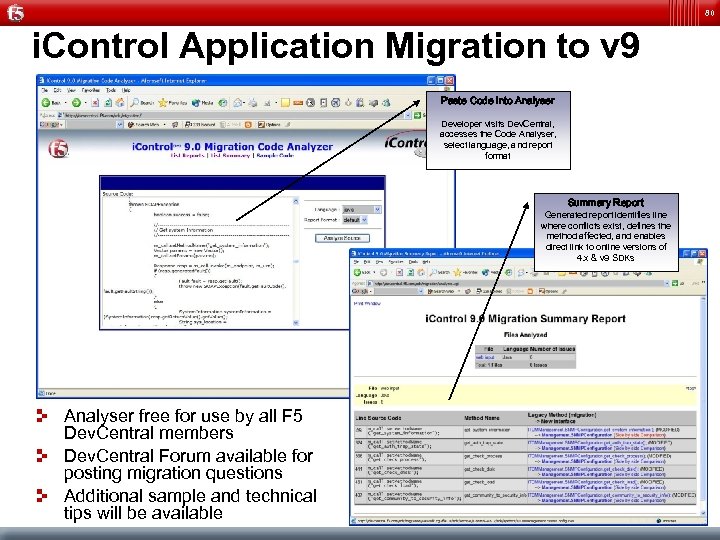
80 i. Control Application Migration to v 9 Paste Code Into Analyser Developer visits Dev. Central, accesses the Code Analyser, select language, and report format Summary Report Generated report identifies line where conflicts exist, defines the method affected, and enables direct link to online versions of 4. x & v 9 SDKs Analyser free for use by all F 5 Dev. Central members Dev. Central Forum available for posting migration questions Additional sample and technical tips will be available
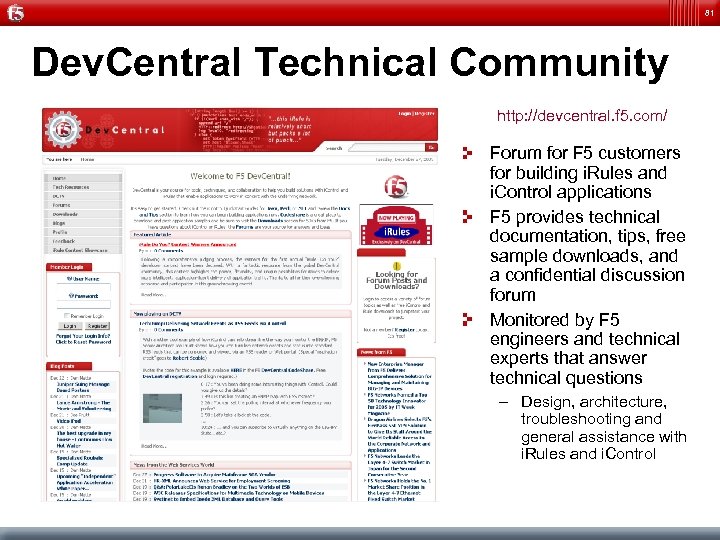
81 Dev. Central Technical Community http: //devcentral. f 5. com/ Forum for F 5 customers for building i. Rules and i. Control applications F 5 provides technical documentation, tips, free sample downloads, and a confidential discussion forum Monitored by F 5 engineers and technical experts that answer technical questions – Design, architecture, troubleshooting and general assistance with i. Rules and i. Control
82 Link Collection Overall Technical www. f 5. com ask. f 5. com devcentral. f 5. com F 5 University www. f 5 university. com/ » » Login: your email Password: adv 5 tech Partner Informaiotn www. f 5. com/partners www. f 5. com/training_services/certification/cert. FAQ. html Gartner Report http: //mediaproducts. gartner. com/reprints/f 5 networks/article 1. html Important deployment information is available at Data Center Virtualization Application Traffic Management Application Briefs Solution Briefs F 5 Compression and Cache Test F 5 i. Control Alliance Partners F 5 Technology Alliance Partners http: //www. f 5. com/solutions/deployment/ http: //www. f 5. com/solutions/technology/pdfs/dc_virtualization_wp. pdf http: //www. f 5. com/solutions/technology/pdfs/atm_wp. pdf http: //www. f 5. com/solutions/applications/ http: //www. f 5. com/solutions/sb/ http: //www. f 5 demo. com/compression/index. php http: //www. f 5. com/solutions/partners/i. Control/ http: //www. f 5. com/solutions/partners/tech/ Let us know if you need any clarification or you have any further questions.

83 Thank You
b62479e83fafa050b6cf987c0ea267b3.ppt